Enterprise customers no longer take vendors at their word when it comes to protecting data. Large buying organizations send extensive security questionnaires before signing purchase orders. They expect suppliers to implement a formal Information Security Management System (ISMS) and to show evidence that software is built and maintained securely. ISO 27001 is the most widely recognized framework for meeting those expectations. Its 2022 update introduced a new control, Annex A 8.25, that formalizes a “secure development life cycle” requirement. By aligning software development processes with this control, vendors demonstrate that security is more than a box‑checking exercise. They mitigate the risk of breaches, accelerate sales cycles, and build confidence among auditors, regulators, and users.
This article explores what ISO 27001 Secure SDLC means, why it matters to enterprise‑focused vendors, and how to implement it. Drawing on guidance from ISO/IEC 27001:2022, NIST’s Secure Software Development Framework, and lessons from more than 6,000 audits delivered by Konfirmity’s experts over 25 years, it offers a pragmatic blueprint for embedding security in your software development lifecycle. Concrete examples and current data points show the business benefits of this discipline. When done right, a secure SDLC is not an overhead—it’s a core part of product quality and business continuity.
What Is ISO 27001 Secure SDLC?
Annex A 8.25 of ISO/IEC 27001:2022 requires organizations to establish and apply rules for the secure development of software and systems. The standard succinctly states that “rules for the secure development of software and systems should be established and applied”. Control 8.25 sits within the preventive controls section of Annex A and aims to make security an inherent aspect of development rather than an after‑the‑fact patch. Advisera notes that the control obliges companies to define rules for secure planning, development, testing, deployment, maintenance and disposal. In other words, the entire lifecycle must be designed with security in mind.
The concept of ISO 27001 Secure SDLC differs from ad hoc coding guidelines or periodic penetration tests. It is a structured process integrated into the ISMS. It covers requirements gathering, design, coding, testing, deployment, and maintenance. The control works hand in hand with related controls such as Annex A 8.28 (secure coding), which mandates that secure coding principles should be applied to software development; Annex A 8.29, which requires organizations to define and implement security testing processes during development; and Annex A 8.31, which calls for the separation of development, test and production environments. Together, these controls form a cohesive framework for building trustworthy software.
Why ISO 27001 Secure SDLC Matters for Enterprise Clients
Security incidents are expensive and disruptive. The IBM 2025 Cost of a Data Breach report, summarized by Bright Defense, found that the global average cost of a breach dropped slightly to USD 4.44 million in 2025 (down from USD 4.88 million in 2024), while the average cost in the United States climbed to USD 10.22 million. Certain attack types—malicious insiders, supply‑chain compromises and phishing—each averaged around USD 4.9 million per incident. The same analysis notes that customer personally identifiable information cost an average of USD 160 per record. These numbers underscore that security failures are not abstract; they directly affect profitability.
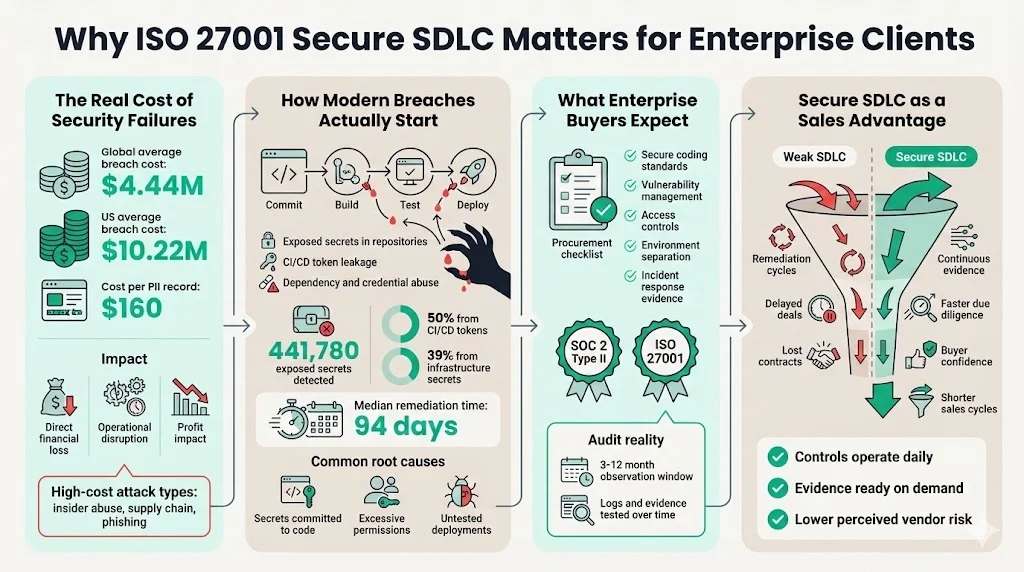
