Most enterprise buyers now ask for assurance evidence before procurement. Without credible security practices and continuous evidence, deals stall even when teams believe they are ready on paper. This guide explains ISO 27001 What Changed In 2026 and what enterprise teams must do to stay audit‑ready. It looks at the revised standard, the 2024 environmental amendment and how these changes affect risk, contracts and audits in 2026. As founder of Konfirmity, a managed security and compliance provider with over 6,000 audits supported and 25 years of combined expertise, I’ll discuss how to build security programmes that satisfy tough buyers and auditors alike.
What is ISO 27001?
ISO 27001 is an international standard for building and operating an Information Security Management System (ISMS). An ISMS sets a structured approach for identifying risks, selecting controls and demonstrating that those controls operate effectively. Certification under ISO 27001 signals that an organisation has considered its business context, documented applicable requirements and follows a defined risk‑management process. Because the standard is vendor‑neutral and globally recognised, it often appears on procurement checklists for large clients.
For enterprise deals, ISO 27001 compliance is frequently mandatory. Procurement teams and security officers use it to verify that vendors manage information risks in a repeatable way. Certification helps address questions about data confidentiality, integrity and availability and can shorten due‑diligence cycles. The standard’s clauses require organisations to:
- Assess their organisational context and external factors that might influence security decisions.
- Maintain documented information such as policies, risk registers and evidence records.
- Implement and monitor Annex A controls (now 93 of them) in areas such as access control, physical security and supplier management.
- Undergo regular internal and external audits to verify control design and operating effectiveness.
The ISMS is not only for IT teams. Executives must approve the scope and objectives, managers must integrate security requirements into business processes, and staff must follow defined procedures. Without executive backing and cross‑functional engagement, certification becomes a paper exercise.
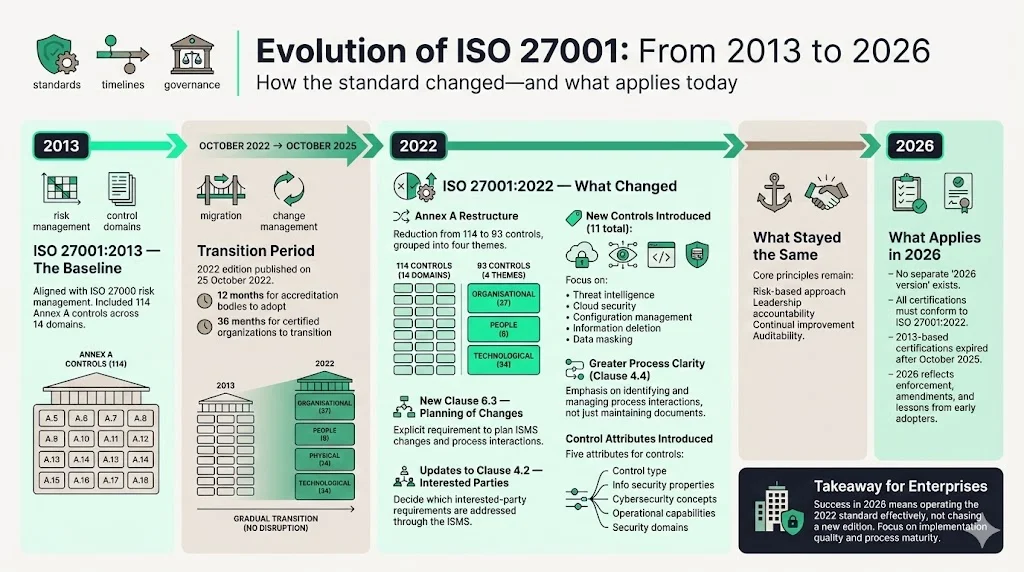
Evolution of ISO 27001: From 2013 to 2026
The modern ISO 27001 standard has evolved through several revisions. The 2013 edition aligned with the risk management framework in ISO 27000 and contained 114 Annex A controls organised into 14 domains. On 25 October 2022, a new version of ISO 27001 was published. Accreditation bodies had 12 months from the publication month to adopt the new edition, and certified organisations were given 36 months – until 31 October 2025 – to transition. This long transition allowed enterprises to update documentation and control implementations without disrupting ongoing audits.
