Most organizations migrating to Azure assume that Microsoft's SOC 2 attestation automatically covers their solution. This creates a fundamental compliance gap—one that becomes apparent when enterprise clients request your SOC 2 report and discover you're relying on inherited controls without implementing your own security infrastructure. The result: stalled procurement cycles, extended security questionnaires, and lost revenue opportunities.
SOC 2 cloud compliance on Azure refers to the process by which a vendor using Azure infrastructure achieves independent attestation that their service meets the American Institute of Certified Public Accountants (AICPA) Trust Services Criteria. While Azure, Dynamics 365, Power Platform, and select Microsoft 365 cloud services undergo rigorous SOC 2 Type 2 audits, your application built on Azure requires separate validation demonstrating that your implemented controls—not just Azure's—effectively protect customer data.
This article provides the structured approach organizations need to achieve SOC 2 compliance on Azure. You'll find step-by-step implementation guidance, control mapping examples, evidence collection templates, and architectural considerations specific to Azure deployments. These are the same frameworks we've used across 6,000+ compliance audits spanning cloud security, identity and access management, data protection, and cloud governance implementations.
Key terminology for this guide:
- Cloud Security: Protective measures securing cloud infrastructure, applications, and data from unauthorized access and threats
- Azure Compliance: Alignment of Azure-based solutions with regulatory frameworks and security standards
- Data Protection: Technical and organizational measures ensuring confidentiality, integrity, and availability of information
- Security Controls: Safeguards implemented to reduce security risks to acceptable levels
- Cloud Governance: Framework of policies, procedures, and controls managing cloud resource use and security
- Identity and Access Management: Systems controlling user authentication, authorization, and access to resources
- Security Monitoring: Continuous observation and analysis of systems to detect security incidents
- Risk Management: Process of identifying, assessing, and mitigating security and compliance risks
- Third-Party Assessment: Independent evaluation by qualified auditors validating control effectiveness
- Audit Readiness: State of preparedness demonstrating controls operate effectively with documented evidence
What is SOC 2 Compliance for the Cloud?
SOC 2 is an attestation framework developed by the AICPA evaluating how service organizations manage customer data based on five Trust Services Criteria: security (mandatory), availability, processing integrity, confidentiality, and privacy. At the conclusion of a SOC 2 audit, the auditor renders an opinion in a SOC 2 Type 2 report, which describes the cloud service provider's (CSP's) system and assesses the fairness of the CSP's description of its controls. It also evaluates whether the CSP's controls are designed appropriately, were in operation on a specified date, and were operating effectively over a specified time period.

When your services operate in the cloud rather than on-premises data centers, the compliance model shifts fundamentally. You no longer control the physical infrastructure, hypervisor layer, or foundational network architecture. Instead, you inherit certain security assurances from your cloud provider while retaining responsibility for everything you build, configure, and deploy within that infrastructure.
The Difference Between Type 1 and Type 2 Reports
Understanding the distinction between SOC 2 Type 1 and Type 2 reports is critical for planning your compliance timeline and setting enterprise client expectations.
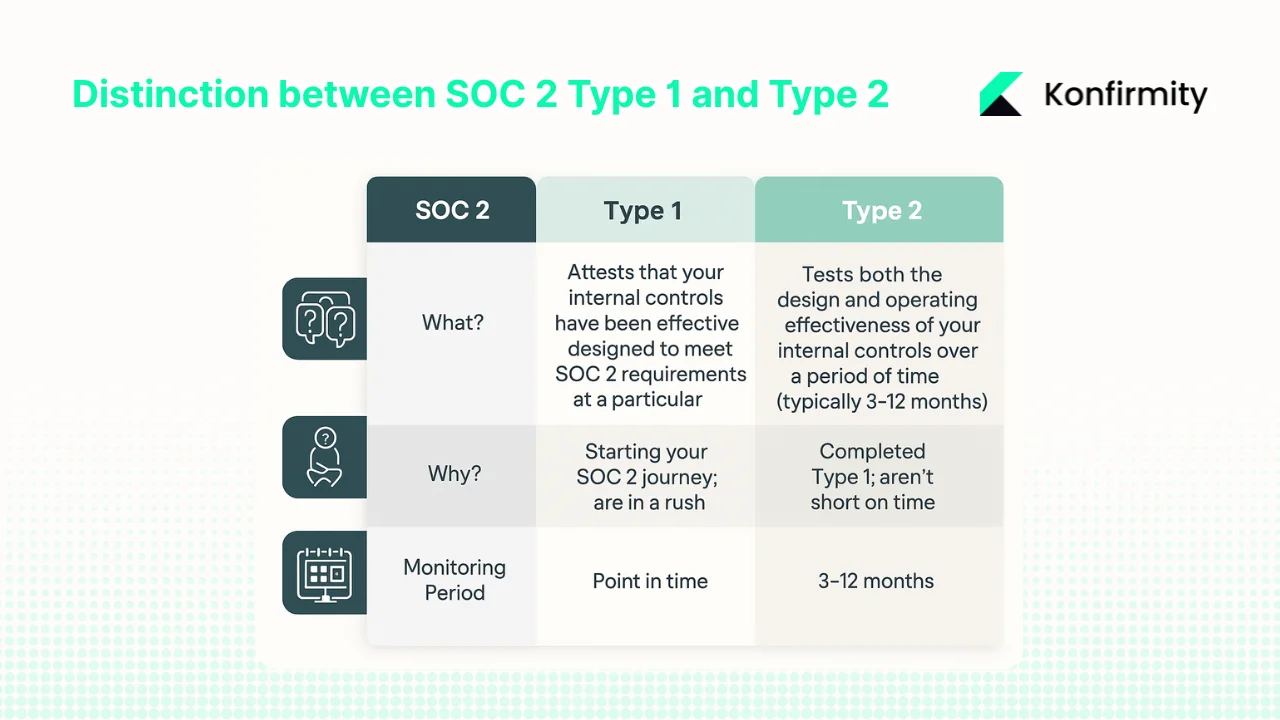
SOC 2 Type 1 evaluates control design at a specific point in time. The auditor assesses whether controls are suitably designed to meet Trust Services Criteria as of a particular date. This provides faster validation—organizations can complete Type 1 audits within 2-4 months of implementing controls. However, Type 1 reports carry limited weight with enterprise procurement teams because they lack evidence of sustained operation.
