Most enterprise and healthcare buyers now ask to see security assurance artifacts before procurement. Without operational security and continuous evidence, deals stall—even when teams think they’re ready on paper. Recent data underlines why neglecting physical security can be costly. IBM’s Cost of a Data Breach report pegged the global average breach cost at $4.88 million in 2024, a 10% rise over 2023. Secureframe’s 2026 breach analysis shows that 2025’s global average dropped slightly to $4.44 million, yet U.S. breaches shot up to $10.22 million, an all‑time high.
These numbers don’t account for operational shutdowns such as the 2021 OVHcloud datacentre fire that took 3.6 million websites offline, causing hundreds of millions of dollars in losses. While organizations obsess over encryption and network hardening, a single unauthorized visitor or environmental hazard can undo those efforts. This guide tackles SOC 2 Physical Security Controls head‑on, showing how to protect facilities, devices, and evidence streams so that your audit narrative reflects real security.
What are physical security controls in SOC 2?
In the SOC 2 context, physical security controls are measures that prevent unauthorized individuals from entering premises, accessing systems, damaging equipment, or stealing media. These controls include facility access control systems, surveillance cameras, security policies, barriers, environmental monitoring, visitor management, keys and locks, and device protection. They complement digital measures by addressing risks such as tailgating, theft, fire, flooding, tampering, and environmental failure. For service organizations that operate in co‑location facilities or rely on cloud providers, understanding these controls is crucial because CC6.4 requires restricting access to facilities and sensitive assets.
What SOC 2 says about physical security
SOC 2’s Trust Services Criteria require that systems are protected against unauthorized access in both logical and physical realms. The common criteria (CC) break this down. CC6 governs logical and physical access controls. CC6.1 demands secure architectures for protecting systems; CC6.2 requires proper user provisioning and revocation; CC6.4 focuses on physical access restrictions to facilities and backup media; CC6.5 addresses protection of physical assets until data is irretrievable; and CC6.6–6.8 cover boundary protection, data transmission, and software integrity. AICPA notes that the best cybersecurity is useless if someone can walk in and plug a device into a server.
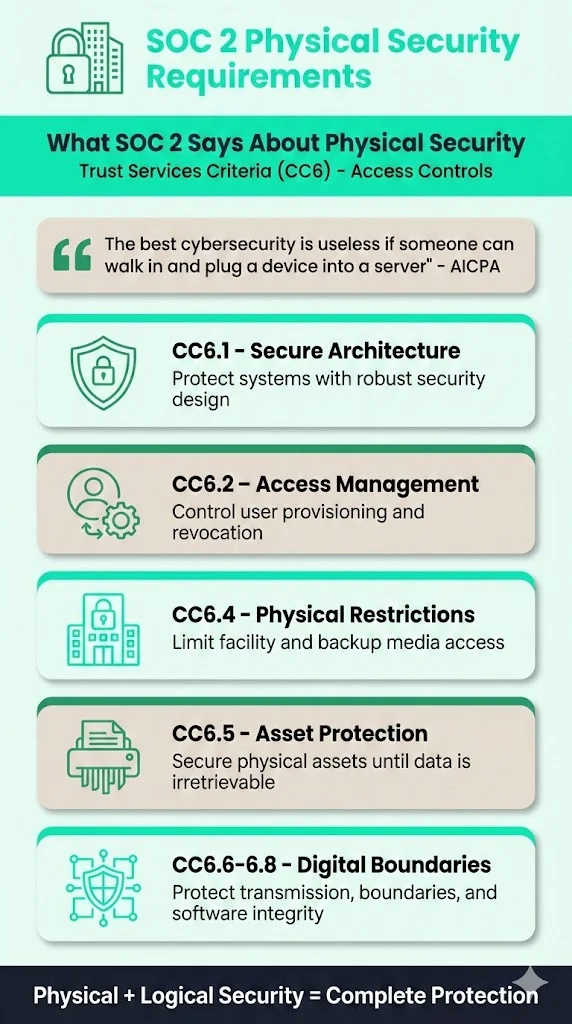
Other frameworks echo SOC 2’s emphasis. NIST 800‑53 mandates access controls, video surveillance, intrusion detection, and environmental monitoring. HIPAA’s Security Rule requires facility access controls with contingency operations, visitor validation, and maintenance records. ISO 27001:2022 dedicates 14 controls to physical security, covering secure perimeters, secure cabling, equipment maintenance, and supporting utilities. These cross‑framework parallels reinforce that physical safeguards aren’t optional; they are integral to a defensible security program.
