Most enterprise buyers now ask for proof of security and compliance before signing a contract. Without operational security and continuous evidence, deals stall—even when teams believe they are ready on paper. This article explains SOC 2 Controls Mapped To COBIT for companies selling to large clients and healthcare organizations. By mapping SOC 2 controls to COBIT, teams can unify security practices with governance and risk management, create clearer audit records, and support due‑diligence requests.
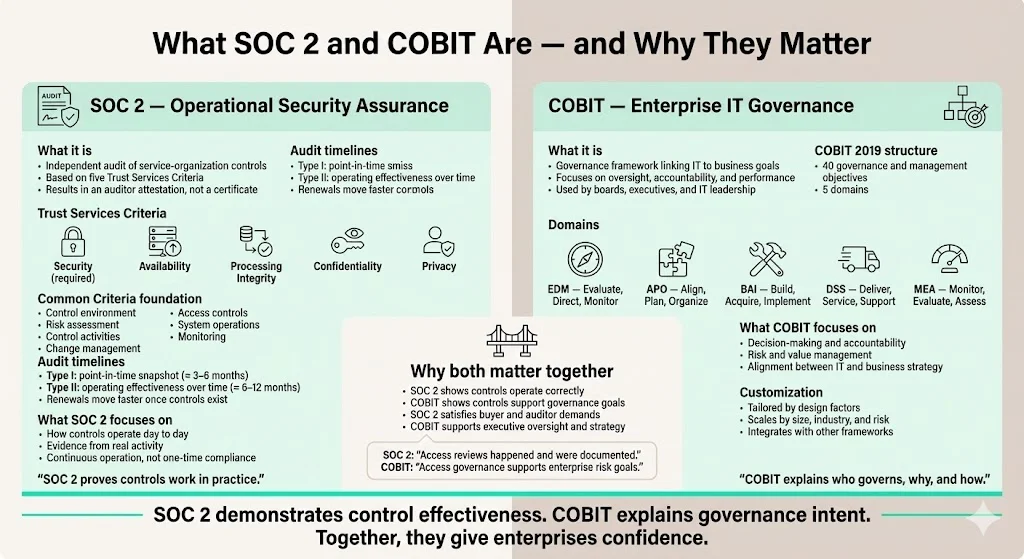
Before diving into the mapping process, it helps to define each framework. SOC 2 is a compliance standard developed by the American Institute of Certified Public Accountants (AICPA). It evaluates how well a service provider protects data across five Trust Services criteria: security, availability, processing integrity, confidentiality and privacy. The security criterion is mandatory; the others can be added based on customer commitments and risks. SOC 2 audits come in two types: Type I assesses whether controls are designed properly at a point in time, while Type II tests whether those controls operate effectively over an observation period of three, six or twelve months. A Type II report is generally required by large buyers and healthcare partners because it demonstrates sustained control operation.
COBIT is an IT governance framework created by ISACA. It is designed to link enterprise goals with information technology processes. The framework’s current edition, COBIT 2019, consists of forty governance and management objectives across five domains: Evaluate, Direct and Monitor (EDM – 5 objectives), Plan and Organize (APO – 14 objectives), Build, Acquire and Implement (BAI – 11 objectives), Deliver, Service and Support (DSS – 6 objectives), and Monitor, Evaluate and Assess (MEA – 4 objectives). Each objective has practices and activities that can be thought of as controls in a broad sense. In earlier versions, COBIT described thirty‑seven processes; mapping to the 2019 objectives therefore requires careful translation.
Mapping SOC 2 controls to COBIT matters for two reasons. First, it helps unify security controls with broader governance and risk management practices. SOC 2 emphasises control execution and evidence collection, while COBIT offers a governance lens that connects controls to business objectives. Second, a mapping supports clearer audit evidence and enterprise reporting. When a security team can show how its SOC 2 controls correspond to COBIT objectives, auditors and procurement teams gain confidence that the organization has a mature governance program.
