A GDPR Incident Response Plan outlines how an organisation detects, analyses, contains, reports and remediates incidents involving personal data. GDPR applies whenever there is accidental or unlawful destruction, loss, alteration or unauthorised disclosure of personal data. Enterprise clients expect proof that vendors can protect high‑volume and sensitive datasets. The plan operationalises GDPR’s principles—lawfulness, fairness, transparency, data minimisation, accuracy, storage limitation, integrity, confidentiality and accountability. Controllers must maintain system availability and resilience, report breaches that pose risks to individuals within 72 hours and sometimes notify those individuals. Failing to do so can lead to fines of up to €20 million or 4 % of global annual turnover. The sections below summarise what the regulation says, define essential concepts and provide a practical framework.
What GDPR Says About Incident Response
Article 33 requires controllers to notify the supervisory authority of a personal data breach without undue delay and, where feasible, within 72 hours of becoming aware. If they miss the deadline, they must justify the delay. Notifications must describe the nature of the breach (including categories and approximate numbers of affected data subjects and records), provide contact details for the data protection officer, outline likely consequences and list measures taken or proposed. Processors must inform controllers promptly. Controllers must also keep a record of facts, effects and remedial actions for each breach.
Communication to individuals
Article 34 states that when a breach is likely to result in a high risk to individuals’ rights, controllers must notify affected data subjects without undue delay. The communication should describe the incident in plain language, mention the same information as provided to authorities and include advice on how individuals can protect themselves. This notification is not required if effective measures (such as encryption) render the data unintelligible, or if subsequent actions ensure the high risk is no longer likely.
Controllers and processors
Controllers determine the purposes and means of processing, while processors act on behalf of controllers. Controllers must report qualifying breaches to authorities and, if necessary, to individuals, whereas processors must notify controllers but are not directly responsible for notifying authorities. Contracts between controllers and processors should specify incident response obligations and timelines.
Definition of a personal data breach
The GDPR defines a personal data breach as any breach of security leading to accidental or unlawful destruction, loss, alteration or unauthorised disclosure or access of personal data. The European Data Protection Board (EDPB) classifies breaches by confidentiality (unauthorised disclosure or access), integrity (unauthorised alteration) and availability (loss or destruction). Examples include a developer accidentally pushing credentials to a public repository, a ransomware attack encrypting databases, a misconfigured cloud bucket exposing customer information or accidental deletion of records. Even temporary loss of access can qualify if it impacts individuals’ rights.
Consequences of non‑compliance
GDPR uses a two‑tier penalty scheme: minor infringements can result in fines up to €10 million or 2 % of global revenue, while serious breaches can lead to penalties up to €20 million or 4 %. By March 2025, regulators had issued more than €5.65 billion in fines across over 2,245 cases. The Irish Data Protection Commission imposed a record €1.2 billion fine against Meta in 2023 for unlawful data transfers. These figures show the importance of compliance.
Common Mistakes and How to Avoid Them
Core Concepts You Need to Understand
1. Data breach
In the GDPR context, a data breach includes any accidental or unlawful destruction, loss, alteration or unauthorised disclosure or access of personal data. The EDPB categorises breaches by confidentiality (unauthorised disclosure or access), integrity (unauthorised alteration) and availability (loss or destruction). Examples relevant to enterprise systems include code repositories exposing secrets, ransomware encrypting backups, compromised third‑party updates and accidental deletion without backup. Recognising these categories helps teams classify incidents quickly and decide whether notification is required.
2. Risk assessment
GDPR is risk‑based. Controllers must evaluate the likelihood and severity of harm to individuals’ rights when designing security measures and deciding whether to notify authorities. Assessments consider the type of data involved (e.g., medical, financial, minors), the number of individuals affected, potential for identity theft or discrimination and system vulnerabilities. The EDPB emphasises that controllers must be able to detect breaches quickly. Risk assessments also underpin Data Protection Impact Assessments (DPIAs) for high‑risk processing.
