Healthcare organizations operate under a unique pressure. Unlike other industries where data loss equates to financial theft or reputation damage, in healthcare, data integrity impacts patient care and safety. Yet, despite the high stakes, we consistently see organizations treating compliance as an annual paperwork exercise rather than an operational reality.
The Department of Health and Human Services (HHS) and the Office for Civil Rights (OCR) have made their stance clear through recent enforcement actions and projected trends for 2025: ignorance is not a defense. Managing Protected Health Information (PHI) requires more than a set of static policy documents stored on a shared drive. It requires active, continuous proof that security controls function as intended.
Why do gaps persist? Often, it is not due to negligence, but complexity. A fast-growing digital health startup or a mid-sized provider network focuses on functionality and patient outcomes. Security frequently trails behind, accumulating "compliance debt." Without regular checks, this debt grows until a breach occurs or an auditor asks for evidence that does not exist.
This HIPAA Gap Assessment Guide serves healthcare companies that store, process, or transmit patient data. Whether you are a covered entity or a business associate, understanding where your security program fails against regulations is the first step toward resilience.
In this guide, we will strip away the jargon. We will explain how to conduct a gap assessment, why it differs from a standard risk analysis, and how to transition from "hoping you are compliant" to knowing you are audit-ready. Drawing from Konfirmity’s experience supporting over 6,000 audits with 25+ years of combined technical expertise, we will show you how to build a security program that survives scrutiny.
Understanding HIPAA Gap Assessments
What a HIPAA Gap Assessment Is
A HIPAA gap assessment is a diagnostic process. It compares your organization’s current data privacy and security practices against the specific requirements of the Health Insurance Portability and Accountability Act (HIPAA). Think of it as a discrepancy report. On one side, you have the regulatory standards (what you must do); on the other, your actual operations (what you currently do). The difference between the two is the "gap."
This is not an abstract concept. If the Security Rule demands that all systems containing ePHI (electronic Protected Health Information) automatically log off after a period of inactivity, and your clinical workstations remain active indefinitely, that is a gap. If the Privacy Rule requires a Business Associate Agreement (BAA) with every vendor handling data, and you use a generic cloud storage provider without one, that is a high-risk gap.
How It Compares to a General Risk Assessment
Many leaders conflate a gap assessment with a risk analysis, but they serve different functions. A risk analysis, required by 45 CFR § 164.308(a)(1)(ii)(A), identifies potential threats and vulnerabilities to your information assets. It asks: "What could go wrong, and how likely is it?"
A gap assessment is more binary and prescriptive. It asks: "Are we meeting the specific implementation specifications defined in the law?" While a risk analysis focuses on threats (e.g., ransomware, insider threat), a gap assessment focuses on controls (e.g., do we have multi-factor authentication enabled? Is encryption active at rest?).
The Role in Compliance and Regulations
For healthcare compliance, the gap assessment is your roadmap. You cannot fix what you do not measure. By identifying deficiencies early, organizations can prioritize budget and engineering resources effectively.
Additionally, NIST (National Institute of Standards and Technology) guidelines and OCR audits emphasize that compliance is not a "one-and-done" achievement. It is a continuous state. A gap assessment provides the baseline measurement needed to demonstrate improvement over time—a critical factor if you ever face an investigation.
