Most enterprise buyers now expect credible evidence of information security before they sign a contract. Without operational security and continuous evidence, deals stall. Data protection and privacy governance are no longer optional add‑ons; they are part of a company’s ability to sell. This is particularly true when healthcare and financial customers need assurance that their vendors meet strict regulatory and contractual requirements. Service Organization Control 2 (SOC 2) attestation is one common way to provide that assurance. In this article we examine SOC 2 DPO responsibilities—how a dedicated data protection officer (DPO) role intersects with the SOC 2 framework and why it matters for companies selling into regulated industries.
SOC 2 is built around five trust service criteria—security, availability, processing integrity, confidentiality and privacy. The American Institute of Certified Public Accountants (AICPA) reports that every SOC 2 report must include the security criterion, while the other four are optional depending on the service. These criteria assure customers that systems are protected from unauthorized access and disruption, that data processing is accurate, that confidential information remains private, and that personal data is handled lawfully. A DPO helps meet these objectives by governing privacy practices, overseeing compliance, and acting as a point of accountability.
This piece is written for technical and business leaders—CTOs, CISOs, VPs of Engineering, security leads, and compliance officers—who want to understand the operational demands of SOC 2 and privacy governance. We will break down what a DPO does in a SOC 2 context, why the role is critical for enterprise sales, how to implement a program in 2026, and common pitfalls. The perspective comes from Konfirmity’s experience supporting more than six thousand audits over twenty‑five years, and the examples reflect real‑world control implementation rather than theory.
What Is a Data Protection Officer in a SOC 2 Context?
A DPO oversees data protection strategy, ensures that personal data is processed lawfully, and serves as a liaison to regulators and data subjects. Under the European General Data Protection Regulation (GDPR), DPOs must monitor compliance, provide guidance on data protection impact assessments, serve as a contact point for individuals, and cooperate with supervisory authorities. They are required to report directly to senior management and must be able to operate independently. While the GDPR is a European law, similar expectations exist under California’s Consumer Privacy Rights Act (CPRA) and India’s data protection law. Having a DPO is increasingly viewed as good practice even when not strictly mandated.
In the SOC 2 world, the role intersects with the trust service criteria. SOC 2 focuses on security and privacy controls, requiring management to design and operate controls that protect customer information. A DPO complements positions such as chief information security officer (CISO) and compliance managers by concentrating on privacy obligations. The DPO ensures that data subject rights, consent management, data minimization, and lawful processing are reflected in policies and that evidence exists to support those practices. SOC 2 auditors look for documentation of control design and operating effectiveness; a DPO helps maintain that documentation and ensures controls reflect current privacy rules.
It’s important to contrast this position with other positions. A CISO designs and runs the security program; a compliance manager coordinates audits and regulatory filings. The DPO’s remit is narrower but deeper in privacy. They interpret evolving regulations, advise on data flows, and guide risk assessments around personal data. In practice, SOC 2 compliance benefits when the DPO works closely with both the security and compliance teams.
Why SOC 2 Needs a Dedicated DPO
Enterprise clients increasingly ask vendors to demonstrate privacy accountability. Procurement questionnaires often include questions about privacy impact assessments, consent management, cross‑border transfers, and the presence of a DPO. A dedicated DPO signals that privacy is governed at a strategic scope and that someone is responsible for ensuring controls are designed and operated consistently. The DPO helps bridge the gap between regulatory expectations and the internal controls that underpin SOC 2 reports.
SOC 2 trust criteria cover more than security; they also include confidentiality and privacy. The privacy criterion ensures that personal data is collected, used, retained and disposed of in accordance with laws and commitments. A DPO interprets these requirements and translates them into policies and procedures. For example, they might oversee records of processing activities, ensure that consent mechanisms are documented, and confirm that data subject requests are tracked and resolved. Without this oversight, companies risk leaving gaps in their SOC 2 reports and undermining the trust they are trying to build.
