Most enterprise buyers now request assurance artifacts before procurement. Without operational security and continuous evidence, deals stall even when teams think they’re “ready” on paper. When you sell into regulated industries, showing a clear GDPR Audit Timeline—the sequence and timing of activities to verify compliance with the EU General Data Protection Regulation—is as important as feature functionality. Large customers expect proof that your controls work, that personal data is handled lawfully, and that you run a program of continuous monitoring.
In this article I walk through the steps and artefacts that underpin a robust GDPR Audit Timeline, explain why it matters in enterprise sales, and offer templates and practical guidance drawn from Konfirmity’s experience running more than 6,000 audits over twenty‑five years.
Why a GDPR Audit Timeline Matters for Enterprise‑Selling Companies
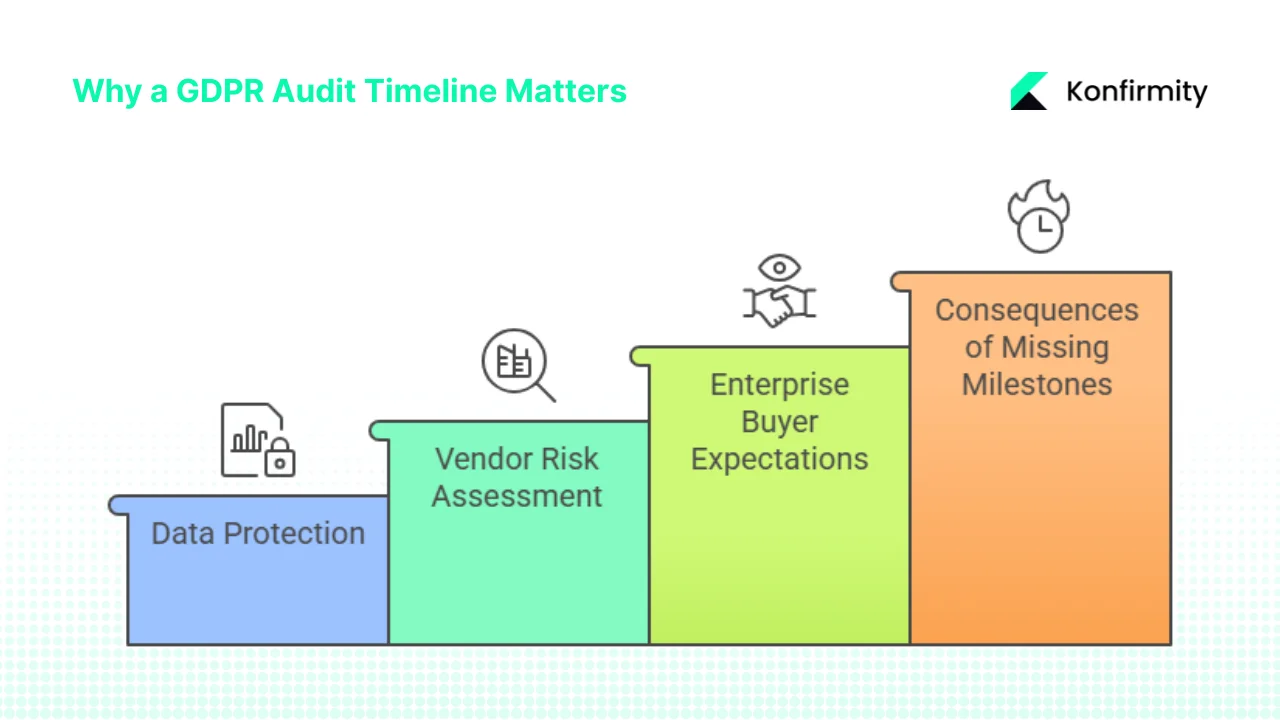
1) Data protection and privacy regulations: The GDPR, the UK GDPR and related state laws set out principles of lawfulness, fairness and transparency for handling personal data. Article 30 of the regulation requires controllers and processors to maintain detailed records of processing activities (ROPAs). Official guidance from the UK Information Commissioner’s Office recommends starting with an information audit or datamapping exercise to clarify what personal data an organisation holds and where. Enterprises look for vendors who can show that they understand these obligations and have mapped data flows across systems and third parties.
