Procurement teams at large customers now ask tough questions before they sign a contract. They want evidence that their suppliers not only follow written policies but operate secure systems day after day. In my experience leading Konfirmity, vendors often say they are ready for an audit but then stall deals because their security controls don’t stand up to scrutiny. One area that repeatedly causes trouble is the handling of sensitive credentials. This article explains why strong secret handling matters when pursuing or maintaining a SOC‑2 attestation, what can go wrong when it’s neglected, and how to build practices that satisfy auditors and enterprise buyers. It also offers actionable steps, real‑world examples, and template outlines to help busy teams get started.
What SOC‑2 Means and Why Secret Handling Is Central
SOC‑2 is a framework maintained by the American Institute of Certified Public Accountants (AICPA). It evaluates whether a service organization’s controls protect customer data across five areas: security, availability, processing integrity, confidentiality and privacy. Only the security criterion is mandatory; the other four are added based on client requirements or the nature of the service. A SOC‑2 report is often requested during enterprise sales because it gives buyers confidence that the provider safeguards systems and information.
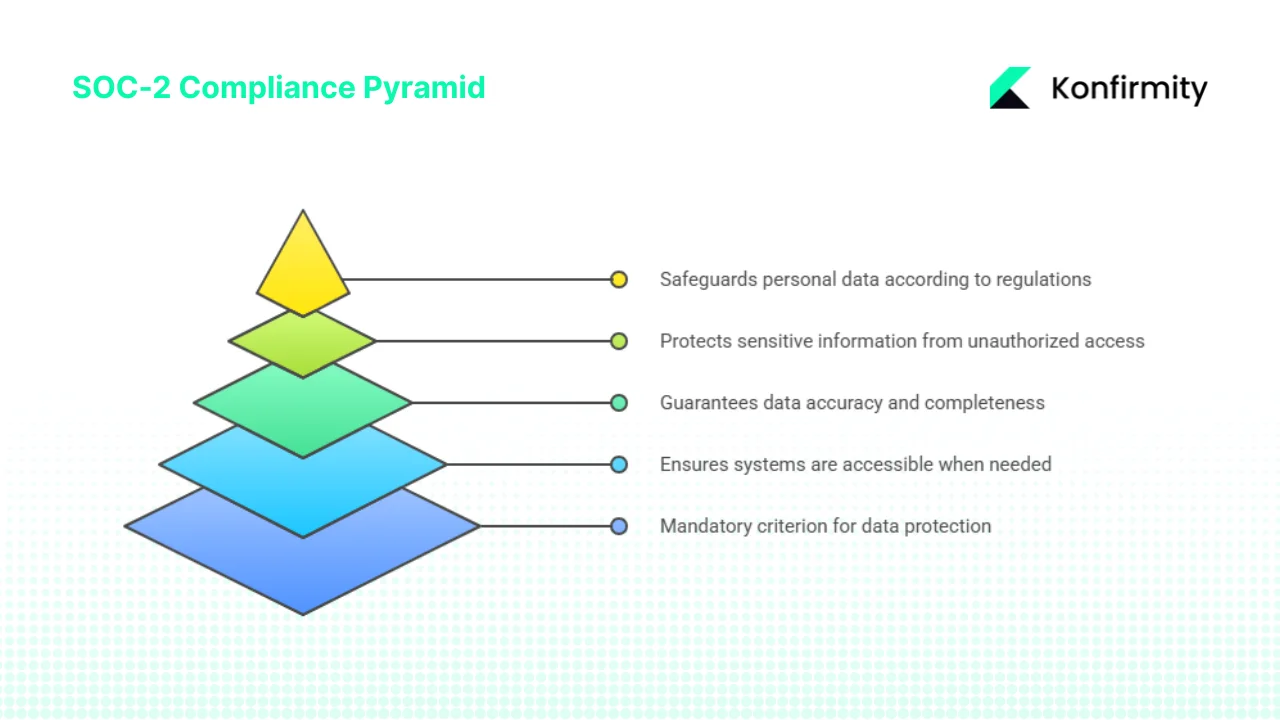
Secrets—passwords, application tokens, API credentials, certificates and encryption material—sit at the heart of these criteria. They control access to databases, cloud services, automation pipelines and third‑party systems. If secrets leak, attackers can bypass authentication, steal confidential data and disrupt services. Poor handling of secrets undermines every trust criterion: it endangers confidentiality, undermines integrity, jeopardizes availability and signals weak risk management. To satisfy auditors and prospective customers, organizations must show that secrets are identified, protected, used by the right people or machines, and rotated or revoked when no longer needed.
