Most enterprise buyers now ask vendors to provide assurance artifacts before procurement. They review control design, testing outcomes, and evidence of continuous operation, not just policies. Deals stall when teams treat security as paperwork rather than a live program. A SOC 2 attestation helps answer due‑diligence questions, but the way you earn it matters. This SOC 2 Auditor Selection Guide explains how auditor choice affects sales cycles, how different report types and trust criteria influence expectations, and how to avoid missteps. It draws on standards from the AICPA, ISO/IEC, NIST, and HIPAA, industry data from 2024–2025, and patterns from Konfirmity’s experience supporting more than 6,000 audits over the past 25 years. The goal is to help enterprise‑focused teams pick an independent auditor who will validate real security controls and support sales success, not just provide a certificate.
Why SOC 2 matters when selling to enterprise buyers
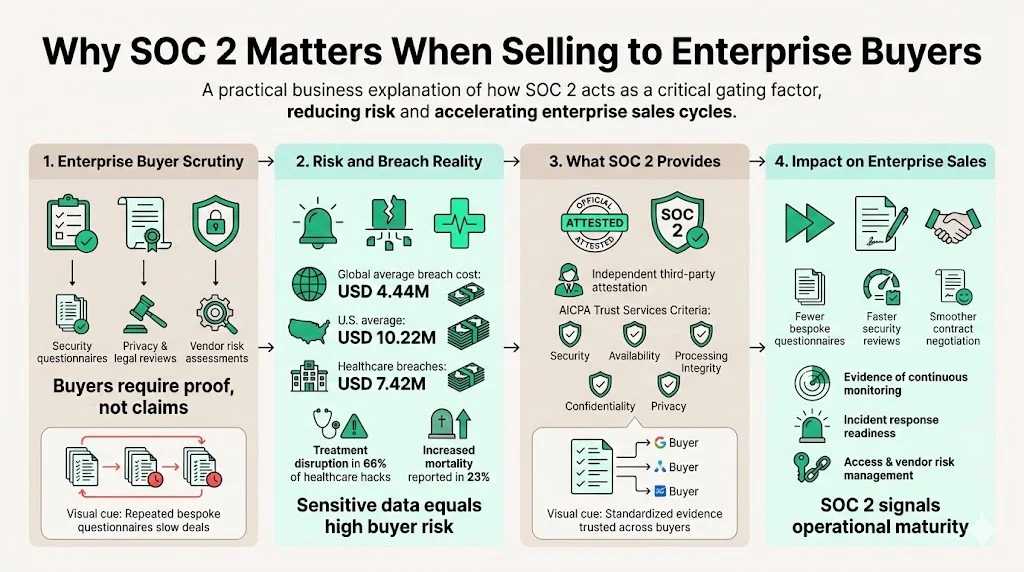
Enterprise procurement teams vet suppliers with legal, privacy and security questionnaires. A SOC 2 report offers a third‑party attestation that your controls meet the AICPA’s trust services criteria – security, availability, processing integrity, confidentiality and privacy. It reduces the number of bespoke questionnaires and speeds up contract negotiation because buyers trust standardized evidence. Recent data shows the global average cost of a data breach was USD 4.44 million in 2025, down from USD 4.88 million in 2024, while the U.S. average rose to USD 10.22 million. Healthcare breaches remain the most expensive at USD 7.42 million. These figures underscore why vendors handling sensitive data must demonstrate strong controls. Hospitals reported treatment disruptions in 66% of hacks and increased mortality in 23% of cases. Enterprise buyers therefore insist on evidence of continuous monitoring, incident response, access management and vendor risk management. A SOC 2 report doesn’t eliminate all due‑diligence work, but a well‑executed report answers many core questions and signals operational maturity.
