Security incidents and data breaches aren’t hypothetical; they’re daily realities with legal, financial and reputational consequences. A breach notification plan explains how an organization will recognise a security incident, determine whether it constitutes a breach and communicate with those affected. For companies seeking SOC 2 attestation — particularly Type II examinations that require evidence over a period — breach notification matters because it demonstrates control over incident response and commitment to transparency. Enterprise clients rely on partners whose security posture is proven, not promised. Failing to notify clients, regulators or contractually obligated partners promptly damages trust and can violate laws such as HIPAA’s 60‑day rule or GDPR’s 72‑hour requirement.
This guide connects security incidents, data breaches, compliance requirements and client trust. It shows how effective breach notification fits into SOC 2’s Trust Services Criteria and how incident response and risk management processes support an environment of accountability. Written in the voice of a practitioner, it addresses the needs of chief information security officers (CISOs), compliance leaders and enterprise buyers who must see more than policy documents; they require proof of operational controls.
What Is SOC 2 and Why It Matters
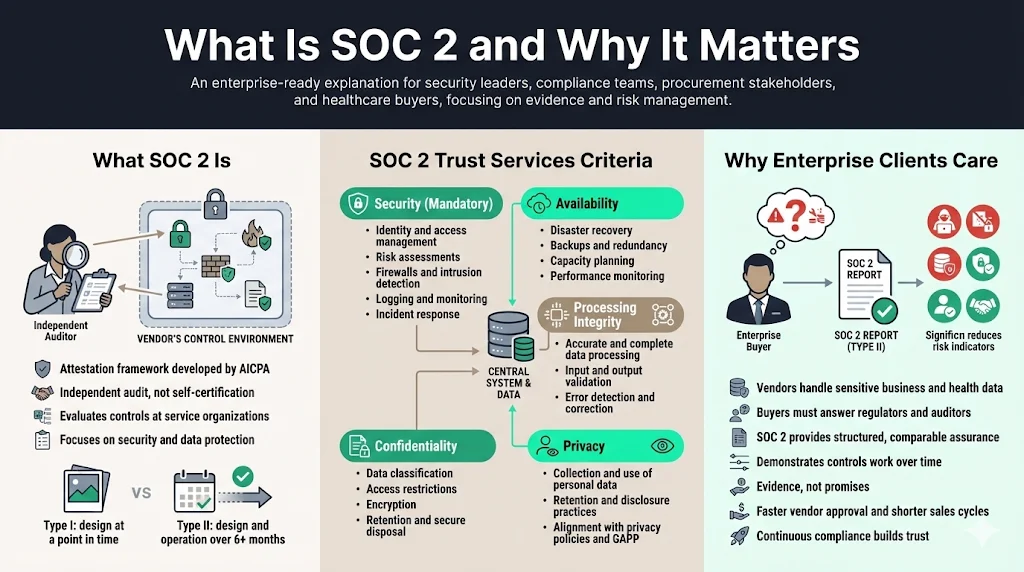
SOC 2 is an attestation framework developed by the American Institute of Certified Public Accountants (AICPA). It is a report on controls at a service organization relevant to security, availability, processing integrity, confidentiality or privacy. Unlike self‑certifications, SOC 2 examinations are conducted by independent auditors who assess whether an organization’s controls meet defined criteria over time. Type I reports examine the design of controls at a moment, while Type II reports review the operation of controls over at least six months.
Why do enterprise clients insist on SOC 2 attestation? Large companies and healthcare providers outsource operations to cloud vendors and software providers. These buyers must answer their own regulators about how third parties protect data. SOC 2 provides a structured set of criteria that correspond to the trust services categories:
- Security — The foundation of every SOC 2 examination. It focuses on protecting systems and data from unauthorized access, misuse or modification. Controls include identity and access management, risk assessments, firewalls, intrusion detection, logging and incident response.
- Availability — Ensures systems are available for operation as committed. It involves controls such as disaster recovery, backups, capacity planning and performance monitoring.
- Processing integrity — Ensures systems process data completely, accurately and timely. Controls include input and output validation, error detection and monitoring.
- Confidentiality — Protects information designated confidential. Controls include data classification, access restrictions, retention/disposal policies and encryption.
- Privacy — Covers collection, use, retention and disclosure of personal data based on privacy policies and the Generally Accepted Privacy Principles.
Enterprise clients care about SOC 2 because it indicates whether their vendors have designed and operated controls that meet these criteria. It isn’t just a seal — it’s evidence that the company has undergone rigorous testing. When a vendor can show continuous compliance and audited incident response logs, deals move faster.