SOC 2 Type 2 evaluates both control design and operating effectiveness over a defined observation period. For a first-time SOC 2 Type 2 report, it's best practice to consider at least a six-month audit period. A SOC 2 Type 2 report evaluates both the design and operating effectiveness of your controls over a period of time. It answers the question: "Were these controls suitably designed and operated effectively throughout the review period?" The audit window for a SOC 2 Type 2 is between three months to a year, depending on the length you choose.
Type 2 reports require significantly more evidence collection and sustained control operation, but they provide the validation enterprise clients demand. Organizations pursuing enterprise business should plan directly for Type 2 attestation rather than treating Type 1 as a stepping stone.
Why Enterprise Clients Care (and Why Vendors Must Respond)
Enterprise procurement processes increasingly mandate SOC 2 attestation before vendors can access production environments or handle sensitive data. This requirement stems from regulatory obligations, board-level risk management directives, and third-party risk assessment frameworks.
Enterprise buyers evaluate SOC 2 reports to answer specific questions: Does this vendor implement sufficient access controls? Can they detect and respond to security incidents? Do they maintain business continuity capabilities? Will they protect our customer data? Without SOC 2 attestation, you face extended security questionnaires consuming 40-60 hours of internal resources per enterprise prospect—questionnaires that often conclude with "provide SOC 2 report" as the preferred evidence.
Achieving SOC 2 compliance fundamentally changes procurement dynamics. Enterprise security teams can reference your auditor's independent validation rather than conducting duplicate assessments. This accelerates deal cycles by 45-60 days on average and reduces friction in contract negotiations.
How the Cloud Model Changes Risk and Controls
As you consider and evaluate public cloud services, it's critical to understand the shared responsibility model and which security tasks the cloud provider handles and which tasks you handle. The workload responsibilities vary depending on whether the workload is hosted on Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS), or in an on-premises datacenter.
In Azure specifically, Microsoft assumes responsibility for securing the physical data center, hardware infrastructure, hypervisor layer, and core network fabric. For all cloud deployment types, you own your data and identities. You're responsible for protecting the security of your data and identities, on-premises resources, and the cloud components you control.
This division fundamentally impacts SOC 2 compliance strategy. You cannot simply reference Azure's SOC 2 attestation as proof of your compliance. Instead, you must implement complementary controls addressing your responsibilities: identity and access management (Azure AD configuration, role-based access control, multi-factor authentication enforcement), data protection (encryption key management, data classification, access logging), security monitoring (Azure Monitor configuration, Security Center policies, incident response procedures), and cloud governance (Azure Policy enforcement, change management, configuration baselines).
The shared responsibility boundary also varies by service type. IaaS deployments (virtual machines, virtual networks) place more responsibility on you—including OS patching, network security group configuration, and vulnerability management. PaaS services (Azure SQL Database, App Service) shift more responsibility to Microsoft, but you retain configuration security, access management, and data protection obligations.
Why Azure? Azure's SOC 2 Offerings and What They Mean for You
Microsoft Azure, Dynamics 365, and other Microsoft cloud services undergo rigorous independent third-party SOC 2 Type 2 audits conducted by a reputable certified public accountant (CPA) firm. SOC reports for Azure, Dynamics 365, and other online services are based on a rolling 12-month run window (audit period) with new reports issued semi-annually (period ends are 31-Mar and 30-Sep). Bridge letters are issued during the first week of each quarter to cover the prior three-month period.