How auditor choice affects deal cycles, security reviews and buyer trust
A SOC 2 audit is not a commodity. Only licensed CPA firms can sign SOC 2 reports according to the AICPA’s attestation standards (SSAE 21). These CPA firms must follow a code of conduct that requires independence, objectivity and competence, undergo peer review, and maintain systems of quality control. Choosing a reputable auditor signals to enterprise buyers that your attestation is trustworthy. Well‑known auditors run structured evidence requests, communicate clearly and provide robust reports that procurement teams respect. Lesser‑known firms may rush through fieldwork, overlook control failures or deliver vague findings, raising red flags for buyers. Poorly executed audits can lengthen deal cycles as buyers ask for supplemental evidence or insist on more trusted attestations. Conversely, engaging a respected auditor who understands your industry can reduce follow‑on questions and accelerate procurement.
What SOC 2 auditors actually do
The role of an independent auditor
A SOC 2 auditor is an independent CPA firm that evaluates the design and operating effectiveness of a service organization’s controls. The auditor issues a report under the AICPA’s attestation standards. They cannot design or operate the controls they audit; independence is mandatory. Their role is to request evidence, test controls and issue an opinion on whether the controls meet the applicable trust services criteria over the relevant period.
How auditors evaluate security controls against audit standards
Auditors use the AICPA trust services criteria to test controls. For example, the Security (common criteria) category requires protections against unauthorized access and disclosure. Availability focuses on disaster recovery and capacity planning. Processing integrity assesses whether system processing is complete, valid, accurate and timely. Confidentiality examines how organizations protect sensitive information, and Privacy focuses on how personal information is collected, used and disclosed. Auditors test controls by sampling evidence, performing walkthroughs and interviewing control owners. For Type I reports they test design at a point in time; for Type II they evaluate operating effectiveness over a period.
Difference between advisory support and audit execution
Many vendors offer readiness assessments or advisory services to prepare you for a SOC 2 audit. These services help design and implement controls, draft policies and conduct mock audits. However, they are separate from the formal attestation, which must be performed by an independent CPA firm. The AICPA prohibits auditors from auditing controls they helped implement because independence would be compromised. Teams should engage advisors to close gaps but retain a separate firm for the formal audit.
Why enterprises care who your auditor is
Enterprise buyers rely on SOC 2 reports to evaluate risk. They are more likely to trust reports signed by firms with strong reputations. Big 4 or large regional firms have rigorous methodologies, secure evidence portals and clear narratives; their reports reduce procurement friction. Reports from lesser‑known firms may still be valid but often trigger follow‑up questions about sampling, scope or independence. Buyers may also check that your auditor has experience in your industry and understands cloud architectures. Choosing an auditor who speaks your buyers’ language can improve trust and shorten security reviews.
Understanding SOC 2 basics before selecting an auditor
SOC 2 Type I vs Type II
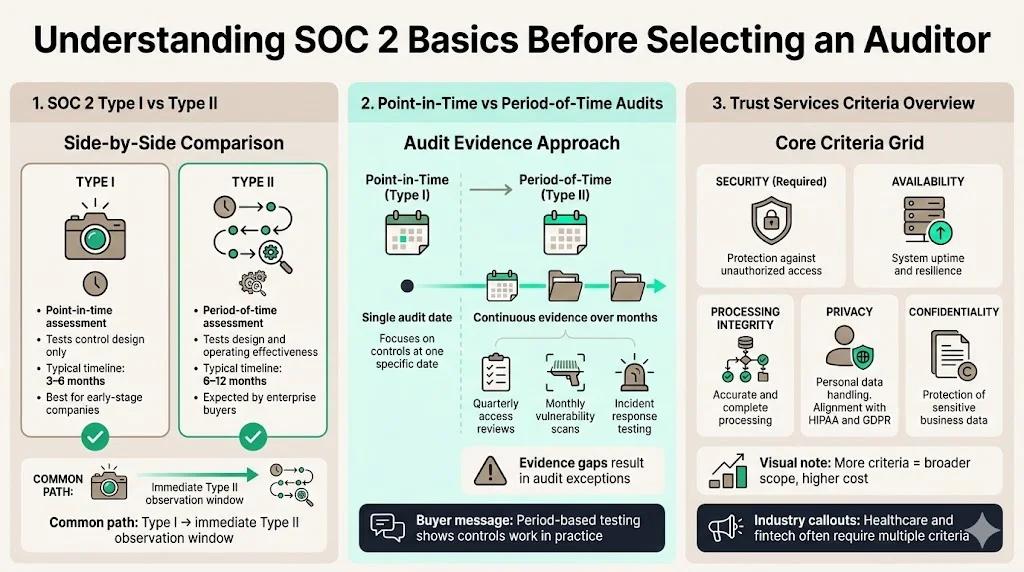
A Type I report evaluates the design of controls at a single point in time. It is faster to achieve (3–6 months) and can be useful for startups showing early commitment to security. A Type II report evaluates both design and operating effectiveness over a period – typically three to twelve months. It provides greater assurance but takes longer (6–12 months). Enterprises usually expect Type II because it demonstrates that controls work in practice. Many teams start with Type I to validate design, then immediately begin the observation window for Type II.
