Most enterprise procurement teams now ask hard questions about security before signing a contract. They want to see proof that vendors can protect data, not just a promise. In parallel, attackers and regulators keep raising the stakes: the 2025 Cost of a Data Breach report shows that the global average cost of a breach dropped slightly to USD 4.4 million, yet the potential impact remains enormous. For companies selling to large clients or handling regulated data such as electronic protected health information (e‑PHI), robust testing is mandatory. ISO 27001 Penetration Testing is one of the most visible measures because it demonstrates how well your controls stand up to actual attacks. This article explains what decision makers expect during security reviews, where testing fits into the ISO framework, and how a human‑led managed service like Konfirmity delivers repeatable, audit‑ready results.
Why ISO 27001 Penetration Testing Matters for Enterprise Buyers
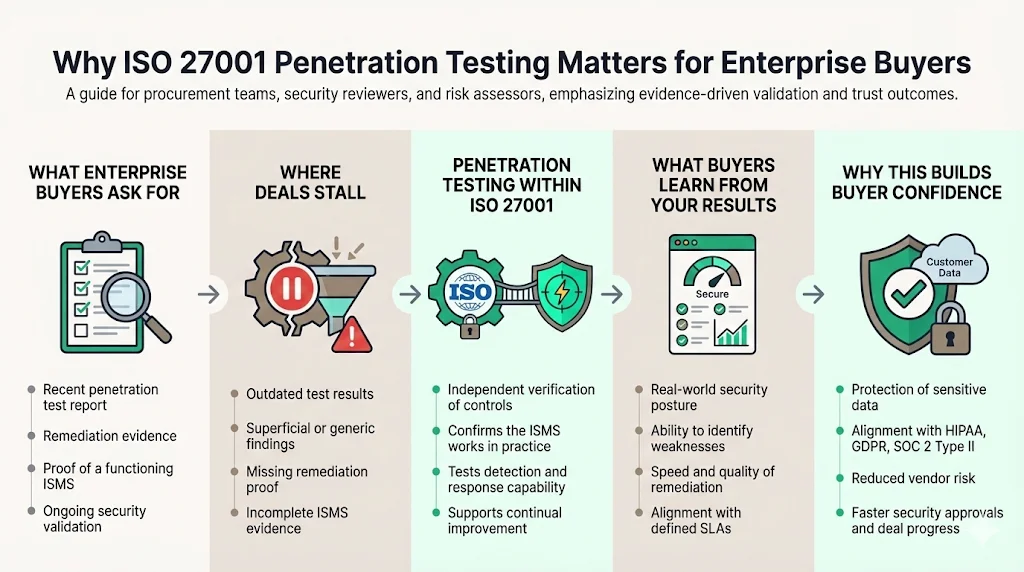
Enterprise buyers have strict vendor risk processes. A typical security questionnaire will ask for your last penetration test, remediation evidence, and proof that you operate a functioning information security management system (ISMS). Deals stall when vendors provide outdated or superficial evidence. Since the ISO/IEC 27001 standard helps organizations establish and continually improve an ISMS, penetration testing acts as an independent check that the system works in practice. Buyers use your testing results to gauge whether your security posture is strong enough to handle their data. A test conducted by a qualified team demonstrates that you identify weaknesses and remediate them in line with agreed service‑level agreements (SLAs). It also shows you’re serious about protecting personal data and complying with frameworks like HIPAA, GDPR and SOC 2 Type II.
Penetration Testing in Modern Security Programs
Penetration testing sits alongside other components of a mature security program. Risk assessments identify threats, vulnerability assessments uncover potential weaknesses, and penetration tests simulate real attackers to validate how far those weaknesses can be exploited. The National Institute of Standards and Technology (NIST) states that an information security assessment uses testing, examination and interviewing to determine how effectively an entity meets its security objectives. Testing is not optional; it provides evidence that controls perform as designed. In practice, penetration testing complements practices such as secure software development, continuous monitoring and incident response. When combined, these activities allow you to start with security and arrive at compliance – the approach Konfirmity takes across its 6,000+ audits.