Physical security within CC6 (CC6.1, CC6.2, CC6.4, and CC6.6)
CC6.1 requires organizations to implement logical access security software and infrastructure to protect information assets, including inventorying data, restricting logical access, authenticating users, and segmenting networks. CC6.2 expands on this by mandating formal user registration and authorization processes, along with timely removal of access. CC6.4 explicitly states that entities must restrict physical access to facilities, backup media, and sensitive locations to authorized personnel. It recognises that cloud‑hosted systems may carve out some physical controls, but organizations still need visitor logs, access reviews, and assurance over the data center’s controls. CC6.6 addresses boundary protection, requiring additional authentication for external access and defining firewall rules to block unauthorized traffic.
These criteria illustrate how physical and logical safeguards intertwine. An access badge system might interface with your identity provider to disable entry when employment ends (CC6.2). A biometric reader at a server room supports CC6.4 by ensuring only authorized individuals enter. A firewall complements CC6.6 by controlling network access, but it cannot stop an intruder with a stolen key. Effective SOC 2 programs implement SOC 2 Physical Security Controls alongside digital measures so there are no gaps in the control chain.
Why physical security is often overlooked—but critical
Organizations focused on cloud services sometimes assume that because their data resides in hyperscale environments, physical risks are negligible. Yet physical breaches can trigger the same or worse outcomes as cyber attacks. The 2021 OVHcloud fire damaged four buildings and knocked out millions of websites. The IBM/Ponemon study shows that data breach costs grew to $4.88 million in 2024, driven by regulatory fines and response costs. Physical vulnerabilities—such as unauthorized access, theft, or environmental hazards—exacerbate these costs and lead to operational downtime. The physical security market is expected to grow from $2.1 billion in 2023 to $3.6 billion by 2029, reflecting industry recognition that physical threats are rising.
Security101’s overview notes that physical controls are often overlooked because digital threats dominate headlines. However, physical breaches can cause reputational damage, data integrity issues, and financial losses. HIPAA warns that unauthorized facility access can lead to theft of electronic protected health information, requiring policies for contingency operations, visitor validation, and maintenance records. URM Consulting points out that physical threats can be as significant as cyber threats, and effective physical controls build a stronger security culture. The takeaway is clear: ignoring SOC 2 Physical Security Controls leaves an organization exposed to consequences that cannot be mitigated by software alone.
Key physical security control domains for SOC 2
The control domains below map each physical safeguard to SOC 2 requirements, with examples to show how teams implement them. SOC 2 Physical Security Controls appear as domain headers and within examples to reinforce alignment.

1. Access control (facility & points of entry)
Access control determines who is allowed inside a facility and to which areas. Methods include badges, biometric scanners, role‑based access lists, and visitor passes. Under CC6.1 and CC6.2, organizations must verify identities and authorize users before granting access, then revoke access when employment ends. For CC6.4, access to server rooms and backup storage should be limited to personnel who need it.
Example: at Konfirmity, we install badge readers at office entrances and server rooms; access rights are managed through the HR system so that termination in HR automatically disables the badge. Logs are retained for audit, and quarterly reviews verify that only authorized roles have physical access.
2. Surveillance systems
Cameras, motion sensors, and video analytics detect and deter unauthorized physical access. Surveillance provides an audit trail to support SOC 2 evidence. Security101 lists surveillance cameras as a key measure for CC6.4.
Example: a SaaS provider uses CCTV covering building entrances and server racks. Footage is retained for 90 days, and access to video is restricted. Monthly checks confirm cameras are functioning. These SOC 2 Physical Security Controls help auditors verify that no unauthorized entries occurred.