What SOC 2 and COBIT Are (and Why They Matter)
Overview of SOC 2
SOC 2 audits measure how well a service organization protects information using the five Trust Services criteria: security, availability, processing integrity, confidentiality and privacy. The AICPA defines nine common criteria across these categories: control environment, communication and information, risk assessment, monitoring activities, control activities, logical and physical access controls, system operations, change management and risk mitigation. These common criteria derive from the COSO internal control framework and make up the backbone of SOC 2 audits. The security criterion (often called the common criteria) is mandatory, while the other criteria are optional but often needed in enterprise contracts.
A typical SOC 2 Type II audit covers an observation period of six to twelve months. According to Scrut’s 2025 guidance, first‑time Type II audits take six to twelve months, while Type I audits (a snapshot of controls) may take three to six months. Renewal audits are faster, often six to eight months, because evidence and processes are already in place. The goal of SOC 2 is not to produce a one‑time certificate but to build continuous controls and evidence collection into everyday operations.
From a control count perspective, SOC 2 does not prescribe a fixed number of controls. The number depends on the organization’s scope and risk profile. The common criteria provide points of focus and guidelines for what auditors expect. For example, the security criterion requires controls for access management, change management, risk assessment, incident response, and monitoring system operations. The availability criterion looks at backup, disaster recovery and business continuity planning. Processing integrity focuses on ensuring systems perform as intended, while confidentiality and privacy focus on protecting sensitive information and personal data.
Overview of COBIT
COBIT is a governance framework that aims to link enterprise information and technology with stakeholder needs. It provides a structure for matching IT goals with business objectives and managing risks. In COBIT 2019, there are forty governance and management objectives across five domains. Each domain addresses a different aspect of IT governance and management:
- Evaluate, Direct and Monitor (EDM): This domain houses five objectives that focus on bringing enterprise and IT strategies together, optimizing resources and securing stakeholder buy‑in.
- Plan and Organize (APO): Fourteen objectives cover organizational structure and strategy, budgeting, resource management, vendor management and risk management.
- Build, Acquire and Implement (BAI): Eleven objectives focus on building and implementing IT solutions, including change and project management.
- Deliver, Service and Support (DSS): Six objectives cover operations management, incident handling, continuity, process controls and security.
- Monitor, Evaluate and Assess (MEA): Four objectives monitor performance and conformance, internal control, external requirements and assurance.
COBIT emphasizes customizing the governance system to the organization. ISACA’s guidance highlights that the 2019 version introduced flexible performance management, design factors and integration with other frameworks such as ISO 27001 and NIST. This flexibility allows enterprises to customize the governance objectives, maturity models and enablers to match their business context.
Why IT Governance and Security Controls Need Alignment
SOC 2 focuses on whether controls exist and operate effectively, while COBIT positions those controls within a broader governance system. Without matching, security teams may build strong technical controls but miss how those controls support enterprise goals or regulatory obligations. For example, a SOC 2 access review process may confirm that administrators review accounts quarterly, yet COBIT’s EDM domain asks whether those reviews support stakeholder needs and correspond to strategic objectives. Matching the two frameworks bridges compliance with strategic risk management and ensures that controls are not just checkboxes but business enablers. This is why mapping SOC 2 controls to COBIT is so important.
A mapping also supports integrated risk management. SOC 2’s risk assessment criterion (CC3) asks organizations to identify and assess risks to achieving the Trust Services criteria. COBIT’s risk‑related objectives in the APO and MEA domains guide how to evaluate, monitor and respond to risk. When the two are mapped, risk assessments can feed both compliance reports and governance dashboards, helping stakeholders see the connection between control operation and enterprise risk.
The Case for Mapping SOC 2 to COBIT
What Control Mapping Means
Control mapping involves matching SOC 2 Trust Services criteria and their common criteria to COBIT governance and management objectives. The AICPA provides mapping spreadsheets that crosswalk SOC 2 common criteria to frameworks like ISO 27001, NIST CSF and COBIT 5. Although those spreadsheets focus on the 2012 version of COBIT, mapping to COBIT 2019 is similar because the domains remain consistent and the number of objectives increased from thirty‑seven to forty. In practice, SOC 2 Controls Mapped To COBIT is a recognized cross‑walk used by many teams.
