Most enterprise buyers now ask for assurance documents well before procurement. Procurement questionnaires, business‑associate agreements and security addenda are now standard for selling software that processes sensitive data. A Service Organization Control (SOC 2) report is one of the most common assurance artifacts. The SOC 2 framework, managed by the American Institute of Certified Public Accountants (AICPA), evaluates how a service organization designs and operates controls for security, availability, processing integrity, confidentiality and privacy. Without operational security and continuous evidence collection, deals can stall even when engineering teams think they are ready. Understanding the SOC 2 Audit Timeline helps align your security program with the expectations of large customers.
This article examines what a SOC 2 audit involves and how its timeline affects sales cycles. After defining the report types and trust criteria, it walks through each phase: planning and pre‑audit preparation, the audit window, formal audit execution, report drafting and post‑audit activities. It then provides common timeline scenarios, practical tools and tips to stay on track, and answers to frequently asked questions. Throughout, it draws on Konfirmity’s experience delivering 6,000+ audits over more than 25 years and integrates insights from AICPA, AuditBoard, ValueMentor, ISO 27001, HIPAA and GDPR guidance.
What Is a SOC 2 Audit and Why It Matters
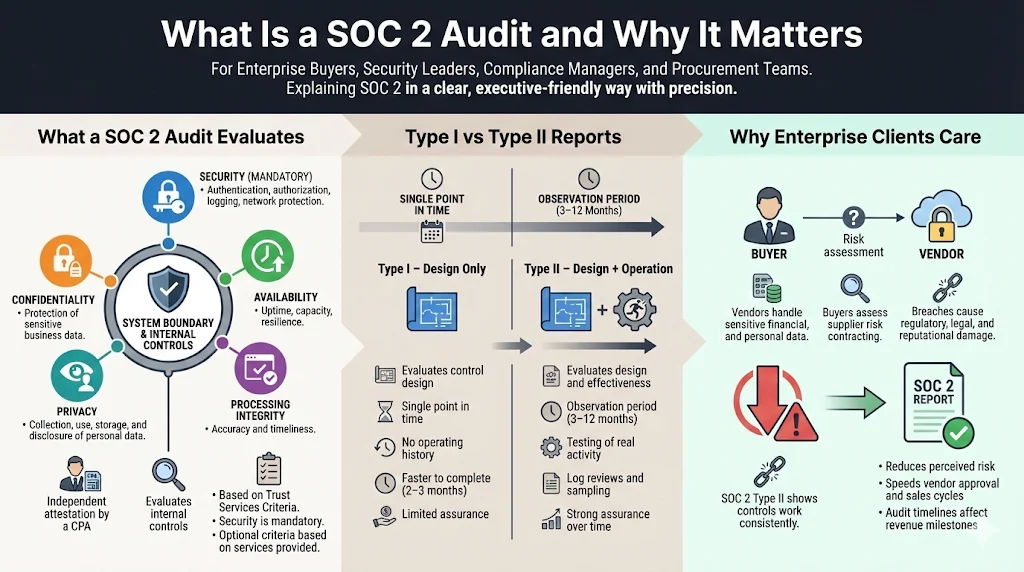
A SOC 2 examination is an attestation report issued by a Certified Public Accountant (CPA) that evaluates controls related to one or more of the Trust Services Criteria: security, availability, processing integrity, confidentiality and privacy. The security principle is mandatory for all SOC 2 examinations, while the other criteria can be selected depending on the services provided. Security controls include authentication, authorization, logging and network defense; availability covers uptime and capacity management; processing integrity focuses on accurate and timely data processing; confidentiality addresses protection of proprietary information; and privacy assesses how personal data is collected, stored and disclosed.
Type I vs. Type II Reports
Understanding the difference between Type I and Type II reports is vital for planning a SOC 2 audit timeline. A Type I report evaluates whether controls are designed effectively at a specific date. The auditor assesses the description of the system and opines on whether the controls were suitably designed as of that single point in time. Because there is no observation period, Type I audits can be completed more quickly—often within two to three months. However, Type I reports provide limited assurance since they do not demonstrate that controls operate consistently.