2) Vendor risk assessments hinge on evidence: Large enterprises and healthcare organisations perform rigorous vendor assessments. They often request SOC 2 Type II or ISO 27001 attestation reports, security questionnaires and privacy exhibits. A credible GDPR Audit Timeline shows you can gather evidence, execute risk assessments and respond to privacy incidents within the required timeframes. For example, the ICO warns that personal data breaches meeting the threshold for reporting must be notified to the regulator within 72 hours of discovery. Missing such deadlines can lead to penalties and reputational damage.
3) Enterprise buyer expectations: Buyers want to see documented controls, third‑party audit reports, risk assessments and a current data processing map. They expect you to demonstrate how you manage lawful bases for processing, retention periods, data subject requests and cross‑border transfers. Many ask whether you operate continuous control monitoring. Failure to produce a timeline or evidence can result in stalled contracts or loss of deals.
4) Consequences of missing milestones: Beyond reputational risk, missing audit deadlines can violate contract provisions. For instance, if your obligations include compliance with HIPAA, proposed revisions to the HIPAA Security Rule would require regulated entities to maintain a technology asset inventory and network map at least once every 12 months. Failure to meet such requirements may trigger regulatory enforcement and damages. A well‑defined timeline helps you track these dates.
Key Concepts & Terms in the Timeline
- Data protection compliance: Adhering to GDPR principles such as lawfulness, fairness and transparency. This includes implementing data minimisation, purpose limitation and storage limitation; selecting an appropriate lawful basis; and honouring subject rights.
- Privacy regulations: Beyond the GDPR, organisations serving enterprise and healthcare clients face frameworks such as SOC 2, ISO 27001 and HIPAA. For example, a SOC 2 Type II report covers a period of 6, 9 or 12 months, with the audit itself usually lasting a few weeks. ISO 27001 surveillance audits occur annually, with recertification every three years. Understanding these schedules helps harmonise your compliance program.
- Personal data review: A data inventory and mapping exercise that identifies what personal data you collect, process and store. The ICO advises starting with an information audit to clarify data holdings and encourages senior management buy‑in.
- Audit planning: Defining the scope, objectives, stakeholders and timelines for the audit. Planning includes identifying systems, departments and vendors in scope, and preparing documentation templates.
- Risk assessment: A structured process for identifying threats, vulnerabilities and potential impacts on personal data. NIST’s Special Publication 800‑30 notes that risk assessments, carried out at all tiers of the risk management hierarchy, provide senior leaders with information needed to determine appropriate actions. This process feeds into the audit plan.
- Compliance checklist: A step‑by‑step list of items to verify, such as lawful basis, data inventory, data protection officer (DPO) decision, security measures, ROPA completeness and breach response.
- Documentation review: Reviewing policies, procedures, vendor contracts and ROPAs to ensure they align with privacy obligations. It includes verifying retention schedules, lawful bases and cross‑border transfer mechanisms.
- Data processing mapping: Mapping data flows through systems and vendors to identify where personal data is stored, transmitted and processed. The ICO guidance emphasises that granular documentation reflecting different categories of data and individuals is required; generic lists without meaningful links do not meet GDPR requirements.
- Training and awareness: Ensuring staff understand GDPR roles and responsibilities. Auditors will check training records and awareness materials during field work.
- Reporting and documentation: Producing an audit report that summarises findings, risks and recommendations. It should include evidence and remediation plans.
- Remediation plan: A schedule of actions to address gaps identified during the audit. It allocates owners and timelines.
