Most enterprise buyers now request assurance artifacts before procurement. Without operational security and continuous evidence, deals stall—even when teams think they have prepared on paper.
If you sell to enterprise clients, particularly in the EU or UK, you know the drill. A prospect is ready to sign, but then the legal team steps in. They demand proof of data protection. Self-attestation questionnaires are no longer enough. They want independent validation. This is where a formal GDPR External Audit Guide becomes your operational playbook for closing deals.
In my experience overseeing 6,000+ audits, I have seen too many companies treat GDPR as a paperwork exercise. They generate policies that sit on a drive, untouched until an incident occurs. That approach fails under scrutiny. Real compliance requires control implementation inside your stack.
This guide details exactly how to prepare for, execute, and pass an external assessment. We will move past the theory and focus on the operational demands required to satisfy enterprise buyers and regulators in 2026.
What is a GDPR External Audit?
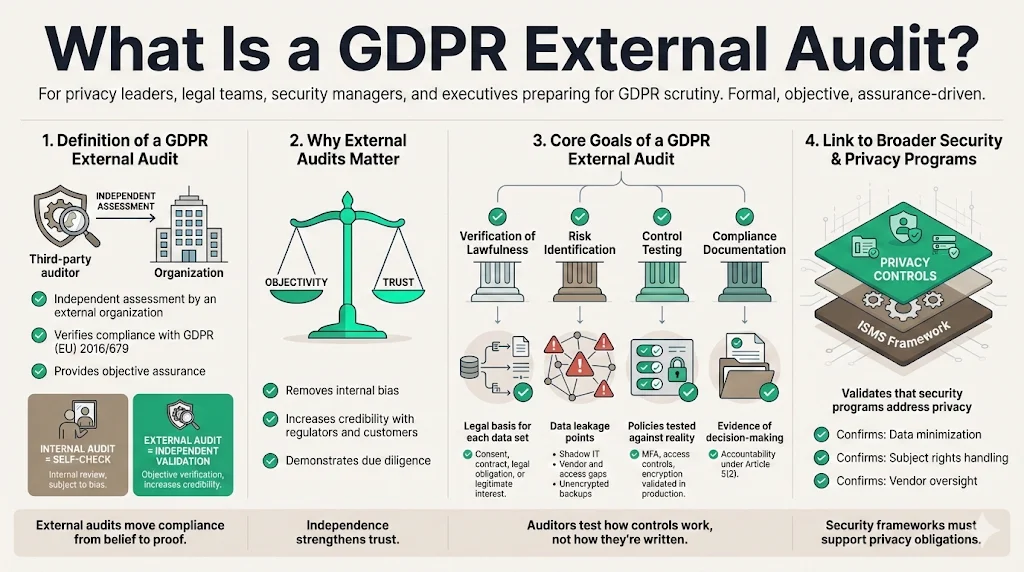
A GDPR external audit is an independent assessment conducted by a third-party organization to verify your compliance with the General Data Protection Regulation (EU) 2016/679.
Unlike an internal audit, which is a self-check typically run by your own DPO or compliance lead, an external audit provides an objective opinion on your control environment. It moves beyond "we believe we are compliant" to "an independent expert has verified we are compliant."
Core Goals of the Audit
The auditor does not just read your privacy policy. They look for operational evidence across four areas:
- Verification of Lawfulness: Do you have a valid legal basis for every data set you hold?
- Risk Identification: Where does data leak? Shadow IT, unencrypted backups, and poorly managed vendor access are common findings.
- Control Testing: Does the Multi-Factor Authentication (MFA) policy actually enforce MFA on the production database, or is it just written on paper?
- Compliance Documentation: Have you documented your decisions? Under the "Accountability Principle" (Article 5(2)), you must prove you made the right choices, not just make them.
This fits into broader data protection by validating that your Information Security Management System (ISMS)—often built for ISO 27001 or SOC 2—actually addresses privacy specifics like data minimization and subject rights.