A basic mapping process includes identifying each SOC 2 control category, finding the equivalent COBIT governance or management objective, and translating those connections into audit and compliance artefacts. For example, SOC 2’s control environment criterion (CC1) corresponds to COBIT’s EDM objectives, while change management controls correspond to BAI objectives and access management corresponds to DSS objectives (more on examples below). Mapping does not replace the need for a SOC 2 audit. It creates a reference matrix that shows where controls live within a governance framework.
Benefits for Busy Teams
Enterprises often manage multiple compliance frameworks—SOC 2, ISO 27001, HIPAA, GDPR and others. Without mapping, each framework may spawn separate control lists, policies and evidence repositories. Mapping SOC 2 controls to COBIT delivers several benefits:
When you apply SOC 2 Controls Mapped To COBIT, you achieve the following benefits:
- Efficient preparation: Teams can reuse evidence across frameworks. For example, access review documentation gathered for SOC 2 can serve COBIT DSS objectives, ISO 27001 Annex A controls and HIPAA security rule safeguards.
- Reduced duplication: Mapping reduces redundant policies and procedures. A single change management process can satisfy SOC 2 change management (CC8), COBIT BAI objectives and ISO 27001 Annex A.12 controls.
- Stronger audit readiness: When auditors see controls linked to COBIT objectives, they can quickly trace them to enterprise governance. This supports due‑diligence questions from buyers who want assurance that security is embedded within IT governance.
From Konfirmity’s delivery work—more than 6,000 audits across 25 years of combined expertise—we see the practical impact of mapping. Without mapping, clients often maintain separate policy documents and evidence lists for each framework. This duplication wastes hundreds of hours. With mapping, teams maintain a single set of controls and evidence tied to multiple frameworks, saving roughly 75 percent of internal effort. Our clients typically achieve SOC 2 readiness in four to five months using a managed program, compared with nine to twelve months using an internal, self‑managed approach. That translates to about 75 hours per year of internal effort versus 550–600 hours when run internally, based on our project data.
How Mapping Supports Risk Management
Mapping SOC 2 controls to COBIT also strengthens risk management. By associating each control with a governance objective, risk assessments can identify where control weaknesses may affect strategic goals. For example, SOC 2’s risk mitigation criterion (CC9) ties into COBIT’s MEA objectives, which focus on monitoring performance and assurance. If a vulnerability management process fails to meet SLAs, the mapping shows not only that a SOC 2 control is weak but also that a governance objective (such as DSS or MEA) is at risk. This enables clear communication to executives and helps prioritize remediation.
How SOC 2 Controls Map to COBIT
Basic Mapping Approach
The SOC 2 Controls Mapped To COBIT methodology includes:
- Identify SOC 2 control categories. List each control under its Trust Services criterion and common criterion. For example, access reviews fall under CC6 (logical and physical access controls), while change management falls under CC8.
- Match to COBIT objectives. For each SOC 2 control, find the COBIT objective that covers the same intent. SOC 2 access controls map to COBIT DSS objectives (which handle service delivery, support and security) and sometimes to APO objectives if they involve vendor or HR processes. Change management maps to BAI objectives, while governance actions map to EDM objectives.
- Translate into artefacts. Document the mapping in a matrix showing each SOC 2 control, the corresponding COBIT objective, the evidence needed and the stakeholders involved. This matrix becomes a living document.
What Gets Mapped
- Security Controls → COBIT security and governance processes: SOC 2’s logical and physical access controls (CC6) correspond to COBIT DSS objectives, which cover identity management, service delivery and incident handling.