- Ongoing monitoring: Compliance is not a one‑time project; it requires periodic control testing, vendor reviews and updates to ROPAs. For HIPAA‑regulated entities, certain inventories must be updated at least annually.
Setting the Stage – Pre‑Audit Preparations
Before field work begins, companies need to lay the groundwork for an effective audit.

- Define audit objectives and scope. Identify the systems, business units and third‑party services that process personal data. Align the scope with your product’s data flows and contractual obligations.
- Build the audit team. Involve compliance, legal and IT/security leaders. If your organisation processes data at scale or monitors EU citizens, decide whether you need to appoint a DPO. Many enterprise buyers expect a named privacy lead.
- Draft a high‑level timeline. Allocate 4 weeks for planning, 6 weeks for field work, 4 weeks for analysis and reporting, and 4 weeks for remediation. These windows can vary depending on complexity. When preparing for a SOC 2 Type II attestation, remember that the observation period typically spans 6–12 months; you should align your GDPR activities so they generate evidence across that same period.
- Inventory personal data and map processing. Gather records of processing activities and create a data flow map. The ICO recommends starting with an information audit, engaging people across the organisation and securing senior management support. Use questionnaires and interviews to gather information on data types, purposes, recipients, retention and security measures.
- Conduct a gap analysis. Compare your current state with GDPR requirements and other frameworks you adhere to. Evaluate lawful bases, retention policies, security controls, consent mechanisms and data subject rights processes. Document any gaps.
- Establish roles and responsibilities. Assign owners for each component of the audit—documentation, risk assessment, vendor review, training and remediation. Include executive sponsors who can approve investments and drive change.
- Prepare documentation templates. Create an audit plan, risk assessment form, remediation log and monitoring schedule. These templates streamline evidence collection and ensure consistency.
- Align with enterprise buyer timelines. If you’re responding to a request for proposal (RFP), ask procurement teams about their due‑diligence schedules. Adjust your audit milestones so you can provide evidence before contract signature.
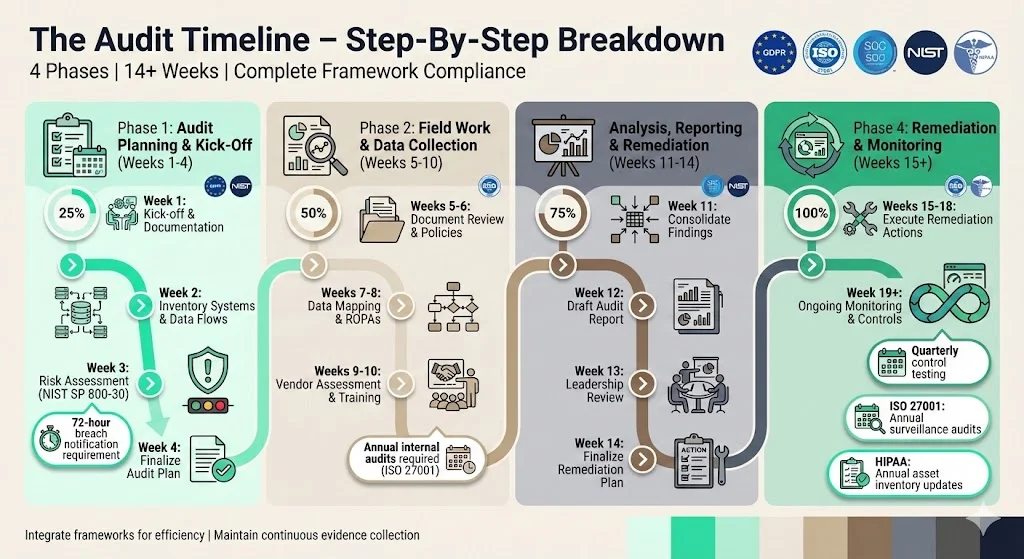
The Audit Timeline – Step‑By‑Step Breakdown with Examples
Phase 1 – Audit Planning and Kick‑Off (Weeks 1–4)
- Week 1: Hold a kick‑off meeting with stakeholders to define the audit scope and objectives. Gather existing documentation—privacy policies, security policies, previous audit reports, ROPAs and vendor contracts.
