Most enterprise buyers now ask for assurance documents before they sign a purchase order. Without operational security, clear evidence of control effectiveness and contractual clarity around protected health information (PHI), deals stall—even when teams think they’re ready on paper. As a founder who has supported more than 6,000 audits over twenty‑five years in security and compliance, I’ve seen how a well‑designed program accelerates sales and reduces risk. This article lays out a SOC 2 BAA Guide for companies selling to enterprise clients, particularly those handling sensitive data or PHI.
Enterprise buyers increasingly demand proof that vendors have implemented controls consistent with industry standards and have legally binding contracts in place. A 2024 Gartner report from its market intelligence group found that forty‑six percent of software buyers prioritise security certifications and data‑privacy practices when choosing a vendor. In regulated sectors such as healthcare, finance and legal services, procurement teams routinely ask for a SOC 2 report and a Business Associate Agreement before moving forward. Lacking these documents can delay or kill deals.
This article offers a practical SOC 2 BAA Guide: a step‑by‑step framework, examples and templates drawn from real engagements. It is written for CTOs, CISOs, security leaders and compliance officers who need to map internal controls to the trust service criteria, draft enforceable BAAs and maintain continuous evidence of compliance. By the end, you will understand why SOC 2 and BAAs work together, how to implement them effectively and how to manage ongoing vendor and subcontractor risk.
What Is SOC 2 and What Is a Business Associate Agreement?
Understanding SOC 2
SOC 2 is part of the AICPA’s “Service Organization Controls” framework. It focuses on how service providers protect customer data and provides assurance that a vendor follows strong information security, operational and data‑protection controls. A SOC 2 audit evaluates controls against five Trust Services Criteria (TSC)—Security, Availability, Processing Integrity, Confidentiality and Privacy. Security is mandatory, while the other criteria are scoped based on client needs. For example:
- Security: Assures that systems are protected from unauthorised access or misuse. Controls include access management, multi‑factor authentication, encryption and incident response.
- Availability: Verifies that services remain accessible and reliable. Controls involve uptime monitoring, backups and disaster‑recovery procedures.
- Processing Integrity: Ensures accurate and complete data processing. This criterion applies to platforms handling financial transactions or analytics.
- Confidentiality: Addresses protection of sensitive business data, like source code or contracts. It requires encryption, strict access restrictions and clear data‑retention policies.
- Privacy: Covers how personal data (PII) is collected, used and shared and how it maps to regulations like HIPAA, GDPR and CCPA.
SOC 2 compliance is voluntary; there is no law requiring it. However, many enterprise clients expect vendors to provide SOC 2 Type II reports as evidence of mature security practices. Failing to provide this report can stall or derail deals. SOC 2 audits come in two flavours:
- Type I: Assesses whether controls are suitably designed at a specific point in time. It’s a good starting point for early‑stage companies but does not prove that controls operate effectively over time.
- Type II: Evaluates control design and operational effectiveness over an observation period (typically three to twelve months). Most enterprise buyers and investors require this type. In 2024, companies engaged in Type II audits often choose observation periods between three and twelve months, balancing control maturity with market pressure.
Understanding the Business Associate Agreement
A Business Associate Agreement (BAA) is a contract mandated by the Health Insurance Portability and Accountability Act (HIPAA) whenever a covered entity (e.g., a hospital) engages a vendor or subcontractor to handle electronic protected health information (ePHI). The BAA specifies permissible uses and disclosures of ePHI, requires administrative, technical and physical safeguards, mandates breach notification and stipulates that subcontractors must comply with the same terms. Its principal obligations include:
- Permitted uses and disclosures: The contract defines how PHI may be used or disclosed, ensuring it is limited to the services described.
- Safeguards: Vendors must implement administrative, technical and physical controls to protect ePHI. The HIPAA Security Rule sets national standards requiring organisations to ensure the confidentiality, integrity and availability of ePHI.
- Breach notification: The BAA must require timely reporting of any security incident involving ePHI.
- Return or destruction of PHI: At the end of the contract, PHI must be returned or destroyed if feasible.