Azure SOC 2 Type 2 reports are relevant to trust services criteria for system security, availability, processing integrity, and confidentiality. Note that not all Azure services include privacy criteria—this becomes relevant when defining your own scope.
Microsoft publishes these reports through the Service Trust Portal, accessible to organizations with Azure subscriptions. You can access Azure SOC audit reports and bridge letters from the Service Trust Portal (STP) SOC reports section. These documents remain confidential and cannot be redistributed—a constraint that frustrates vendors hoping to simply forward Azure's attestation to prospects.

What It Implies for Your Solution Built on Azure
Azure's SOC 2 attestation provides foundational assurance that the underlying infrastructure meets rigorous security standards. You can rely on this attestation when documenting your control environment and responding to audit inquiries about infrastructure security. Your SOC 2 report will reference Azure as a subservice organization, acknowledging that certain controls operate at Microsoft rather than within your direct management.
However, Azure's compliance does not eliminate your obligations. Your auditor will evaluate controls you implement and manage: application security, access management, data handling procedures, change management, monitoring and alerting configuration, incident response processes, and vendor risk management. These controls exist entirely within your responsibility boundary regardless of Azure's attestation status.
The in-scope services list within Azure's SOC 2 report becomes critical during your audit. If you utilize Azure services not included in Microsoft's attestation scope, you cannot claim inherited controls for those services. This requires additional control documentation and potentially alternative attestations or assessments.
Azure-Specific Controls & Tools Mapped to SOC 2
Azure provides purpose-built tooling to support SOC 2 compliance efforts, reducing the implementation burden for organizations building on the platform.
The Azure Policy Regulatory Compliance built-in initiative definition maps to compliance domains and controls in System and Organization Controls (SOC) 2. Many of the controls are implemented with an Azure Policy initiative definition. Find and select the SOC 2 Type 2 Regulatory Compliance built-in initiative definition within the Azure Portal Policy definitions page to review the complete control mapping.
Critical context: Each control below is associated with one or more Azure Policy definitions. These policies may help you assess compliance with the control; however, there often is not a one-to-one or complete match between a control and one or more policies. As such, Compliant in Azure Policy refers only to the policy definitions themselves; this doesn't ensure you're fully compliant with all requirements of a control.
This distinction matters. Azure Policy provides automated assessment of infrastructure configuration against SOC 2-mapped controls, but policy compliance alone doesn't satisfy audit requirements. You still need documented procedures, evidence of control operation, and organizational policies supporting technical controls.
Step-by-Step Guide: Achieving SOC 2 Cloud Compliance On Azure
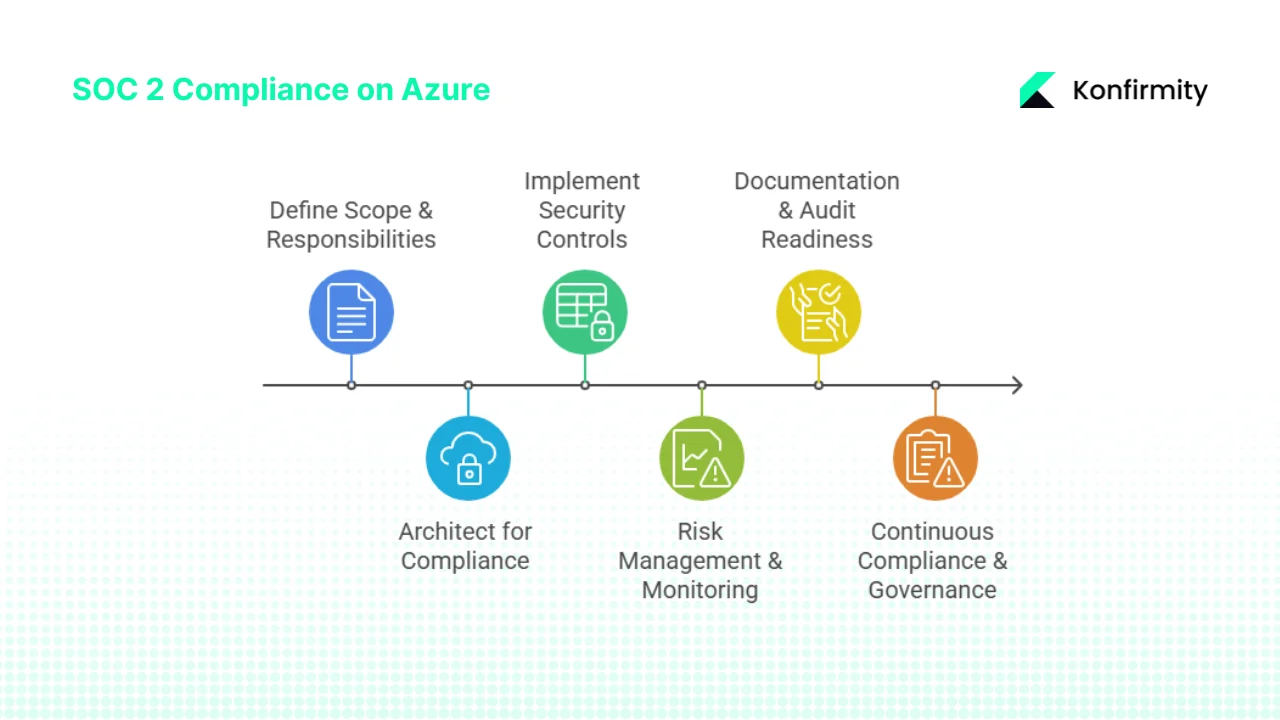
Step 1: Define Scope & Responsibilities
Begin by documenting precisely which systems, applications, and data flows fall within your SOC 2 scope. This includes Azure resources (specific subscriptions, resource groups, services), supporting systems (identity providers, monitoring platforms, third-party integrations), data types and locations, and personnel with access to in-scope systems.
