Most enterprise buyers now request assurance artifacts before they sign a new contract. Procurement teams ask to see not only the scope of controls but proof that those controls work. This shift has been driven by a sharp rise in cloud breaches and supply‑chain disruptions. PwC’s 2024 Global Digital Trust Insights survey found that the percentage of breaches costing more than $1 million jumped from 27% to 36%, and IBM’s 2024 Cost of a Data Breach Report noted that 40% of breaches involved data spread across multiple environments. Check Point’s 2024 cloud security report showed that 61% of organizations suffered a cloud security incident and 21% ended in a breach. Meanwhile, 62% of respondents in Hyperproof’s 2024 benchmark survey reported a cybersecurity‑related supply‑chain disruption. When the cost of a breach averaged $4.88 million in 2024 and held steady at $4.44 million in 2025, buyers became wary. They want partners who can demonstrate resilient engineering and continuous evidence, not just a polished policy.
This article explains how to build a SOC 2 Secure SDLC—the intersection of SOC 2 compliance and a security‑focused software development lifecycle (SDLC). I’ll define SOC 2 and its relevance to software engineering, then walk through the core requirements that shape an SDLC. You’ll see how to embed controls and evidence into each phase, learn about useful templates and tools, and read practical tips to overcome common challenges. I speak from experience: Konfirmity has delivered more than 6 000 audits over the past decade, and our team of specialists has seen what works and what fails. Our managed approach combines human expertise with continuous monitoring so that clients can “start with security and arrive at compliance” year‑round.
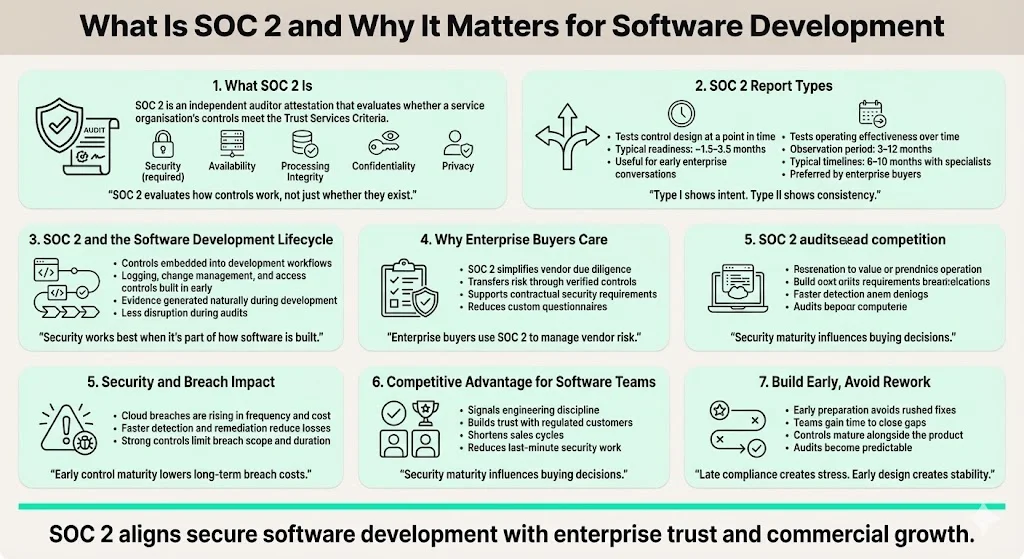
What is SOC 2 and why it matters for software development
SOC 2 is an attestation report, issued by independent auditors, that evaluates whether a service organization’s controls meet the Trust Services Criteria: security, availability, processing integrity, confidentiality and privacy. Security is mandatory for every SOC 2 report; the other four criteria are optional but increasingly expected, especially by enterprise customers and regulated industries.
There are two report types. A Type I report assesses the design of controls at a point in time and can be completed in a few months. Practitioners like EasyAudit estimate Type I readiness at roughly 1.5 – 3.5 months. A Type II report tests whether controls operate effectively over an “observation period,” typically three to twelve months; overall timelines commonly range from 6 – 10 months with specialist auditors or 9 – 14 months with regional firms. These windows align with our own delivery patterns. We often complete SOC 2 readiness in about four to five months by embedding controls into the SDLC and maintaining them throughout the observation period. Self‑managed efforts, by contrast, often take nine months or more because teams must build processes from scratch and collect evidence manually.
