Most organizations pursuing SOC 2 compliance treat it as a certification milestone rather than an operational discipline. This approach creates a fundamental gap between audit readiness and actual security posture—a gap that becomes apparent when enterprise procurement teams conduct vendor risk assessments. Gartner projects that 60% of organizations will treat a supplier's security posture as a primary buying criterion by 2025, making the combination of SOC 2 attestation and Zero Trust architecture a strategic differentiator for vendors selling to large enterprises.
This guide explains how implementing Zero Trust principles strengthens SOC 2 compliance, provides step-by-step implementation guidance, and delivers templates designed to accelerate audit readiness for companies targeting enterprise clients.
What is SOC 2?
The SOC 2 framework is based on five Trust Services Criteria—Security, Availability, Confidentiality, Processing Integrity, and Privacy—with Security being the only required criterion for all audits. SOC 2 is an evidence-based attestation developed by the American Institute of Certified Public Accountants (AICPA) that evaluates how service organizations manage customer data.

For vendors selling to enterprise clients, SOC 2 matters because procurement teams require documented proof that your organization implements and maintains effective security controls. Standards such as SOC 2 or ISO 27001 may be required before enterprise customers will agree to do business with you, making this attestation a prerequisite rather than a competitive advantage.
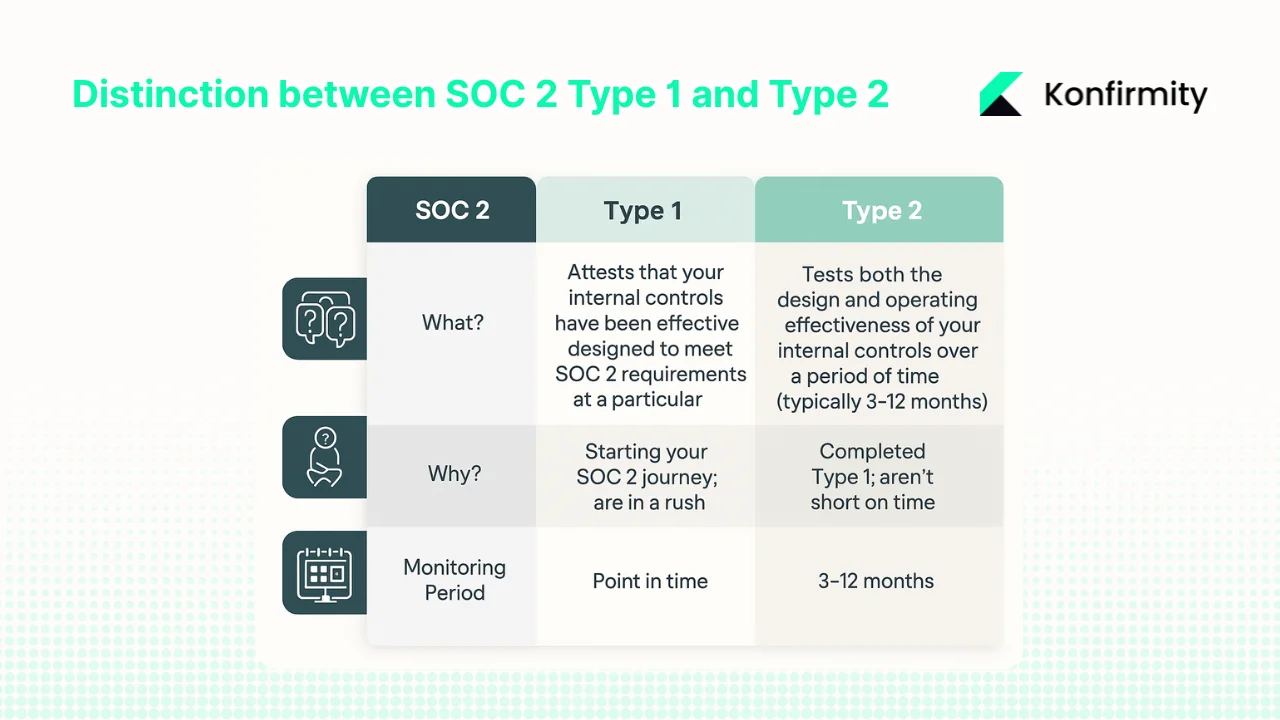
SOC 2 Type 1 vs Type 2
Type 1 affirms an organization's controls are designed effectively. Type 2 affirms the controls are being used effectively. SOC 2 Type 2 compliance is an independent attestation by a licensed CPA firm that verifies your security controls are not only well-designed but also operate effectively over a period of 3 to 12 months. Enterprise buyers overwhelmingly prefer Type 2 reports because they demonstrate operational effectiveness over time, not just point-in-time design.
