Most organizations pursuing SOC 2 compliance focus engineering resources on infrastructure hardening—firewalls, encryption, vulnerability scanning. This creates a fundamental blind spot: when SOC 2 auditors arrive, they're not just interested in IT infrastructure but want to understand the human fabric of the organization—where HR becomes a strategic compliance partner. Enterprise clients scrutinizing your SOC 2 report examine how you manage employee access to their data, verify workforce backgrounds, enforce confidentiality obligations, and revoke permissions when personnel depart.
SOC 2 compliance is built around five Trust Services Criteria (Security, Availability, Confidentiality, Processing Integrity, and Privacy), with Security as the only mandatory criterion for all SOC 2 audits. Within this framework, HR-controlled processes—onboarding, offboarding, background verification, role-based permissions, training programs, and access management—directly impact your ability to demonstrate control design and operating effectiveness. Organizations selling to enterprise clients face heightened scrutiny in these areas because vendor risk assessments specifically target employee lifecycle controls as indicators of data security maturity.
This guide provides practical steps, concrete examples, templates, and implementation workflows for HR security controls within the SOC 2 context. You'll understand which HR processes auditors examine, how to document evidence of operating effectiveness, and how to integrate compliance requirements into existing operations without manufacturing additional workload. The approach targets B2B, SaaS, and service organizations where enterprise sales depend on demonstrating credible security operations—not performative compliance.
What Are SOC 2 HR Security Controls?
SOC 2 controls are policies, procedures, and technical measures used to protect systems and data, reducing the risk of security incidents, mistakes, or unauthorized access. HR security controls represent the subset of these safeguards that address the employee and contractor lifecycle: how personnel gain access to systems and data, how that access is monitored and modified, and how it's terminated when employment ends.
The SOC 2 framework includes 5 Trust Services Criteria made up of 64 individual requirements. While Security is the only Trust Services Criteria required for every SOC 2 audit, with other criteria added to report scope if the organization chooses, most enterprise-selling companies pursue Security-focused audits initially. For a SOC 2 report covering the security criteria, organizations can expect about 60-80 controls, with Security alone potentially including nearly 100 controls such as password security, employee onboarding, training, physical access controls, background checks, security training, incident response, and multifactor authentication.

HR intersects with SOC 2 controls at multiple points. HR is responsible for developing and enforcing policies that impact data security, with auditors reviewing policies on data access, confidentiality, incident response, and acceptable use. Specifically, HR functions control:
- Employee lifecycle management: Provisioning access during onboarding, modifying permissions during role changes, revoking access during offboarding
- Data confidentiality: Enforcing confidentiality agreements, classifying employee-accessible data, restricting access to customer information
- User authentication protocols: Coordinating with IT to implement password policies, MFA requirements, credential management for employees and vendors
- Background verification: Conducting role-appropriate background checks that satisfy due diligence requirements
- Training and awareness: Delivering security training, phishing simulations, policy acknowledgments
- Vendor and contractor management: Onboarding third-party personnel with system access, managing contractor access duration, enforcing vendor security requirements
- Incident response: Participating in investigations of employee data misuse, policy violations, or HR system breaches
For companies selling to enterprise clients, auditors dig deep into how organizations manage human risks, with HR directly impacting SOC 2 compliance in several critical areas including effective onboarding and precise access management for safeguarding sensitive data. Enterprise procurement teams specifically request evidence of background check policies, access revocation procedures, and employee training completion rates—areas where HR documentation directly supports or undermines SOC 2 attestation.
