Most enterprise procurement teams now ask to see a SOC 2 report before they sign a contract, and the bar is higher than simply having a policy on paper. A SOC 2 examination is a report on controls at a service organization relevant to security, availability, processing integrity, confidentiality, or privacy, and it provides assurance that you operate your systems safely. When selling into regulated sectors such as healthcare or finance, large buyers scrutinise how you manage personal data. SOC 2 includes a Privacy Trust Services Criterion that focuses on how you collect, use, retain, disclose and dispose of personal data. Managing individual data permissions—knowing who agreed to what, when and why—is a core part of that criterion. This article explores SOC 2 Consent Management and how to build an audit‑ready consent program that satisfies auditors and enterprise customers. Rather than surveying every SOC 2 control, we focus on consent: why it matters, what auditors expect, and how to implement it within your product and governance processes.
What is SOC 2 Consent Management?
The Privacy category in SOC 2 aims to protect people’s personal data. The AICPA’s privacy principle states that a service organization must collect, use, retain, disclose and dispose of personal information in accordance with its commitments and generally accepted privacy principles. A core requirement is choice and consent—the organization must describe the choices available to the individual and obtain implicit or explicit consent for the collection, use and disclosure of personal information. This is more than publishing a privacy notice; auditors expect a defined process with clear documentation. Privacy policies, consent forms and internal procedures must align, and evidence of user permissions must be available.
Key terms
- Consent records: documented proof that a user agreed (explicitly or implicitly) to a specific data processing purpose. Under the GDPR, consent must be freely given, specific, informed and unambiguous, and users must have real choice without pressure. SOC 2 auditors look for documentation of each consent event, including timestamps, identity and the scope of the consent.
- User permissions: the set of rights and preferences a user has expressed regarding their data. This includes opt‑in or opt‑out choices, cookie preferences, marketing preferences, and restrictions on data sharing. When you change your product or business model, you must re‑obtain consent where required and record the new permission state.
- Data subject rights: the rights individuals have over their personal data under modern privacy laws. The GDPR grants eight fundamental rights—rights to be informed, access, rectification, erasure, data portability, restriction of processing, withdrawal of consent and objection to automated decision making. Controllers must respond to data subject access requests within one month. SOC 2 privacy controls intersect with these rights because a consent management system should support access, deletion and withdrawal requests.