Modern breaches often start with compromised credentials or exploited dependencies rather than headline‑grabbing exploits. Verizon’s 2025 Data Breach Investigations Report revealed that scanners monitoring public repositories found 441,780 exposed secrets, with GitLab tokens making up 50% of CI/CD‑related leaks and web application infrastructure secrets representing 39%. The median time to remediate leaked secrets was 94 days, giving attackers three months to weaponize them. Credential abuse was identified as the most common initial access vector (22%), followed by exploitation of vulnerabilities (20%) and phishing (15%). These statistics show that unsound practices—committing keys to code, deploying untested code, granting excessive permissions—are the root cause of breaches.
Enterprise procurement teams know this. Their due diligence questionnaires require proof of information security policies, secure coding standards, vulnerability management, access controls, and environment separation. Large buyers often demand SOC 2 Type II or ISO 27001 certificates before closing contracts. For SOC 2, the observation period for a Type II report typically ranges from three to twelve months. During this window auditors test controls using logs, access records and incident response actions. The process demonstrates that security controls operate effectively over time, not just on paper. When vendors lack a secure SDLC, they face delayed sales cycles, endless remediations, and lost deals. Conversely, vendors that can produce evidence of a secure SDLC shorten due‑diligence cycles and inspire confidence.
How ISO 27001 Secure SDLC Fits Within an ISMS
Relation to ISO 27001 Clauses and Controls
In ISO 27001:2022, Control 8.25 belongs to a cluster of development‑related controls designed to ensure that security is built into software from conception to retirement. Control 8.25 mandates secure development rules; Control 8.28 extends these rules by requiring adherence to secure coding principles so that software is written securely and vulnerabilities are minimized. Control 8.29 calls for a defined security testing process during development and acceptance, emphasizing that security testing processes should be defined and implemented in the development life cycle. Control 8.31 requires that development, testing and production environments be separated and secured to prevent test data or tools from compromising live systems. Controls 8.24 (change management), 8.27 (secure systems architecture) and 8.32 (change management) also support the secure SDLC.
Secure SDLC is not isolated from the rest of the ISMS. Clauses 4–10 of ISO 27001 prescribe the context, leadership, planning, support, operation, performance evaluation, and improvement of the ISMS. Secure development activities must be scoped within the ISMS, supported by leadership, and aligned with the risk assessment process. For example, when developing new features, teams should evaluate threats, assign risk ratings, and map them to the Statement of Applicability (SoA). Control 8.25 also interacts with A.5.7 (Threat intelligence), A.5.8 (Information security in project management) and A.5.14 (Monitoring and logging) to ensure that development activities are informed by threat data and monitored appropriately.
Information Security Management Integration
A secure SDLC aligns with ISO 27001’s core principles: risk‑based thinking, continual improvement and documented evidence. The Secure Software Development Framework (SSDF) published by NIST describes secure software practices that complement ISO 27001. NIST notes that secure development practices, such as those in the SSDF, reduce the number of vulnerabilities in released software, reduce the impact of unaddressed vulnerabilities, and address root causes to prevent recurrence. The SSDF organizes practices into four groups—Prepare the organization, Protect the software, Produce well‑secured software, and Respond to vulnerabilities—mirroring ISO 27001’s emphasis on planning, implementation, operation and improvement.
