SOC 2 attestations remain valid for 12 months from issuance, creating a cyclical compliance obligation for organizations serving enterprise clients. Most organizations treat renewal as a discrete annual project rather than an operational discipline—a fundamental gap that surfaces when enterprise procurement teams request current reports or when audit preparation reveals control deterioration.
This SOC 2 Renewal Guide addresses the specific requirements faced by companies selling to enterprise clients, where SOC 2 reports are mandatory during vendor evaluations and third-party risk management programs. Your enterprise customers maintain vendor management frameworks requiring current attestations; a lapsed or stale report flags your organization as elevated risk within their procurement systems.
This guide covers pre-renewal planning, systematic renewal execution, post-audit maintenance protocols, practical templates for evidence management, and the strategic positioning required to maintain trust with enterprise buyers.
Understanding SOC 2 Renewal – The Operational Reality
SOC 2 renewal differs fundamentally from initial certification. The initial audit establishes baseline controls and validates design effectiveness at a point in time or over an initial observation window. Renewal audits verify that documented controls operated continuously throughout a subsequent period—typically 12 months—demonstrating sustained operational effectiveness rather than one-time implementation.
SOC 2 Type 2 requires annual recertification to maintain compliance, with attestation reports evaluated against evidence spanning the entire observation window. Organizations maintaining mature control environments face fewer implementation gaps during renewal, but must demonstrate consistent execution across incident response, vendor management, access controls, change management, and monitoring functions.
How Often is SOC 2 Renewed?

Most companies complete a SOC 2 audit on an annual (12 months) or semi-annual (6 months) basis. Industry standard practice establishes annual renewal cycles, though certain enterprise clients with heightened security requirements or regulatory obligations may request semi-annual attestations. For subsequent audits, a 12-month observation period becomes standard, allowing organizations to demonstrate year-over-year control effectiveness without temporal gaps.
Organizations pursuing semi-annual audits typically serve highly regulated enterprise customers or operate in sectors with elevated threat profiles. This approach maintains continuous attestation coverage but increases audit costs and internal resource allocation, as biannual assessments incur higher total annual audit costs compared to single annual audits.
Why Renewal Matters for Enterprise-Facing Vendors
Enterprise procurement and vendor risk management programs operate on defined assessment cycles. Reports older than one year become "stale" and provide diminished value to potential customers conducting due diligence. When your SOC 2 attestation expires, enterprise prospects escalate security questionnaires, request additional documentation, or pause contract negotiations pending updated attestation.
Current SOC 2 reports directly impact commercial outcomes. Having a report ready speeds up sales cycles, simplifies security reviews, and opens access to larger deals and regulated industries. Expired attestations create friction in vendor onboarding workflows, extend procurement timelines, and position your organization unfavorably against competitors maintaining current compliance posture.
Continuous monitoring between audits demonstrates operational maturity. Enterprise clients increasingly require evidence that security controls operate year-round, not merely during audit observation windows. Organizations treating SOC 2 as an annual sprint rather than sustained operational practice risk control failures, incident response gaps, and attestation exceptions that undermine customer confidence.