Consent management within SOC 2 is therefore the practice of capturing user permissions, storing them securely, linking them to privacy notices and policies, and being able to prove to an auditor that you honour those permissions. It ties to modern data regulation because regulators expect accountability. The GDPR requires controllers to keep records of processing activities and to demonstrate that consent was obtained appropriately. The SOC 2 privacy criterion mirrors these principles, emphasising explicit consent, limited use and proper disposal.
Why consent management is critical for enterprise‑level SOC 2
Large buyers want more than a checkbox. They need assurance that you can demonstrate data governance in practice. Modern procurement questionnaires ask about data retention, cross‑border transfers, cookie policies and data subject rights. Without a robust SOC 2 Consent Management system, deals stall because legal teams insist on clarity around consent capture and withdrawal. Consent management supports three broader objectives:
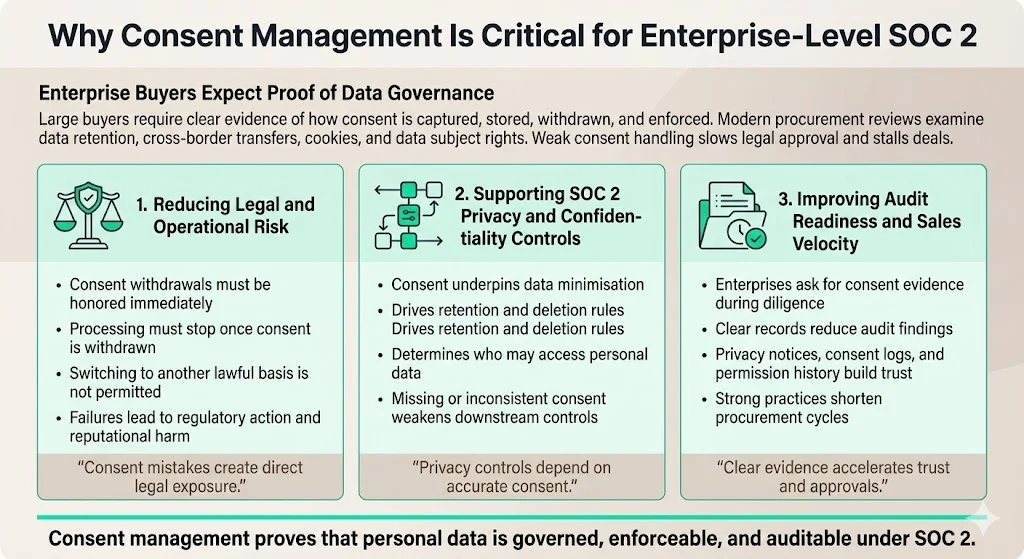
- Reducing legal and operational risk. Mismanaging consent can lead to regulatory fines and lawsuits. The European Data Protection Board emphasises that controllers must honour withdrawals and cannot switch to another lawful basis once consent is withdrawn. Failing to comply leads to enforcement actions and reputational damage.
- Supporting broader SOC 2 privacy and confidentiality controls. Consent capture is intertwined with data minimisation, retention policies and access controls. For example, the SOC 2 privacy principle requires that personal information is collected only for purposes identified in the notice and used only for those purposes. If consents are inconsistent or missing, other controls fall apart.
- Improving audit readiness and sales velocity. Enterprises often ask for evidence of consent management during diligence. Being able to show a clear evidence chain—privacy notices, consent records, and user‑permission logs—accelerates trust. Our experience at Konfirmity, after supporting over 6,000 audits across 25 years of combined expertise, shows that companies with strong consent practices reduce audit findings and shorten sales cycles.
The stakes are high. IBM’s 2025 Cost of a Data Breach Report found that while global average breach costs fell to $4.44 million—thanks to AI‑powered detection—U.S. breach costs rose to $10.22 million. Shadow AI incidents, largely ungoverned AI tools, accounted for 20% of breaches. These figures highlight how attackers exploit gaps in governance. Consent management won’t prevent a breach, but it ensures that personal data is properly governed and that you can demonstrate accountability to regulators and buyers. In highly regulated industries, the cost of failing to honour consent or respond to a data subject request can far exceed the cost of implementing proper controls.
Core components of SOC 2 Consent Management
Building an audit‑ready consent program requires a combination of policies, technical controls and evidence management. The following components provide a framework:
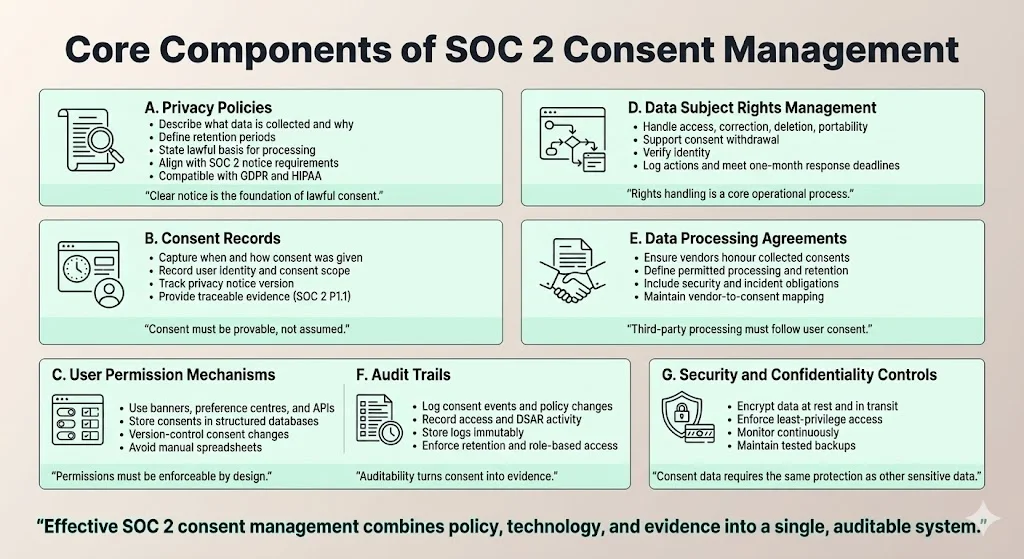
a. Privacy policies
Your privacy policy should explain what personal data you collect, why you collect it, how long you keep it, and the lawful basis for processing. It must align with the AICPA’s requirement to provide notice and obtain consent for collection, use and disclosure and with frameworks such as GDPR and HIPAA.