Regulators are also increasing enforcement. The CMS Law GDPR enforcement tracker reports that regulators targeted large technology companies and issued a billion‑euro fine in 2023, followed by three significant fines in the hundreds of millions of euros in 2024. HIPAA enforcement activity escalated in 2024, with the U.S. Office for Civil Rights (OCR) reporting that 22 investigations led to settlements or civil monetary penalties. These actions show that data protection obligations carry real financial risk. Having a DPO who understands regulatory expectations and proactively manages compliance reduces the likelihood of violations and fines.
Lastly, enterprise buyers often evaluate vendor risk as part of procurement. They want assurance that vendors can handle personal data responsibly and meet contractual commitments. A dedicated DPO helps answer customer due‑diligence questionnaires, explains how controls match privacy laws, and demonstrates that privacy is not an afterthought. For vendors that operate in healthcare, financial services, or cross‑border contexts, a DPO is increasingly seen as essential.
Core Responsibilities of a SOC 2 DPO
The responsibilities of a DPO in a SOC 2 context correspond to regulatory obligations and the trust service criteria. These SOC 2 DPO responsibilities translate high‑level privacy expectations into concrete control activities. Below are the areas where a DPO provides the most value.
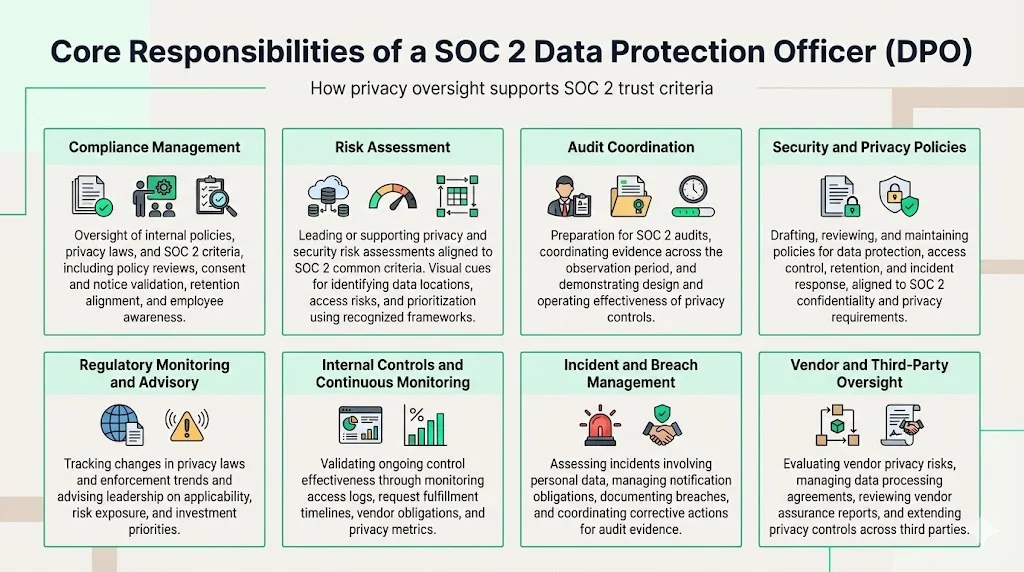
1) Compliance Management
As part of SOC 2 DPO responsibilities, the DPO oversees compliance with internal policies, privacy laws, and SOC 2 trust criteria. They monitor adherence to rules about data collection, use, storage and sharing. The European Commission states that DPOs must monitor organizational compliance, including through audits and training. In practice, this means reviewing policies to ensure they reflect current regulations, confirming that privacy notices and consents are up to date, and verifying that data retention schedules match contracts and laws. The DPO also runs awareness sessions to educate employees on their obligations and ensures that staff know how to handle personal data properly.