What Decision Makers Expect During Vendor Reviews
Procurement and security teams reviewing a vendor will ask for more than a certificate. They want to know when the last ISO 27001 Penetration Testing exercise took place, whether the scope covered all relevant assets, how findings were rated and remediated, and who performed the test. They may request sanitized evidence, such as an executive summary of the penetration test report and a remediation tracker. Enterprise buyers also check alignment with other frameworks (SOC 2, HIPAA, GDPR) to ensure the ISMS addresses broader compliance obligations. Because penetration testing reveals exploitable weaknesses and the actions taken to fix them, it plays a direct role in accelerating or delaying contract negotiations.
What ISO 27001 Actually Says About Penetration Testing
Clearing Up Mandatory vs. Expected Testing
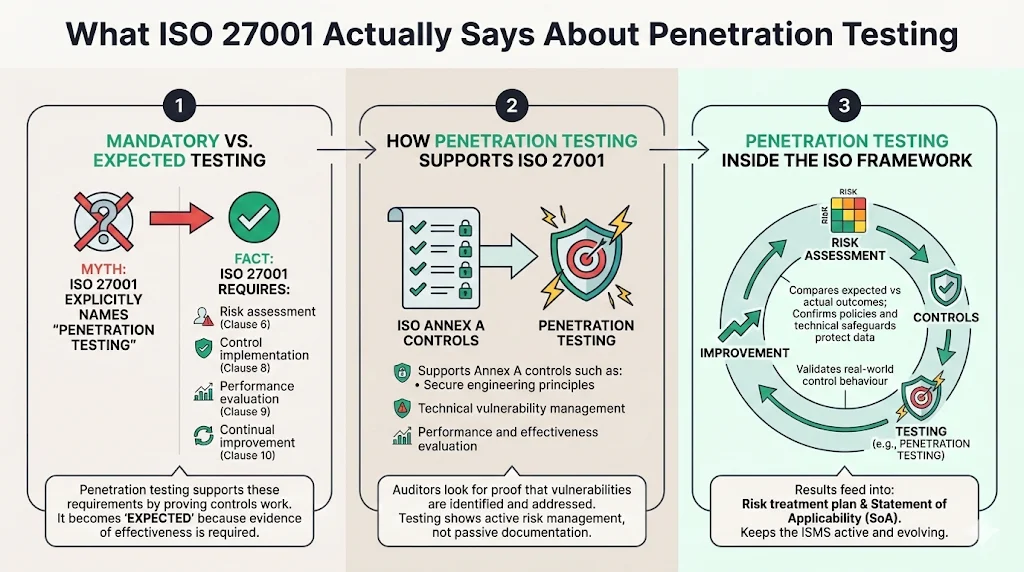
One of the most common misconceptions is that ISO 27001 explicitly requires penetration testing. In fact, the standard does not mention the term directly. What it does require is that organizations establish, implement, maintain and continually improve an ISMS. To meet this requirement, organizations must perform risk assessments (Clause 6), implement controls (Clause 8), evaluate performance (Clause 9) and pursue continual improvement (Clause 10). Penetration testing supports these activities by providing evidence that technical controls are effective. It becomes “expected” because without demonstrating effective control performance, it is difficult to show that risks are managed.
Supporting ISO 27001 Compliance Without Being Named
Penetration testing supports several Annex A controls, such as A.8.5 (secure engineering principles), A.8.8 (management of technical vulnerabilities) and A.5.25 (evaluation of performance and effectiveness). When auditors review your ISMS, they look for evidence that technical vulnerabilities are identified and treated. The ISO overview emphasises that conformity with ISO 27001 involves managing risks related to data security and following best practices. Even though the standard is flexible about how to achieve these objectives, penetration testing offers a clear way to show that you are actively managing vulnerabilities and verifying control effectiveness.
The Role of Penetration Testing Inside the ISO Framework
Within the ISO/IEC 27001 framework, penetration testing acts as a validation step that closes the loop between risk assessment and control implementation. NIST’s guidance on security assessments notes that testing compares actual and expected behaviours. By exercising systems under real attack conditions, penetration testing confirms whether your policies, procedures and technical controls actually protect data. The results feed back into the risk treatment plan and Statement of Applicability (SoA), ensuring that the ISMS remains a living system rather than a static document.