SOC 2 and Security Incidents
A security incident is any event that jeopardizes confidentiality, integrity or availability of information systems. A data breach is a security incident in which sensitive information is accessed or disclosed without authorization. SOC 2 doesn’t define incidents in statute, but the Trust Services Criteria require organizations to implement processes to detect and respond to security incidents. The common criteria emphasise detection and response, requiring organizations to have tools and procedures to detect incidents in real time and respond quickly. In other words, auditors expect more than an incident response policy; they look for evidence that incidents are logged, categorized and handled systematically.
Security incidents vary from credential‑stuffing attempts to ransomware, supply‑chain intrusions and insider errors. The 2025 Verizon Data Breach Investigations Report found that ransomware was present in 44% of breaches, stolen credentials accounted for 22% of breaches and human error contributed to 60%. Third‑party breaches jumped from 15% to 30% of all incidents, showing how vulnerable vendor ecosystems have become. These figures show why detection and triage must be disciplined. When incidents remain unclassified or buried in logs, organizations fail to meet SOC 2’s expectations and risk missing regulatory reporting deadlines.
Incident Response and Risk Management in SOC 2
Incident response planning is not just about technical containment; it’s a structured, repeatable process that starts long before a breach occurs. NIST SP 800‑61r3, updated in April 2025, frames incident response within the NIST Cybersecurity Framework functions: Protect, Detect, Respond and Recover. While governance and risk identification underpin readiness, the active incident response cycle focuses on detection, response and recovery. This process maps to SOC 2 controls and is critical for evidencing compliance.
1) Detect
Detection means identifying potential cybersecurity attacks through monitoring, alerts and anomaly analysis. Under SOC 2, detection controls may include real‑time threat monitoring, intrusion detection systems, log correlation and user‑behaviour analytics. The NIST guidance emphasises that detection is a distinct function that works alongside identification and improvement. Service organizations must tune alerts to reduce false positives and ensure that personnel review logs regularly. In our work at Konfirmity, we often discover clients rely solely on vendor dashboards; auditors expect additional oversight, such as daily log reviews and documented escalations.
2) Assess
Once an incident has been detected, teams must assess severity and classify the type of incident. This stage involves triage: determining whether it’s a false alarm, minor security event or a potential breach. Assessments should consider factors like data types affected, systems involved and whether confidentiality, integrity or availability were impacted. Integrating frameworks such as the Common Vulnerability Scoring System (CVSS) helps prioritise incidents. Konfirmity’s managed service uses CVSS to assign severity and sets service targets based on impact — critical incidents get investigated within hours, while low‑risk events are logged for later review.
3) Respond
Response activities aim to contain the incident, eradicate malicious elements and prevent further harm. In SOC 2, response controls include procedures for isolating affected systems, revoking compromised credentials, communicating with stakeholders and documenting actions. NIST calls for clear roles and responsibilities: leadership to approve major decisions, incident handlers to coordinate technical actions, technology teams to analyse and remediate, legal to advise on regulatory obligations, and communications teams to handle public statements. Service organizations should have runbooks that match these responsibilities. In our audits we often see gaps where developers react spontaneously without formal escalation; auditors flag this because it fails to show structured response.
4) Recover
Recovery restores systems and data to normal operation. Activities include rebuilding infrastructure, restoring from backups, validating system integrity and monitoring for residual threats. For SOC 2, recovery also means resuming service availability according to documented recovery time objectives (RTOs) and recovery point objectives (RPOs). Clients may request proof of disaster recovery tests, failover drills and evidence that backups are encrypted and tested regularly. A clear recovery plan also sets expectations on customer communications during outages.
5) Review
The final step is lessons learned. After an incident, teams should perform a post‑mortem to evaluate the response, identify what worked and what failed, and update procedures accordingly. NIST’s model emphasises continuous improvement, feeding findings back into risk assessment and control design. SOC 2 auditors check whether organisations review incidents and refine controls. Konfirmity encourages clients to conduct tabletop drills and record improvement actions. Without this feedback loop, the same vulnerabilities remain and compliance efforts stagnate.
Incident response planning sits alongside risk management. Effective programs continuously assess threats, vulnerabilities and the likelihood of incidents. They maintain a risk register, run vulnerability scans, enforce patch management and conduct regular access reviews. SOC 2 requires that risk responses match risk appetite and be reviewed periodically. When incident response is integrated with risk management, detection and notification decisions become faster and more defensible.