2) Risk Assessment
Risk assessments are central to SOC 2. A major component of SOC 2 DPO responsibilities is leading or supporting privacy and security risk assessments. The security criterion includes risk assessment as one of its common criteria (CC3). A DPO works with security and risk teams to perform privacy and security risk assessments. This includes cataloging data flows, identifying where personal data is stored and processed, and evaluating the risk of unauthorized access or disclosure. They use frameworks like NIST SP 800‑53 to categorize risks and assign priorities. In an enterprise sales context, risk assessments show customers that the vendor understands its risk exposure and has taken steps to mitigate it.
3) Audit Coordination
SOC 2 audits require extensive evidence collection. Another essential SOC 2 DPO responsibilities area involves coordinating audits. A DPO supports audit readiness by preparing documentation, coordinating responses to auditor requests, and ensuring that privacy controls are properly described. According to Vanta’s guidance on audit timelines, a SOC 2 Type 2 engagement includes a compliance observation window of three to twelve months followed by two to five weeks for the official audit and two to six weeks for report creation. Evidence must demonstrate both design and operating effectiveness over that window. The DPO helps compile evidence of privacy controls—such as records of data subject requests, consent logs and Data Processing Agreements—and works with auditors to explain how these controls meet the SOC 2 criteria.
4) Developing and Reviewing Security and Privacy Policies
Drafting and reviewing policies is integral to SOC 2 DPO responsibilities. An effective DPO drafts and maintains policies that govern data protection, access control, data retention and incident response. Policies must match SOC 2 criteria as well as broader regulations. For example, the confidentiality criterion requires that systems protect sensitive information from unauthorized exposure. The privacy criterion requires that personal data be handled in line with laws and commitments. The DPO ensures that policies address these requirements and that they are enforced across the organization. They also review policies regularly in light of changes in laws such as the GDPR, CPRA, and India’s data protection law.
5) Monitoring Laws and Advising on Regulatory Applicability
Staying current with laws is part of SOC 2 DPO responsibilities. Privacy law is evolving quickly. In 2025 regulators in the U.S., EU, India and other regions issued or updated laws affecting data transfers, consent and cross‑border processing. A DPO stays current with these changes and advises leadership on which laws apply to the organization. They monitor enforcement actions to gauge regulatory priorities. For example, the Abacode overview of IBM’s 2025 Cost of a Data Breach report notes that the global average cost of a breach fell from $4.88 million in 2024 to $4.44 million in 2025, but the U.S. average cost rose to $10.22 million. These numbers illustrate both progress and heightened risk. The DPO uses such data to contextualize risk and to propose investments in privacy controls.
6) Internal Controls and Continuous Monitoring
Implementing internal controls and continuous monitoring forms part of SOC 2 DPO responsibilities. SOC 2 Type 2 reports evaluate the operating effectiveness of controls over time. Continuous monitoring is essential. The DPO validates that controls around data handling and privacy remain effective. This includes checking access logs, verifying that data subject requests are fulfilled within statutory timelines, and ensuring that vendors meet contractual privacy obligations. They may work with security teams to establish dashboards that track privacy and security metrics, such as the number of open privacy incidents, average time to close Data Protection Impact Assessments (DPIAs), and completion rates for privacy training. By monitoring these metrics, the DPO can provide early warning when controls start to drift.
7) Incident Response and Breach Management
When incidents occur, the DPO ensures that privacy obligations are met. This includes confirming whether personal data was involved, assessing the severity, and determining whether regulators or affected individuals must be notified. The DPO collaborates with the security team to integrate privacy requirements into the incident response plan. They help define the documentation needed for incidents and ensure that breaches are recorded for SOC 2 audit evidence. If a breach triggers notification obligations, the DPO manages the communication with regulators and impacted customers and ensures that corrective actions are documented.
8) Vendor Management and Third‑Party Oversight
Service organizations seldom operate in isolation. They rely on cloud providers, payment processors and other vendors. Third‑party risk and supply‑chain breaches remain a major threat. The Abacode report notes that third‑party and supply chain compromises represented 15 % of all breaches in the IBM study. A DPO evaluates vendors for privacy risk, ensures that Data Processing Agreements include appropriate clauses, and verifies that vendors support SOC 2 controls. They may conduct due‑diligence questionnaires, review SOC reports from vendors and monitor their compliance. This helps ensure that the organization’s privacy controls extend into the supply chain.