3. Electronic security measures
Electronic locks, badge readers, alarm panels, and access logging systems provide granular control and evidence. Logs must integrate with identity management to show who entered and when. DesignCS notes that video surveillance and alarm systems complement sign‑in logs and visitor escorts.
Example: a company implements an access control system that logs every door event. Logs feed into the governance, risk, and compliance (GRC) platform. When an employee leaves, their badge is automatically disabled, and logs demonstrate enforcement.
4. Entry restrictions
Entry restrictions ensure that certain areas are only accessible under defined conditions—such as escorted entry, time‑based access, or role‑based approval. HIPAA calls for policies that limit access to facilities while permitting authorized entry during contingency operations.
Example: contractors working on the network infrastructure can only access the server room during business hours and must be escorted by a full‑time employee. Visitors sign in, wear temporary badges, and stay in designated zones. These restrictions, documented in access logs, support SOC 2 Physical Security Controls requirements.
5. Security policies
A written physical security policy codifies roles, responsibilities, and procedures. ISO 27001 emphasises clear desk policies, secure perimeters, and equipment maintenance. The policy should define asset ownership, review cycles, enforcement actions, and exceptions.
Example: Konfirmity’s template includes sections on badge issuance, visitor management, device protection, environmental controls, and incident response. The policy is reviewed annually and upon major facility changes.
6. Physical barriers
Physical barriers like fences, turnstiles, locked doors, cages, and server cabinets provide the first line of defence. Security101 highlights locks, fences, and gates as fundamental measures.
Example: the server racks are enclosed within cages requiring separate keys. Only designated administrators have keys, recorded in a key inventory. Exterior doors use steel frames and reinforced locks. Cages deter unauthorized access and support the SOC 2 Physical Security Controls narrative.
7. Alarm systems
Intrusion alarms detect forced entry, tampering, and environmental anomalies. Alarm events must trigger notifications to a security operations center and be recorded for evidence. Security101 mentions alarm systems as “extra credit” for CC6.4.
Example: a facility uses door sensors and glass‑break detectors connected to a monitoring service. When a door is forced open, the system alerts security and starts incident response. Logs show the time of alarm, response actions, and resolution.
8. Visitor management
Visitor management involves logging external visitors, issuing badges, verifying identification, and ensuring escorting. HIPAA’s facility access and validation procedures require visitor control. DesignCS notes the need for sign‑in processes, visitor logs, and escorts.
Example: reception uses a digital kiosk that captures visitor names, the host, arrival time, and a photo. Visitors receive color‑coded badges. After departure, logs are retained for one year. This process satisfies auditors that physical access is controlled.
9. Locks and keys
Even with electronic systems, physical keys remain common. Key management includes issuance, inventory, auditing, and retrieval.
Example: an organization issues master keys only to facilities managers. A key inventory lists each key holder, and quarterly audits ensure keys are returned when roles change. Key‑cards used with electronic locks also require deactivation upon termination. These measures align with SOC 2 Physical Security Controls and CC6.4’s emphasis on restricting physical access.
10. Environmental controls
Environmental controls mitigate hazards such as fire, smoke, overheating, water leaks, and power failures. DataCenterDynamics notes that NIST 800‑53 demands environmental monitoring.
Example: server rooms use HVAC systems with temperature sensors and humidity controls. Water‑leak sensors under raised floors alert facilities when leaks occur. Fire suppression systems use inert gas rather than sprinklers to avoid equipment damage. Uninterruptible power supplies (UPS) maintain uptime during power outages. Monitoring logs provide evidence during SOC 2 audits.
11. Risk assessment
Conducting physical risk assessments identifies threats—unauthorised entry, theft, natural disasters, sabotage—and guides control selection. Security101 recommends regular risk assessments to uncover vulnerabilities and implement appropriate controls.
Example: a risk workshop maps high‑risk areas like server rooms, reception, and storage closets. For each area, the team assesses likelihood and impact, then implements specific controls (e.g., cameras, locks, alarms). The assessment results feed into CC3 (risk assessment) and CC6 requirements. Organisations should update assessments annually or when adding new facilities.