Define which Trust Services Criteria you'll address. Security is mandatory. Availability, processing integrity, confidentiality, and privacy are optional but frequently required by enterprise clients. Review your customer contracts and security questionnaire responses to determine client expectations—implementing criteria now that you'll need in six months avoids scope expansion mid-audit.
Map the shared responsibility model to your specific architecture. Create a responsibility matrix documenting: Azure-managed controls (physical security, hardware lifecycle, network infrastructure), shared controls (network security configuration, encryption implementation, monitoring and logging), and customer-managed controls (access management, application security, data classification, incident response).
Scope Document Template Structure:
- In-scope Azure subscriptions and resource groups
- Architectural diagram showing data flows and trust boundaries
- Trust Services Criteria included in scope with business justification
- Shared responsibility matrix specific to your Azure services
- Exclusions with rationale (development environments, deprecated services)
- Key personnel and their roles in compliance program
Step 2: Architect for Compliance
SOC 2 compliance begins with sound cloud architecture. Poorly designed Azure deployments create control gaps that cannot be remediated through documentation alone.
Cloud Architecture Review: Map complete data flows from customer interaction through storage and processing. Identify where sensitive data resides—Azure SQL databases, storage accounts, Key Vaults, log repositories. Implement network segmentation using virtual networks, subnets, and network security groups. Deploy Azure Firewall or network virtual appliances for centralized traffic inspection. Design for defense in depth rather than perimeter-only security.
Identity & Access Management: Azure Active Directory serves as the foundation for identity controls. Implement role-based access control (RBAC) with least-privilege principles—avoid broad Owner or Contributor assignments. Enforce multi-factor authentication across all accounts, particularly those with administrative access. Deploy Conditional Access policies restricting access based on location, device compliance, and risk level. Utilize Privileged Identity Management (PIM) for just-in-time administrative access with approval workflows and time-bound elevation.
Data Protection: Configure encryption at rest for all storage services—Azure Storage Service Encryption, Azure Disk Encryption, Transparent Data Encryption for databases. Enforce TLS 1.2 or higher for all data in transit. Deploy Azure Key Vault for centralized key management with hardware security module (HSM) backing for production keys. Implement key rotation policies and maintain audit logs of key access. Configure data classification and apply protection policies based on sensitivity levels.
Governance Model: Establish Azure Policy assignments enforcing security baselines—required tags, allowed resource types, geographic restrictions, encryption requirements. Implement change management procedures covering infrastructure modifications, application deployments, and policy updates. Deploy configuration management ensuring consistent security settings across resources. Utilize Azure Blueprints for repeatable environment deployment with compliance guardrails.
Step 3: Implement Required Security Controls
Map your controls to SOC 2 Trust Services Criteria systematically. For each criterion, identify applicable control objectives and document specific control activities addressing those objectives.
Security Criteria Controls:
- Logical and physical access controls (Azure AD, RBAC, PIM, MFA)
- System operations (change management, capacity management, monitoring)
- Change management (Azure DevOps, approval workflows, rollback procedures)
- Risk mitigation (vulnerability scanning, patch management, threat detection)
Availability Criteria Controls:
- Performance monitoring (Azure Monitor, Application Insights, Log Analytics)
- Backup operations (Azure Backup, geo-redundant storage)
- Disaster recovery (Azure Site Recovery, failover procedures, tested recovery)
- Incident management (Azure Service Health, alerting, escalation procedures)
Processing Integrity Criteria Controls:
- Data validation (input validation, output verification)
- Processing authorization (workflow approvals, segregation of duties)
- Error handling (exception logging, automated alerting, remediation tracking)
Confidentiality Criteria Controls:
- Encryption (Key Vault, encryption at rest and in transit)
- Data disposal (secure deletion procedures, retention policies)
- Access restrictions (network security groups, private endpoints, data classification)
Implementation Checklist:
- ✅ Azure AD configured with MFA enforced for all users
- ✅ RBAC assignments follow least-privilege model with quarterly reviews
- ✅ PIM configured for administrative roles with approval workflows
- ✅ Network security groups restrict traffic to required ports and sources
- ✅ Azure Policy initiative assigned with SOC 2 control mappings
- ✅ Encryption enabled for all storage accounts and databases
- ✅ Key Vault deployed with access policies and audit logging
- ✅ Azure Security Center enabled with continuous assessment
- ✅ Azure Monitor configured with alert rules for security events
- ✅ Backup policies configured with tested recovery procedures
- ✅ Change management procedures documented with approval evidence
- ✅ Vulnerability scanning implemented with remediation SLAs
Step 4: Risk Management & Monitoring
Identify risks specific to your Azure environment: unauthorized access through compromised credentials, data exfiltration via misconfigured storage accounts, availability disruptions from resource exhaustion, configuration drift from unauthorized changes, and dependency failures in third-party services.