Principles and Themes: How SOC‑2 Maps to Secret Handling
Security controls & access management
The security criterion demands that only authorized identities can get to systems and data. For secrets, this means adopting role‑based access control and least‑privilege policies. Each secret should be linked to a specific service or user and exposed only as long as necessary. Workflows for requesting and granting access should include identity verification steps. Automated services such as CI/CD pipelines need dedicated identities so their credentials don’t become shared across human users.
Data confidentiality & credential protection
The confidentiality criterion focuses on limiting access, storage and use of sensitive information. Secrets must remain confidential at rest, during transit and when shared between systems. Use encryption for storage and TLS for transmission. Avoid embedding secrets in code or configuration files. A Microsoft guidance document warns that placing credentials in code or version control is a significant risk and recommends using secure stores instead.
Identity verification & vendor management
Service providers often work with third‑party vendors, contractors or partners. Those external parties may require access to certain secrets. SOC‑2 auditors expect clear policies on how vendors are vetted, how their access is limited, and how credentials are revoked when the engagement ends. Access should be time‑bound and based on documented need. Vendor secrets should live in the same vault and adhere to the same rotation schedules as internal secrets.
Monitoring, logging & audit readiness
Auditors look for evidence that secret usage is tracked. Logs should record when a credential was retrieved, by whom or which process, and from where. Those logs must be tamper‑resistant and retained for the length of the observation window. The Cloud Security Alliance notes that the rapid changes in microservices and serverless environments make continuous monitoring essential. Without real‑time visibility, it’s hard to prove that only authorized entities access high‑risk secrets.
Encryption practices & risk mitigation
Encryption defends secrets in two ways: it protects the secret itself, and it reduces the impact if a vault service is compromised. The NIST key management guidelines explain that cryptographic keying material must be protected throughout its lifecycle, including handling, storage and distribution. Use a vault that encrypts secrets before storage (preferably with end‑to‑end protection) and enforce TLS for any retrieval. Cloud providers offer managed key services—such as AWS KMS—but the vault should ensure that encryption material is kept separate from the secrets it secures.
Security policies, training & incident response
Technology alone doesn’t satisfy SOC‑2. A strong program requires written policies that define how secrets are created, reviewed, rotated and revoked. Those policies must be communicated and enforced through training and regular reviews. Response procedures should outline how to revoke and replace exposed credentials, notify affected parties and investigate causes. Continuous education reduces the chance that developers embed secrets in code or share them over insecure channels.
How Cloud‑Native Architectures Change Secret Handling
Modern platforms rely on containers, serverless functions and dozens of microservices. Each component requires credentials to communicate with databases, message queues and external APIs. The Cloud Security Alliance observes that the explosion of microservices has increased the number of secrets, making their protection an urgent challenge. In this fluid environment, old practices—manual rotation, hard‑coded passwords—no longer work. Resources are created and destroyed in minutes; service accounts may live for days. As a result:
- Secret sprawl increases. Developers spin up short‑lived workloads that generate new tokens. Without a central inventory, tokens proliferate across repositories, pipelines and chat messages. The CSA notes that eliminating hard‑coded secrets in code repositories and messaging systems is an essential first step.
- Visibility becomes harder. When infrastructure is ever‑changing, periodic audits miss exposures. The same article stresses the need for real‑time monitoring and automated compliance checks to keep up.
- Ephemeral access is the norm. Service accounts may need credentials only for the duration of a build or deployment. Tools must generate and revoke secrets on demand, not rely on long‑lived passwords. Policies must reflect this transience.
- Automated systems use most secrets. In modern stacks, non‑human identities—such as service accounts, API clients or machine agents—outnumber human users. These identities often have broad privileges. CSA guidance recommends maintaining an inventory of non‑human identities, classifying them by risk and applying continuous authentication.