- Week 2: Inventory systems, data flows and vendors. Start mapping personal data flows, noting categories of data, purposes, locations and transfers.
- Week 3: Conduct an initial risk assessment. Use NIST SP 800‑30 guidance to identify threats, vulnerabilities and impacts. Prioritise high‑risk processing activities such as processing sensitive data or cross‑border transfers.
- Week 4: Finalise the audit plan. Schedule interviews with system owners, confirm field work dates and communicate expectations to teams.
Phase 2 – Field Work / Data Collection (Weeks 5–10)
- Weeks 5–6: Perform document review. Examine privacy policies, data breach response plans, security policies, vendor contracts and DPO documentation. Confirm that breach notification procedures meet the 72‑hour reporting requirement.
- Weeks 7–8: Complete the personal data review and mapping. Identify types of personal data (identifiers, financial information, behavioural data), special categories, processing purposes, lawful bases, retention periods and recipients. Compare your map with the ROPAs and update gaps.
- Weeks 9–10: Review vendors and third parties. Assess contracts for standard contractual clauses and data protection addenda. Evaluate international transfers and vendor security practices. Review training and awareness records to ensure staff understand policies. If you’re pursuing ISO 27001 certification, remember that internal audits should be conducted at planned intervals and at least annually.
Phase 3 – Analysis, Reporting and Remediation Planning (Weeks 11–14)
- Week 11: Consolidate audit findings. Score risks, compare actual practices against your compliance checklist and summarise deviations.
- Week 12: Draft the audit report. Include findings, risk ratings, recommendations and a proposed remediation plan. Outline improvements such as updating privacy notices, refining access controls or changing vendors. Draw attention to any misalignments with cross frameworks. For instance, if your SOC 2 Type II observation period is nine months and your GDPR audit evidence spans four months, highlight the gap and propose continuous evidence collection.
- Week 13: Review the draft report with leadership. Obtain feedback, prioritise remediation actions and assign owners. Discuss budget and resource needs.
- Week 14: Finalise the remediation plan and integrate it into the ongoing monitoring schedule. Communicate responsibilities and due dates to all stakeholders.
Phase 4 – Remediation and Monitoring (Weeks 15 onward)
- Weeks 15–18: Execute remediation actions. Update policies, implement technical controls, revise vendor contracts, run training sessions and close gaps identified in the audit. Document evidence of completion.
- Week 19+: Shift to ongoing monitoring. Establish quarterly or monthly control testing, update your data inventory, conduct vendor reviews and run refresher training. For HIPAA‑regulated entities, maintain an up‑to‑date technology asset inventory and network map at least annually. For SOC 2 Type II, continue to collect evidence across the observation period. Surveillance audits under ISO 27001 occur annually and recertification audits every three years.
Timeline Variations by Company Size
Konfirmity’s experience shows that smaller SaaS vendors with simple data flows can complete a GDPR readiness audit in roughly 3–6 months. In contrast, enterprise‑scale companies with multiple business units, global data transfers and dozens of vendors often need 12 months or more to document processing activities, align contracts and test controls. Align your GDPR Audit Timeline with the complexity of your data environment, the number of controls you must evidence across frameworks and the observation period of attestation reports.
CTA: Book a demo
Templates for Busy Teams
The following templates provide starting points for documenting your GDPR Audit Timeline and related artefacts. Adjust them based on your scope and industry.
GDPR Audit Timeline Template
Compliance Checklist Template (10 Steps)
- Confirm lawful bases for all processing activities (consent, contract, legitimate interests, etc.).
- Verify data inventory and ROPA completeness.
- Determine whether a Data Protection Officer or privacy lead is required.
