Most enterprise buyers now request assurance artefacts before procurement. Without operational security and continuous evidence, deals stall—even when teams think they’re “ready” on paper. The GDPR Encryption Requirements framework often sits at the heart of these conversations. For anyone selling into health care or B2B markets, understanding when and how to encrypt personal data is critical. This article draws on two decades of delivery work, more than 6,000 audits and firsthand knowledge from Konfirmity’s security experts to explain what the law says, why encryption matters for enterprise clients and how to implement cryptographic measures that stand up to auditors and buyers.
The goal of this guide is to help technical leaders, security officers and procurement teams understand the operational demands behind compliance with GDPR Encryption Requirements. We explain the legal foundations, outline a risk‑based approach, link encryption to other frameworks like SOC 2, ISO 27001 and HIPAA, and give practical steps for implementing and maintaining strong cryptography. Along the way, we reference authoritative sources—including the text of the GDPR, ICO guidance from 2025, NIST publications and recent cost‑of‑breach research—to ground our guidance in evidence. By the end, you will know when encryption is necessary, how to select suitable algorithms, how to manage keys, and how to avoid pitfalls that could derail deals or invite regulatory fines.
What the GDPR Says About Encryption
Legal foundations
The GDPR’s core security provision is Article 32. It requires controllers and processors to implement measures “appropriate to the risk,” taking into account “the state of the art, the costs of implementation and the nature, scope, context and purposes of the processing”. The Article lists pseudonymisation and encryption as examples of such measures. Recital 83 reinforces this, recommending that personal data be processed in a way that ensures confidentiality and calls out encryption as a way to mitigate risks. Article 34 then links encryption to breach notification: if a breach occurs but encrypted data remains unintelligible to unauthorized parties, controllers may not need to notify individuals.
This framework makes clear that GDPR Encryption Requirements are not prescriptive. Regulators do not demand that every byte of personal data be encrypted, but they expect organisations to adopt encryption when it is an effective and proportionate way to reduce risk. The UK Information Commissioner’s Office (ICO) updated its encryption guidance in November 2025, advising that although encryption is not mandatory, it should be widely used because it is now affordable and available. The guidance outlines non‑negotiable obligations: organisations must put in place appropriate technical and organisational measures, consider state‑of‑the‑art encryption at the design stage, avoid outdated protocols like SSL, and use transport‑layer encryption such as TLS.
Risk‑based nature of the GDPR
The GDPR requires organisations to make risk‑based decisions about encryption. Article 32 asks controllers to weigh the state of the art, implementation cost and processing context. Recital 83 notes that encryption should be applied to prevent risks to data subjects. The ICO’s 2025 guidance echoes this, urging organisations to assess the necessity of encryption during system design and throughout the data lifecycle. In practice, this means security leaders must evaluate threats to confidentiality, integrity and availability, consider potential harm to individuals and choose cryptographic measures proportionate to those risks.
When deciding whether to encrypt, factors include:
- State of the art: Use modern protocols and avoid insecure or deprecated algorithms. The ICO advises against SSL and requires TLS for data in transit. NIST’s guidelines on Advanced Encryption Standard (AES) specify 128‑, 192‑ or 256‑bit keys, and NIST warns that keys providing less than 112 bits of security should not be used.
- Nature and scope of processing: Sensitive data (health records, financial data, biometric identifiers) typically justifies stronger encryption. Cross‑border transfers or multi‑tenant cloud environments may warrant end‑to‑end encryption or hardware security modules.
- Cost of implementation: Encryption is inexpensive relative to the cost of breaches. IBM’s 2025 Cost of a Data Breach report found that global breach costs averaged $4.44 million and that U.S. breach costs exceeded $10 million. The report also noted that 97% of AI‑related breaches occurred where proper access controls were absent. Investing in encryption reduces both the likelihood and the impact of such breaches.
- Impact on data subject rights: Encryption must not impede individuals’ ability to access, rectify or delete their data. Key management practices should allow timely decryption when necessary while preventing unauthorised access.