Point‑in‑time vs period‑of‑time audits
Because a Type I is a snapshot, auditors only test whether controls are designed appropriately as of the audit date. In a Type II, auditors test how controls operated throughout the chosen period. This requires consistent evidence – such as quarterly access reviews, monthly vulnerability scans or incident response exercises – to show that controls functioned over time. If evidence gaps arise, auditors record exceptions. Buyers view Type II as more reliable because it demonstrates operational discipline.
Trust services criteria overview
Every SOC 2 report includes the Security criteria, also known as the common criteria. Organizations may add any combination of the other four criteria depending on their services and customer expectations. Availability assesses whether systems are resilient and available to meet business objectives. Processing integrity looks at accuracy and completeness of processing. Confidentiality examines how sensitive information is protected throughout its lifecycle. Privacy focuses on personal data handling and overlaps with frameworks like HIPAA and GDPR. Including more criteria expands the audit scope and cost but may be necessary for industries such as healthcare and fintech.
How audit scope impacts auditor selection
Systems, products and regions included
The audit scope defines which products, systems and regions are covered by the report. A scope that includes multiple data centers, regions or product lines increases evidence requirements. Some organizations choose to carve out third‑party sub‑service organizations; others include them. Defining scope early helps you select an auditor with experience in similar environments – for example, SaaS platforms, fintech services, or healthcare providers. If you operate in multiple jurisdictions, consider whether you need to address privacy laws like the GDPR’s cross‑border transfer rules or HIPAA’s safeguards for electronic protected health information. Choosing an auditor familiar with these regulations reduces the risk of gaps.
How scope affects cost, timeline and audit depth
Expanding scope increases the number of controls tested and the amount of evidence collected. A narrow scope may shorten the observation period and reduce fees, but it could limit your ability to use the report with enterprise buyers. For example, including both application and infrastructure layers may cost more but provide deeper assurance. DSALTA’s 2025 data shows readiness assessments typically cost USD 5,000–15,000 and Type I audits USD 10,000–30,000. Type II audits range from USD 25,000–70,000+. Secureframe’s breakdown indicates total costs (including readiness, risk assessment, penetration testing, audit and annual maintenance) can reach USD 80,000–350,000. Adding more criteria or systems moves you toward the higher end. Align your scope with customer demands and budget.
Why auditor selection is a business decision, not just a compliance task
How auditor reputation affects vendor assessment reviews
Procurement teams evaluate vendor risk based on more than the presence of a SOC 2 report. They consider the auditor’s reputation, the clarity of the system description, and the number of exceptions. A report from a Big 4 firm may carry more weight than one from a little‑known local firm. However, large firms can be costlier and slower. Mid‑sized firms with deep SaaS experience may provide a better balance of rigor and efficiency. If your customers are primarily Fortune 500 enterprises or regulated entities, choose an auditor they recognize.
Impact on procurement, security questionnaires and deal velocity
An auditor who understands enterprise expectations will proactively gather evidence that maps to common procurement questionnaires. They will produce a report that addresses concerns about access controls, encryption, vendor risk and incident response. This reduces the number of follow‑up questions from security and legal teams. For example, Konfirmity’s managed service approach typically reduces in‑house effort from 550–600 hours per year to about 75 hours, accelerating sales cycles and freeing engineers to focus on product development. Teams using experienced auditors report shorter negotiation cycles because the report addresses buyer concerns upfront.