Risk assessment is the heart of an ISMS. Before starting a project, teams should perform a threat analysis, evaluate the likelihood and impact of security failures, and decide on controls. For example, if a module will handle personal health information (PHI), the team must determine whether HIPAA safeguards apply. If encryption is mandated, the design phase must include key management planning. During implementation, risk assessment drives the selection of secure coding libraries and dependency management. Continuous monitoring—another ISO 27001 requirement—feeds back into the SDLC, highlighting emerging threats and vulnerabilities. The improvement cycle then updates development processes, training, and documentation.
Core Requirements of ISO 27001 Secure SDLC
Defined Rules and Process Documentation
The starting point for ISO 27001 Secure SDLC is documentation. Organizations must define and document their secure development processes, covering planning, requirements, design, coding, testing, deployment, maintenance and retirement. This documentation should outline responsibilities, approval workflows, and acceptance criteria. A Secure Development Policy or a secure software development procedure can serve as the governing document. It should reference related policies such as change management, access control, and incident response. The policy ensures consistency across teams and provides auditors with a single reference point.
Separation of Environments
A fundamental requirement is that development, test and production environments remain separate. The standard states that development, testing and production environments should be separated and secured. In practice, this means that code under development and testing cannot run on production servers. Production data must not be used in development without proper anonymization. Access to each environment should follow the principle of least privilege. Deployments should go through a formal promotion process with documented approvals. In many organizations, infrastructure as code and continuous integration/continuous deployment (CI/CD) pipelines enforce these separations automatically, using different accounts, networks and storage for each stage.
Security Requirements Early in SDLC
Security is most effective when addressed during planning and requirements. Risk assessments, threat modeling and data classification should occur before design. Requirements should specify authentication methods, encryption, logging, and privacy constraints. When security requirements are defined too late, they often conflict with architecture choices and lead to costly redesign. Organizations that integrate security requirements early see fewer defects and shorter remediation times. Our experience at Konfirmity shows that addressing security requirements in the first two sprints reduces later vulnerability remediation by 60–70%.
Secure Coding Standards
ISO 27001 Annex A 8.28 mandates secure coding principles. Wiz’s secure coding overview notes that secure coding tackles vulnerabilities like cross‑site scripting and memory leaks early, boosting software resilience and reducing risks. It emphasizes that best practices include validating inputs, securing third‑party code and using static application security testing (SAST) tools. Security Journey’s training guide lists nine core practices: validate all user inputs, encode outputs, enforce strong authentication and session management, apply least privilege, use secure error handling, conduct code reviews and automate scanning, manage third‑party dependencies with Software Bills of Materials (SBOMs), include threat modeling early in design, and use parameterized queries to prevent SQL injection. A documented coding standard should incorporate these practices and map them to language‑specific guidelines. Teams should also establish code review checklists to verify adherence.
Security Testing and Vulnerabilities Management
Annex A 8.29 requires security testing during development and acceptance. The control stipulates that security testing processes should be defined and implemented in the development life cycle. Testing must cover unit, integration, system and acceptance phases, with security‑specific activities such as static code analysis, dynamic analysis, fuzzing, dependency scanning and penetration tests. Test plans should define success criteria and remediation timelines. All findings must be logged, prioritized (e.g., using CVSS scores) and tracked through remediation. At Konfirmity, we advocate vulnerability SLAs—critical vulnerabilities fixed within seven days, high within 14 days and medium within 30 days. Meeting these SLAs improves audit outcomes and reduces breach risk.
Access and Code Repository Controls
Securing the software supply chain requires controlling access to source code, build systems and repositories. Secrets exposure is a leading cause of breaches; Verizon’s 2025 report found that 43% of cloud‑related secrets exposed in public repos were Google Cloud API keys. Organizations must implement least‑privilege access to repositories, enforce multi‑factor authentication, and regularly review permissions. Secrets should be stored in vaults, never in code or configuration files. Code repositories should enforce branch protections, require code reviews and integrate scanning tools. Access logs must be retained for audits. For third‑party components, maintain an SBOM and monitor for vulnerabilities. NIST’s SSDF emphasises the need to protect all components of software from tampering and unauthorized access.