What is the Zero Trust Model?
Zero Trust operates on the principle of "never trust, always verify"—eliminating implicit trust within network architecture and requiring validation at every access point. A fourth quarter 2023 Gartner survey of 303 security leaders whose organizations had already implemented (fully or partially) or are planning to implement a zero-trust strategy found that 56% of organizations are primarily pursuing a zero-trust strategy because it's cited as an industry best practice.

The Zero Trust model encompasses several core components:
- Identity verification: Continuous authentication of users, devices, and service accounts
- Device posture assessment: Validating security health before granting access
- Least privilege access: Restricting permissions to minimum necessary levels
- Network micro-segmentation: Preventing lateral movement within networks
- Continuous monitoring: Real-time analysis of access patterns and behavior
These principles align directly with risk management, threat mitigation, and network security requirements embedded within SOC 2 controls.
Why "SOC 2 Zero Trust" is a Powerful Pairing
Zero Trust architecture provides the technical foundation that makes SOC 2 compliance operationally sustainable. Rather than implementing controls solely to satisfy auditors, Zero Trust creates a security posture where SOC 2 evidence is a natural byproduct of your operational practices.
This pairing offers three strategic advantages for enterprise-selling vendors:
- Accelerated procurement cycles: Security questionnaires are answered with documented policies, access logs, and architectural diagrams that already exist
- Reduced audit preparation burden: Continuous monitoring generates the evidence trail auditors require
- Demonstrable operational maturity: Enterprise buyers distinguish between vendors with compliance theater versus genuine security infrastructure
Enterprise Zero Trust security model deployments demonstrate measurable improvements in threat detection and incident response, with organizations achieving average reductions of 67% in successful breach attempts following comprehensive Zero Trust implementation. This quantifiable risk reduction resonates with enterprise security teams conducting vendor assessments.
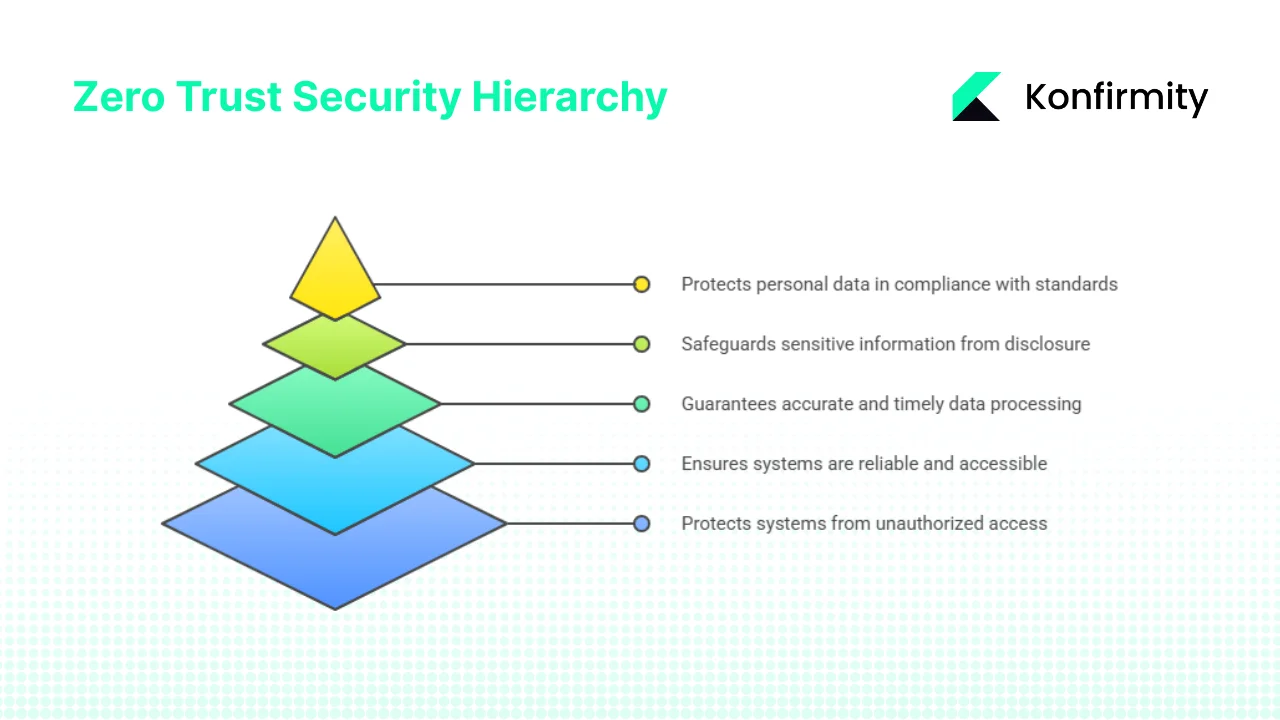
Mapping Zero Trust to the SOC 2 Trust Service Principles
Each Trust Services Criterion can be reinforced through specific Zero Trust practices. This mapping demonstrates to auditors—and enterprise buyers—how your security architecture supports compliance requirements.