To manage this complexity under SOC‑2, organizations need vaults and identity systems that integrate with cloud platforms, container orchestration tools and CI/CD pipelines. Manual tracking with spreadsheets is insufficient.
Step‑by‑Step Guide to SOC‑2‑Aligned Secret Handling
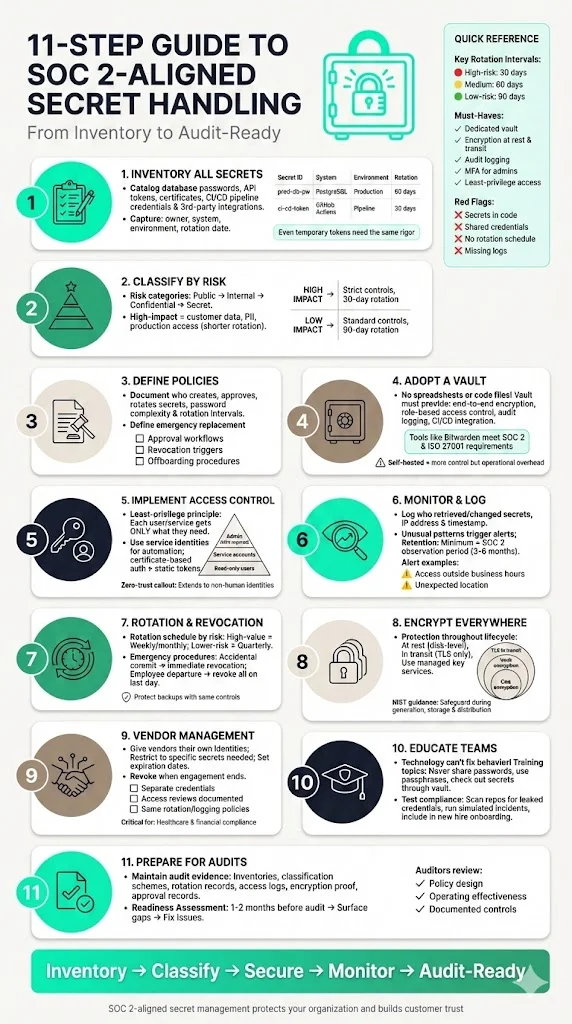
1. Inventory all secrets
Start by cataloging every secret used across development, staging and production. This includes database passwords, API tokens, service account credentials, private certificates and deployment keys. Don’t forget tokens in CI/CD pipelines and third‑party integrations. Microsoft’s guidance stresses that even temporary tokens require the same rigor as long‑term secrets. Capture metadata such as owner, system, environment, last rotation date and who can approve changes.
An example inventory entry:
2. Classify and prioritize by risk
Once you have a list, rank secrets by impact if compromised. Define categories such as public, internal, confidential and secret. High‑impact items—credentials that access customer data, production systems or personally identifiable information—must receive strict controls and shorter rotation cycles. Lower‑impact items may allow longer rotation but should still be recorded and periodically reviewed.
3. Define and document policies
Clear policies transform best practices into repeatable processes. Define who can create a secret, who can approve access, and how rotation and revocation occur. Document minimum standards: password length, complexity requirements, rotation intervals, encryption requirements, approval workflows and revocation triggers. Include procedures for emergency replacement if a secret is exposed. Policies should also specify how to onboard and offboard team members, ensuring that departing staff lose access promptly.
4. Adopt a dedicated vault
Storing passwords in code, configuration files or spreadsheets is not acceptable. Adopt a purpose‑built secret manager or password manager. Many companies use Bitwarden to meet SOC‑2 and ISO 27001 requirements because it offers encryption before storage, granular access control and audit logs. Whatever product you choose, ensure that it provides:
- End‑to‑end encryption so that only authorized users can read the data, even if the vault provider is compromised.
- Role‑based access control with fine‑grained permissions.
- Audit logging for every read or write operation.
- Integration with cloud identity providers and CI/CD tools so secrets can be injected into pipelines without manual copying.
For organizations with strict sovereignty or latency requirements, self‑hosted vaults may be preferable. However, self‑hosting carries operational overhead. Assess whether your team can maintain the infrastructure while also building product features.