Why Encryption Matters for Enterprise Clients
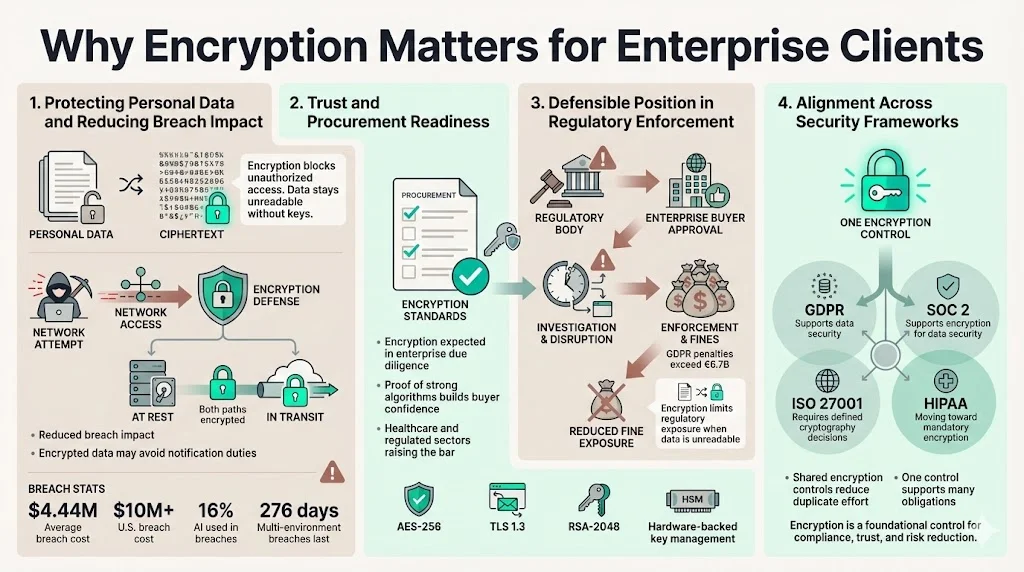
Protecting personal data and reducing breach impact
Enterprise clients process large volumes of personal data across complex systems. Encryption secures that data by converting it into ciphertext that is readable only with the appropriate key. This prevents unauthorized access even if an attacker breaches the network. By encrypting data both in transit and at rest, organisations reduce the chance of exposure and make breaches less damaging. Article 34 recognises this; encrypted data rendered unintelligible does not trigger breach notification obligations.
Statistics reinforce the stakes. IBM’s 2025 report found that the global average cost of a data breach decreased to $4.44 million and that U.S. breaches cost more than $10 million. The same study discovered that 16% of breaches involved attackers using AI and that 97% of AI‑related breaches happened in organisations lacking proper access controls. Breaches involving multi‑environment systems cost $5.05 million and lasted 276 days. These figures show why encryption and associated controls (like access management) are critical to reducing both the likelihood and cost of breaches.
Building trust and addressing procurement requirements
Enterprise buyers now routinely ask for data protection assurances during procurement. Our team at Konfirmity has helped hundreds of companies answer security questionnaires, negotiate data‑processing agreements and navigate Data Protection Impact Assessments (DPIAs). When an organisation can demonstrate that personal data is encrypted using industry‑standard algorithms with robust key management, buyers gain confidence that their data will be safe. In regulated industries such as health care, encryption is quickly moving from recommended to required. The HIPAA Journal reports that proposed 2026 updates to the HIPAA Security Rule include encryption of all electronic protected health information (ePHI) at rest and in transit. Censinet’s 2025 overview notes that AES‑256, TLS 1.3 and RSA‑2048 (minimum) are the expected algorithms and that hardware security modules should be used for key management.
Defensible measure in regulatory enforcement
Regulators increasingly impose fines for inadequate security. As of late 2025, cumulative GDPR penalties exceeded €6.7 billion across more than 2,600 enforcement actions. Fines peaked at €3 billion in 2023 and remained substantial in 2024. Investigations disrupt operations, trigger expensive remediation and can delay product launches. Demonstrating that personal data is encrypted, keys are managed responsibly and breaches would render data unintelligible provides a defensible position when regulators come calling.