The 2022 revision introduced important updates:
- Fewer controls and new groupings. Annex A now contains 93 controls instead of 114, grouped into four themes: organisational, people, physical and technological. The reduction was achieved by merging similar controls and introducing 11 new ones. Those new controls cover threat intelligence, cloud service security, configuration management, information deletion, data masking, data leakage prevention, monitoring, web filtering and secure coding.
- New clause 6.3 – planning of changes. The standard now explicitly requires organisations to plan ISMS changes, including process interactions.
- Updated requirements for interested parties. Clause 4.2 adds a bullet requiring organisations to decide which interested‑party requirements will be addressed through the ISMS.
- Greater clarity on processes. Clause 4.4 emphasises that organisations must not only maintain the ISMS but also identify and manage the interactions of processes.
- Attributes for controls. The 2022 version introduces five attributes – control type, information security properties, cybersecurity concepts, operational capabilities and security domains – to help teams categorise and rationalise controls.
These updates were designed to reflect modern threats and to simplify the structure. A comparison of the 2013 and 2022 editions shows that the number of controls decreased and the standard’s wording was adjusted, but core principles remain. The International Accreditation Forum (IAF) mandated that organisations transition to the 2022 edition by October 2025; certifications based on the 2013 version will expire after that.
By 2026, all organisations pursuing ISO 27001 certification must therefore conform to the 2022 edition. There is no standalone “2026 version” of the standard. However, the environment in 2026 includes the 2022 version and its amendments, enforcement of transition deadlines and lessons learned from early adopters.
What Has Actually Changed in 2026
Although there is no official ISO 27001:2026 edition, the compliance landscape in 2026 reflects several significant developments:
- Transition deadline enforcement. Certification bodies and auditors now operate under the assumption that organisations have moved to the 2022 edition. According to the Cloud Security Alliance, there was a 36‑month transition period for certified organisations beginning when ISO/IEC 27002:2022 was published, with all ISO 27001:2013 certifications expiring by 31 October 2025. Any organisation that did not complete its transition by that date must start the certification process anew.
- Environmental change considerations. In February 2024, ISO published Amendment 1 (often referred to as the climate action amendment) to ISO 27001:2022. This amendment directs organisations to consider whether environmental changes and extreme weather are relevant issues in their context and to recognise that interested parties may have requirements related to environmental conditions. The amendment adds a sentence to clause 4.1 requiring organisations to assess whether changes in the environment are relevant. It also adds a note to clause 4.2 stating that interested parties may have requirements related to environmental conditions. If an organisation determines that such changes are not relevant, it must still document that decision. This amendment acknowledges that floods, fires and supply‑chain disruptions can affect data availability and thus fall within the scope of an ISMS.
- Auditor expectations. In 2026, auditors are focusing not only on the presence of controls but on how effectively they reduce risk. There is greater scrutiny of risk assessments, documented evidence and continuous monitoring. Auditors expect to see documented risk treatment plans, updated statements of applicability and traceable evidence of control operation. They also expect to see how environmental risks have been considered.
- Increased penalties for breaches. The cost of non‑compliance has risen. IBM’s 2025 Cost of a Data Breach report found that the average cost of a data breach in the United States reached USD 10.22 million, while the global average cost fell to USD 4.44 million. The report noted that shorter detection times reduce costs; however, U.S. organisations continue to face higher regulatory fines. This financial pressure makes certification and effective controls more crucial.
- Market expectations. Buyers increasingly demand evidence of continuous control operation. Procurement questionnaires now include detailed queries about risk assessments, third‑party oversight, vulnerability management and incident response metrics. ISO 27001 certification remains a baseline requirement, but many clients also expect alignment with other frameworks such as SOC 2, HIPAA and GDPR.
Transition to ISO 27001:2022 and Beyond
The transition from the 2013 edition to the 2022 edition has been more than an administrative exercise. It has required organisations to update risk assessments, policies and procedures, and to re-evaluate the relevance of controls.