Why should software teams care? First, cloud breaches are increasing in frequency and cost. When 62% of organizations suffer supply‑chain disruptions and 89% expect audit findings related to third‑party risk they cannot promptly resolve, companies that demonstrate strong controls gain a competitive advantage. Second, enterprise buyers use SOC 2 reports as a risk‑transfer mechanism; they allow procurement teams to evaluate whether a vendor’s security posture meets contractual requirements. Finally, an SDLC anchored in SOC 2 principles produces resilient systems. Reducing vulnerabilities and remediating issues early lowers breach costs—as IBM’s 2025 report showed, breaches contained within 200 days cost $3.87 million on average, versus $5.01 million when containment exceeded 200 days.
Why a secure SDLC matters for SOC 2
A secure SDLC weaves security into every stage of software development. Instead of treating compliance as an afterthought or a once‑a‑year exercise, it embeds risk assessment, secure design, coding standards, testing and monitoring into daily work. Cobalt’s secure SDLC guidance stresses that risk assessments and threat modeling should occur in the planning and design phases, not just before deployment. Digital Maelstrom likewise highlights that risk assessment is the first step and must be revisited regularly. Embedding controls early supports continuous compliance and risk management.
SOC 2 compliance encourages this integration. Auditors look for evidence that organizations “define, implement and prove” their processes across an observation period. When secure practices live inside the SDLC—backed by tooling and human oversight—compliance becomes a byproduct of good engineering rather than a bureaucratic burden. The result is less friction during audits, fewer urgent fixes, and stronger trust with customers.
Core SOC 2 requirements that affect the SDLC
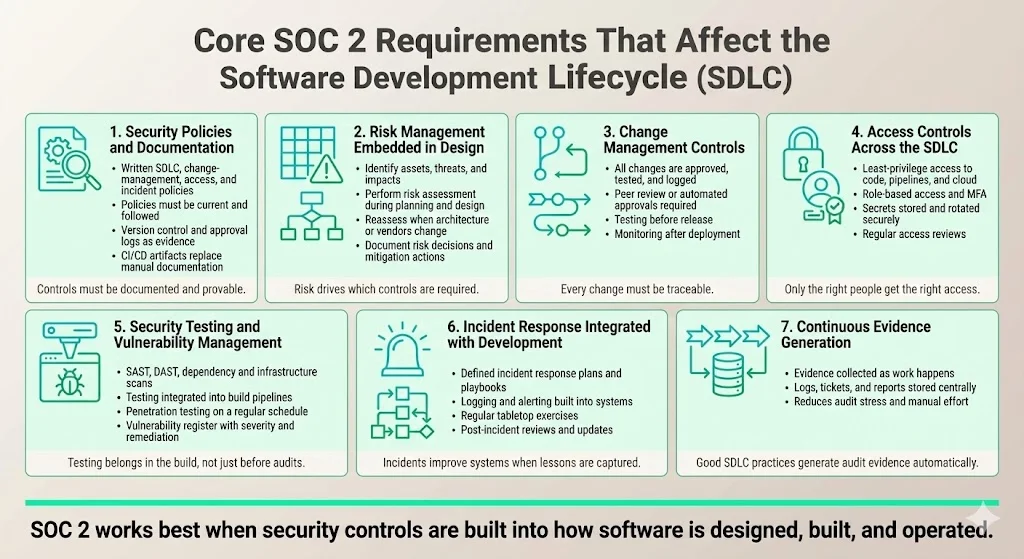
1. Security policies and documentation
Well‑defined policies are the foundation of any SOC 2 program. Onspring notes that security controls—such as authentication, role‑based access and encryption—are non‑negotiable. Auditors expect to see a software development policy, change‑management policy, access control policy and incident response plan (we’ll discuss each of these below). Sikich’s 2025 report on common SOC 2 pitfalls warns that insufficient documentation can lead to compliance gaps; teams must keep policies up to date and demonstrate how controls are implemented and monitored.
