Enterprise procurement now hinges on more than a signed security questionnaire. Buyers want to see that you operate a living security program, not one‑time documentation. SOC 2 vulnerability management is where this rigor begins. By proactively discovering and fixing software and configuration flaws, you protect customer data, satisfy regulatory demands, and shorten sales cycles. This article explains the core elements of SOC 2 vulnerability management, shows how they map to the Trust Services Criteria, and provides templates, evidence expectations, and best practices learned from thousands of engagements.
What Is SOC 2 Vulnerability Management?
Vulnerability management is a continuous process that finds, rates, fixes, and verifies weaknesses in your technology stack. The NIST vulnerability management framework describes six core activities: identification through scanning and monitoring, assessment using risk‑based scoring systems such as the Common Vulnerability Scoring System (CVSS), mitigation through patching or configuration updates, remediation to remove weaknesses, verification via follow‑up scans, and continuous monitoring for new vulnerabilities. When implemented for SOC 2, this process supports trust criteria by creating evidence of risk assessment, control design, and remediation. It isn’t a one‑time exercise; it is built into day‑to‑day operations.
In practical terms, vulnerability management means inventorying your assets, running regular scans to identify missing patches or misconfigured settings, scoring each finding based on severity and business impact, applying updates or configuration changes, and tracking remediation progress. It also means adjusting priorities based on real risks, verifying fixes with follow‑up scans, and documenting all actions so auditors can trace each decision. SOC 2 vulnerability management emphasises continuous evidence across an observation period and ties each step back to control objectives.
How Vulnerability Management Supports SOC 2 Controls
SOC 2 reporting is built around the AICPA Trust Services Criteria. The security criterion (the common requirement for all SOC 2 reports) requires organisations to protect systems and data against unauthorised access, disclosure, or damage. Under the security criteria, control CC7.1 states that entities must employ detection and monitoring procedures to identify configuration changes that may introduce new vulnerabilities and to recognise susceptibility to newly discovered threats. CC7.1’s points of focus call for defined configuration standards, monitored infrastructure and code, change detection mechanisms, identification of unauthorised components, and vulnerability scans performed regularly and after material changes. CC7.2 requires monitoring of system components for anomalies symptomatic of malicious acts or errors and the use of threat intelligence to detect new threats. Even though SOC 2 does not mandate specific tools, these criteria clearly expect ongoing vulnerability identification and remediation.
Vulnerability management also underpins other criteria. Risk assessment (CC3.1 – CC3.3) requires companies to identify and assess risks to their objectives, including risks from unpatched software and misconfigurations. Logical and physical access controls (CC6.1 – CC6.7) and system operations (CC7.3) demand processes to restrict access, monitor events, and resolve deviations. Continuous vulnerability management provides evidence across these areas, showing that you know what weaknesses exist, have assessed the risk to the business, and have taken timely action.
Why Enterprise Buyers Care
Enterprise procurement teams and healthcare partners care about vulnerability management because unaddressed weaknesses can lead to breaches that disrupt services, expose regulated data and trigger penalties. IBM’s 2024 report found the global average cost of a data breach reached $4.88 million — a ten percent increase over the previous year — with business disruption and remediation driving costs. The 2025 report shows the average dropped to $4.44 million globally but remained $10.22 million in the United States and multi‑environment breaches cost an average of $5.05 million and took 276 days to contain. These figures illustrate the financial stakes. Buyers now ask for vulnerability scan reports, patching policies, and remediation logs as part of due diligence. A robust program shortens procurement cycles because it demonstrates that you can protect their data and meet incident response obligations.
Core Components of SOC 2 Vulnerability Management
A mature program combines multiple disciplines. Each contributes different evidence to the SOC 2 audit and to enterprise questionnaires.