The HR Control Landscape: What Needs to Be Covered
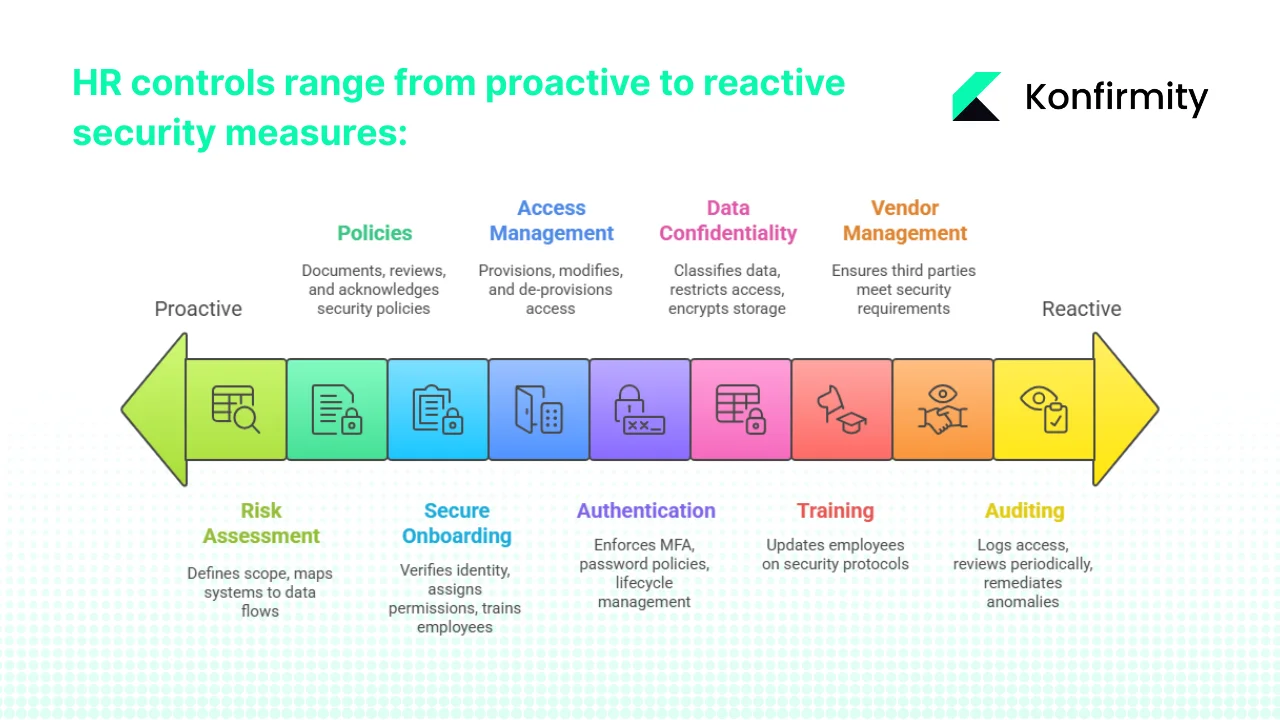
1) Risk Assessment & Scope Definition
HR's first obligation in SOC 2 compliance involves identifying which HR-managed processes and systems handle data falling within audit scope. This means mapping HR systems (HRIS platforms, payroll systems, onboarding tools, performance management software) to data flows and privileged access points.
Example: An organization's HRIS contains employee personally identifiable information (PII), payroll data, and role assignments that determine system permissions. If HRIS also tracks which employees have access to customer data environments, it becomes a control point for SOC 2 purposes. HR must document: which personnel have administrative access to the HRIS, how that access is logged, who reviews those logs, and how often access permissions are audited.
HR coordinates with compliance and IT teams to define scope boundaries: which employee data is in-scope, which vendor or contractor roles require background checks, which third-party staffing relationships introduce access to customer data. This scoping exercise determines the extent of HR controls that auditors will examine.
2) Policies & Procedures
SOC 2 audits require documented, reviewed, and employee-acknowledged policies. All SOC 2 examinations involve auditor review of organizational policies, which must be documented, formally reviewed, and accepted by employees, with each policy supporting an element of overall security and customer data handling.
HR-relevant policies include:
- Employment policy: Defines onboarding requirements, background check standards, confidentiality obligations, acceptable use expectations
- Access management policy: Specifies how HR and IT coordinate user provisioning, role-based permission assignments, access review schedules, and de-provisioning workflows
- Offboarding policy: Details termination procedures, asset return requirements, access revocation timelines, exit interview protocols
- Confidentiality and NDA requirements: Establishes employee obligations regarding customer data, intellectual property, and confidential business information
- Acceptable use policy: Governs employee use of company systems, devices, networks, and data
Example: A documented employee access management policy defines that HR submits new hire information to IT within 24 hours of start date confirmation, IT provisions accounts within 48 hours based on role templates, HR verifies training completion before access activation, and access logs are retained for audit purposes.
Template suggestion: Create a policy checklist matrix covering: policy name, owner (HR vs. IT vs. Security), review frequency (annual, biannual), approval authority, employee acknowledgment mechanism, and version control tracking.
3) Secure Onboarding & Background Checks
Onboarding refers to the ongoing process of transforming a new hire into an integrated employee, and from a security perspective, this process determines initial access permissions and establishes security awareness. Secure onboarding ensures that identity verification, background checks, confidentiality agreements, role-based permission assignment, and security training occur before system access is granted.
Background checks satisfy due diligence requirements and demonstrate that organizations verify workforce integrity before granting access to customer data. SOC 2 auditors examine whether background check policies exist, whether they're consistently applied, and whether verification is documented and retained.
Example: Onboarding workflow for a new software engineer:
- HR conducts background check (criminal, employment verification) before start date
- HR issues confidentiality agreement and acceptable use policy for signature on day one
- HR notifies IT of role assignment and required system access based on role template
- IT creates user accounts with role-based permissions (least privilege)
- HR assigns mandatory security awareness training with completion deadline
- IT enables MFA enrollment as prerequisite for system access
- HR documents onboarding checklist completion and files evidence for audit
Template: Onboarding checklist capturing: background check completion date, NDA signature, role-based permissions requested, training assigned, MFA enrolled, access granted date, logging enabled, onboarding sign-off by HR and IT.