- Downstream compliance: Any subcontractor handling ePHI must sign a similar BAA.
The BAA is a legal contract. Signing it does not automatically guarantee HIPAA compliance—your organisation still must implement the required safeguards and processes. Fines and settlements in 2024 show the stakes: the HIPAA Journal reported that twenty‑two investigations that year resulted in civil monetary penalties or settlements. Violations often stem from inadequate risk assessments, weak access controls or failure to notify affected parties after breaches.
SOC 2 vs BAA / SOC 2 vs HIPAA
SOC 2 and BAAs serve different purposes. SOC 2 is an attestation report that provides assurance about security practices and controls. A BAA is a legal contract ensuring compliance with HIPAA’s Privacy and Security Rules. There is overlap—SOC 2’s Security and Confidentiality criteria correspond to important HIPAA requirements such as access control, encryption and breach procedures. However, possessing a SOC 2 report does not automatically make an organisation HIPAA compliant. Additional HIPAA controls, like sanction policies, workforce authorisation and device/media handling, may be needed.
One common misconception is that SOC 2 compliance substitutes for HIPAA compliance. In reality, SOC 2 is voluntary and designed for any service organisation, while HIPAA applies specifically to covered entities and business associates that handle PHI. SOC 2 emphasises general information security; HIPAA imposes detailed requirements for privacy and security of ePHI. Vendors handling PHI must sign BAAs and implement HIPAA’s administrative, physical and technical safeguards. This is why combining SOC 2 and BAAs is critical for enterprise‑facing healthcare vendors.
Why “SOC 2 BAA” Matters for Enterprise‑Facing Vendors
Enterprise clients, particularly in regulated sectors, expect both contractual and technical assurance. They need to manage third‑party risk across a growing supply chain. Combining SOC 2 and BAAs offers a dual assurance: legal guarantees of privacy compliance and evidence that your organisation’s controls meet recognised standards. Here’s why this combination matters:
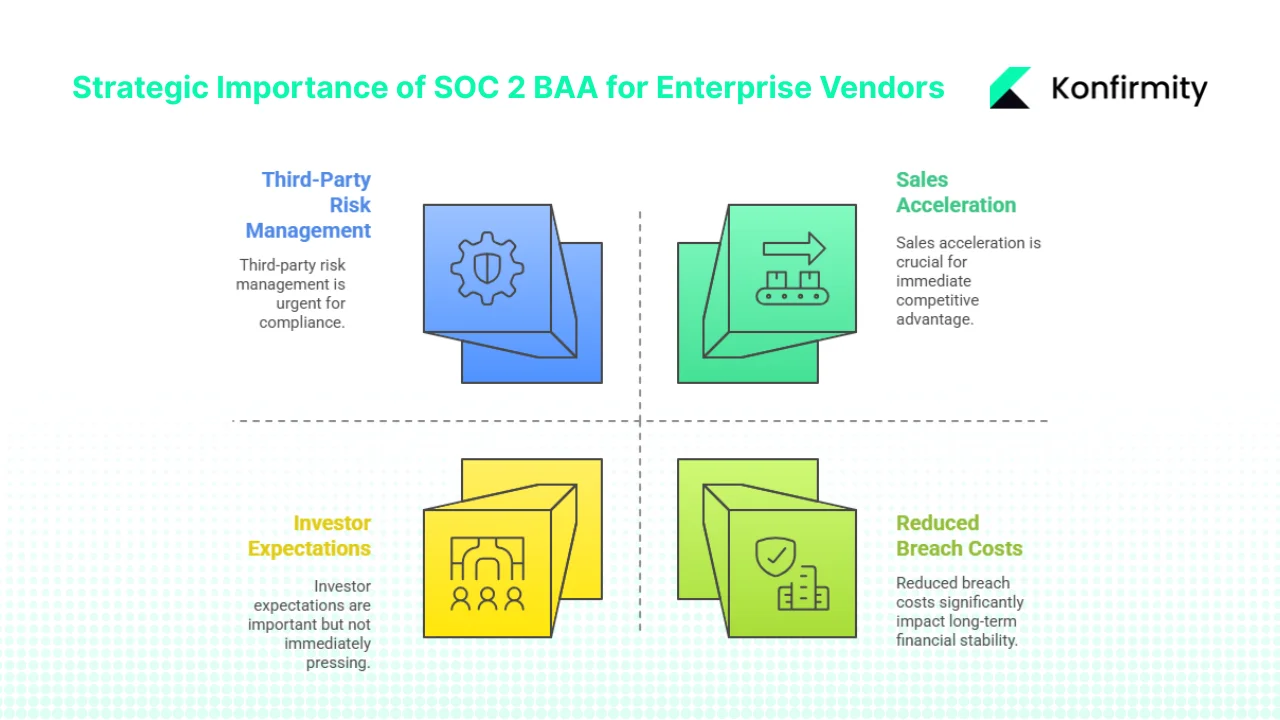
- Third‑party risk management: Clients must assess vendors for security, privacy and operational resilience. SOC 2 Type II reports provide independent attestation of control design and effectiveness, while BAAs ensure compliance with HIPAA’s specific requirements. The combination demonstrates seriousness about information security and data confidentiality.