Common enterprise red flags tied to weak audit firms
Buyers may request additional attestation if they perceive the auditor as inexperienced or biased. Red flags include audits completed in weeks with little fieldwork; reports with vague control descriptions; and a lack of industry experience. Some automation vendors offer “two‑week SOC 2” promises – these often produce superficial reports that buyers distrust. Real audits involve months of evidence collection and testing. Choose firms that reject unrealistic timelines and insist on thorough observation periods. Buyers also look for independence; the auditor should not be the same organization that sold you a compliance tool or implemented your controls.
Internal alignment between security, legal and sales teams
Selecting an auditor is a cross‑functional decision. Security teams assess technical expertise; legal teams examine engagement contracts and confidentiality; sales teams care about report usability and timing. Aligning these groups prevents last‑minute surprises. For example, sales may need the report by a contract renewal date; legal may require non‑disclosure terms; and security may need extra time for remediation. Start alignment early to avoid conflicting priorities.
Step‑by‑step SOC 2 auditor selection guide
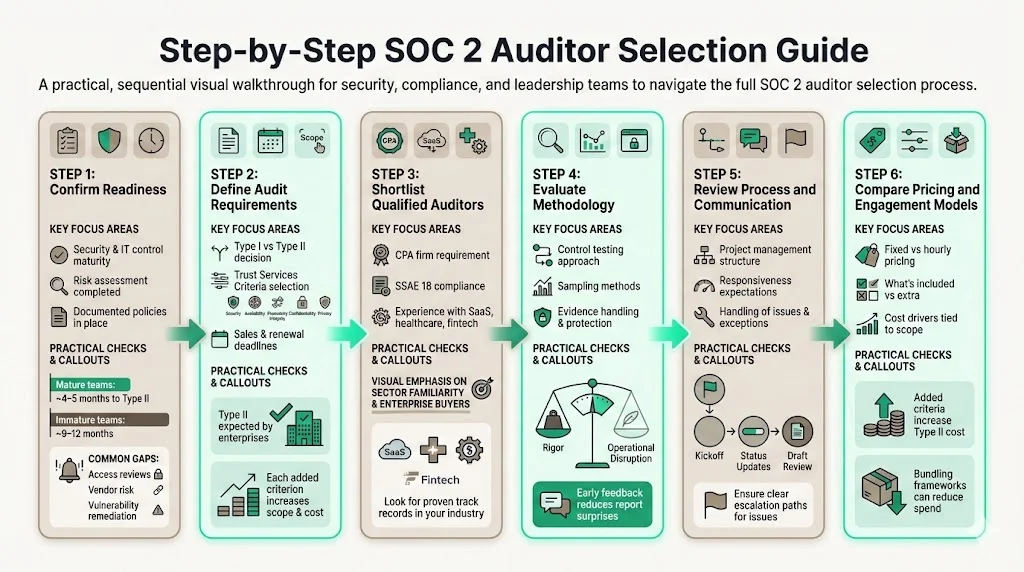
Step 1: Confirm your readiness level
Internal security and IT controls maturity: Assess whether your organization has basic security controls in place. This includes access management, change management, incident response, vulnerability management and vendor risk management. For HIPAA‑covered entities, ensure administrative, technical and physical safeguards meet the Security Rule’s requirements. Perform a risk assessment (often using frameworks like NIST SP 800‑30) and document findings. Konfirmity’s audits show that teams with mature controls need about 4–5 months to reach Type II readiness, while immature teams may need 9–12 months.
Existing policies and documentation: Evaluate whether you have documented policies for information security, privacy, acceptable use, access reviews, change management and incident response. For ISO 27001 alignment, the ISMS must be documented and audited regularly. In healthcare, HIPAA requires documented administrative safeguards, including risk analysis and assigned security responsibility. Without documented policies, auditors will not have evidence of control design.