Why It Matters for Enterprise Sales
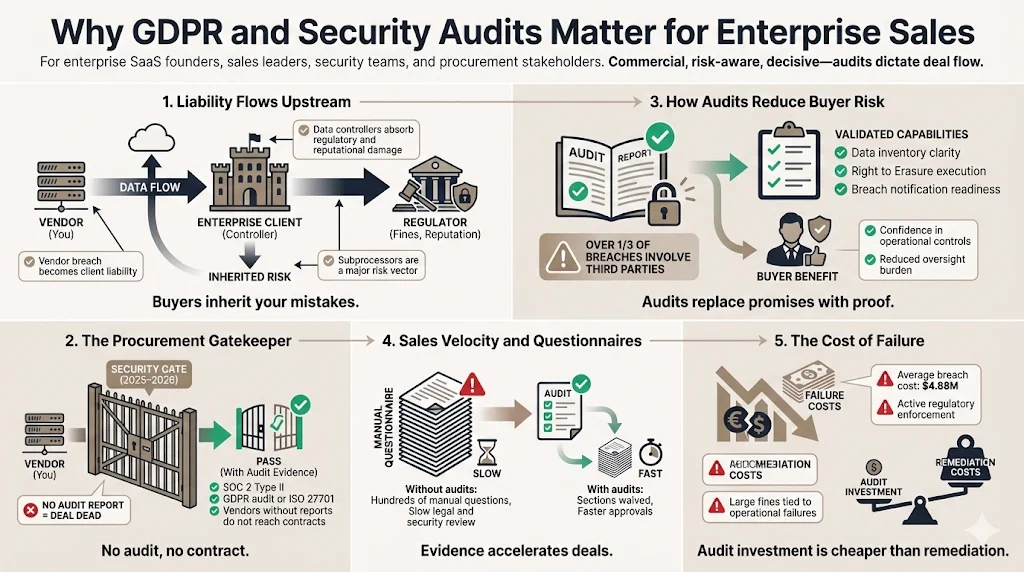
Enterprise clients demand verifiable audit evidence because they carry the liability. If a subprocessor (you) suffers a breach, the data controller (your client) faces the regulatory heat and reputational fallout.
The Procurement Gatekeeper
In 2025 and 2026, we see enterprise procurement teams using "compliance gates." If a vendor cannot produce a SOC 2 Type II report and a GDPR validation (or ISO 27701 certification), they do not pass to the contract phase. This is driven by risk; 35.5% of all breaches in 2024 involved a third party, a figure that continues to rise.
Risk Reduction
Formal audits help validate controls around personal data processing. They prove to the buyer that:
- You know exactly what data you have.
- You can delete it if their customers ask (Right to Erasure).
- You notify them immediately if a breach occurs.
Without this external validation, your sales team enters every negotiation with a handicap, forced to answer hundreds of security questionnaire rows manually. With an audit report, you can often bypass huge sections of those questionnaires.
The Cost of Failure
The financial argument is clear. The global average cost of a data breach hit $4.88 million in the latest IBM report. Furthermore, regulatory enforcement is active. In January 2026, French regulators fined telecom operators €42 million for security failures, signaling that authorities are targeting operational negligence, not just policy wording.
Key GDPR Requirements External Audits Focus On
Auditors do not test the entire regulation. They focus on the high-risk areas that impact data subjects and controllers. Based on our delivery work, these are the specific domains an auditor will examine.
Data Inventory and Mapping (Article 30)
You cannot protect what you do not track. Auditors expect a Record of Processing Activities (RoPA) that serves as a living map of your data.
- What they check: Does the inventory match the reality in your AWS/Azure environment?
- Common failure: The RoPA lists three databases, but the infrastructure scan reveals five S3 buckets containing PII.
Lawful Basis for Processing (Article 6)
For every data category (emails, IP addresses, health data), you must document why you are allowed to process it.
- Consent: Are logs kept? Is it granular?
- Legitimate Interest: Have you conducted a Legitimate Interest Assessment (LIA)?