SOC 2 Breach Notification: Common Misconceptions
One misconception is that SOC 2 mandates breach notification timelines similar to regulatory rules. SOC 2 is an attestation standard, not a law. It doesn’t specify a number of hours or days for notifying customers or regulators. Instead, auditors look for documented procedures that help management decide when and how to notify. This contrasts with frameworks like HIPAA, which requires covered entities to notify affected individuals without unreasonable delay and no later than 60 days after discovery, and the GDPR, which requires controllers to notify the supervisory authority without undue delay and, where feasible, within 72 hours of becoming aware of a personal data breach. U.S. regulatory changes add more complexity: the SEC’s amended Regulation S‑P demands written cyber policies and notice to individuals within 30 days absent a no‑harm finding, and the forthcoming Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) will require certain entities to report substantial cyber incidents within 72 hours and ransomware payments within 24 hours. These laws illustrate that SOC 2 alone does not free you from statutory obligations.
Another misconception is that SOC 2 is purely about documentation. Some firms sell one‑time audit packages, promising a fast certificate in two weeks. Such “compliance manufacturing” fails under real‑world incident pressure. Auditors do not just check whether a company has a breach notification policy; they examine whether incidents are logged, evidence exists for decisions taken, and notifications were issued when required. Our experience supporting thousands of audits shows that clients who view SOC 2 as a continuous program — with controls embedded into their systems and run daily — have fewer audit findings and smoother sales cycles. On the other hand, companies that view compliance as a box‑ticking activity often get stuck in remediation after the first audit and must rework processes.
Elements of an Effective Breach Notification Procedure
For enterprise‑grade readiness, breach notification procedures must support rapid detection, informed decisions and clear communications. Below are the important elements and how they relate to SOC 2 control expectations.
1) Incident Detection and Initial Triage
Notification begins with early detection. Organizations must monitor systems, endpoints and third‑party connections to recognise anomalies. Logging must capture security events, and detection tools should trigger alerts. SOC 2’s common criteria emphasise detection and response, requiring documented procedures and tools. When an alert fires, the team should perform initial triage: classify the event, record the time and source, and assign a severity rating. Logs should be immutable, time‑stamped and correlated to show context. At Konfirmity we often implement automated playbooks that augment alerts with user and system data, speeding triage and reducing manual errors.
2) Investigation and Impact Assessment
Once an incident is classified as potentially serious, teams must investigate. This involves gathering evidence, analysing logs and determining what data or systems are affected. Risk management and legal/privacy stakeholders should be involved early to assess confidentiality impact and legal obligations. Severity assessment should consider whether personal data, financial information or protected health information were exposed. For example, HIPAA breaches involve sensitive health data and trigger specific notification requirements. Konfirmity’s incident handlers use structured forms to capture evidence, incident description, data categories, root cause analysis and containment actions. A clear chain of custody prevents tampering and supports forensic investigations.
3) Regulatory and Contractual Considerations
Regulatory requirements vary by jurisdiction and sector. HIPAA requires notifying affected individuals and the Secretary of Health and Human Services within 60 days. The GDPR demands notification to the supervisory authority within 72 hours and to the data subjects if the breach is likely to result in a high risk to their rights. CIRCIA will impose 72‑hour reporting for certain critical infrastructure incidents and 24 hours for ransomware payments. In the United States, at least 24 states have introduced 72‑hour breach notification laws as of early 2026. Contracts with enterprise clients often specify shorter notification periods — some require notice within 24 hours. Service organizations should map their breach notification procedures to each regulatory regime and contract. A matrix that lists jurisdictions, notification triggers, timelines and reporting channels ensures nothing is overlooked.
4) Decision to Notify
The decision to notify depends on severity and legal requirements. Internal stakeholders — security leaders, legal counsel, privacy officers and the executive team — need to weigh the risks of under‑reporting against premature disclosure. The criteria may include: the type of data compromised, the potential for harm to individuals, whether the breach is contained and contractual obligations. Transparency is essential; if an incident involves personal data and poses a risk, the default should be to notify. In our program, we advise clients to maintain a decision register documenting who approved the notification, when and why. This register proves to auditors that decisions were deliberate and consistent with policy.
5) Notification Timing and Content
When a breach requires notification, timing is critical. Organizations should aim to notify affected parties as soon as practical after confirming the breach and gathering essential facts. Timeliness builds trust and satisfies regulators. Notifications should include:
- Nature of the incident — A plain‑language description of what happened without exposing sensitive details.
- Scope of affected data — Types of data involved (e.g., names, addresses, financial records, health information) and approximate number of records affected.
- Estimated timing and impact — When the incident occurred, when it was discovered and how long data was exposed. Provide context on system downtime if relevant.