Pre-Renewal Planning: Establishing Operational Foundation
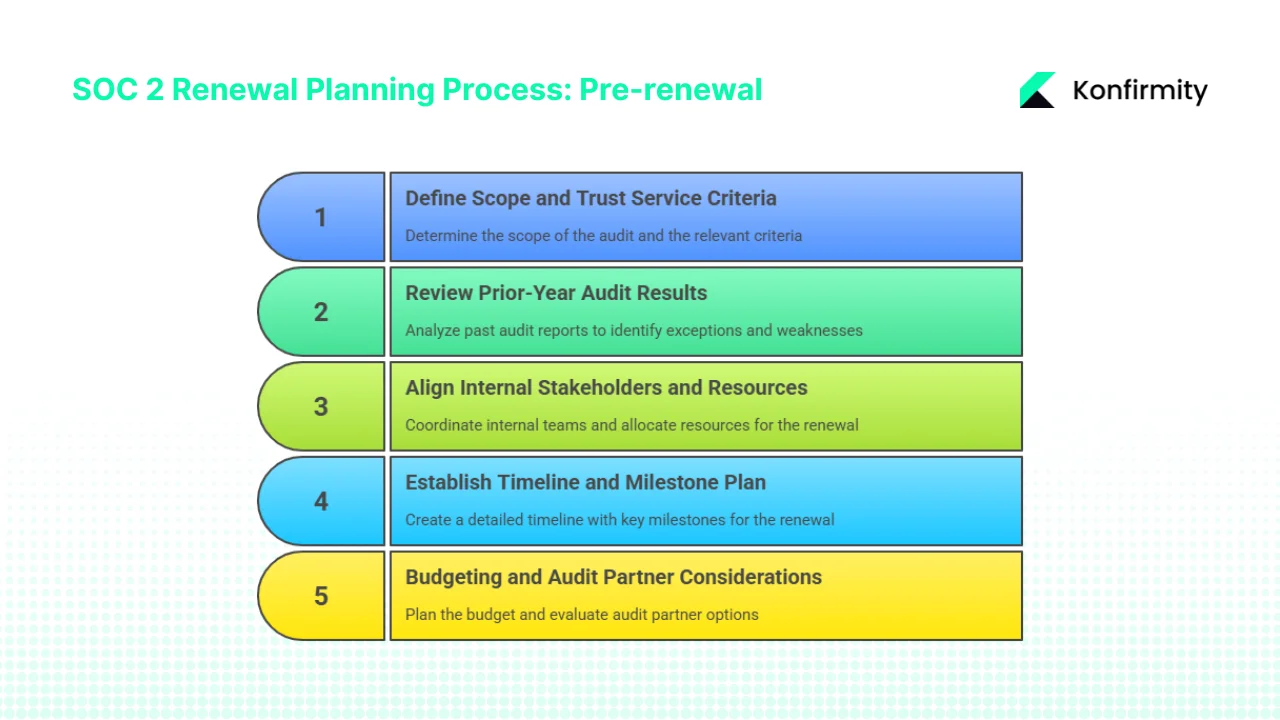
1) Define Scope and Trust Service Criteria
SOC 2 audits evaluate controls against five Trust Service Criteria: Security (mandatory), Availability, Processing Integrity, Confidentiality, and Privacy. Renewal scoping decisions should reflect organizational growth, service expansion, or evolving customer requirements since the prior audit.
Organizations adding new services, expanding data processing capabilities, or entering regulated markets may need to expand TSC scope. Each additional criterion increases audit complexity, evidence requirements, and testing scope. Security remains foundational; Availability and Confidentiality typically add 10-20% incremental audit cost, while Processing Integrity and Privacy involve more extensive testing and documentation.
2) Review Prior-Year Audit Results and Exceptions
Prior audit documentation provides critical insight into control weaknesses, testing failures, and remediation requirements. Audit reports identify control exceptions—instances where documented controls failed to operate as designed or produced testing failures during the observation period.
Organizations should catalog prior exceptions, track remediation implementation, and verify corrective actions to eliminate root causes. For example: if the prior audit identified access review control failures due to incomplete population sampling, renewal preparation should verify access review procedures now capture all in-scope systems and maintain complete audit trails.
3) Align Internal Stakeholders and Resources
SOC 2 renewal requires cross-functional coordination across security, IT operations, compliance, legal, vendor management, and executive leadership. Designate control owners for each TSC domain, establish evidence collection protocols, and define escalation paths for control failures or documentation gaps.
Personnel familiar with vendor services should complete vendor vetting and ongoing monitoring; for example, individuals knowledgeable about AWS configurations should participate in annual AWS SOC 2 report reviews. Maintaining consistent internal teams and audit partners year-over-year accelerates renewal processes through institutional knowledge and established communication protocols.
4) Establish Timeline and Milestone Plan
Renewal timelines should commence 4-6 months before current report expiration to allow readiness assessment, evidence collection, auditor engagement, and report finalization without temporal gaps. Map key milestones: readiness assessment completion, observation period boundaries, evidence submission deadlines, auditor fieldwork, and final report delivery.
Organizations maintaining continuous 12-month observation periods should align audit windows with customer fiscal year-ends where possible. Reports overlapping at least six months with user entity financial statement periods maximize report utility for customer auditors and vendor assessments.
5) Budgeting and Audit Partner Considerations
Annual audit fees typically represent 70-80% of initial audit costs, reflecting reduced scope definition and streamlined control review compared to initial certification. Multi-year audit firm relationships can reduce per-audit costs by 10-30% while providing predictable compliance budgeting.
Evaluate multi-year engagement structures with your CPA audit firm. Bundled arrangements reduce audit costs through efficiency gains, standardized evidence requests, and consistent testing methodologies. Audit partner continuity accelerates fieldwork, minimizes redundant documentation requests, and produces cleaner attestation reports through accumulated organizational knowledge.