4) Employee Access Management & Role-Based Permissions
Employee access management encompasses provisioning (granting access), modification (adjusting permissions during role changes), and de-provisioning (revoking access upon termination). HR oversees the onboarding process, ensuring new hires have appropriate access levels, which is vital for maintaining the principle of least privilege—a key concept in SOC 2.
Role-based permissions link job functions to specific system access rights, ensuring that employees access only the data and systems necessary for their responsibilities. HR defines roles in coordination with IT and security teams, mapping role templates to permission sets.
Example: A customer success manager role requires access to the CRM, support ticketing system, and customer communication platform—but not to production infrastructure, source code repositories, or financial systems. HR uses a role matrix to define this access template. When a customer success manager is promoted to team lead, HR initiates an access review and modification request to IT, adding team management permissions while maintaining least-privilege principles.
When an employee leaves, HR must coordinate with IT to promptly revoke access, as delays can leave systems vulnerable to unauthorized access. This coordination requires documented workflows, automated notifications, and verification procedures.
Template: Access matrix documenting [Role → Required Systems → Permission Level → Review Frequency] plus an offboarding checklist covering: termination date notification, IT access revocation request, verification of account disablement, hardware return confirmation, access log retention.
5) User Authentication & Password Policies
User authentication controls—including multi-factor authentication, single sign-on, password complexity requirements, and credential lifecycle management—fall under IT implementation but require HR coordination for policy enforcement and employee compliance. HR ensures that employees understand authentication requirements, complete MFA enrollment during onboarding, and follow password rotation schedules.
Example: A new vendor contractor completes onboarding, receives temporary credentials, must complete MFA setup within 24 hours, perform initial password change meeting complexity requirements (minimum 14 characters, alphanumeric with special characters), and complete authentication policy training acknowledging credential protection obligations.
Template: Password policy summary sheet distributed by HR to new hires and contractors, covering: minimum password requirements, MFA enrollment procedure, password manager recommendations, credential sharing prohibitions, incident reporting for suspected credential compromise.
6) Data Confidentiality & Confidential Information Handling
Data confidentiality controls ensure that employee data, customer data accessed by employees, and vendor personnel data are protected through classification, access restriction, encryption, and secure storage. HR must classify data handled within HR systems, restrict access based on need-to-know principles, and ensure proper storage in encrypted, access-logged environments.
Example: HR maintains a spreadsheet of sensitive employee compensation data. Controls include: file encryption at rest, storage on access-controlled network drive (not local desktop), access limited to compensation team members only, activity logging enabled, quarterly access reviews conducted, and retention policy enforced. When sharing compensation data with finance for budgeting, HR uses secure file transfer with recipient authentication rather than email attachment.
Template: Confidentiality agreement template for employees and contractors, plus a data classification matrix for HR systems categorizing data as Public, Internal, Confidential, or Restricted—with corresponding handling requirements documented for each classification level.
7) Training & Awareness
Regularly updating employees on security protocols reduces the risk of breaches due to human error. HR-led training programs ensure that all employees and contractors understand their role in maintaining security controls and SOC 2 compliance. Training topics include: security awareness fundamentals, phishing recognition, data handling procedures, acceptable use policies, incident reporting obligations, and confidentiality requirements.
Organizations should provide regular security awareness training covering phishing, social engineering, password security, and data handling best practices, using interactive training methods, real-world examples, and simulated phishing exercises to make training engaging and effective, with tailored programs addressing specific security challenges relevant to different departments.
Example: Annual security training program includes: onboarding security module completed within first week of employment, quarterly phishing simulation exercises, annual policy review and acknowledgment, role-specific training for personnel with elevated access (e.g., developers receive secure coding training, support staff receive customer data protection training). HR tracks completion rates, documents quiz results, and remediates non-compliance through follow-up and escalation.
Template: Training schedule matrix documenting [Training Type → Audience → Frequency → Delivery Method → Completion Tracking → Acknowledgment Form], plus sample quiz/acknowledgment form requiring employee signature confirming training completion and policy understanding.
8) Vendor Management
HR frequently engages contractors, third-party staffing agencies, and consultants who require system access to perform services. Vendor management controls ensure that these third parties meet security requirements, undergo appropriate background checks, sign confidentiality agreements, receive time-limited access, and are offboarded when contracts end.
Example: A staffing agency contractor is granted access for a 3-month project. HR ensures: contract includes security and confidentiality clauses, staffing agency provides background check verification, contractor signs company NDA, HR requests role-appropriate access from IT with defined end date, access is logged and reviewed monthly, and HR schedules automatic access revocation notification 48 hours before contract expiration. Upon contract completion, HR verifies access termination and asset return.
Template: Vendor security checklist for HR and procurement, covering: contract security requirements (SOC 2 attestation, background check, confidentiality clause), vendor onboarding procedures, access approval workflow, periodic access review schedule, offboarding requirements, and vendor risk assessment criteria.