Transition timeline
According to the International Accreditation Forum and guidance from accreditation bodies, the timeline for the transition has three tiers:
- Accreditation bodies were required to transition their own accreditation processes within 12 months of the publication month of ISO 27001:2022 – by 31 October 2023.
- Certification bodies had to begin certifying against the 2022 edition within that same 12‑month window. They have been performing transition audits and recertifications on their clients during regular surveillance or recertification visits.
- Certified organisations had a 36‑month window to transition, ending 31 October 2025. After that date, any ISO 27001:2013 certificate expires.
The Cloud Security Alliance notes that organisations conducting recertification reviews during the transition period were required to start those reviews against ISO 27001:2022 no later than 18 months after publication – by 30 April 2024. Organisations not yet certified were not allowed to initiate certification against the 2013 edition after 30 April 2024. These dates mean that by 2026 every certification audit is against the 2022 edition.
Transition audit focus
Transition audits include:
- A gap analysis comparing the existing ISMS against the 2022 edition.
- Updates to the statement of applicability and risk treatment plan to reflect the revised controls.
- Assessment of new or changed controls selected by the organisation, verifying their effectiveness.
When carried out during recertification, transition audits typically require an additional half day of auditor time; when done separately or during surveillance audits, they may require a full additional day.
New and Updated Control Requirements
The most visible change in the 2022 edition is the restructuring of Annex A controls. Understanding these changes is vital to answering procurement questionnaires and passing audits in 2026.
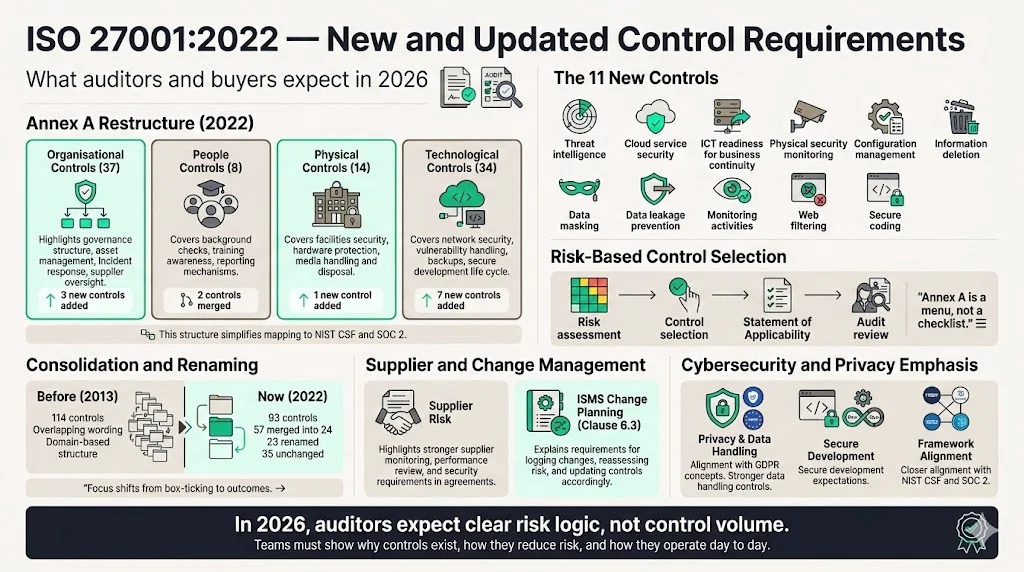
Four control categories
Annex A controls are now divided into four categories:
- Organisational controls (37) – cover governance, asset management, business continuity, access control, incident response and supplier management. Three new controls were added in this category.
- People controls (8) – address background checks, training, remote working and incident reporting. Two controls were merged.
- Physical controls (14) – ensure that facilities, hardware and storage media are protected. One new control was added.
- Technological controls (34) – focus on networks, software, vulnerability management, backups and secure development. Seven new controls were added.
This structure simplifies control mapping and helps organisations group related processes. It also makes it easier to cross‑reference controls with other frameworks such as NIST CSF (Identify, Protect, Detect, Respond, Recover) or SOC 2’s Trust Services Criteria.