Training and Skills
Developers and stakeholders need appropriate training on secure development. Secure SDLC requires more than awareness; it demands competency. That means training on threat modeling, secure coding patterns, dependency management, and vulnerability triage. Security Journey highlights the importance of role‑based training paths that go beyond generic awareness. At Konfirmity, we deliver hands-on workshops where developers fix real vulnerabilities, practice code reviews, and simulate attack chains. We also train project managers on how to plan for security, testers on security testing methods, and DevOps teams on secure CI/CD. Competency matrices help identify gaps and guide training priorities.
Step‑by‑Step Secure SDLC Walkthrough
This section offers a practical roadmap to implement ISO 27001 Secure SDLC in your organization. It aligns with the principles of ISO 27001 and the NIST SSDF while reflecting lessons from thousands of audits.
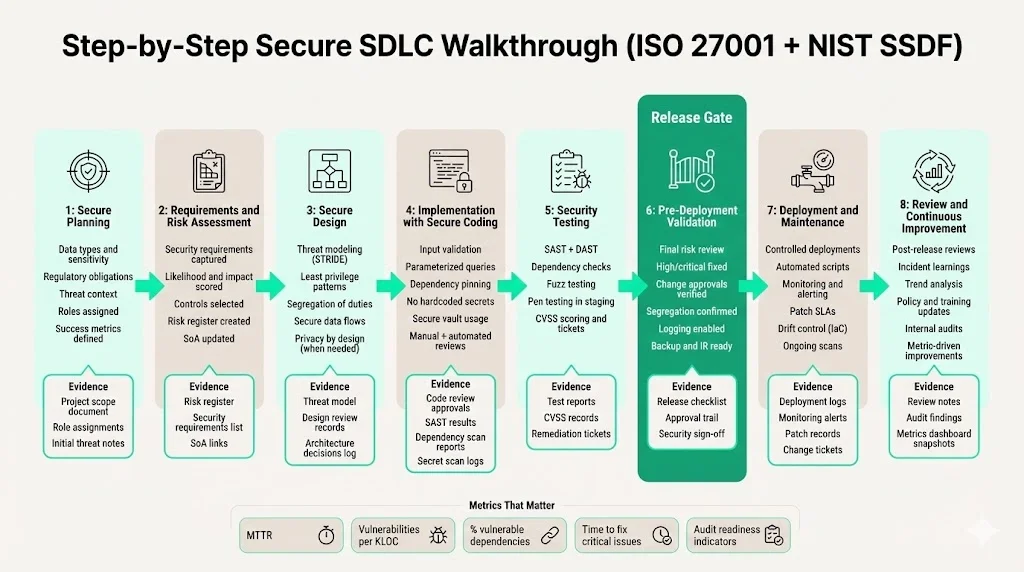
Step #1: Secure Planning
Every project should start with clear objectives and risk context. Identify the data types involved (PII, PHI, intellectual property), regulatory obligations (e.g., HIPAA, GDPR), and business requirements (uptime, scalability). Perform a preliminary threat analysis to understand potential attack vectors. Align objectives with the organization’s risk appetite and existing ISMS. Document the scope and assign roles—product owner, security architect, developers, testers. Define success metrics such as vulnerability density, time to fix, and audit‑readiness measures. At Konfirmity, we embed a security representative in every project to ensure alignment from day one.
Step #2: Requirements and Risk Assessment
Gather functional and non‑functional requirements with security front and center. Conduct a formal risk assessment that identifies threats, evaluates their likelihood and impact, and recommends controls. For example, if the system processes personal data, plan encryption at rest and in transit. If the system will be available to third parties via API, specify rate limiting, input validation and authentication requirements. Document these as security requirements alongside functional ones. Align them with compliance standards such as ISO 27001 Secure SDLC, SOC 2 Trust Services Criteria, HIPAA or GDPR. The risk assessment should produce a risk register and an updated SoA.
Step #3: Secure Design
Translate security requirements into architecture and design decisions. Use threat modeling techniques, such as STRIDE, to identify attack surfaces and design mitigations. Choose design patterns that enforce least privilege and segregation of duties. For example, implement a layered architecture with separate interfaces, business logic and data access layers; use microservices with separate identities and RBAC; design data flows that avoid sharing secrets across services. Document design decisions and their security rationale. Incorporate privacy by design principles if personal data is processed. Engage security architects and engineers in design reviews to ensure controls are integrated and practical.