Renewal Steps in Practical Sequence
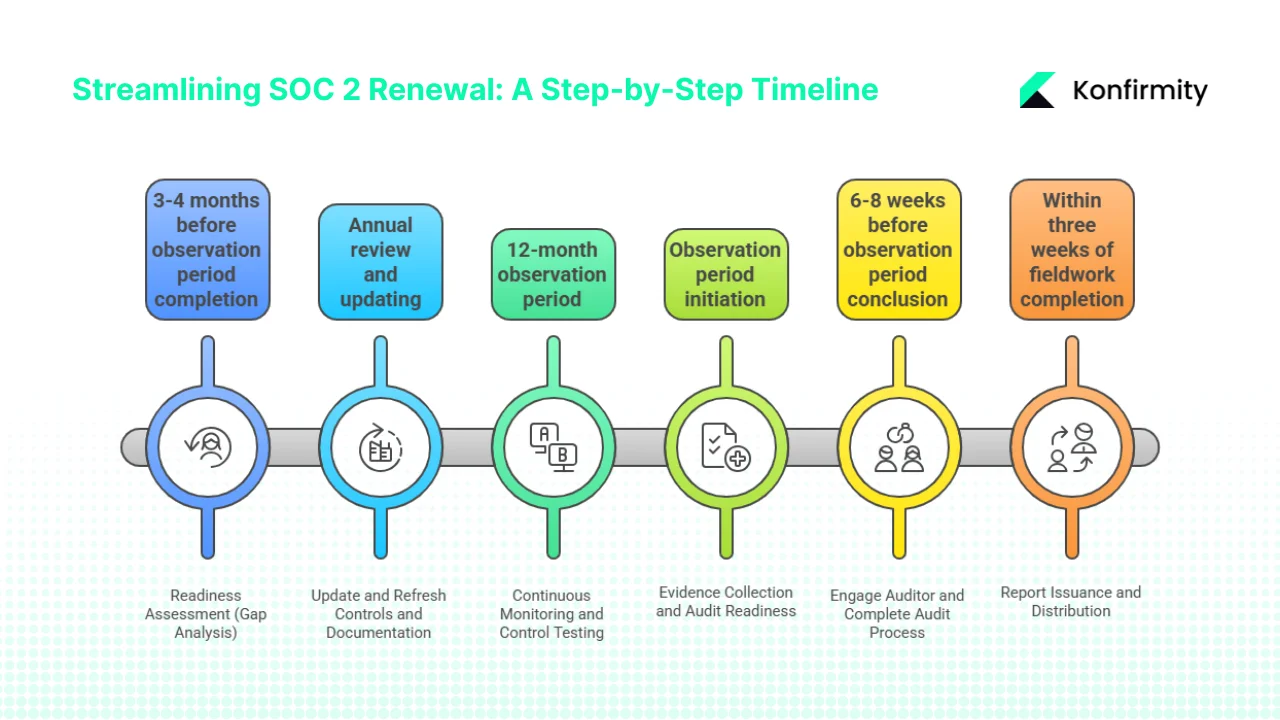
1) Readiness Assessment (Gap Analysis)
Conduct internal control reviews 3-4 months before observation period completion. Readiness assessments identify control design gaps, operational failures, documentation deficiencies, and evidence collection requirements before formal audit engagement.
Gap analysis should evaluate security policies, incident response procedures, vendor management protocols, access control implementation, change management workflows, vulnerability management practices, and monitoring infrastructure against established control baselines. Identify control exceptions early—remediating gaps during readiness rather than during formal audit reduces exceptions in final attestation reports.
2) Update and Refresh Controls and Documentation
Security policies require annual review and updating to reflect organizational changes, technology adoption, threat landscape evolution, and regulatory developments. Review and refresh information security policies, incident response plans, business continuity procedures, vendor management frameworks, acceptable use policies, and data classification standards.
Document organizational changes implemented since prior audit: new systems deployed, services launched, vendors engaged, personnel changes, or infrastructure modifications. These changes impact control scope, evidence requirements, and testing populations during audit fieldwork.
3) Continuous Monitoring and Control Testing
Subsequent SOC 2 Type 2 audits require a 12-month observation period demonstrating consistent control operation. Controls must operate continuously throughout this window—not merely during discrete testing intervals.
Implement continuous monitoring infrastructure: automated log collection, security information and event management (SIEM) platforms, vulnerability scanning, access review workflows, and vendor assessment tracking. Evidence artifacts should demonstrate control execution at defined frequencies: quarterly access reviews, monthly vulnerability assessments, continuous log monitoring, and documented incident response for security events occurring during the observation period.