Eleven new controls
The 2022 edition introduces 11 new controls. These additions reflect modern threat vectors and technology practices:
- Threat intelligence – collect and analyse threat data and integrate it into incident response.
- Cloud service security – define policies for using cloud services, including requirements for data transfer, retention, deletion and access.
- ICT readiness for business continuity – translate business impact analyses into continuity strategies.
- Physical security monitoring – implement surveillance systems that are tamper‑proof and respect privacy requirements.
- Configuration management – establish secure configuration baselines and monitor for deviations.
- Information deletion – ensure data is destroyed when no longer needed, taking legal requirements into account.
- Data masking – apply techniques such as pseudonymisation and anonymisation to protect sensitive information.
- Data leakage prevention – classify information, monitor channels and prevent unauthorised disclosure.
- Monitoring activities – continuously monitor the network and systems for anomalies.
- Web filtering – block malicious content and train staff on acceptable use.
- Secure coding – embed secure coding practices into software development.
Consolidation and renaming
Fifty‑seven controls were merged into 24 groups and 23 controls were renamed for clarity. Thirty‑five controls remain unchanged. This consolidation reduces redundancy and encourages organisations to focus on outcomes rather than ticking boxes. Because controls now include attributes such as control type and cybersecurity concepts, organisations can more easily map them to other frameworks or risk‑management models.
Risk‑based control selection
The revised standard reinforces a risk‑based approach. Clause 6.1.3 in ISO 27001:2022 clarifies that Annex A is a list of possible information security controls rather than an exhaustive checklist. Organisations must design or select controls based on their own risk assessments and business context. This means that not all 93 controls are mandatory; only those relevant to identified risks must be implemented. However, auditors will scrutinise the rationale behind control selection and expect to see evidence that risks have been assessed and treated appropriately.
Supplier and change management
Procurement teams care deeply about third‑party risk. The 2022 revision strengthens requirements for supplier management by combining several supplier‑related controls and adding more specific guidance on monitoring supplier performance. It also introduces a new clause (6.3) requiring organisations to plan changes to their ISMS. In practice, this means that companies must maintain change logs, assess the impact of changes on controls and ensure that risk assessments remain current.
Cybersecurity and privacy focus
Several new controls address data protection and privacy. Data masking and data leakage prevention align with global privacy regulations such as GDPR, while secure coding reflects the increasing reliance on internal development. By explicitly acknowledging threat intelligence and monitoring, the standard nudges organisations toward proactive security. These changes bring ISO 27001 closer to frameworks such as the NIST Cybersecurity Framework and SOC 2, making cross‑framework mapping easier for teams that must satisfy multiple clients.
Impact of ISO 27001 Amendments
The most notable amendment to ISO 27001:2022 as of 2026 is Amendment 1:2024, which integrates environmental considerations. The amendment requires that organisations:
- Evaluate whether environmental changes (such as floods, fires, storms or prolonged heat) could affect the confidentiality, integrity or availability of information.
- Recognise that customers, regulators and other interested parties may require them to address environmental risks.
- Document their decision if they determine that environmental changes are not relevant.
For enterprises selling to large clients, this amendment means that risk assessments, business continuity plans and supplier management must consider extreme weather scenarios. Disaster recovery plans should cover scenarios where data centres are inaccessible or power and communications networks fail. Vendor due‑diligence questionnaires may now include questions about environmental risk planning.
Alignment with Other Standards
Enterprise buyers often ask vendors to show compliance with multiple frameworks. ISO 27001 intersects with several other standards:
- ISO 27701 for privacy management. ISO 27701 extends ISO 27001 to include privacy requirements. It adds controls for data subject rights, data retention and disclosure management. Aligning with ISO 27701 allows organisations to address GDPR and other privacy regulations more effectively.
- SOC 2. The AICPA’s SOC 2 framework evaluates controls against five trust services criteria: security, availability, processing integrity, confidentiality and privacy. ISO 27001’s organisational, technological and people controls map well to SOC 2 criteria. Konfirmity often helps clients build a unified control library that satisfies both ISO 27001 and SOC 2, reducing evidence collection overhead.