Step #4: Implementation with Secure Coding
During development, follow the secure coding standards established earlier. Validate and sanitize all user inputs. Encode outputs appropriately to prevent injection attacks. Use parameterized queries and prepared statements. Pin third‑party dependencies to specific versions and monitor for vulnerabilities. Enforce least‑privilege access to code repositories. Automate code reviews with linters, SAST and software composition analysis, but supplement them with manual reviews. Avoid hardcoded secrets; retrieve them from secure vaults. Keep code comments and logs free of sensitive data. Document code for maintainability, but ensure internal details are not exposed to end users. Use modern languages or memory‑safe constructs when possible. Where system programming requires C/C++, use smart pointers and static analyzers.
Step #5: Security Testing
Combine functional quality assurance with security testing. Create test plans that cover unit, integration, system and acceptance levels. Use static and dynamic analysis tools to detect code‑level vulnerabilities. Run dependency checks to identify known vulnerabilities in libraries. Perform fuzz testing on input interfaces. Conduct authenticated penetration tests on staging environments to simulate real attack paths. For critical releases, include red team exercises. Document all test results, classify vulnerabilities using CVSS, and open tickets for remediation. Ensure testers have clear criteria for passing or failing a build based on security findings. Incorporate testing in continuous integration pipelines to prevent vulnerable code from reaching production.
Step #6: Pre‑Deployment Validation
Before deployment, conduct a final risk review. Verify that all security requirements have been implemented and that high‑ and critical‑severity vulnerabilities have been fixed. Review the change management process to ensure approvals are documented. Check that environment segregation remains intact and that secrets are stored properly. Ensure that logging and monitoring are enabled at the right levels. Confirm that backups, disaster recovery and incident response plans are in place. At Konfirmity, we hold a “release gate” meeting where the security lead signs off on deployment readiness. Only after this sign‑off can the code be promoted to production.
Step #7: Deployment and Maintenance
Deploy code through a controlled pipeline that enforces approvals and reproducibility. Use automated scripts rather than manual steps to reduce human error. After deployment, monitor systems using SIEM and application performance monitoring to detect anomalies. Patch vulnerabilities promptly, following defined SLAs. Conduct regular vulnerability scans and penetration tests. Manage configuration drift through infrastructure as code. For third‑party components, track new vulnerabilities and apply updates promptly. Document all changes, fixes and incidents for audit trails. Over time, track metrics such as mean time to remediation (MTTR), number of vulnerabilities per thousand lines of code, and percentage of dependencies with known vulnerabilities.
Step #8: Review and Continuous Improvement
Security is never static. After each release or audit, review what worked and what didn’t. Analyze incident reports, vulnerability trends and audit findings. Update policies, procedures and training accordingly. Perform periodic internal audits to test compliance with the secure SDLC. Engage external auditors annually or biannually to validate. Use metrics to drive improvement—for example, reducing the percentage of high‑severity vulnerabilities by a certain percentage each quarter. Encourage a culture where developers report and fix security issues without blame. The goal is a feedback loop that continually enhances security and quality.
Templates and Tools to Support Implementation
Secure Development Policy Template
A secure development policy should define the purpose, scope, roles and responsibilities for secure software development. It should reference the ISO 27001 controls, outline phases of the SDLC, specify coding and testing standards, and describe approval workflows. The policy should also establish requirements for documentation, training, and evidence retention. While there is no mandated template, high‑quality policies cover these elements and are reviewed annually. Konfirmity provides a policy template that aligns with ISO 27001 Secure SDLC and maps each section to specific Annex A controls.
Risk Assessment and Threat Model Templates
Effective risk management requires structured documents. A risk assessment template should capture assets, threats, vulnerabilities, impact, likelihood, risk ratings, and proposed controls. It should also link to compliance requirements and assign owners for remediation. A threat modeling template can guide teams through identifying attack surfaces, modeling abuse cases, and prioritizing mitigations. Templates accelerate this work and standardize outputs, making audits smoother.