- Sales acceleration: Without a SOC 2 report and a BAA, procurement teams will likely request extensive questionnaires, risk assessments and additional audits. In 2024, 46 percent of software buyers prioritised security certifications and data‑privacy practices, which means lacking SOC 2 or a BAA could place you behind competitors. When both documents are ready, deals move faster and due diligence friction decreases.
- Reduced breach costs and enforcement risk: Data breaches are expensive. Thomson Reuters reported that the average cost of a data breach in 2024 was $4.88 million, a ten‑percent increase over the previous year. Violations of HIPAA can also lead to regulatory fines; twenty‑two investigations in 2024 resulted in settlements. Having strong controls and legal agreements reduces the likelihood of breaches and demonstrates due diligence if an incident occurs.
- Investor and board expectations: As venture capital and private equity firms take a more risk‑aware approach, they expect portfolio companies to have formal security programs, SOC 2 attestation and appropriate BAAs. This drives readiness not only for sales but for fundraising and exit events.
Step‑by‑Step SOC 2 BAA Guide Implementation
Building a security program that satisfies both SOC 2 and HIPAA obligations requires a systematic approach. Below is a practical step‑by‑step plan with approximate timelines based on our experience supporting more than 6,000 audits. On average, companies working with a managed service like Konfirmity achieve SOC 2 readiness within four to five months, while self‑managed efforts can take nine to twelve months.
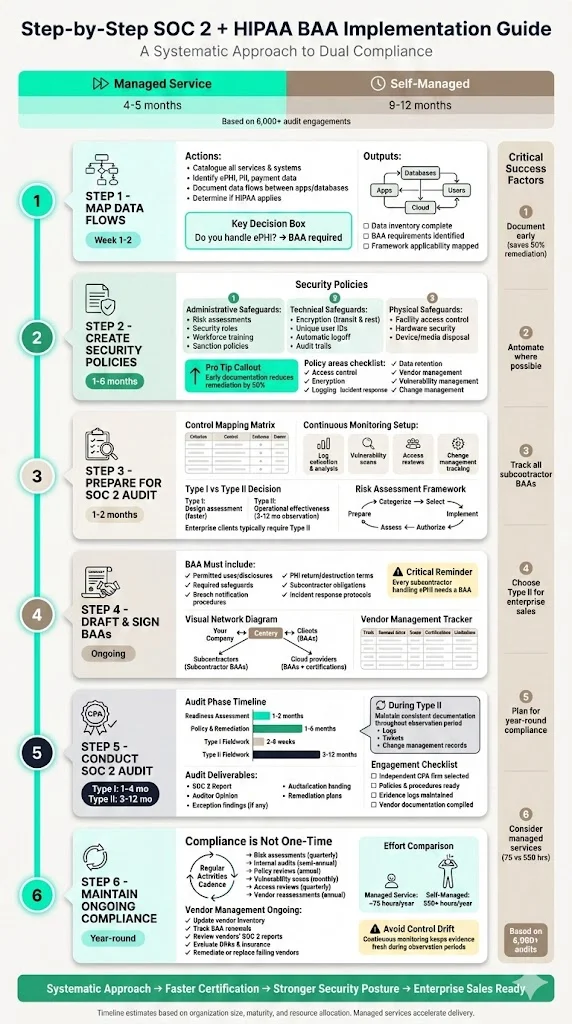
Step 1: Map Data Flows and Identify PHI or Sensitive Client Data
Start by cataloguing all services you provide and the systems where data is stored or processed. Identify whether you handle ePHI, personal data, payment card data or proprietary information. Document data flows between applications, databases and third‑party services. This mapping helps determine whether HIPAA applies and which SOC 2 criteria are relevant.
