In the high-stakes environment of healthcare data, an audit is not a paperwork exercise—it is a stress test of your operational reality. Most enterprise buyers and auditors now demand proof of security before procurement signatures ever land. If your security posture exists only in policy documents but fails in your server settings, you are effectively uninsured against the threats of 2025 and 2026.
With the average cost of a healthcare data breach in the U.S. hitting a record $10.22 million in 2025, the financial stakes have never been higher. One of the most frequent failures we see across the 6,000+ audits we have supported is configuration drift. Systems start secure but degrade over time as patches are missed, ports are opened for testing and never closed, or default settings are left unchanged on new deployments.
This is where HIPAA Secure Configuration Baselines become critical. They are not merely a compliance checkbox; they are the technical bedrock that protects electronic protected health information (ePHI). Without a defined, enforced, and monitored baseline, your organization is managing risk by guesswork rather than by design.
At Konfirmity, we operate as a human-led managed service. We do not just advise you on what settings to change; we implement controls inside your stack. We know that durable security—the kind that survives an OCR investigation or a rigorous SOC 2 Type II audit—requires consistent configuration management, not just a one-time setup.
What Are Secure Configuration Baselines?
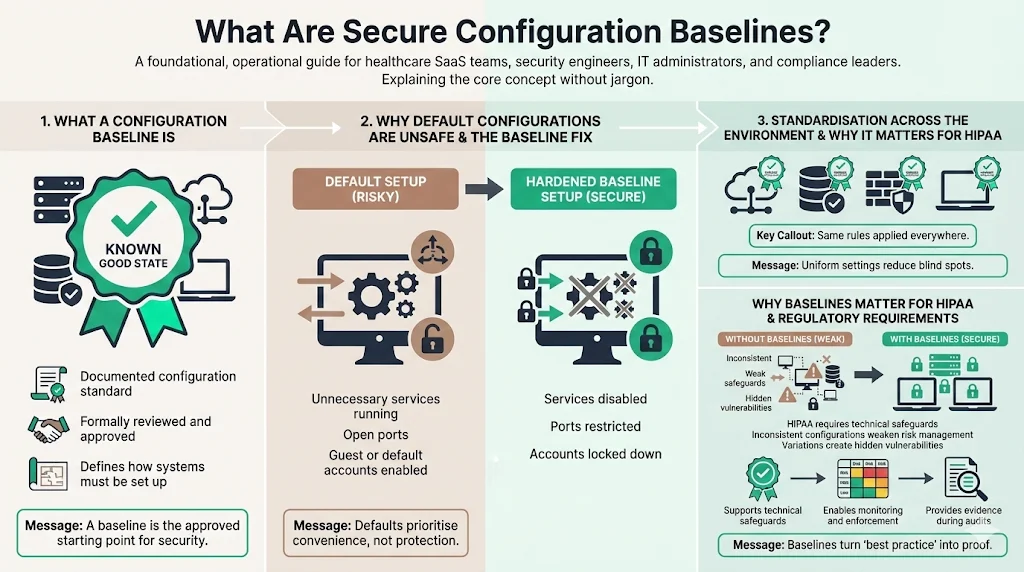
In simple terms, a configuration baseline is a documented set of specifications for a system, or configuration items within a system, that has been formally reviewed and agreed on. It represents the "known good" state of your infrastructure.
When you deploy a new server, a cloud instance, or a firewall, the default settings are rarely secure. Vendors design default configurations for usability and compatibility, often leaving unnecessary services running, ports open, and guest accounts active. A secure configuration baseline dictates exactly how that device must be set up before it touches ePHI.
This standardizes security settings across your entire fleet. Whether you are spinning up an AWS EC2 instance or provisioning a laptop for a clinician, the baseline ensures uniformity.
In the context of HIPAA Secure Configuration Baselines, this concept moves from "best practice" to regulatory necessity. The HIPAA Security Rule requires covered entities and business associates to implement technical safeguards. If every server in your network has a different security configuration, you cannot reasonably claim to have implemented effective risk management. You have created a fragmented environment where vulnerabilities hide in the inconsistencies.
Why Baselines Matter for HIPAA Compliance
Compliance is often viewed as a burden, but in reality, it is a byproduct of good security. If you focus on building a resilient system, compliance naturally follows.