Where Penetration Testing Fits Within ISO 27001
1) Relationship Between Risk Assessment, Vulnerability Assessment and Penetration Testing
Clause 6 of ISO 27001 requires organizations to perform risk assessments and determine how to treat identified risks. A risk assessment identifies assets, threats, vulnerabilities and the likelihood of exploitation. Vulnerability assessments then detect specific weaknesses—often through automated scans—which reveal misconfigurations or unpatched software. Penetration testing goes one step further: it attempts to exploit those weaknesses to demonstrate impact and validate whether controls prevent compromise. NIST describes penetration testing as a four‑phase process—planning, discovery, attack and reporting—where the planning phase sets rules and objectives, discovery gathers information and analyses vulnerabilities, and the attack phase attempts exploitation to confirm vulnerabilities and discover additional issues.
2) Supporting Annex A Security Controls
Annex A contains controls that underpin the ISMS. For example, A.5.25 requires organizations to monitor and review controls for effectiveness. Penetration testing provides real data to fulfil this requirement by showing whether network segmentation, multi‑factor authentication or encryption are working as intended. A.8.8 requires management of technical vulnerabilities; penetration testing identifies high‑risk weaknesses that automated scanners might miss. Similarly, A.5.11 and A.5.12 focus on secure design and engineering—areas where penetration testers can identify systemic flaws early in the development cycle. In this way, penetration testing is not an isolated activity but a critical mechanism that supports multiple controls.
3) Mapping Penetration Testing to Information Security Objectives
ISO 27001 emphasises confidentiality, integrity and availability, known as the CIA triad. The ISO website explains that the standard helps organizations proactively identify and address weaknesses and promotes a holistic approach to people, policies and technology. Penetration testing directly supports these objectives: by verifying whether data remains confidential during an attempted breach, whether unauthorized changes can be made to systems or information, and whether systems remain available under simulated attack. A penetration test thus offers measurable insight into whether your ISMS upholds the CIA triad in real‑world conditions.
ISO 27001 Clauses That Drive Penetration Testing
Clause 6: Risk Assessment and Risk Treatment
Clause 6.1 requires organizations to plan actions to address risks and opportunities. A risk assessment identifies which assets and processes are critical, the threats they face, and the vulnerabilities that could be exploited. Penetration testing supports risk treatment by providing empirical evidence of exploitation potential. Results from a penetration test help prioritize remediation in the risk treatment plan, inform SLAs for vulnerability remediation and support decisions on control selection. For example, if a penetration test reveals that a misconfigured firewall allows unauthorized access, the risk treatment plan may include strengthening network segmentation and updating access rules.
Clause 8: Operational Planning and Control
Clause 8 requires organizations to implement and operate the necessary processes to meet ISMS requirements. It emphasises that processes should be planned, documented and controlled. Penetration testing falls under this clause because it is an operational activity that must be planned (scope, objectives, rules of engagement) and executed by competent personnel. NIST recommends establishing an assessment policy that addresses roles, methodology and frequency. Organizations should integrate penetration testing into their ISMS planning to ensure that testing occurs at appropriate intervals and that findings feed back into operational controls.
Clause 9: Performance Evaluation and Security Audit Readiness
Clause 9 requires organizations to monitor, measure, analyse and evaluate the performance of their ISMS. Internal audits and management reviews are central to this clause. Penetration testing provides objective measurements of control performance. By incorporating test results into performance evaluations, organizations can demonstrate to auditors that they track how well controls mitigate risks over time. For example, a management review might compare the number of high‑risk findings in successive penetration tests and track the speed of remediation. These metrics reveal whether the ISMS is improving and whether resources are allocated effectively.