Integration with SOC 2, ISO 27001 and other frameworks
Encryption is not just a GDPR topic. SOC 2’s Trust Services Criteria do not explicitly mandate encryption, but guidance on data security (CC6) recommends encryption at rest, in transit and end‑to‑end, using algorithms such as AES or RSA and ensuring key strengths of at least 112 bits. ISO 27001:2022’s control 8.24 requires organisations to decide when and why cryptography is needed, specify algorithms and key sizes, implement key management and apply controls consistently. HIPAA’s proposed security rule would make encryption of ePHI mandatory. Aligning with GDPR Encryption Requirements therefore supports compliance across frameworks, reducing redundant work and accelerating sales.
Core Concepts: Encryption and Cryptographic Measures
Basic definitions
Encryption transforms readable data (plaintext) into unreadable data (ciphertext) using cryptographic keys. Only those with the correct key can return the ciphertext to its original state. Hashing, by contrast, applies a one‑way mathematical function to data to produce a fixed‑length “digest” that cannot be reversed. Hashes are used to verify authenticity and integrity; the Okta security team notes that hashes prove stored data hasn’t been altered rather than concealing the data itself. Pseudonymisation replaces direct identifiers with pseudonyms and keeps the additional information separate; it reduces risk but the data remains personal. Pseudonymisation is useful when you need to link records without revealing identity, but it does not substitute encryption when confidentiality is a concern.
Types of encryption
- Encryption in transit: Protects data moving between systems (e.g., between a client browser and a web server). The ICO warns that SSL is deprecated and should not be used; transport‑layer security (TLS) should be implemented instead. TLS 1.2 and 1.3 are considered state of the art.
- Encryption at rest: Protects stored data (databases, backups, file systems). AES is the industry standard. NIST’s FIPS 197 defines AES as a symmetric block cipher with 128‑bit blocks and keys of 128, 192 or 256 bits. Post‑quantum considerations suggest using longer keys (192 or 256 bits) for data that must remain confidential for decades.
- End‑to‑end encryption: Encrypts data from sender to recipient without exposing plaintext to intermediaries. This is important for messaging services, remote support tools and highly sensitive business workflows. It is not explicitly required under GDPR Encryption Requirements, but it demonstrates a strong commitment to confidentiality and can be a competitive advantage during sales.
Cryptography methods
- Symmetric encryption uses the same key to encrypt and decrypt. AES is the most common example; it is fast and efficient for large data volumes.
- Asymmetric encryption uses a public key for encryption and a private key for decryption. Algorithms like RSA and Elliptic Curve Cryptography (ECC) support key exchange and digital signatures. SOC 2 guidance recommends RSA with 2,048‑bit keys or higher.
- Post‑quantum cryptography: NIST has begun standardising quantum‑resistant algorithms to address future threats. While this is not yet part of the GDPR’s state‑of‑the‑art assessment, organisations with long retention requirements should monitor these developments.
Aligning with state‑of‑the‑art standards
Regulators expect encryption to reflect current best practice. ISO 27001 control 8.24 asks organisations to define algorithms, key sizes and protocols, and to implement policies for key management and cryptographic controls. The ICO instructs organisations to consider the state of the art and cost of implementation. NIST cautions that keys providing less than 112 bits of security should not be used. These points suggest that enterprises should deploy AES‑256 for data at rest, TLS 1.2/1.3 for data in transit and RSA‑2048 or stronger for key exchanges.
Step‑by‑Step Implementation Guide
Konfirmity’s team has implemented encryption programmes across cloud, on‑premises and hybrid environments. We understand that simply buying encryption tools isn’t enough. Evidence must be collected, controls must be observed over time and designs must fit within existing systems. Here is a seven‑step guide based on our delivery work and aligned with GDPR Encryption Requirements.