- HIPAA. For healthcare providers, HIPAA requires administrative, physical and technical safeguards to protect electronic protected health information (ePHI). ISO 27001 controls such as access management, audit logging and incident response support these safeguards. A Business Associate Agreement (BAA) may still be required.
- GDPR. The European Union’s data‑protection regulation demands data minimisation, purpose limitation and accountability. ISO 27001’s risk assessment and data protection controls (e.g., data masking, deletion) provide a foundation for GDPR compliance.
Aligning ISO 27001 controls with these frameworks helps vendors respond to due‑diligence questionnaires more efficiently. At Konfirmity, we routinely map controls across SOC 2, ISO 27001, HIPAA and GDPR, delivering unified evidence packages. This approach allows enterprise buyers to verify controls once instead of requesting separate sets of artifacts.
What These Changes Mean for Your Team
With the transition complete and the environmental amendment in place, teams must shift from documentation updates to operational practice. Below are practical impacts under four themes.

1. Information Security Management in Practice
- Update documentation. Maintain a current risk register, policies and procedures. Include environmental risks, and ensure your statement of applicability references the 2022 controls.
- Review organisational context. As your business expands or introduces new services (e.g., SaaS products, mobile apps), re‑evaluate external factors and interested parties. Consider geopolitical events, new laws and environmental hazards.
- Maintain evidence. Evidence must show that controls operate consistently over time. For example, logs of access reviews, change approvals, incident tickets and training records should be kept and periodically reviewed.
Konfirmity’s managed service maintains living documentation on behalf of clients. Our experts update policies and risk registers and produce evidence automatically. This reduces internal workload from hundreds of hours to about 75 hours per year, compared with 550–600 hours for self‑managed programmes.
2. Risk Management Expectations
- Formal risk assessments. Conduct regular risk assessments and link each identified risk to a control or treatment plan. Use structured scoring methods (e.g., probability × impact) and document rationale.
- Continuous monitoring. The cost of breaches and the speed of attacks demand continuous monitoring. Controls such as monitoring activities and threat intelligence should feed into risk assessments, enabling rapid adjustments. According to IBM’s 2025 report, faster detection reduces breach costs.
At Konfirmity we integrate threat feeds, vulnerability scans and configuration monitoring into a unified risk dashboard. This live view allows clients to identify issues before they become audit findings.
3. Compliance Requirements and Enterprise Contracts
- Procurement questionnaires. Enterprise buyers now ask not only for ISO 27001 certification but for evidence of control operation. Questions often cover incident response metrics, recovery time objectives, supplier oversight and data protection measures. Be prepared to provide evidence of the 11 new controls and to explain how environmental risks are managed.
- Contract clauses. Expect contractual clauses requiring compliance with ISO 27001:2022 and other frameworks. Some contracts impose service‑level agreements (SLAs) for incident response, vulnerability remediation and supplier monitoring. Document these commitments and track performance.
- Recertification timing. Plan recertification audits well ahead of deadlines. Engage with your certification body early; the BSI recommends completing transition visits a couple of months before the deadline to allow for delays.
4. Audit Process Shifts
- Auditors focus on outcomes. Auditors in 2026 focus on whether controls reduce risk rather than on whether policies exist. They examine metrics such as time to patch, access review frequency and incident detection times.
- Recertification preparation. Conduct internal audits using the 2022 control list and ensure that issues are addressed. Assess the new controls for threat intelligence, cloud security, secure coding and environmental factors.
- Evidence depth. Provide artifacts spanning the observation window (usually 6–12 months). Evidence should include logs, tickets and documented reviews; screenshots alone are insufficient.
Roadmap for Busy Teams
To adapt to ISO 27001 What Changed In 2026, follow a structured plan:
- Perform a gap analysis against the 2022 edition and the 2024 environmental amendment. Identify missing controls, documentation gaps and process weaknesses.
- Update documentation. Revise policies, procedures and the statement of applicability. Include environmental risks and reference the new controls.
- Educate staff. Train internal stakeholders on updated requirements. Include developers (secure coding), operations teams (configuration management) and procurement (supplier oversight).
- Conduct internal audits. Use the 2022 control categories and attributes. Test the effectiveness of controls and evidence collection processes.
