For B2B companies selling to large enterprises or healthcare organizations, the procurement cycle hits a concrete wall when the buyer’s risk team asks for proof of data protection. With 28% of sales professionals citing lengthy processes as the primary reason deals stall, the security review has become a major bottleneck.
Buyers do not care about your marketing claims regarding privacy. They care about liability. They want to know that if they transfer customer data to your SaaS platform, you have the operational machinery to protect it.
Most vendors fail here because they treat compliance as a legal disclaimer. They offer a privacy policy when the buyer asks for a GDPR Controls List.
A privacy policy is a public statement; a controls list is operational proof. It maps specific regulatory requirements to the actual configurations, workflows, and checks happening inside your engineering and HR teams. Without a clear, mapped set of controls, security questionnaires drag on for weeks. Legal teams get stuck in redlines over Data Processing Addendums (DPAs).
At Konfirmity, we have supported over 6,000 audits across SOC 2, ISO 27001, and GDPR. We see a consistent pattern: companies with a structured control set close deals 4–5 months faster than those scrambling to "manufacture" evidence during due diligence.
This guide explains how to build a GDPR Controls List that satisfies enterprise auditors and shortens your sales cycle.
What Is a GDPR Control List?
A GDPR Controls List is a documented registry of the technical and organizational measures (TOMs) your company uses to satisfy the General Data Protection Regulation.
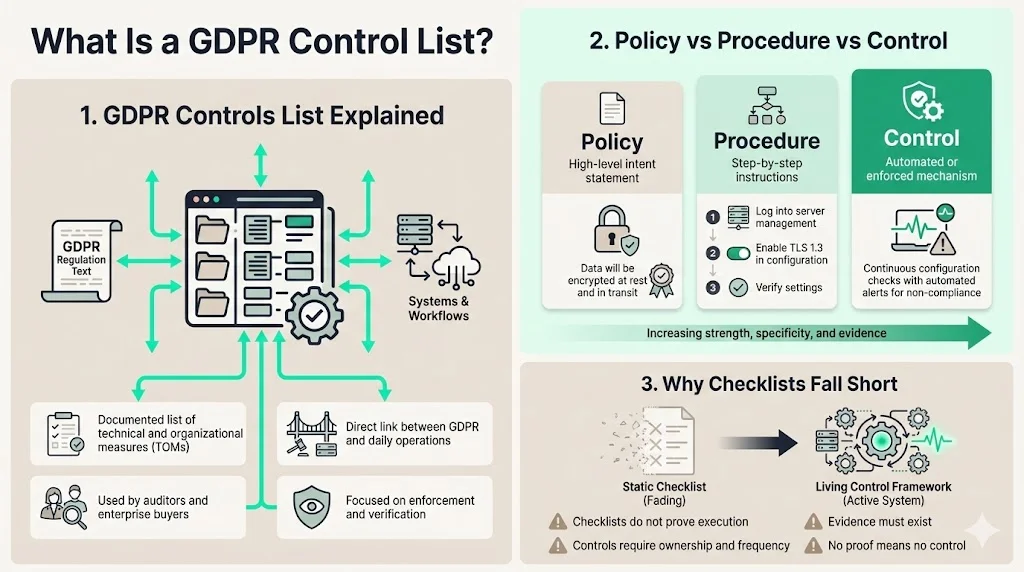
It is critical to distinguish between policies, procedures, and controls, as enterprise auditors will test them differently.
- Policy: A high-level statement of intent (e.g., "We encrypt all personal data").
- Procedure: The step-by-step instruction (e.g., "Engineers must enable TLS 1.3 on the load balancer").
- Control: The active mechanism that enforces or verifies the rule (e.g., "An automated configuration check runs daily to verify TLS 1.3 is enabled and alerts the CISO if disabled").
When an enterprise buyer asks, "How are you GDPR compliant?" they are not asking if you have read the law. They are asking for your controls list. They want to see the link between the regulation and your day-to-day operations.