4) Evidence Collection and Audit Readiness
Systematic evidence collection should commence at observation period initiation, not weeks before audit fieldwork. Evidence artifacts include system logs, access review documentation, vulnerability scan reports, penetration test results, vendor SOC 2 reports, incident response records, change management approvals, training completion records, and risk assessment outputs.
Organize evidence repositories mapping each control to supporting documentation. Maintain evidence registers tracking control identifiers, responsible owners, collection frequency, artifact locations, and submission status. Centralized evidence management accelerates auditor requests, reduces follow-up inquiries, and shortens audit fieldwork duration.
5) Engage Auditor and Complete Audit Process
Formal audit engagement typically begins 6-8 weeks before observation period conclusion. Auditors conduct scoping discussions, review system descriptions, issue evidence request lists, perform control walkthroughs, execute testing procedures, and document findings.
Audit fieldwork generally requires two to six weeks depending on scope, locations, and TSC complexity. Respond promptly to auditor information requests, provide complete populations for sampling, and maintain audit team availability for interviews and walkthroughs.
6) Report Issuance and Distribution
Following fieldwork completion, auditors prepare draft reports for management review—typically within three weeks. Draft reports identify proposed findings, control exceptions, and management responses. Final reports incorporate management feedback and receive CPA firm signature before distribution.
Distribute final SOC 2 reports through secure channels to enterprise customers, vendor risk management portals, and procurement teams. Maintain distribution logs tracking report recipients, transmission dates, and access controls to protect confidential attestation content.
Post-Audit: Maintain and Prepare for Next Renewal
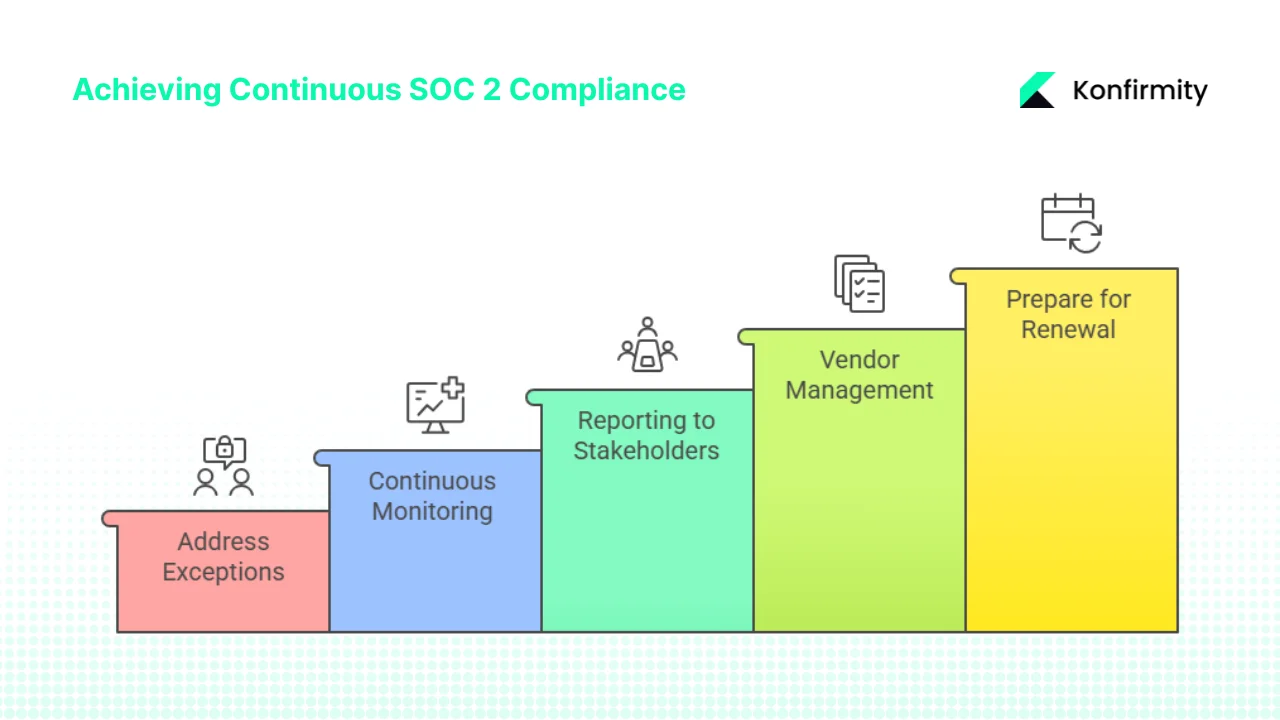
1) Address Exceptions and Improvement Items
Audit reports may identify control exceptions—instances where controls failed testing or operated inconsistently during the observation period. Develop remediation plans addressing root causes: update procedures, implement compensating controls, enhance monitoring, or redesign control activities.