- Schedule external audits. Coordinate with certification bodies to conduct transition or recertification audits ahead of the deadline. Ensure resources are available to address findings.
- Integrate continuous monitoring. Implement tools and processes for threat intelligence, configuration management and incident detection. Automate evidence collection where possible.
Konfirmity’s managed service handles these tasks as part of our outcome‑as‑a‑service model. Our team performs gap analyses, updates documents, implements controls and prepares for audits, freeing internal teams to focus on product development.
Common Misconceptions
- Myth: If we were compliant before, we are automatically good now.
Fact: The 2022 revision changed control structure, added new controls and introduced environmental considerations. Certifications based on the 2013 edition expire after October 2025. Organisations must update their ISMS and evidence to remain certified. - Myth: ISO 27001 changes only affect IT.
Fact: The standard requires organisational context, leadership commitment and supplier management. Environmental risks, business continuity and people controls involve executives, procurement and HR. A siloed approach fails audits. - Myth: Certification is purely a checkbox.
Fact: Auditors now scrutinise control effectiveness. Evidence must show that controls operate over time and reduce risk. Buyers also use certifications as a starting point, then ask for detailed assurance artefacts. Compliance without real security exposes organisations to costly breaches.
Conclusion
In 2026, there will be no new ISO 27001 edition. Instead, the 2022 revision, accompanied by the 2024 environmental amendment, defines the current standard. The number of controls decreased from 114 to 93 and was restructured into four categories. New controls address threat intelligence, cloud security, configuration management and other modern risks. A three‑year transition period ended on 31 October 2025, meaning all certifications now refer to the 2022 edition. The 2024 amendment introduces environmental considerations, requiring organisations to assess the impact of extreme weather on information security.
For enterprise teams, the implications are clear: update your ISMS, revise risk assessments, implement the new controls and demonstrate continuous operation. Align ISO 27001 with other frameworks such as SOC 2, HIPAA and GDPR to satisfy varied client requirements. Most importantly, build security programmes that deliver real outcomes. ISO 27001 What Changed In 2026 is less about chasing a new certificate and more about embedding security into daily operations. With expert guidance and managed support, teams can achieve lasting compliance while reducing internal burdens.
FAQs
1. What is the major difference between ISO 27001:2013 and the post‑2025 versions?
The 2022 edition, which applies after 2025, reduces the number of Annex A controls from 114 to 93. Controls are grouped into four categories and 11 new controls cover areas such as threat intelligence, cloud security, configuration management and secure coding. It introduces clause 6.3 for planning changes and emphasises process interactions.
2. Is ISO 27001:2026 an official new version or part of the transition from the 2022 edition?
There is no official ISO 27001:2026 version. ISO 27001:2022 is the latest published standard, with an environmental amendment in 2024. The 2026 context reflects completion of the transition period and enforcement of the 2022 edition.
3. How does the updated standard impact risk management documentation?
The 2022 edition requires organisations to plan changes (clause 6.3) and to decide which interested‑party requirements will be addressed through the ISMS. Annex A is now a list of possible controls, so risk assessments must justify control selection. Documentation should include environmental risk assessments due to the 2024 amendment.
4. Do enterprise clients require updated certificates immediately?
Yes. Certifications against ISO 27001:2013 expired after 31 October 2025. Clients expect certificates reflecting the 2022 edition and evidence that new controls operate effectively. Organisations initiating certification after April 2024 must be assessed against the 2022 edition.
5. How should teams prepare for updated audits and certification criteria?
Conduct a gap analysis against the 2022 edition; update documentation; train staff on new controls; perform internal audits; and schedule transition or recertification audits ahead of deadlines. Include environmental risks and demonstrate continuous monitoring. Managed services like Konfirmity can reduce the workload and ensure that evidence collection meets auditor expectations.
6. How do changes to documented information affect my ISMS?
Documents such as the risk register, statement of applicability and policies must now reference the 93 controls and include environmental considerations. Organisations must record which interested‑party requirements are addressed by the ISMS and plan how process interactions are managed. Evidence must show that controls operate over time and remain effective.





.svg)






.svg)
.svg)