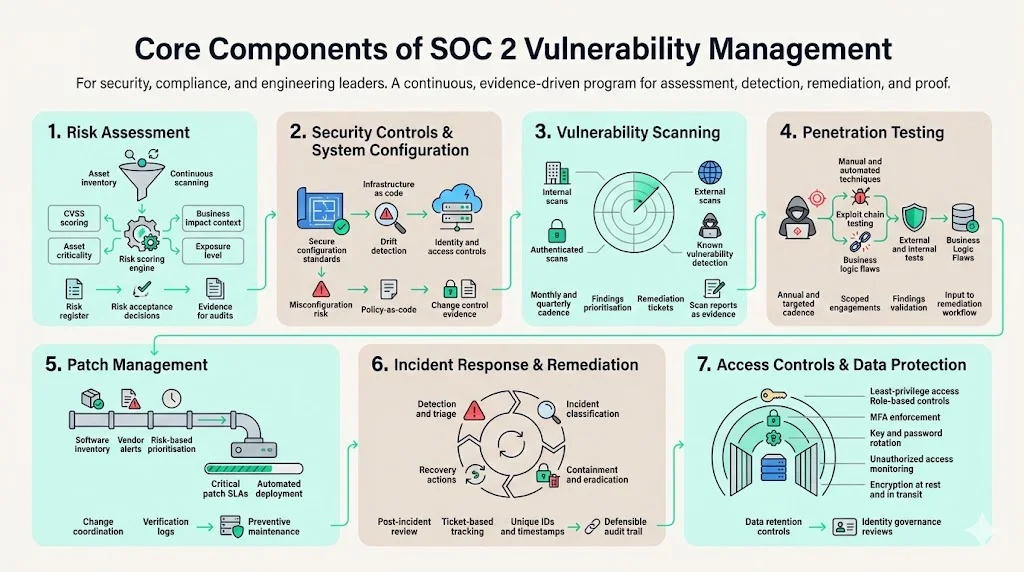
1. Risk Assessment
Risk assessment is the foundation of vulnerability management. You start by understanding what could go wrong and what matters most. The NIST framework emphasises asset inventory and continuous scanning, followed by rating each finding based on CVSS and contextual business impact. RA‑3 and RA‑5 controls in NIST SP 800‑53 require organisations to assess and continuously scan for known vulnerabilities regularly and after significant changes. In practice you maintain a live inventory of servers, containers, databases, and services, then use scanners to identify weaknesses. Each finding is assigned a severity score; however severity alone does not drive decisions. You must factor in asset criticality, exposure (public‑facing vs internal), and potential impact on customers.
Risk assessment also looks beyond technical flaws. Business owners and security teams evaluate the risk of data loss, operational downtime, contractual penalties, and regulatory fines. This evaluation informs risk acceptance decisions and remediation timelines. A risk register and a Statement of Applicability (for organisations that also pursue ISO 27001) demonstrate that risks have been identified, assessed, and addressed.
2. Security Controls & System Configuration
The design and configuration of your systems can either reduce or amplify vulnerabilities. The SOC 2 criteria expect defined configuration standards, monitoring of infrastructure and code repositories, and change detection mechanisms. Misconfiguration is one of the most common causes of breaches. A 2024 Gartner report predicted that more than 99 percent of cloud breaches through 2025 would be caused by preventable misconfigurations. Seventy‑four percent of organisations had publicly exposed storage buckets. Inadequate identity and access management is also a leading cause of cloud breaches; issues include overly permissive access controls, lack of multi‑factor authentication and insufficient monitoring. To address these risks, you set baseline configurations (for example, hardened virtual machine images, secure container registries, infrastructure‑as‑code templates) and continuously compare running systems against them. Tools such as configuration management platforms and policy‑as‑code frameworks automate detection of drift. When deviations occur, you assess the risk and remediate quickly. Documented change control and configuration management processes form part of the evidence.
3. Vulnerability Scanning
Vulnerability scanning uses automated tools to detect known weaknesses in systems and applications. SOC 2 does not prescribe specific tools, but CC7.1 expects entities to conduct vulnerability scans periodically and after significant changes and to remediate identified deficiencies. There are two main types of scans:
- Internal scans operate from inside your network to identify vulnerabilities accessible to insiders. They uncover missing patches, outdated libraries, and misconfigured services.
- External scans originate from outside the network and simulate attacker perspectives, finding open ports, insecure protocols, deprecated services, and other publicly accessible weaknesses.
You may also perform authenticated scans, where the scanner logs into servers or applications to provide a deeper view of software versions and configuration settings. Scans should run at least monthly for internet‑facing assets and quarterly for internal systems, but frequency depends on risk and change velocity. You should always run a scan after material changes such as infrastructure updates, new deployments, or major code releases.
Scanning is not a one‑off event. After each run, you review the findings, correlate them with asset criticality and risk context, assign priorities, and create remediation tickets. Documented scan reports, tool configurations, and remediation records are key evidence during a SOC 2 audit.
