The Health Insurance Portability and Accountability Act (HIPAA) sets the standard for protecting sensitive patient data. For modern healthcare technology companies, compliance is no longer just a legal obligation; it is a commercial necessity. Enterprise buyers and hospital systems now demand rigorous proof of security—often in the form of SOC 2 Type II reports or HIPAA performance audits—before procurement can proceed.
However, the migration to cloud computing has introduced complexity. When you lease infrastructure, you split the risk. The HIPAA Shared Responsibility Model clarifies this division. It dictates that while your cloud provider protects the hardware running your services, you remain accountable for protecting the patient data stored within those services.
Failing to grasp this distinction leads to "compliance gaps"—areas where the provider assumes you are handling security, and you assume the provider is handling it. In these gaps, breaches occur. The financial stakes are higher than ever: the 2024 IBM Cost of a Data Breach Report reveals that the average cost of a healthcare data breach has reached $10.1 million, the highest of any industry for 12 consecutive years.
The HHS Office for Civil Rights (OCR) has made it clear: you can outsource your infrastructure, but you cannot outsource your liability.
What Is the HIPAA Shared Responsibility Model?
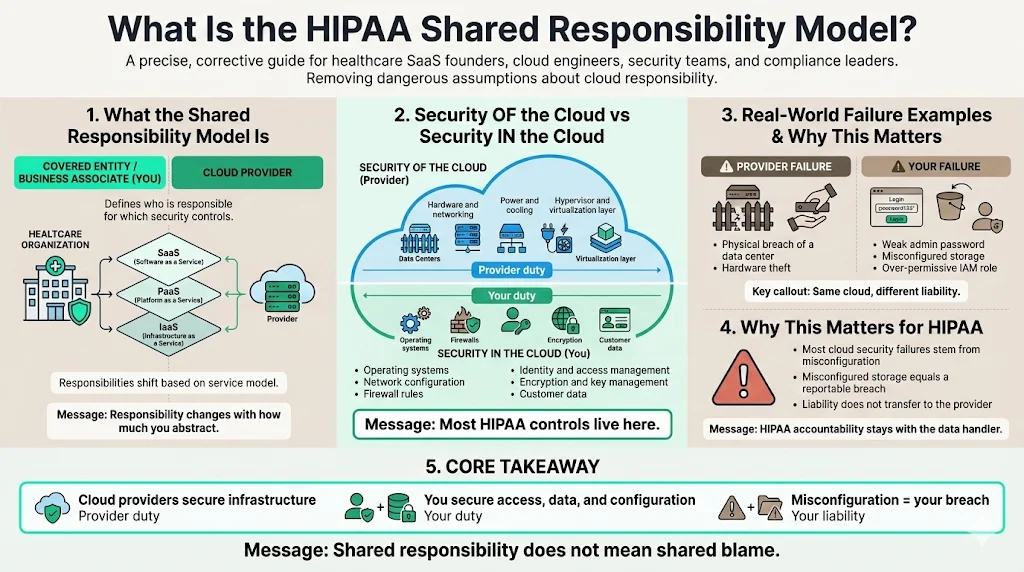
Security of the Cloud vs. Security in the Cloud
To simplify, major providers like AWS and Microsoft Azure define the split as follows:
- Security of the Cloud (Provider’s Duty): The provider safeguards the physical facilities, servers, networking hardware, and the virtualization layer. They ensure the power stays on, the building is secure from physical intrusion, and the hypervisor is patched.
- Security The HIPAA Shared Responsibility Model is a security and compliance framework that delineates the obligations of a Covered Entity (you, or your client) and a Business Associate (your cloud provider and vendors). It is not a 50/50 split. The distribution of duties shifts depending on the service model you use—Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS). the Cloud (Your Duty): You secure the operating systems, network configurations, firewall rules, identity and access management (IAM), customer data, and encryption.
If an attacker physically breaks into an AWS data center and steals a hard drive, that is the provider's failure. If an attacker guesses a weak password for your administrator account and exfiltrates a database, that is your failure.