Checklists alone are insufficient. A checklist is static; a control framework is alive. It involves ownership, evidence collection, and frequency. If your list says you "review access rights," but you are unable to produce a ticket or log showing that review happened last quarter, you do not have control—you have a wish.
GDPR Roles and Scope
Before defining controls, you must define your position in the data supply chain. This is the first question on every enterprise vendor risk assessment.
Controllers vs Processors
In the B2B context, this distinction drives your liability.
- Controller: The entity that decides why and how data is processed. If you sell directly to consumers (B2C) or determine how to use your employees' data, you are a Controller.
- Processor: The entity that processes data on behalf of the Controller. Most B2B SaaS companies are Processors. Your enterprise client (the Controller) sends you their data to perform a service (hosting, analytics, CRM).
Responsibilities:
- Controllers must prove they have a lawful basis for processing and managing consent.
- Processors must secure the data, assist the Controller with data subject requests, and only process data based on written instructions (the DPA).
Confusion arises when a Processor starts using client data to train their own AI models or for internal analytics. At that moment, you may cross the line into becoming a Controller, triggering a much heavier compliance burden.
Why This Matters for Enterprise Sales
Enterprise buyers assess you based on your role. If you are a Processor, they will demand strict controls around "Data Segregation" and "Instruction Adherence." They will ask: Can your support team see our data without a ticket? Do you delete our data 30 days after contract termination?
If you fail to answer these questions with specific controls, the buyer’s legal team will assume you are a high-risk vendor.
Core GDPR Control Categories
This section details the specific operational areas your GDPR Controls List must cover. These are not theoretical; they are the rows in your spreadsheet or GRC platform that auditors will inspect.
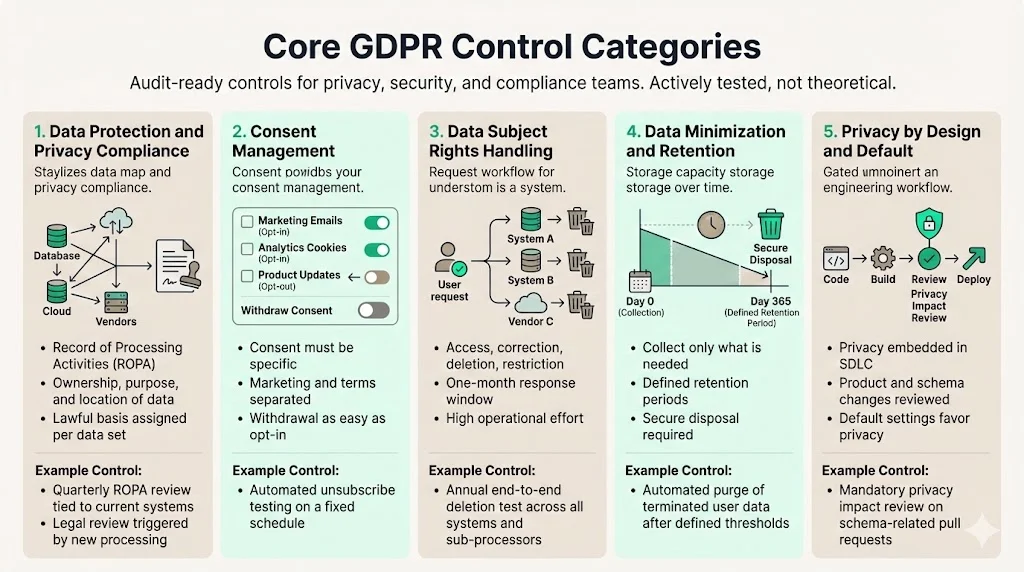
1) Data Protection and Privacy Compliance
This category establishes your legal footing.
- Record of Processing Activities (ROPA): Article 30 requires you to maintain a map of where personal data lives, who owns it, and why you have it.
- Control: "Quarterly review of data inventory by Department Heads to ensure the ROPA matches current tech stack usage."