Clause 10: Continual Improvement Through Testing Results
Clause 10 emphasises continual improvement. Penetration testing delivers actionable insights that drive improvement: each finding identifies a control that did not work as intended, and the remediation process corrects that weakness. Over multiple testing cycles, organizations can demonstrate a reduction in recurring issues and a shortened mean time to remediate. By integrating test results with root‑cause analysis, organizations ensure that improvements address underlying issues rather than symptoms. NIST advises performing root‑cause analysis after assessments to translate findings into mitigation actions.
Penetration Testing vs. Vulnerability Assessment
Clear Differences in Scope, Depth and Outcomes
Vulnerability assessments and penetration testing are complementary but distinct. A vulnerability assessment uses automated or manual methods to uncover security weaknesses and potential entry points; it identifies unpatched software, misconfigurations and exposed services. Kroll notes that a vulnerability assessment aims to uncover weaknesses irrespective of exploitability. In contrast, a penetration test is a controlled exercise with defined objectives, rules of engagement and time limits. It attempts to exploit identified weaknesses to determine whether an attacker could actually gain unauthorized access. The classic analogy is that a vulnerability assessment rattles the doorknob to see whether the door is unlocked, while a penetration test opens the door and walks inside. This difference in intent means that penetration testing provides deeper insights into impact and risk, while vulnerability assessments provide breadth across many assets.
Why Enterprise Clients Expect Both
Enterprise buyers recognise that automated scans alone are insufficient. Vulnerability scans can miss logic flaws, chained exploits or context‑specific weaknesses. They also produce false positives that need triage. A well‑designed security program uses vulnerability assessments to maintain baseline hygiene and penetration testing to validate that critical controls work. Buyers expect to see evidence of both because vulnerability assessments feed into penetration testing and because each addresses different objectives. Combining the two ensures that you identify more weaknesses, prioritize them correctly and address them before they can be exploited.
How Each Activity Supports Threat Identification and Risk Reduction
Vulnerability assessments improve visibility. They detect outdated libraries, weak encryption ciphers or misconfigured permissions, providing a list of issues to fix. Penetration testing illustrates how an attacker could chain these issues to gain unauthorized access or exfiltrate data. Together they enable risk‑based prioritization: issues that allow real exploitation receive higher priority than those that pose only theoretical risk. In turn, remediation efforts can be aligned with risk appetite and contractual requirements. This combination reduces the likelihood of costly breaches and accelerates audit readiness.
Penetration Testing Methodology Aligned With ISO 27001
1) Scoping and Rules of Engagement
Successful penetration testing starts with clear scoping. The scope should define which applications, networks, and cloud services are in play, whether testing is external or internal, and what constraints exist (e.g., production downtime limitations). The planning phase is critical: NIST’s four‑stage methodology lists planning as the first phase, where rules are identified and testing goals are set. Management approval is finalised, and no testing occurs until the scope and rules are documented. At Konfirmity, we define the scope in collaboration with your security and engineering teams to ensure coverage of crown‑jewel assets without impacting critical operations.
2) Asset Identification and Attack Surface Review
Once scoping is complete, testers inventory the assets in scope and map the attack surface. The discovery phase begins with information gathering—collecting host names, IP addresses, open ports, services, and application versions. NIST explains that discovery involves gathering information through DNS queries, WHOIS lookups, network sniffing and other methods. Attack surface review ensures that testers understand how systems connect, what data flows through them and where attackers might enter. Proper discovery prevents blind spots and informs which vulnerabilities merit manual attention.
3) Testing Phases and Validation Steps
The next step is vulnerability analysis. Automated scanners and manual techniques compare discovered services, applications and operating systems against vulnerability databases. NIST notes that testers can use public databases such as the National Vulnerability Database (NVD) and their own knowledge to identify vulnerabilities. Manual analysis uncovers new or obscure vulnerabilities that scanners might miss. In the attack phase, testers attempt to exploit identified vulnerabilities to confirm their existence and determine impact. As NIST describes, executing an attack verifies vulnerabilities, allows testers to learn more about the targeted network, and may enable privilege escalation. These steps are repeated iteratively: after exploitation, testers often loop back to discovery to identify additional weaknesses.
