Most enterprise buyers now request assurance artifacts before procurement. Without operational security and continuous evidence, deals stall—even when teams believe they possess the necessary documentation. In the current market, your ability to recover from a disruption is scrutinized just as heavily as your ability to prevent one. This is where GDPR Business Continuity And DR becomes a critical operational requirement, not just a regulatory checkbox.
For companies selling to large enterprise clients, the definition of compliance has shifted. It is no longer enough to simply protect data from unauthorized access; you must guarantee its availability and resilience against failure. According to the Allianz Risk Barometer 2025, cyber incidents (such as ransomware and data breaches) rank as the top global business risk (38%), with business interruption following closely at number two (31%). When a system goes down, it is not merely an IT ticket—it is a potential violation of the General Data Protection Regulation (GDPR) if personal data becomes inaccessible.
At Konfirmity, having supported over 6,000 audits across 25+ years of combined expertise, we see a clear pattern: organizations that treat Business Continuity (BC) and Disaster Recovery (DR) as static documents fail during real-world incidents. Those that integrate these disciplines into a human-led, managed security program survive. This guide details how to build a durable GDPR Business Continuity And DR strategy that satisfies regulators and accelerates enterprise sales cycles.
Understanding the Basics
To implement an effective strategy, we must first strip away the jargon and focus on the operational mechanisms that keep a business running.
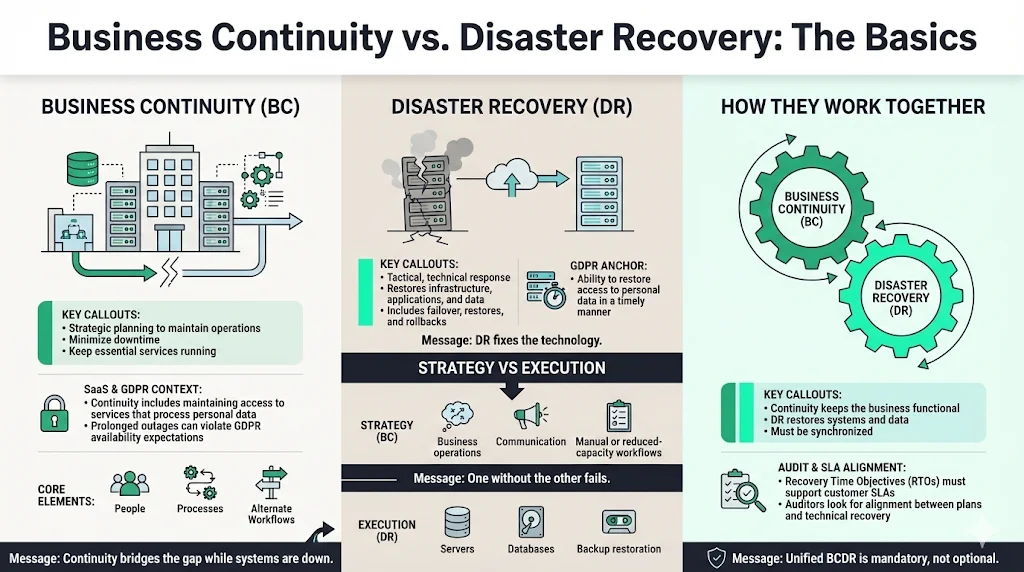
What is Business Continuity?
In an enterprise context, business continuity is the strategic planning required to maintain operational resilience. It focuses on keeping the business running during a disruption, minimizing downtime, and ensuring that essential functions continue to serve clients.
For a SaaS provider or a data processor, continuity is not just about keeping the lights on. It implies maintaining the integrity of the services that process personal data. If your customer support platform handles EU citizen data and goes offline for 48 hours, you have likely breached the "availability" principle of GDPR. Continuity planning maps out the people, processes, and alternate workflows needed to bridge the gap between an incident and full recovery.
What is Disaster Recovery (DR)?
While continuity is the strategy, Disaster Recovery (DR) is the tactical, technical response. DR consists of the specific steps taken to restore IT infrastructure, applications, and data sets after a critical failure.
DR is the engine room of GDPR Business Continuity And DR. It involves server restoration, database rollbacks, and switching to failover sites. From a compliance perspective, DR is non-negotiable because GDPR Article 32 mandates the ability to restore access to personal data in a "timely manner." If you cannot technically recover the data, you are non-compliant, regardless of your policies.