This distinction is critical because, according to industry analysis, 99% of cloud security failures are the customer's fault. Under the HIPAA Shared Responsibility Model, a misconfigured S3 bucket constitutes a breach for which your organization is solely liable.
Core Elements of HIPAA Compliance
To implement this model effectively, you must understand the three central rules of HIPAA and how they interact with shared duties.
a. Privacy Rule
The Privacy Rule governs the use and disclosure of Protected Health Information (PHI). It focuses on who has access to data.
- Provider Role: They must ensure their support staff cannot access your data without authorization.
- Your Role: You must implement "Minimum Necessary" standards. This means configuring permissions so that only employees who absolutely need access to ePHI (electronic PHI) can see it. If you grant global admin rights to every developer, you violate the Privacy Rule, regardless of how secure the server is.
b. Security Rule
This is the technical heavy lifter. It mandates administrative, physical, and technical safeguards.
- Administrative: Policies, risk assessments, and training. This is almost entirely your burden. AWS cannot train your staff on phishing.
- Physical: Controlling access to servers. This is largely the provider's burden in a cloud environment.
- Technical: Audit logs, encryption, and automatic log-off. This is the friction point. The provider offers the tools (e.g., encryption keys), but you must configure and manage them.
c. Breach Notification Rule
This rule dictates the steps taken following a compromise.
- The Chain of Command: If the cloud provider suffers a breach, they must notify you. However, you are then responsible for notifying the affected individuals, the HHS Secretary, and potentially the media. The reputation damage hits your brand, not the infrastructure provider's.
Division of Duties: Who Does What?
In our work delivering managed security for growth-focused companies, we find that ambiguity creates risk. Here is a clear demarcation of roles.
a. Vendor / Cloud Provider Responsibilities
Your cloud provider handles the "concrete and steel" of security. Their duties include:
- Physical Security: Guards, fences, biometric entry for data centers.
- Host Infrastructure: Securing the computer, storage, and database networking hardware.
- Network Segmentation: Ensuring that one customer's data does not bleed into another's on the same physical hardware.
- Disposal: Properly destroying old hard drives and hardware.
The Business Associate Agreement (BAA):
Providers like Google Cloud or AWS will sign a BAA. This contract creates a liability bond. However, a BAA does not make a service compliant by default. It merely attests that the service can be configured in a compliant manner.
b. Healthcare Company Responsibilities
You handle the "logic and configuration" of security. Your duties include:
- Client-Side Encryption: Encrypting data before it leaves your internal environment.
- Server-Side Encryption: Configuring the cloud storage (e.g., S3 buckets) to encrypt data at rest.
- Network Traffic Protection: Managing SSL/TLS certificates and firewall configurations.
- Identity Management: Controlling user accounts, implementing Multi-Factor Authentication (MFA), and managing API keys.
- Operating System Patching: If you run EC2 instances or virtual machines, you must patch the OS.
- Application Logic: Ensuring your code does not contain vulnerabilities (like SQL injection) that could expose ePHI.
Security and Privacy Controls Under Shared Responsibility
To satisfy the HIPAA Shared Responsibility Model, you must implement specific controls. At Konfirmity, we implement these controls directly within our clients' environments rather than handing them a PDF of recommendations.
a. Data Security & Encryption
HIPAA requires encryption "whenever reasonable and appropriate." In 2025, it is always reasonable.
- At Rest: Use AES-256 encryption for all databases and file stores. Ensure you manage the keys or strictly control access to the key management service (KMS).
- In Transit: All data moving between your server and the user, or between internal microservices, must be encrypted using TLS 1.2 or higher.
b. Access Controls
Identity is the new perimeter.
- Least Privilege: Default to "deny all." Explicitly grant access only to specific resources.
- MFA: Mandate Multi-Factor Authentication for all access to cloud consoles and VPNs.
- Offboarding: When an employee leaves, their access must be revoked immediately. Gartner research indicates that 60% of companies with poor offboarding processes experience security breaches.
c. Incident Response
You cannot rely on your cloud provider to detect a logic breach.
- Logging: Enable CloudTrail (AWS) or equivalent logs. You must capture who accessed what data and when.
- Monitoring: Set up alerts for anomalies, such as a sudden export of large datasets.