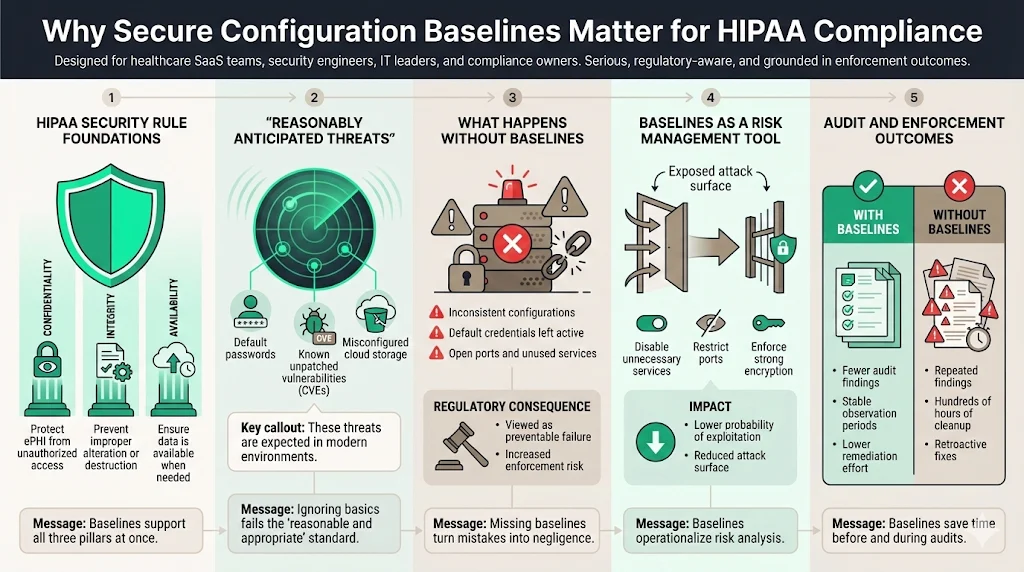
HIPAA Security Rule Foundations
The core mandate of the HIPAA Security Rule is to ensure the confidentiality, integrity, and availability (CIA) of ePHI.
- Confidentiality: Only authorized personnel can view data.
- Integrity: Data is not altered or destroyed in an unauthorized manner.
- Availability: Data is accessible when needed.
Standard 45 CFR § 164.306(a) requires you to ensure compliance by your workforce and protect against reasonably anticipated threats. "Reasonably anticipated" is the operative phrase. In 2026, it is reasonable to anticipate that attackers will scan for default passwords, unpatched known vulnerabilities (CVEs), and misconfigured S3 buckets.
Without HIPAA Secure Configuration Baselines, you fail the "reasonable and appropriate" test. If a breach occurs because a server retained a default password—a violation of a basic baseline—the Office for Civil Rights (OCR) will likely view this as willful neglect. In fact, the OCR's recent Risk Analysis Initiative has already resulted in multiple settlements in 2025 specifically targeting the failure to conduct thorough risk assessments.
Risk Management and Vulnerability Control
HIPAA is unique because it is non-prescriptive regarding specific technologies but highly prescriptive regarding risk analysis (45 CFR § 164.308(a)(1)(ii)(A)). You must conduct an accurate and thorough assessment of potential risks.
Baselines are your primary tool for vulnerability control. By reducing the attack surface—turning off unused services, blocking unneeded ports, and enforcing strong encryption suites—you statistically lower the probability of a successful attack. This is crucial given that the Verizon DBIR reported a 180% increase in attacks exploiting vulnerabilities over the previous year.
In our work helping clients achieve readiness for SOC 2 and HIPAA, we see a direct correlation: organizations with strict baselines have significantly fewer findings during the observation period. Those without baselines spend hundreds of hours retroactively fixing issues that should never have existed.
Key Components of a Secure Configuration Baseline
A baseline is not a generic list; it is a technical specification tailored to your operating systems and software. However, effective HIPAA Secure Configuration Baselines share several non-negotiable components.
1) System Hardening
Hardening is the process of securing a system by reducing its surface of vulnerability.
- Servers: Disabling the root user for SSH, disabling USB mounts on physical servers, and removing all non-essential software packages.
- Endpoints: Disabling autorun features, enforcing screen locks, and restricting software installation rights.