5. Implement access management and identity verification
Map each secret to the identities that need it. Use least‑privilege—give each user or service only the access necessary for their function. For automation, assign service identities rather than sharing human credentials. Where supported, use certificate‑based authentication or managed identities instead of static tokens. According to CSA, extending zero‑trust principles to non‑human identities improves security. Enforce multi‑factor authentication for administrative accounts.
6. Monitor and log usage
Continuous monitoring ensures that secret usage aligns with expectations. Enable logging at the vault level to capture who retrieved or changed a secret and from which IP address. Forward logs to a centralized system and set up alerts for unusual patterns—for example, a secret being retrieved outside normal business hours or from an unexpected location. Maintain these records for at least the duration of your SOC‑2 observation period, which is typically three to six months. In the event of an incident, these logs provide evidence for forensic analysis and demonstrate to auditors that controls operate effectively.
7. Define rotation, revocation and backup procedures
Set rotation intervals based on risk. High‑value secrets might rotate weekly or monthly, while lower‑risk items rotate quarterly. Automate rotation where possible; many vaults can rotate database passwords or cloud credentials and update dependent services. Document emergency revocation procedures: how to replace a credential if a developer accidentally commits it to a repository, and how to revoke all secrets belonging to a departing employee on their last day. Maintain secure backups of the vault so that secrets can be restored in case of disaster, but protect those backups with the same controls as the primary store.
8. Encrypt at rest and in transit
Do not rely on the vault alone; use encryption to protect secrets throughout their lifecycle. NIST notes that cryptographic materials need safeguards during generation, storage and distribution. Use disk‑level encryption on servers hosting vaults, and ensure secrets are transmitted via TLS. In cloud environments, use managed key services to manage encryption material separately from the data they protect. When sharing secrets between systems, use secure channels such as mutually authenticated HTTPS.
9. Onboard vendors and third parties carefully
Vendors often require access to certain environments. Provide them with their own identities and restrict them to the specific secrets they need. Set expiration dates on their access and revoke it when the engagement ends. Treat vendor secrets with the same rotation and logging policies as internal secrets. Maintain documentation of vendor onboarding procedures and evidence of access reviews. This is especially important for healthcare or financial customers, where regulations require demonstrating control over third‑party access to sensitive data.
10. Educate teams and enforce policies
Technology can’t fix behaviour. Run regular training sessions to remind engineers, product managers and support staff why secret handling matters. Cover topics like not sharing passwords over chat, using passphrases, and checking out secrets through the vault. Periodically test compliance by scanning code repositories for leaked credentials and running simulated incidents. Document findings and follow up with corrective actions. Incorporate secret handling into onboarding for new hires.
11. Prepare for audits
SOC‑2 audits review both design and operating effectiveness of controls. Maintain documentation that proves you follow your policies: inventories, classification schemes, rotation records, access logs and audit trails. Keep evidence that secrets are encrypted and that access requests were approved by authorized personnel. Conduct internal readiness assessments before inviting an external auditor. A readiness exercise typically lasts one to two months and surfaces gaps while there’s still time to fix them.