- Testing: Run tabletop exercises. If you suffer a ransomware attack on a Friday night, does your team know who to call?
d. Training & Awareness
Technology cannot fix human error. The 2024 Verizon Data Breach Investigations Report found that the human element was involved in 68% of breaches.
- Phishing Sims: Regularly test employees.
- Policy Acknowledgement: Ensure all staff sign off on acceptable use policies annually.
e. Risk Management
HIPAA requires a formal risk assessment.
- Continuous Assessment: Risk is not a yearly checkbox. New code deploys introduce new risks. You must track vulnerabilities (CVSS scores) and remediation timelines.
Practical Implementation Templates
To move from theory to execution, use these templates as a starting point for your compliance operations.
a. Shared Responsibility Checklist
b. BAA Template Clauses
When reviewing a BAA with a vendor, ensure these clauses are clear:
- Breach Reporting Timeline: How quickly must they notify you of a security incident? (Ideally < 72 hours).
- Data Return/Destruction: What happens to the data if you terminate the contract?
- Subcontractors: Do they use third parties? The BAA must extend to them.
c. Risk Assessment Worksheet
Create a log (spreadsheet or GRC tool) with the following columns:
- Threat Source: (e.g., Phishing, SQL Injection, Insider Threat).
- Vulnerability: (e.g., Lack of MFA, Unpatched Server).
- Likelihood: (High/Medium/Low).
- Impact: (High/Medium/Low - consider financial, reputational, legal).
- Current Control: (e.g., "We use Okta for MFA").
- Remediation Plan: (Action item if control is weak).
d. Incident Response Plan Template
- Preparation: List of contacts (Legal, PR, Tech), tools, and access.
- Detection: How alerts are triaged.
- Containment: Steps to isolate the infected system (e.g., severing network connection).
- Eradication: Removing the threat.
- Recovery: Restoring data from backups.
- Post-Incident Activity: Documentation and "Lessons Learned."
Case Studies
The "Default Setting" Leak
A mid-sized telehealth provider migrated to the cloud. They signed a BAA with their provider and assumed compliance was achieved. However, they left an S3 storage bucket containing patient x-rays with "Public Read" access enabled—the default setting for that specific legacy configuration.
- The Result: 10,000 records exposed.
- The Verdict: The cloud provider was not at fault. They provided the tool to make the bucket private; the customer failed to use it. This highlights that the HIPAA Shared Responsibility Model requires active configuration, not passive consumption.
The Misconfigured Firewall
An EHR SaaS company opened port 22 (SSH) to the entire internet to allow developers easier access for debugging. Hackers brute-forced the root password.
- The Result: Ransomware installation.
- The Lesson: The provider secured the physical server, but the customer failed the "Security in the Cloud" obligation by allowing unrestricted network ingress.
Common Pitfalls and How to Avoid Them
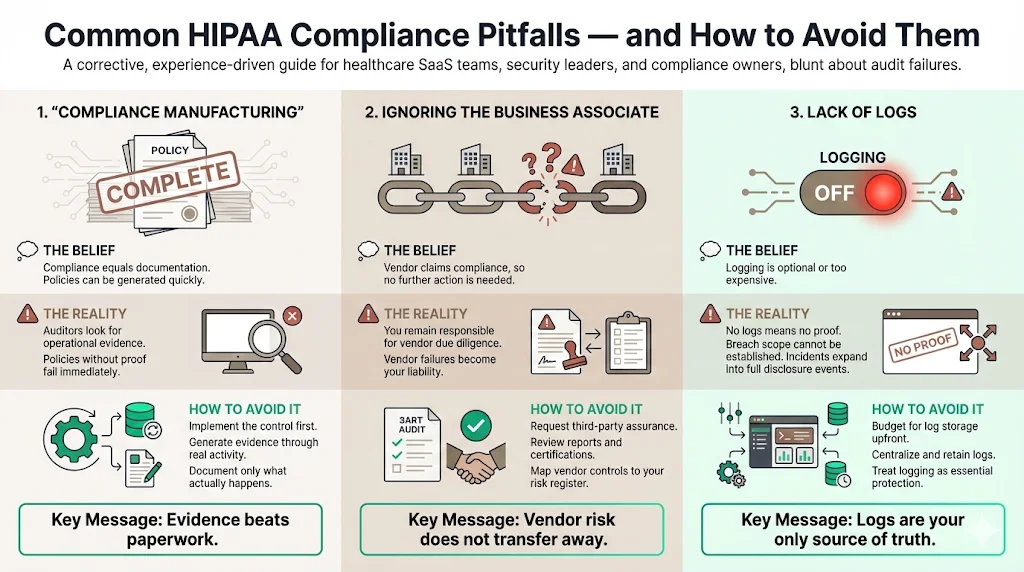
Pitfall 1: "Compliance Manufacturing"
Many companies treat compliance as a documentation exercise. They buy software that generates 50 policies in a day.