- Network Devices: Disabling unencrypted management protocols (like Telnet) in favor of SSH v2, and turning off unused interfaces.
For example, a standard hardening baseline for a Windows Server handling ePHI would mandate disabling SMBv1 (a common vector for ransomware) and ensuring only TLS 1.2 or 1.3 is enabled for secure communications.
2) Access Controls
Your baseline must enforce the principle of least privilege.
- Authentication: Mandating Multi-Factor Authentication (MFA) for all remote access and administrative accounts. Credential theft remains the most common entry point for breaches, making this non-negotiable.
- Password Policies: Enforcing complexity, rotation (if applicable under NIST guidelines), and lockout thresholds after failed attempts.
- Account Management: The baseline should require the immediate disablement of default vendor accounts and the removal of guest accounts.
3) Audit Controls
You cannot protect what you do not monitor. HIPAA requires hardware, software, and/or procedural mechanisms that record and examine activity in information systems.
- Logging: Your baseline must configure systems to log specific events: successful and failed logins, file access modification, and privilege elevation.
- Retention: Logs should be shipped to a centralized server or SIEM (Security Information and Event Management) system to prevent tampering. Local logging is insufficient if an attacker wipes the drive.
4) Encryption
While HIPAA technically lists encryption as "addressable," in the modern threat environment, it is effectively mandatory.
- Data at Rest: Baselines should enforce full-disk encryption (e.g., BitLocker, dm-crypt) on all laptops and servers.
- Data in Transit: Web servers must be configured to reject weak ciphers and enforce HTTPS with valid certificates.
5) Patch and Vulnerability Management
A baseline is not static. It must dictate the configuration of update agents.
- Automation: Systems should be configured to check for critical security updates automatically.
- Scanning: The baseline includes the installation and configuration of agents that allow for regular vulnerability scanning.
6) Cloud and Hybrid Environments
The cloud is not secure by default. AWS, Azure, and Google Cloud follow a "Shared Responsibility Model." They secure the cloud; you secure what is in the cloud. Recent data shows that breaches involving data stored in public clouds incurred the highest average cost at $5.17 million.
- Storage: Public access to S3 buckets (or equivalent) must be blocked by policy.
- IAM: Root access keys should be deleted, and IAM roles used instead of hard-coded credentials.
- Databases: RDS instances should not be publicly accessible via the internet.
How to Develop and Implement Baselines
Developing HIPAA Secure Configuration Baselines is a rigorous process. It requires technical expertise and a deep understanding of your specific risks.
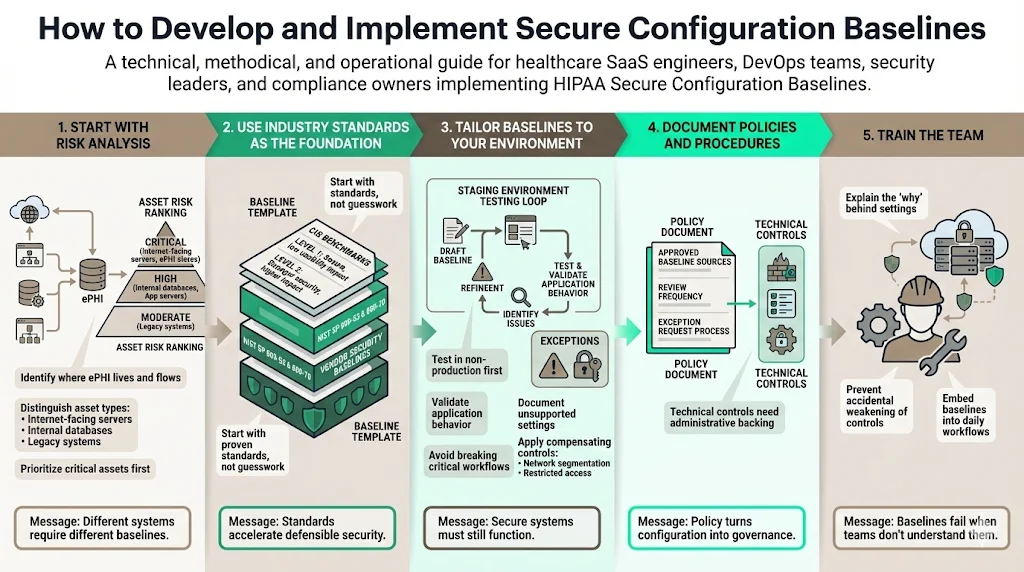
1) Start With Risk Analysis
Do not apply settings blindly. Conduct a risk analysis to understand where ePHI lives and flows. A database server behind a firewall requires a different baseline than a web server exposed to the public internet. Identify your critical assets and prioritize their baselines.