Why HIPAA Gap Assessments Matter
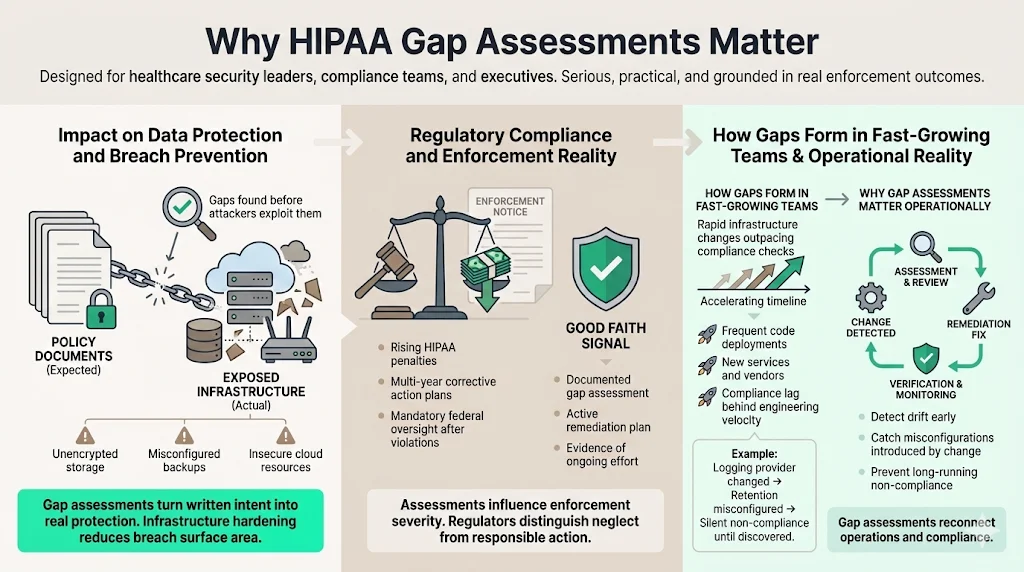
Impact on Data Protection and Breach Prevention
A gap assessment is often the primary mechanism for discovering a vulnerability before an attacker does. At Konfirmity, we often find that the most dangerous gaps are not missing policies, but missing technical configurations. A policy might state that "all data is encrypted," but a technical review during a gap assessment reveals an unencrypted S3 bucket or a database backup stored in cleartext.
Closing these gaps directly hardens your infrastructure. It moves security from a theoretical document to a practical defense, reducing the surface area available for a breach.
Connection to Regulatory Compliance and Enforcement
The cost of non-compliance is rising. In 2025, penalty tiers for HIPAA violations continue to adjust for inflation, with maximum annual penalties reaching nearly $2 million per violation category (see Federal Register notices for exact CMP adjustments). Beyond fines, the OCR often mandates Corrective Action Plans (CAPs) that force organizations into years of strict federal monitoring.
A documented HIPAA Gap Assessment Guide and the resulting remediation plan serve as evidence of "good faith." If a breach occurs, being able to show that you identified gaps and were actively working to close them can significantly influence the severity of enforcement actions. It distinguishes an organization that is trying to do right from one that is willfully neglectful.
How Gaps Appear in Fast-Growing Teams
In high-growth healthcare environments, infrastructure changes weekly. Engineering teams ship code, adopt new microservices, and onboard new SaaS tools to improve velocity. Compliance documentation rarely keeps pace.
A gap often opens when a technical change occurs without a corresponding compliance check. For example, an engineering team might switch logging providers to save costs but fail to configure the new provider to retain logs for the required six years. Without a scheduled assessment to catch this change, the organization remains non-compliant until an external event exposes the issue.
HIPAA Rules That Shape a Gap Assessment
To conduct a successful review, you must understand the three major pillars of HIPAA.
HIPAA Privacy Rule
The Privacy Rule governs the use and disclosure of PHI. It focuses on patient rights and administrative requirements.
- Use and Disclosure: Are you only sharing the "minimum necessary" data to accomplish a specific task?
- Policies: Do you have a Notice of Privacy Practices? Is it accessible to patients?
- Access Limits: Does your workforce have access to all patient records, or only the records relevant to their job function?
A gap assessment here often flags operational issues, such as receptionists repeating sensitive conditions aloud or marketing teams using patient emails without proper consent.
HIPAA Security Rule
The Security Rule is the technical core of HIPAA, covering ePHI. It dictates the safeguards that must be in place to ensure confidentiality, integrity, and availability.
- Administrative Safeguards: Governance, risk analysis, and workforce training.
- Physical Safeguards: Facility access controls, workstation security, and device media controls.
- Technical Safeguards: Access control, audit controls, integrity, person or entity authentication, and transmission security.