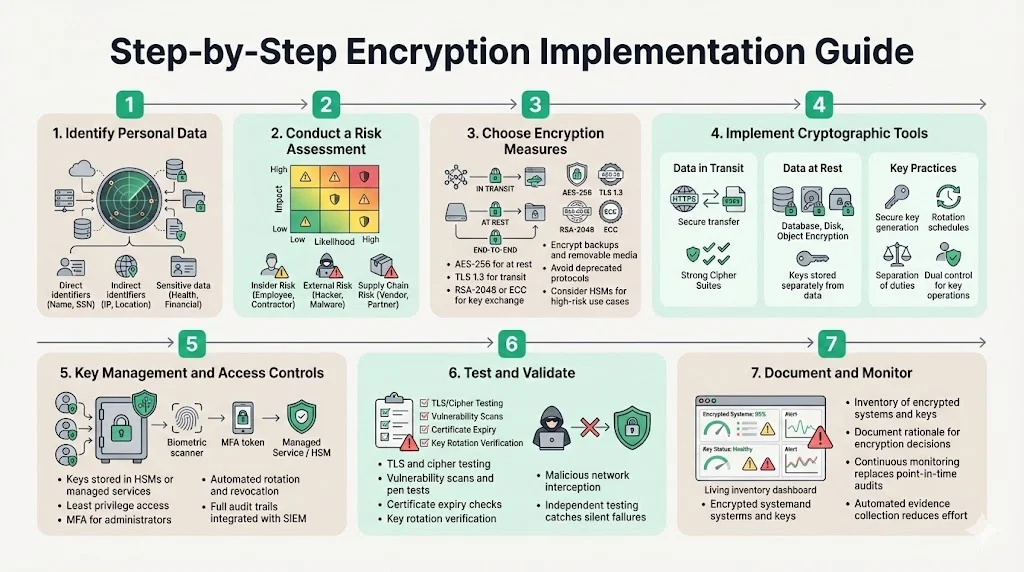
Step 1 — Identify personal data
Begin by inventorying systems and classifying data that qualifies as personal data under the GDPR. This includes obvious identifiers (names, email addresses), indirect identifiers (IP addresses) and sensitive data (health information, biometrics). Use data discovery tools to scan databases, file stores and pipelines. Define data categories and label them within repositories and metadata. Classification is essential because only by knowing where personal data resides can you decide where encryption is needed.
Step 2 — Conduct a risk assessment
Map the threats to confidentiality, integrity and availability. Consider insider threats, external attackers, supply chain risks and potential impact on data subjects. Use frameworks like ISO 27005 for risk analysis or incorporate NIST’s risk management approach. For each processing activity, evaluate whether encryption would materially reduce risk. Remember to weigh state‑of‑the‑art technology, cost and potential harm. For example, storing pseudonymous analytics data may not require full encryption if risk is low, whereas storing health records in the cloud should trigger strong encryption and key management.
Step 3 — Choose appropriate encryption measures
Decide where encryption is necessary (in transit, at rest, end‑to‑end). Align with industry standards: AES‑256 for at‑rest data, TLS 1.3 for transit, RSA‑2048 or ECC for key exchange. Ensure encryption of backup media and removable drives. Avoid deprecated protocols; the ICO warns against SSL. Choose libraries and tools with validated implementations (e.g., NIST‑validated cryptographic modules, FIPS 140‑2/3 compliant modules). For high‑risk processing, consider hardware security modules (HSMs) or cloud key management services.
Step 4 — Implement cryptographic tools
Deploy encryption in your systems:
- Data in transit: Configure HTTPS with modern TLS versions. Use strong cipher suites and disable weak ciphers. Implement secure file transfer protocols (SFTP, FTPS) and secure messaging channels. Document certificate generation and renewal processes to avoid expired or misconfigured certificates.
- Data at rest: Enable database or disk‑level encryption. Use transparent data encryption (TDE) in relational databases and server‑side encryption (SSE) in object stores. When using client‑side encryption, integrate encryption into application logic. Ensure that encryption keys are separate from the data (e.g., store keys in HSMs or key management services).
- Key management practices: Generate keys using cryptographically secure random generators. Define rotation intervals (e.g., rotate master keys every 12 months or sooner if compromise is suspected). Implement separation of duties so that no single individual can both encrypt and decrypt data. Use dual control for key import/export. Document key ownership, creation dates, rotation schedules and destruction policies.