Security Control Checklist
For each phase of the SDLC, create a checklist of security tasks tied to ISO 27001 Secure SDLC requirements and related controls. For example:
- Planning: identify data types, regulatory obligations, threat sources.
- Requirements: document security requirements alongside functional ones.
- Design: conduct threat modeling; define authentication, authorization, encryption and logging approaches.
- Implementation: follow secure coding standards; avoid hardcoded secrets; integrate code scanning tools.
- Testing: run SAST, dynamic testing, dependency scanning and penetration tests.
- Deployment: verify environment separation; ensure secure configurations; enable monitoring.
- Maintenance: monitor vulnerabilities; patch promptly; review access rights.
Checklists improve consistency, help new team members quickly understand expectations and simplify evidence collection during audits.
Audit and Compliance Evidence Templates
Auditors look for evidence that controls operate consistently. Maintain logs of code reviews, test results, vulnerability reports, change approvals, access reviews, training records and incident responses. Use templates to standardize how evidence is recorded—e.g., test report templates with summary, test cases, outcomes, and remediation actions. Keep an evidence register that maps artifacts to specific controls in the Statement of Applicability. During an ISO 27001 audit, having organized evidence can reduce disruption and shorten the audit cycle.
Best Practices and Pitfalls to Avoid
1) Embed Security Throughout, Not at the End
Security must be integrated into every SDLC phase. Fixing vulnerabilities after deployment costs far more than preventing them during development. Security Journey notes that secure coding best practices prevent vulnerabilities and reduce expensive fixes. Starting with clear security requirements and a threat model ensures that later phases are aligned. Avoid the trap of scheduling a penetration test a week before release and calling it secure development. That approach breeds last‑minute remediation and expensive delays.
2) Use Automated Tools to Augment Manual Reviews
Automation accelerates detection and remediation. Static and dynamic analysis tools, linters, dependency scanners and secret scanners catch issues that human reviewers may miss. For example, automated secret scanning can prevent the leakage of API keys and tokens, a common initial access vector. However, automation should complement—not replace—human oversight. Code reviews, threat modeling sessions and design discussions are essential for contextual understanding.
3) Track Metrics for Continuous Improvement
Without metrics, it’s hard to know if your secure SDLC is working. Track the number of vulnerabilities found per release, time to remediation, test coverage, and percentage of dependencies with known vulnerabilities. Measure training completion rates and assess developer competency through secure coding assessments. Use these metrics to set goals and drive accountability. For example, aim to reduce high‑severity findings by 30% within a year or decrease average time to fix critical vulnerabilities to seven days. Monitoring metrics helps demonstrate to auditors and clients that security is under control.
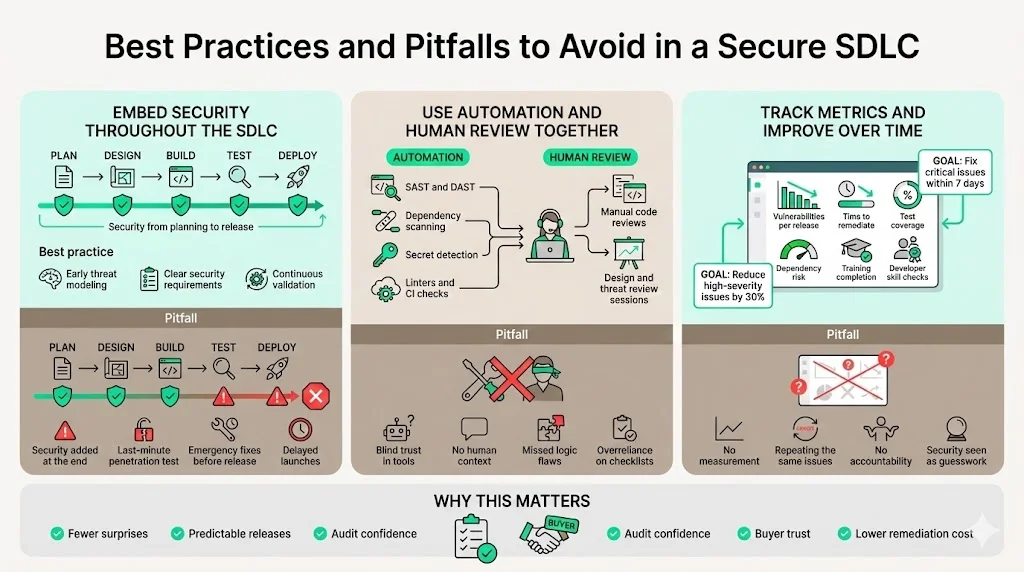
Avoid Common Pitfalls
Several pitfalls derail secure SDLC efforts:
- Lack of leadership buy‑in: Security requires executive support. Without it, teams prioritize features over controls.