Establish detection and response capabilities using Azure-native tooling. Deploy Azure Security Center (now Microsoft Defender for Cloud) for continuous security assessment and threat protection. Configure Azure Sentinel for security information and event management (SIEM) if you require advanced threat detection and investigation. Implement Azure Monitor with Log Analytics workspaces collecting logs from all in-scope resources—activity logs, diagnostic logs, Azure AD sign-in logs, and security alerts.
Define alerting thresholds triggering security team notifications: failed authentication attempts exceeding baseline, privileged role assignments, network security group rule modifications, Key Vault access from unexpected locations, and compliance policy violations detected by Azure Policy.
Document your incident response plan covering: detection and triage procedures, escalation paths with contact information, containment and remediation steps, communication protocols, and post-incident review requirements. Test this plan through tabletop exercises at minimum annually.
Risk Management Template Elements:
- Risk register identifying threats, likelihood, and impact
- Control mapping showing which controls mitigate each risk
- Monitoring dashboard displaying control health metrics
- Incident response playbook with step-by-step procedures
- Escalation matrix with role-based notification paths
Step 5: Documentation & Audit Readiness
SOC 2 audits fundamentally evaluate documented evidence proving controls operated effectively throughout the observation period. Inadequate documentation represents the most common audit deficiency we observe—organizations implement strong technical controls but fail to maintain evidence of their operation.
Maintain systematic evidence collection: policies and procedures describing control activities, access reviews showing quarterly validation of user permissions, change logs documenting infrastructure modifications with approval records, security scan results with remediation tracking, training completion records, incident response documentation showing detection and resolution, and monitoring logs proving continuous operation.
Azure provides compliance reports and bridge letters supporting your audit. Reference Azure's SOC 2 Type 2 attestation in your system description. Include Azure in your subservice organization listing with appropriate carved-out control language indicating which security aspects Azure manages versus your organization.
Audit Readiness Checklist:
- ✅ System description documenting architecture and control environment
- ✅ Policies and procedures covering all Trust Services Criteria in scope
- ✅ Evidence repository organized by control and observation period date
- ✅ Azure SOC 2 reports downloaded from Service Trust Portal
- ✅ Vendor risk assessments completed for third-party service providers
- ✅ Access review evidence covering entire observation period
- ✅ Change log with approval documentation for all production changes
- ✅ Security scan results with risk ratings and remediation status
- ✅ Training records showing security awareness completion
- ✅ Incident log documenting detection, response, and resolution
- ✅ Backup and recovery test results proving availability controls
Evidence Tracker Template:
- Control ID and description
- Evidence type (screenshot, log export, policy document, approval email)
- Collection frequency (daily, weekly, monthly, quarterly, annually)
- Responsible party
- Storage location
- Observation period coverage dates
- Auditor sample dates (populated during audit)
Step 6: Continuous Compliance and Governance
SOC 2 compliance is not a project with a defined end date—it requires sustained operation of controls with continuous monitoring and periodic reassessment.
Cloud environments evolve constantly: new Azure services deployed, application updates introducing architectural changes, personnel joining and departing requiring access modifications, and regulatory requirements shifting based on jurisdiction or industry standards. Each change potentially impacts your control environment and requires governance oversight.
Implement Azure Policy for automated compliance monitoring. Assign the SOC 2 Type 2 Regulatory Compliance initiative and review compliance dashboards weekly. Configure remediation tasks for policy violations, either automated or manual based on risk level. Establish change advisory boards reviewing significant modifications before production deployment.
Conduct periodic control assessments validating continued effectiveness. Quarterly access reviews ensure privilege assignments remain appropriate. Annual policy reviews update procedures reflecting operational changes. Monthly vulnerability scans identify emerging risks requiring remediation.
Plan for your next SOC 2 audit immediately after completing the current one. SOC reports for Azure, Dynamics 365, and other online services are based on a rolling 12-month run window (audit period) with new reports issued semi-annually—your observation period for the subsequent audit should commence the day after your previous period ends, maintaining continuous attestation.