b. Consent records
Maintain a record for each user capturing when and how they consented, the scope, user identity and the version of the notice they saw. Under GDPR, consent must be affirmative, and SOC 2 privacy control P1.1 requires a traceable evidence chain.
c. User permissions mechanisms
Use a combination of banners, preference centres and APIs to capture consents on the front end and store them in a structured, version‑controlled database. Automate logging to track changes, and avoid manual spreadsheets.
d. Data subject rights management
Design workflows and logs to handle access, rectification, erasure and portability requests, as well as consent withdrawals. Provide forms for intake, automate assignment and logging, verify identities, and respond within one month, as the GDPR requires.
e. Data processing agreements
Ensure your third‑party processors honour the consents you collect. HIPAA mandates business associate agreements; in SOC 2, DPAs should define permitted processing, retention limits, security requirements and incident reporting. Maintain an inventory mapping vendors to user consents.
f. Audit trails
Store logs of consent captures, policy changes, access events and DSAR fulfilment in an immutable system, with role‑based access and retention periods that satisfy SOC 2 and HIPAA requirements.
g. Security protocols and confidentiality controls
Implement encryption for data at rest and in transit, least‑privilege access, continuous monitoring and tested backups. These controls meet SOC 2 criteria for confidentiality and HIPAA’s technical safeguards.
Best practices for implementing SOC 2 Consent Management
Drawing on our experience running over 6,000 audits and operating security programs for clients in healthcare, financial services and SaaS, we recommend the following steps to build a mature consent management program.
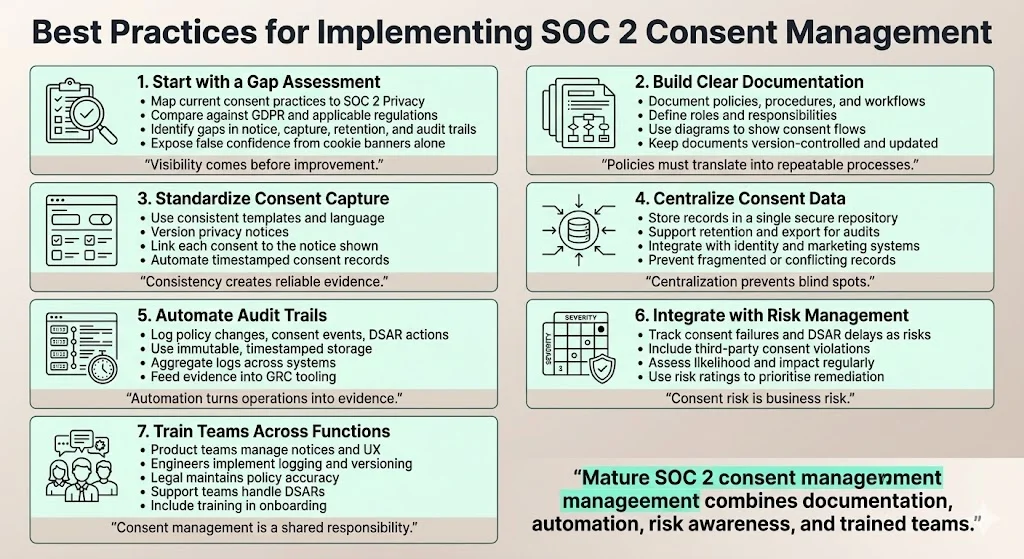
1. Start with a gap assessment
Map how you currently collect and store user consents against the SOC 2 privacy criterion, GDPR requirements and other applicable regulations. Identify gaps in notice content, consent capture processes, record retention and audit trails. Many companies think they have consent management because they display a cookie banner, yet they lack verifiable evidence chains. A structured gap assessment surfaces these issues early.