1. Security (Mandatory for SOC 2)
Security is the only Trust Services Criteria required for every SOC 2 audit. The other criteria can be added to your report scope if your organization chooses, but they are not required to achieve SOC 2 compliance. The Security criterion addresses protecting information and systems from unauthorized access, disclosure, and damage.
Zero Trust reinforces Security through:
- Multi-factor authentication (MFA) at every access point, eliminating reliance on passwords alone
- Least privilege access controls that restrict permissions to business-critical functions
- Device posture checks ensuring only compliant endpoints access corporate resources
- Continuous authentication that re-verifies identity throughout sessions, not just at login
Example: A SaaS vendor implements identity-based access controls requiring MFA plus device certificate validation before employees or customers access production systems. Access logs, MFA enrollment records, and device compliance reports become audit evidence demonstrating control effectiveness over the observation period.
2. Availability
The Availability Criteria determine whether your employees and clients can rely on your systems to do their work. Some examples are data backups, disaster recovery, and business continuity planning.
Zero Trust supports Availability through:
- Continuous system health monitoring detecting anomalous access patterns that indicate potential outages or attacks
- Automated containment isolating compromised segments without disrupting entire systems
- Real-time telemetry providing visibility into workload performance and access behavior
Example: A cloud infrastructure provider uses Zero Trust network access (ZTNA) to monitor service account behavior. When unusual API access patterns are detected outside business hours, automated alerts trigger investigation workflows, preventing service degradation before customers are impacted.
3. Processing Integrity
The Processing Integrity Criteria determines whether a system works properly. Does it perform its intended functions without delay, error, omission, or accidental manipulation?
Zero Trust enhances Processing Integrity by:
- Enforcing controlled workflows where changes require authenticated approvals
- Device verification ensuring only authorized systems can initiate data processing
- Audit trails capturing who initiated processes, when, and from which device
- Change control integration requiring verification before code deployments or configuration changes
Example: A financial services vendor implements role-based access with device posture checks for personnel approving transaction batches. The system logs every approval action with device fingerprint, location, and authentication method—evidence that transaction processing follows documented procedures.
4. Confidentiality
The Confidentiality Criteria evaluates how organizations protect confidential information. I.e., by limiting its access, storage, and use. It can help organizations define which individuals can access what data and how that data can be shared. This ensures that only authorized people can view sensitive information, like legal documents or intellectual property.
Zero Trust protects Confidentiality through:
- Data encryption at rest and in transit, with key management tied to identity
- Network segmentation isolating confidential data in separate zones
- Identity-driven access policies granting access based on role, device, and context
- Continuous verification re-checking authorization throughout data access sessions
Example: A multi-tenant SaaS platform uses micro-segmentation to isolate customer data environments. Access to each tenant's confidential information requires not just valid credentials but also device compliance verification and IP allowlisting, with all access events logged for audit review.
5. Privacy
This TSC looks at how an organization's control activities protect customers' personally identifiable information (PII). It also ensures that a system that uses personal data complies with the AICPA's Generally Accepted Privacy Principles. Name, physical address, email address, and Social Security number are a few examples of information that falls under this privacy category.