Gaps that may affect audit outcomes: Identify gaps through a readiness assessment. Common issues include missing access reviews, inconsistent vendor due‑diligence, or lack of vulnerability remediation procedures. Some teams rely on manual processes that cannot produce evidence across a three‑month observation window. Fix these gaps before selecting an auditor, or select an auditor who offers pre‑audit advisory services (separate from the formal audit).
Step 2: Define your audit requirements
Type I or Type II: Determine which report type customers expect. Most enterprises expect Type II, but startups may start with Type I. If you choose Type I, plan to begin the Type II observation period immediately after the report is issued to avoid losing momentum. This reduces the total timeline.
Required trust services criteria: Decide which criteria beyond security are relevant. For example, SaaS vendors may include availability to address uptime commitments; payment processors may include processing integrity; healthcare vendors should include confidentiality and privacy. Including privacy helps demonstrate compliance with HIPAA and GDPR. Each additional criterion increases evidence requirements and cost.
Reporting deadlines tied to sales or renewals: Align the audit timeline with key contract milestones. A renewal audit takes 6–8 months. Work backwards from sales cycles to ensure reports are ready when needed. If deals are pending, communicate realistic dates to the sales team and avoid promising early completion.
Step 3: Shortlist qualified SOC 2 auditors
CPA firm requirements: Only CPA firms can sign SOC 2 reports. Confirm that the firm is licensed and undergoes peer review. Ask whether they have experience with AICPA attestation standards and whether they adhere to SSAE 18 (which supersedes SSAE 16).
Experience with companies selling to enterprises: Look for auditors who work with organizations similar in size and sector. Audit firms with SaaS and cloud expertise understand microservice architectures, DevOps pipelines and CI/CD evidence, making them more efficient. For healthcare, ensure the auditor understands HIPAA safeguards and Business Associate Agreements (BAAs). For fintech, confirm familiarity with PCI DSS and payment processing environments.
Industry and SaaS familiarity: Ask about previous clients in your vertical. An auditor experienced with multi‑tenant SaaS platforms will know how to test tenant isolation and encryption at rest. An auditor used to healthcare will know how to evaluate audit logs for electronic protected health information (ePHI) and verify that Business Associate Agreements are in place.
Step 4: Evaluate auditor experience and methodology
How they test security controls: Ask how the auditor plans to test each control category. For example, will they perform sample‑based testing of access logs? Will they review change management tickets for evidence of approvals? A rigorous methodology uses sampling appropriate for the population size and considers risk.
Approach to sampling and evidence: Understand their evidence collection process. Do they use secure portals? Will they accept screenshots? Ask how they protect sensitive data submitted during the audit. Clarify how many samples they require and whether they will test both design and operating effectiveness for each control.
Balance between rigor and efficiency: A good auditor strikes a balance between thorough testing and minimizing disruption. Some auditors unnecessarily ask for evidence outside the scope; others accept limited evidence and risk missing issues. Ask how they handle requests that may not be relevant to your scope and whether they provide preliminary feedback to avoid surprises in the final report.
Step 5: Review audit process and communication style
Project management approach: Understand the auditor’s timeline, milestone meetings and tools. Will there be a kickoff call, weekly status updates and a pre‑report review? Clear project management reduces last‑minute panic.
Responsiveness during the audit timeline: Ask how quickly auditors respond to questions and evidence submissions. A responsive team helps you stay on track. Delays in communication often cause observation periods to extend beyond planned timelines.
How issues and exceptions are handled: Auditors should provide early warnings when they identify control failures so you can remediate during the observation period. Ask whether they allow remediation of minor issues before finalizing the report and how they document exceptions.
Step 6: Compare pricing and engagement models
Fixed vs variable pricing: Some firms offer fixed fees based on scope; others charge hourly rates. Fixed fees provide predictability but may include contingencies. Hourly models can balloon if the scope increases or if evidence is missing. Ask for details on what is included in the fee: readiness assessments, gap analysis, report writing, and follow‑up calls.