2) Use Industry Standards for Baselines
You do not need to invent these settings from scratch. Authoritative bodies publish detailed benchmarks that serve as excellent starting points.
- CIS Benchmarks (Center for Internet Security): The gold standard. They offer Level 1 (good security, low impact on usability) and Level 2 (high security, potential impact) profiles.
- NIST SP 800-53 and SP 800-70: The National Institute of Standards and Technology provides federal-grade guidance on configuration checklists.
- Vendor Guidelines: Microsoft, Red Hat, and cloud providers publish their own security baselines.
At Konfirmity, we often start with CIS Benchmarks and map them to specific HIPAA requirements for our clients, creating a custom but standardized profile.
3) Tailor to Your Environment
This is where the "human-led" aspect of our service is vital. If you apply a "Level 2" CIS benchmark blindly to a legacy healthcare application, you might break the application.
- Testing: Apply the baseline in a staging environment first.
- Exceptions: Document any setting you cannot apply due to business needs. If an old MRI machine requires an outdated protocol, document the exception and implement compensating controls (like network segmentation).
4) Document Policies and Procedures
Technical settings must be backed by administrative policy. Write a "Configuration Management Policy" that dictates:
- Which baselines are used.
- How often they are reviewed.
- The process for requesting exceptions.
5) Train the Team
Your DevOps engineers and IT administrators must understand why these settings exist. If an engineer disables a firewall rule to "troubleshoot" and forgets to re-enable it, the baseline is broken. Training ensures that secure configuration is part of the daily workflow, not an obstacle to it.
Monitoring, Auditing, and Continuous Review
A baseline is a snapshot in time. The moment a system goes live, entropy sets in. This is called "drift." An admin changes a setting to fix a bug, a new software update alters a config file, or a shadow IT deployment bypasses standard provisioning.
To maintain HIPAA Secure Configuration Baselines, you must move from "set and forget" to "continuous monitoring."
- Automated Audits: Use tools that compare current settings against your gold image daily.
- Change Management: Every change to a production configuration must go through a formal approval process.
- Quarterly Reviews: Re-evaluate your baselines against new threats. If a new encryption protocol becomes the standard (e.g., the shift from TLS 1.1 to 1.2), your baseline must update.
This is the difference between "compliance manufacturing"—scrambling for two weeks before an audit—and true security. Konfirmity stays engaged year-round, monitoring these controls so that when the auditor asks for evidence, it is ready immediately.
Common Challenges and How to Overcome Them
Implementing strict baselines in healthcare is rarely simple.
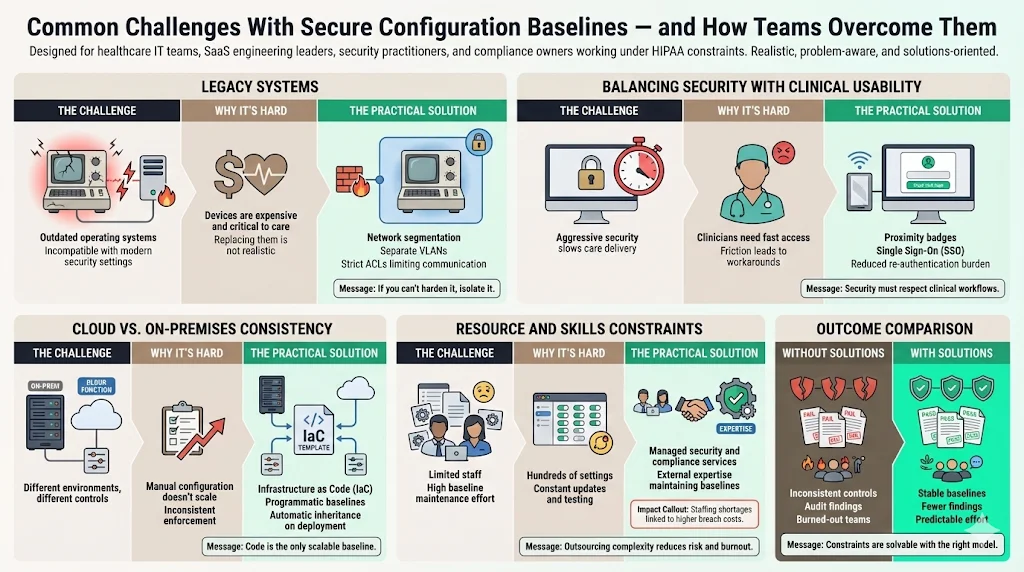
Legacy Systems: Hospitals and clinics often run expensive medical devices on outdated operating systems (e.g., Windows 7 or even XP) that cannot support modern baselines.