- Assess technical and organisational security measures.
- Maintain a data register with categories of data, individuals and purposes.
- Perform Data Protection Impact Assessments (DPIAs) for high‑risk processing.
- Publish an up‑to‑date privacy policy and notice.
- Maintain a breach response plan that meets the 72‑hour notification requirement.
- Appoint an EU representative if you lack an EU establishment.
- Assess third‑party risks and maintain vendor contracts with data protection clauses.
Risk Assessment Template
Remediation Plan Template
Monitoring Schedule Template
These templates streamline evidence collection and ensure that documentation remains up to date. Tailor them to your organisation’s structure. For example, if you already conduct SOC 2 Type II readiness assessments, integrate data protection checkpoints into your existing control testing. Konfirmity’s managed service often reduces internal effort by more than 70 percent: many clients achieve readiness in 4–5 months instead of 9–12 when managing compliance themselves. We assign a dedicated CISO, perform continuous monitoring and provide outcome‑oriented artefacts so your team spends roughly 75 hours per year rather than 550–600 hours on compliance operations.
CTA: Book a demo
Practical Tips & Pitfalls for Enterprise‑Selling Vendors
- Synchronise with procurement schedules. Align your GDPR Audit Timeline with your client’s due‑diligence process. If the client reviews security evidence in Q3, ensure your audit report and updated ROPA are ready before then.
- Be transparent about findings. Enterprises often request the full audit report, remediation plan and monitoring logs. Explaining gaps and planned remediation actions builds trust and demonstrates accountability.
- Use automation where appropriate. Modern compliance platforms can collect evidence automatically, conduct continuous control monitoring and generate reminders. Automation reduces manual effort and helps maintain a 12‑month observation period for SOC 2 Type II.
- Don’t ignore vendor risk. Many delays occur because vendor contracts and data transfer mechanisms are not aligned with GDPR requirements. Conduct vendor assessments early and build time into your plan to renegotiate clauses.
- Avoid treating the audit as a one‑time project. Regulatory frameworks require ongoing monitoring. ISO 27001 mandates internal audits at planned intervals, and HIPAA may require annual updates to asset inventories and network maps. Build recurring reviews into your schedule.
- Keep documentation current. Maintain your ROPA, risk assessments and control logs continuously. The ICO emphasises that documentation must be granular and meaningful; generic lists do not meet GDPR requirements.
- Scale the timeline to your complexity. Small SaaS vendors with a handful of data flows may complete their initial audit in 3–6 months. Large enterprises with dozens of systems and global transfers may need 12–18 months. Plan accordingly and secure executive commitment.
Example Scenarios
Company A – Small SaaS vendor: It processes customer names, email addresses and payment tokens. The data flows through a single cloud provider and two sub‑processors. Konfirmity helped Company A (can’t disclose the name) become GDPR audit‑ready in roughly four months, integrating the GDPR review into its SOC 2 observation period. Evidence collection consumed around 60 staff hours.
Company B – Global enterprise: It operates across five countries, processes special‑category data and uses dozens of sub‑processors. The team required 12 months to complete data mapping, update vendor agreements and run multiple DPIAs. The first audit report identified twelve gaps. Remediation spanned six months with weekly check‑ins. The buyer appreciated the detailed GDPR Audit Timeline, which was included in their RFP response.
Clear timelines differentiate you in sales conversations. When prospective customers ask “How often do you audit your GDPR program?” you can answer with precision: “We perform a GDPR audit every 12 months, with an observation period aligned to our SOC 2 Type II report. Our audit plan runs for 14 weeks, and remediation actions are tracked continuously.” That specificity builds confidence.