- Lawful Basis: You must document the legal justification for every data set (e.g., contract necessity, legitimate interest).
- Control: "New processing activities trigger a legal review to assign a lawful basis before deployment."
2) Consent Management
Even as a B2B Processor, consent controls apply to your marketing lists and cookies.
- Granularity: Consent must be specific. Lumping "Terms of Service" and "Marketing Emails" into one checkbox is a violation.
- Withdrawal: It must be as easy to withdraw consent as it was to give it.
- Control: "Automated unsubscription workflow tests are conducted bi-annually to verify removal from active mailing lists."
3) Data Subject Rights (DSR) Handling
This is often the most operationally expensive area. Under GDPR, individuals have the right to access, correct, delete (Right to be Forgotten), or restrict the processing of their data.
- Response Timelines: You typically have one month to respond.
- The Technical Challenge: If a user asks for deletion, do you know where their data is? Is it in your primary database? Backups? Third-party tools like HubSpot or Salesforce?
- Control: "DSR procedural test conducted annually where a dummy user is fully deleted across all sub-processors within 30 days."
4) Data Minimization and Retention
Hoarding data is a liability. The GDPR mandates you collect only what is necessary and keep it only as long as needed.
- Retention Schedules: You need a policy that dictates deletion times (e.g., "Financial records: 7 years," "Session logs: 90 days").
- Secure Disposal: Deleting a file isn't enough; storage media must be sanitized.
- Control: "Automated script runs nightly to purge user data flagged as 'terminated' > 30 days."
5) Privacy by Design and Default
Article 25 requires that privacy isn't an afterthought. This means engineering controls.
- Product Changes: Privacy checks must be part of the SDLC (Software Development Life Cycle).
- Control: "All engineering change requests (PRs) involving schema changes require a 'Privacy Impact' tag and security review before merge."
Security and Technical Controls
Security is the foundation of privacy. Privacy is impossible if your database is leaked on the dark web. This is where your GDPR Controls List will overlap significantly with frameworks like SOC 2 and ISO 27001.
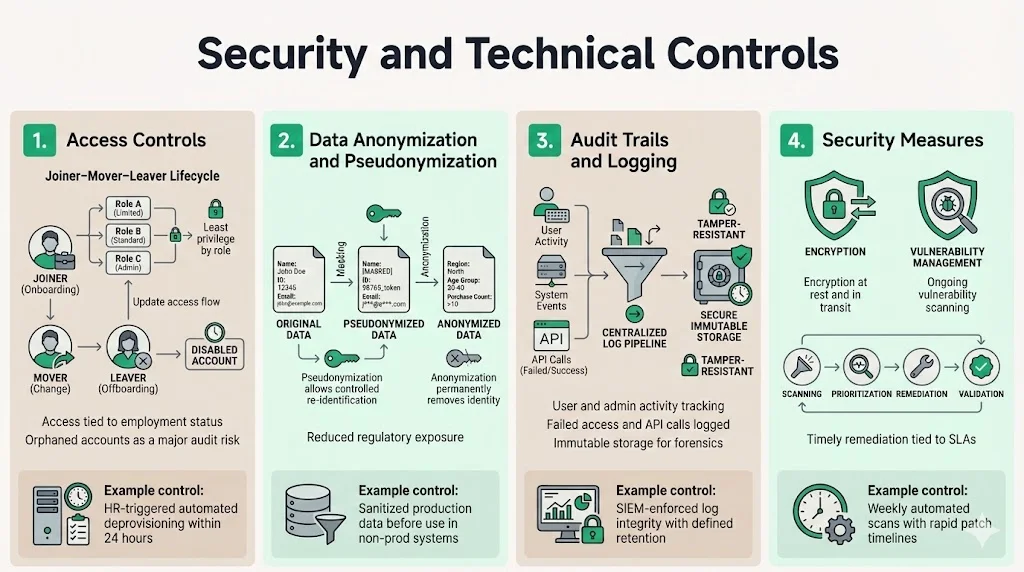
1) Access Controls
Enterprise buyers are obsessed with who can see their data.