4. Penetration Testing
Penetration testing involves security professionals simulating attacks to discover and exploit weaknesses. It complements automated scanning by testing real exploit chains, business logic and multi‑stage paths. Unlike scans, which automate detection of known vulnerabilities, penetration testers use manual techniques and creative thinking to find unknown vulnerabilities. Balbix notes that penetration testing is a simulated cyberattack performed by professionals who combine manual and automated techniques; vulnerability scanning is an automated process that identifies known weaknesses. SOC 2 does not explicitly require penetration testing, but auditors and enterprise customers often expect it for high‑risk systems. CC7.1’s focus on detection and monitoring can be fulfilled through a mix of scanning, continuous security assessments, and penetration testing. A typical cadence is annual for external penetration tests and quarterly for internal tests, with targeted tests when major changes occur. You should scope the test, agree on rules of engagement, document findings, and provide a remediation report. Penetration testing findings feed into the vulnerability management workflow, ensuring that exploited weaknesses are prioritised.
5. Patch Management
Patch management closes vulnerabilities by updating software, firmware and operating systems. NIST SP 800‑40 states that enterprise patch management involves identifying, prioritising, acquiring, installing and verifying patches across the organisation and should be considered preventive maintenance. Microsoft’s security team highlights that patch management mitigates vulnerabilities by ensuring systems are consistently updated; they analyse patches based on CVSS severity and other risk factors and deploy them in stages, reporting overdue vulnerabilities to management. Effective patch management reduces attack surface, improves system stability, ensures regulatory compliance and lowers costs. To implement this, you should maintain an accurate inventory of software and operating system versions, subscribe to vendor vulnerability alerts, prioritise patches based on risk, and define service‑level agreements (SLAs) for applying critical and high‑severity updates. Automate patch deployment where feasible and coordinate with change management to avoid service disruptions. Evidence includes patch schedules, change records, and verification logs.
6. Incident Response & Remediation Process
Vulnerability management is only valuable if you act on the findings. A well‑defined incident response plan provides structure for detection, analysis, containment, eradication and recovery. The NIST incident response lifecycle includes preparation, detection and analysis, containment/eradication/recovery, and post‑incident activity. Preparation involves creating an incident response plan, building a trained team, deploying detection tools and establishing communication protocols. During detection and analysis you triage alerts, classify incidents, gather evidence and understand scope. Containment and eradication involve isolating affected systems, removing malicious artefacts, restoring systems, applying patches and monitoring for recurrence. Post‑incident activities include documenting findings, adjusting controls and updating policies. Security teams use incident tickets to record and manage suspected or confirmed events; each ticket includes a unique ID, timestamp, severity classification, description, affected assets and actions taken. Tracking remediation through tickets and dashboards provides a defensible audit trail for SOC 2 and regulatory reporting.
7. Access Controls & Data Protection
Strong identity management and data protection reduce your vulnerability footprint. Misconfigured or overly permissive access rights remain a leading cause of cloud breaches. SOC 2 controls require you to define and enforce least‑privilege access, implement multi‑factor authentication (MFA), rotate keys and passwords, and monitor for unauthorized access. Data at rest and in transit must be encrypted and data retention must follow legal requirements. Implementing role‑based access control, privilege separation, network segmentation and data masking reduces exposure. Identity governance tools can automate provisioning, de‑provisioning and periodic access reviews. Evidence includes access logs, review records, encryption configurations and key management practices. Effective access control also supports other frameworks such as HIPAA (for ePHI), GDPR, and ISO 27001.