Beyond documentation, organizations should use version control and review logs to evidence adherence. For example, a change‑management policy may require that every production deployment has an approved pull request with peer review. Collecting these artifacts automatically (e.g., via Git hooks or CI/CD integrations) ensures they are available for the auditor without manual work.
2. Risk management
Risk assessments underpin SOC 2. They help teams prioritize security requirements, allocate resources and justify controls. A risk assessment identifies assets, threats, vulnerabilities and potential impacts; it then guides decisions about mitigation measures. Secure SDLC guidance emphasizes that risk assessments should happen during planning and design and continue throughout the lifecycle. Every time the business model, architecture or threat landscape changes, the assessment should be revisited.
For example, adding a third‑party API may introduce new data flows and potential attack vectors. A risk assessment would examine confidentiality and privacy risks, identify relevant trust criteria (e.g., confidentiality or privacy), and lead to controls such as input validation, encryption and vendor due diligence. Evidence of risk treatment—such as meeting minutes or risk registers with assigned actions—demonstrates to auditors that the organization actively manages risk.
3. Change management
SOC 2 requires that system changes be authorized, tested and documented. Thoropass describes change‑management elements ranging from identifying and documenting changes to design, development, testing, baseline configuration and emergency procedures. Sikich lists “poor change management” as a common pitfall. To satisfy auditors, teams should adopt a structured process that tracks every change: who proposed it, who approved it, how it was tested, when it was deployed and whether any rollback occurred. This is often implemented through pull requests, issue trackers and deployment logs.
Key practices include:
- Separation of duties — Developers should not approve their own code; peer reviews or automated approval flows enforce this principle.
- Pre‑implementation testing — All changes must be verified in staging environments through automated tests and security scans.
- Post‑implementation monitoring — After deployment, logs and alerts should be monitored to catch regressions quickly.
By automating these steps through the CI/CD pipeline, organizations can demonstrate that changes are traceable and controlled.
4. Access controls
Access control determines who can view or modify code, systems and data. Zluri explains that SOC 2 access controls emphasize the least‑privilege principle, using role‑based access control (RBAC) and multi‑factor authentication (MFA) to restrict access. It notes that controls should cover different trust criteria—security, privacy, confidentiality and processing integrity—by ensuring that only authorized personnel can handle sensitive data. Sikich identifies weak access controls as a common failure; companies must regularly review and update permissions.
In practice, access controls intersect with the SDLC through tools like Git, CI/CD platforms and cloud providers. Access to repositories and build pipelines should be granted via least privilege and documented through identity providers (SSO) with MFA. At runtime, secrets should be stored in vaults and rotated regularly. Quarterly access reviews should verify that inactive accounts are removed and that engineers’ roles match their current duties.
5. Security testing and vulnerability assessment
Regular testing is essential to uncover vulnerabilities before they become incidents. Linford & Company points out that SOC 2 criteria CC7.1, CC4.1 and CC4.2 call for procedures to detect and monitor vulnerabilities and to evaluate and communicate results. That means organizations must define how often they run static application security testing (SAST), dynamic testing (DAST), dependency scanning, penetration testing and infrastructure scans. They must also assign severity ratings, document remediation timelines and communicate results to stakeholders.
To align testing with the SDLC, incorporate automated scans into the build pipeline so that vulnerabilities are caught during development. Conduct regular penetration tests (at least annually) and threat modeling exercises to find design flaws. Maintain a vulnerability register that records findings, severity, planned remediation and evidence of closure. This register becomes audit evidence.
6. Incident response
An incident response program ensures that breaches or system failures are detected, reported and resolved promptly. Fractional CISO notes that SOC 2 requires organizations to plan, report, test and improve their incident response capabilities. Plans should detail logging and monitoring, define who reports incidents and outline escalation paths. The program must be tested annually and continually improved based on lessons learned.
Integrate incident response into the SDLC by:
- Defining playbooks for different incident types (e.g., data breach, service outage, denial‑of‑service attack).