Zero Trust supports Privacy by:
- Granular access controls limiting PII exposure to specific roles
- Contextual policies restricting PII access based on device security posture and location
- Comprehensive audit trails documenting who accessed PII, when, why, and from where
- Data minimization through least privilege, reducing PII exposure across the organization
Example: A healthcare technology vendor restricts access to protected health information (PHI) through role-based policies combined with device health validation. Access from unmanaged devices is denied, and all PHI queries generate audit logs mapping to specific business justifications, satisfying both HIPAA and SOC 2 Privacy requirements.
Practical Step-by-Step Implementation Guide
Most organizations achieve SOC 2 readiness in 4-5 months when implementing Zero Trust principles concurrently, compared to 9-12 months with traditional control implementation. The following roadmap provides actionable steps, examples, and references to supporting templates.
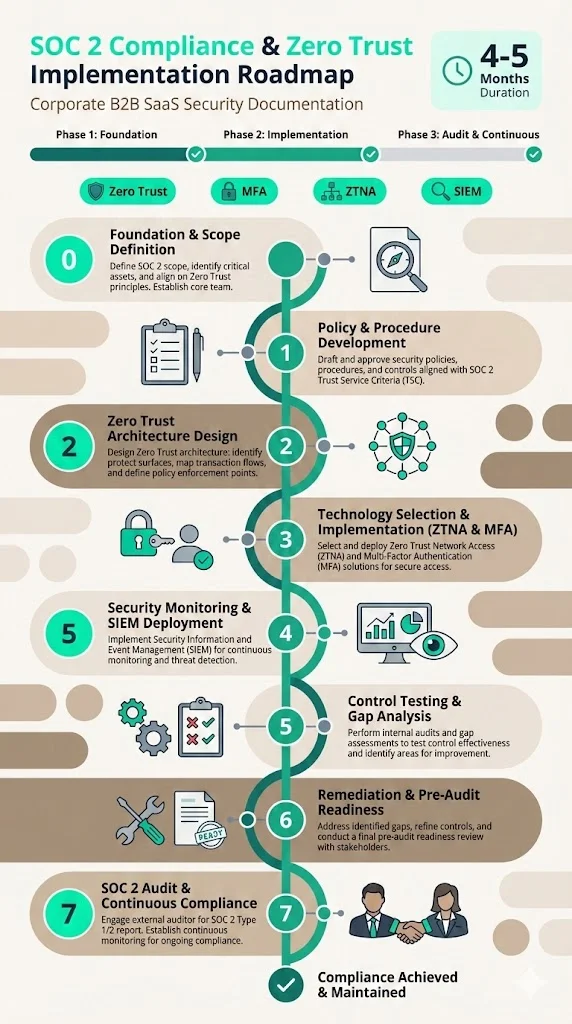
Step 0: Define Scope and Objectives
Before implementing controls, define which services, applications, and infrastructure components fall within your SOC 2 audit scope.
Actions:
- Identify systems that process, store, or transmit customer data
- Determine which Trust Services Criteria apply based on enterprise client requirements
- Document business drivers (e.g., specific enterprise prospects requiring SOC 2 Type 2)
Example: A B2B SaaS company selects its core application, customer database, and authentication services as in-scope. Based on customer contracts, they pursue Security (mandatory), Availability, and Confidentiality criteria.
Template: Scope Definition Worksheet documenting in-scope systems, applicable TSC, business justification, and stakeholder approval.
Step 1: Inventory Assets, Identities, and Data Flows
Zero Trust requires comprehensive visibility into what you're protecting. Without an accurate inventory, you cannot apply appropriate access controls or demonstrate control effectiveness to auditors.
Actions:
- Catalog all users, service accounts, devices, and third-party integrations
- Map data flows showing how information moves between systems
- Classify data sensitivity (public, internal, confidential, restricted)
- Document network architecture including cloud resources and on-premises infrastructure
Example: An infrastructure-as-a-service vendor maps all API service accounts, employee devices, contractor access points, and customer-facing systems. Data flow diagrams illustrate how customer data moves from ingestion through processing, storage, and eventual deletion.
Template: Asset and Data Flow Mapping Matrix capturing identity types, endpoint inventory, data classification labels, and architectural diagrams.
Step 2: Define Zero Trust Policies
Establish the policies governing who can access what, under which conditions, and with what level of privilege.
Actions:
- Define roles and associated permissions using least privilege principles
- Establish device posture requirements (OS versions, patch levels, endpoint security)
- Document MFA requirements for different access scenarios
- Create network segmentation policies separating production, development, and administrative environments
Example: A cloud analytics platform mandates MFA plus device compliance checks for production system access. Contractors receive time-limited access scoped to specific projects. Administrative access to infrastructure requires additional approval workflows and session recording.