How SOC 2 Vulnerability Management Maps to Trust Services Criteria
To satisfy SOC 2, you must demonstrate alignment with the AICPA Trust Services Criteria. The security criterion is mandatory for all SOC 2 reports and includes nine points of focus (CC1 through CC9). Vulnerability management touches each point:
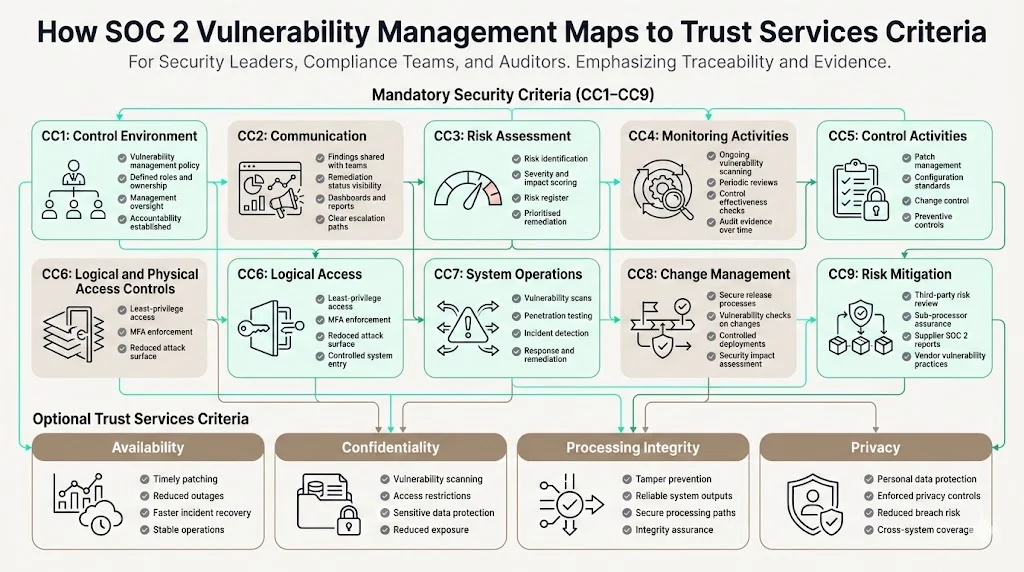
- CC1 – Control environment: establishing accountability and oversight for security. A vulnerability management policy and defined roles show that management has assigned responsibilities.
- CC2 – Communication: ensuring that security policies and procedures are communicated. Vulnerability findings and remediation statuses should be shared with relevant teams through dashboards and status reports.
- CC3 – Risk assessment: identifying and evaluating risks to system objectives. Risk scoring and the risk register demonstrate compliance.
- CC4 – Monitoring activities: evaluating the performance of controls over time. Continuous scanning and periodic internal audits provide evidence.
- CC5 – Control activities: implementing policies and procedures to achieve control objectives. Patch management, configuration standards, and change control illustrate this.
- CC6 – Logical and physical access controls: restricting access to systems and data. Implementing least privilege and MFA reduces vulnerability exposure.
- CC7 – System operations: monitoring system performance and security events, detecting and addressing deviations. Vulnerability scans, penetration tests and incident response fulfil these points.
- CC8 – Change management: developing and maintaining system changes in a controlled manner. Integrating vulnerability management with change processes ensures that releases are assessed for security impact.
- CC9 – Risk mitigation: addressing risks arising from vendors and business partners. Evaluating supplier security (for example, requiring SOC 2 reports from sub‑processors) and ensuring they follow similar vulnerability management practices mitigates third‑party risk.
When you select optional criteria — availability, confidentiality, processing integrity or privacy — vulnerability management supports them. For availability, timely patching and incident response reduce downtime. For confidentiality, scanning and access controls protect sensitive data. For processing integrity, vulnerability management ensures systems produce accurate and reliable outputs by preventing tampering. For privacy, vulnerability management safeguards personal information and shows that privacy controls are enforced across systems.
Formalising Vulnerability Management into Policies
A policy framework codifies how your organisation manages vulnerabilities and provides evidence to auditors and buyers. At minimum you should document:
- Vulnerability management policy: describes roles, responsibilities, scanning and patching cadence, risk assessment methods, and reporting procedures. It should tie back to SOC 2 CC7.1/CC7.2 requirements and incorporate references to NIST and industry best practices.
- Risk assessment procedure: outlines how you identify assets, rate vulnerabilities, assess business impact and decide on remediation timelines. It may include a worksheet or register.
- Vulnerability scanning standards: specify scan types (internal, external, authenticated), frequency, tools, and reporting format. Include a requirement to scan after material changes.
- Patch management policy: defines processes for monitoring vendor alerts, prioritising patches based on severity, scheduling deployment, testing, and verifying installation. Include SLAs for applying critical patches (often within 48 hours) and high‑severity patches (within 30 days).
- Incident response plan: explains preparation, detection, analysis, containment, eradication and recovery processes. It should define escalation paths, communication protocols and training requirements.
- System configuration standard: provides baseline configurations for systems, networks, and applications and requires regular reviews to detect drift.
- Access control and data protection policy: sets least‑privilege principles, MFA requirements, encryption standards, and periodic access reviews.