- Solution: Network segmentation. Isolate these devices on a separate VLAN with strict ACLs (Access Control Lists) so they cannot communicate with the rest of the network or the internet.
Balancing Usability: Clinicians prioritize patient care speed. Aggressive screen lockouts or complex MFA can impede their work.
- Solution: Use proximity badges for authentication or Single Sign-On (SSO) to reduce friction while maintaining security.
Cloud vs. On-Premises Consistency: Applying the same logic to a physical server and a serverless function is difficult.
- Solution: Treat infrastructure as code (IaC). Use Terraform or Ansible to define baselines programmatically. This ensures that every time a resource is deployed, it inherits the correct configuration automatically.
Resource Constraints: Small IT teams lack the bandwidth to research, test, and maintain hundreds of configuration settings. This skills gap is costly; organizations with severe security staffing shortages faced $1.76 million higher breach costs in 2024.
- Solution: This is the core use case for a managed service. Instead of burning 550–600 hours a year managing this internally, partners like Konfirmity can handle the heavy lifting, reducing your internal effort to around 75 hours per year.
Tools and Resources to Support Baseline Management
While tools alone do not solve the problem, they are essential for scale.
- CIS-CAT Pro: A tool from CIS that scans systems and reports compliance scores against benchmarks.
- Tenable / Nessus: excellent for identifying configuration vulnerabilities alongside patch deficits.
- Cloud Native Tools: AWS Security Hub, Azure Policy, and Google Cloud Security Command Center can enforce and audit configurations in real-time.
- OpenSCAP: An open-source tool for checking configuration compliance on Linux systems.
However, a tool only produces a report. It requires a human expert to interpret that report, prioritize remediation, and fix the root cause without disrupting hospital operations.
Conclusion
Security that looks good in documents but fails under incident pressure is a liability. HIPAA Secure Configuration Baselines are the difference between a resilient infrastructure and a fragile one. They reduce your attack surface, ensure consistency, and provide the concrete evidence auditors require.
For healthcare companies, the cost of delay is high. With the healthcare sector facing an average breach cost of $10.22 million, delaying implementation is a financial risk you cannot afford. By implementing hard, technical baselines, you protect your patients' data and your organization's reputation.
At Konfirmity, we believe in outcomes. We do not sell you a software subscription and wish you luck. We act as your implementation partner, ensuring that your baselines are built, monitored, and maintained year-round. Start with security, and compliance will follow.
FAQ: HIPAA Secure Configuration Baselines
1) What is a secure configuration baseline under HIPAA?
A secure configuration baseline is a defined set of security controls and settings applied to systems (OS, applications, network devices) to ensure they operate securely. Under HIPAA, it plays a critical role in the technical safeguards required to protect ePHI, standardizing hardening measures like disabling unused services and enforcing encryption.
2) Which systems need HIPAA configuration baselines?
All systems that create, receive, maintain, or transmit ePHI require baselines. This includes backend servers, databases, cloud instances (AWS/Azure/GCP), clinician workstations, mobile devices, network firewalls, and medical IoT devices.
3) How often should configuration baselines be reviewed?
Baselines should be reviewed at least annually or whenever there is a significant change in the technology stack (e.g., a major OS upgrade) or the threat environment. Continuous monitoring should occur daily to detect drift from the established baseline.
4) Do configuration baselines apply to cloud infrastructure?
Yes. Cloud resources often present the highest risk due to misconfiguration. HIPAA Secure Configuration Baselines must cover cloud-specific settings such as Identity and Access Management (IAM) policies, storage bucket permissions, and virtual network security groups.




.svg)





.svg)
.svg)