Step 5 — Establish key management and access controls
Key management is often the weakest link. A strong programme should include:
- Secure generation and storage: Use HSMs or cloud‑based key management services that support FIPS 140‑2/3. Never hard‑code keys in source code or embed them in configuration files.
- Access controls: Grant least privilege. Only authorised systems and personnel should access keys, and administrative access should require multi‑factor authentication. Role‑based access control (RBAC) and just‑in‑time access reduce the window of exposure.
- Rotation and revocation: Define rotation schedules and automate the process. Invalidate keys immediately if compromise is suspected. Document how keys are revoked, archived or destroyed.
- Audit trails: Maintain logs of key access and operations. Integrate with your security information and event management (SIEM) tool for continuous monitoring.
Step 6 — Test and validate
Cryptography can fail silently if misconfigured. Run regular vulnerability scans and penetration tests to verify encryption settings. Include certificate validation tests, cipher‑suite scans and attempts to intercept traffic. Perform decryption tests to ensure keys work as expected. Engage independent auditors or penetration testers to uncover issues. Konfirmity’s experience shows that misconfigured TLS certificates and unrotated keys are among the most common findings during audits.
Step 7 — Document and monitor
Documentation is vital for audits and buyer due diligence. Maintain an inventory of encrypted systems, data categories, key storage locations and rotation schedules. Record the rationale for encryption decisions (state of the art, risk evaluation, cost) to demonstrate a risk‑based approach. Monitor encryption status continuously. Set alerts for certificate expiry, failed encryption processes and anomalies in key usage. Integrate monitoring into your continuous compliance platform so that evidence is collected automatically throughout the year. In our managed engagements, continuous monitoring reduces evidence collection effort by up to 75% compared with manual, point‑in‑time audits.
Real Examples and Case Scenarios
Example 1: Encrypting customer records in a CRM platform
An enterprise software provider stores millions of customer records—including contact details and business contracts—in a cloud‑hosted CRM. The data is processed in the EU and transferred to support teams in North America. A DPIA reveals risks from cross‑border transfers and third‑party access. Following GDPR Encryption Requirements, the provider implements AES‑256 encryption at rest using the cloud vendor’s KMS. Customer identifiers are tokenised to decouple identifiers from profiles. Transit encryption is enforced using TLS 1.3, and session management includes mutual TLS between the application and database layer. Keys are stored in a dedicated HSM with rotation every six months. Audit logs record all key operations. As a result, the provider demonstrates to enterprise buyers that data remains confidential, cross‑border transfers are protected and Article 34 breach‑notification obligations are mitigated.
Example 2: Securing data pipelines with TLS
A health‑tech start‑up integrates patient data from wearable devices into its analytics platform. The pipeline includes ingestion services, message queues and analytics workers. Because the data includes ePHI, HIPAA and GDPR obligations apply. The team uses an internal certificate authority to issue TLS certificates for each microservice. Mutual TLS secures communication between services, and certificates are rotated every 90 days. A network policy denies plaintext traffic. Application logs send metadata to a SIEM with alerts on failed handshakes. These controls align with HIPAA’s proposed requirement to encrypt ePHI at rest and in transit and demonstrate compliance with GDPR Encryption Requirements.
Example 3: Using hardware key management services (HSM)
A financial services company processes payment data and personal identifiers. To meet PCI DSS, SOC 2 and GDPR obligations, the company deploys a hardware security module to manage encryption keys. The HSM generates master keys, which are used to encrypt data‑encryption keys (DEKs). These DEKs encrypt records in the company’s databases. Multi‑factor authentication and dual‑control policies restrict access to the HSM. Keys are rotated and destroyed according to documented schedules. By using an HSM, the company reduces the risk of key compromise, demonstrates alignment with ISO 27001 control 8.24 and meets the GDPR Encryption Requirements for appropriate technical measures.
Best Practices for Enterprise Implementation
Integrate encryption with broader security controls
Encryption is powerful but not sufficient on its own. Pair it with layered defences: access management, multi‑factor authentication, network segmentation, intrusion detection, vulnerability management and continuous monitoring. HIPAA’s proposed security rule emphasises a suite of controls—including encryption, multi‑factor authentication and network segmentation—to prevent lateral movement. SOC 2 guidance also highlights the need for broader cyber hygiene alongside encryption. These controls work together to prevent, detect and respond to breaches.