3. Incident management vs incident response
Incident management spans preparation, detection, analysis, containment, recovery and lessons learned. Incident response describes the actions taken once an incident is detected. NIST SP 800‑61r3 stresses that incident response should be integrated into overall risk management and supported by all functions of the NIST Cybersecurity Framework: Govern, Identify, Protect, Detect, Respond and Recover. Effective management ties together policy, technology, people and communication to ensure swift detection and coordination.
4. Stakeholder communication
Communication during a breach is critical. Internally, security teams must keep executives, legal counsel, privacy officers, operations and customer success informed. Externally, vendors may need to notify enterprise clients (who may be controllers or processors themselves), supervisory authorities and, when required, affected individuals. Messages should describe the incident, the data categories involved, potential consequences, measures taken and contact details. Clear messaging prevents panic and demonstrates accountability.
Step‑by‑Step Framework: Building Your GDPR Incident Response Plan
This framework synthesises GDPR obligations, NIST and ISO guidance and Konfirmity’s experience supporting thousands of audits. Adjust each step to fit your organisation’s size and risk profile. It forms the heart of your GDPR Incident Response Plan and guides your team through preparation, detection, containment and recovery.
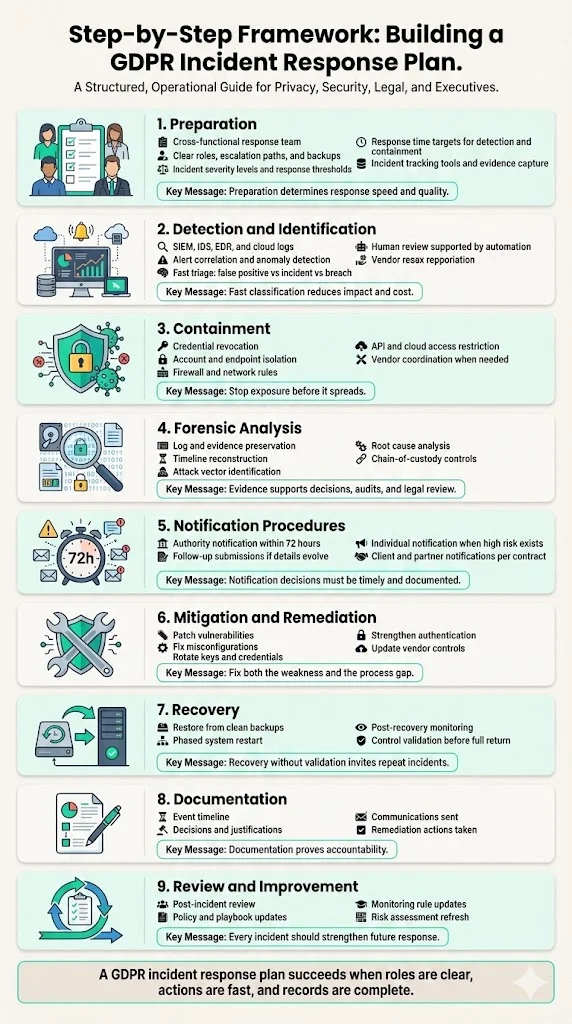
1) Preparation
Build your team. Assemble a multidisciplinary team including cybersecurity professionals, engineers, legal counsel, privacy officers, operations and communications experts. Appoint a coordinator (often the Chief Information Security Officer) with authority to mobilise resources. Define roles, escalation paths and backups. Maintain a central register of contacts.
Establish governance. Develop a policy that classifies incidents by severity and sets thresholds for escalation. Determine when to involve legal counsel, forensic specialists or regulators. Map your response with other frameworks such as SOC 2, ISO 27001 and HIPAA. Set response objectives (SLOs) for detection (e.g., within 24 hours) and initial containment (e.g., within two hours).
Choose tools and document procedures. Adopt an incident management platform to track events, assign tasks and capture evidence. Automate collection of logs, alerts and communications where possible. Documentation simplifies audits and post‑incident reviews. Konfirmity’s managed service integrates with clients’ ticketing systems to capture evidence automatically.