How Business Continuity and DR Work Together
The distinction is clear but often misunderstood: continuity keeps the business functioning (perhaps manually or with reduced capacity), while DR fixes the broken technology.
A unified BCDR (Business Continuity & Disaster Recovery) strategy is essential. You cannot have one without the other. A perfect technical recovery is useless if your staff does not know how to communicate with clients during the outage. Conversely, a great communication plan fails if the data is permanently corrupted. In our work implementing ISO 27001 and SOC 2 programs, we see that auditors look for the synchronization of these two elements. They want to see that the technical recovery times (RTOs) support the business promises made in Service Level Agreements (SLAs).
GDPR Requirements That Impact BCDR
Many organizations mistakenly view GDPR solely as a privacy law—a set of rules about consent and cookies. However, it is equally a security and resilience law.
GDPR Data Protection Fundamentals
Article 32 of the GDPR specifically addresses the "Security of Processing." It mandates that controllers and processors implement technical and organizational measures to ensure a level of security appropriate to the risk. Crucially, it lists four primary pillars:
- Pseudonymization and encryption.
- Confidentiality.
- Integrity.
- Availability and resilience of processing systems.
The inclusion of "availability and resilience" directly ties GDPR Business Continuity And DR to legal compliance. If a ransomware attack locks your systems and you lack a clean backup to restore from, you have failed to maintain availability. This is a reportable breach.
Regulatory Interpretation of Business Continuity and DR
Regulators like the UK's Information Commissioner’s Office (ICO) and Ireland's DPC have made it clear: hope is not a strategy. You must have a plan to prevent the permanent loss of personal data.
The ICO guidance suggests that organizations must test their ability to restore data. During an audit or a breach investigation, regulators will ask for evidence of your last DR test. If your answer is "we haven't tested it yet," you face significantly higher fines. In 2024 alone, GDPR fines totaled €1.2 billion across Europe, emphasizing that enforcement is active and costly. The focus is on "timely" restoration. "Timely" is subjective, but in the enterprise world, it is defined by the sensitivity of the data and the impact on the data subjects.
Processor and Vendor Compliance
This is where many B2B companies get caught. If you are a vendor providing software or services to an enterprise, you are likely a "Data Processor." Under GDPR, processors have direct statutory obligations to assist the "Data Controller" (your client) in ensuring compliance.
If your client relies on your GDPR Business Continuity And DR posture to meet their own obligations, your failure becomes their failure. This is why procurement teams send 200-question security assessments. They need to verify that your DR plan works so they don't face penalties for your downtime. At Konfirmity, we help clients answer these questionnaires not with vague promises, but with evidence of recent failover tests and backup logs.
Step-by-Step GDPR Business Continuity and DR Planning
Building a compliant program is not about downloading a template. It requires a structured, risk-based approach that sits inside your actual technology stack.
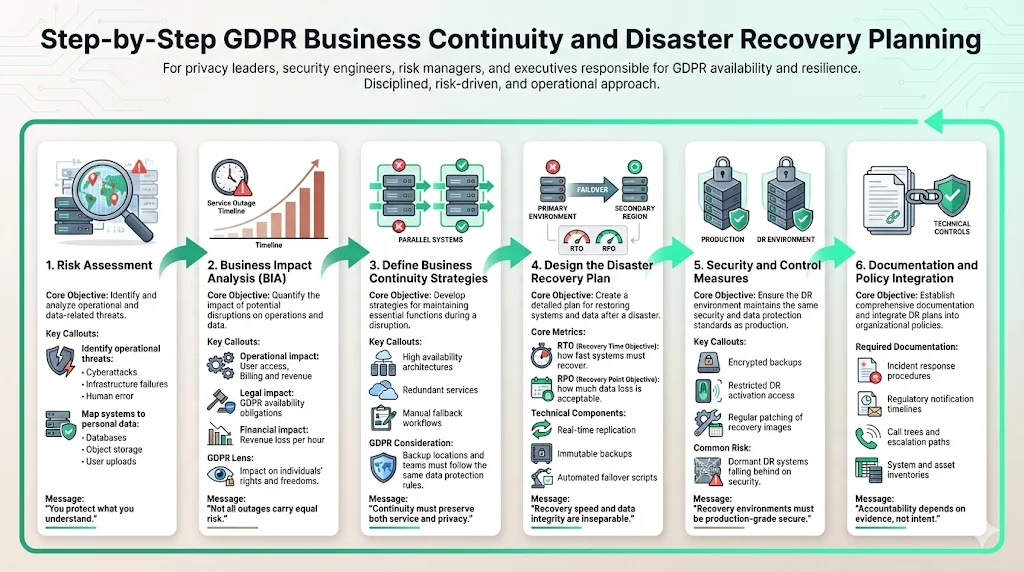
Step 1: Risk Assessment
The foundation of any security framework—whether SOC 2, ISO 27001, or GDPR—is the risk assessment. You must identify threats that could disrupt your operations. These range from cyberattacks (ransomware, DDoS) to physical issues (power outages, data center fires) and human error.