A Type II report evaluates both the design and operating effectiveness of controls over a period of time, typically three to twelve months. The auditor tests samples of transactions, reviews logs and interviews personnel to ensure controls function as intended throughout the observation period. Enterprise buyers prefer Type II reports because they provide confidence that security and compliance are maintained over time. This preference means sales cycles often hinge on the schedule for obtaining a Type II report.
Why Enterprise Clients Care
Large customers often process sensitive financial, health or personal data through their suppliers’ platforms. Failure to meet security obligations can lead to regulatory fines, reputational damage and contract termination. IBM’s 2025 Cost of a Data Breach report notes that the global average cost of a breach fell slightly to $4.44 million, yet the U.S. average climbed to $10.22 million. The report also found that 97 percent of organizations affected by artificial‑intelligence‑related incidents lacked proper access controls. By demonstrating a rigorous control environment, a SOC 2 Type II report reduces perceived risk and accelerates vendor approval. Aligning the SOC 2 Audit Timeline with procurement milestones therefore has direct revenue implications.
High‑Level SOC 2 Timeline Overview
The journey to a SOC 2 Type II report consists of several discrete phases: pre‑audit preparation, an audit window (for Type II), formal audit execution, report drafting and remediation. Each phase has its own duration and tasks. The total SOC 2 Audit Timeline can range from four months for a Type I report to a full year for a Type II report with a twelve‑month observation period.
Below is a high‑level representation of the phases. The horizontal bar shows typical durations based on Konfirmity’s delivery work. Keep in mind that actual timelines vary depending on scope, control maturity and resource availability.
High‑level SOC 2 audit phases and estimated durations
Phase 1: Planning and Pre‑Audit Preparation
This phase lays the foundation for a successful audit. Upfront work ensures your controls meet the selected criteria and reduces surprises later. Konfirmity’s managed service program compresses this phase to around six weeks by providing templates, automation and dedicated personnel; self‑managed efforts can take three to five months.
Define Audit Scope & Objectives
Defining the scope involves deciding which Trust Services Criteria apply and whether to pursue a Type I or Type II report. Security is mandatory; availability, processing integrity, confidentiality and privacy are optional and should align with customer requirements.
The scope also defines the systems and processes subject to audit, such as the core application, infrastructure and third‑party services. The statement of applicability should reflect the boundaries and justify any exclusions. Selecting a Type II audit requires planning for the observation period. Align your SOC 2 Audit Timeline with sales targets so that the final report arrives before procurement due dates.
Gap Analysis and Readiness Assessment
A readiness assessment identifies differences between current practices and SOC 2 requirements. This involves mapping existing processes to the Trust Services Criteria. For example, evaluate whether you conduct periodic access reviews, implement least‑privilege principles, maintain incident response plans and monitor configuration changes. An internal gap analysis typically takes two to four weeks for small teams and up to two months for complex environments. Konfirmity’s program uses automated control mapping and risk scoring to highlight gaps quickly. The ISO 27001:2022 update reduced controls from 114 to 93 and introduced 11 new ones addressing cloud security and threat intelligence; many of these map directly to SOC 2 controls and can be assessed in parallel.
Remediation Planning & Documentation
Once gaps are identified, develop remediation plans that address technical and administrative controls. HIPAA’s administrative safeguards emphasise risk analysis, workforce training and contingency planning. Documentation must describe each control, the owner, frequency and evidence required. Draft policies and procedures, create a control matrix and assign responsibilities.
Select an audit firm, schedule fieldwork and negotiate the audit window early. Dedicated support and automation compress remediation to about six weeks; self‑managed programs often take longer, so start preparation well ahead of sales deadlines.
Phase 2: Audit Window (Type II Only)
A Type II report requires an observation period—also called the audit window—during which controls must operate consistently. This phase does not apply to Type I reports.
What Is the Audit Window?
The audit window is the timeframe over which the auditor evaluates operational effectiveness. Typical windows are three, six, nine or twelve months. A shorter window such as three months allows organizations to obtain a Type II report sooner but yields fewer data points. A twelve‑month window demonstrates long‑term maturity but postpones report issuance. The choice should balance internal readiness, sales pressures and client expectations. According to ValueMentor’s guidance, observation periods usually range from three to twelve months, with Type I reports completed in two to three months.