2) Detection & identification
Monitor continuously. Deploy security information and event management (SIEM) tools, intrusion detection systems (IDS), endpoint detection and response (EDR) solutions and cloud provider logs. Configure alerts for anomalous behaviour, failed logins, unusual data transfers and configuration changes. Centralise logs and apply correlation rules to identify patterns.
Classify rapidly. When an alert triggers, analysts must determine whether it’s a false positive, a minor security event or a potential data breach. Consider the data type, number of records, possible unauthorised access and potential harm. Quick classification reduces dwell time and can cut costs; IBM reported that average breach costs dropped from USD 4.88 million in 2024 to USD 4.44 million in 2025 partly due to faster containment.
Use automation wisely. Machine learning can prioritise alerts, but it should augment, not replace, skilled analysts. In 2025, 97 % of organisations reporting incidents involving machine‑learning systems lacked proper access controls. Ensure automation is governed and complements human oversight.
3) Containment
Limit damage. Once a data breach is confirmed, the immediate goal is to stop further loss or exposure. Revoke compromised credentials, disable affected accounts, isolate infected endpoints, apply firewall rules and, if necessary, temporarily shut down impacted services. Restrict access to compromised cloud storage or APIs and rotate keys. If the breach involves third‑party software, coordinate with the vendor to apply patches.
Segment networks. Implement least‑privilege access and micro‑segmentation to limit lateral movement. In Konfirmity engagements, network segmentation reduces blast radius and response effort by up to 30 %.
4) Forensic analysis
Gather evidence. Preserve logs, database snapshots, memory dumps, network captures and configuration files in a manner admissible for legal proceedings. Document the attack vector, timeline, systems accessed, data affected and any exfiltration. Use tools that maintain a chain of custody. Large breaches may require external forensic experts or law enforcement.
Identify the root cause. Determine how the breach occurred and why existing controls failed. Review exploited vulnerabilities, misconfigurations and social engineering tactics. Use vulnerability scoring frameworks (e.g., CVSS) to prioritise remediation. If the breach involves third‑party components, update your vendor risk management process.
5) Notification procedures
Inform authorities. If the risk assessment concludes that the breach may affect individuals’ rights, controllers must notify the supervisory authority within 72 hours. The notification should describe the incident, provide categories and approximate numbers of data subjects and records, list contact details, outline likely consequences and describe measures taken or proposed. If information is incomplete, send what you have and follow up.
Notify affected individuals. When a breach poses a high risk to individuals’ rights, controllers must communicate directly with those individuals without undue delay. Use clear language and explain what happened, what data is involved, possible consequences, measures taken and actions individuals can take (such as changing passwords or watching for fraud). Notification may not be required if encryption renders data unreadable or the risk has been mitigated.
Notify clients and partners. Contracts often require suppliers to notify enterprise clients and partners promptly, even if GDPR thresholds are not met. Transparent communication builds trust and allows clients to take their own steps.
6) Mitigation & remediation
Fix vulnerabilities. Based on forensic findings, patch software, update firewall rules, rotate encryption keys, harden configurations and enforce stronger authentication (e.g., passkeys). Ensure backups are secure and accessible. If third‑party components contributed to the breach, coordinate with vendors and revise vendor risk policies. Document remediation actions and verify they are effective.
7) Recovery
Restore safely. Recover systems from clean backups once the environment is secured. Bring services back up in phases and monitor for signs of persistence. Validate that security controls function correctly before returning to normal operations.
8) Documentation
Record everything. GDPR requires controllers to document facts, effects and remedial actions for each breach. Maintain a timeline of events, decisions, communications and remediation efforts. Use an incident management platform to ensure records are complete. Documentation supports regulatory inquiries, audits and post‑incident reviews.
9) Review & continuous improvement
Learn and adapt. Conduct a post‑incident review to identify lessons learned. Update policies, playbooks and escalation paths. Improve training, adjust monitoring rules and refine risk assessments. Incorporate insights into your information security management system (ISMS) and cross‑framework compliance program. Continual improvement ensures the plan stays effective.
