Most enterprise buyers now request assurance artefacts before they purchase a service. Without operational security and continuous evidence, deals stall – even when teams think they’re ready on paper. The stakes are high. The average cost of a data breach fell 9% from US$4.88 million in 2024 to US$4.44 million in 2025, but in the United States breach costs rose to US$10.22 million because of increasing fines and expensive incident response In healthcare, the average breach still costs US$7.42 million. Enterprises respond by asking vendors for detailed controls and proof of privacy by design. A Data Protection Impact Assessment (DPIA) – once a compliance exercise for European regulators – has become a central part of trust conversations. This SOC 2 DPIA Guide explains how a strong DPIA supports sales, security reviews, and audits. It’s written for chief technology officers, chief information security officers, engineering leaders, compliance officers, and enterprise buyers who need clear, operational guidance on privacy risk management.
Konfirmity’s team has supported more than 6,000 audits over 25 years of combined technical experience, helping firms reach SOC 2 readiness in 4–5 months instead of the 6–18 months many companies spend alone. Our human-led, managed service reduces internal effort from 550–600 hours down to about 75 hours each year by running the program on your behalf. With that perspective, this SOC 2 DPIA Guide demystifies the process and shows how to turn privacy assessments into a tool for faster enterprise sales and cleaner audits.
Understanding DPIA in the Context of SOC 2
A DPIA is a process designed to help you systematically analyse, identify and minimise the data protection risks of a project or plan. The UK Information Commissioner’s Office (ICO) emphasises that a DPIA supports accountability, helps you assess and demonstrate compliance with data protection obligations, and does not have to eradicate all risk – it guides teams to determine whether risk is acceptable given the benefits. Under UK GDPR, failing to carry out a DPIA when required may lead to enforcement action and fines. Although the General Data Protection Regulation mandates DPIAs for high‑risk processing, the methodology is flexible and scalable.
How does a DPIA differ from a general risk assessment? The GDPR Local article clarifies that a DPIA is mandated under Article 35 for processing activities likely to result in a high risk to individuals’ rights; it is more prescriptive than a broader privacy impact assessment (PIA). PIAs can be adapted across jurisdictions and are not tied to a specific regulatory framework. In contrast, a DPIA has defined triggers (e.g., profiling, large‑scale sensitive data processing, systematic monitoring) and includes consultation with a data protection officer. A DPIA also differs from a generic information security risk assessment: NIST’s guidance calls for identifying threat sources, determining exploit probabilities, estimating the impact of each event, and combining likelihood and impact into a risk level. A DPIA overlays this technical analysis with a focus on the rights and freedoms of individuals, data minimisation, and lawful processing. It bridges information security and privacy law, making it a natural complement to SOC 2’s Trust Services Criteria (TSC).
SOC 2 examinations report on controls at a service organisation relevant to security, availability, processing integrity, confidentiality and privacy. A SOC 2 Type II report evaluates not only control design but also operating effectiveness over an observation period, typically 3–12 months. A DPIA fits within the Privacy criterion of SOC 2 by documenting how the organisation collects, uses, retains, discloses and disposes of personal information. It also relates to the Security and Confidentiality criteria by demonstrating risk analysis, access controls and encryption practices. SOC 2 auditors expect to see a clear description of data flows, risk identification, and mitigations. While SOC 2 does not explicitly require a DPIA, enterprise clients increasingly demand it during vendor due diligence. Conducting a DPIA helps service organisations align their privacy practices with SOC 2’s trust principles and provide evidence that stands up to audit scrutiny.
When and Why a DPIA Is Needed for SOC 2
Determining when to conduct a DPIA requires understanding triggers. Article 35 of the UK GDPR requires a DPIA where processing is likely to result in a high risk to individuals’ rights. The ICO lists three types of processing that always require a DPIA: systematic and extensive profiling that has legal or similar significant effects; large‑scale use of sensitive data; and systematic monitoring of a publicly accessible area. Additional indicators of likely high risk include evaluation or scoring, automated decision‑making, systematic monitoring, large‑scale data processing, matching datasets, vulnerable data subjects and innovative technology. To assess whether processing is likely to result in high risk, you must consider both the likelihood and severity of harm.