- Contract: Is the processing strictly necessary to fulfill the service?
Data Subject Rights Handling (Articles 12–23)
It is not enough to say you handle Subject Access Requests (DSARs). You need evidence.
- The test: Auditors often ask to see the log of past requests and the tickets showing they were fulfilled within 30 days.
- The gap: Engineering teams often manually delete data from the main DB but forget backups or logs.
Third-Party Vendor Management (Article 28)
This is a massive focus area. You are responsible for your vendors (AWS, Stripe, HubSpot, etc.). With retail and hospitality sectors seeing over 52% of breaches originate from third parties, auditors will demand rigorous proof of vendor oversight.
- Requirement: Signed Data Processing Agreements (DPAs) with all subprocessors.
- Verification: Do you review their security posture annually?
Security of Processing (Article 32)
This overlaps heavily with SOC 2 and ISO 27001.
- Controls: Pseudonymization, encryption at rest and in transit, ability to restore availability (backups), and regular testing (pen tests).
Transparency Obligations (Articles 12–14)
A priority for 2026 audits is the clarity of privacy notices. Regulators are cracking down on "legalese."
- Audit check: Is the privacy policy easily accessible? Is the language clear enough for a 13-year-old to understand? 75% of consumers state they will not buy from companies they do not trust with their data.
Step-by-Step GDPR External Audit Process
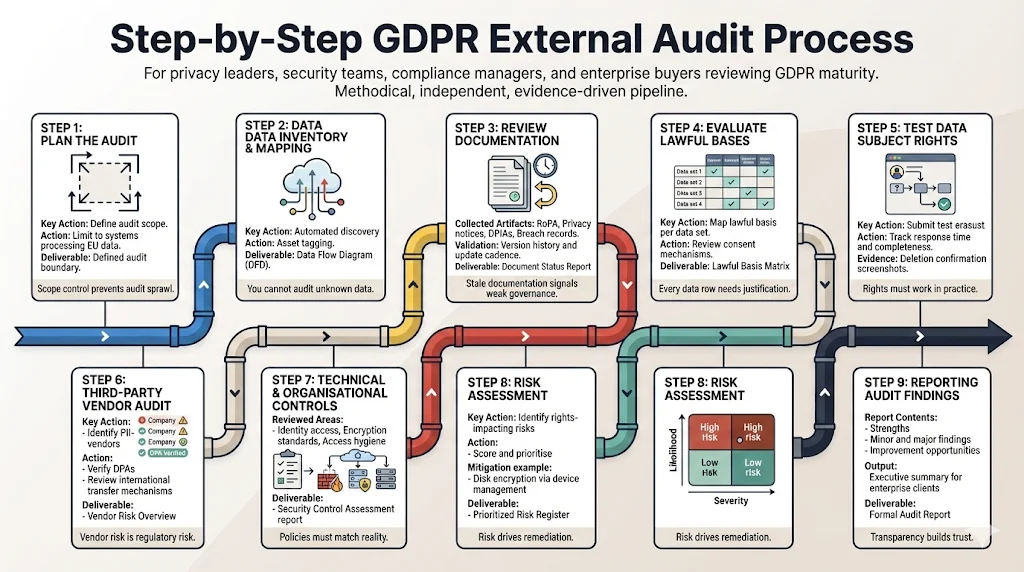
This section of our GDPR External Audit Guide breaks down the execution. This is how we run managed programs at Konfirmity.
Step 1: Plan the Audit
Defining scope is critical. If you process enterprise data only in your EU region, do not include your US marketing operations in the audit scope unless necessary.
- Action: Define the "boundary" of the audit. Which systems, people, and locations touch EU data?
- Stakeholders: Identify Data Owners (Engineering Lead, HR Director, Marketing VP).
Step 2: Data Inventory & Mapping
You must create a visual map of data flows.
- Action: Run automated discovery tools on your cloud environment to tag assets.
- Deliverable: A Data Flow Diagram (DFD) showing data intake, storage, transfer, and deletion points.