- Actions taken — Steps already taken to contain the incident, such as disabling compromised accounts, applying patches or rotating keys.
- Mitigation steps for individuals — Advice on monitoring accounts, changing passwords or enrolling in credit monitoring. For HIPAA breaches, notices should explain recommended steps to protect health information.
Notifications to regulators may require additional details, such as contact information for a point of contact, description of likely consequences and measures to address the breach. For enterprise clients, communications should include assurances about ongoing remediation and improvements.
6) Post‑Notification Steps
After initial notification, organizations must continue mitigation and keep stakeholders informed. This includes monitoring systems for further signs of compromise, restoring services and addressing root causes. It also involves regulatory follow‑up. For example, HIPAA requires that notices to the Secretary of HHS for breaches involving fewer than 500 individuals be submitted within 60 days after the end of the calendar year. Organizations should prepare consolidated reports for internal leadership, update risk registers and adjust controls. A second round of communication may be necessary if the investigation reveals additional affected parties or new facts. Documenting these communications ensures auditors can verify that the organization followed its procedures.
Documentation and Audit Preparedness
Documentation is a pillar of SOC 2 readiness. Auditors need evidence that controls exist and operate effectively. For breach notification, organizations must maintain:
- Incident logs — Time‑stamped records of alerts, actions taken, investigators involved and outcomes. These logs should be immutable and accessible to auditors.
- Communications — Copies of notification letters, emails and regulatory filings. For HIPAA, this includes letters to individuals, media notices for breaches affecting more than 500 people and submissions to the HHS Secretary.
- Evidence — Documentation of risk assessments, vulnerability scans, access reviews, change management and incident response drills. Bright Defense notes that auditors look for documented incident response and escalation procedures and incident response reports.
- Decision registers — Records of decisions made about whether to notify and why. These should include references to contractual clauses, regulatory obligations and severity assessments.
- Policies and procedures — Written incident response plans, breach notification policies and privacy notices. These documents should reflect current regulatory requirements and contractual commitments.
Well‑organized documentation supports audit readiness and reduces the time internal teams spend answering auditor questions. At Konfirmity, our managed service reduces evidence collection hours by 75%, from 550–600 hours for self‑managed programs to about 75 hours per year for clients, by maintaining curated evidence repositories and automating data ingestion.
Third‑Party Vendors and Breach Notification
Modern businesses rely on vendors, cloud providers and other partners to deliver services. Breaches affecting third parties often ripple into your environment. Verizon’s 2025 report found that 30% of all breaches stemmed from third parties and SecurityScorecard’s 2025 study suggested 35.5% of breaches are linked to third‑party access. The cost of a third‑party breach averages $4.91 million and increases total breach cost by around $370,000. These statistics show why vendor management is integral to breach notification.
Embedding Notification Obligations into Vendor Contracts
Contracts should require vendors to report incidents that affect your data or services within defined timeframes. Shorter timeframes (e.g., 24 hours) give your organization headroom to meet 72‑hour deadlines like GDPR or CIRCIA. Contracts should also obligate vendors to provide details on the nature of the breach, data affected, remediation actions and cooperation with investigations. Specify contact points, encryption requirements for notifications and responsibilities for public communications. Many organizations include right‑to‑audit clauses to verify vendors’ incident response capabilities.
Third‑Party Risk Management Best Practices
To manage vendor risk, organizations should:
- Maintain a vendor inventory with risk ratings and data flows.
- Perform due diligence before onboarding, assessing security controls, policies and previous incidents.
- Conduct periodic reviews including penetration tests, vulnerability scans and evidence requests.
- Monitor third‑party breaches by subscribing to threat intelligence feeds and industry notices.
- Simulate incidents involving vendor integrations to test notification workflows.
When Vendor Incidents Trigger Your Own Notification
If a vendor breach involves your data or could affect your operations, handle it as if it were your own. Start the incident response process: detect (through vendor notification or public disclosure), assess impact, and decide whether to notify your clients and regulators. Third‑party breaches may extend your notification timelines because you rely on the vendor for information. Document all communications and update your risk register accordingly. In our experience, companies that proactively reach out to vendors for clarifications are better positioned to meet regulatory deadlines than those who wait for vendors to volunteer details.
Templates and Practical Tools
Templates offer structure and consistency. The following examples illustrate fields and items to include in your internal documents. Adapt them to suit your environment and regulatory obligations.
Incident Report Template
Internal Breach Notification Memo
An internal memo to executives and principal teams should contain:
- Incident description and timeline.
- Systems and data affected.
- Severity rating and potential impact on operations and customers.