This is where Konfirmity spends the majority of its time. We map these requirements to frameworks like SOC 2 and ISO 27001 to create a unified control set. If you are encryption-compliant for SOC 2, you are likely encryption-compliant for HIPAA, provided the scope includes ePHI.
HIPAA Breach Notification Rule
This Breach Notification Rule dictates what you must do when things go wrong.
- Timelines: You generally have 60 days to report a breach.
- Documentation: Do you have a defined process for investigating a potential incident?
A common gap we see is a lack of a clear internal reporting channel. Employees may suspect a security issue but not know whom to alert, causing delays that violate the notification timeline.
When a HIPAA Gap Assessment Should Be Performed
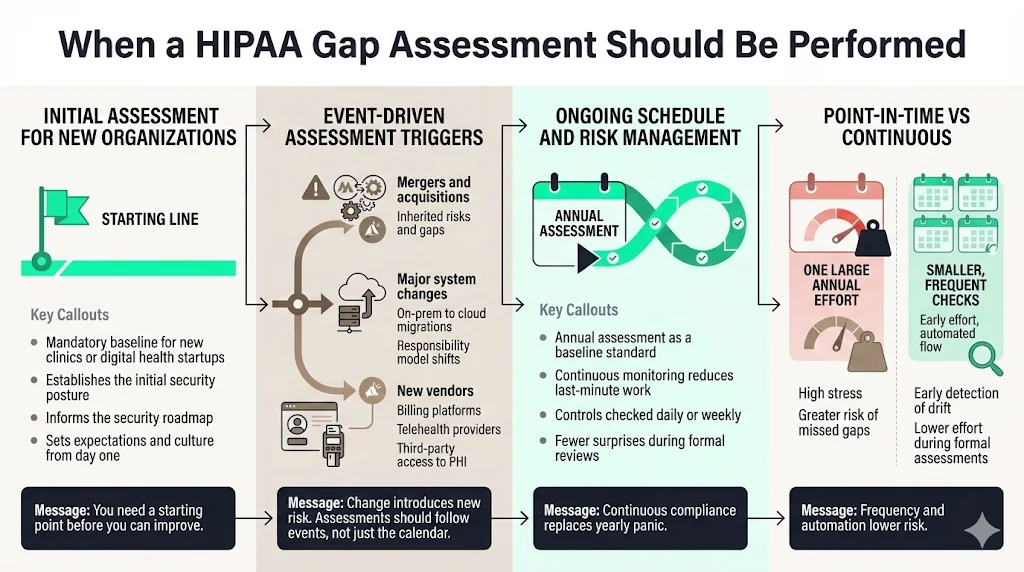
Initial Assessment for New Organizations
If you are a new digital health startup or a clinic opening its doors, a baseline assessment is mandatory. You cannot build a security roadmap without knowing your starting point. This initial assessment sets the tone for your security culture.
Triggers: System Changes, Mergers, or Vendors
Assessment should be event-driven.
- Mergers and Acquisitions: When acquiring another practice, you inherit their risks. Their gaps become your gaps.
- System Changes: Migrating from an on-premise server to AWS or Azure changes your responsibility model. A gap assessment ensures new cloud configurations meet Security Rule standards.
- Vendor Onboarding: Adopting a new billing platform or telehealth provider introduces third-party risk that must be evaluated.
Ongoing Schedules and Risk Management
For stable organizations, an annual assessment is the standard recommendation. However, at Konfirmity, we advocate for continuous compliance. Rather than a massive yearly panic, we implement monitoring that checks controls daily or weekly. This shift from "point-in-time" to "continuous" reduces the effort required for annual reviews.
Core Areas Reviewed in a HIPAA Gap Analysis
Policies and Documentation
Auditors trust what they can read. Your first step is reviewing the "paper" layer.
- Privacy Policies: Are they current? Do they reflect actual workflows?
- Security Procedures: Do you have written instructions for onboarding/offboarding employees, responding to malware, and managing passwords?
- Gap Analysis: We often find policies downloaded from the internet that reference technologies the company does not own. This is an immediate red flag.
Technical Safeguards
This review dives into your tech stack.