- Logging and alerting — Build instrumentation into your code and infrastructure to detect anomalies. Ensure logs are retained and protected.
- Training — Conduct tabletop exercises so that developers and operations staff know their roles.
- Post‑mortems — After incidents, hold blameless reviews to identify root causes and update controls and documentation.
Evidence of incident response includes incident tickets, timelines, communications, root‑cause analyses and remediation actions.
Secure SDLC steps for SOC 2 compliance
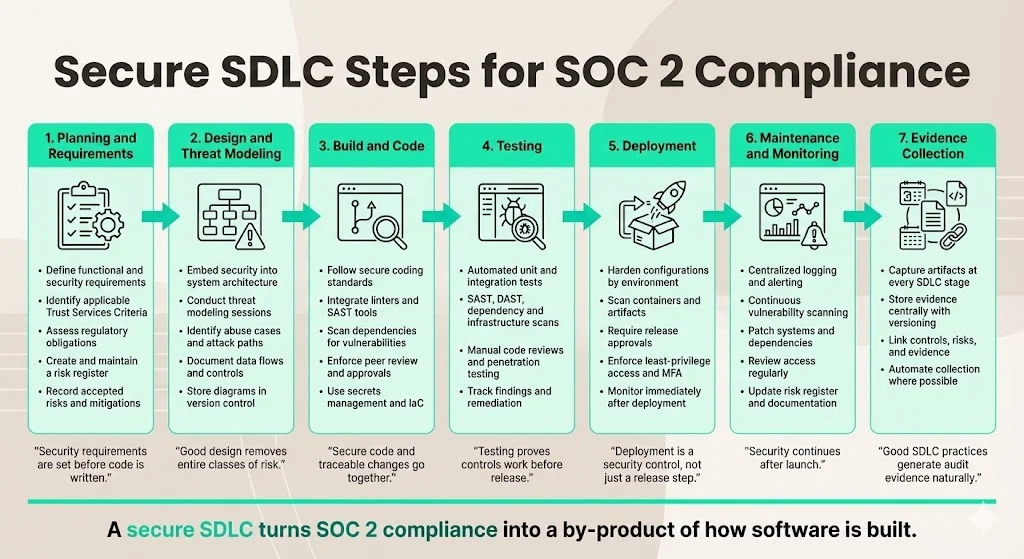
1) Planning & requirements
Begin every project by documenting both functional and security requirements. Identify the Trust Services Criteria that apply (security is mandatory; availability, confidentiality, processing integrity and privacy may apply depending on your industry and contractual obligations). Assess risks associated with the product or feature: What data will be processed? What regulatory obligations (HIPAA, GDPR, etc.) apply? Use a risk register to prioritize threats and define mitigating controls. Plan for privacy by design if personal data is involved.
Engage stakeholders from engineering, security, compliance and legal early. Cross‑functional planning ensures that security requirements are aligned with business goals. Document accepted risks and mitigation plans and store them in a central repository; auditors will want to see that decisions were deliberate.
2) Design & threat modeling
In the design phase, embed security principles into architecture diagrams. Threat modeling workshops help teams anticipate abuse cases, injection points and escalation paths. Cobalt’s secure SDLC guide recommends using frameworks like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) to map threats and controls. Align design decisions with the identified Trust Services Criteria: for instance, adopt encryption (confidentiality), redundancy (availability) or transaction logging (processing integrity). Document data flows and security controls and maintain diagrams in version control for traceability.
3) Build & code
During development, enforce coding standards that address common vulnerabilities—input validation, output encoding, proper authentication and secure error handling. Integrate linters and SAST tools into the developer workflow so that insecure patterns are flagged early. Use dependency scanning to identify vulnerable libraries. Structure work through pull requests; require peer reviews and security sign‑offs. These practices both improve code quality and create a clear audit trail of who changed what and when.
Adopt secrets management to prevent credentials from being hard‑coded. Manage infrastructure as code (IaC) to ensure configuration is reviewed and version controlled. For regulated data (e.g., health information), implement field‑level encryption and redaction; maintain audit logs for all data access.