Next, identify contracts that require a BAA. If you handle ePHI on behalf of a covered entity, you are a business associate and must sign a BAA. For other sensitive data, SOC 2 may be sufficient, though additional frameworks like ISO 27001 or GDPR may apply depending on geography and data types.
Step 2: Create or Review Internal Security Policies and Controls
Develop clear security policies covering access control, encryption (in transit and at rest), logging, incident response, data retention and disposal, vendor management, vulnerability management and change management. These policies should be consistent with the five SOC 2 trust criteria and HIPAA safeguards. The HIPAA Security Rule requires administrative, technical and physical safeguards to ensure the confidentiality, integrity and availability of ePHI. Examples include:
- Administrative safeguards: Conduct risk assessments, assign security roles, establish sanction policies, implement workforce training and enforce workforce authorisation and oversight.
- Technical safeguards: Use encryption for ePHI, implement unique user IDs, enable automatic logoff, and establish audit trails.
- Physical safeguards: Control facility access, secure hardware and manage device/media disposal.
Policies must be enforceable and supported by operational procedures. Use automation where possible (e.g., identity access management, patch management). Ensure policies apply to all subcontractors and vendors. In our experience, companies that document policies early cut remediation efforts by up to fifty percent during the audit phase.
Step 3: Prepare for the SOC 2 Audit – Match Policies to Trust Services Criteria
Once policies are defined, map each one to the SOC 2 trust services criteria. For each criterion, identify the controls you’ve implemented, the evidence you will collect (e.g., logs, access reviews, incident reports) and the owners responsible for operating and monitoring those controls. Maintain a control matrix that lists the criterion, the internal policy/control, evidence to capture and the responsible individual. This matrix becomes the basis for your SOC 2 audit.
Implement continuous monitoring. This includes collecting and analysing logs, conducting regular vulnerability scans, performing access reviews, and monitoring change management. Document risk assessments following recognised frameworks such as NIST’s Risk Management Framework, which includes seven steps: Prepare, Categorise, Select, Implement, Assess, Authorise and Monitor. Regular risk assessments help prioritise remediation, match controls to threats and provide evidence for auditors.
In this preparation phase, consider whether you’ll pursue a Type I or Type II report. For most vendors selling to enterprise clients, a Type II report is necessary. Observation periods typically range from three to twelve months. Shorter periods suit mature organisations seeking quick certification; longer periods provide stronger evidence of control operation and satisfy more conservative clients.
Step 4: Draft and Sign BAAs With Clients and Subcontractors
If you handle ePHI, prepare a BAA that addresses HIPAA requirements. Use a template that includes permitted uses/disclosures of PHI, required safeguards, breach notification procedures, return or destruction of PHI upon termination and subcontractor obligations. Clarify responsibilities around incident response, breach notification and cooperation during audits.
Ensure that a BAA covers every subcontractor who might handle ePHI. If you use a cloud service provider, confirm they have appropriate certifications and are willing to sign a subcontractor BAA. Document these agreements in your vendor management system, tracking renewal dates, scope of services and any limitations. This process forms part of your due diligence and third‑party risk management.
Step 5: Conduct the SOC 2 Audit (Type I or Type II)
Engage an independent CPA firm experienced in SOC 2 audits for technology companies. Provide them with your policies, procedures, risk assessments, evidence logs and vendor documentation. A readiness assessment often precedes the formal audit, identifying gaps and remediation tasks. According to Cherry Bekaert, readiness assessments typically take one to two months, policy and remediation phases last one to six months, Type I fieldwork takes a few weeks to two months and Type II fieldwork spans three to twelve months. Create a timeline that fits your sales goals.