- Access Controls: Are you using Unique User IDs? Is Multi-Factor Authentication (MFA) enforced on all remote access points?
- Encryption: Is data encrypted at rest (AES-256) and in transit (TLS 1.2+)?
- System Monitoring: Are you collecting logs? Are you reviewing them? Many organizations collect terabytes of logs but lack the alerts to notify them of suspicious activity.
Administrative Safeguards
This covers the human element.
- Workforce Training: Is security awareness training mandatory upon hire and annually thereafter? Do you have proof of completion?
- Role-Based Access: Who decides who gets admin privileges? Is there a periodic review to revoke unnecessary access?
- Incident Response: Is there a team designated to handle breaches? Have they practiced the plan?
Physical Safeguards
Even cloud companies have physical assets.
- Facility Access: Who has a key or badge to the office?
- Device Security: Are laptops encrypted? Do you track mobile devices containing ePHI?
- Remote Work: With the rise of distributed teams, home office security (clean desk policy, secure Wi-Fi) is now a scrutiny point.
Vendor and Third-Party Risk
You are responsible for your supply chain.
- Business Associate Agreements (BAAs): Do you have a signed BAA with every vendor handling ePHI?
- Shared Responsibility: Do you understand where your cloud provider’s security stops and yours begins?
Step-by-Step HIPAA Gap Assessment Process
Conducting a HIPAA Gap Assessment Guide focused review requires a structured approach.
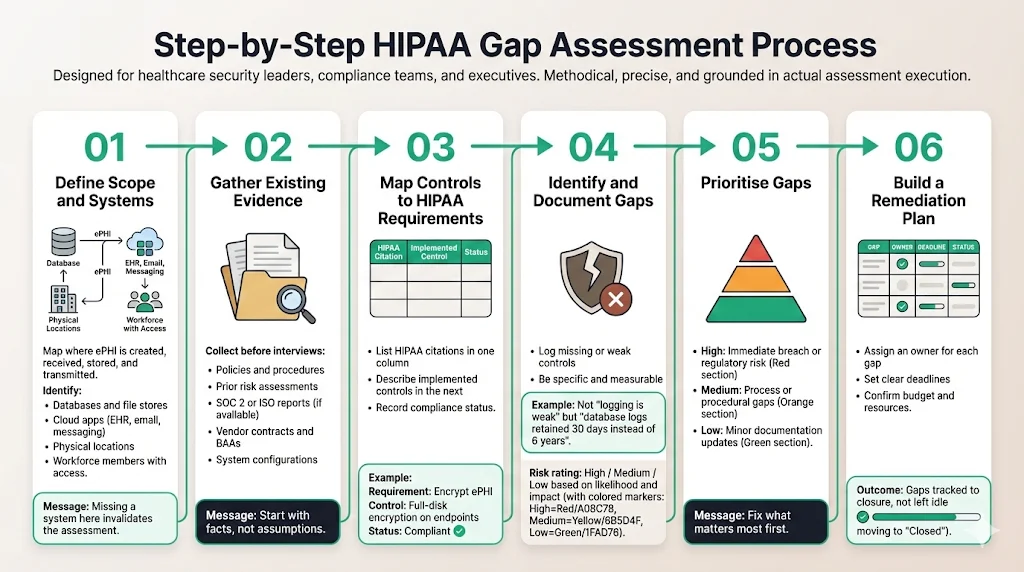
Step 1: Define Scope and Systems
You cannot protect what you cannot see. Begin by mapping the flow of data. Where is ePHI created, received, maintained, or transmitted?
- Identify all databases, file servers, and cloud applications (EHR, Slack, Email).
- Identify all physical locations.
- Identify all workforce members with access.
If you miss a system here, the rest of the assessment is flawed.
Step 2: Gather Existing Evidence
Before interviewing staff, collect what you have.
- Current policy manuals.
- Previous risk assessments.
- SOC 2 or ISO 27001 reports (if available).
- Vendor contracts and BAAs.
- System configurations (password policies, firewall rules).
Step 3: Map Controls Against HIPAA Requirements
Create a matrix. List every HIPAA citation (e.g., §164.312(a)(1)) in one column. In the next, describe the control you have in place.