12. Security audits
Regular physical security audits verify that controls operate as intended. Audits may involve reviewing access logs, visitor logs, key inventories, barrier inspections, and surveillance footage. Evidence from these audits supports the SOC 2 Type II opinion because auditors want to see controls functioning over time.
Example: a quarterly audit shows that badge logs match HR rosters, keys are accounted for, and all cameras are operational. Any discrepancies trigger remediation.
13. Incident response
Physical incidents—unauthorised entry, theft, equipment damage, environmental events—must tie into the broader incident response plan. CC7 of SOC 2 covers system operations and incident handling.
Example: when an alarm triggers, security guards respond, gather evidence, and file an incident report. The root cause is analysed, and remediation actions (e.g., repair a broken door) are tracked. Incident records are stored for the observation period to prove control effectiveness. Integrating physical incidents into digital incident response ensures that the organization treats all security events holistically.
14. Security training
Staff awareness is a critical defence against tailgating, lost keys, and insecure habits. Regular training ensures employees understand the physical security policy and know how to handle visitors. URM Consulting highlights that physical controls support a strong security culture.
Example: every quarter, employees complete a training module covering badge usage, reporting suspicious behavior, and proper device handling. Posters remind staff to challenge unknown individuals. Attendance is tracked and forms part of the audit evidence. These measures reinforce SOC 2 Physical Security Controls and reduce human error.
15. Device protection
Even in the cloud era, physical devices remain entry points. Controls include locking laptops to desks, securing desktops with cable locks, restricting USB ports, tagging assets, and maintaining inventory. DesignCS notes that physical controls also apply to mobile devices, requiring encryption and mobile device management to protect data.
Example: remote employees receive laptops with full‑disk encryption and tethering cables. When not in use, laptops must be stored in lockable drawers. Asset tags help track devices, and an asset management system records issuance and returns. These steps protect against device theft and align with CC6.5’s requirement to secure physical assets until data is wiped.
Step‑by‑step implementation for busy teams
The following roadmap helps organizations implement SOC 2 Physical Security Controls systematically. At each step, align actions with CC6 and the broader Trust Services Criteria while collecting evidence for auditors.
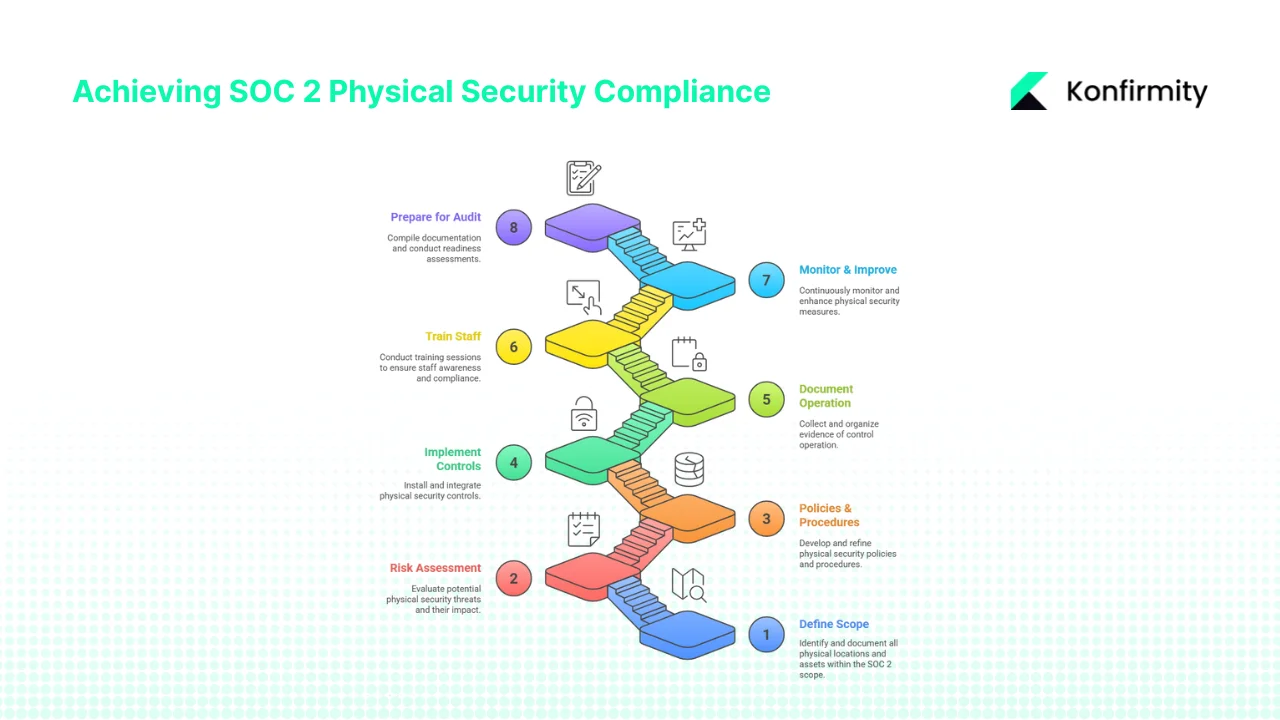
Step 1: Define the scope
Identify all physical locations, facilities, and devices that fall within your SOC 2 scope. Include headquarters, branch offices, co‑location data centers, cloud data center responsibilities, backup sites, and remote devices. Document the boundaries of each facility and the critical assets inside. For cloud‑hosted systems, determine which physical controls the provider covers (review their SOC 2 report) and which you must implement. Scoping ensures that controls and evidence align with what auditors will evaluate.