9) Auditing and Logging & Continuous Monitoring
SOC 2 controls focus on ensuring companies regularly review who has access to critical IT infrastructure, with requirements to log these reviews and take actions to resolve any access issues discovered during review. HR must ensure that access to HR systems, privileged administrative actions, and vendor/contractor accounts are logged, reviewed periodically, and remediated when anomalies are identified.
Continuous monitoring involves ongoing review of HR-related access logs, identification of dormant accounts, detection of role changes requiring permission adjustments, and verification of policy adherence. User access reviews should be conducted at least annually, with quarterly reviews recommended for greater risk reduction.
Example: HR system access logs are reviewed quarterly. The review identifies: dormant vendor accounts inactive for 90+ days (flagged for revocation), administrative access granted outside standard procedures (investigated and documented), employees with access mismatched to current role (corrected), and access modification requests lacking proper approval (remediated with policy reinforcement).
Template: Audit review table documenting [Review Date → Reviewer → Systems Reviewed → Findings → Remediation Actions → Completion Date], plus monitoring schedule specifying quarterly access reviews, monthly dormant account checks, and annual comprehensive audit.
10) Incident Response
HR participates in incident response when employee or contractor data misuse occurs, when HR system breaches are detected, or when policy violations require investigation. HR integrates with the security incident process by: receiving incident notifications, conducting investigations (including employee interviews and access log review), coordinating termination procedures when warranted, implementing remedial training, and preserving evidence for auditor review.
Example: A contractor's account is compromised and used to export customer data. Incident response involves: IT detects anomalous activity and triggers incident protocol, security team isolates compromised account, HR coordinates with security to terminate contractor access immediately, HR and security conduct joint investigation reviewing access logs and interviewing contractor, HR documents incident timeline and remediation actions, security notifies auditor per SOC 2 requirements, and HR implements enhanced contractor access controls to prevent recurrence.
Template: HR incident response run-sheet documenting [Incident Type → Notification Procedure → HR Actions Required → Communication Protocol → Documentation Requirements → Evidence Preservation → Post-Incident Review], tailored for HR-related security events including policy violations, data misuse, and HR system breaches.
Step-by-Step Implementation for Busy HR / Security Teams
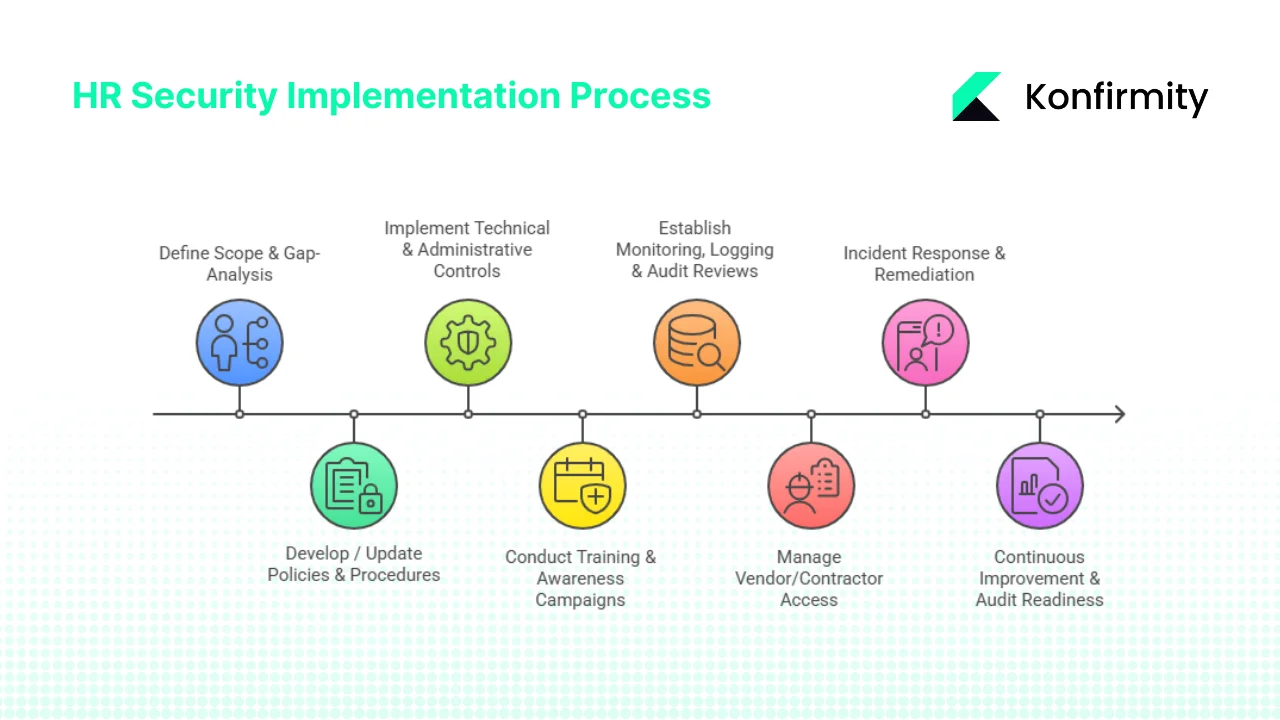
Step 1: Define Scope & Gap-Analysis
Map HR systems, processes, and vendor relationships to identify which functions handle sensitive data or control access to critical systems. Conduct gap-analysis comparing existing HR controls against SOC 2 requirements.