Template: Access Policy Framework Document outlining identity requirements, device standards, network segmentation rules, and exception processes.
Step 3: Implement Identity Verification and Access Controls
Identity becomes your security perimeter under Zero Trust. Implementing strong authentication and authorization mechanisms is foundational to both Zero Trust and SOC 2 compliance.
Actions:
- Deploy enterprise identity provider supporting MFA and SSO
- Implement least privilege access through role-based access control (RBAC)
- Enforce device posture checks before granting access
- Establish access review processes (quarterly recommended)
- Issue machine identity certificates for service accounts and APIs
Example: A fintech vendor implements passwordless authentication using FIDO2 keys for employees and MFA for customers. Service accounts use mutual TLS certificates rather than static API keys. Access reviews occur quarterly, with automated de-provisioning for inactive accounts.
Template: Access Control Implementation Checklist covering identity provider configuration, MFA enrollment, RBAC mapping, device compliance policies, and review schedules.
Step 4: Enforce Network Segmentation and Zero Trust Network Access
Traditional VPNs provide network-level access—once authenticated, users can potentially reach any system. Zero Trust network access (ZTNA) restricts access to specific applications rather than entire networks.
Actions:
- Segment networks into zones (production, staging, development, administrative)
- Implement ZTNA replacing broad VPN access with application-specific connectivity
- Restrict lateral movement between segments using microsegmentation
- Apply context-aware policies considering user role, device posture, and location
Example: A software vendor eliminates VPN access for remote employees and contractors. Instead, ZTNA grants application-level access based on identity and device health. A compromised laptop cannot traverse the network or access adjacent systems—attack surface is minimized.
Template: Network Segmentation Design Template documenting zone architecture, ZTNA implementation plan, firewall rules, and application access policies.
Step 5: Implement Continuous Monitoring and Threat Detection
SOC 2 Type 2 requires evidence that controls operated effectively throughout the observation period. Continuous monitoring generates this evidence while also detecting security incidents in real time.
Actions:
- Deploy Security Information and Event Management (SIEM) or Extended Detection and Response (XDR) platform
- Configure alerting for anomalous behavior (unusual login locations, off-hours access, privilege escalation attempts)
- Establish incident response workflows and escalation procedures
- Define metrics measuring control effectiveness (MFA adoption rate, patch compliance, access review completion)
Example: An enterprise SaaS vendor configures SIEM alerts when service accounts authenticate from unexpected IP addresses or when administrative privileges are used outside change windows. Incident response playbooks define containment, investigation, and remediation steps. Quarterly security reviews analyze trends in access anomalies.
Template: Monitoring and Incident Response Playbook documenting alerting rules, escalation contacts, investigation procedures, and post-incident review processes.
Step 6: Document Controls and Collect Audit Evidence
SOC 2 audits require documented policies, procedures, and evidence demonstrating that controls operated as designed throughout the observation period.
Actions:
- Compile security policies (acceptable use, access management, incident response, change management)
- Organize evidence: access logs, MFA enrollment records, device compliance reports, network diagrams, access review documentation
- Conduct SOC 2 readiness assessment identifying gaps
- Engage licensed CPA firm to conduct audit
- Prepare system description documenting scope, architecture, and control environment
Example: A data platform vendor compiles six months of access logs, quarterly access review records, device compliance reports, and incident response tickets. The system description explains their Zero Trust architecture, identity provider configuration, and network segmentation approach. Evidence demonstrates that controls operated consistently across the observation period.
Template: SOC 2 Readiness Checklist and Audit Evidence Tracker organizing required documentation, evidence location, responsible parties, and gap remediation plans.
Step 7: Maintain and Iterate Continuously
SOC 2 Type 2 is not a one-time certification—enterprise clients expect annual attestations demonstrating sustained compliance. Zero Trust is an operational discipline requiring ongoing refinement.
Actions:
- Schedule quarterly access reviews with automated reminders
- Update security policies annually or when significant changes occur
- Conduct annual network segmentation audits validating firewall rules
- Provide continuous security training for employees and contractors
- Monitor emerging threats and adjust controls accordingly
Example: A SaaS vendor maintains a compliance calendar scheduling quarterly access reviews, annual policy updates, and vulnerability assessments. When new attack techniques emerge, security teams evaluate whether existing Zero Trust controls mitigate the threats or if adjustments are required.