Step 2: Perform a physical security risk assessment
Use a template to list each location, asset, and associated threats. Rate risks by likelihood and impact. For example, leaving the server room door unlocked overnight might be a medium‑impact, high‑likelihood risk. Identify controls that mitigate each risk (locks, cameras, alarms) and assign owners. Integrate this assessment into your broader risk register to satisfy CC3.
Step 3: Define policies and procedures
Draft or refine a physical security policy that covers access control, visitor management, device protection, environmental controls, key management, and incident response. Create procedures for requesting access, issuing badges and keys, escorting visitors, and handling lost devices. Use checklists to ensure consistency. Align policies with HIPAA, NIST, and ISO 27001 requirements where applicable. Make sure the policy clearly states who owns each control and how often it is reviewed.
Step 4: Implement the controls
Map the control domains described earlier to concrete actions. Install surveillance cameras and ensure coverage of all access points. Deploy electronic locks, badge readers, and biometric scanners. Set up alarms for doors and windows. Build a visitor management system. Secure devices with locks and asset tagging. For remote employees, implement secure storage and shipping for laptops. Assign owners, budgets, and timelines for each control. Integrate systems with HR or identity management for automatic provisioning and de‑provisioning.
Step 5: Document control operation and gather evidence
SOC 2 Type II reports require evidence that controls operated over an observation period (often three to twelve months). For physical security, collect access logs, visitor logs, alarm events, maintenance records, key inventories, camera footage access logs, and training records. Document when each control was tested and what the result was. For example, a monthly review of CCTV logs might note which personnel viewed footage and confirm no unexplained access. A quarterly key inventory audit checks that all issued keys are accounted for. Keep evidence organised in an evidence tracker with dates, control domains, and remediation actions.
Step 6: Train staff and enforce awareness
Roll out initial training and periodic refreshers on physical security policies. Use internal intranet, meetings, or short modules to remind employees about tailgating prevention, badge usage, and visitor escorting. Provide guidelines for remote workers on storing and securing devices. Collect attendance logs and quiz results as evidence. Encourage a speak‑up culture where staff report suspicious behaviour or lost keys immediately.
Step 7: Monitor, audit, review, and improve
Establish a schedule for monitoring and auditing physical controls. Set key performance indicators (KPIs) such as the number of unauthorized entry attempts detected, overdue key returns, or training completion rates. Conduct barrier inspections, review access logs, test alarm systems, and ensure cameras are functioning. Annually, refresh the risk assessment and update controls to address new threats or facility changes. Continuous improvement demonstrates maturity to auditors and enterprise buyers.
