Most enterprise buyers now want assurance that their suppliers guard data and operate with sound security. IBM’s Cost of a Data Breach report estimated that the global average cost of a data breach reached $4.88 million in 2024 and only fell to $4.44 million in 2025. Another analysis found that more than 82% of breaches involve cloud data and that breaches spanning several environments cost about $4.75 million. Those numbers make clear why prospects demand proof of strong controls before signing a contract. For companies that sell into enterprises, SOC 2 Cloud Compliance On GCP is now a business enabler rather than a compliance checkbox.
This guide explains what SOC 2 requires, how cloud hosting changes the game, how Google Cloud Platform (GCP) supports compliance, and how to build a program that stands up to auditors and buyers. The insights draw on the AICPA trust services criteria, recent research, and Konfirmity’s experience supporting more than 6,000 audits over the past 25 years.
What is SOC 2?
The American Institute of Certified Public Accountants (AICPA) created SOC 2 so service organizations can show that they protect information and maintain reliable operations. SOC 2 exams assess controls aligned to five trust services criteria: security, availability, processing integrity, confidentiality, and privacy. These criteria cover whether your system prevents unauthorized access, stays up and running, produces accurate results, restricts data disclosure, and handles personal data according to commitments.

SOC 2 is an attestation—an independent auditor expresses an opinion on your controls rather than issuing a certification. Reports come in two forms:
- A Type I report examines the design of controls at a point in time.
- A Type II report evaluates both the design and operational effectiveness over a period (usually six to twelve months).
Because Type II proves that controls work in practice, enterprise buyers often insist on it. Google Cloud only issues Type II reports for its core services, so vendors must plan for an observation window and continuous evidence.
Why do cloud platforms change the compliance game?
Building on cloud services introduces new security opportunities and risks. On‑premises infrastructure offers physical access and full control. With cloud platforms, providers take care of facilities, hardware, and the hypervisor, but customers remain responsible for the configuration and operation of their own projects. Several factors stand out:
- Shared responsibility. Google secures the infrastructure of the cloud while you secure applications, data, and configurations within it. Enterprise clients expect you to map which controls are provided by GCP and which are your responsibility.
- Automated monitoring. Breaches often spread quickly. Research cited by UpGuard notes that adversaries can move laterally within 84 seconds in cloud environments. Continuous logging and alerting are crucial to detect suspicious activity.
- Dynamic infrastructure. Developers can spin up instances, databases, and services on demand. Without disciplined governance, identities proliferate and privileges accumulate. Policies and change management need to cover how services are provisioned, reviewed, and retired.
- Encryption and cryptographic management. GCP encrypts data at rest and in transit by default, but clients may need to control cryptographic material through Cloud KMS or hardware modules. Enterprise buyers will ask whether sensitive information is covered by customer‑managed encryption and whether you rotate secrets.
Because the cloud changes technical and procedural control requirements, your program must show how it addresses these specifics. When presenting SOC 2 Cloud Compliance On GCP evidence to potential buyers, clearly distinguish what GCP handles and what you handle.
Unforced errors are another issue. Public cloud storage buckets left open or misconfigured privileges in serverless functions have led to high‑profile data exposures. The 2025 IBM report noted that systems misconfiguration was among the leading breach causes, with average detection taking over 200 days. To achieve SOC 2 Cloud Compliance On GCP, teams must document how they prevent such lapses, whether through automated configuration scanning, policy‑as‑code, or regular reviews. A disciplined approach reduces risk and demonstrates to auditors that you understand the nuances of operating in a multi‑tenant environment.
How GCP supports SOC 2
Google Cloud undergoes independent SOC 2 Type II audits for many of its services. Ernst & Young and Coalfire produce reports covering periods from May 1 to April 30 and from November 1 to October 31. These reports are available through the Compliance Reports Manager. Separate annual reports cover additional services such as AppSheet, Looker, VMware Engine, and Mandiant. Between reporting cycles, Google issues bridge letters—short statements extending assurance to interim months. While these reports give assurance about the underlying platform, they don’t make your product compliant; you must still implement controls specific to your environment.