2. Build clear documentation
Document your privacy policies, consent collection procedures, retention schedules and data subject request workflows. Include details on roles and responsibilities. A policy without procedures is a passive edict; auditors need evidence that processes are actually followed. Use diagrams and process maps to show how consent flows through your systems. Keep documentation under version control and update it at least annually.
3. Standardize consent capture
Use templated forms and preference centers with consistent language and versioning. Link each consent event to the exact notice shown to the user. Implement automated logging so that each consent creates a record with timestamp and scope. Avoid manual spreadsheets, which are error‑prone and unsuited for SOC 2 Type II observation periods (commonly 3–12 months). Standardization also makes cross‑framework mapping easier—for example, aligning Privacy P1.1 controls with ISO 27001’s Clause A.7.3 on consent and ISO 27701’s requirements for privacy information management.
4. Centralize consent data
Store consent records in a searchable, secure repository that supports retention policies and data export for audits. Ideally, your consent store should integrate with your identity provider and marketing tools to enforce user preferences. Centralization prevents fragmented records and ensures that updates propagate across systems.
5. Automate audit trails
Set up systems that automatically log control activities—changes to privacy policies, consent capture events, DSAR processing steps and vendor access. Use immutable storage and timestamping. Automated logs minimize human error and provide continuous evidence. Tools such as SIEMs (security information and event management) can aggregate logs across systems. Integrate audit trail outputs with your GRC platform to support audit readiness.
6. Integrate with your risk management program
Treat consent risk as part of your overall risk management. Include consent failures, DSAR response delays and third‑party consent violations in your risk register. Perform regular risk assessments that consider the likelihood and impact of consent mismanagement. Align risk ratings with CVSS scores where relevant. Map controls to the Statement of Applicability (SoA) in ISO 27001 or the control matrix in SOC 2. Use risk assessments to prioritise remediation and inform policy updates.
7. Train teams
Education is essential. Product managers must understand how to display notices and track consent. Engineers need to build logging and versioning. Legal teams must keep policies current. Support teams should know how to triage DSARs. Provide regular training sessions and incorporate consent management into onboarding for new hires. Our clients who invest in cross‑team training see fewer compliance incidents and faster audit cycles.