Update and migrate regularly
Cryptographic standards evolve. Avoid outdated protocols like SSL or RC4; follow the ICO’s advice to use TLS and keep up with NIST recommendations. Monitor deprecation schedules and plan migrations—such as moving to TLS 1.3 or adopting post‑quantum algorithms when relevant. An encryption scheme that is adequate today may be insufficient in five years; periodic reviews ensure your controls remain state of the art.
Educate internal teams
Encryption failures often result from human error. Educate developers, system administrators and product managers on how and when to use encryption, what constitutes a secure cipher suite and how to handle keys. Provide guidelines on secure coding, secrets management and incident response. Include encryption topics in onboarding and annual training. Make sure teams understand that encryption is not a universal fix; they must still implement proper access controls, logging and monitoring.
Embed encryption into privacy by design
Article 25 of the GDPR requires data protection by design and by default. When designing new services or features, include encryption decisions at the outset. Align with the ICO’s guidance to consider encryption at the design phase. This means selecting encrypted storage options, designing APIs that use HTTPS, and planning how keys will be generated and rotated. Integrating encryption early reduces technical debt and eliminates retrofitting later.
Leverage managed services for better outcomes
Our experience shows that fully implementing encryption across an enterprise is labour‑intensive. Self‑managed programmes often take nine to twelve months and consume 550–600 internal hours. With Konfirmity’s human‑led managed service, typical SOC 2 readiness—including encryption and related controls—takes four to five months, with about 75 hours per year of client effort. We handle control mapping, evidence collection, key rotation and compliance documentation, allowing your team to focus on product development. This approach aligns with GDPR Encryption Requirements and other frameworks, speeds up sales cycles and reduces the risk of audit findings.
Common Pitfalls to Avoid
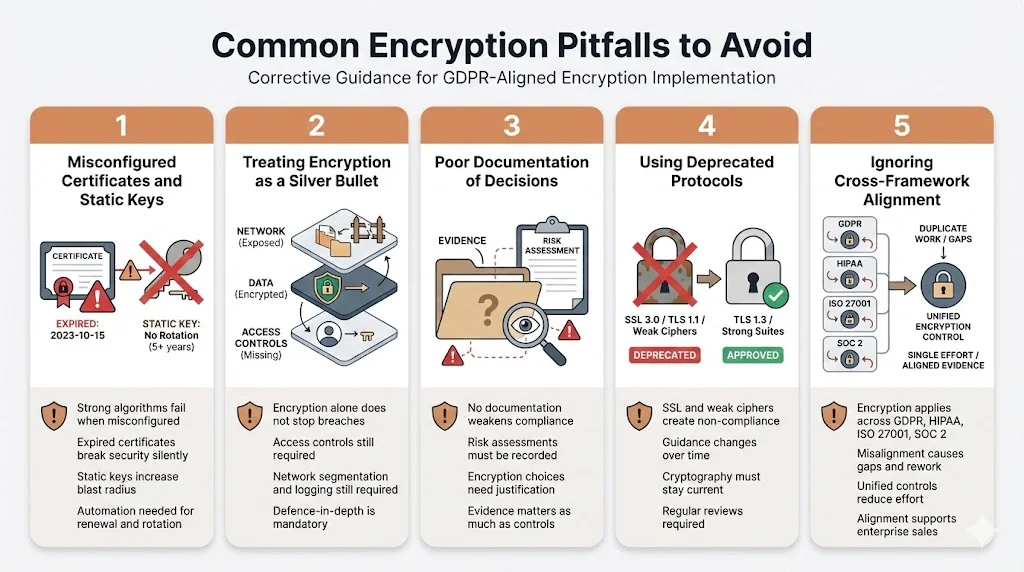
- Misconfiguring certificates or skipping key rotation: Even strong algorithms fail if certificates are misconfigured or keys remain static. Use automation to renew certificates and rotate keys regularly. Monitor for expired certificates and misconfigured cipher suites.