Auditors expect you to provide Google’s report and bridge letters as evidence. These documents confirm there were no material changes during the interim periods and are essential for SOC 2 Cloud Compliance On GCP.
Native services for control implementation
GCP includes several security services that map directly to SOC 2 criteria, allowing you to meet many requirements without building from scratch. Auditors at Linford & Company estimate that customers who use these services can address up to 30% of control requirements before layering their own controls. Important services include:
- Identity and Access Management (IAM). Cloud IAM provides granular permissions for users and service accounts and supports custom roles with multi‑factor authentication.
- Cloud Audit Logs and Cloud Logging. These services record API calls and user actions and can export logs to BigQuery or external systems.
- Cloud KMS. Cloud KMS generates and manages cryptographic secrets and supports customer‑managed encryption and rotation.
- Security Command Center. This platform aggregates vulnerability findings and misconfiguration alerts into a dashboard that can feed issue trackers.
- VPC Service Controls. VPC Service Controls create perimeters around projects to reduce data exfiltration.
- Organization policies. Resource Manager constraints enforce allowed regions and service settings.
They reduce custom work but do not replace procedures, documentation, and regular reviews. You need to configure them correctly, test them, and collect evidence they operate as intended.
GCP’s SOC 2 report documents the controls Google operates. Your job is to configure these services properly and provide evidence that they operate as intended. Keep in mind the shared responsibility model: Google secures the data centers and network, while you secure identities, access, and data within your projects.
A condensed path to SOC 2 Cloud Compliance on GCP
Konfirmity’s experience shows that teams can achieve SOC 2 Cloud Compliance On GCP within four to five months when they follow a structured approach and use cloud‑native services. The process can be condensed into five main stages:
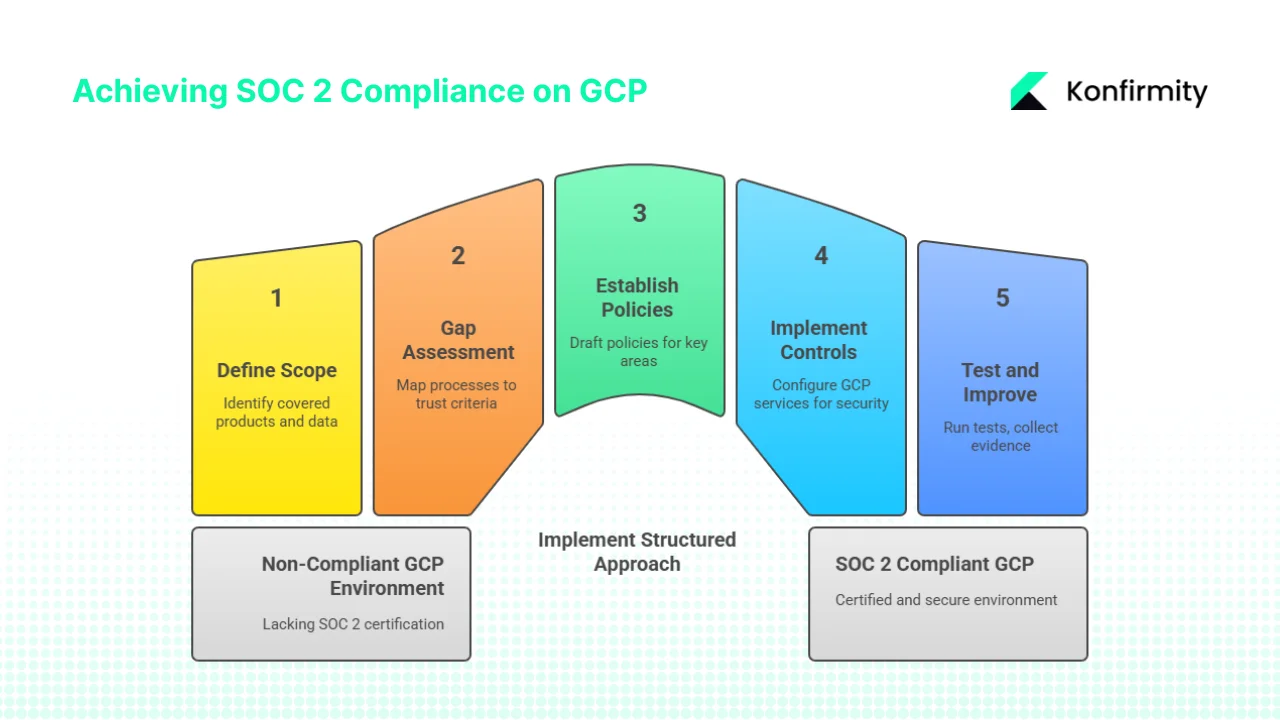
1. Define scope and stakeholders
Identify which products, features, and data flows will be covered. List the GCP projects and regions where they run and classify the types of data processed (personal, sensitive, operational). Engage engineering, security, product, and legal teams to agree on boundaries. A simple checklist can record project names, regions, data categories, and owners.