Step 8: Prepare for the SOC 2 audit
Compile a documentation package that includes a system description of your physical environment, a control matrix mapping each control domain to relevant criteria (CC6.x, CC3.x, CC7.x), and an evidence folder with logs and reports. Draft management assertions that describe how physical controls operate and support the security objective. Conduct a readiness assessment to identify gaps before the formal audit. With SOC 2 Physical Security Controls well documented and evidenced, auditors can verify compliance without protracted remediation.
Real‑world examples
- Multi‑site SaaS vendor: A software provider with offices in New York and Bangalore implemented visitor management and electronic access logs. During its SOC 2 Type II audit, the access logs showed no unauthorized entries in the past 12 months. The auditor noted this as a strength, contributing to a clean opinion.
- Cloud‑service provider moving data centers: When migrating from an on‑premises data center to a co‑location facility, the provider installed flood sensors and HVAC monitoring to protect servers and backups. These measures aligned with the environmental controls domain and allowed the auditor to confirm that physical risks were controlled.
- Remote/hybrid workforce: An organization with many remote employees adopted asset tagging, cable locks, and secure shipping processes for laptops. Physical training emphasised secure storage when working from home. These device protection measures, combined with encryption and mobile device management, satisfied CC6.5 and CC6.7 requirements.
Templates & resources
To streamline execution, create or adapt these templates:
- Physical Security Policy: covers access control, visitor management, environmental controls, locks and keys, key issuance and return, incident response, and training requirements.
- Control Matrix: maps physical controls to SOC 2 criteria with columns for control description, domain, owner, evidence, frequency, and status.
- Evidence Tracker: a spreadsheet that records each control domain, evidence artifact, date collected, next review date, issues found, and remediation actions.
- Risk Assessment Worksheet: lists locations, assets, threats, vulnerabilities, risk ratings, mitigating controls, owners, and status.
- Audit Checklist: includes barrier inspections, surveillance functionality checks, access log reviews, key inventory audits, visitor log reviews, and training attendance verification.
Conclusion
Enterprise buyers and healthcare organizations demand more than polished policies; they expect proof that physical and logical controls operate together to safeguard data and maintain uptime. For cloud‑based service companies, SOC 2 Physical Security Controls are not optional afterthoughts—physical threats, from unauthorized visitors to fires and floods, can undo digital safeguards and stall business. Implementing robust physical controls builds trust, accelerates procurement, and protects customers’ data. Use the steps and templates in this guide to move from reactive fixes to a proactive, evidence‑driven control posture. Security that reads well but fails under incident pressure is a liability; build the program once, operate it daily, and let compliance follow.
FAQs
1) Does SOC 2 cover physical security?
Yes. The SOC 2 framework explicitly includes physical access controls under Common Criteria CC6, requiring organizations to restrict access to facilities and protect physical assets. CC6.1–6.8 tie physical safeguards to logical controls, so physical security is inseparable from the security Trust Services Criterion.
2) What are SOC 2 security controls?
SOC 2 security controls are processes, policies, and technologies that ensure systems are protected against unauthorized access. They include logical access controls (user provisioning, authentication, network segmentation), monitoring (logging, intrusion detection), encryption, incident response, change management, vendor risk management, and SOC 2 Physical Security Controls covering facilities, visitor management, devices, and environmental safeguards. These controls map to the Security criterion of the Trust Services Criteria.
3) What are logical and physical access controls in SOC 2?
Logical access controls refer to digital measures such as password policies, multi‑factor authentication, role‑based access, and network segmentation. Physical access controls restrict entry to facilities and sensitive areas through badges, biometrics, locks, surveillance, and visitor logs. SOC 2 requires organizations to implement both, because unauthorized physical access can undermine digital protections.
4) What are physical security controls?
Physical security controls include access control to facilities (badges, biometric readers), surveillance systems, electronic locks, visitor management, physical barriers (fences, gates, cages), alarm systems, environmental controls (HVAC, fire suppression, water detection), key management, device protection (locks, secure cabinets, asset tagging), and routine auditing of these controls. These measures prevent unauthorized physical access and protect equipment, data centres, and devices, ensuring that the organization meets SOC 2 and other framework requirements.





.svg)






.svg)
.svg)