- Requirement: Implement a mechanism to encrypt and decrypt ePHI.
- Control: All MacBook hard drives are encrypted via FileVault; keys are managed via MDM.
- Status: Compliant.
Step 4: Identify and Document Gaps
Where a control is missing or insufficient, log a gap. Be specific.
- Vague: "Logging is weak."
- Specific: "Production database access logs are overwritten every 30 days; HIPAA requires 6 years of retention."
Assign a risk rating (High, Medium, Low) based on the likelihood of exploitation and the potential impact on data confidentiality.
Step 5: Prioritize Gaps
You cannot fix everything overnight. Prioritize based on risk and effort.
- Critical/High: Immediate breach risks or flagrant regulatory violations (e.g., no BAA with a hosting provider, no MFA). Fix these immediately.
- Medium: Process improvements (e.g., updating the employee handbook, formalizing the disaster recovery test).
- Low: Minor documentation edits.
Step 6: Build a Remediation Plan
For every gap, assign an owner and a due date.
- Ownership: Who is responsible? (e.g., CTO for encryption, HR Director for training).
- Resources: Do they have the budget and time to fix it?
At Konfirmity, we help clients manage this remediation. We know that self-managed compliance often takes 550–600 hours of internal time. By utilizing a managed service, we reduce that burden to approximately 75 hours per year, ensuring remediation actually happens rather than stalling in a Jira backlog.
Practical HIPAA Gap Assessment Examples
To illustrate how this works, let us look at three common scenarios we encounter.
Example 1: Access Control Weakness
Finding: During an assessment of a mid-sized clinic, we discovered that three nurses shared a single login ("NurseStation1") to access the Electronic Health Record (EHR) system.
The Gap: HIPAA requires unique user identification (§ 164.312(a)(1)). Shared accounts destroy accountability; if "NurseStation1" deletes a record, you cannot prove who did it.
Risk: High. Inability to audit user actions.
Correction: We integrated the EHR with the clinic’s central identity provider (Okta), issued individual credentials to all nurses, and disabled the shared account.
Example 2: Missing Vendor Agreements
Finding: A health-tech startup used a popular email marketing tool to send patient appointment reminders.
The Gap: The startup had not signed a BAA with the email provider. Additionally, the standard terms of service for the email provider claimed ownership of the data.
Risk: Critical. Unauthorized disclosure of PHI to a third party.
Correction: The startup migrated to a HIPAA-compliant email service that signed a BAA and updated their data flow diagram to reflect the change.
Example 3: Incomplete Incident Response Plan
Finding: An organization had an Incident Response policy that simply stated, "Call the IT Manager."
The Gap: The plan lacked definitions of what constitutes an incident, escalation paths, legal counsel involvement, and communication templates.
Risk: Medium/High. In the event of a breach, chaos would ensue, leading to missed notification deadlines.
Correction: We drafted a detailed playbook, established a "war room" protocol, and conducted a tabletop exercise to simulate a ransomware attack.
Common HIPAA Compliance Gaps to Watch For
Through our work across thousands of audits, we see recurring patterns.
- Infrequent Risk Assessment Updates: Many companies do one assessment and never return to it. Risk is dynamic; your assessment must be too.
- Training Gaps: Organizations often train full-time staff but neglect contractors or interns. Everyone with access to data needs training.
- Weak Monitoring: Buying a security tool is not enough. Someone must look at the dashboard. We often see intrusion detection systems that have been alerting for months with no response.
- Poor Documentation Control: Policies saved as "Final_Final_v2.docx" on a desktop are not sufficient. You need version control and distribution logs.
- Terminated User Access: A surprisingly common gap is failing to revoke access for employees who have left the company. This is an easy win for attackers.