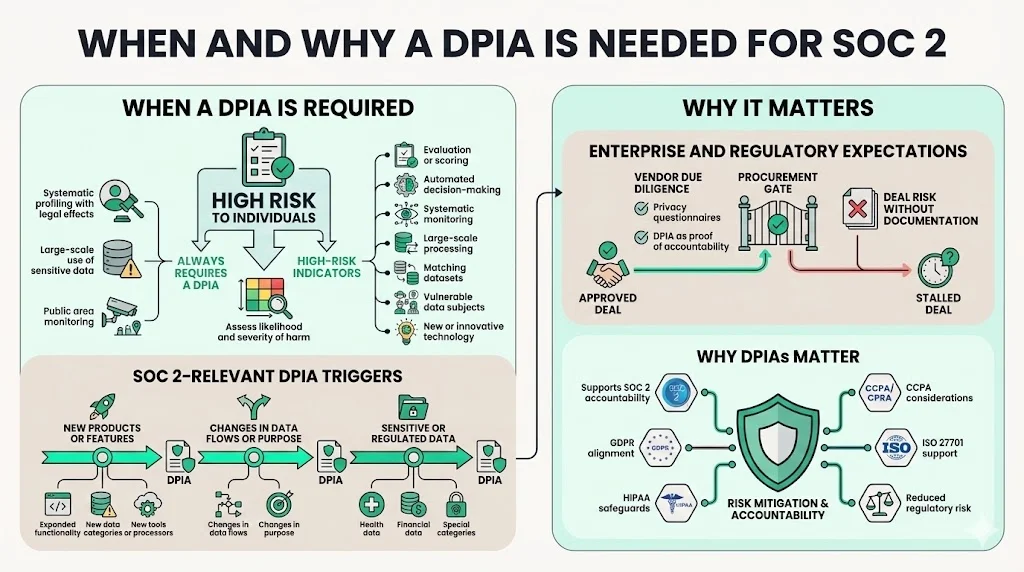
For SOC 2 purposes, the following events should trigger a DPIA:
- New products or features: launching a new application or expanding functionality can introduce new data flows or change how personal information is processed. When you develop a new feature for an enterprise client, you should perform a DPIA to document the purpose, data types and potential risks.
- Changes in data flows or processing purposes: if you start collecting new categories of data, send information to new analytics tools or use data for a purpose different from the original intent, it qualifies as a new processing operation. Article 35 requires a DPIA when new technology or processing is likely to result in high risk.
- Use of sensitive or regulated data: processing health data, financial records or other special categories significantly increases risk. The GDPR explicitly requires DPIAs for large‑scale use of sensitive data. HIPAA’s Security Rule also emphasises administrative, physical and technical safeguards to protect electronic protected health information (e‑PHI).
- Enterprise client expectations during vendor due diligence: many procurement teams now include a privacy and security addendum in their questionnaires. They want to see evidence of a DPIA to assess how you handle personal data. Without this documentation, deals can stall or go to competitors.
- Regulatory and contractual obligations: even when SOC 2 does not explicitly demand a DPIA, privacy regulators like the ICO emphasise that DPIAs support accountability and demonstrate compliance. Conducting a DPIA helps meet GDPR, HIPAA, CCPA or ISO 27701 requirements and reduces the chance of fines.
Core Components of a SOC 2–Aligned DPIA
A strong DPIA contains several elements that align with SOC 2 requirements:
- Description of data processing activities: outline what personal data is collected, by whom, how and for what purpose. Include system diagrams, data elements and processing steps.
- Purpose and business justification: explain why the data is needed, whether the purpose is compatible with the original collection purpose, and the legal basis (e.g., consent, contractual necessity). This addresses the purpose limitation principle.
- Data types, sources and storage locations: classify data into categories (e.g., identifiers, financial information, health records). Identify whether data comes directly from users, third parties or automated systems. Document where data is stored (e.g., cloud regions, on‑premise servers) and whether it is encrypted at rest.
- Data subjects involved: identify whose information is processed (customers, users, employees, vendors). Flag vulnerable groups (children, patients) that may elevate risk.
- Data retention and deletion practices: define how long each data type is retained, the disposal method and any legal requirements. This demonstrates compliance with the storage limitation principle.