Gap-analysis template: Create matrix listing [SOC 2 Requirement → Current HR Control → Evidence Available → Gap Identified → Remediation Priority → Owner → Target Completion Date]. Focus initially on high-impact gaps: missing background check policy, undocumented offboarding procedures, absence of access review process, lack of training tracking.
Typically, a SOC 2 Type 2 audit that covers security will address the suitability of design and operating effectiveness of 80 controls on average. Organizations should identify which of these 60-100 controls involve HR functions and prioritize gap remediation accordingly.
Step 2: Develop / Update Policies & Procedures
Based on gap-analysis findings, create or revise HR security policies covering employee access management, onboarding/offboarding, vendor access, training requirements, and confidentiality. Ensure policies are approved by appropriate stakeholders (HR leadership, security, legal), communicated to employees through formal acknowledgment process, and included in training curricula.
Documented policies satisfy auditor evidence requirements for every SOC 2 examination. Policies must demonstrate both design (what you commit to doing) and operating effectiveness (evidence you actually do it consistently).
Step 3: Implement Technical & Administrative Controls
Coordinate HR processes with IT and security teams to implement role-based permissions, user authentication requirements, password policies, access revocation workflows, and vendor contract security clauses. Use templates provided in previous sections: access matrix, password policy sheet, vendor checklist, onboarding/offboarding checklists.
Real-world example: New hire onboarding control implementation requires: HR completes background check before start date (administrative control), HR issues NDA and policy acknowledgments on day one (administrative control), HR submits role-based access request to IT via ticketing system (technical control), IT provisions accounts using pre-defined role templates (technical control), HR assigns training with automated completion tracking (technical control), access is logged and reviewed quarterly (monitoring control).
Step 4: Conduct Training & Awareness Campaigns
Schedule onboarding security training for all employees and vendors, covering confidentiality obligations, access management expectations, incident reporting procedures, and SOC 2 awareness. Implement quiz/acknowledgment forms to document training completion. Establish quarterly refresher training cycles and monitor completion rates, remediating non-compliance through escalation procedures.
Example: Quarterly training cycle includes: automated training assignment via LMS, two-week completion deadline, automated reminder emails at 7-day and 1-day before deadline, completion tracking dashboard reviewed by HR weekly, non-completion escalated to direct managers, and persistent non-compliance addressed through performance management.
Step 5: Establish Monitoring, Logging & Audit Reviews
Configure automated and manual logging of HR system access, vendor account activity, administrative actions, and access modification events. Schedule periodic audits (quarterly recommended) for user access reviews, vendor status verification, and offboarding completeness validation.
Example: HR system audit log configuration captures: user login attempts (successful and failed), administrative permission changes, access to sensitive employee data modules, bulk data exports, and account provisioning/de-provisioning events. Logs are fed into a centralized SIEM or audit tool, with the security team reviewing anomalies and HR conducting quarterly comprehensive access reviews comparing active accounts against current employee roster.
Step 6: Manage Vendor/Contractor Access
Implement vendor management checklist ensuring contracts include security requirements (background check verification, confidentiality clauses, optional SOC 2 attestation for high-risk vendors), vendor onboarding follows documented procedures, access is time-limited with defined expiration, periodic reviews occur, and offboarding procedures execute when contracts end.
Example: Staffing contractor granted system access for 6-month engagement requires: HR verifies staffing agency background check policy, contractor signs NDA, access request specifies 6-month expiration date, HR schedules calendar reminder for access review at 5-month mark and termination at 6-month mark, monthly access reviews verify contractor account remains appropriate, and automated notification triggers IT to revoke access on contract end date.
Step 7: Incident Response & Remediation
HR participates in incident response by establishing clear roles defining actions when HR-system breaches or employee misuse occurs. Document incident actions, preserve evidence (access logs, email communications, policy violation records), and update controls when incidents reveal gaps.
Example: Terminated employee's credentials weren't revoked, allowing unauthorized access for 48 hours post-termination. Incident triggers: immediate access revocation, security investigation reviewing accessed data, HR audit of offboarding checklist identifying process failure, policy update requiring IT to disable accounts within 4 hours of termination notification, implementation of automated offboarding workflow, and quarterly audit of offboarding completeness.