During Type II audits, maintain continuous evidence collection throughout the observation period. Auditors will test whether controls operate effectively, so ensure consistent logging, ticketing and change‑management documentation. After fieldwork, auditors issue the report and an opinion. If deficiencies are identified, document remediation plans and track them through closure. Be transparent with clients about the scope of the report and any exceptions.
Step 6: Maintain Ongoing Compliance and Vendor Management
SOC 2 and HIPAA compliance are not one‑time projects. Once you obtain a Type II report and sign BAAs, you must operate controls year‑round. Establish a cadence of risk assessments, internal audits, policy reviews, vulnerability scans and access reviews. Use automated tools where possible but maintain human oversight.
For vendor management, update your vendor inventory regularly, track BAAs and evaluate vendors’ own security posture. Periodically reassess your subcontractors’ compliance, review their SOC 2 reports, data‑processing agreements (DPAs) and insurance coverage. If a vendor fails to meet standards, develop remediation plans or consider alternatives.
Organisations often underestimate the operational effort of continuous compliance. A managed service can reduce the burden: our clients typically spend about seventy‑five hours per year on evidence collection and meetings, compared with five hundred and fifty hours or more for self‑managed programs. Continuous monitoring ensures that evidence remains fresh, addressing the common challenge of “control drift” during observation periods.
CTA: Book a demo
Examples and Templates for Busy Teams
To streamline implementation, here are overview outlines of the templates and tools we provide to clients. Adapt these to your environment.
Sample BAA Template Outline
- Parties and definitions: Identify the covered entity and business associate, define ePHI and specify the services.
- Permitted uses and disclosures: Specify how PHI may be used or disclosed, including minimum necessary principles.
- Safeguards and compliance: Require the business associate to implement administrative, physical and technical safeguards in line with HIPAA Security Rule.
- Breach notification: Define procedures and timelines for reporting security incidents.
- Subcontractors: Require subcontractors to sign equivalent BAAs and comply with the same obligations.
- Return/destroy PHI: Outline procedures for returning or destroying PHI at contract termination.
- Miscellaneous: Include governing law, liability limits and termination clauses.
Example Control‑Mapping Table
SOC 2 Readiness Timeline/Checklist (12‑Week Plan)
- Weeks 1–2: Map data flows and identify applicable trust criteria. Begin drafting policies.
- Weeks 3–4: Finalise policies; implement core controls (access management, encryption). Start vendor inventory.
- Weeks 5–6: Conduct risk assessment using NIST RMF. Begin continuous logging and vulnerability scanning.
- Weeks 7–8: Create control‑mapping table, prepare evidence collection processes. Draft BAA template.
- Weeks 9–10: Engage auditor for readiness assessment, remediate gaps. Finalise BAAs with clients and subcontractors.
- Weeks 11–12: Start observation period (if pursuing Type II). Collect evidence and prepare for fieldwork.