- Legal and regulatory context: map applicable laws and frameworks (GDPR, CCPA, HIPAA, COPPA, ISO 27001, SOC 2 TSC) and highlight any cross‑border transfer considerations. DPIAs should mention standard contractual clauses or data transfer agreements when relevant.
- Stakeholder consultation: summarise feedback from internal stakeholders (security, legal, engineering, product, executive) and, where appropriate, external stakeholders or representatives of the data subjects.
- Outcome of the assessment: document identified risks, proposed mitigation measures, decisions about whether to proceed and any conditions for approval.
By structuring your DPIA around these components, you create a document that auditors and clients can follow easily. It also becomes a living record that supports evidence collection during SOC 2 audits.
Mapping Data Flows and Processing Activities
Mapping data flows is the backbone of a DPIA. You need to identify where data enters, moves and exits your systems. This includes:
- Entry points: user input forms, mobile app interfaces, APIs, file uploads or integrations with enterprise systems.
- Internal systems: databases, application servers, message queues, analytics pipelines, and logs. Document how data is transformed, enriched or aggregated. Avoiding the banned word for improved quality, we refer to these as the processing pipeline.
- External services: third‑party email providers, cloud storage platforms, payment processors, fraud detection tools, or marketing platforms. List each vendor, the data shared, and any privacy certifications (SOC 2, ISO 27001, PCI DSS) they hold.
- Exit points: data exported to clients, reports, dashboards or destruction after retention periods.
When mapping, consider cross‑border data flows. If you host data in multiple jurisdictions or rely on a content delivery network, you may trigger international transfer requirements. Document the legal mechanism for each transfer (e.g., standard contractual clauses). Common gaps flagged by enterprise security reviews include undocumented data flows to subcontractors, unclear retention periods, and lack of encryption for internal logs. A clear data flow diagram helps auditors trace evidence of control operation and reduces follow‑up questions.
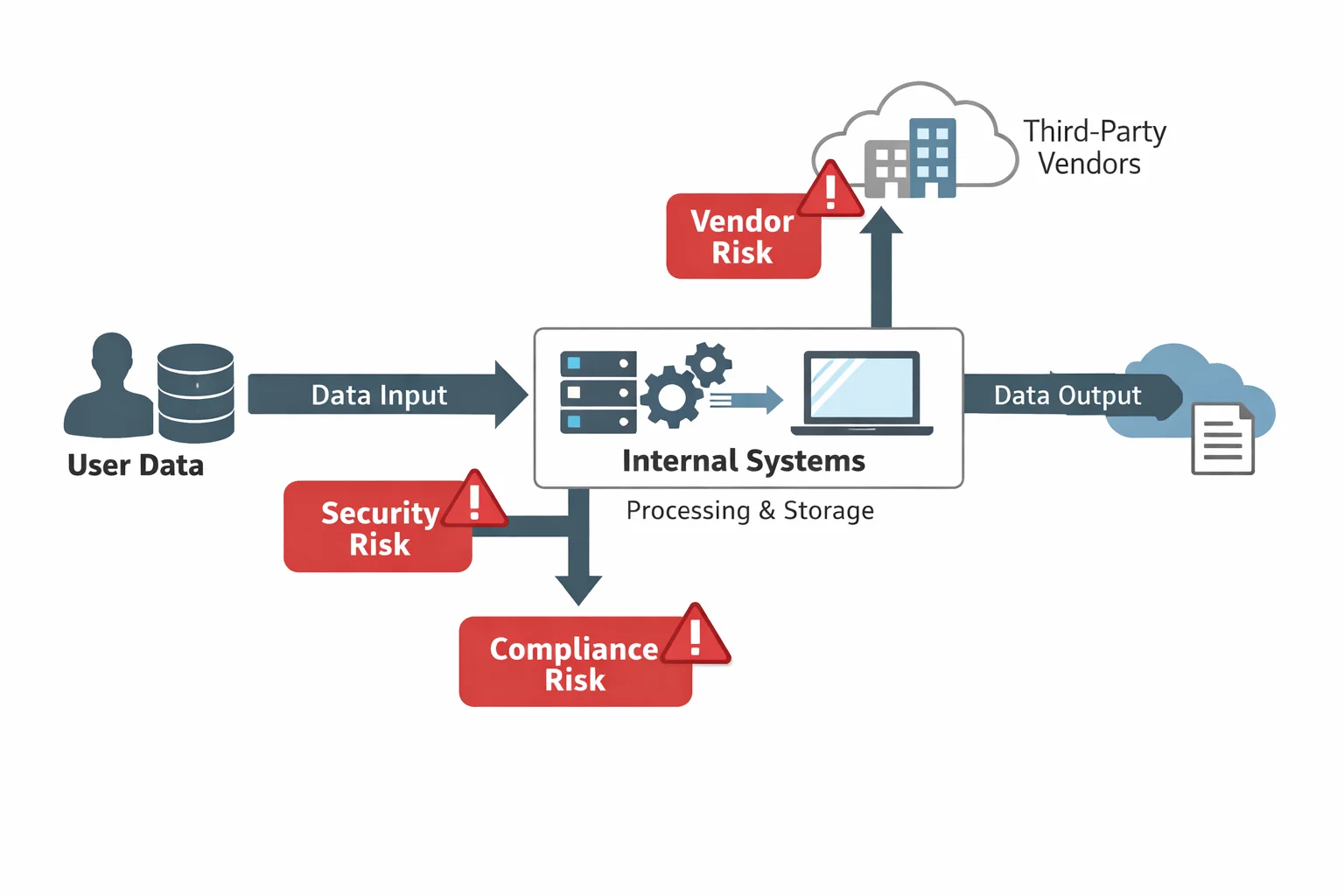