Step 8: Continuous Improvement & Audit Readiness
Track metrics including training completion percentages, dormant account ratios, access review findings, vendor compliance rates, and offboarding completion timeliness. Use metrics for continuous monitoring and audit readiness preparation.
SOC 2 Type 2 controls evaluate the extent to which controls function as designed, with audits lasting 3-12 months. Type 2 audits cover design and operating effectiveness over an observation period (typically 6-12 months), emphasizing continuous control operation rather than point-in-time snapshots.
Audit readiness preparation includes: assembling management assertion document, compiling system description covering HR controls, creating control matrix mapping HR controls to SOC 2 criteria, organizing evidence documentation (policies, training records, access review logs, background check documentation, offboarding verification), and conducting pre-audit internal control testing.
Examples & Mini-Templates
Onboarding Checklist (HR):
- Background check completed: [Date]
- NDA signed: [Date]
- Acceptable use policy acknowledged: [Date]
- Role-based access request submitted to IT: [Date]
- Training assigned: [Date]
- MFA enrolled: [Date]
- Access granted and logged: [Date]
- Onboarding complete: [HR Signature] [Date]
Offboarding Checklist (HR):
- Termination notice submitted to IT: [Date/Time]
- Access revocation request: [Date/Time]
- IT confirmation of account disablement: [Date/Time]
- Hardware return verified: [Date]
- Final paycheck processed: [Date]
- Exit interview completed: [Date]
- Access logs retained: [Location]
- Offboarding complete: [HR Signature] [Date]
Access Matrix (Role → Permissions):
Vendor Security Checklist (HR/Procurement):
- Contract includes security requirements: [Yes/No]
- Background check verification received: [Yes/No]
- NDA signed: [Date]
- Access expiration date defined: [Date]
- Monthly access review scheduled: [Yes/No]
- Offboarding procedure documented: [Yes/No]
Training Schedule + Acknowledgement:
- Onboarding security training: Week 1 of employment
- Phishing simulation: Quarterly
- Annual policy review: Annual, within 30 days of anniversary
- Role-specific training: Upon role change
Training Acknowledgement: "I confirm completion of [Training Name] on [Date] and understand my security obligations."
Employee Signature: _________________ Date: _________
Audit/Log Review Schedule:
Incident Response Run-Sheet (HR Focus):
- Incident notification received: [Document time, source, description]
- HR immediate actions: [Account suspension, access review, evidence preservation]
- Investigation coordination: [Security team involvement, manager notification]
- Documentation: [Access logs, emails, policy violations, witness statements]
- Remediation: [Policy update, training, access revocation, termination if warranted]
- Auditor notification: [If material to SOC 2, notify within defined timeframe]
- Post-incident review: [Root cause analysis, control improvement]
Password/Authentication Policy Summary Sheet:
- Minimum password length: 14 characters
- Complexity requirements: Uppercase, lowercase, numbers, special characters
- MFA required for: All system access
- Password rotation: 90 days
- Password manager: Recommended [Tool Name]
- Credential sharing: Prohibited
- Incident reporting: Report suspected compromise to security@company.com immediately
Data Classification/Confidentiality Handling Matrix (HR Systems):
Common Pitfalls & How Busy Teams Can Avoid Them
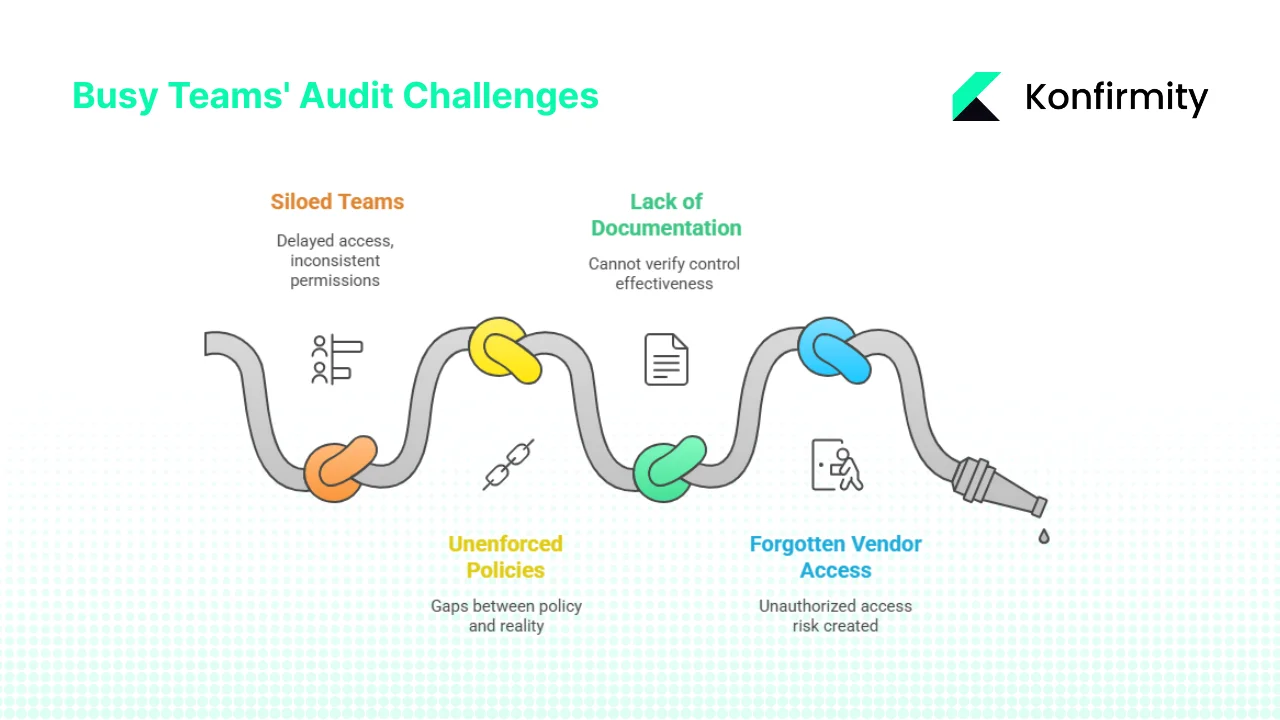
Pitfall #1: HR and IT work in silos
Consequence: Delayed access revocations, uncontrolled vendor access, inconsistent permission assignments, audit findings.