Template: Review Calendar and Continuous Improvement Roadmap documenting recurring activities, responsible owners, and multi-year compliance objectives.
Real-World Examples and Use Cases
Example 1: SaaS Vendor Wins Enterprise Deal
A customer data platform implemented Zero Trust identity controls and network segmentation while pursuing SOC 2 Type 2 certification. During procurement with a Fortune 500 retailer, the vendor provided their SOC 2 report, network architecture diagrams, and access control policies. The documented Zero Trust approach satisfied the retailer's vendor risk assessment within two weeks, compared to competitors who faced months of back-and-forth questionnaires. The deal closed 40% faster than the vendor's typical enterprise sales cycle.
Example 2: Cloud-Native Platform Demonstrates Operational Maturity
A cloud infrastructure provider used Zero Trust micro-segmentation and continuous authentication to protect customer workloads. When pursuing SOC 2 Type 2 certification covering Security, Availability, and Confidentiality criteria, their existing Zero Trust architecture generated the evidence auditors required. Access logs, device compliance records, and network segmentation documentation demonstrated sustained control effectiveness. The audit required 75 hours of internal effort versus typical 200-hour burdens because evidence collection was automated.
Example 3: Managed Service Provider Secures Remote Workforce
A managed security service provider (MSP) implemented ZTNA for contractors and employees accessing customer environments. By replacing VPN access with application-specific connectivity and device posture checks, the MSP achieved SOC 2 Type 2 certification addressing Security, Availability, and Confidentiality. Their Zero Trust approach directly addressed risk management and threat mitigation requirements within customer contracts, differentiating them from competitors still using traditional VPN architectures.
Templates and Resources for Implementation
The following templates support rapid implementation for teams targeting enterprise clients:
- Scope Definition Worksheet: Documents in-scope systems, applicable Trust Services Criteria, business drivers, and stakeholder approvals
- Asset and Data Flow Mapping Matrix: Captures identity inventory, endpoint catalog, data classification, and architectural diagrams
- Access Policy Framework Document: Outlines identity requirements, device standards, network segmentation rules, and exception handling
- Access Control Implementation Checklist: Covers identity provider setup, MFA enrollment, RBAC configuration, device policies, and review schedules
- Network Segmentation Design Template: Documents zone architecture, ZTNA implementation, firewall configurations, and application policies
- Monitoring and Incident Response Playbook: Defines alerting rules, escalation procedures, investigation steps, and post-incident reviews
- SOC 2 Readiness Checklist and Audit Evidence Tracker: Organizes documentation requirements, evidence locations, responsible parties, and gap remediation
These templates reduce the compliance preparation burden, allowing technical teams to focus on implementation rather than documentation creation. Organizations using structured templates typically achieve audit readiness 30-40% faster than those building documentation from scratch.
Positioning for Enterprise Sales Teams
When selling to enterprise clients, security and compliance function as qualifiers—not differentiators. Prospects expect SOC 2 Type 2 attestation as table stakes. However, how you achieved compliance and the operational maturity you demonstrate can differentiate your offering.
Effective messaging for procurement conversations:
"We implement Zero Trust architecture combining continuous identity verification, device posture assessment, and network micro-segmentation. Our SOC 2 Type 2 report demonstrates that these controls operated effectively over a 12-month observation period. Our approach ensures actual security—not just audit compliance."
Evidence to present during vendor risk assessments:
- SOC 2 Type 2 report (provide executive summary for initial review)
- Access control policies documenting MFA requirements and least privilege principles
- Network architecture diagrams illustrating segmentation and ZTNA implementation
- Sample audit logs demonstrating continuous monitoring and alerting capabilities
- Incident response procedures and post-mortem examples
Addressing ongoing compliance expectations:
Enterprise buyers understand that security is continuous. Position your Zero Trust implementation as operational discipline rather than a compliance project. Explain quarterly access reviews, annual policy updates, and continuous monitoring demonstrating sustained commitment to security. This reassures buyers that your security posture won't degrade between audit cycles.