- Steps taken and next steps.
- Recommendations for management decisions, including whether external notifications are required.
Customer Notification Template
When communicating with customers, use clear language and avoid technical jargon. Include the following sections:
- Overview of the incident — A concise statement describing what occurred, without assigning blame.
- Information involved — Types of data affected and whether sensitive data was exposed.
- Actions taken — Immediate steps your organization has taken to contain the breach and protect data.
- Guidance for customers — Steps customers should take, such as resetting passwords, monitoring accounts or contacting support.
- Contact information — Provide a dedicated channel for inquiries (email or hotline) and an assurance that updates will follow as new information becomes available.
Regulatory Notification Checklist
- Identify the applicable law or regulation (HIPAA, GDPR, CIRCIA, state law).
- Determine the supervisory authority or regulator to notify.
- Check the notification timeline (60 days, 72 hours, 30 days, etc.).
- Gather required information: description of breach, categories and number of data subjects, contact details, consequences and measures taken.
- Submit notification via the prescribed channel (portal, email or letter).
- Document the notification date, confirmation of receipt and any regulator responses.
Best Practices for Enterprise Compliance
To maintain readiness, organizations should integrate breach notification into broader security and compliance strategies:
- Test and revise procedures regularly. Conduct tabletop drills simulating different scenarios (e.g., ransomware, vendor breach, insider threat). Review logs and decisions to improve reaction times.
- Conduct continuous monitoring. Use automated tools to monitor vulnerabilities, access controls and configurations. Establish service‑level agreements for patching high‑risk vulnerabilities within specific timeframes.
- Integrate with risk management. Maintain up‑to‑date risk registers and ensure incident response plans address identified threats. Use risk assessments to prioritise investments in detection and response.
- Engage legal and privacy counsel. Laws and regulations change. Regularly review breach notification requirements across jurisdictions and update policies accordingly.
- Train employees. Awareness training should cover how to report incidents, avoid phishing and follow data handling policies. Human error remains a top factor in breaches.
- Review vendors. As third‑party breaches surge, evaluate vendor security practices and ensure contracts include notification and cooperation clauses.
When partnering with a managed service provider like Konfirmity, companies benefit from a dedicated team that implements, operates and improves controls throughout the year. Our program typically reduces SOC 2 readiness timelines to 4–5 months compared with 9–12 months for self‑managed programs and cuts the internal effort from roughly 550–600 hours to about 75 hours annually. Continuous monitoring, access reviews, vendor risk workflows and evidence management let clients focus on their core mission while meeting buyer and auditor expectations.
Wrap‑Up
Security that looks good on paper but fails under incident pressure is a liability. The SOC 2 Breach Notification Guide offers more than policy templates; it outlines the operational realities of incident response, risk management and regulatory obligations. By starting with security and arriving at compliance, organizations build controls that stand up to buyers, auditors and attackers. Documented procedures and evidence help accelerate procurement cycles, reduce findings and enhance client confidence. In a time when third‑party breaches are rising and regulators are tightening reporting rules, a well‑designed breach notification process isn’t optional — it’s essential to protect your business and the people who rely on your services.
FAQ — SOC 2 Breach Notification Guide
1. Does SOC 2 require mandatory breach notification?
No. SOC 2 does not prescribe specific timelines or obligations for notifying customers or regulators. It focuses on having documented procedures and controls that guide response decisions. Regulatory rules like HIPAA’s 60‑day requirement, GDPR’s 72‑hour rule or the forthcoming CIRCIA timelines still apply.
2. What’s the difference between incident response and breach notification?
Incident response covers the entire cycle: detection, assessment, containment, investigation, recovery and improvement. Breach notification is a subset of incident response. It focuses on communicating to affected stakeholders once a breach is confirmed and legal or contractual thresholds are met.
3. How does breach notification tie into SOC 2 audit criteria?
Auditors review whether your notification procedures are documented, whether you’ve implemented controls to detect and assess incidents and whether you followed your procedures when incidents occurred. Proper documentation — incident logs, decision registers and evidence of notifications — enhances audit preparedness.
4. Should third‑party vendor breaches be included in my notification process?
Yes. If a third‑party incident affects your services or client data, you have to handle it as your own. Include vendors in your breach notification and risk management procedures and ensure contracts require timely disclosure.
5. What should a customer notification include?
At minimum, your notice should explain what happened, what data types were involved, when it occurred, what you’ve done to mitigate the risk and what steps customers should take to protect themselves. It should also provide a point of contact for additional information and commit to follow‑up updates.





.svg)




.svg)
.svg)