Collecting Evidence During the Window
Continuous evidence collection is crucial. Collect access logs, change records, security alerts, vulnerability scans and vendor risk assessments. Automation platforms like SIEM, cloud‑posture management and workflow automation reduce manual effort. Evidence should demonstrate that controls operated throughout the window rather than only near the end. Store evidence centrally and review it periodically with your auditor.
Choosing the Right Interval for Your Business
First‑time SOC 2 audits often opt for a three‑ or six‑month window to accelerate certification. Shorter windows can fit within sales cycles; however, some customers may request at least six months of operational evidence. Longer windows—nine or twelve months—demonstrate mature control environments and may reduce client due‑diligence questions. We advise aligning the audit window with major renewals or fiscal quarters. If a significant system change occurs, consider splitting the audit into two shorter windows to avoid invalidating existing evidence. Ultimately, choose an interval that balances agility with buyer assurance.
Phase 3: Formal Audit Execution
During this phase, the auditor performs fieldwork, tests controls, interviews personnel and requests additional evidence. Timely responses from your team help keep the audit on schedule.
Fieldwork and Control Testing
Auditors validate the system description, review documentation and test controls by sampling transactions and observing procedures. The fieldwork period usually lasts two to four weeks, depending on the scope. It can be conducted remotely or onsite. Provide a single point of contact for communications and keep an open question log to avoid delays.
Evidence Review and Follow‑Up
After testing, auditors analyze the evidence and may request clarifications. Respond promptly and provide additional proof or context to avoid exceptions. Organized evidence repositories and clear communication channels shorten follow‑up cycles.
Phase 4: Report Drafting and Completion
Once fieldwork ends, the auditor prepares a draft report. This document includes the system description, auditor’s tests, results, and an opinion on whether controls were suitably designed (Type I) and operated effectively (Type II). It also lists any exceptions.
Draft Report Review
When you receive the draft report, verify the system description and control narratives, clarify misunderstandings with the auditor and provide corrections promptly. Draft reviews usually take one to two weeks.
Final Report Issuance
After revisions, the auditor issues the final report. Management must sign a representation letter asserting that the controls and system description are accurate and that no material changes occurred during the audit period. Once the final report is delivered, you can share it with customers under non‑disclosure agreements. The drafting and finalization phase generally lasts three to six weeks. Factor this into your overall SOC 2 Audit Timeline when planning sales conversations.
Post‑Audit Activities and Ongoing Compliance
Obtaining a SOC 2 report is not a one‑time milestone; it marks the beginning of continuous compliance and improvement.
Remediation Period
If the audit identifies exceptions, create remediation plans and close them promptly. Keep clients informed of progress and update control documentation accordingly.
Scheduling Next Audit
SOC 2 reports are typically refreshed annually to maintain relevance. Plan your next audit window early, considering fiscal year‑end, product releases and major infrastructure changes. A continuous compliance program with automated evidence collection reduces the time required for future audits and allows you to deliver new reports on schedule. Konfirmity’s managed service reduces internal effort from 550–600 hours per year for self‑managed compliance to roughly 75 hours by handling evidence collection, monitoring and coordination.
Common Timeline Scenarios
Organizations pursue SOC 2 reports for various reasons: urgent enterprise deals, regulatory requirements, or general market credibility. Below are three typical timelines drawn from Konfirmity’s experience.
1. Quick Start (Three‑Month Window) – Preparation takes about six weeks, the observation period runs three months and fieldwork plus reporting add another six weeks, yielding a total of around six months. This accelerated cycle is often used to support urgent deals but may provide limited evidence for discerning buyers.
2. Standard First Report (Six‑Month Window) – Preparation and remediation usually take two to three months, followed by a six‑month observation period. Fieldwork and report drafting add roughly six weeks, putting the overall timeline close to nine or ten months. This schedule balances evidence depth with time to market.
3. Enterprise‑Ready Cycle (Twelve‑Month Window) – Mature companies may commit to a three‑month planning phase followed by a year‑long observation period. Including six weeks for fieldwork and reporting, the cycle spans roughly 15 to 18 months and can align with fiscal years or other frameworks such as ISO 27001, HIPAA or GDPR.