Figure: A conceptual diagram of data flows and risk points. The arrows show how user data enters internal systems, moves to third‑party vendors and exits to outputs. Red warning icons indicate potential security, compliance and vendor risks.
Risk Identification and Privacy Impact Analysis
After mapping your data flows, the next step is to identify potential privacy and security risks. NIST guidance recommends defining threat sources, identifying existing vulnerabilities, analysing the likelihood of each security event and determining the impact. The combination of likelihood and impact produces a risk score that helps prioritise mitigation. In a DPIA, you extend this technical assessment to consider harm to individuals’ rights, such as discrimination, identity theft, financial loss or psychological distress.
Common risk scenarios include:
- Unauthorised access: attackers or insiders gaining access to personal data because of weak authentication, excessive permissions or unpatched systems. ISO 27001 emphasises the confidentiality, integrity and availability triad and requires controls like multi‑factor authentication and access logging.
- Misuse or secondary use: data collected for one purpose being used for another without consent. For example, using user activity logs for marketing without proper notice.
- Data loss or corruption: accidental deletion, ransomware, hardware failure or natural disasters. Assess both the probability of occurrence and the impact on individuals and business operations.
- Cross‑border legal conflicts: transferring data to a country without adequate privacy protections may expose individuals to surveillance or regulatory risks.
To link privacy risks to broader risk management, use a risk matrix similar to ISO 27001’s approach: classify risks as high, medium or low; map them to business impact; and document the justification for the classification. Align the severity definitions with your enterprise risk appetite. For example, high‑risk events could lead to regulatory fines above US$1 million or significant brand damage. Low‑risk events may involve minor process deviations with no impact on individuals. Integrating privacy risks into your enterprise risk register encourages management oversight and ensures they are addressed alongside financial and operational risks.