Risk Assessment Template (Partial)
Vendor Management Spreadsheet Columns
- Vendor name and contact
- Data types handled (ePHI, PII, proprietary)
- BAA status (Signed/Not required/In progress)
- SOC 2 status (Type I/Type II/None)
- Review date and next audit date
- Risk rating and mitigation actions
Common Challenges and How to Address Them
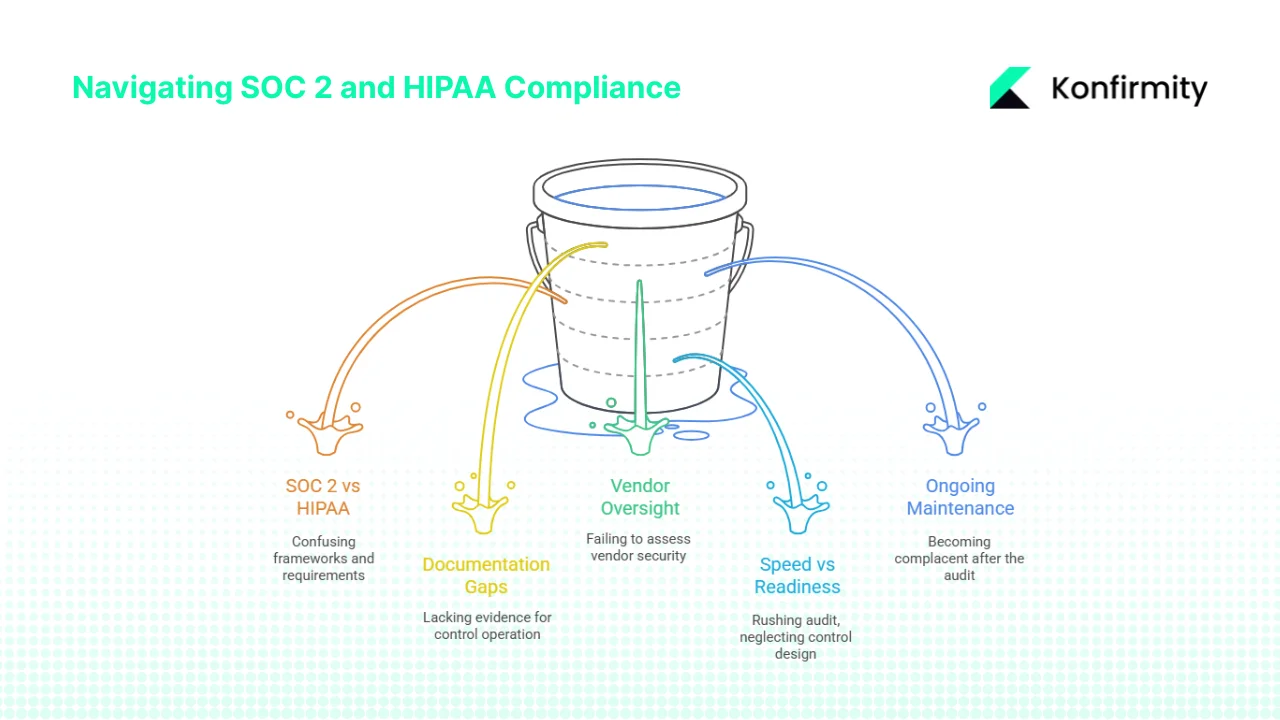
Mistaking SOC 2 for HIPAA compliance: Organisations sometimes believe a SOC 2 report substitutes for HIPAA compliance or a valid BAA. This is incorrect; HIPAA requires specific controls and legal agreements. Ensure you understand the scope of each framework.
Documentation gaps: Small or fast‑growing teams often lack evidence for control operation. Start with simple, enforceable policies and build evidence collection into daily workflows. Use tools for logging, access reviews and ticket tracking. Conduct internal audits to verify documentation before the external auditor arrives.
Subcontractor and vendor oversight: Failing to obtain BAAs from subcontractors or to assess vendors’ security posture can expose you to liability. Maintain a vendor management program with routine reviews, risk assessments and contract management.
Balancing speed and audit readiness: Start‑ups sometimes rush to pass an audit, focusing on document generation rather than control design. Taking a phased approach—starting with a Type I report, then maturing controls before Type II—reduces rework and ensures controls operate effectively. Recognise that SOC 2 Type II requires sustained evidence across many control points, and observation windows can’t be shortcut.
Ongoing maintenance: After the audit, teams may become complacent. SOC 2 and HIPAA compliance require continuous monitoring, regular training, vulnerability management and periodic risk assessments. Build compliance operations into daily life; assign ownership and provide resources to sustain them. Failure to maintain controls may result in findings in subsequent audits or non‑compliance with BAAs.
How SOC 2 + BAA Tie Into Broader Themes
Vendor Management and Third‑Party Risk
Enterprises increasingly manage complex supply chains. Data flows through SaaS providers, infrastructure vendors and subcontractors. SOC 2 Type II reports and signed BAAs provide tangible evidence that vendors are managing risks appropriately. They feed into third‑party risk programs that score vendors, track remediation and inform procurement decisions. Without such evidence, vendors may be excluded from consideration.