- The Reality: Auditors check for evidence, not just policies. If your policy says "We review access quarterly," but you have no logs proving you did it, you fail.
- Avoidance: Focus on security operations first. Build the control, then document it.
Pitfall 2: Ignoring the Business Associate
Believing that because a vendor claims to be "HIPAA Compliant," you don't need to vet them.
- The Reality: You are responsible for doing due diligence on your vendors.
- Avoidance: Request their SOC 2 report or HITRUST certification. Review it. Map their controls to your risk register.
Pitfall 3: Lack of Logs
Turning on logging often costs extra money (storage costs), so teams disable it.
- The Reality: Without logs, you cannot prove the scope of a breach. This turns a minor incident into a total disclosure event.
- Avoidance: Treat logging costs as a non-negotiable insurance premium.
Conclusion
The HIPAA Shared Responsibility Model is the defining contract of modern healthcare cloud computing. It offers a powerful advantage: you no longer need to build a fortress to protect a data center. However, it demands a pivot in mindset. You are now the architect of your own security controls within a rented facility.
For healthcare leaders, the path forward is clear. Stop viewing compliance as a hurdle to clear every 12 months. Start viewing it as a daily operational discipline. Implement strong access controls, encrypt everything, and monitor your environment continuously.
If this sounds like a heavy operational lift, that is because it is. Building a security program that stands up to scrutiny often requires hundreds of hours of internal effort if self-managed. This is why Konfirmity exists. We provide a human-led, managed service that embeds these controls into your stack, ensuring you are audit-ready year-round without burning out your engineering team.
Secure the data, and the compliance will follow.
FAQ Section
1) What is the HIPAA Shared Responsibility Model?
It is a framework that separates security obligations between a cloud provider and the healthcare organization. The provider secures the physical infrastructure (hardware, facilities), while the organization secures the data, applications, and access configurations living on that infrastructure.
2) Do I still need to sign a Business Associate Agreement (BAA)?
Yes. A BAA is legally mandatory under HIPAA for any vendor that processes, stores, or transmits ePHI on your behalf. It creates a liability chain. Without it, using that vendor for protected data is a HIPAA violation, regardless of technical security.
3) Who is ultimately responsible for HIPAA compliance?
The Covered Entity (the healthcare provider or plan) retains ultimate accountability. Even if a breach is the vendor's fault, the Covered Entity is responsible to the patient and the regulator for ensuring notification occurs. You cannot delegate accountability.
4) What security controls must my team implement?
At a minimum, you must implement Identity and Access Management (MFA, least privilege), Encryption (at rest and in transit), Audit Logging (tracking all access to ePHI), Vulnerability Management (patching), and Incident Response protocols.
5) Can HIPAA compliance be automated?
Automation can handle monitoring and evidence collection (e.g., checking if encryption is on), but it cannot replace governance. Automation cannot decide who should have access to data, nor can it negotiate a BAA. Compliance requires human judgment supported by automated tools.
6) How often should we conduct a risk assessment?
HIPAA requires it "periodically," but best practice is at least annually or whenever a significant change occurs in your environment (e.g., a new product launch, a merger, or a major infrastructure migration). Continuous risk monitoring is the gold standard for high-growth tech companies.





.svg)





.svg)
.svg)