Step 3: Review Documentation Requirements
Gather your evidence artifacts.
- Collect: Current RoPA, Privacy Notices, Data Protection Impact Assessments (DPIAs) for high-risk features, and breach logs.
- Validation: Ensure version history is active. A policy last updated in 2019 is an immediate red flag.
Step 4: Evaluate Lawful Bases for Processing
Map a legal justification to every row in your inventory.
- Action: If you rely on "Consent," audit your cookie banner and signup forms. Do boxes default to "checked"? (That is non-compliant).
- Deliverable: A Lawful Basis Matrix.
Step 5: Assess Data Subject Rights Management
Test your own process.
- Simulation: Submit a dummy "Right to be Forgotten" request.
- Track: How many hours did it take engineering to find the data? Did they miss the logs?
- Evidence: Screenshot the deletion confirmation from the database.
Step 6: Third-Party Vendor Audit
This is tedious but necessary.
- Action: List all 50+ SaaS tools you use. Filter for those holding PII.
- Check: Do you have a DPA for each? If a vendor transfers data to the US, do they rely on the EU-US Data Privacy Framework or Standard Contractual Clauses (SCCs)?
Step 7: Technical & Organizational Controls Review
This is the security deep dive.
- IAM: Review access lists. Does a former developer still have GitHub access?
- Encryption: Verify TLS 1.2+ usage and AES-256 for storage.
- Deliverable: A Security Control Assessment report (often mapped to ISO 27001 Annex A).
Step 8: Risk Assessment
Identify risks that could harm the rights and freedoms of individuals.
- Methodology: Score risks based on Likelihood and Severity.
- Example: "Risk of unencrypted laptop theft containing customer DB dump."
- Mitigation: Enforce disk encryption via MDM.
Step 9: Reporting Audit Findings
The auditor produces a report detailing strengths, non-conformities (minor/major), and opportunities for improvement.
- Output: An executive summary you can share with enterprise clients to prove maturity.
Sample GDPR Audit Timeline
Speed depends on your starting point. A self-managed approach often drags on for 9–12 months. With a human-led managed service like Konfirmity, where we implement the controls for you, this shrinks significantly.
Here is a typical timeline for a mid-sized B2B SaaS company:
- Weeks 1–2: Planning & Scoping. Define the boundary. Kick off with stakeholders.
- Weeks 3–6: Inventory & Documentation. The heavy lift. Building the RoPA and mapping flows.
- Weeks 7–10: Controls & Vendor Review. Implementing technical fixes (e.g., setting up log retention, fixing encryption). Chasing vendors for DPAs.
- Weeks 11–14: Gap Remediation. Fixing the issues identified in the mock audit phase.
- Weeks 15–16: Final Report. The external auditor conducts the review and issues the finding.
Konfirmity Difference: By embedding controls directly into your stack and handling the documentation, we typically reduce the internal effort from ~600 hours to ~75 hours per year.
Audit Evidence Checklist
To satisfy an auditor, you need artifacts. Use this checklist from our GDPR External Audit Guide to prepare.
- Governance:
- [ ] Organizational chart with security roles defined.
- [ ] Information Security Policy (signed/acknowledged by staff).
- [ ] Data Protection Policy.
- Processing:
- [ ] Record of Processing Activities (RoPA) – timestamped export.
- [ ] DPIA samples for high-risk processing (e.g., AI modeling, biometric data).
- [ ] Legitimate Interest Assessments (LIAs).
- Rights & Consent:
- [ ] Privacy Notice (current and previous versions).
- [ ] Cookie consent logs (proof of opt-in).
- [ ] DSAR capability test/logs.
- Supply Chain:
- [ ] List of sub-processors.
- [ ] Signed DPAs for all material vendors.
- [ ] Vendor security review records.
- Security (Technical):
- [ ] Access Control Lists (reviews conducted quarterly).
- [ ] Penetration testing report (within last 12 months).
- [ ] Vulnerability scan reports (clean or remediated).