Step‑by‑step guide to building audit‑ready consent management
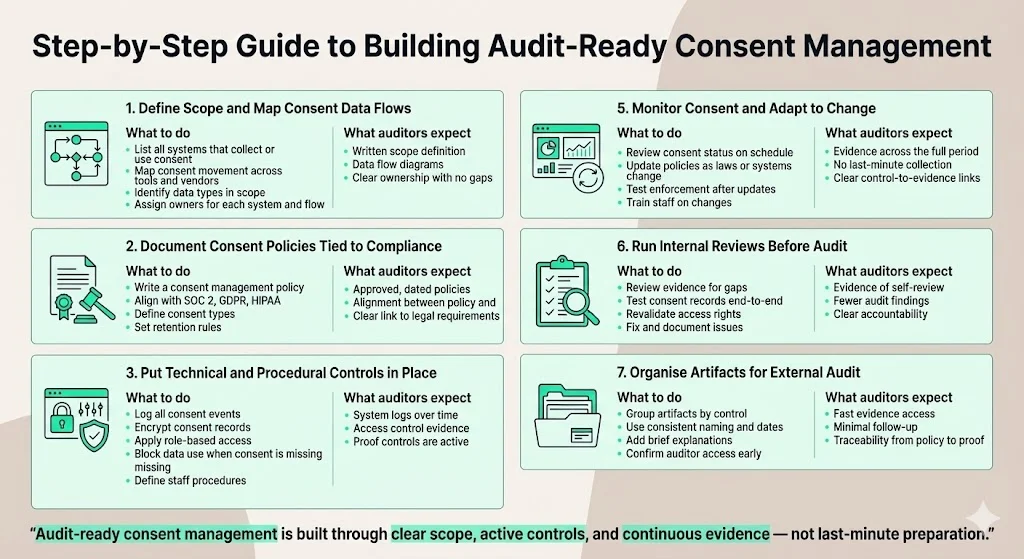
1. Define scope and map consent data flows
Start by setting clear boundaries. Audits fall apart when scope is vague.
What to do
- List all systems that collect, store, or rely on user consent
- Map how consent data moves between products, vendors, and internal tools
- Identify which data types are in scope, such as personal data, health data, or marketing preferences
- Assign an owner for each system and data flow
What auditors expect
- A written scope statement
- Data flow diagrams showing where consent is captured, stored, and used
- Clear ownership with no gaps
2. Document consent policies tied to compliance needs
Policies show intent. They must connect directly to SOC 2 and applicable laws.
What to do
- Write a consent management policy that explains how consent is collected, stored, updated, and revoked
- Align language with SOC 2 trust principles and legal rules like GDPR and HIPAA
- Define consent types, such as explicit, implied, and withdrawn
- Set retention rules for consent records
What auditors expect
- Approved, dated policies
- Evidence that policies match actual practices
- Clear links between legal rules and internal controls
3. Put technical and procedural controls in place
This is where theory turns into proof.
What to do
- Log all consent events with timestamps, user IDs, and source
- Encrypt consent records at rest and in transit
- Restrict access using role-based rules
- Block data use when valid consent is missing or withdrawn
- Add procedures for staff who handle consent requests
What auditors expect
- System logs that show consent actions over time
- Access control settings and user lists
- Proof that controls are active, not just documented
4. Collect evidence during the observation period
SOC 2 Type II focuses on how controls work over time, not one moment.
What to do
- Save logs, screenshots, tickets, and system reports regularly
- Track consent updates and withdrawals as they happen
- Keep change records for policy or system updates
- Store evidence in a central location with clear labels
What auditors expect
- Consistent evidence across the full observation window
- No last-minute data pulls
- Clear ties between controls and proof
5. Monitor consent status and adapt to change
Consent rules do not stay still. Products and laws shift.
What to do
- Review consent status dashboards on a set schedule
- Update policies when laws, features, or data use changes
- Test consent enforcement after system changes
- Train staff on updated rules and workflows
What auditors expect
- Change logs with reasons and approval
- Proof that updates were communicated and applied
- Ongoing monitoring, not one-time setup
6. Run internal reviews before auditors arrive
Internal checks reduce risk and stress.
What to do
- Review evidence for gaps or inconsistencies
- Test a sample of consent records end to end
- Verify that access rights still match roles
- Fix issues and record the actions taken
What auditors expect
- Signs of self-review and correction
- Fewer surprises during testing
- Clear accountability
7. Organise artifacts for external audit
Preparation saves weeks during fieldwork.
What to do
- Group artifacts by control and audit section
- Use consistent file names and dates
- Add short explanations for complex items
- Confirm access for audit reviewers ahead of time
What auditors expect
- Fast access to evidence
- Minimal back-and-forth
- Clear traceability from policy to control to proof
In our experience supporting more than 6,000 audits over 25 years of combined expertise, companies using a human‑led managed service typically reach SOC 2 Type II readiness in four to five months versus nine to twelve months when self‑managed, and reduce internal effort from hundreds of hours to roughly 75 hours per year.