Governance Review Schedule:
- Weekly: Azure Policy compliance dashboard review, security alert triage
- Monthly: Vulnerability scan results review, access anomaly investigation
- Quarterly: Access rights certification, policy and procedure updates
- Annually: Comprehensive risk assessment, disaster recovery testing, third-party auditor engagement
Concrete Examples & Use Cases
Example Architecture Diagram
A representative Azure deployment for a SaaS vendor achieving SOC 2 compliance includes:
User Access Layer:
- Azure Front Door with WAF protecting public endpoints
- Azure AD B2C or B2B for customer identity management
- Conditional Access policies enforcing MFA and device compliance
Application Layer:
- Azure App Service hosting application code in isolated network
- Private endpoints eliminating public internet exposure
- Managed identity authentication to Azure resources
- Application Insights monitoring performance and errors
Data Layer:
- Azure SQL Database with Transparent Data Encryption enabled
- Geo-redundant storage ensuring availability
- Azure Key Vault storing connection strings and encryption keys
- Azure Storage with encryption at rest and network restrictions
Security & Monitoring Layer:
- Azure Security Center providing threat protection
- Azure Monitor with Log Analytics collecting centralized logs
- Azure Sentinel for advanced threat detection (optional)
- Network security groups restricting traffic between tiers
Management & Governance Layer:
- Azure Policy enforcing SOC 2 control mappings
- Azure Blueprints deploying consistent environments
- Azure DevOps managing infrastructure as code deployments
- Azure Backup protecting critical resources with tested recovery
Example Control Mapping Table
Example Templates for Busy Teams
Scope Definition Template: Document in-scope systems (Azure subscriptions, resource groups, services), data types handled (customer data, financial data, authentication credentials), Trust Services Criteria included (security, availability, confidentiality), personnel with system access (development, operations, security teams), and boundary definition (what's excluded and why).
Control Implementation Checklist: Organized by Trust Services Criteria with specific Azure services implementing each control, configuration requirements, responsible teams, target completion dates, and validation methods.
Audit Evidence Tracker: List each control with required evidence type, collection frequency, storage location, responsible party, and audit period coverage. Pre-populate sample requirements based on control frequency.
Incident Response Playbook Template: Define detection mechanisms (Azure alerts, Security Center recommendations), initial triage procedures (severity classification, stakeholder notification), containment actions (isolate affected resources, revoke compromised credentials), investigation steps (log analysis, root cause identification), remediation activities (apply patches, update configurations), and communication protocols (customer notification thresholds, regulatory reporting requirements).
Governance Review Schedule Template: Create recurring calendar entries for weekly policy compliance reviews, monthly access anomaly investigations, quarterly access certifications, and annual comprehensive assessments. Assign ownership and define deliverables for each review cycle.
Real-Life Vendor Scenario
Acme SaaS provides financial analytics software to mid-market and enterprise customers. Their application runs entirely on Azure using App Service, Azure SQL Database, and Azure Storage. When a Fortune 500 prospect required SOC 2 Type 2 attestation before signing a $500,000 annual contract, Acme initiated their compliance program.
Scope Definition (Month 1): Acme defined scope covering their production Azure subscription, excluding development and testing environments. They selected Security, Availability, and Confidentiality criteria based on customer contracts. They mapped shared responsibility: Azure managed physical security and infrastructure, Acme managed application security, access controls, and data protection.
Architecture Review (Month 2): The security team identified control gaps: overly permissive RBAC assignments, absent MFA enforcement, public endpoints exposing databases, and unencrypted storage accounts. They remediated these issues: implemented Azure AD Conditional Access requiring MFA, configured private endpoints for databases, enabled storage encryption, and refined RBAC using PIM for administrative access.
Control Implementation (Months 3-4): Acme deployed Azure Policy with SOC 2 mappings, configured Security Center with threat protection, implemented Log Analytics collecting centralized logs, established change management procedures with approval workflows, documented incident response plans, and configured automated backups with tested recovery.
Observation Period (Months 5-10): The 6-month observation period commenced once controls operated consistently. Acme maintained evidence: quarterly access reviews, change logs with approvals, security scan results with remediation tracking, monitoring dashboards proving continuous operation, and incident response documentation.
Audit & Report (Months 11-12): The auditor tested control design and operating effectiveness through evidence sampling across the observation period. Acme received their SOC 2 Type 2 report with no exceptions. The Fortune 500 prospect accelerated procurement upon receiving the report, and three additional enterprise deals closed within 90 days referencing the attestation.
Key Lessons Learned: Documenting shared responsibility prevented scope confusion. Aligning IAM strategy early avoided mid-observation remediation. Automated evidence collection through Azure Monitor reduced manual effort. Starting with a 6-month observation period balanced speed with credibility.