Security Controls Evaluation
Once risks are identified, evaluate whether your existing controls adequately mitigate them. Mapping risks to controls helps demonstrate compliance with SOC 2, ISO 27001 and HIPAA requirements. Consider three categories of controls:
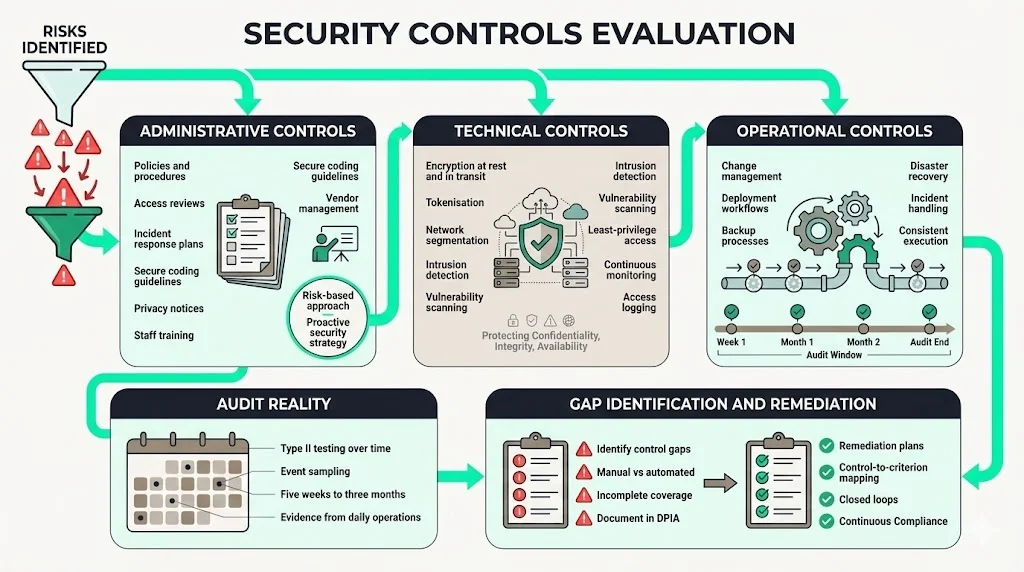
- Administrative controls: policies, procedures, and training. For example, access review processes, incident response plans, secure coding guidelines, vendor management policies and privacy notices. ISO 27001 emphasises a structured risk-based approach that shifts compliance from a checklist to a proactive security strategy.
- Technical controls: encryption, tokenisation, network segmentation, intrusion detection, vulnerability scanning, and least‑privilege configurations. The HIPAA Security Rule mandates appropriate administrative, physical and technical safeguards to protect the confidentiality, integrity and availability of electronic health information. In SOC 2, technical controls must support the TSC, such as encryption at rest and in transit, access logging and continuous monitoring.
- Operational controls: change management, deployment processes, backups, disaster recovery, and incident response. For a SOC 2 Type II report, auditors will test whether these processes operate consistently over the audit window. The actual SOC 2 audit typically takes five weeks to three months, during which auditors sample events from across the observation period. To pass, you must show that controls work every day, not just when you prepare documentation.
Identify gaps between current controls and enterprise expectations. For example, you may have encryption at rest but not for backups, or you might rely on manual access reviews instead of automated workflows. Document these gaps in your DPIA and plan remediation. Align each control with the relevant SOC 2 criterion to show auditors exactly how you meet requirements.
Third‑Party and Vendor Risk Considerations
Third‑party services are integral to modern platforms. They also introduce risks. A DPIA must evaluate subprocessors and service providers to determine whether they provide adequate privacy and security protections. Consider the following:
- Shared responsibility models: define where your responsibilities end and the vendors begin. For example, a cloud provider may secure the infrastructure, but you are responsible for access management and data encryption.
- Vendor due diligence: request SOC 2 reports, ISO 27001 certificates, penetration test reports and data processing addendums from vendors. For high‑risk vendors, review their DPIAs or privacy impact assessments.
- Data minimisation: share only the data needed for the service. For example, sending hashed identifiers instead of raw names to analytics providers.
- Contractual safeguards: include clauses on privacy, data breach notification, subcontracting, cross‑border transfers and audit rights.
By documenting vendor risks, you build a record that auditors and customers can review. Many enterprise clients ask for a list of subprocessors with associated risk ratings. Including this in your DPIA demonstrates maturity and reduces friction during procurement.
Mitigation Measures and Action Plans
After evaluating controls, select appropriate safeguards to reduce residual risks. Examples include:
- Enhancing technical protections: implement multi‑factor authentication, network segmentation, encryption for backups and continuous vulnerability scanning. Prioritise measures with the greatest risk‑reduction impact.
- Updating internal policies and procedures: formalise data retention schedules, incident response playbooks, privacy notices and training curricula. Ensure policies reflect current legal requirements and align with SOC 2 TSC.