These policies should integrate with your broader information security management system (ISMS) if you pursue ISO 27001 and with privacy frameworks such as HIPAA and GDPR. Cross‑mapping controls reduce duplication of effort and facilitates multi‑framework audits.
Evidence That Auditors Look For
SOC 2 Type II audits assess the operating effectiveness of controls over a six‑ to twelve‑month observation period. Auditors look for documentary evidence that shows you operate your program consistently. Typical artifacts include:
- Scan results and tool configurations: Retain copies of vulnerability scan reports, including dates, scope, tool versions, and severity ratings. Document configurations, scanner settings, and authentication methods.
- Risk assessments and registers: Provide risk assessment worksheets showing asset inventory, vulnerability ratings, business impact and remediation decisions.
- Patch records: Show patch schedules, deployment dates, change approval records and verification logs to demonstrate timely remediation.
- Remediation tickets: Provide tickets or change records that track each vulnerability from identification through remediation and verification. Tickets should include severity, affected assets, due dates, assigned owners, and closure evidence.
- Incident response records: Supply incident tickets, root‑cause analyses and after‑action reports to show how you handled security events. Include evidence of containment, eradication and recovery activities.
- Access logs and reviews: Provide audit logs for critical systems, MFA enforcement records, and evidence of periodic access reviews. Logs should show who accessed what and when.
- Training records: Document security awareness training and role‑specific training for developers and engineers. Evidence that vulnerabilities identified in training sessions are addressed.
- Policies and procedures: Present formalised policies described above along with evidence that they are reviewed annually and communicated to the workforce.
Auditors may request additional evidence based on your environment and any optional trust criteria selected. They may also perform interviews and observe processes. Transparency and readiness reduce audit friction and build buyer trust.
Templates & Practical Assets
Organisations often need structured templates to operationalise vulnerability management. Below is a table summarising common assets and why each matters.
Below is an abstract illustration that conveys the flow of vulnerability management from identification through remediation and evidence collection.
Best Practices for Enterprise‑Grade SOC 2 Vulnerability Management
Delivering SOC 2 vulnerability management at an enterprise level requires discipline, coordination and automation. Based on Konfirmity’s experience supporting more than 6 000 audits, the following practices yield reliable outcomes:
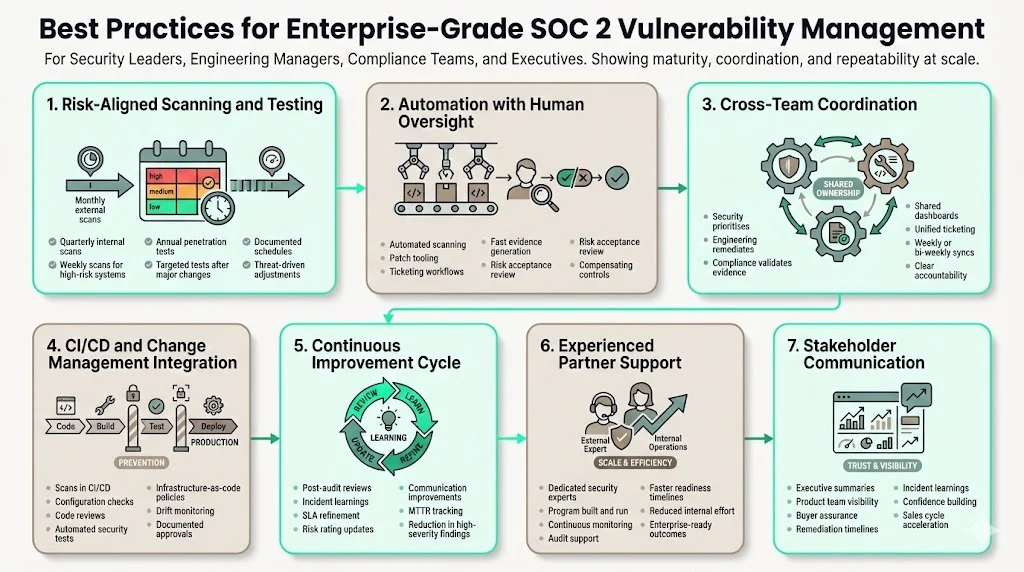
- Perform scans and tests on a cadence aligned with risk. Monthly external scans and quarterly internal scans are common baselines. High‑risk systems or those processing regulated data (e.g., ePHI) may require weekly scans. Penetration tests should occur at least annually for external surfaces and more frequently for critical applications. Always run a scan after significant changes. Document all schedules and adjust them based on emerging threats.