Example Timeline Visuals & Milestones
The following graphic provides a Gantt‑style overview of a typical GDPR Audit Timeline, showing key phases and milestones. The planning phase (Weeks 1–4) sets the scope and risk assessment. Field work (Weeks 5–10) includes documentation review, personal data mapping and vendor assessments. Analysis and reporting (Weeks 11–14) consolidate findings and finalise the remediation plan. Remediation actions (Weeks 15–18) follow, and ongoing monitoring begins from Week 19 onward. Milestones such as “Kick‑off meeting”, “Data inventory complete”, “Vendor contract review done”, “Audit report submitted” and “Remediation plan signed off” help teams gauge progress.
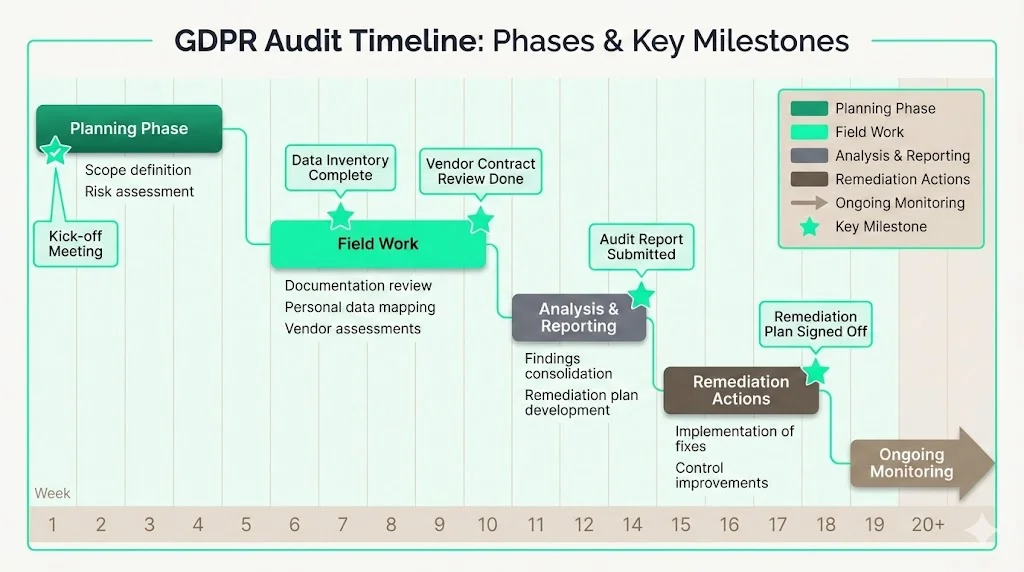
For medium‑size enterprises, the full cycle may last 6–12 months; larger organisations may require a year or more. Busy teams can compress certain phases by using automation and leveraging existing frameworks. For example, if your SOC 2 observation period started in January, start data mapping in parallel so you can reuse evidence across frameworks. Conversely, if vendor contract negotiations slow progress, extend the field work phase while continuing risk assessments.
What the Enterprise Buyer Will Look For (and How You Prove It)
Enterprise customers expect tangible evidence that your privacy program works. Key deliverables include:
- Audit report: Summarises scope, methodology, findings and risk ratings. It includes evidence of controls and references cross frameworks (e.g., SOC 2, ISO 27001, HIPAA) and should be updated annually. The report demonstrates your commitment to security and compliance. In Linford & Company’s guidance, SOC 2 Type II reports cover 6, 9 or 12 months and should be reproduced annually.
- Remediation plan: Details each finding, root cause, remediation action, owner and timeline. It shows that identified gaps are tracked and resolved.
- Monitoring logs: Evidence of continuous control testing—access reviews, vulnerability scans, vendor assessments and training completion. For HIPAA‑regulated entities, logs should show asset inventory updates every 12 months.
- Vendor assessments: Completed questionnaires, contractual clauses and audit reports for sub‑processors and partners.
- Training records: Proof that employees completed privacy and security training relevant to their roles. Auditors often ask for completion percentages and content outlines.