How the DPO Works with Other Teams
No single role can achieve SOC 2 compliance alone. A DPO’s effectiveness depends on collaboration with other departments.
IT and Security Teams. The DPO collaborates with IT and security to incorporate privacy requirements into technical controls. This includes ensuring that encryption is applied to sensitive data, that access controls follow least‑privilege principles, and that logging captures required evidence. Coordination is essential when implementing vulnerability management and patching processes; the DPO may need to ensure that personal data is not exposed during remediation activities.
Legal and Compliance. Legal teams draft contracts, privacy notices and Data Processing Agreements. The DPO reviews these documents and provides input to ensure they reflect actual practices. Compliance teams coordinate audits and maintain evidence repositories. The DPO ensures that privacy evidence is collected and properly catalogued.
Human Resources. HR handles sensitive employee data and plays a role in training. The DPO collaborates with HR to design privacy training curricula and to ensure that employee data is processed lawfully.
Product and Engineering. Developers need to integrate privacy by design. The DPO advises on data minimization, purpose limitation and retention requirements. When building new features, the DPO participates in design reviews to ensure that personal data handling complies with regulations.
Executive Leadership. Because the DPO reports to senior management, they provide regular updates on compliance posture, risks and audit readiness. Senior leaders are responsible for SOC 2 compliance, but the DPO supports them by providing insight into privacy obligations and proposing corrective actions.
Practical Steps to Build an Effective SOC 2 DPO Program in 2026
Establishing a DPO function is not just about appointing someone; it involves designing a program that supports both privacy and SOC 2 objectives.
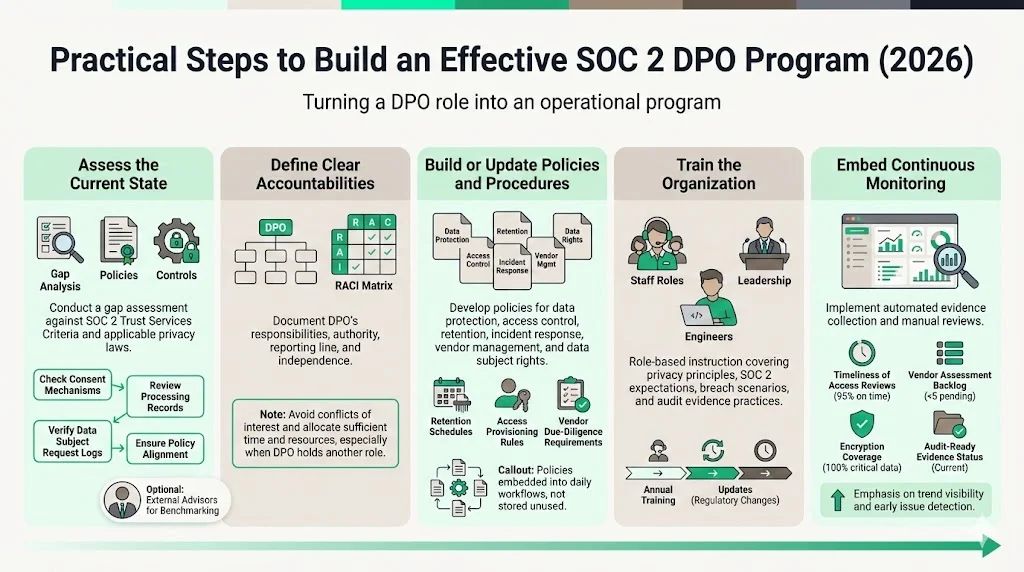
1) Assess Your Current State
Start with a gap analysis against the trust service criteria and relevant privacy laws. Identify which controls already address privacy and where new controls are needed. For example, confirm whether consent mechanisms exist, whether records of processing are maintained and whether data subject requests are logged. Review existing policies and compare them to SOC 2 requirements. Some organizations choose to engage an external advisor for this step to gain an objective view of gaps and to benchmark against peers.