4) Reporting and Evidence Collection for Auditors
The final phase is reporting. Penetration testing reports should provide a narrative of what was tested, the techniques used, and the vulnerabilities found. Findings must include risk ratings (often using a standard such as CVSS), proof of exploitation, impacted assets and remediation advice. Evidence collection is critical: auditors and buyers need to see logs, screenshots and command outputs that demonstrate how vulnerabilities were exploited and remediated. NIST emphasises that organizations should conduct analysis and reporting to translate findings into risk mitigation actions. At Konfirmity, we produce reports that map each finding to ISO 27001 controls and track remediation status. Our human‑led teams guide you through root‑cause analysis and ensure that fixes are verified.
Types of Penetration Tests Relevant to ISO 27001
1) Network Security Testing
Network penetration tests focus on routers, firewalls, switches and other infrastructure devices. They evaluate network segmentation, firewall rules, intrusion detection systems and remote access controls. Testers attempt to bypass network defenses, pivot between network segments and exploit protocol weaknesses. For organizations seeking ISO 27001 certification, network testing validates that network controls (e.g., A.8.20 secure network architecture) are effective.
2) Web Application Testing
Many businesses deliver services through web applications. Web application penetration testing examines code, APIs and authentication flows to uncover injection flaws, broken access control, insecure session management and other issues. Testers use methods such as SQL injection, cross‑site scripting and business logic abuse to demonstrate impact. Because vulnerabilities such as SQL injection are specifically mentioned in NIST’s guide, addressing them is vital. Web testing supports ISO controls around secure development and vulnerability management.
3) Internal vs. External Testing
External testing simulates attacks originating from the internet. It shows how a remote attacker could breach public‑facing services, compromise exposed credentials or exploit misconfigured cloud resources. Internal testing simulates a malicious insider or an attacker who has already breached the perimeter. Internal tests assess lateral movement, privilege escalation and data exfiltration. Both perspectives are important for ISO 27001 because they validate different control layers. Regular internal tests also support SOC 2 Type II requirements for detection and response.
4) Cloud and Infrastructure Testing
As more workloads move to public cloud platforms, penetration testing must include cloud configuration reviews. These tests look for misconfigured storage buckets, overly permissive IAM roles, insecure networking rules and unpatched virtual machines. Cloud testing aligns with ISO 27017 and ISO 27018 guidance for cloud security and data privacy. Infrastructure tests also cover container orchestration platforms (e.g., Kubernetes) and infrastructure‑code pipelines, ensuring that DevOps practices do not introduce hidden risks.
5) Social Engineering Considerations
Technical controls are only part of the equation. Attackers often target people through phishing, pretexting or physical intrusion. Social engineering tests evaluate how well staff follow policies, recognize phishing attempts and report suspicious activity. While ISO 27001 emphasises awareness training, many organizations choose not to include social engineering in their penetration test scope due to privacy and HR considerations. When performed, social engineering tests should be carefully scoped and approved at the highest level.
Penetration Testing Frequency and Timing
How Often Testing Should Be Performed
ISO 27001 does not prescribe a fixed testing cadence. Instead, testing frequency should be risk‑based. High‑risk systems, such as those processing financial transactions or e‑PHI, may require penetration testing every six to twelve months. Lower‑risk systems might be tested annually or after significant changes. NIST recommends that organizations implement a repeatable assessment methodology and address assessment frequency in policy. Konfirmity’s experience shows that enterprise clients undergoing SOC 2 Type II or HIPAA audits typically test critical applications at least annually and conduct targeted tests whenever major changes are introduced.
Triggers for Additional Testing
Triggers for unscheduled tests include: significant changes to infrastructure or applications, mergers or acquisitions, major feature releases, new regulatory obligations, or discovery of major vulnerabilities (e.g., a high‑severity CVE affecting your stack). After an incident, a targeted penetration test can help verify that containment and remediation were effective. Organizations should integrate penetration testing with change‑management processes so that major changes automatically prompt discussions about testing.