Track remediation timelines, assign ownership, and document corrective actions for subsequent audit review. Exceptions appearing in consecutive audits signal systemic control weaknesses requiring architectural remediation rather than procedural adjustments.
2) Continuous Monitoring and Internal Controls Upkeep
Sustained audit readiness requires continuous control operation between formal audit cycles. Implement quarterly internal control testing, vulnerability management workflows, access review procedures, and incident response drills to identify and remediate control drift before subsequent audits.
Leverage automation platforms for evidence collection, control monitoring, and compliance dashboards providing real-time visibility into control health. Automation reduces manual effort, eliminates evidence collection gaps, and enables early detection of control failures requiring immediate remediation.
3) Reporting Requirements and Updating Stakeholders
Maintain executive leadership, board, and risk committee visibility into SOC 2 compliance posture through quarterly reporting. Compliance dashboards should track control testing results, exception remediation status, vendor risk profiles, incident response metrics, and preparation progress for subsequent audit cycles.
4) Vendor Management and Third-Party Risks
SOC 2 examinations extend to key subservice organizations providing services to your clients; effective vendor management ensures subservice organizations meet equivalent security, availability, processing integrity, confidentiality, and privacy standards.
Conduct annual vendor assessments including current SOC 1 or SOC 2 report review, periodic security evaluations, risk assessments, and SLA performance monitoring. Vendor management frameworks should address vendor onboarding due diligence, ongoing monitoring, issue remediation protocols, and termination procedures including secure data return and deletion.
5) Prepare for Next Renewal Cycle
Renewal preparation should commence immediately following current audit completion. Integrate renewal milestones into annual compliance calendars, schedule readiness assessments 4-6 months before observation period conclusion, and maintain continuous evidence collection eliminating last-minute documentation scrambles.
Organizations treating renewal as business-as-usual operational practice rather than annual crisis management demonstrate mature security postures to enterprise customers and audit firms.
Templates and Example Artifacts
Control Mapping Template
Develop control mapping matrices linking each TSC criterion to implemented controls, responsible owners, testing frequency, and evidence artifacts. Example structure:
Evidence Register Template
Maintain evidence registers tracking collection status, submission deadlines, and artifact completeness:
Vendor Risk Assessment Checklist
Track vendor due diligence, attestation review, and ongoing monitoring:
Audit Readiness Checklist
Pre-audit validation checklist verifying preparation completeness:
- ✅ Scope definition finalized and documented
- ✅ All controls documented with clear ownership
- ✅ Continuous monitoring active for observation period
- ✅ Vendor list current with attestations reviewed
- ✅ Incident response tested with documented exercises
- ✅ Prior audit exceptions remediated and verified
- ✅ Evidence repository organized and accessible
- ✅ System description updated reflecting current architecture
- ✅ Risk assessment completed and documented
Sample Renewal Timeline
Structured timeline mapping renewal preparation across 12-month cycles:
Common Pitfalls and Avoidance Strategies
Organizations frequently undermine renewal effectiveness through predictable failures:
Treating renewal as a discrete project rather than a continuous process. Security controls must operate year-round, not merely during audit windows. Implement continuous monitoring, automated evidence collection, and quarterly internal testing to maintain sustained readiness.
Switching audit firms annually. Auditor continuity accelerates renewal through institutional knowledge, standardized evidence requests, and established communication. Multi-year audit relationships reduce costs through efficiency gains and eliminate redundant scoping exercises.
Neglecting policy and control updates between audits. Technology environments, threat landscapes, and organizational structures evolve continuously. Implement annual policy review cycles, update control documentation reflecting architectural changes, and validate control relevance against current operations.
Failing to track vendor risk and subservice organizations. SOC 2 examinations scrutinize key subservice organizations providing services to your clients. Maintain current vendor inventories, review vendor SOC 2 reports annually, and document vendor risk assessments as required by CC9.2 criterion.
Delaying evidence collection until audit commencement. Evidence artifacts spanning 12-month observation periods cannot be recreated retroactively. Implement automated evidence collection at observation period initiation, maintain organized repositories, and validate evidence completeness quarterly.