- Least Privilege: Employees should only have access necessary for their role.
- JML Process (Joiners, Movers, Leavers): The most common audit failure is active accounts belonging to former employees.
- Control: "HR system automatically triggers IT deprovisioning workflow upon employee termination; access revoked within 24 hours."
2) Data Anonymization and Pseudonymization
If you can strip identifiers from data, GDPR restrictions loosen.
- Pseudonymization: Replacing names with IDs (e.g., User_123). The data can be re-identified with a key.
- Anonymization: Irreversibly destroying the link to the individual.
- Control: "Production database snapshots are sanitized (PII removed) before migration to staging/QA environments."
3) Audit Trails and Logging
Accountability requires evidence.
- What to Log: User logins, failed access attempts, privileged actions (sudo commands), and API access to sensitive data.
- Log Retention: Logs should be kept secure and immutable for forensic analysis.
- Control: "SIEM configuration prevents log modification; logs retained for 12 months in cold storage."
4) Security Measures
These are the standard "hard" security controls referenced in Article 32.
- Encryption: Data must be encrypted at rest (AES-256) and in transit (TLS 1.2+).
- Vulnerability Management: Regular scanning and patching.
- Control: "Weekly automated vulnerability scans on all public-facing endpoints; critical findings patched within 72 hours per SLA."
Risk and Incident Management
Risk Assessment
Protecting what you do not understand is impossible. The GDPR requires a risk-based approach.
- DPIA (Data Protection Impact Assessment): Required for high-risk processing (e.g., large-scale tracking, biometric data).
- Control: "DPIA trigger checklist applied to all new projects; assessments filed with the DPO."
- Cadence: Risk assessments should happen at least annually or upon major structural changes.
Data Breach Notification
Article 33 sets a strict timer: 72 hours to notify the supervisory authority after becoming aware of a breach, unless the breach is unlikely to result in a risk to rights and freedoms.
- Escalation: Your engineers need to know that a "weird server log" might be a legal emergency.
- Control: "Annual tabletop exercise simulating a data breach to test communication channels and legal escalation paths."
People and Process Controls
Technology fails, but people fail more often.
Training and Awareness
Ignorance is not a defense.
- Frequency: Onboarding and annual refreshers are the minimum.
- Content: Training must be relevant. Developers need secure coding training; sales teams need training on not promising features that violate privacy.
- Control: "Learning Management System (LMS) report generated monthly to identify and follow up with non-compliant staff."
Vendor Management
Your liability extends to your supply chain (sub-processors).
- Due Diligence: You must vet AWS, Stripe, Slack, and that small AI plugin your marketing team wants to use.
- Contractual Clauses: Every vendor touching PII needs a signed DPA.
- Control: "Procurement policy blocks payment to new vendors until Security completes a risk review and Legal confirms DPA execution."
Mapping Controls to Enterprise Expectations
When an enterprise buyer sends you a spreadsheet with 300 questions, they are looking for maturity. They map your answers against frameworks like the NIST Privacy Framework or ISO 27701.
Common requests from procurement teams include:
- SOC 2 Type II Report: This validates your security controls are operating effectively over time.
- Penetration Test Report: Proof you test your own defenses.
- GDPR Statement of Applicability: A document stating which GDPR articles apply to you and how you meet them.
If you have a solid GDPR Controls List, you can map these requests directly to your existing evidence. Instead of answering "Yes, we do that," you answer: "Yes, refer to Control Priv-04; here is the evidence of our last review."
GDPR Controls List Templates
What a Good Template Includes
A usable control template is more than just a list of rules. It acts as a database for your compliance program.
- Control ID: Unique identifier (e.g., GDPR-ACC-01).
- Description: The action required.
- Owner: The specific role responsible (e.g., VP of Engineering).