Common Pitfalls & How to Avoid Them
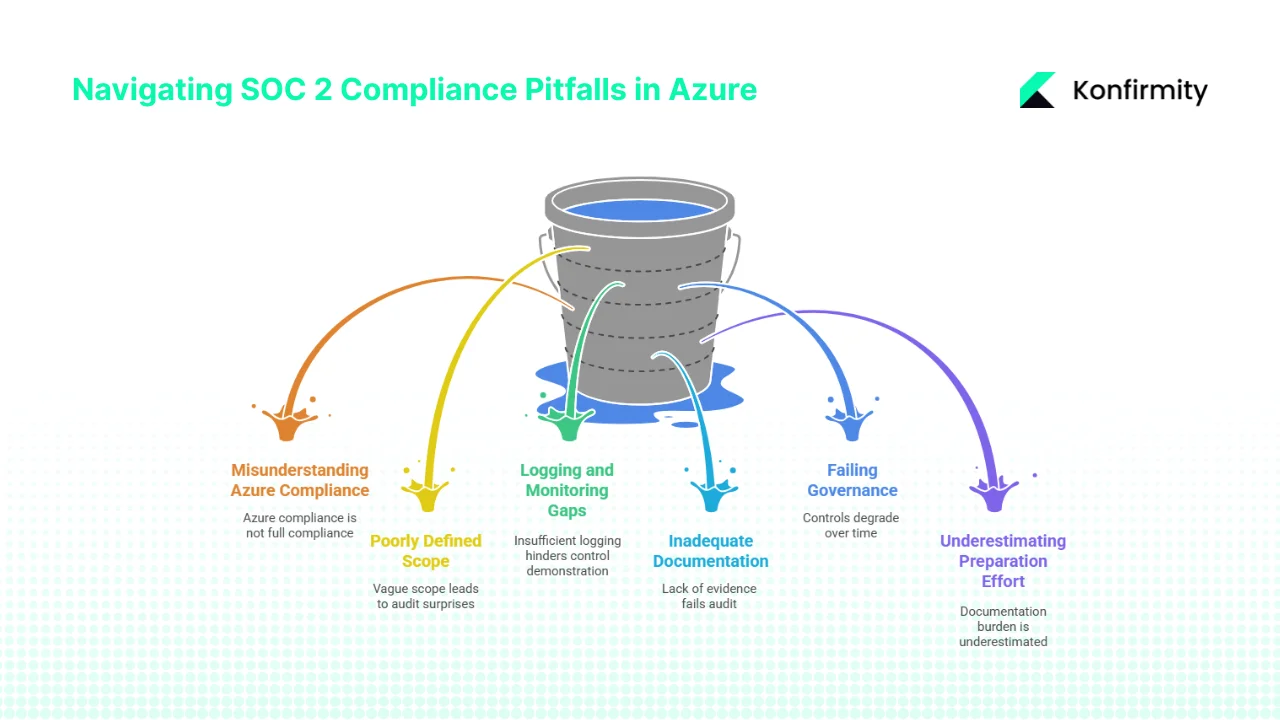
1) Mistaking "Azure is SOC 2 Compliant" for "My Service is SOC 2 Compliant": Azure's attestation covers Microsoft-managed infrastructure controls. It does not validate controls you implement and manage within your application. Your SOC 2 report must address your complete control environment, not just inherited Azure controls. Document the shared responsibility boundary explicitly and implement complementary controls for your responsibilities.
2) Poorly Defined Scope Leading to Audit Surprises: Vague scope definitions result in auditor questioning about excluded systems or unexpected control requirements. Define scope precisely: specific Azure subscriptions, resource groups, and services. Document exclusions with clear rationale. Review scope with your auditor during planning to ensure alignment before the observation period begins.
3) Logging and Monitoring Gaps: Many organizations enable basic logging without centralized collection or retention policies. SOC 2 audits require evidence throughout the observation period—if logs expired before the auditor requests samples, you cannot demonstrate control operation. Configure Log Analytics with minimum 12-month retention. Enable diagnostic logging for all in-scope resources. Test log queries before the observation period to ensure data availability.
4) Not Documenting Controls or Evidence Properly: Technical controls implemented perfectly fail audit if you cannot provide documented evidence. Maintain systematic evidence collection from day one of the observation period. Organize evidence by control and date. Document procedures describing how controls operate. Avoid relying on tribal knowledge—new team members should understand control operation from documentation alone.
5) Failing to Define Ongoing Governance and Drift Controls: Achieving initial compliance means little if controls degrade over subsequent months. Azure environments change constantly through deployments, updates, and scaling. Implement Azure Policy to detect and remediate drift automatically. Establish change advisory boards reviewing significant modifications. Conduct quarterly control assessments validating continued effectiveness. Plan for continuous monitoring rather than point-in-time compliance.
6) Underestimating the Audit Preparation Effort for Enterprise Clients: Organizations new to SOC 2 consistently underestimate the documentation burden and evidence collection requirements. Budget 4-6 months minimum from control implementation to observation period completion for first-time Type 2 audits. Allocate dedicated resources—attempting SOC 2 preparation as secondary responsibility for already-overloaded engineering teams creates delays and incomplete evidence. Consider engaging compliance automation platforms or consultants with Azure expertise to accelerate readiness.