- Believing encryption alone is sufficient: Encryption should be part of a defence‑in‑depth strategy. Without access controls, network segmentation and logging, attackers can still exfiltrate data or ransom encrypted datasets. Combine encryption with other technical and organisational measures outlined in ISO 27001, SOC 2 and HIPAA.
- Failing to document decisions: Regulators and auditors expect evidence of risk assessments, encryption policies and key management processes. Lack of documentation undermines your compliance posture. Keep clear records of data classification, risk analyses and the rationale behind cryptographic choices.
- Using deprecated protocols: The ICO warns that using SSL may result in non‑compliance. Keep up to date with cryptographic guidance and avoid outdated algorithms.
- Ignoring cross‑framework alignment: Encryption controls often intersect with multiple frameworks (GDPR, HIPAA, ISO 27001, SOC 2). Treat encryption as a unifying control that can satisfy several requirements. Failure to align with one standard can lead to duplication of effort or gaps that hinder sales.
Conclusion
Encryption is a cornerstone of modern data protection and an essential element of GDPR Encryption Requirements. The GDPR takes a risk‑based approach, naming encryption as an appropriate technical measure and recognising that encrypted data may not trigger breach‑notification obligations. Regulators expect organisations to consider state‑of‑the‑art algorithms, costs and the nature of processing. Recent enforcement trends show that fines and operational disruptions are real; cumulative GDPR penalties exceed €6.7 billion by late 2025, and U.S. data breach costs top $10 million. Meanwhile, HIPAA is moving toward mandatory encryption for all ePHI. Enterprises that implement strong cryptography, integrate it with wider controls and document their decisions will be well positioned for audits, procurement and cross‑framework compliance.
Konfirmity’s approach is to start with security and arrive at compliance. We build encryption into the stack, manage keys, monitor controls and collect evidence year‑round. This human‑led managed service delivers durable security that satisfies regulators, auditors and buyers. Security that looks good in documents but fails under incident pressure is a liability. Build your programme once, operate it daily and let compliance follow.
FAQ
1. Does the GDPR make encryption mandatory?
No. The GDPR does not mandate encryption in every case. Article 32 lists pseudonymisation and encryption as examples of appropriate technical measures but stresses that measures must be proportionate to the risk. Recital 83 recommends using encryption to mitigate risks. Regulators expect organisations to consider encryption wherever unauthorised access could harm individuals.
2. When should my organisation encrypt personal data?
Encrypt data whenever the risk assessment identifies the potential for unauthorised access or significant harm to individuals. High‑risk processing—such as storing health, financial or biometric data, transferring data across borders or using third‑party processors—typically warrants encryption. Use AES‑256 for data at rest and TLS for data in transit, as recommended by NIST and the ICO. HIPAA’s proposed rule would require encryption of all ePHI at rest and in transit.
3. Does encryption reduce GDPR breach notification requirements?
Yes. Article 34 states that when personal data is rendered unintelligible through encryption, controllers may not need to notify affected individuals. However, this applies only if the encryption is strong and the keys remain secure. Always consult with legal counsel before deciding not to notify.
4. What encryption standards should we follow?
Use modern, widely accepted algorithms. NIST’s FIPS 197 defines AES with 128‑, 192‑ and 256‑bit keys. SOC 2 guidance recommends RSA‑2048 or stronger and AES‑128 or higher. The ICO advises using TLS over SSL. NIST warns against keys providing less than 112 bits of security. For health data, HIPAA updates specify AES‑256 for data at rest and TLS 1.3 for data in transit.
5. How do we manage encryption keys securely?
Establish strict key‑lifecycle policies: generate keys in secure hardware or trusted services, store them separately from data, rotate them regularly and revoke them promptly if compromise is suspected. Use role‑based access control, multi‑factor authentication and audit logging for all key operations. Document key management procedures for auditors and regulators. ISO 27001 control 8.24 emphasises defining key sizes, implementing policies and ensuring keys are managed systematically.





.svg)





.svg)
.svg)