4) Testing
Testing should include functional verification and security validation. Automate unit tests, integration tests and acceptance tests. Incorporate SAST, DAST, software composition analysis and infrastructure scans into the CI/CD pipeline. Perform manual code reviews and penetration tests to find issues automated tools miss. Capture test results and link them to requirements and risk registers. When a test fails, track the remediation and retest outcome as evidence.
5) Deployment
When deploying, apply configuration hardening and enforce environment‑specific secrets. Use container security best practices (minimal base images, no root user) and scan images before deployment. Implement release approvals and change logs. Access to deployment tools should require least privilege and MFA. Use environment variables and parameter stores for secrets. Post‑deployment, monitor metrics and logs to detect anomalies quickly.
6) Maintenance & monitoring
Once software is in production, continuous monitoring becomes essential. Deploy log aggregation and alerting systems to track unusual behaviour. Use vulnerability scanners to check for misconfigurations and outdated packages. Perform regular patch management and infrastructure updates. Review access rights quarterly and adjust as roles change. Monitor third‑party dependencies for new vulnerabilities. Keep the risk register and documentation current so that auditors can see ongoing governance.
7) Evidence collection
Collecting evidence as you work makes audits less disruptive. Each stage of the SDLC should produce artifacts—risk assessments, design diagrams, pull requests, test reports, deployment logs, incident tickets. Store these artifacts in a centralized system with timestamps and versions. DSALTA’s 2025 unified compliance checklist highlights the importance of automating evidence collection and notes that linking controls, evidence and frameworks can reduce audit preparation time by over 60%. When auditors arrive, you can supply evidence without scrambling.
Mapping SOC 2 controls into SDLC phases
Mapping SOC 2 controls to SDLC phases helps ensure that every trust criterion is addressed at the right time. Below is a conceptual mapping (not exhaustive) that illustrates how controls fit within the lifecycle:
This approach draws on the idea from unified compliance platforms that each stage serves as a checkpoint for collecting defensible evidence. By tying controls and artifacts to SDLC phases, you can trace how each requirement is met.
Templates and practical tools
Policy templates
You don’t need to start from scratch. Many organizations use templates to accelerate policy creation and ensure completeness. Typical templates include:
- SDLC policy — Describes the phases of your development lifecycle, roles and responsibilities, risk assessment cadence, secure coding requirements and evidence expectations.
- Change‑management policy — Outlines how changes are proposed, reviewed, tested and deployed. It should address emergency changes and rollback procedures.
- Access control policy — Defines account provisioning, least privilege, MFA requirements, periodic access reviews and termination procedures.
- Incident response plan — Provides logging and monitoring requirements, incident classification, escalation paths, communication plans and post‑incident review. Fractional CISO highlights the need to test the plan and continually improve.
These templates serve as starting points; tailor them to reflect your actual processes and technology rather than copying generic policies that auditors may reject.
Process and evidence templates
Beyond policies, process templates help operationalize the secure SDLC. Examples include:
- Secure SDLC playbook — A step‑by‑step guide that defines tasks, checkpoints and evidence for each SDLC phase. It may include threat modeling worksheets, code review checklists and release approval forms.
- Evidence collection checklist — Lists artifacts to capture (risk assessments, training records, test reports, change approvals) and associates them with trust criteria. DSALTA’s universal checklist emphasises evidence collection as a core control.
- Access review worksheet — Used quarterly to confirm that user privileges match role requirements and that inactive accounts are removed.
- Incident report template — Captures the timeline, impact, root cause and remediation actions for each incident, fulfilling SOC 2 incident response expectations.
Practical tools to support these templates include version control systems (Git), ticketing systems (Jira), automated scanning tools, logging and monitoring platforms, and compliance management solutions that centralize evidence and map controls across frameworks.
Best practices for SOC 2 Secure SDLC
Organizations selling to enterprise clients or handling regulated data can enhance their SOC 2 Secure SDLC by adopting the following practices:
- Continuous monitoring instead of periodic checks — Attackers adapt quickly; waiting until the next audit or annual penetration test leaves gaps. Integrate real‑time logging, alerting and vulnerability scanning into daily operations. IBM’s report shows that shortening the detection window reduces breach costs.