2. Conduct a gap assessment
Map your current processes and configurations to the five trust services criteria. Consult GCP’s SOC 2 report to see which controls are inherited. Identify gaps—such as missing incident response procedures, unreviewed access privileges, or absent logging. Prioritize remediation based on risk. A gap matrix listing each criterion, current state, and required actions is a useful tool.
3. Establish policies and governance
Draft or update policies for access control, data protection, incident response, change management, vendor management, and privacy. Each policy should state its scope, responsibilities, and review cycle, and an owner should be assigned. Keep descriptions concise, focusing on how you manage projects and classify data.
4. Implement technical controls and monitoring
Configure GCP services to enforce least‑privilege access, customer‑managed cryptography, service perimeters, and logging. Enable Security Command Center for vulnerability detection. Then design a monitoring plan that lists data sources, alert triggers (for instance, creation of new service accounts or firewall rule changes) and who responds to each alert.
5. Test, evidence, and continuous improvement
Run internal tests to ensure controls function as expected, such as removing user access, recovering from a failure, or simulating a breach. Collect evidence—policies, configurations, screenshots, and log exports—organized by trust criterion. During the observation window (typically six or more months), operate controls consistently. After the attestation, schedule recurring access reviews, risk assessments, policy updates, and incident response drills. Evaluate new GCP services and decide whether they fall within your scope.
CTA: Book a demo
A focused example: Acme CloudServices Inc.
To illustrate this process, consider a fictitious firm, Acme CloudServices Inc., which provides an analytics platform to large enterprises. The company runs its stack on GCP and wants to satisfy buyer due‑diligence before closing deals.
Scope. Acme defined the in‑scope products: its analytics API, dashboards, and data processing jobs. It listed the acme‑prod and acme‑staging projects and identified us‑central1 and europe‑west3 as regions. The team distinguished customer data from internal usage and noted that it handles pseudonymized personal information.
Gap assessment. Comparing their current state with the SOC 2 criteria, Acme found they lacked formal change‑management procedures and had not enabled Data Access logs for all services. They noted that GCP’s IAM, Logging, and KMS services covered many security controls.
Policies and governance. The company drafted policies for access control, data classification, incident response, vendor management, and risk assessment. Each document identified a responsible owner and a review schedule.
Technical configuration. Engineers applied least‑privilege roles in Cloud IAM, turned on customer‑managed encryption in BigQuery and Cloud Storage, configured VPC Service Controls around the production projects, and exported logs to a SIEM. They deployed the Security Command Center and integrated its findings into their ticketing system.
Monitoring and testing. Acme set alerts for high‑risk events—such as creation of new service accounts or modifications to firewall rules. They ran quarterly disaster recovery drills and monthly access reviews. During testing they discovered that log retention settings were too short for the observation window, so they adjusted them. Over a six‑month period the controls operated consistently. An independent auditor reviewed evidence and issued a SOC 2 Type II report with a minor recommendation about documentation. Acme’s enterprise sales deals accelerated because they could provide a clear report and evidence package.