Real‑World Examples
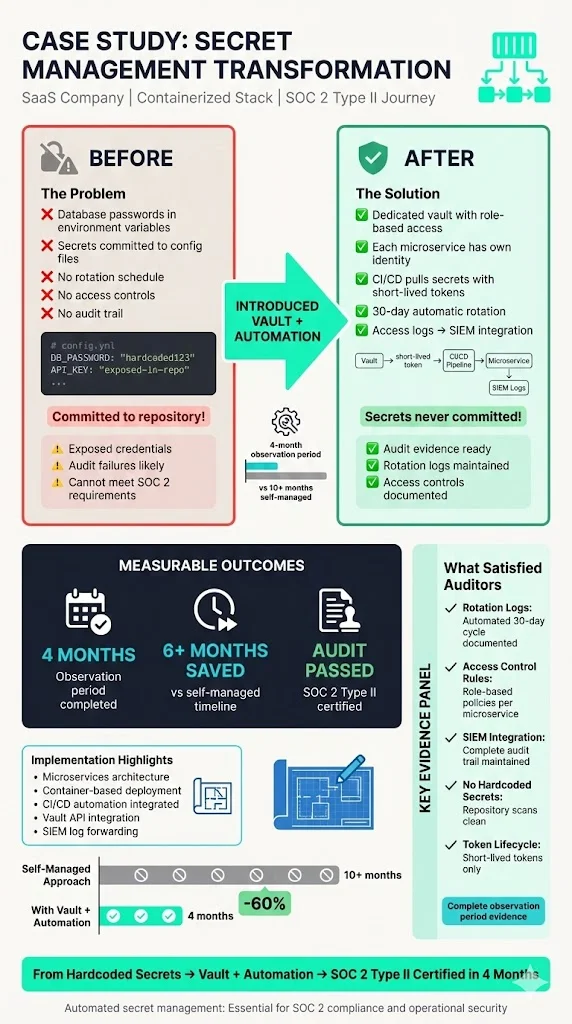
Cloud‑native startup: A software‑as‑a‑service company with a containerized stack used to embed database passwords in environment variables and commit them to configuration files. When pursuing SOC‑2 Type II, we introduced a vault with role‑based access for each microservice. The company’s CI/CD pipeline pulled secrets at deployment using short‑lived tokens. Secrets rotated every 30 days. Access logs fed into the company’s security information and event management (SIEM) system. During the audit, evidence showing rotation logs and access control rules satisfied the auditor’s questions. The company completed the observation period in four months, shaving at least six months off the timeline typical for self‑managed efforts.
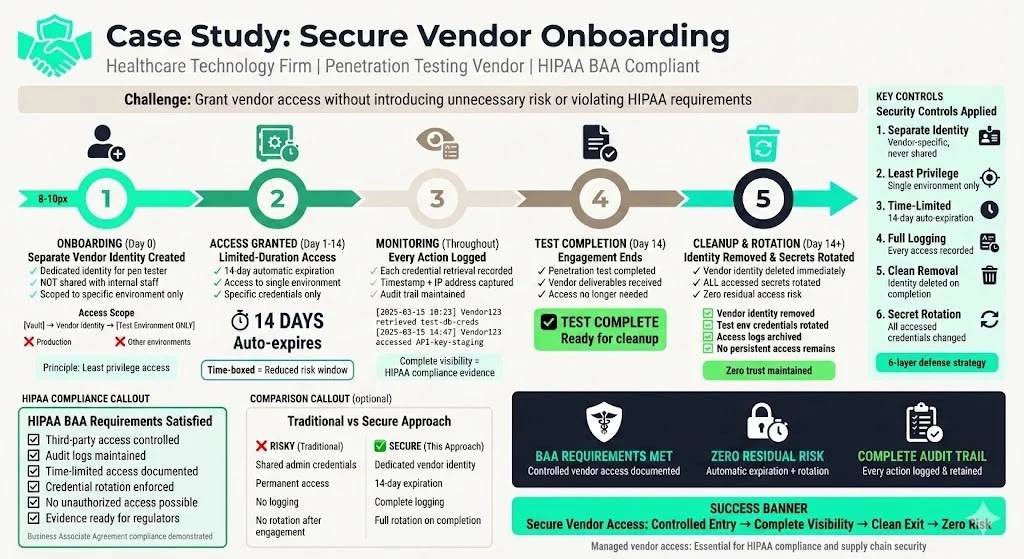
Vendor onboarding: A healthcare technology firm hired a penetration testing vendor. Through Konfirmity’s managed program, the firm issued a separate identity for the tester in its vault and granted access to a single environment. The access expired automatically after 14 days. Logs recorded each retrieval of credentials. When the test finished, the identity was removed and all secrets rotated. This level of control helped satisfy HIPAA business associate agreement requirements without introducing unnecessary risk.
Secrets leak prevention: In another case, a developer inadvertently committed an API token to a public repository. Automated scanning detected the secret within minutes. Because the token was managed through the vault, rotation took seconds—no code deployment was needed. The leaked token was revoked, a new one generated and injected into the application, and incident logs were kept for auditors. The quick response prevented unauthorized use and demonstrated the effectiveness of the rotation and logging controls.