- Security training for developers — Code is written by humans. Educate teams on secure coding patterns, common vulnerabilities and privacy requirements. Sikich notes that neglecting employee training is a key pitfall. Include secure coding guidelines, threat modeling sessions and incident response drills.
- Automation for compliance and evidence — Use CI/CD pipelines, infrastructure‑as‑code and compliance tools to enforce policies and collect evidence automatically. DSALTA’s research shows that linking controls and evidence across frameworks can reduce audit preparation time by 60%.
- Link SDLC artifacts to controls — Tag each pull request, ticket and test result with the relevant trust criterion. This creates an audit trail and simplifies cross‑framework compliance. For example, a pull request for a new feature might map to security (authentication changes) and processing integrity (input validation).
- Centralize vendor risk management — Supply‑chain disruptions are rising. Maintain an inventory of third‑party vendors, perform risk assessments and require SOC 2 or equivalent assurances. Automate vendor questionnaires and track remediation actions.
- Use dedicated expertise — Compliance manufacturing promises two‑week certificates but overlooks the observation period and the complexity of control implementation. Konfirmity’s managed service pairs clients with dedicated security and compliance experts. Our specialists implement controls inside your stack, run continuous monitoring and prepare audit evidence year‑round. Clients typically spend about 75 hours per year on compliance tasks, compared with 550–600 hours in self‑managed programs. In a world where time is expensive and expertise is scarce, a human‑led managed service delivers better outcomes than generic software alone.
Challenges and how to overcome them
Implementing a SOC 2 Secure SDLC is not without obstacles. Below are common challenges and ways to address them:
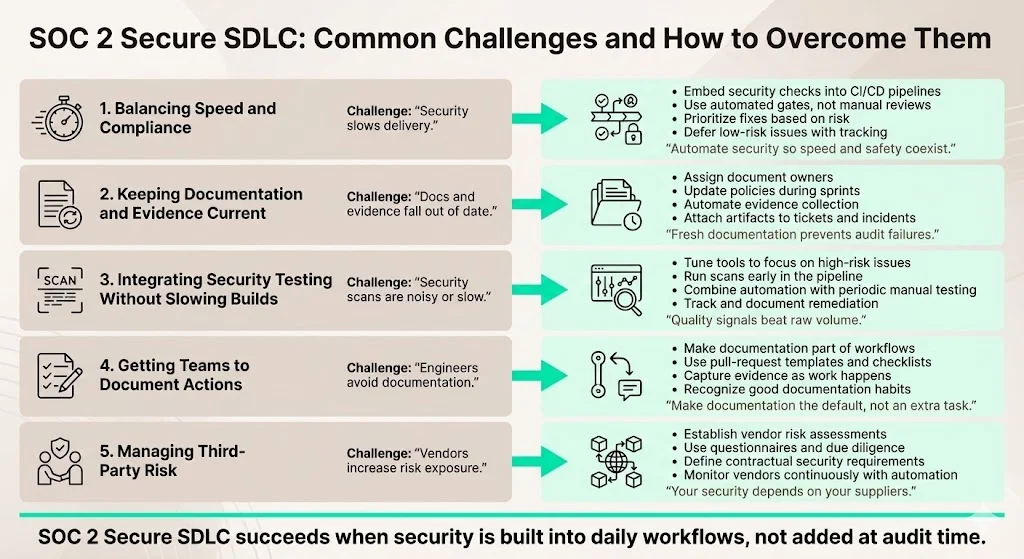
1) Balancing speed and compliance
Engineering teams often feel that security slows them down. Yet unaddressed vulnerabilities lead to breaches and long‑term delays. Adopt an agile security model: embed automated checks into pipelines so that security gates are part of the workflow rather than separate steps. Use risk‑based prioritization so that critical issues are fixed first and low‑risk issues are scheduled later.