Allowing attestation gaps between audit cycles. Reports older than 12 months become stale and lose value for enterprise customers. Schedule renewal audits ensure observation periods overlap without temporal gaps, eliminating the need for bridge letters or customer explanations.
Business and Sales Impact for Enterprise-Facing Organizations
Current SOC 2 attestations function as commercial enablers for enterprise sales. Procurement teams maintain vendor risk frameworks requiring current security attestations as gate criteria; expired or missing SOC 2 reports trigger elevated due diligence, extended security questionnaires, or vendor disqualification.
Enterprise vendors require SOC 2 reports during evaluations, and current reports speed sales cycles, simplify security reviews, and unlock access to larger deals. Organizations maintaining continuous compliance posture through systematic renewal demonstrate operational maturity and security commitment differentiating them from competitors operating reactive compliance programs.
SOC 2 renewal supports vendor management due diligence conducted by your enterprise customers. When customer procurement teams assess third-party risk, current attestations with clean opinions and minimal exceptions position your organization as a low-risk vendor. Conversely, lapsed attestations, numerous control exceptions, or qualified opinions elevate vendor risk scoring and trigger additional oversight requirements.
Renewal protects existing contract relationships. Enterprise customers increasingly include SOC 2 maintenance requirements in vendor contracts with annual attestation delivery obligations. Failure to provide current reports may constitute contract breaches triggering termination rights or service suspensions.
Conclusion
SOC 2 renewal represents operational necessity—not optional certification maintenance—for organizations serving enterprise clients. Enterprise procurement, vendor risk management, and compliance frameworks require current attestations demonstrating sustained security control effectiveness.
Effective renewal execution requires systematic planning, continuous control operation, automated evidence collection, and consistent audit partner relationships. Organizations implementing repeatable renewal processes through documented templates, established timelines, and continuous monitoring infrastructure transform renewal from annual crisis into routine operational discipline.
The distinction between compliance theater and genuine security posture becomes apparent during renewal cycles. Organizations maintaining controls continuously, collecting evidence systematically, and addressing gaps proactively produce clean attestation reports demonstrating authentic security programs. Those treating renewal as checklist exercise inevitably face rushed preparation, incomplete evidence, and attestation exceptions undermining customer confidence.
Treat renewal as ongoing risk management integrated into security operations rather than discrete annual projects. Leverage the templates provided, implement continuous monitoring, maintain evidence repositories, and establish multi-year audit relationships accelerating subsequent cycles. Your enterprise customers evaluate vendor security posture through attestation currency, opinion quality, and exception patterns—demonstrating operational maturity through systematic renewal protects commercial relationships and competitive positioning.
Frequently Asked Questions
Q1. How often is SOC 2 renewed?
SOC 2 reports are typically valid for 12 months from issuance, requiring annual renewal to maintain current status. Some organizations complete audits semi-annually (6 months) or adopt multi-year arrangements depending on customer requirements and risk posture. Enterprise-facing vendors typically maintain annual renewal cycles aligned with customer procurement and vendor assessment schedules.
Q2. What is the SOC 2 compliance checklist?
SOC 2 preparation encompasses scoping Trust Service Criteria, conducting readiness assessments, documenting controls across security policies, incident response, vendor management, data protection, and internal controls, implementing continuous monitoring and control testing, collecting evidence systematically, engaging CPA audit firms, and producing attestation reports. Readiness checklists should verify control documentation completeness, evidence repository organization, vendor attestation currency, incident response testing, and prior exception remediation before audit engagement.
Q3. How long is the SOC 2 certification valid for?
SOC 2 attestations are generally valid for 12 months from report issuance, after which organizations should complete renewal audits maintaining current compliance status. Reports exceeding 12 months become stale and provide diminished value to enterprise customers conducting vendor assessments.
Q4. What are the 5 principles of SOC 2?
The five Trust Service Criteria (TSC)—often termed "principles"—include Security (mandatory for all SOC 2 audits), Availability, Processing Integrity, Confidentiality, and Privacy. Security addresses protection against unauthorized access, use, or modification. Availability evaluates system accessibility for operation and use. Processing Integrity assesses whether systems achieve intended purposes without unauthorized or unintended alteration. Confidentiality protects information designated confidential. Privacy addresses collection, use, retention, disclosure, and disposal of personal information according to stated privacy commitments.





.svg)






.svg)
.svg)