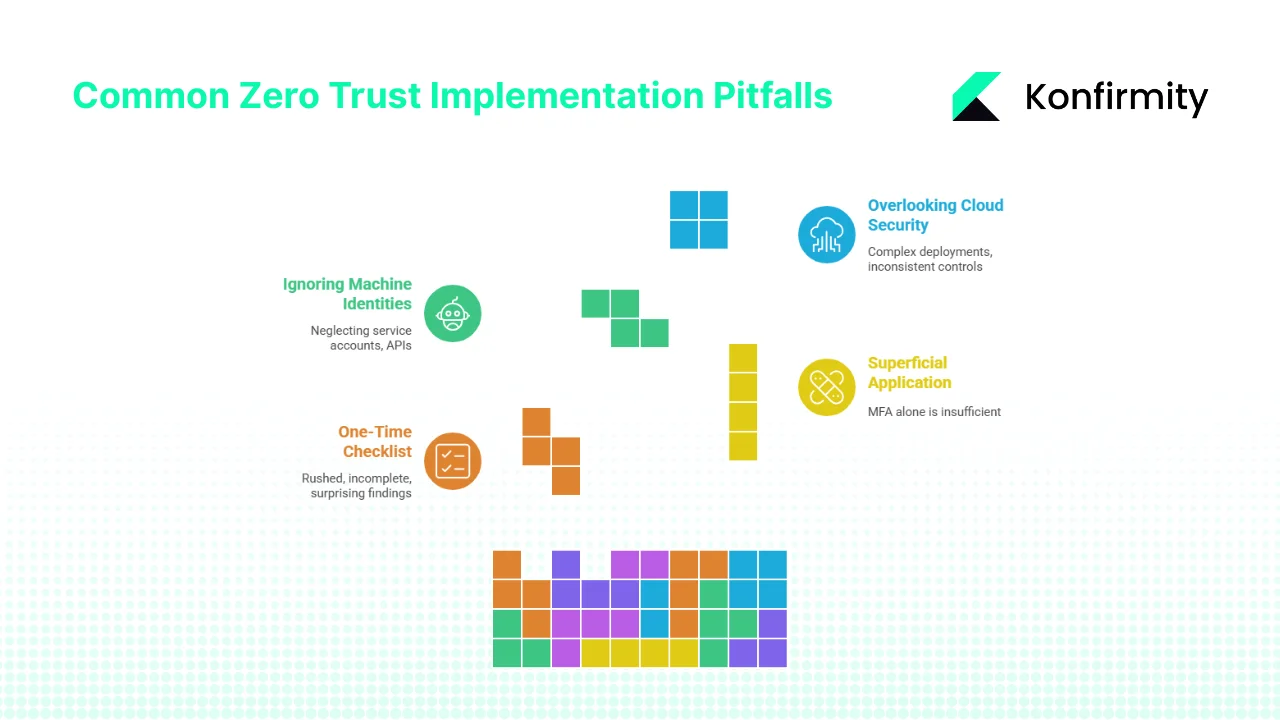
Common Pitfalls and How to Avoid Them
Pitfall 1: Treating SOC 2 as a One-Time Checklist
Organizations approaching SOC 2 as a point-in-time project inevitably face rushed audit preparations, incomplete evidence collection, and surprise findings. Technically, SOC 2 Type 2 reports never expire and are "valid" forever. However, customers want their vendors to have an updated report on at least an annual basis to ensure they can continue to rely on the customers' internal controls.
Solution: Implement Zero Trust as operational practice generating continuous evidence. Automated logging, quarterly access reviews, and continuous monitoring transform compliance from an annual burden into sustained readiness.
Pitfall 2: Applying Zero Trust Superficially
Implementing MFA alone does not constitute Zero Trust architecture. Organizations must also enforce device posture checks, continuous authentication, network segmentation, and least privilege access.
Solution: Follow the step-by-step roadmap addressing identity, devices, network architecture, monitoring, and documentation. Validate implementation completeness through readiness assessments before engaging auditors.
Pitfall 3: Ignoring Machine and Service Identities
Many organizations focus Zero Trust controls on human users while neglecting service accounts, APIs, and machine-to-machine authentication. These non-human identities often have elevated privileges and represent a significant attack surface.
Solution: Inventory all service accounts and API keys. Replace static credentials with machine identity certificates. Apply the same verification and least privilege principles to service identities as human users.
Pitfall 4: Overlooking Cloud Security and Hybrid Architectures
Organizations with complex cloud deployments—spanning multiple providers or hybrid on-premises and cloud infrastructure—face additional challenges mapping data flows and enforcing consistent access controls.
Solution: Use the Asset and Data Flow Mapping Matrix to document multi-cloud architectures comprehensively. Implement identity federation and centralized policy enforcement ensuring consistent controls regardless of resource location.