- [ ] Incident Response Plan and test records (tabletop exercise).
- [ ] Training logs (security awareness completion).
Remediation Strategies
Audits reveal gaps. That is their purpose. How you fix them matters more than the gap itself.
Prioritization is key.
- High Severity: Issues that directly violate Article principles or leave data exposed to the public internet. Example: An S3 bucket with patient data is public. Fix immediately.
- Medium Severity: Process failures or lack of documentation. Example: DSARs are handled ad-hoc via email rather than a ticketing system. Fix within 30-60 days.
- Low Severity: Optimizations. Example: Policy language is slightly outdated. Fix during the next review cycle.
Operational Fixes: Often, the fix is not "write a policy" but "change the config." If password policies are weak, update your Okta/Auth0 configuration to enforce complexity and rotation. If laptops are unmanaged, deploy an MDM solution. This is where "outcome-as-a-service" providers shine—we implement the config change rather than just telling you to do it.
Best Practices for Continuous Compliance
The biggest mistake companies make is treating the audit as a finish line. In reality, compliance has a half-life. The moment the auditor leaves, your environment changes. Developers ship new code, new vendors are onboarded, and access permissions drift.
Outcome-as-a-Service vs. Software
GRC software tools act as a repository, but they do not do the work. They send alerts, creating noise for your team.
At Konfirmity, we believe in Human-Led Managed Services. We do not just flag that a vendor is missing a DPA; we chase the vendor and get it signed. We do not just alert you that a vulnerability exists; we help triage it based on CVSS scores and ensure it is patched within SLA. This is critical given the current global shortage of 4.8 million cybersecurity professionals, which leaves most internal teams understaffed.
The Quarterly Cadence
Instead of a panic-driven annual sprint, adopt a quarterly maintenance schedule:
- Q1: Full Access Review and Vendor Review.
- Q2: Disaster Recovery test and Penetration Test.
- Q3: Policy review and Staff Training refresh.
- Q4: Risk Assessment update and Audit prep.
This levels the workload and ensures that when a client asks for evidence, you have fresh data ready.
Conclusion
A successful audit is not about generating paper; it is about proving operational competence. When enterprise buyers look at your security posture, they want to see that you take their data seriously.
This GDPR External Audit Guide outlines the path, but the execution is where value is created. Security that looks good in documents but fails under incident pressure is a liability. You must build controls that stand up to buyers, auditors, and attackers alike.
By focusing on durable control implementation—real encryption, real access governance, real vendor management—compliance becomes a natural byproduct of good security. You stop scrambling for audits and start using them as a competitive advantage to win bigger deals, faster.
FAQs (Frequently Asked Questions)
1) What is the difference between internal and external GDPR audits?
An internal audit is a self-assessment conducted by your own organization to identify gaps and prepare. An independent third party performs an external audit to validate compliance and provide a formal report or certification (such as ISO 27701 or a SOC 2 privacy chapter) to share with clients.
2) How often should we conduct GDPR external audits?
Best practice dictates an annual cadence. However, if you make significant changes to your processing activities—such as launching a new AI feature or entering a new market—you should conduct a targeted assessment immediately.
3) What documents do enterprise clients expect to see?
They typically request a high-level summary of your audit report (or an ISO 27001/27701 certificate), your penetration test executive summary, your disaster recovery test results, and your standard Data Processing Agreement (DPA).
4) How long does a typical audit take?
From planning to final report, expect 3 to 4 months. The "observation period" for testing controls is usually the longest phase. Using a managed service like Konfirmity can compress the preparation time significantly by handling the heavy lifting of evidence collection and control implementation.
5) Can we fail a GDPR audit?
Yes. If the auditor finds major non-conformities—such as lacking a lawful basis for processing or having no process for data breaches—they cannot issue a validation. However, most audits allow a remediation period where you can address findings before the final opinion is issued. This is why we conduct a pre-audit gap analysis—so you can fix issues privately before the official auditor arrives.





.svg)





.svg)
.svg)