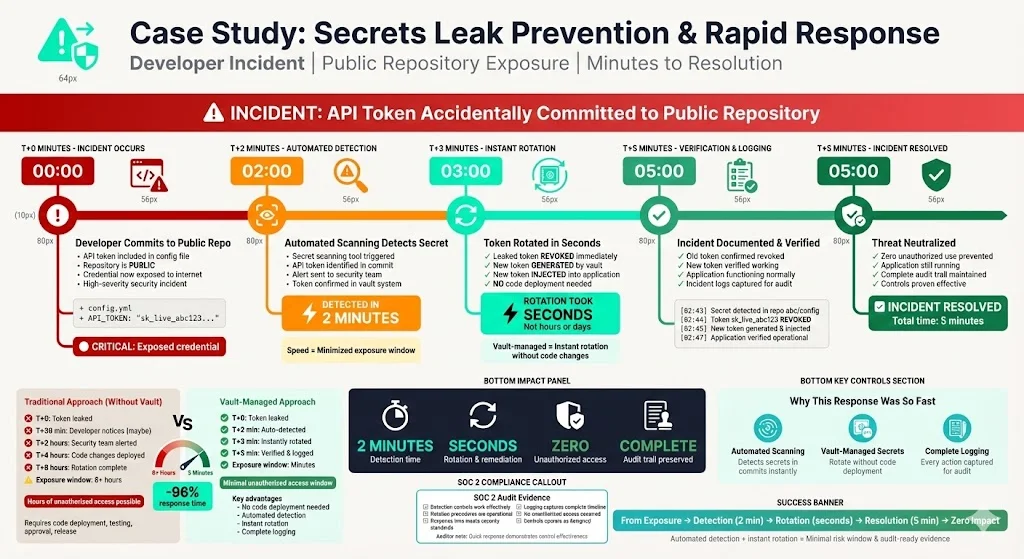
Common Mistakes and How to Avoid Them
- Storing credentials in code or configuration files. This exposes secrets when repositories are shared or logs are sent to third‑party services. Use a vault and environment injection instead.
- Manual processes. Manually rotating passwords or revoking access invites human error. Automate whenever possible and document procedures for exceptions.
- Over‑permissive access. Granting broad permissions to teams or service accounts increases blast radius. Enforce least‑privilege and review permissions regularly.
- Lack of logging. Without audit logs, there’s no way to prove controls are operating. Enable logging at the vault, infrastructure and application levels.
- Missing encryption. Unencrypted secrets at rest or in transit can be stolen. Use vaults with encryption and secure communication channels.
- Ignoring vendor credentials. Third‑party users often slip through the cracks. Apply the same policies to vendors and revoke access promptly.
- Neglecting rotation after personnel changes. People move roles or leave the company. Always rotate secrets when staff with access depart.
How Robust Secret Handling Demonstrates SOC‑2 Compliance
A well‑implemented secret management program supports every trust criterion. Security and access control are strengthened when only authorized identities can retrieve credentials and all usage is logged. Confidentiality is protected by encrypting secrets and enforcing least‑privilege, preventing leakage of customer data. Processing integrity is supported because systems use validated credentials to communicate; expired or revoked credentials trigger failsafe responses. Availability improves because automated rotation prevents service interruptions caused by expired passwords. Risk management is documented through policies, inventories and monitoring. The Cloud Security Alliance stresses that ongoing monitoring and continuous improvement are essential for maintaining compliance in fluid cloud environments. By implementing structured secret handling, organizations build a foundation that withstands audits and real attacks.
The approach is particularly important for microservice and container infrastructures. CSA research notes that the proliferation of microservices and serverless functions increases the number of secrets and makes protection more urgent. By adopting zero‑trust principles, maintaining inventories and integrating vaults with orchestration platforms, organizations can keep up with the pace of cloud deployment and still satisfy SOC‑2 requirements.
Tools and Solutions: What to Look For
When selecting a secret manager or password vault, look for capabilities that support SOC‑2 audits and daily operations:
- Strong encryption. The vault should encrypt secrets before storage and use secure transport for retrieval. End‑to‑end encryption ensures the provider cannot read your data.
- Granular access control. Define roles and permissions at the secret level. Support for single sign‑on and multi‑factor authentication simplifies management.