- Assigning ownership and timelines: designate accountable owners for each mitigation. Set realistic due dates and track progress. Use dashboards or project management tools to provide visibility to executives and auditors.
- Tracking remediation progress: maintain a risk register that records the status of each action. During a SOC 2 audit, auditors may ask for evidence of remediation, such as change tickets, training records or updated configurations.
Mitigation is not a one‑time exercise. As new threats or business changes arise, the DPIA should be updated to reflect current risks and controls.
Documentation and Audit Readiness
DPIA documentation must be clear, current and accessible. Auditors expect to see evidence that the DPIA was conducted before the processing began and that it was approved by the appropriate stakeholders. Key points include:
- Evidence of reviews: minutes from DPIA review meetings, sign‑offs from security, legal and engineering, and version history showing updates.
- Link to controls and evidence: cross‑reference the DPIA with the control catalogue and evidence repository. For example, if a risk is mitigated by encryption, link to the configuration documentation.
- Readiness for SOC 2 audits: a strong DPIA reduces audit preparation time by showing that you understand data flows, risks and controls. Auditors often test controls across a 3, 6, 9 or 12 month window, so having a DPIA that covers the same period helps maintain consistency.
- Supporting enterprise security reviews: send the DPIA to potential customers under NDA. Many buyers evaluate vendor security posture as part of procurement. A thorough DPIA can accelerate approvals.
Governance and Ownership of the DPIA Process
A DPIA is not just a privacy office exercise. It requires involvement across the organisation:
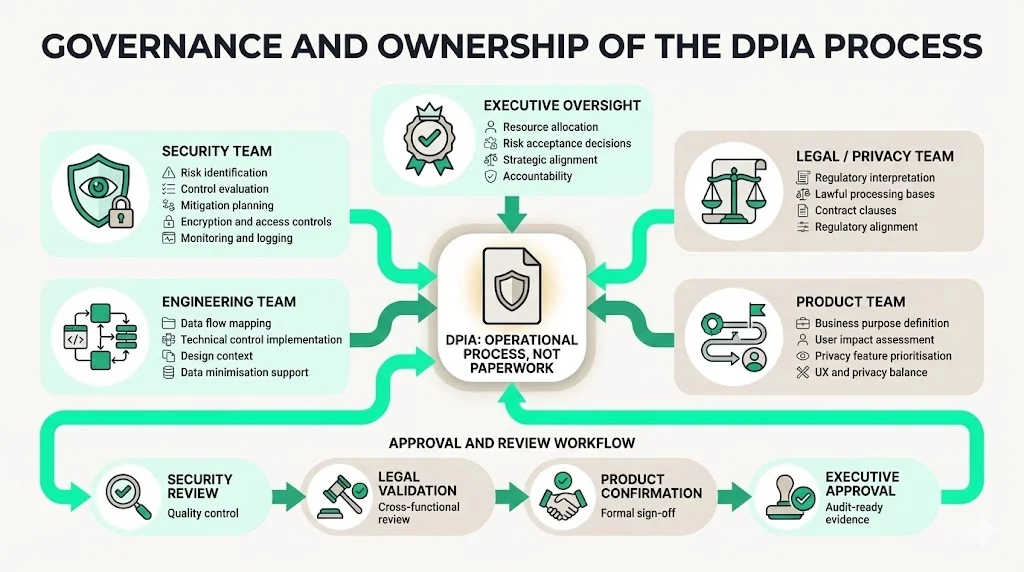
- Security team: leads risk identification, control evaluation and mitigation planning. Provides technical expertise on encryption, access management and monitoring.
- Legal or privacy team: interprets regulatory requirements, advises on lawful bases for processing and ensures contracts include appropriate clauses.
- Engineering team: maps data flows, implements technical controls and provides design context. Works with products to reduce data collection where possible.
- Product team: defines business purposes, assesses user impact and helps prioritise privacy features. Balances user experience with privacy constraints.
- Executive oversight: ensures that resources are allocated, risks are accepted or mitigated at the right stage, and that privacy aligns with business strategy. Accountability at the executive tier is essential; without it, DPIAs become paperwork rather than operational safeguards.
Internal review and approval workflows help maintain quality. For example, after drafting the DPIA, the security team reviews technical content, the legal team verifies compliance, the product team ensures accuracy of purpose statements and the executive sponsor approves. This sign‑off becomes evidence for auditors.