Regulatory Compliance and Data Protection
HIPAA is just one of many regulations. GDPR, CCPA and other privacy laws also require contracts and due diligence when processing personal data. SOC 2’s Privacy criterion corresponds to these regulations, emphasising purpose limitation, consent management and secure data handling. Combining SOC 2 and BAAs can simplify cross‑framework compliance: a strong security program addresses common control families, while BAAs cover legal obligations specific to PHI.
Security Compliance and Audit Readiness
SOC 2 and BAAs demonstrate that security is integrated into operations. They provide evidence for due diligence, RFPs and investor evaluations. By implementing controls, collecting evidence and managing vendors continuously, you reduce the risk of expensive breaches and enforcement actions. The average cost of a breach in 2024 reached $4.88 million, so investing in security and compliance up front is cost‑effective.
Risk Assessment and Continuous Monitoring
Using frameworks like NIST’s RMF enables systematic risk assessment and continuous monitoring. These processes are not checkboxes but integral to security posture. When paired with SOC 2 and HIPAA requirements, they create a strong program that addresses evolving threats, regulatory changes and customer demands.
Konfirmity’s Human‑Led Approach
At Konfirmity, we provide an end‑to‑end managed service for security and compliance. We operate as an extension of your team, designing controls within your stack, implementing them and monitoring them year‑round. Rather than handing you software and leaving you to “do the work,” we deliver outcomes. Our clients typically reach SOC 2 readiness in four to five months and cut internal effort by 75 percent compared with self‑managed programs. We triage vulnerabilities using CVSS with automated SLAs, conduct least‑privilege reviews, manage vendor risk workflows and integrate privacy and HIPAA requirements. Our human‑led approach ensures that compliance follows from solid security practices rather than from checklists.
CTA: Book a demo
Conclusion
Combining SOC 2 compliance with a legally sound BAA offers both operational security assurance and contractual clarity. For enterprise‑facing vendors, this combination addresses third‑party risk, accelerates sales, reduces breach costs and matches regulatory expectations. Implementing a SOC 2 program requires careful planning: mapping data flows, creating enforceable policies, matching controls to the trust service criteria, drafting BAAs and maintaining continuous evidence. It is not a quick fix but a long‑term investment in security maturity.
A well‑run compliance program is more than documents. It means designing controls that work in production, monitoring them continuously and adapting to new threats. When security is part of daily operations, compliance becomes a by‑product. As Marc Benioff of Salesforce said, “Trust has to be the highest value in your company—if you lose it, you lose everything”. Build the program once, operate it every day, and view SOC 2 and BAAs as part of core vendor hygiene—not optional extras.
FAQs
1) Is SOC 2 Type II HIPAA compliant?
No. SOC 2 and HIPAA serve different purposes. SOC 2 provides assurance about security practices; HIPAA governs the privacy and security of ePHI. Although there is overlap, SOC 2 does not automatically satisfy HIPAA requirements. Organisations handling ePHI must sign BAAs and implement additional controls outlined in the HIPAA Security Rule.
2) What are the five criteria for SOC 2?
The five trust services criteria are Security, Availability, Processing Integrity, Confidentiality and Privacy. Security is mandatory; the others are scoped based on services and client needs.
3) What is the SOC 2 Type II compliance checklist?
Essential components include mapping data flows, defining policies, implementing controls that satisfy each trust criterion, conducting risk assessments, collecting evidence over an observation period, engaging an independent auditor, and addressing any findings. Observation periods typically range from three to twelve months. Our twelve‑week plan above outlines an overview checklist.
4) What is required to be SOC 2 compliant?
You must design and implement controls that satisfy the relevant trust services criteria, collect evidence of control operation, and undergo an audit by a licensed CPA firm. For Type II, controls must operate effectively over an observation period. Although SOC 2 is voluntary, many enterprise buyers demand it. Maintaining compliance requires ongoing monitoring, risk assessments, policy updates and vendor management.





.svg)






.svg)
.svg)