Practical examples & templates
Scenario 1: Cloud misconfiguration. A misconfigured storage bucket exposes customer records. Monitoring detects unusual outbound traffic. The team revokes public access, rotates keys and conducts a forensic review. The breach involves names and emails. Risk assessment indicates high risk, so the controller notifies the authority within 72 hours and informs customers. Lessons: continuous monitoring and clear escalation paths enabled timely containment.
Scenario 2: Lost encrypted laptop. An employee loses a laptop with encrypted HR data. Full‑disk encryption and remote wipe were enabled. The organisation concludes risk is low and does not notify individuals. The incident is documented and used to reinforce device security training. Lessons: strong encryption can prevent high‑risk breaches and reduce notification obligations.
Notification structure. When notifying authorities or individuals, include: nature of the incident; categories and approximate number of data subjects and records; likely consequences; measures taken; contact details; and a promise to provide further updates.
Simplified plan template. A nine‑step checklist summarises the framework: (1) Preparation—define roles and train staff; (2) Detection & identification—monitor and classify; (3) Containment—limit damage; (4) Forensic analysis—collect evidence and find root cause; (5) Notification—inform authorities, individuals and clients; (6) Mitigation & remediation—fix vulnerabilities and update controls; (7) Recovery—restore systems from backups; (8) Documentation—record actions; (9) Review & improvement—learn and refine.
Tools & Security Measures to Support Response Plans
Effective plans rely on technology and controls. These tools support a strong GDPR Incident Response Plan:
- Monitoring & detection. Deploy SIEM, IDS/IPS, EDR and vulnerability scanners. Enable logging at application, database and infrastructure layers. Centralise logs and use correlation rules to detect patterns. Use threat intelligence feeds.
- Incident management platforms. Use tools such as TheHive, PagerDuty or ServiceNow to coordinate tasks and communications. Integrate with ticketing and collaboration platforms to create a single source of truth.
- Automation. Automate alerts, evidence capture and notification drafts. Automation reduces dwell time but must be governed. Konfirmity’s service combines automation with expert oversight.
- Security controls. Enforce encryption at rest and in transit, strong authentication (passkeys or hardware tokens), least‑privilege access and secure coding. Patch systems regularly and conduct vulnerability scans. Use network segmentation and maintain an asset inventory to ensure nothing escapes monitoring.
Training & Awareness
People remain a critical factor in incident response:
- Run tabletop exercises. Simulate breaches to test readiness, clarify roles and uncover bottlenecks. Walk through detection, containment, notification and recovery. Use lessons to refine playbooks.
- Educate employees. Provide training on phishing, password hygiene, secure data handling and device security. Encourage staff to report suspicious activity. Use interactive modules and periodic refreshers.
- Invest in resources. Staffing shortages raise breach costs. Training, automation and managed services help reduce detection and containment time, freeing internal teams to focus on high‑impact tasks.
Common Mistakes and How to Avoid Them
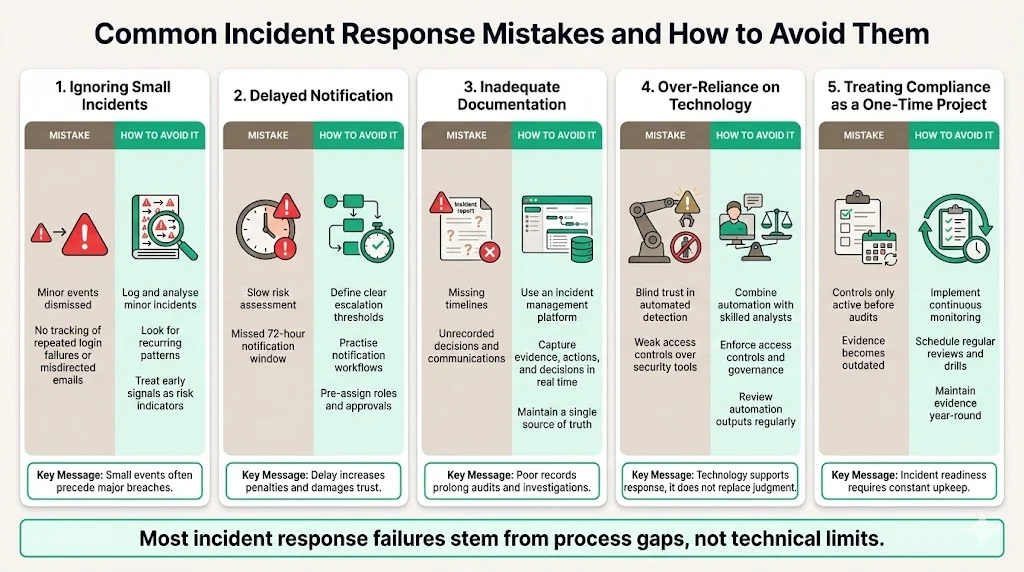
Avoid these pitfalls:
- Ignoring small incidents. Repeated login failures or misdirected emails may signal larger problems. Document and analyse minor events to spot patterns.