What is included vs billed separately: Clarify whether readiness assessments, remediation support, and subsequent letters (e.g., SOC 3 for marketing purposes) are separate services. Some firms include a gap analysis and readiness assessment; others bill these separately. Understand whether you can bundle multiple frameworks (e.g., ISO 27001, HIPAA, PCI DSS) to reuse evidence and reduce cost.
Cost drivers tied to scope and complexity: Ask how adding more trust services criteria or systems impacts fees. For example, DSALTA reports that each additional criteria or complex environment increases Type II costs. Secureframe’s data shows penetration tests, risk assessments and annual maintenance can push costs toward six figures. Choose a scope that meets buyer expectations without overextending resources.
Key criteria to use when comparing SOC 2 auditors
Questions to ask before hiring a SOC 2 auditor
- How many SOC 2 audits do you run each year? Large volumes indicate a refined methodology and experience across industries.
- What industries do you work with most? Ensure alignment with your sector – SaaS, healthcare, fintech or manufacturing.
- How do you handle control failures or gaps? Ask whether they notify you during the observation period, allow remediation and how they document exceptions.
- Who will be assigned to our audit team? Meet the engagement partner and manager; confirm their experience and certifications.
- What support do you provide during remediation? Some auditors offer limited advisory; others remain strictly independent. Understand whether they provide a management letter or recommendations separate from the attestation.
Preparing for a smooth SOC 2 audit
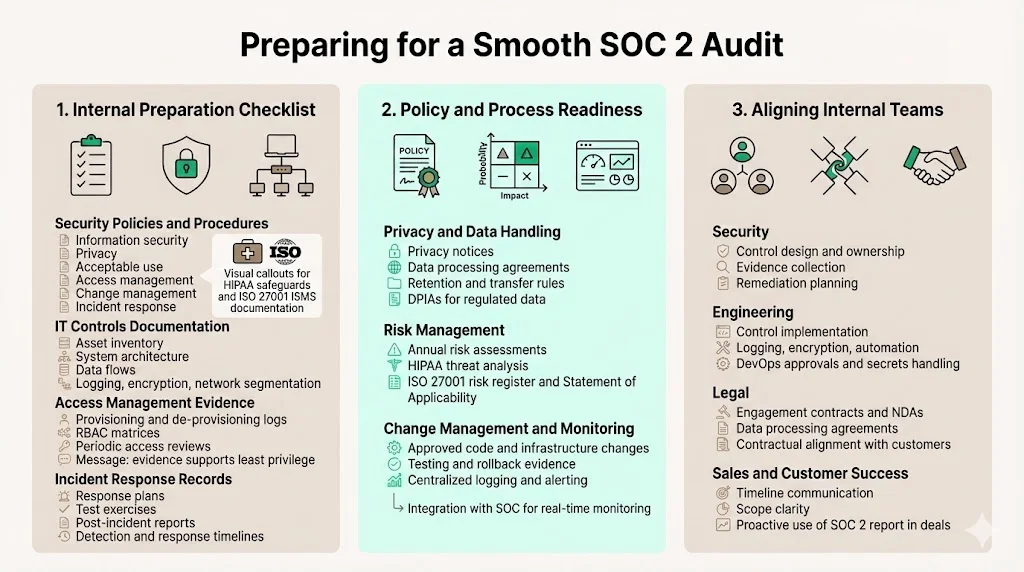
1 – Internal preparation checklist
- Security policies and procedures: Establish information security, privacy, acceptable use, access management, change management and incident response policies. For HIPAA, administrative, technical and physical safeguards are required. For ISO 27001, the ISMS should be documented and reviewed regularly.
- IT controls documentation: Maintain inventories of assets, system architectures and data flows. Document access controls, logging configurations, encryption settings and network segmentation.
- Access management evidence: Keep logs of access provisioning and de‑provisioning, role‑based access control (RBAC) matrices and user access reviews. Auditors will sample these records to verify least privilege.
- Incident response records: Document incident response plans, test exercises, and post‑incident reports. Record detection, response times and lessons learned. This evidence demonstrates control over detection and response processes.