Aligning Testing Cycles With Risk Assessment Updates
Risk assessments should be updated at regular intervals and after significant events. Because penetration testing informs risk assessments, the two processes should be aligned. For example, updating the risk register after a penetration test ensures that newly identified risks are recorded and treated. Similarly, when risk assessments identify new threats or changes in threat landscape, they may prompt additional testing. Aligning cycles avoids outdated evidence and ensures that decisions are based on current risk data.
Penetration Test Tools and Techniques
Automated Tools vs. Manual Testing
Automated tools (e.g., network scanners, web vulnerability scanners) can quickly detect known vulnerabilities and misconfigurations. They are essential for initial discovery and for maintaining baseline hygiene. However, they have limitations: they may miss business logic flaws, chained exploits, or context‑specific issues. NIST’s guidance notes that manual testing can uncover new or obscure vulnerabilities that automated scanners may miss. Manual testing involves creative thinking, tailored payloads and custom scripts to probe complex applications and network paths. A balanced approach uses automated tools to cover breadth and manual techniques to achieve depth.
Why Tooling Alone Is Not Enough
Penetration testing is not just about running a scanner. It requires expertise to interpret results, distinguish false positives from true findings, and craft exploits that reflect real attacker behaviour. Attackers chain multiple weaknesses: a seemingly low‑impact vulnerability might be combined with a misconfiguration to gain full access. Tools cannot simulate this creativity. That is why Konfirmity emphasises human‑led testing: our experts bring experience from thousands of audits to spot patterns that automated tools miss. In regulated sectors, auditors recognise the value of experienced testers and may question evidence produced solely by automated tools.
What Auditors Care About When Tools Are Used
Auditors focus on process, evidence and independence. They want to see that tools were selected based on scope and risk, that testing followed a documented methodology, and that findings were validated manually. They may ask for tool output samples to verify that scans were actually performed. Auditors also care about segmentation of duties: internal testing is acceptable when the team is independent from development and operations; otherwise, third‑party testing provides greater assurance. Providing this context helps auditors understand the reliability of the testing results.
Handling Security Vulnerabilities Found During Testing
1) Risk Rating and Prioritisation
Every finding must be classified based on impact and likelihood. Many organizations use the Common Vulnerability Scoring System (CVSS) to assign severity levels. High‑risk vulnerabilities—such as unauthenticated remote code execution—require immediate attention. Medium‑risk vulnerabilities may be accepted temporarily if compensating controls exist. Low‑risk findings can be scheduled for future releases. Prioritisation should also consider regulatory obligations (e.g., HIPAA’s requirement to protect e‑PHI) and contractual SLAs with clients. A risk register tracks each vulnerability, its severity, owner and target remediation date.
2) Linking Findings to Risk Treatment Plans
Each penetration test finding should map back to the risk treatment plan. This linkage shows auditors and buyers that you are treating risks systematically. For example, if a test discovers an insecure API endpoint, the risk treatment plan might include implementing authentication, updating secure coding guidelines and performing code reviews. Updating the Statement of Applicability (SoA) ensures that controls selected to address the risk are documented.
3) Tracking Remediation and Verification
Remediation should follow a structured process: assign an owner, set a deadline, implement the fix, retest to confirm the vulnerability is closed and update documentation. Evidence of remediation—such as patches applied, configuration changes or code updates—should be stored with the penetration testing report. For high‑risk findings, verify that the fix eliminates the root cause rather than only the symptom. Many enterprises fail audits because they cannot show evidence of retesting.
4) Showing Improvement Over Time
Continuous improvement is at the heart of ISO 27001. By tracking metrics such as the number of high‑severity findings, average remediation time and recurrence of previously fixed issues, organizations can measure progress. A downward trend in high‑risk findings and faster remediation demonstrates maturity. Sharing these metrics with stakeholders builds confidence that security investments translate into tangible risk reduction.
Documentation Requirements for ISO 27001
What Auditors Expect to See
Auditors look for a clear chain of evidence that connects risk assessment, control implementation, testing and improvement. For penetration testing, they typically request:
- Penetration Testing Policy – A document defining why, when and how testing is conducted, who approves scopes and how results are handled.