- Delayed notification. Missing the 72‑hour window increases penalties and erodes trust. Establish clear processes to assess risk quickly and rehearse notification procedures.
- Inadequate documentation. Incomplete records hinder investigations and prolong audits. Use incident management tools to capture evidence, decisions and communications in real time.
- Over‑reliance on technology. Automation aids detection but must be governed. In 2025, most incidents involving machine‑learning systems lacked proper access controls. Maintain skilled analysts and clear policies.
- Treating compliance as a project. Compliance is continuous. One‑off initiatives lead to control drift and last‑minute scrambles. Ongoing monitoring and managed services keep controls in place and evidence fresh.
Conclusion
A mature GDPR Incident Response Plan is essential for enterprise suppliers. It demonstrates the ability to detect, manage and report breaches effectively and to protect individuals’ rights. Regulators have issued over €5.65 billion in fines, including a €1.2 billion penalty for unlawful transfers, and the average cost of a breach remains high—USD 4.88 million in 2024, dropping to USD 4.44 million in 2025 due to faster containment. Building a plan requires clear roles, strong monitoring, regular exercises and thorough documentation. Integrating the plan with SOC 2, ISO 27001 and HIPAA ensures that controls withstand audits and buyer scrutiny. Incident response is a continuous operation supported by trained staff, automation and a mindset of accountability. Security that only looks good on paper is a liability. Start with real security, operate it daily and let compliance follow.
Konfirmity’s human‑led managed service supports teams throughout this process and focuses on implementing real controls inside your stack rather than producing paperwork.
FAQs
1) Does GDPR require an incident response plan?
While the GDPR does not explicitly demand a written “plan,” it requires organisations to detect, document and report personal data breaches quickly and to implement appropriate technical and organisational measures. To meet these obligations consistently, a documented GDPR Incident Response Plan is effectively necessary.
2) What is a GDPR response plan?
A GDPR Incident Response Plan is a set of procedures that guides an organisation in identifying, analysing, containing, investigating, reporting and recovering from incidents involving personal data. It defines roles, escalation paths, tools, notification processes and post‑incident reviews, ensuring compliance with Articles 33 and 34 and alignment with SOC 2, ISO 27001 and HIPAA.
3) What are the seven steps of an incident response plan?
A widely used model includes: Preparation, Detection & identification, Containment, Forensic analysis, Notification, Mitigation & remediation, Recovery and Review. This guide adds documentation as a separate step because GDPR requires recording facts, effects and actions. NIST’s incident response guidance integrates these steps across the govern, identify, protect, detect, respond and recover functions.
4) What is Article 33 of the GDPR?
Article 33 covers notification of personal data breaches to supervisory authorities. It obliges controllers to report a breach without undue delay and, where feasible, within 72 hours of becoming aware. The notification must describe the incident, provide contact details, outline likely consequences and list measures taken or proposed. Controllers must also document breaches and justify any delay.





.svg)





.svg)
.svg)