- Risk Management → COBIT risk evaluation and monitoring: SOC 2’s risk assessment (CC3) and risk mitigation (CC9) map to APO and MEA objectives for risk evaluation, risk response and assurance.
- Business Process Controls → COBIT IT process objectives: SOC 2’s system operations (CC7), monitoring activities (CC4) and change management (CC8) map to BAI and DSS objectives. These objectives govern system development, implementation, maintenance and support.
- Data Protection and Privacy → COBIT practices that support confidentiality and integrity: SOC 2’s confidentiality and privacy criteria correspond to APO objectives around vendor and contract management, DSS objectives for incident response, and MEA objectives for compliance monitoring.
Example Mapping Details
- Control environment (CC1) → EDM: The control environment criterion requires governance oversight, a board or committee charter and a tone‑at‑the‑top that promotes control importance. This corresponds to COBIT’s EDM domain, particularly objectives that focus on bringing enterprise and IT strategies together and engaging stakeholders.
- Change management (CC8) → BAI: SOC 2 expects documented change management processes for software and infrastructure, including approvals, testing and segregation of duties. COBIT’s BAI objectives address change management and project management, making them natural matches.
- Logical and physical access controls (CC6) → DSS: SOC 2 requires control over user access, authentication, authorization and physical security. COBIT’s DSS objectives handle service delivery, problem and incident management, continuity and security. Mapping CC6 to DSS ensures that access control is not just a technical function but part of service delivery and support.
Exact mapping depends on organizational context and the version of COBIT. For instance, COBIT 2019 expanded objectives and introduced design factors, while COBIT 5 described thirty‑seven processes. The mapping matrix should reflect the version in use and be reviewed periodically.
Step‑by‑Step Guide to Performing the Mapping
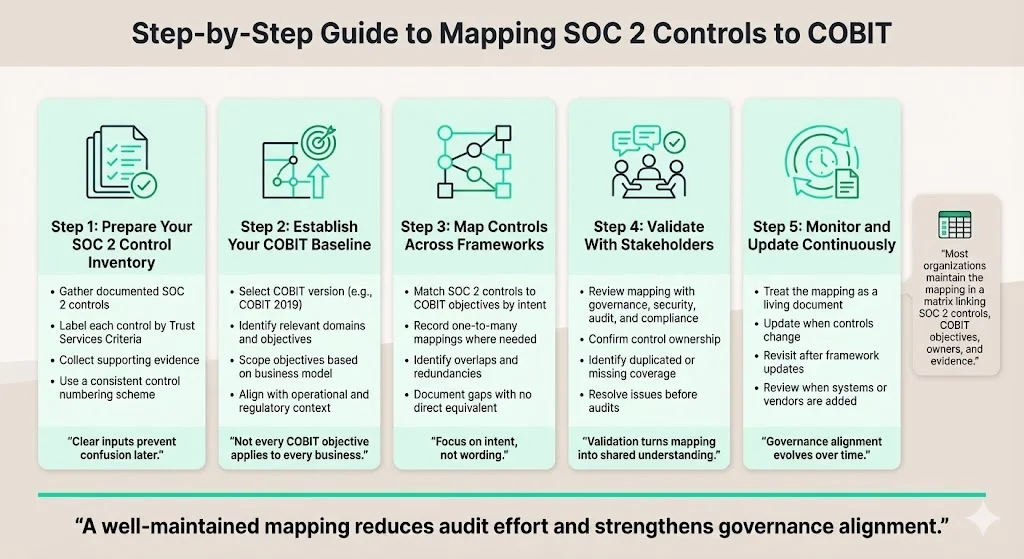
Step 1: Prepare Your SOC 2 Control Inventory
Gather your documented SOC 2 control descriptions. Label each control by its Trust Services criterion and common criterion. Collect evidence such as policies, procedures, logs, tickets and reports. Use a consistent numbering system to avoid confusion when mapping across frameworks.