How Gap Assessments Support Audit Readiness
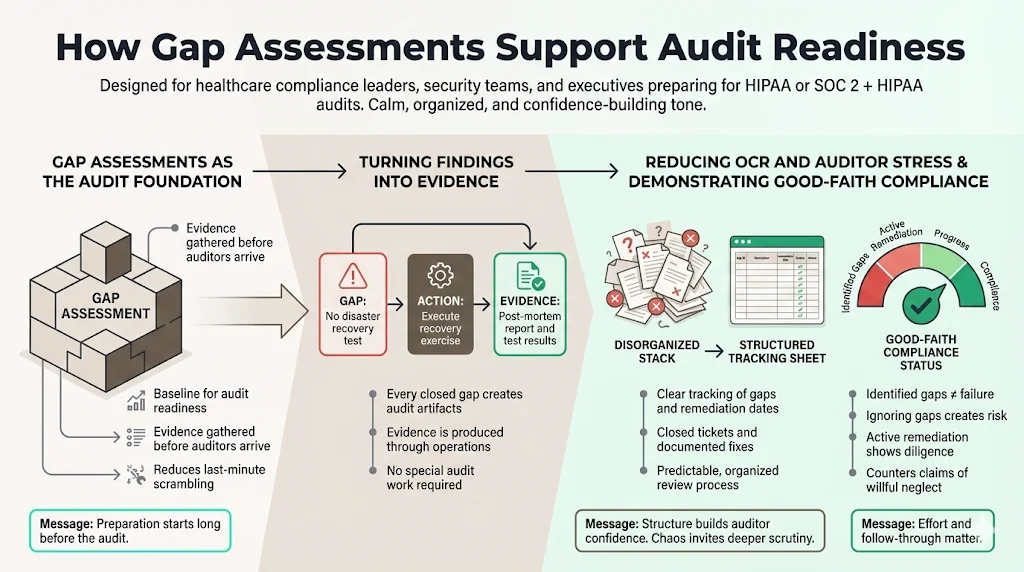
If your goal is to pass a HIPAA audit or obtain a SOC 2 + HIPAA attestation, the gap assessment is your foundation. It allows you to gather evidence before the auditor arrives.
Turning Findings into Evidence
Every gap you close generates a piece of evidence.
- Gap: "No disaster recovery test."
- Fix: Run the test.
- Evidence: The post-mortem report from the test.
Reducing OCR and Auditor Stress
Auditors are human. When they see a disorganized mess, they dig deeper. When they see a structured HIPAA Gap Assessment Guide tracking sheet with clear remediation dates and closed tickets, they gain confidence in your management. It signals that you are in control.
Showing Good-Faith Compliance
As mentioned regarding enforcement, the OCR looks for "willful neglect." A gap assessment proves the opposite. It shows diligence. Even if you have open gaps, the fact that you have identified them and are actively fixing them is a strong defense.
Tools and Checklists That Support Gap Assessments
While you can conduct a gap assessment using spreadsheets, it is inefficient and prone to error.
Structured Checklists
Use standard checklists provided by NIST (SP 800-66) or the OCR’s audit protocol. These lists break down every rule into testable inquiries.
Internal Tracking
You need a system of record. Whether it is a GRC (Governance, Risk, and Compliance) platform or a dedicated project in Jira, tracking must be centralized.
The Role of Automation
Automation is essential for scaling. You cannot manually check 500 laptops for encryption every week. Konfirmity utilizes automated agents that sit within your infrastructure, querying configurations and reporting status back to a central dashboard. This moves you from "checking boxes" to "monitoring reality."
However, software alone is not the answer. Software creates alerts; humans provide context. A managed service combines the speed of automation with the judgment of a CISO.