Common challenges and how to overcome them
Despite best intentions, several pitfalls repeatedly appear in the field:
- Fragmented consent records: Multiple systems collect consents (marketing tools, web apps, mobile apps), leading to inconsistent records. Solution: centralize consent storage and integrate upstream systems via APIs. Perform periodic reconciliations and de‑duplication.
- Lack of policy alignment: Privacy notices, DPAs and internal procedures are often out of sync. Solution: establish a change management process for policies. When products or laws change, update all relevant documents simultaneously. Maintain version histories and communicate updates to users.
- Insufficient logs: Teams sometimes neglect to record consent updates or DSAR fulfilment. Solution: automate logging and enforce retention. Use immutable storage and regularly test that logs contain required data.
- Cross‑team coordination gaps: Engineering may build features without consulting legal or compliance teams, leading to data flows that violate consent boundaries. Solution: hold regular privacy reviews where product, legal and security teams evaluate proposed changes. Use a privacy impact assessment (PIA) or data protection impact assessment (DPIA) process.
- Changing compliance landscape: Regulations evolve (e.g., EU Digital Services Act, India’s Digital Personal Data Protection Act). Solution: schedule periodic risk assessments and horizon scanning. Update consent management processes to incorporate new requirements and consult with external counsel when necessary.
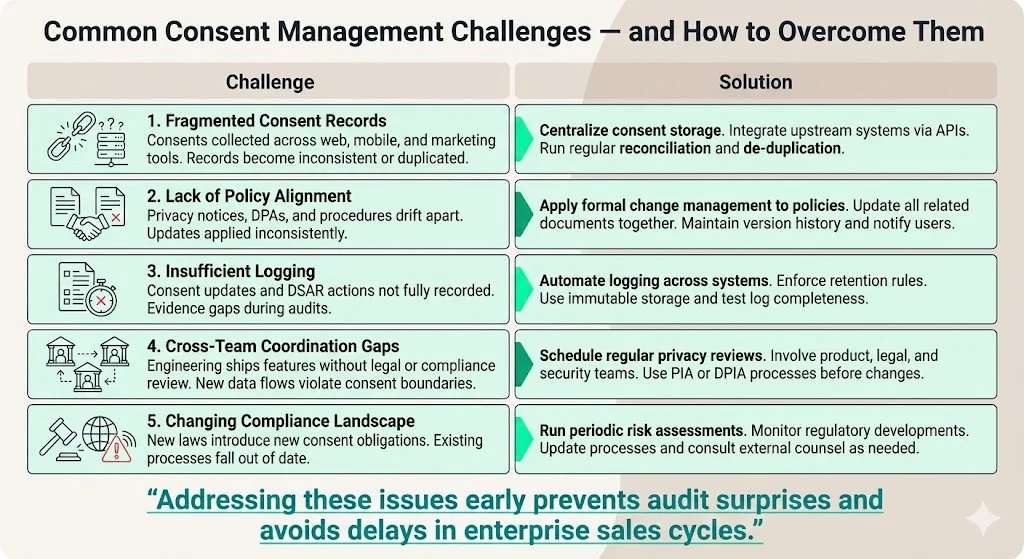
Addressing these challenges early prevents last‑minute fire drills during audits and avoids delays in enterprise sales cycles.
How consent management fits into overall SOC 2 controls
Consent management lives primarily under the Privacy and Confidentiality Trust Services Criteria, but it intersects with other categories:
- Security: Access control, logging and incident response, which are foundational for SOC 2, support consent management by protecting consent data and detecting misuse. The HIPAA Security Rule’s requirement for audit controls is a prime example of a security control that also supports consent management.