2) Define Clear Accountabilities
Document the DPO’s responsibilities in the context of SOC 2. Clarify their authority, reporting line, and scope. Ensure that there is no conflict of interest—GDPR requires the DPO to operate independently. In smaller companies, the DPO may also hold another position, but they must be given sufficient time and resources to perform their duties. A RACI (Responsible–Accountable–Consulted–Informed) matrix can help clarify roles across security, legal, and product teams.
3) Build or Update Policies and Procedures
Develop a suite of policies covering data protection, access control, retention, incident response, vendor management and data subject rights. Ensure that policies reference both SOC 2 criteria and applicable privacy laws. For example, retention schedules should specify how long personal data is kept and when it is deleted. Access control policies should specify how privileges are assigned and revoked. Vendor management procedures should require Data Processing Agreements and third‑party risk assessments. Once drafted, policies must be communicated to employees and embedded into processes.
4) Train the Organization
Training is essential for embedding privacy practices. The DPO should develop role‑based instruction that covers privacy principles, SOC 2 requirements, and real examples of breaches. Front‑line staff need to know how to recognize data subject requests, respond to potential incidents, and follow proper data handling procedures. Engineers need to understand privacy by design and how to log evidence for audits. Instruction should be repeated at least annually and whenever there are regulatory updates.
5) Embed Continuous Monitoring
Implement tools and processes to monitor control effectiveness. This includes automated evidence collection for SOC 2 (such as access logs, change management records and vulnerability scans) and manual reviews (such as vendor risk assessments and DPIAs). Set up critical performance indicators such as time to complete access reviews, number of overdue vendor assessments, and percentage of systems with encryption enabled. Build dashboards so that leadership can see trends and take action before issues become findings during an audit.
Common Challenges and How to Overcome Them
1) Conflicts of interest. A common pitfall is assigning DPO duties to someone who also manages information systems or security operations. This may create a conflict because the DPO is supposed to evaluate and report on the effectiveness of controls. To mitigate this, separate DPO responsibilities from operational ownership and ensure that the DPO has direct access to leadership.
2) Keeping up with regulatory changes while meeting audit deadlines. Laws and guidance change rapidly. DPOs must allocate time for ongoing education and maintain a network of advisors. One tactic is to subscribe to regulatory alerts and to schedule quarterly policy reviews. Another is to adopt an information security management system (ISMS) that maps controls across frameworks (ISO 27001, SOC 2, HIPAA), enabling reuse of evidence and reducing the burden of constant updates.
3) Documenting evidence for SOC 2 efficiently. Evidence collection can consume hundreds of hours. Managed services like Konfirmity reduce that burden by automating evidence capture and providing dedicated experts. For example, in our experience, small and mid‑sized companies often spend 550–600 hours per year preparing for a SOC 2 Type 2 audit when they manage it internally. With a managed service, that effort can drop to roughly 75 hours per year because experts handle control design, evidence gathering, and auditor communication. The DPO plays a role by ensuring privacy evidence is collected as part of these workflows.
Case Example: A DPO’s Quarter Preparing for a SOC 2 Type II Audit
Consider a mid‑size healthcare technology company preparing for its first SOC 2 Type II report. Their products process electronic health information, so privacy and security requirements are high. The company has appointed a DPO who reports to the CFO. Here’s a snapshot of their activities over a three‑month observation window:
- Risk and control review. The DPO leads a risk assessment to map data flows, identify systems containing personal information and evaluate existing controls. Working with the security team, they confirm that encryption, access controls and monitoring are in place and that breach notification procedures meet HIPAA requirements.