Maintaining and Updating DPIAs Over Time
DPIAs must be living documents. Events that require updates include:
- New processing operations: launching a new product, feature or integration.
- Significant changes to data flows: adopting a new analytics platform, migrating data to a different cloud region, or integrating with a third‑party service.
- New legal or contractual obligations: new laws (e.g., India’s Digital Personal Data Protection Act), client requirements or cross‑border transfer restrictions.
- Incidents or near misses: data breaches, security incidents or significant privacy complaints should trigger a DPIA review to see if risks were underestimated.
Growing companies benefit from setting review cycles. For example, conduct an annual DPIA review or whenever a material change occurs. Integrate DPIA updates into your change management process. When engineers propose a change that affects personal data, require them to flag a DPIA update. Avoid stale assessments; auditors and clients view outdated DPIAs as a red flag.
Common Mistakes Companies Make With DPIAs
- Treating DPIAs as one‑time paperwork: a DPIA is not a compliance tick‑box. It should inform design and operational decisions. Services that claim you can complete a SOC 2 DPIA in two weeks often deliver a document that fails under audit pressure.
- Ignoring vendor risks: failing to assess subcontractors can lead to blind spots. Many breaches occur through third parties. Include vendor risk analysis in the DPIA and keep it updated as vendors change.
- Weak linkage between risks and controls: describing risks without mapping them to controls results in vague remediation plans. Use your control catalogue to connect each risk to specific technical and operational measures.
- Poor documentation quality: incomplete descriptions, missing data flows, or out‑of‑date references make it hard for auditors to understand the assessment. Write in clear, concise language and avoid jargon.
Conclusion
A DPIA is more than a document – it is evidence that you operate with mature privacy practices. Conducting DPIAs proactively shows clients, auditors and regulators that you take data protection seriously and that your service will stand up to scrutiny. When integrated with SOC 2, a DPIA supports trust services criteria by documenting data flows, risks and controls. It also improves internal clarity: teams know why they collect data, how it is used and what safeguards exist. Firms that invest in DPIAs see fewer audit findings, faster buyer approvals and better alignment across security, legal and engineering.
At Konfirmity, we advocate a simple principle: start with security and arrive at compliance. A well‑executed DPIA is one piece of that puzzle. With our human‑led, managed service, we implement controls inside your stack, collect evidence year‑round and stand by you during audits. As this SOC 2 DPIA Guide has shown, privacy assessments aren’t just a regulatory obligation – they are tools for building trust, speeding sales cycles and protecting individuals. Build your program once, operate it every day and let compliance follow.
Frequently Asked Questions (FAQ)
1) What is a DPIA in SOC 2?
A DPIA is a structured assessment that maps data flows, identifies privacy and security risks, and selects controls to minimise harm. In SOC 2, it supports the Privacy, Confidentiality and Security criteria by demonstrating how personal data is collected, used and safeguarded. Unlike a general risk assessment, it focuses on individuals’ rights and lawful processing.
2) When is a DPIA required for SOC 2?
You should conduct a DPIA when launching new products or features, changing data flows or purposes, processing sensitive information or responding to enterprise client demands. The UK GDPR mandates DPIAs for high‑risk processing, and enterprise buyers increasingly expect them as part of vendor due diligence.
3) Who should be involved in a DPIA?
Security, legal, engineering and product teams all play a role. Executive oversight ensures accountability and resources. Cross‑team input ensures the DPIA reflects technical realities, legal obligations and business goals.
4) How does a DPIA support SOC 2 audits?
Auditors want evidence that you understand your data flows, have identified risks and implemented controls. A complete DPIA provides a roadmap that auditors can follow. It reduces follow‑up questions and speeds up the audit, which typically lasts five weeks to three months. It also signals to buyers that your program is mature.
5) How often should a DPIA be updated?
Update your DPIA whenever you introduce new processing operations, change data flows, adopt new regulations or experience incidents. At a minimum, review it annually. Growing companies should integrate DPIA updates into change management processes so assessments remain current and useful.





.svg)






.svg)
.svg)