2) Maintaining documentation and evidence
Documentation can quickly become stale, and manual evidence collection is tedious. Integrate policy updates into regular sprints, assign owners for each document and automate evidence capture through tools. Sikich cautions that insufficient documentation is a common SOC 2 failure. Use centralized repositories and require attachments of artifacts to change tickets and incidents.
3) Integrating security testing without slowing delivery
Automated scanning tools sometimes produce false positives or slow builds. Tune tools to focus on high‑risk vulnerabilities and integrate them early in the pipeline. Combine automated tools with periodic manual penetration testing and threat modeling to catch logic flaws. Document results and remediation actions for audit readiness.
4) Getting teams to document actions
Engineers may see documentation as extra work. Make it part of the workflow: require pull request templates that include risk assessments, and use checklists to capture evidence. Recognize and reward thorough documentation. Over time, this habit reduces scramble during audits.
5) Managing third‑party risk
Third‑party incidents and supply‑chain disruptions are rising. Create a vendor risk program that includes due diligence, security questionnaires, contractual requirements (e.g., confidentiality clauses and service level agreements), and ongoing monitoring. Use automation to track vendor responses and reminders. DSALTA’s universal checklist includes vendor risk management as a core control.
Avoiding common SOC 2 pitfalls
Sikich’s analysis identifies pitfalls that derail compliance: inadequate scoping, generic policies, weak access controls, inadequate monitoring, skipping risk assessments, poor change management, overlooking vendor compliance and ignoring incident response. Address these by clearly defining audit scope, customizing policies to your environment, enforcing least privilege, implementing comprehensive logging, performing regular risk assessments, formalizing change management, vetting vendors and testing incident response plans.
Conclusion
A SOC 2 Secure SDLC is not just a checklist; it’s a disciplined approach to building and operating software that stands up to buyers, auditors and attackers alike. By embedding security and compliance into every phase—from planning through maintenance—you reduce risk and produce reliable evidence. A secure SDLC yields tangible benefits: shorter sales cycles because procurement teams see real controls; fewer audit findings because evidence is continuous; and lower breach costs through early detection and remediation. Enterprises that invest in durable controls and continuous monitoring build trust with customers and regulators. Superficial compliance may satisfy a questionnaire, but only a well‑designed, operational security program delivers lasting protection and business growth.
FAQs
1. What is a “SOC 2 Secure SDLC”?
It’s an SDLC in which security controls and documentation are integrated to satisfy SOC 2 requirements. Instead of treating compliance as an external task, teams embed risk assessment, secure design, coding standards, testing, access control, change management and incident response into daily work. The outcome is a software development process that produces continuous evidence for auditors and reduces the likelihood of breaches.
2. Do I need templates to be SOC 2 compliant?
Templates aren’t strictly required, but they help ensure consistency, completeness and audit readiness. Policy templates for change management, access control and incident response provide a starting point. Process and evidence templates, such as secure SDLC playbooks and evidence checklists, guide teams through required steps and prompt them to collect artifacts. Avoid generic templates that do not reflect your actual processes—Sikich warns that relying on off‑the‑shelf policies can create a false sense of compliance.
3. How does a secure SDLC support audit readiness?
By embedding controls into the lifecycle, the SDLC produces evidence as a by‑product of normal work. Risk registers, design diagrams, pull requests, test results, deployment logs and incident reports show auditors that controls operate effectively over time. Automated evidence collection and mapping tools can reduce audit preparation time by more than 60%. This continuous evidence eliminates the scramble to produce artifacts at the end of the observation period.
4. Can a SOC 2 Secure SDLC integrate with DevOps or DevSecOps processes?
Yes. Modern DevOps and DevSecOps practices align perfectly with SOC 2. Continuous integration and delivery pipelines provide natural hooks for automated security testing, change management and evidence capture. Infrastructure‑as‑code ensures that configurations are version controlled and auditable. A DevSecOps culture—where developers, security and operations collaborate—makes it easier to embed controls without impeding velocity. The NIST Secure Software Development Framework (SSDF) supports this approach by offering a common language for secure development practices and encouraging a risk‑based, outcome‑oriented process.





.svg)






.svg)
.svg)