2 – Policy and process readiness
- Privacy policies: Develop clear privacy notices and data processing agreements (DPAs) covering personal data collection, use and retention. For GDPR compliance, include provisions for cross‑border transfers and data protection impact assessments (DPIAs).
- Risk management procedures: Conduct risk assessments at least annually. For HIPAA, carry out “accurate and thorough” assessments of threats to ePHI. For ISO 27001, conduct risk assessments and maintain a Statement of Applicability (SoA) listing applicable controls.
- Change management and monitoring: Implement processes to document code changes, infrastructure modifications and configuration updates. Capture approvals, testing evidence and rollback plans. Ensure monitoring covers application and infrastructure logs and integrates with a Security Operations Center (SOC) for real‑time alerting.
3 – Aligning internal teams
- Security: Lead control design, policy development and evidence collection. Allocate time for remediation and readiness assessments.
- Engineering: Support implementation of security controls, such as encryption, logging, and infrastructure automation. Provide access to system data and help create evidence. Ensure DevOps pipelines capture approvals and that secrets management follows best practices.
- Legal: Review audit engagement contracts, NDAs, and data processing agreements. Ensure the engagement does not create conflicts with other obligations and that the final report meets contractual requirements with customers.
- Sales and customer success: Communicate timelines and scope to customers. Use the SOC 2 report proactively in sales conversations. Manage expectations about when the report will be available and what it covers.
Common mistakes companies make when choosing an auditor
- Picking based on price alone: Lowest‑cost providers may lack independence, experience or robust methodologies. Price should be balanced against the auditor’s reputation, industry expertise and report quality.
- Underestimating audit scope: Teams often include too many products or regions without understanding the evidence requirements. Overly broad scope increases cost and delays. Conversely, too narrow scope may make the report unusable for customers.
- Choosing firms without enterprise credibility: Reports from unknown auditors may lead to follow‑up questions and slow deals. Select firms recognized by your customer base.
- Failing to plan for future Type II audits: Starting with Type I is fine, but you should have a roadmap for Type II. Waiting too long between Type I and the Type II observation window results in duplicated work.
SOC 2 audit timeline and what to expect
Typical phases from kickoff to final audit report
- Preparation and gap remediation (2–3 months): Define scope, map controls, implement policies and remediate gaps identified in a readiness assessment.
- Observation period (Type II only, 3–12 months): Collect evidence over the chosen period. The longer the period, the stronger the assurance but the longer the timeline.
- Fieldwork and testing (2–8 weeks): The auditor requests evidence, conducts walkthroughs and performs sampling. For Type I this may take 2–5 weeks; for Type II, 4–8 weeks.
- Reporting and QA (2–3 weeks): The auditor prepares the draft report, management reviews it, and the final report is issued.
- Renewal audits (6–8 months): For annual renewals, the process is shorter because controls and policies are already in place.
Time ranges for Type I and Type II
Scrut’s 2025 guidance suggests Type I audits take 3–6 months total, including preparation and fieldwork. DSALTA reports a preparation phase of 4–8 weeks, Type I fieldwork 2–4 weeks, and Type II audits 3–12 months depending on the observation period. These ranges assume you have basic controls in place; organizations with immature controls may require longer readiness phases.
Where delays usually happen
Delays typically occur when evidence is incomplete or scattered. For example, missing access reviews or change management records can pause testing. Additionally, stakeholder availability may slow walkthroughs. Clarify responsibilities early and maintain a central repository for evidence. Automation tools can pull evidence continuously, reducing manual work and preventing stale data.
How auditor efficiency affects outcomes
Experienced auditors use secure portals and automated evidence collection, reducing back‑and‑forth emails. They provide clear testing plans and early feedback, which helps you remediate quickly. Inefficient auditors may ask for redundant evidence or mismanage sampling, extending fieldwork and causing frustration. During selection, ask about their tools and processes.