In proposals and RFP responses, articulate how your GDPR Audit Timeline feeds into these deliverables: by Week 14 you have a draft report; by Week 18 remediation actions have started; and from Week 19 onward monitoring operates continuously. Highlight that your program is human‑led and managed—Konfirmity assigns a dedicated CISO, implements controls inside your stack and runs your program year‑round so you remain audit‑ready.
CTA: Book a demo
Conclusion
Enterprise buyers and healthcare organisations demand evidence that vendors handle personal data responsibly and comply with multiple frameworks. A GDPR Audit Timeline brings structure to the complex tasks of data mapping, risk assessment, control testing and remediation. The key take‑aways are:
- Understand the timeline. Effective audits follow clear phases—planning, field work, analysis, remediation and monitoring. Align your GDPR activities with SOC 2 observation periods and ISO 27001 internal audits, and integrate HIPAA‑specific requirements like annual asset inventories.
- Use templates and structured phases. Prepare in advance with a data inventory, risk assessment form and remediation log. Use the templates provided to capture key actions and responsibilities.
- Align with enterprise expectations. Large buyers expect evidence across multiple frameworks. Provide audit reports, remediation plans, monitoring logs, vendor assessments and training records.
- Build in ongoing monitoring. Compliance isn’t a one‑time project. Regularly update your ROPA, conduct vendor reviews, test controls and refresh training. The global average cost of a data breach dropped to USD 4.44 million in 2025—down from USD 4.88 million the previous year—thanks to faster containment. Continuous monitoring shortens detection and reduces costs.
For companies selling to enterprise clients, a clear GDPR Audit Timeline is more than a checklist—it’s a trust signal and competitive edge. With the right plan and tools, even busy teams can achieve durable security and compliance. Konfirmity’s human‑led managed service demonstrates that security that looks good in documents but fails under incident pressure is a liability; build the program once, operate it daily and let compliance follow.
FAQs
1. What is the timeline for GDPR compliance?
The initial compliance timeline varies by company size and complexity. Small SaaS vendors may achieve readiness in 3–6 months, whereas larger enterprises with complex data flows and many vendors often need 12 months or more. The observation period for SOC 2 Type II reports is typically 6–12 months, so aligning GDPR evidence collection with this period helps consolidate efforts. Remember that compliance is not finished after the first audit; ongoing monitoring, vendor reviews and internal audits continue year‑round.
2. What is the audit process of GDPR?
The process follows four phases: planning and kick‑off (weeks 1–4), field work/data collection (weeks 5–10), analysis and reporting (weeks 11–14) and remediation and monitoring (weeks 15 onward). Planning defines scope and risk assessment, field work involves document review, personal data mapping and vendor assessments, analysis consolidates findings and produces the report, and remediation implements fixes and sets up continuous monitoring. These phases align with general audit practices across frameworks such as ISO 27001, which requires internal audits at planned intervals.
3. Are GDPR audits mandatory?
The GDPR does not mandate a formal external audit for all organisations, but it does require accountability, documented processing activities, risk assessments and appropriate controls. Many enterprise customers, regulators and certification bodies expect independent audits or attestations. For example, SOC 2 Type II reports are attestation reports—not certifications—and are typically renewed annually. HIPAA’s proposed update would require regulated entities to document a technology asset inventory and network map at least annually. Undertaking periodic GDPR audits is a best practice that demonstrates accountability and supports enterprise procurement.
4. What is the timeframe for GDPR?
The General Data Protection Regulation came into force in May 2018. It applies to any organisation that processes the personal data of EU or UK residents, regardless of location. For audit purposes, timeframes refer to how often you update ROPAs, conduct risk assessments and monitor controls. The ICO states that organisations must report certain personal data breaches to the regulator within 72 hours of discovery. HIPAA proposes annual updates to asset inventories, and ISO 27001 requires internal audits at planned intervals. Align your schedules to meet these requirements and your customer’s expectations.





.svg)






.svg)
.svg)