- Availability and processing integrity: Consent workflows must be available and accurate. If a user’s consent update fails to propagate, you risk violating their preferences. Capacity planning and reliable processing are therefore relevant.
- Vendor management: Third‑party processors must respect your consent boundaries. SOC 2 requires that you assess vendors and document their compliance. Track vendor risk and include consent considerations in vendor due diligence.
- Risk management and continuous monitoring: SOC 2 encourages a risk‑based approach. Consent mismanagement should be part of your risk register, with controls mapped to mitigate it.
The Konfirmity difference
As a human‑led, managed security and compliance service, Konfirmity doesn’t stop at guidance. Our dedicated CISOs and security engineers embed with your team to design, implement and operate the controls described above. We align SOC 2 Consent Management with broader frameworks like ISO 27001 and HIPAA, mapping each control to a risk register and Statement of Applicability. Because we handle evidence collection, vendor risk reviews and ongoing monitoring, your team typically spends about 75 hours per year on compliance activities instead of hundreds. This outcome‑as‑a‑service model is why our customers achieve SOC 2 Type II readiness months faster than self‑managed projects. We start with security and arrive at compliance, ensuring that consent management is woven into your product stack and that it stands up under buyer scrutiny and real‑world incidents.
SOC 2 is flexible: you design controls that are suitable for your risk and architecture. For small SaaS platforms, consent management might involve a single service; for healthcare or fintech companies, it may span multiple systems and jurisdictions. The key is to tailor controls to your environment while satisfying the trust services criteria.
Conclusion
Consent management is no longer optional for companies selling into regulated enterprise markets. SOC 2 Consent Management integrates privacy principles, regulatory requirements and operational controls. By implementing clear policies, capturing and storing consent events with evidence chains, supporting data subject rights and securing consent data, you demonstrate accountability to auditors and buyers. The payoff is tangible: better trust signals, fewer audit findings and faster sales cycles. With data breach costs averaging $4.44 million globally and $10.22 million in the U.S. in 2025, proper consent management is a business imperative. Build the program once, operate it continuously and let compliance follow.
Frequently asked questions
Effective SOC 2 Consent Management underscores your commitment to user privacy and security.
1. What exactly does SOC 2 require for consent management?
SOC 2’s Privacy criterion expects that you describe choices available to individuals and obtain explicit or implicit consent for collection, use and disclosure of personal information. You must limit data collection to stated purposes, use information only with consent, and provide access rights. Auditors will look for policies, procedures and evidence (e.g., consent logs, notices, DPAs) showing that these requirements are met.
2. Do I need a separate consent module in my product?
Not necessarily. Small applications can implement consent capture within existing authentication or subscription flows. For complex products with multiple data streams, a dedicated consent management module or a third‑party consent management platform may be appropriate. The key is to centralize records, standardize capture and integrate with your access control and marketing systems.
3. How can I demonstrate consent management to an auditor?
Provide your privacy policy and consent collection procedures. Show sample consent records with timestamps, user identities and scope. Offer evidence of DSAR fulfilment, vendor DPAs and audit logs demonstrating access control. Document how you map each control to the SOC 2 Privacy criterion and how you monitor ongoing compliance.
4. What’s the difference between consent management and privacy policy documentation?
A privacy policy is a high‑level statement explaining how you handle personal data; consent management is the operational system that implements and enforces that policy. The policy describes purposes, rights and lawful bases; consent management records each user’s permissions, maintains audit trails and supports withdrawals and rights requests. Without an operational system, a policy alone does not satisfy SOC 2.
5. Can a third‑party tool help with consent tracking?
Yes. Many organizations use consent management platforms to manage cookie banners, marketing preferences and DSAR workflows. When selecting a tool, ensure it integrates with your systems, supports evidence collection and allows you to export data for audits. Regardless of whether you use a third‑party tool or build in‑house, you remain accountable for compliance and must ensure the tool aligns with your privacy commitments.





.svg)






.svg)
.svg)