- Audit logging and monitoring. The system must record every action and integrate with your SIEM or log management platform. Audit logs should include user identity, time, action and origin.
- Integration with infrastructure. Support for cloud identity and access management, CI/CD pipelines, Kubernetes secrets and serverless functions allows secrets to be injected automatically.
- Scalability and redundancy. The solution should handle growth in the number of secrets without performance degradation and provide high availability.
- Vendor compliance posture. If you choose a SaaS vault, verify that the provider maintains its own SOC‑2 or ISO 27001 attestations.
Bitwarden, HashiCorp Vault, Akeyless, 1Password and Keeper are often used by teams aiming for SOC‑2 because they offer encryption, role‑based access and robust logging. Evaluate whether you need a self‑hosted deployment or a managed service. Self‑hosting offers control but increases maintenance burden. Managed services reduce operational overhead and often provide builtin compliance features.
Templates and Checklists for Busy Teams
To accelerate implementation, prepare templates and checklists that your teams can adopt. Konfirmity offers ready‑to‑use resources such as:
- Secrets inventory worksheet. A spreadsheet with columns for secret identifier, owner, system, environment, sensitivity and rotation frequency. The example table above illustrates the structure.
- Access request form. A form used by staff to request new secrets or access. It captures requester details, justification, scope of access and approving manager.
- Role‑based access matrix. A template mapping roles (developer, admin, CI/CD service) to permitted secrets and actions.
- Rotation schedule. A chart listing all secrets with their rotation intervals and next rotation date.
- Vendor onboarding checklist. Steps to vet vendors, issue credentials, set expirations, and record approvals.
- Incident response flow. A diagram showing detection, containment, rotation and notification steps in case of secret exposure.
- Audit log retention policy. A document defining how long logs are retained, how they’re protected, and who can access them.
These templates save time and help maintain consistency across teams. Feel free to adapt them to your specific environment and regulatory obligations.
Closing Thoughts
Strong secret handling is not a project you finish and shelve; it’s an operational discipline that supports every aspect of a SOC‑2 program. As enterprise buyers raise the bar on security evidence, poorly managed credentials become deal breakers. Building a program takes time and expertise. At Konfirmity we have guided more than six thousand audits and draw on more than 25 years of combined technical experience. We have seen the pitfalls: hard‑coded passwords, ad‑hoc rotation, lack of logging, and non‑human identities that accumulate unchecked. We also know that with the right mix of policies, automation and human oversight, teams can meet SOC‑2 requirements in four to five months rather than a year and free more than 500 hours of internal effort.
Start with the basics: identify all your secrets, classify them by risk, adopt a vault, define policies and train your people. Integrate the vault with your pipelines and enforce least‑privilege. Monitor continuously, rotate regularly and be ready to revoke. When auditors or buyers ask for evidence, you will have logs, policies and real operating history rather than hasty paperwork. In short, build a program that stands up to scrutiny and leaves no room for doubt.
FAQs
1) What are the five criteria for SOC‑2?
The AICPA defines five trust service criteria: security, availability, processing integrity, confidentiality and privacy. Only security is required; the others are optional depending on your services.
2) Are SOC‑2 reports confidential?
Yes. SOC‑2 reports contain detailed descriptions of a company’s systems and controls. They are shared under non‑disclosure agreements with customers or partners who need assurance. Public disclosure can introduce risk by exposing internal processes.
3) How should a company prepare for a SOC‑2 Type II audit?
Define the scope (systems, trust criteria and period), implement controls, and collect evidence over the observation period. Conduct a readiness assessment to identify gaps before starting the audit. Maintain detailed documentation and logs. Engage with a firm that has hands-on experience implementing controls, not just writing policies. Plan for a timeline of at least four months, plus observation time.
4) Does SOC‑2 require encryption at rest?
SOC‑2 does not prescribe specific technologies, but encryption is strongly advised. Protecting secrets and customer data with encryption is a practical way to meet the security and confidentiality criteria. NIST guidance stresses that cryptographic materials need protection throughout their lifecycle. Microsoft also recommends encrypting secrets both at rest and in transit. Auditors will look for evidence that sensitive data is not stored in plain text.





.svg)






.svg)
.svg)