Conclusion
Combining Zero Trust architecture with SOC 2 compliance creates a security posture where enterprise-grade controls produce attestation-ready evidence as a natural outcome. Organizations implementing Zero Trust principles achieve SOC 2 readiness 40-50% faster while building security infrastructure that actually protects systems rather than merely satisfying auditors.
For vendors selling to enterprise clients, this combination addresses procurement requirements while demonstrating operational maturity. The investment in Zero Trust architecture pays dividends beyond compliance—reducing breach risk, accelerating vendor risk assessments, and shortening sales cycles with security-conscious buyers.
Following the implementation roadmap, using the provided templates, and avoiding common pitfalls transforms security and compliance from obstacles into sales enablers. Start by defining your scope, inventorying assets and identities, establishing Zero Trust policies, and engaging your auditor early. Organizations that approach SOC 2 and Zero Trust as integrated operational disciplines—rather than separate compliance projects—build security infrastructure supporting long-term enterprise growth.
Frequently Asked Questions
1) What are the trust criteria for SOC 2?
The SOC 2 framework is based on five Trust Services Criteria—Security, Availability, Confidentiality, Processing Integrity, and Privacy—with Security being the only required criterion for all audits. Organizations select additional criteria based on the services they provide and customer requirements. Security addresses protection against unauthorized access. Availability ensures systems remain operational. Processing Integrity validates that system processing is complete, accurate, and timely. Confidentiality protects information designated as confidential. Privacy governs collection, use, retention, and disposal of personal information.
2) What is SOC 2 Type 2 compliant?
SOC 2 Type 2 compliance is an independent attestation by a licensed CPA firm that verifies your security controls are not only well-designed but also operate effectively over a period of 3 to 12 months. Type 2 reports assess both design effectiveness and operational effectiveness throughout an observation period. Enterprise clients prefer Type 2 because it demonstrates sustained control operation rather than point-in-time assessment. Technically, SOC 2 Type 2 reports never expire and are "valid" forever. However, customers want their vendors to have an updated report on at least an annual basis to ensure they can continue to rely on the customers' internal controls.
3) Does HITRUST cover SOC 2?
HITRUST CSF (Common Security Framework) and SOC 2 are distinct frameworks addressing overlapping security domains. HITRUST is a certifiable framework incorporating requirements from multiple regulations including HIPAA, PCI DSS, and elements of SOC 2 Trust Services Criteria. Organizations can pursue both certifications, and many controls implemented for SOC 2 support HITRUST requirements. However, HITRUST certification does not automatically satisfy SOC 2 requirements. Organizations selling to healthcare enterprises often pursue both frameworks—HITRUST for healthcare-specific requirements and SOC 2 for broader enterprise buyers.
4) How to become SOC 2 Type 2 compliant?
Achieving SOC 2 Type 2 compliance requires systematic implementation and operation of security controls over a defined observation period:
- Define scope: Identify in-scope systems and select applicable Trust Services Criteria
- Implement controls: Deploy security controls addressing selected criteria, using Zero Trust principles to strengthen effectiveness
- Document policies: Create security policies, procedures, and system descriptions
- Operate controls: Maintain control effectiveness throughout a 3-12 month observation period
- Collect evidence: Generate logs, access reviews, device compliance reports, and monitoring data demonstrating control operation
- Engage auditor: Select licensed CPA firm to conduct formal audit
- Remediate findings: Address any control deficiencies identified during audit
- Receive report: Obtain Type 2 report documenting control design and operating effectiveness
Organizations implementing Zero Trust concurrently with SOC 2 preparation typically achieve audit readiness in 4-5 months compared to 9-12 months using traditional approaches.
5) How does Zero Trust help with SOC 2 audit readiness?
Zero Trust practices generate the evidence auditors require while strengthening actual security posture. Continuous identity verification produces authentication logs. Device posture checks create compliance records. Network segmentation provides architectural documentation. Access reviews demonstrate least privilege enforcement. Continuous monitoring generates security event logs and incident records. This approach transforms compliance from periodic audit preparation into sustained operational discipline—evidence collection becomes automated rather than manual scramble preceding audits. Organizations implementing Zero Trust report 50-70% reduction in audit preparation effort because monitoring and logging infrastructure already captures required evidence continuously.





.svg)






.svg)
.svg)