You must map your systems to the personal data they hold. Which servers house the customer database? Which S3 buckets store user uploads? By identifying where personal data lives, you can prioritize which systems need the strongest protection. In our managed service model, we conduct these assessments annually, or whenever a major infrastructure change occurs, ensuring the risk register reflects reality, not history.
Step 2: Business Impact Analysis (BIA)
Once risks are identified, the Business Impact Analysis (BIA) quantifies the consequence of disruption. You cannot protect everything equally; you must prioritize.
A BIA answers the question: "What happens if this specific service dies?"
- Operational Impact: Can we invoice? Can users log in?
- Legal/Compliance Impact: Are we breaching GDPR availability rules?
- Financial Impact: How much revenue do we lose per hour? The IBM Cost of a Data Breach Report 2024 indicates the global average cost has reached $4.88 million, with financial industry breaches soaring to $6.08 million.
For GDPR, you must specifically analyze the impact on the rights and freedoms of individuals. If a health app goes down, patients might miss medication reminders—a high-risk scenario demanding rapid recovery.
Step 3: Define Business Continuity Strategies
With the BIA complete, you define the strategies to keep running. This might involve:
- High Availability (HA): Using load balancers and redundant server clusters so that if one node fails, the service remains up.
- Alternate Workflows: If the automated identity verification system fails, do you have a manual process, or do you stop onboarding new users?
You must coordinate these strategies with GDPR principles. For instance, if your continuity plan involves switching to a backup call center, are the agents there trained on GDPR data handling? Does that location have the same security controls as your primary site?
Step 4: Design the Disaster Recovery Plan
This is the technical core. Your DR plan depends on two critical metrics:
- Recovery Time Objective (RTO): How quickly must the system be up? (e.g., 4 hours).
- Recovery Point Objective (RPO): How much data can you afford to lose? (e.g., 15 minutes of transactions).
For GDPR Business Continuity And DR, strict RPOs are often necessary to minimize data loss. We advise frequent, automated snapshots for databases containing PII (Personally Identifiable Information).
Core Technical Components:
- Replication: Real-time data mirroring to a secondary region.
- Immutable Backups: Backups that cannot be altered or deleted, providing a safeguard against ransomware encryption.
- Failover Scripts: Automated Infrastructure-as-Code (IaC) scripts (Terraform, Ansible) to rebuild environments instantly.
Step 5: Security and Control Measures
A common pitfall is restoring data into an insecure environment. The DR site must be as secure as the production site.
- Encryption: Backups must be encrypted at rest. If you ship tapes or drives (rare now, but it happens), they must be encrypted.
- Access Control: Who has the authority to trigger the DR plan? This should be restricted to authorized personnel to prevent malicious sabotage.
- Vulnerability Management: Your "dormant" DR infrastructure needs patching just like your active servers. We often find "gold images" for recovery that are years old and full of vulnerabilities.
Step 6: Documentation and Policy Integration
GDPR requires "accountability"—you must prove you are compliant. This means every step of your BCDR strategy must be documented.
Your documentation should include:
- Incident Response Plan: Who to call, when to report to the ICO (within 72 hours).
- Call Trees: Contact information for critical decision-makers.
- System Inventories: An up-to-date asset list.
This documentation serves as your audit trail. When we manage SOC 2 or ISO 27001 programs, we update these documents actively, ensuring they evolve as the business scales.
Testing and Maintenance
A plan that sits on a shelf is a liability. It provides a false sense of security that evaporates the moment a server fails.
Regular Testing
You must test your GDPR Business Continuity And DR capabilities regularly. We advise different levels of testing:
- Tabletop Exercises: A guided discussion where the team walks through a scenario (e.g., "Ransomware has encrypted our primary database"). This validates the decision-making process.
- Technical Failover Tests: Actually flipping the switch. For example, spinning up the backup database and verifying data integrity.