- Fragmented ownership: When responsibility for security is unclear, tasks fall through the cracks. Assign roles and responsibilities in your policy.
- Untrained developers: Secure coding requires knowledge. Invest in training and continuous learning.
- Ignoring third‑party risks: Dependencies and SaaS services bring their own risks. Maintain an SBOM and monitor vendor security.
- Insufficient testing coverage: Running a single SAST tool is not enough. Combine static, dynamic, interactive and manual testing.
- Poor secrets management: Hardcoded credentials are still a leading cause of breaches. Use vaults and enforce rotation.
- Complacency after certification: ISO 27001 is not a one‑and‑done exercise. Continual improvement is mandatory.
Conclusion
Enterprise clients and healthcare organizations demand evidence that vendors build secure software. ISO 27001 Secure SDLC, formalized in Annex A 8.25, provides a structured way to meet those expectations. The control requires defined rules for secure development, supported by related controls on secure coding, security testing and environment separation. Integrating these controls into an ISMS aligns software development with risk management and continual improvement. The benefits are tangible: fewer breaches, faster sales cycles, lower remediation costs and stronger trust.
At Konfirmity, we’ve witnessed how organizations transform when they embrace a secure SDLC. Teams that incorporate security requirements from day one, enforce secure coding standards, conduct regular security testing, and document evidence find that audits become routine rather than traumatic. They also discover that security practices improve product quality. Conversely, teams that treat security as an add‑on face delayed deals, long remediation lists and higher breach costs.
Security that looks good on paper but fails under incident pressure is a liability. The path forward is clear: build controls into your software once, operate them daily, measure outcomes and improve continuously. A well‑implemented ISO 27001 Secure SDLC isn’t just about passing audits—it’s about earning the trust of customers and regulators while delivering resilient products.
FAQ
Q1: What is ISO 27001 Secure SDLC?
ISO 27001 Secure SDLC refers to Annex A 8.25 of ISO/IEC 27001:2022, which requires organizations to establish and apply rules for the secure development of software and systems. It ensures that security is addressed throughout the development lifecycle, from planning through disposal.
Q2: Do we need a Secure SDLC for ISO 27001 certification?
Yes. Control 8.25 is part of Annex A, and auditors typically expect to see policies, procedures and evidence showing that secure development practices are applied. This includes documented processes, training records, risk assessments, coding standards, test results and environment separation.
Q3: How does a Secure SDLC differ from a regular SDLC?
A regular SDLC focuses on delivering functional requirements. A Secure SDLC integrates risk assessment, threat modeling, secure coding practices, security testing and environment separation at every stage. It follows ISO 27001 controls (8.25, 8.28, 8.29, 8.31) to embed security rather than bolting it on later.
Q4: What documents are required for ISO 27001 SDLC compliance?
Key documents include a Secure Development Policy, risk assessment records, threat models, secure coding standards, security test plans and reports, change approvals, access reviews, training logs, and evidence of environment separation. These documents map to the Statement of Applicability and provide audit evidence.
Q5: How do enterprises prove Secure SDLC during an audit?
Auditors look for documented policies and procedures, evidence of training, risk assessments, design reviews, code review records, test results, vulnerability management logs, change management approvals, environment separation evidence and continuous improvement reports. The presence of a functioning Secure SDLC that produces consistent evidence over time is the best proof.





.svg)






.svg)
.svg)