- Frequency: How often it runs (Daily, Weekly, Quarterly).
- Evidence Location: Where the proof lives (e.g., "Jira Project X," "AWS Config").
- Last Tested: Date of last verification.
Sample GDPR Controls List Template
Using Templates Across Teams
Compliance is a team sport.
- Engineering: Focuses on automation (backups, encryption, logging).
- Legal: Focuses on contracts (DPAs, Terms, Privacy Policy).
- HR: Focuses on people (training, background checks).
- Sales: Focuses on accuracy (answering customer questions honestly).
How Templates Speed Up Compliance Work
At Konfirmity, we often see companies spending 550–600 hours a year trying to manage compliance manually. They chase engineers for screenshots, dig through emails for contracts, and panic before audits.
By implementing a rigorous controls list and maintaining it via a managed service, that effort drops to approximately 75 hours per year for the internal team.
Why?
- Faster Audits: Auditors do not need to hunt for information. You hand them the list and the mapped evidence folder.
- Cleaner Internal Reviews: You spot gaps before the customer does.
- Reduced Back-and-Forth: When a prospect asks, "Do you have a breach notification policy?" you don't draft one from scratch; you export Control RISK-02 and its evidence.
Common Mistakes Companies Make
- Paper Compliance: Writing a policy but failing to implement the technical control. If your policy says "passwords expire every 90 days" but your Active Directory is set to "Never Expire," you will fail the audit.
- Copy-Pasting Checklists: Downloading a generic GDPR Controls List from the internet without adapting it. If the list mentions "CCTV monitoring" and you are a fully remote SaaS company, you look incompetent.
- Weak Ownership: Assigning controls to "IT Dept" instead of a specific person. If everyone is responsible, no one is responsible.
- Missing Evidence: Doing the work but failing to record it. If you patched the server but didn't log the ticket, in the eyes of an auditor, it never happened.
Conclusion
A strong GDPR Controls List is more than a compliance requirement; it is a revenue asset. In the current market (2025–2026), enterprise buyers are risk-averse. With the average cost of a data breach hitting $4.88 million in 2024, they are under immense pressure to secure their supply chains.
When you present a mature, well-documented control set, you signal that you are a safe partner. You move from the "high-risk" pile to the "fast-track" pile.
However, building this is not a one-time project. It requires ongoing operation. Controls drift. Configurations change. New vendors are added. This is why Konfirmity operates as a human-led managed service. We don't just give you the software and wish you luck; we act as your operational compliance arm, ensuring your controls list remains green year-round.
Start with security. Build controls that actually protect data. The compliance certification—and the enterprise deals—will naturally follow.
FAQs
1) What are GDPR controls?
GDPR controls are the specific operational, technical, and physical measures an organization implements to comply with the GDPR. Examples include encrypting hard drives (technical), signing data processing agreements (legal), and training staff (organizational).
2) Which controls apply to processors vs controllers?
Controllers need strict controls for consent collection, lawful basis determination, and transparency (privacy notices). Processors need heavy controls on data security, instruction adherence, and sub-processor management. Both need strong security and record-keeping controls.
3) How often should controls be reviewed?
High-risk controls (like access reviews and vulnerability scans) should be continuous or monthly. Policy-level controls (like reviewing the privacy policy) should happen at least annually.
4) What documentation is required for audits?
Enterprise auditors typically ask for your Information Security Policy, Incident Response Plan, Record of Processing Activities (ROPA), evidence of staff training, Pen Test reports, and a completed GDPR Controls List or similar questionnaire (like SIG or CAIQ).
5) How do templates speed up compliance work?
Templates provide a pre-structured roadmap. Instead of interpreting the law from scratch ("What does Article 32 mean for my database?"), a good template translates the legal requirement into a technical task ("Enable encryption at rest"). This saves hundreds of hours of research and legal consultation.





.svg)






.svg)
.svg)