Cost considerations for SOC 2 audits
Typical cost ranges by company size
Secureframe’s 2025 cost breakdown lists readiness assessments around USD 15,000, risk assessments USD 10,000–20,000, penetration tests USD 15,000, compliance preparation USD 25,000–85,000, formal audits USD 5,000–150,000 and annual maintenance USD 10,000–60,000. The total can range from USD 80,000 to USD 350,000 depending on scope. DSALTA reports more conservative averages: USD 5,000–15,000 for readiness, USD 10,000–30,000 for Type I, and USD 25,000–70,000+ for Type II.
How scope and criteria affect pricing
Costs increase with each additional trust services criterion and the number of systems audited. Including availability may require testing disaster recovery plans; including confidentiality requires encryption and data retention evidence; adding privacy introduces policies around consent and data subject rights. Multi‑regional scopes involve multiple data centers and local regulations. Each factor drives more sampling and documentation, increasing auditor hours and internal preparation time.
Ongoing costs for annual renewals
SOC 2 reports are valid for 12 months. Renewal audits involve new observation periods and fieldwork but are typically faster and cheaper because controls are established. Budget for annual updates to policies, training and evidence collection. For ISO 27001, surveillance audits occur annually and recertification every three years. For HIPAA, ongoing risk assessments and incident response exercises add to operational costs.
Budgeting tips for growing teams
- Allocate funds for readiness and gap remediation early. Investing in control implementation reduces auditor findings and repeat costs.
- Use automation platforms that collect evidence continuously and map controls across frameworks (SOC 2, ISO 27001, HIPAA) to reduce duplicate efforts.
- Negotiate multi‑year engagements with auditors to secure better rates and ensure continuity.
- Consider bundling SOC 2 with other attestations (e.g., ISO 27001 or HIPAA) to maximize reuse of evidence and achieve economies of scale.
Conclusion
A strong SOC 2 program is more than a checkbox. It shows buyers that security and privacy are ingrained in your operations. Choosing the right auditor is crucial because their independence, experience and methodology directly influence the quality of your report and the trust buyers place in it. Following a structured SOC 2 Auditor Selection Guide helps teams avoid missteps, align stakeholders, and focus on operational security. Konfirmity’s human‑led, managed security and compliance model delivers outcomes as a service: we build controls inside your stack, collect evidence continuously and keep you audit‑ready year‑round. Rather than chasing paper, invest in controls that withstand auditor scrutiny, satisfy buyers and protect your customers. Security that looks good in documents but fails under incident pressure is a liability; build the program once, operate it daily and let compliance follow.
FAQs
1) How do you verify an auditor’s credentials?
Auditors must be licensed CPA firms and follow AICPA attestation standards. Verify licensing, peer review status and SOC 2 audit history. Ask for sample reports and client references. Independent CPA status ensures adherence to SSAE 21 requirements.
2) What questions should you ask before hiring a SOC 2 auditor?
Inquire about the number of SOC 2 audits conducted annually, industries served, how they handle control failures, who will lead your engagement and what remediation support they provide. Clarify their testing methodology, sampling approach and evidence portal.
3) How long does a SOC 2 audit take?
Type I audits typically take 3–6 months, including preparation. Type II audits take 6–12 months because of the observation period. The exact duration depends on readiness, scope and the chosen observation window.
4) What is the cost range for SOC 2 audits?
Recent data indicates total costs can range from USD 80,000–350,000, including readiness assessments, risk assessments, penetration testing, formal audits and annual maintenance. Type I audits typically cost USD 10,000–30,000, while Type II audits range from USD 25,000–70,000+. Costs depend on scope, trust services criteria and company size.
5) Can you switch auditors between SOC 2 Type I and Type II?
Yes. Some organizations engage one firm for Type I and another for Type II, especially if they outgrow the initial firm’s capabilities. Switching may be sensible if your customers expect a more recognizable auditor or if the first firm lacked depth. Ensure a thorough handoff: provide the new auditor with the prior report, control descriptions and remediation steps to avoid rework. Because independence is critical, never engage a firm that designed your controls to perform the attestation.





.svg)





.svg)
.svg)