Step 2: Establish Your COBIT Baseline
Identify the COBIT version you will use—COBIT 2019 is generally preferred for enterprise adoption. Define which domains and objectives are relevant based on your business scope. For example, a cloud SaaS provider may focus on BAI and DSS objectives, while a healthcare provider handling ePHI must also consider APO objectives around vendor and contract management.
Step 3: Map Controls
For each SOC 2 control, identify the COBIT objective with the same intent. Document gaps and overlaps. If a control maps to multiple COBIT objectives, record all connections. Where no equivalent objective exists, record the gap and decide whether to add a compensating control or adjust your governance practices.
Step 4: Validate With Stakeholders
Review the mapping with stakeholders across IT governance, security, audit and compliance. Ensure that control owners understand how their controls support governance objectives. This review may reveal duplications or gaps that can be resolved before the audit.
Step 5: Monitor and Update
View the mapping as a living artefact. Update it whenever controls change or when frameworks are updated. For example, if ISACA releases an update to COBIT or if your organization adds new systems, revisit the matrix to ensure coverage. Regular reviews help maintain continuous compliance and governance matching.
Practical Tips for Enterprise Teams
To implement SOC 2 Controls Mapped To COBIT effectively, consider these tips:
- Invest in a tool that supports framework matching. A compliance platform that allows cross‑framework mapping and evidence reuse can save hundreds of hours. Look for features like automated evidence collection, control libraries and cross‑walking matrices.
- Use visual matrices for executive reporting. Executives need to see how controls support business objectives. A matrix that shows SOC 2 controls mapped to COBIT objectives, ISO 27001 clauses, HIPAA safeguards and GDPR articles provides clarity during due‑diligence meetings.
- Tie risk assessments directly to mapped controls. When performing risk assessments (CVSS‑based vulnerability scoring, vendor risk assessments, DPIAs for GDPR or ePHI risk analyses for HIPAA), link each risk to the relevant SOC 2 controls and COBIT objectives. This ensures that risk treatments improve both compliance and governance.
- Keep the documentation audit‑ready and version‑controlled. Use version control systems to track changes to policies and evidence. Maintain an evidence register that shows the last time each control was tested and which frameworks it covers. During the observation period for a SOC 2 Type II audit, auditors will examine evidence from the entire period, so as to ensure that logs and tickets are captured consistently.
Common Challenges and How to Overcome Them
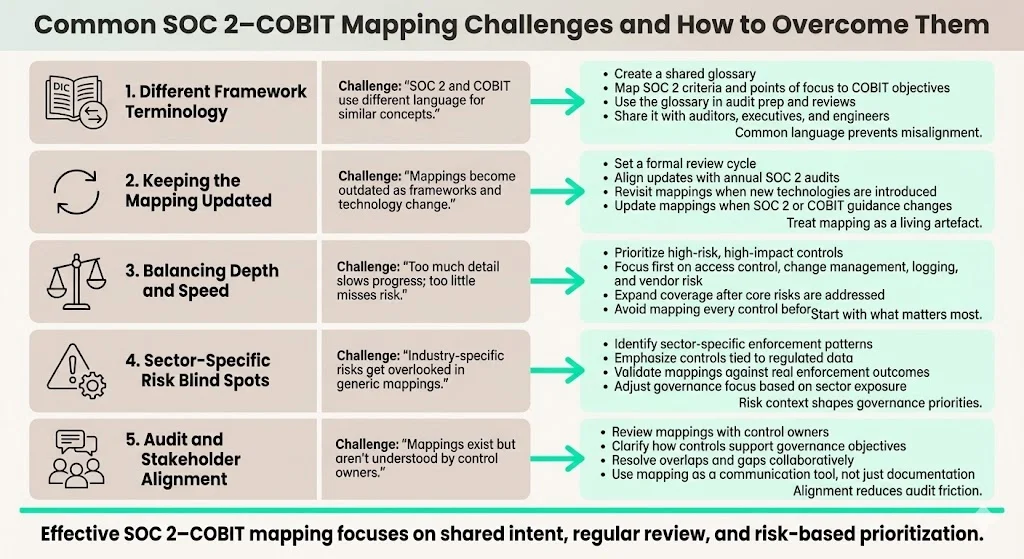
Different Framework Terminology
SOC 2 and COBIT use different terminology. For example, SOC 2 refers to “criteria” and “points of focus,” while COBIT refers to “objectives” and “practices.” To bridge these differences, create a glossary for your team. For each SOC 2 criterion, list the COBIT objective(s) that cover the same area. This helps avoid confusion when communicating with auditors, executives and engineers.