Solution: Establish cross-functional workflows with defined handoffs. HR owns termination notification and offboarding checklist initiation; IT owns technical access revocation and verification; Security reviews logs. Implement automated ticketing system linking HR actions to IT tasks, with SLA-defined response times (e.g., access revocation within 4 hours of HR termination notification). Conduct monthly HR-IT-Security coordination meetings reviewing offboarding completeness, access review findings, and process improvements.
Pitfall #2: Policies exist but no enforcement or monitoring
Consequence: Auditors identify gaps between policy statements and operational reality, resulting in control design vs. operating effectiveness deficiencies.
Solution: Implement monitoring mechanisms for every policy. Background check policy requires documented verification for 100% of new hires—track completion rate monthly. Training policy mandates annual completion—automate tracking dashboard and escalate non-compliance. Access review policy specifies quarterly reviews—calendar-schedule reviews with documented findings. Auditors require evidence of consistent policy operation over the observation period (6-12 months for Type 2), not merely policy documents.
Pitfall #3: Lack of documentation
Consequence: Auditors cannot verify control operating effectiveness without documentation. Missing evidence results in audit qualifications or failed controls.
Solution: Document everything: onboarding checklists with completion dates and signatures, offboarding verification records, training completion reports, access review findings, background check confirmations, vendor contract security clauses, incident response actions. Establish centralized evidence repository (secure file share, GRC platform, HRIS with audit trail capabilities) where documentation is systematically filed by control and date. Implement "if it wasn't documented, it didn't happen" operating principle for audit-relevant activities.
Pitfall #4: Vendor/contractor access forgotten after term ends
Consequence: Dormant accounts create unauthorized access risk, violate least-privilege principles, and represent audit control failures.
Solution: Implement vendor access lifecycle management with defined expiration dates for all contractor accounts. Calendar-schedule access reviews 30 days before contract expiration. Automate notifications to HR and IT 48 hours before expiration requiring extension justification or termination. Conduct monthly dormant account audits identifying accounts inactive 90+ days for investigation and revocation. Require vendor contracts to specify access duration, permitted systems, and offboarding procedures.
Practical tips:
- Assign clear responsibilities: HR owns employee lifecycle documentation and policy enforcement; IT owns technical implementation and access provisioning; Security owns monitoring and audit coordination. Document responsibilities in RACI matrix.
- Automate where possible: Use HRIS systems with audit trail capabilities, automated training assignment and tracking, ticketing systems for access requests, calendar reminders for periodic reviews, and SIEM tools for access log monitoring.
- Use checklists and reminders: Onboarding/offboarding checklists prevent missed steps. Calendar reminders ensure periodic reviews occur. Automated workflows reduce human error.
- Build audit-ready evidence as you go: Don't scramble during audit preparation. File evidence systematically: monthly access review reports stored in audit evidence folder, training completion exports generated quarterly, background check documentation filed during onboarding, policy acknowledgments collected via HRIS.