- Restoration Tests: Randomly selecting a backup file and restoring it to a sandbox environment to prove it is not corrupted.
Updating Plans
Technology changes fast. If you migrate from AWS to Google Cloud, your old DR plan is trash. If you add a new microservice that processes credit card numbers, it needs to be added to the BIA.
We continually update compliance artifacts for our clients. A "set and forget" mentality is dangerous. The plan must be reviewed at least annually or after significant infrastructure changes.
Role of Monitoring and Audit
You cannot recover from an incident you do not detect. Monitoring tools (SIEM, APM) are vital for triggering the BCDR process.
Internal audit plays a role here too. An internal auditor (or a managed partner like Konfirmity) should review the logs of your DR tests. Did you meet the RTO? If the target was 4 hours but it took 12, that is a "non-conformity" that needs fixing before a real crisis hits.
People and Training
Technology breaks, but people fix it. Your team is your most valuable asset during a disaster, but they can also be your biggest weakness if untrained.
Employee Training on Continuity Roles
Every employee needs to know their role. Developers need to know how to execute recovery scripts. Support staff need to know what to tell angry customers. Legal needs to know how to draft a breach notification.
We emphasize role-specific training. A general "security awareness" video once a year is insufficient for the engineering team responsible for database integrity. They need hands-on drills.
Importance of Incident Response Drills
Incident response drills strengthen the muscle memory of the organization. When a real event happens, panic is the enemy. Drills reduce panic.
These drills also reveal gaps in the GDPR Business Continuity And DR plan. You might discover that the person with the root password is on vacation and no one else has access. It is better to find that out during a Tuesday afternoon drill than during a Friday night outage.
Mapping Compliance to Enterprise Expectations
Enterprise buyers look at your security posture through the lens of their own risk management. They are not just buying software; they are buying a dependency.
Mapping to Enterprise Risk Management
Your BCDR strategy must map to the enterprise risk frameworks your clients use. If they follow NIST or ISO 31000, they expect your risk language to match theirs.
When we engage with client procurement teams, we map our clients' controls to the frameworks the enterprise cares about. We show them that our client's risk assessment methodology is sound and that the residual risk is acceptable. This builds trust and speeds up the "Vendor Risk Management" (VRM) phase of the sales cycle.
Reporting and Governance
Governance is about visibility. The Board of Directors needs to know if the company is resilient. They do not need to know the technical details of the SQL backup, but they do need to know if the RTO is being met.
Regular reporting on BCDR testing results, incident trends, and compliance status is crucial. This demonstrates to stakeholders—and eventually auditors—that the organization takes its obligations seriously.
Continual Improvement
There is no finish line. The threat environment changes, and so must your defense.
Feedback loops are essential. After every test or minor incident, perform a "Lessons Learned" or "Post-Mortem" analysis. What went wrong? What went right? Use these insights to refine the controls. This cycle of Plan-Do-Check-Act is the heart of ISO 27001 and is exactly what drives a mature GDPR Business Continuity And DR program.
Conclusion
GDPR Business Continuity And DR is a strategic imperative for any company dealing with enterprise data. It shifts the conversation from "Are we secure?" to "Are we resilient?"
Inadequate planning carries a heavy cost. Beyond the massive GDPR fines (up to 4% of global turnover), the reputational damage can be fatal. Enterprise clients do not forgive data loss. They churn.
At Konfirmity, we believe that security should look as good in practice as it does on paper. We don't just advise—we execute. By integrating continuity and recovery into a managed service, we ensure that when the worst happens, your business keeps moving. Start with security, build for resilience, and compliance will follow naturally.
FAQs
1) What’s the difference between business continuity and DR?
A continuity plan keeps operations running during disruption, often using workarounds; a DR plan restores technical systems and data after a major failure.
2) Do enterprise vendors need GDPR-compliant DR solutions?
Yes. Any vendor handling personal data or DR services for GDPR-covered data must meet compliance obligations. You are a processor, and your resilience is legally mandated.
3) How often should DR and continuity plans be tested?
Regularly, with documented results. We advise at least annual full-scale tests and quarterly tabletop exercises to show recoverability and compliance match.
4) What role do backups play in GDPR compliance?
Backups ensure availability and recoverability of personal data, which is a core GDPR requirement. They must be encrypted, tested, and controlled to prevent unauthorized access.





.svg)





.svg)
.svg)