What Happens After Gaps Are Identified
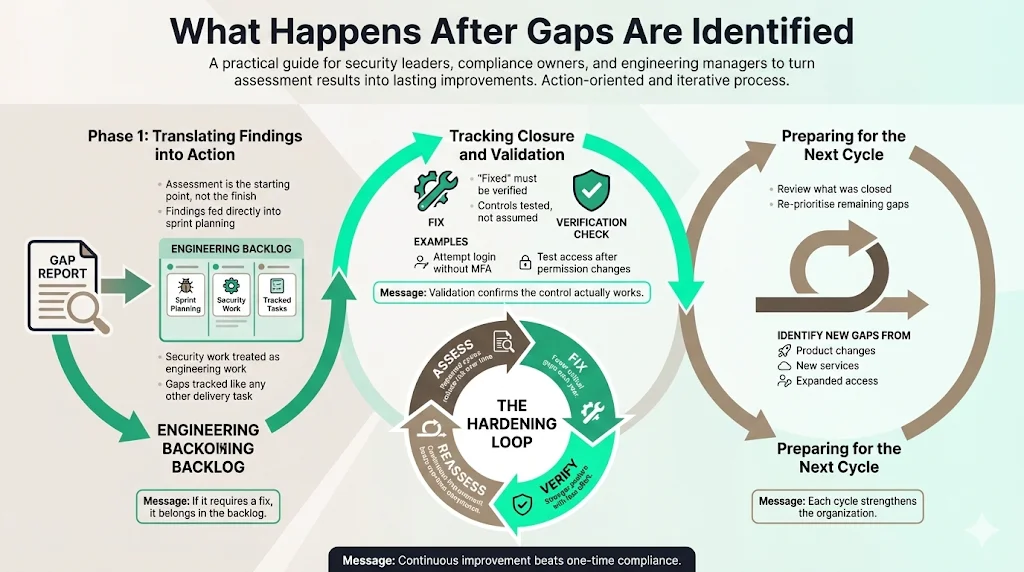
The assessment is not the end; it is the starting line.
Translating Findings into Action
Do not let the report gather dust. Integrate findings into your engineering sprints. Security work is engineering work. If a gap requires a code change, put it in the backlog alongside feature requests.
Tracking Closure and Validation
Once a gap is marked "fixed," verify it. Don't take a developer’s word for it; test it. If the fix was enabling MFA, try to log in without it. Validation ensures the control is effective.
Preparing for the Next Cycle
Use the current assessment to inform the next one. Did we fix the high-priority items? Did new gaps emerge in the new product lines? This cyclical process creates a hardening loop, making your organization stronger every year.
Conclusion
A HIPAA Gap Assessment Guide is more than a document; it is a critical operational tool for any healthcare organization. It bridges the divide between regulatory expectations and technical reality.
In a market where enterprise buyers demand proof of security before signing contracts, and where patients entrust you with their most sensitive data, you cannot afford to operate in the dark. A gap assessment turns the lights on. It reveals the cracks in your foundation so you can repair them before the pressure of a breach causes a collapse.
We encourage you to treat this process not as a burden, but as a competitive advantage. A secure, compliant organization closes deals faster, retains patient trust, and avoids the catastrophic costs of regulatory enforcement.
Start with security. Build durable controls. Let compliance follow naturally.
Frequently Asked Questions
1) What is a HIPAA gap assessment?
A HIPAA gap assessment is a review process that compares an organization’s current data privacy and security measures against the specific requirements of the HIPAA Privacy, Security, and Breach Notification Rules. Its purpose is to identify areas of non-compliance (gaps) so they can be remediated.
2) How often should a HIPAA gap assessment be done?
While HIPAA does not specify an exact frequency, industry best practice is to perform a gap assessment annually. Additionally, assessments should be triggered by major operational changes, such as mergers, new system implementations, or significant changes to the threat environment.
3) What areas are reviewed during a HIPAA gap analysis?
A comprehensive analysis reviews policies and procedures (documentation), technical safeguards (access control, encryption, auditing), physical safeguards (facility access, device security), administrative safeguards (training, risk management), and third-party vendor relationships (BAAs).
4) How does a gap assessment support audit readiness?
It identifies deficiencies before an external auditor does, allowing the organization to fix issues and generate the necessary proof (evidence) of compliance. It demonstrates a proactive, risk-based approach to security, which is a key requirement for both HIPAA and frameworks like SOC 2.
5) What happens after gaps are identified?
The organization creates a remediation plan. Gaps are prioritized based on risk, owners are assigned, and timelines are set. The organization then works to close these gaps, validating the fixes and documenting the improvements for future reference.





.svg)





.svg)
.svg)