Tools and Tips to Keep Your Timeline on Track
Implementing a SOC 2 program requires coordination across engineering, security, operations, HR and legal teams. The following tools and practices help maintain the timeline:
- Evidence collection platforms – Centralize logs, policies, risk assessments and control artifacts. Use tools that integrate with cloud providers, identity platforms and ticketing systems to pull evidence automatically. Konfirmity’s dashboard aggregates evidence across your stack and surfaces outstanding tasks.
- Documentation templates – Adopt standard templates for policies and procedures, control matrices and risk assessments. Templates derived from AICPA, ISO 27001 and HIPAA guidance accelerate drafting. Include cross‑references to control owners, frequencies and evidence types and training.
- Additional enablers – Use project management systems to assign owners and monitor deadlines. Deploy tools such as SIEMs and identity governance to automate evidence collection. Finally, consider a managed service partner to coordinate audits.
Konfirmity’s clients typically spend about 75 hours of internal effort per year on compliance activities, compared with the 550–600 hours often required for self‑managed programs. This reduction comes from automation, dedicated specialists and streamlined evidence collection.
Cross‑Framework Considerations
Enterprise buyers often request assurance beyond SOC 2. International clients may ask for ISO 27001 certification, healthcare partners must comply with HIPAA, and European customers care about GDPR. These frameworks share common themes—risk assessments, access control, vendor management and incident response. Designing controls that address these overlapping requirements reduces duplication and accelerates multiple audits. Understanding the SOC 2 Audit Timeline within multi‑framework programs will help you coordinate audits and sales pipelines. For example, the 2022 revision of ISO 27001 introduced cloud‑security and threat‑intelligence controls, while the HIPAA Security Rule requires administrative, physical and technical safeguards including risk analysis and access management. GDPR principles emphasise lawfulness, data minimization and accountability. Konfirmity maps control evidence across frameworks so that a single program can satisfy SOC 2, ISO 27001, HIPAA and GDPR requirements simultaneously, streamlining audits and embedding privacy and security into operations.
Conclusion
An effective SOC 2 program combines rigorous control design, continuous evidence collection and pragmatic project management. The SOC 2 Audit Timeline touches every phase of an organization’s operations—from planning and documentation through an observation period to final report issuance and ongoing compliance. For enterprise deals, a well‑timed Type II report can be the difference between winning and losing a contract. Conversely, rushing a report without operational readiness can lead to exceptions, costly remediation and eroded trust. Resilient controls inspire confidence.
Security that reads well but collapses during incidents is a liability. Build the program once, operate it every day and compliance will follow. A human‑led managed service like Konfirmity can help you start with security, achieve compliance and deliver outcomes as a service. Align your SOC 2 Audit Timeline with sales cycles and maintain year‑round vigilance to shorten procurement approvals, reduce breach risk and satisfy demanding buyers.
FAQs
1. How long does a SOC 2 audit take overall?
For a Type I report, preparation and completion can take as little as two to three months, since the auditor evaluates controls at a single point in time. A Type II report requires an observation period; the total timeline ranges from four to five months for a three‑month window to over a year for a twelve‑month window. Factors include scope, control maturity, resource availability and the auditor’s schedule.
2. What’s the difference between the audit window and the audit phase?
The audit window is the period during which your controls operate and evidence is collected for a Type II report (e.g., three or six months). The audit phase is the fieldwork period when the auditor formally evaluates and tests those controls, typically lasting two to four weeks.
3. Can I start a SOC 2 audit before I’m fully ready?
You can begin scoping and readiness assessments early, but auditors will test only controls already in place. Starting too soon may lead to exceptions if policies or evidence are incomplete. Conduct a gap analysis and remediate critical issues before commencing the observation period. A managed service can shorten readiness by providing templates and guidance.
4. How often do I need to re‑audit?
Most companies perform SOC 2 audits annually to meet enterprise expectations and maintain report relevance. Some high‑risk industries conduct semi‑annual or quarterly internal assessments. Plan your next audit early and maintain continuous evidence collection to reduce effort.
5. How do enterprise client requirements affect my timeline?
Clients may require specific Trust Services Criteria (e.g., privacy for healthcare clients under HIPAA) or a minimum observation window (often six months). These requirements dictate the scope and duration of your audit. Engage with sales and legal teams to understand contractual obligations and align your SOC 2 Audit Timeline accordingly.





.svg)





.svg)
.svg)