- Automate wherever possible but retain human oversight. Use vulnerability scanners, patch management tools and ticketing platforms to streamline detection and remediation. But decisions about risk acceptance, patch timing and compensating controls require human judgement. Automated tools help produce evidence quickly but cannot replace experienced security analysts.
- Coordinate across security, engineering and compliance teams. Vulnerability management is not solely an IT function. Security identifies and prioritises issues, engineering applies fixes, and compliance ensures that evidence meets audit requirements. Weekly or bi‑weekly meetings keep everyone aligned. Shared dashboards and ticket systems help track progress.
- Integrate with change management and CI/CD pipelines. Incorporate scanning and configuration checks into your development workflow to catch vulnerabilities before they reach production. Enforce code reviews and automated security tests. For infrastructure‑as‑code, apply policy‑as‑code and monitor for drift. Document all changes and approvals.
- Adopt a continuous improvement cycle. After each audit or incident, review what worked and what didn’t. Update policies, adjust SLAs, refine risk ratings and improve communication. Use metrics such as mean time to remediate (MTTR), patch adherence rates, and reduction in high‑severity findings to measure progress. Implement feedback loops to ensure lessons translate into stronger controls.
- Engage experienced partners. Many organisations underestimate the effort required to build and maintain a program. Typical self‑managed SOC 2 readiness can take nine to twelve months and consume more than 550 hours of internal time. With a human‑led managed service like Konfirmity, readiness often takes four to five months and about 75 hours of internal effort because our team builds and runs the program on your behalf. We embed dedicated security and compliance experts, integrate controls into your stack, monitor continuously and provide audit support. This frees your teams to focus on product development while meeting enterprise expectations.
- Communicate progress to stakeholders. Keep executives, product managers and enterprise buyers informed about vulnerability management efforts. Share summary metrics, remediation timelines and incident learnings. Transparency builds confidence and accelerates sales cycles.
Conclusion
Vulnerability management is not just a compliance exercise — it is a core security discipline that protects your business and earns the trust of enterprise customers. SOC 2 vulnerability management ties together risk assessment, configuration standards, scanning, penetration testing, patch management, incident response and access control. When combined with clear policies and evidence, it demonstrates that you operate a living security program rather than manufacturing compliance.
Real security is not achieved by paper controls alone. It requires trained people, tested processes and technology that work together every day. By investing in a human‑led, managed security and compliance service, you can start with security and arrive at compliance, shorten audit timelines and reduce the risk of costly breaches. Enterprise buyers and regulators will see not just that you pass audits, but that you operate secure services.
Frequently Asked Questions
1. Is vulnerability scanning required for SOC 2?
SOC 2 does not explicitly mandate vulnerability scanning, but trust criteria CC7.1 and CC7.2 expect you to identify and monitor changes that could introduce new weaknesses. Regular vulnerability scanning is the most practical way to meet this expectation. Auditors and customers often interpret the criteria as requiring evidence of scanning and remediation.
2. How often should scans be performed?
Frequency depends on risk and change velocity. Monthly external scans and quarterly internal scans are common baselines, but high‑risk systems may require weekly scans. Always scan after major changes such as infrastructure upgrades or significant code releases. Penetration tests should occur at least once per year, and more often if your environment changes quickly.
3. What evidence do auditors ask for?
Auditors seek scan results, tool configurations, risk assessments, patch records, remediation tickets, incident response reports and policy documents. Evidence should cover the entire observation period and demonstrate that you identify, prioritise and resolve vulnerabilities promptly. Logs showing access controls, MFA enforcement and monitoring activities may also be requested.
4. How do you track remediation progress?
Use a ticketing system or a remediation tracking log to record each vulnerability, assign an owner, set due dates and track status. Severity ratings and asset criticality should drive prioritisation. Regular reviews ensure accountability, and dashboards provide visibility into open issues. Incident tickets record actions taken and provide a defensible audit trail.
5. Can automated tools support SOC 2 vulnerability management?
Yes. Vulnerability scanners, patch management platforms, and security orchestration tools automate detection, reporting and remediation. However, human oversight is essential to interpret findings, evaluate risk and decide on remediation timelines. A human‑led, managed service combines automation with expert judgement to deliver consistent outcomes.





.svg)






.svg)
.svg)