Keeping the Mapping Updated
Frameworks change over time. SOC 2 guidance is revised periodically by the AICPA; COBIT updates occur as technology and governance practices change over time. To keep the mapping current, institutionalize a review cycle. Match updates with your annual SOC 2 audit and IT governance planning cycle. When new technologies (such as serverless computing or machine learning services) are adopted, assess whether existing controls cover them and map them to the appropriate COBIT objectives.
Balancing Depth vs. Speed
Organizations often struggle to balance thoroughness with speed. A rushed mapping may miss critical controls, while an overly detailed mapping can delay readiness. Prioritize controls with the highest risk and audit impact. For example, access control drift, change‑management gaps, vendor sprawl and weak logging are common pitfalls. In healthcare, unencrypted ePHI, incomplete Business Associate Agreements and inadequate audit logs are frequent causes of penalties. In 2024 the U.S. Office for Civil Rights reported that since 2003 it had received over 374,321 HIPAA complaints and settled or penalized 152 cases for a total of $144,878,972. These enforcement numbers show the importance of getting essential controls right. Focus on those first and then expand coverage.
Conclusion
Mapping SOC 2 Controls Mapped To COBIT provides a way to connect control execution with governance and risk management. SOC 2 assesses whether controls exist and operate effectively; COBIT positions those controls within a strategic context. For companies selling to enterprise and healthcare buyers, this mapping brings clarity to how security, risk and governance intersect. It shows buyers and auditors that your security program is not just a document but a living system. It supports due‑diligence responses, shortens sales cycles and strengthens risk management. The alternative—stovepiped compliance efforts and inconsistent governance—delays deals and exposes the organization to breaches that cost millions. According to Thomson Reuters, the average cost of a data breach reached $4.88 million in 2024, a ten percent increase over the previous year. With penalties rising and buyer scrutiny increasing, investing in a mapped, operational program is not optional.
Konfirmity’s stance is straightforward: start with real security controls and end up with compliance. Through thousands of audits, we have learned that security that looks good in documents but fails under incident pressure is a liability. Build your control environment once, operate it daily, and map it across frameworks so that compliance follows naturally. That is the purpose of SOC 2 Controls Mapped To COBIT—not to check boxes, but to show that your organization’s security and governance are inseparable.
FAQs
1. Can SOC 2 be mapped to other frameworks besides COBIT?
Yes. The AICPA provides mapping guidance for SOC 2 to ISO 27001, NIST Cybersecurity Framework, NIST 800‑53, GDPR and other frameworks. Mapping allows organizations to reuse controls and evidence across multiple standards. In practice, SOC 2 Controls Mapped To COBIT is a recognized cross‑walk used by many teams.
2. Which version of COBIT should we use for mapping?
COBIT 2019 is the latest version. It contains forty governance and management objectives across five domains and provides design factors for customizing the framework. Many organizations still rely on COBIT 5 because the AICPA’s published mappings target that version. However, mapping from SOC 2 to COBIT 2019 is straightforward because the core domains remain the same. When deciding, consider which version your auditors and customers reference.
3. Does mapping SOC 2 controls to COBIT replace the need for an audit?
No. The mapping helps organize controls and evidence, but an official audit by a qualified CPA firm is still required to obtain SOC 2 attestation. Mapping supports audit readiness and may reduce effort, but it does not replace the independent assurance provided by auditors.





.svg)






.svg)
.svg)