How This Helps Companies Selling to Enterprise Clients
Enterprise procurement processes evaluate third-party risk systematically before granting vendor access to production environments or sensitive data. Security teams assess vendor controls through standardized frameworks—SOC 2 attestation directly addresses these requirements, reducing duplicative security assessments and accelerating procurement cycles.
Presenting SOC 2 Type 2 reports demonstrates operational maturity enterprise buyers demand. Rather than completing 60-question security questionnaires repeatedly, you provide independent auditor validation covering security, availability, processing integrity, confidentiality, and privacy controls. This differentiation matters when competing against vendors lacking attestation—enterprise buyers default to compliant vendors rather than accepting assessment burden for non-compliant alternatives.
The templates, examples, and step-by-step guidance in this article enable your team to implement SOC 2 controls systematically rather than reactively responding to customer demands. You can reuse scope definitions across audits, accelerate evidence collection through structured templates, reduce auditor questions through comprehensive documentation, and maintain continuous compliance supporting annual attestation cycles.
Building compliance infrastructure on Azure provides foundational advantages: inherited controls from Microsoft's attestation reduce implementation burden, built-in tooling (Policy, Security Center, Monitor) automates compliance assessment, centralized logging simplifies evidence collection, and programmatic configuration through infrastructure as code ensures consistent control deployment.
Organizations achieving SOC 2 compliance on Azure report 45-60 day reductions in enterprise procurement cycles, 75% decreases in security questionnaire volume, higher win rates against non-compliant competitors, and improved security posture benefiting all customers regardless of compliance requirements.
Conclusion
SOC 2 cloud compliance on Azure is achievable through systematic implementation: define scope and shared responsibility boundaries, architect with security controls embedded in infrastructure design, implement required controls mapped to Trust Services Criteria, establish risk management and continuous monitoring, document control operation with comprehensive evidence, and govern changes ensuring sustained compliance.
Microsoft Azure, Dynamics 365, and other Microsoft cloud services undergo rigorous independent third-party SOC 2 Type 2 audits conducted by a reputable certified public accountant (CPA) firm. Azure SOC 2 Type 2 reports are relevant to trust services criteria for system security, availability, processing integrity, and confidentiality. Leveraging Azure's built-in attestation, Policy initiatives, Security Center capabilities, and monitoring tools provides a strong compliance foundation—but only when combined with controls you implement addressing your shared responsibility obligations.
Take action immediately: select one template from this guide, assign an owner from your security or engineering team, and establish a schedule. Begin with scope definition documenting your Azure architecture and responsibility boundaries. This foundation enables subsequent control implementation, evidence collection, and audit readiness activities.
Organizations selling to enterprise clients cannot afford compliance delays. SOC 2 attestation directly impacts revenue by accelerating procurement, reducing sales cycle friction, and providing competitive differentiation. The structured approach outlined here—refined across 6,000+ audits—enables you to achieve Type 2 attestation within 6-9 months while building sustainable compliance infrastructure supporting ongoing attestation cycles.
FAQ
1) Is Azure SOC 2 compliant?
Yes. Microsoft Azure, Dynamics 365, and other Microsoft cloud services undergo rigorous independent third-party SOC 2 Type 2 audits conducted by a reputable certified public accountant (CPA) firm. SOC reports for Azure, Dynamics 365, and other online services are based on a rolling 12-month run window (audit period) with new reports issued semi-annually (period ends are 31-Mar and 30-Sep). However, Azure's compliance does not automatically make your application compliant—you must implement controls addressing your responsibilities under the shared responsibility model.
2) What is SOC 2 compliance for the cloud?
SOC 2 compliance for cloud-based organizations refers to the process of implementing and validating controls that meet AICPA Trust Services Criteria (security, availability, processing integrity, confidentiality, privacy) within cloud infrastructure. It requires understanding the shared responsibility model—distinguishing between controls the cloud provider manages and controls you must implement—and demonstrating through independent audit that your implemented controls operate effectively over a sustained period.
3) Does Microsoft have a SOC report?
Yes. Microsoft publishes SOC 2 Type 2 reports for Azure and other cloud services. You can access Azure SOC audit reports and bridge letters from the Service Trust Portal (STP) SOC reports section. Bridge letters are issued during the first week of each quarter to cover the prior three-month period. These reports remain confidential and require an Azure subscription to access—they cannot be publicly shared or redistributed.
4) What is required for SOC 2 compliance?
SOC 2 compliance requires: defined scope identifying in-scope systems and Trust Services Criteria, documented controls addressing applicable criteria, implemented security and governance practices (access management, encryption, monitoring, incident response, change management), evidence of control operation throughout the observation period, continuous monitoring detecting control failures or drift, audit readiness with organized evidence and documentation, and independent assessment by a qualified CPA firm. In cloud environments, you must additionally understand and document shared responsibility—clearly distinguishing between cloud provider controls and controls you implement and manage.





.svg)






.svg)
.svg)