How This Supports Sales To Enterprise Clients
Enterprise buyers conduct vendor security assessments before contract execution, frequently requiring SOC 2 reports as procurement prerequisites. The SOC 2 report demonstrates your controls—including HR security controls—through independent auditor attestation. Specifically, enterprise procurement and security teams examine:
- Background check policies: Verification that personnel accessing their data have undergone appropriate screening
- Access management procedures: Evidence that you provision, review, and revoke access systematically using least-privilege principles
- Training completion rates: Confirmation that your workforce understands security obligations and data handling requirements
- Offboarding timeliness: Demonstration that terminated personnel lose access promptly, reducing insider threat risk
- Vendor management controls: Assurance that third-party contractors follow the same security standards as employees
Implementing HR-specific controls reduces vendor risk perception, strengthens your position in enterprise procurement security reviews, and shortens due-diligence cycles. Organizations with documented, consistently-operated HR security controls answer vendor questionnaires efficiently, provide evidence on demand, and accelerate contract execution.
When presenting your security posture to enterprise prospects, reference HR controls explicitly in vendor security decks: "Our SOC 2 Type 2 report covers employee onboarding with background verification, role-based access controls audited quarterly, mandatory security training with 100% completion rates, and offboarding procedures ensuring access revocation within 4 hours of termination." These specifics build trust more effectively than generic "we take security seriously" statements.
Conclusion
HR security controls are vital for SOC 2 compliance, especially for the mandatory Security criterion, addressing employee lifecycle, access, background checks, training, vendor management, and incident response. The implementation roadmap includes: scope definition/gap analysis, policy development, control implementation (HR-IT coordination), training, monitoring/audits, vendor management, incident response participation, and continuous improvement. Use provided templates (onboarding/offboarding checklists, access matrices, etc.) to operationalize controls. Start with a quick gap assessment (e.g., background checks, offboarding consistency, quarterly access reviews, training tracking) and schedule the first access review to begin building audit evidence. Organizations with genuine HR security controls protect data, meet client expectations, and achieve natural SOC 2 compliance.
FAQ Section
Q1: What are the SOC 2 controls for security?
The Security criterion ensures that systems are protected against unauthorized access, both physical and logical, and is the foundational trust service principle that must be included in every SOC 2 report. The Security category includes nine Common Criteria (CC1–CC9), which apply across all Trust Services Criteria. These controls address: control environment and integrity (CC1), communication and information (CC2), risk assessment and mitigation (CC3), monitoring activities (CC4), control activities (CC5), logical and physical access security (CC6), system operations (CC7), change management (CC8), and risk mitigation (CC9). Common security controls include password rules, multi-factor authentication, logical access security measures, access permissions, and steps for onboarding and offboarding employees.
Q2: What is SOC 2 compliance in HR?
SOC 2 compliance in HR refers to how Human Resources functions support the organization's SOC 2 audit by managing employee and contractor lifecycle controls. Human Resources manages employee onboarding and offboarding, and oversees training on security protocols. Specifically, HR ensures: background checks are conducted before system access is granted, confidentiality agreements and policy acknowledgments are signed, role-based access requests are coordinated with IT, security training is assigned and completion tracked, access reviews are conducted periodically, vendor and contractor security requirements are enforced, offboarding procedures are executed promptly with access revocation verification, and audit evidence is documented and retained. HR's controls directly impact the organization's ability to demonstrate SOC 2 control design and operating effectiveness, particularly regarding employee access management, data confidentiality, training and awareness, and incident response—all critical components of the Security criterion required in every SOC 2 audit.
Q3: How many controls are there in SOC 2 Type 2?
The number of SOC 2 controls depends on scope (which Trust Services Criteria are included) and organizational complexity. There is no fixed number, with most audits including 60 to 100 controls depending on which trust services principles are included and system complexity, noting that Security is always required and adding more criteria increases the number of controls. For a SOC 2 report covering the security criteria, organizations can expect about 60-80 controls. Cloud-only firms typically implement around 60 controls, while more complex organizations with multiple Trust Services Criteria may require 100+ controls. Security alone can include nearly 100 controls, like password security, employee onboarding, training, physical access controls, background checks, security training, incident response, and multifactor authentication. Organizations work with auditors to define their specific control set based on business model, systems in scope, and selected Trust Services Criteria. Unlike prescriptive frameworks with fixed control lists, SOC 2 allows flexibility to design controls appropriate to organizational risk profile and operational model.
Q4: Which is the mandatory control in a SOC 2 audit?
Security is the mandatory criterion in every SOC 2 audit—the only Trust Service Criteria required for all SOC 2 reports. Security is the only Trust Services Criteria required for every SOC 2 audit, with other criteria added to report scope if the organization chooses but not required to achieve SOC 2 compliance. The Security criterion encompasses nine Common Criteria (CC1-CC9) addressing control environment, communication, risk assessment, monitoring, control activities, access controls, system operations, change management, and risk mitigation. While Security is mandatory, the other four Trust Services Criteria—Availability, Confidentiality, Processing Integrity, and Privacy—are optional and included based on business needs and customer requirements. Most organizations pursuing initial SOC 2 certification begin with Security-only audits, adding additional criteria in subsequent audit cycles as business requirements evolve or enterprise clients specifically request expanded scope.





.svg)






.svg)
.svg)