- Policy refresh. Regulations have changed in several jurisdictions, so the DPO updates privacy notices, records of processing and cross‑border transfer clauses. They work with legal counsel to ensure that consent wording meets local requirements and that Data Processing Agreements with vendors are up to date.
- Evidence collection. Throughout the quarter, the DPO gathers evidence required for the SOC 2 report: logs of data subject requests, records of DPIAs, vendor assessment reports, training attendance logs and updated policies. They coordinate with engineers to retrieve access logs and with HR to obtain training records.
- Client engagement. Several enterprise customers ask about privacy practices. The DPO responds by sharing the SOC 2 Type I report, explaining how controls have been updated for the Type II observation period, and answering questions about data subject rights. They also provide excerpts from HIPAA policies and evidence of encryption for electronic health records.
- Incident readiness drill. To prepare for potential incidents, the DPO and security team conduct a tabletop drill simulating a ransomware attack. They test the incident response plan, verify that communication channels are in place for notifying regulators and customers, and document lessons learned.
- Audit coordination. When the auditor begins fieldwork, the DPO acts as the single point of contact for privacy matters. They provide documentation, answer questions about data flows and privacy controls, and ensure that any requests for additional evidence are addressed promptly.
This example shows how integrated the DPO’s work is with SOC 2 preparation. By focusing on privacy controls while coordinating with security and legal teams, the DPO helps the audit run smoothly and gives enterprise customers credible assurance.
Conclusion
Data protection is a business requirement, not just a legal one. Enterprise buyers ask for proof that vendors can protect personal information and meet regulatory obligations. SOC 2 provides a framework for demonstrating that commitment, but it only works when controls are real and continuously operated. A DPO plays a central role in matching privacy obligations with SOC 2 criteria, supporting compliance, and building trust. They oversee compliance management, coordinate risk assessments, prepare for audits, develop policies, monitor regulatory changes, and work across teams to embed privacy into everyday operations. The benefits go past passing audits; organizations with a strong DPO program are better prepared for regulatory scrutiny, client due‑diligence and the inevitable security incidents.
As regulators impose higher fines—three major GDPR fines in the hundreds of millions were levied in 2024and OCR enforcement actions spiked to 22 settlements in 2024—investment in privacy governance makes sense. Data breaches remain expensive; IBM’s 2025 report recorded a global average breach cost of $4.44 million and a U.S. average of $10.22 million. Companies that integrate SOC 2 DPO responsibilities into their security programs protect themselves from these costs and demonstrate to customers that they take privacy seriously. The message is clear: build controls inside your systems, operate them daily, and let compliance follow.
Frequently Asked Questions
1) What are the core duties of a DPO?
A DPO monitors compliance with privacy laws and internal policies, advises on privacy matters, conducts privacy impact assessments, trains staff, and serves as a liaison to regulators and data subjects. In a SOC 2 context, these duties extend to coordinating audit evidence and harmonizing privacy controls with trust service criteria.
2) Is the DPO role full time?
It depends on the complexity of the organization. Large enterprises with international footprints and multiple product lines often require a full‑time DPO. Smaller firms may outsource the role or combine it with other functions, but they must ensure that the person has sufficient independence and authority. Regardless of whether the role is full time, the responsibilities must be clearly documented and supported.
3) What are the main tasks of a data protection officer?
The main tasks include monitoring compliance, advising on privacy laws, coordinating audits, conducting data protection impact assessments, supporting incident response, and maintaining documentation of data processing activities. They also train staff and work with legal and security teams to embed privacy into processes.
4) Who is responsible for SOC 2?
Organizational leadership is responsible for SOC 2 compliance. The DPO supports privacy and evidence readiness, but SOC 2 spans security, compliance and executive functions. Leaders must allocate resources to implement controls, maintain evidence and engage auditors. A managed service like Konfirmity provides experts who execute these tasks, allowing internal teams to focus on product and service delivery.





.svg)






.svg)
.svg)