Their experience shows that a structured approach to SOC 2 Cloud Compliance On GCP reduces internal effort, speeds up revenue, and improves resilience. By investing in reusable policies, native services, and continuous monitoring, Acme maintained compliance without slowing development. They also discovered that the disciplined work strengthened their security posture well after the audit.
Templates and workflows
Konfirmity provides downloadable resources to help teams move quickly. Each template fits a stage in the process:
These tools save time and ensure that evidence aligns with SOC 2 expectations. They are especially useful for small teams juggling sales and security tasks.
Common pitfalls and how to avoid them
1) Treating SOC 2 as a project rather than a program. Some teams enable controls just long enough for the audit. Once they receive the report, they stop monitoring and reviewing access. Over the next year the controls degrade. Avoid this by embedding access reviews, policy updates, and incident response drills into your calendar.
2) Assuming provider compliance covers everything. Because GCP has a SOC 2 Type II report, some leaders think their application is automatically covered. This is false: you must implement controls at your layer and provide evidence.
3) Ignoring documentation. Many companies focus on technical controls but neglect policies, change records, and incident reports. Auditors and clients will want to see version‑controlled documents with assigned owners and review cycles.
4) Underestimating monitoring. Teams often set up logs but fail to review them or configure alerts. Monitoring should include clear thresholds and assigned responders. During tests, verify that alerts trigger and that the team can investigate and resolve incidents.
5) Misaligning controls with risk. Not all systems have the same risk profile. Spending equal effort across low‑risk test environments and high‑risk production data can waste resources. Use risk assessments to direct attention to what matters most.
CTA: Book a demo
Conclusion
SOC 2 Cloud Compliance On GCP is achievable for companies selling into enterprises, but it demands discipline and continuous operation. By understanding the trust services criteria, separating provider and customer responsibilities, and leveraging GCP’s builtin services, you can build a program that satisfies auditors and buyers. The payoff is substantial: lower risk of breaches (which averaged $4.44 million in 2025), faster procurement cycles, and greater customer confidence. Konfirmity’s human‑led managed service helps teams design and operate such programs year‑round, so security remains strong and compliance follows naturally. Gather your stakeholders, use the templates provided, and start your path toward a reliable SOC 2 Type II report today.
When you treat security as an everyday practice instead of a deadline‑driven project, SOC 2 Cloud Compliance On GCP becomes a natural outcome rather than a burden. Those who invest early find that the same controls support other frameworks and make them more attractive to enterprise buyers. In an era when trust drives revenue, there is no better time to commit to this work.
Frequently asked questions
1) How are Type I and Type II different?
Type I reports cover design at a moment in time; Type II reports cover both design and operational effectiveness over a period.
2) Does using GCP’s report make me compliant?
No. Google’s report covers the platform; you must implement and document your own controls.
3) Which GCP services are covered?
Core services such as Compute Engine, App Engine, Cloud Storage, BigQuery, and IAM are included in the semi‑annual report. Additional services have separate annual reports.
4) How often should I review and test controls?
Regularly. Access reviews should occur quarterly, risk assessments annually, and incident response drills periodically.
5) What documentation do buyers expect?
Current policies, procedures, risk assessments, vendor management records, and evidence showing how controls operate. Include relevant sections of Google’s report and bridge letters.
6) Can controls be reused for other frameworks?
Many controls (e.g., access control, encryption, incident response) are common across SOC 2, ISO 27001, HIPAA, and GDPR. A risk‑based approach makes it easier to adapt evidence.
7) What is a bridge letter?
A short document from Google that extends assurance from the last report end date to the present.
8) How do I show I’m using GCP’s services correctly?
Provide evidence of IAM roles, encryption settings, audit log configurations, and resolution of Security Command Center findings. Screenshots, configuration exports, and log samples help.
9) What if I adopt a new GCP service mid‑period?
Evaluate whether it affects your scope and risk. Update your risk assessment and controls, and discuss with your auditor whether additional evidence is needed.





.svg)






.svg)
.svg)