- Scope and Rules of Engagement – Evidence that tests were planned and approved, including targets, constraints and exclusion zones.
- Penetration Test Report – A report detailing methodology, findings, risk ratings and remediation recommendations.
- Remediation Tracking – Records of actions taken to address findings, evidence of retesting and closure dates.
- Risk Register and SoA Updates – Evidence that test results were integrated into risk management and that controls were updated.
Lack of any of these documents can delay or jeopardize certification. Auditors also expect that sensitive information is redacted in deliverables provided to third parties.
How Penetration Testing Supports Data Protection Claims
For frameworks like HIPAA, organizations must protect e‑PHI by implementing administrative, physical and technical safeguards. The HHS guidance stresses that a risk analysis is the first step in identifying and implementing safeguards. Penetration testing provides evidence that technical safeguards work and that vulnerabilities are promptly addressed. When clients ask whether you can protect personal data, showing recent penetration tests and remediation records supports your claims.
Common Documentation Gaps That Cause Audit Issues
Common pitfalls include outdated policies, incomplete scope documents, missing approval signatures, and failing to update the risk register after testing. Some organizations keep test results in isolation rather than feeding them back into the ISMS. Others treat penetration test reports as confidential and refuse to share even high‑level summaries with auditors or customers. These gaps undermine trust. Establishing a documented process that integrates penetration testing with risk management avoids last‑minute scrambling.
ISO 27001 Penetration Testing Templates
Organizations often struggle to organise testing evidence. The following templates can streamline your program:
- Penetration Testing Policy Template – Defines objectives, roles, testing frequency and approval workflows. This ensures consistency across tests and sets expectations for internal and third‑party teams.
- Scope Document Template – Captures assets, constraints, test types (e.g., black‑box, white‑box), timing and escalation procedures. Having a template reduces scoping errors and ensures that critical systems are included.
- Risk Assessment Linkage Template – Provides a table linking each finding to risk categories, likelihood, impact and chosen treatment actions. This helps auditors verify that risks are managed systematically.
- Penetration Test Report Template – Standardizes how findings are documented, including methodology, proof of exploitation and remediation recommendations. A consistent format makes it easier for stakeholders to review results.
- Remediation Tracking Template – Tracks status, owner, due dates and verification results for each finding. It also records evidence of closure, making audit preparation more efficient.
By using standardized templates, you reduce the chance of missing key information and ensure that evidence is ready when needed.
Common Mistakes Companies Make
1) Treating Penetration Testing as a Checkbox
Many organizations schedule a penetration test solely to satisfy a questionnaire, then ignore the results. Treating testing as a checkbox robs you of its value. Without remediation and retesting, vulnerabilities remain. Enterprise clients can sense when testing is superficial; they ask for remediation evidence and may decline to work with vendors who treat security as an afterthought.
2) Using Outdated Reports
Penetration test reports lose relevance quickly as systems change. Submitting a report that is more than twelve months old often prompts follow‑up questions or rejection. Testing should align with the observation period for SOC 2 Type II (typically six to twelve months) and the ISO surveillance audit cycle (every twelve months). If significant changes occur between tests, schedule targeted assessments to keep evidence current.
3) Poor Scoping That Misses Real Risk
Scoping errors can render a test meaningless. Excluding critical systems or data flows from scope leaves major risks untested. Overly narrow scopes may pass audits on paper but fail during incidents. Conversely, excessively broad scopes can overwhelm testers and dilute focus. Collaborate with experienced professionals to define a scope that balances depth and breadth, and update it as your environment evolves.
4) Missing Links Between Findings and Security Controls
Penetration test findings must connect to specific controls. Failing to map findings to controls makes it hard to understand why the vulnerability exists and how to fix it. It also prevents auditors from assessing whether controls are effective. At Konfirmity, we map each finding to ISO 27001 controls and cross‑map to SOC 2 Trust Services Criteria, HIPAA safeguards and GDPR articles when applicable. This integrated approach helps clients respond to multi‑framework audits more efficiently.
How Enterprise Buyers Review Penetration Testing Evidence
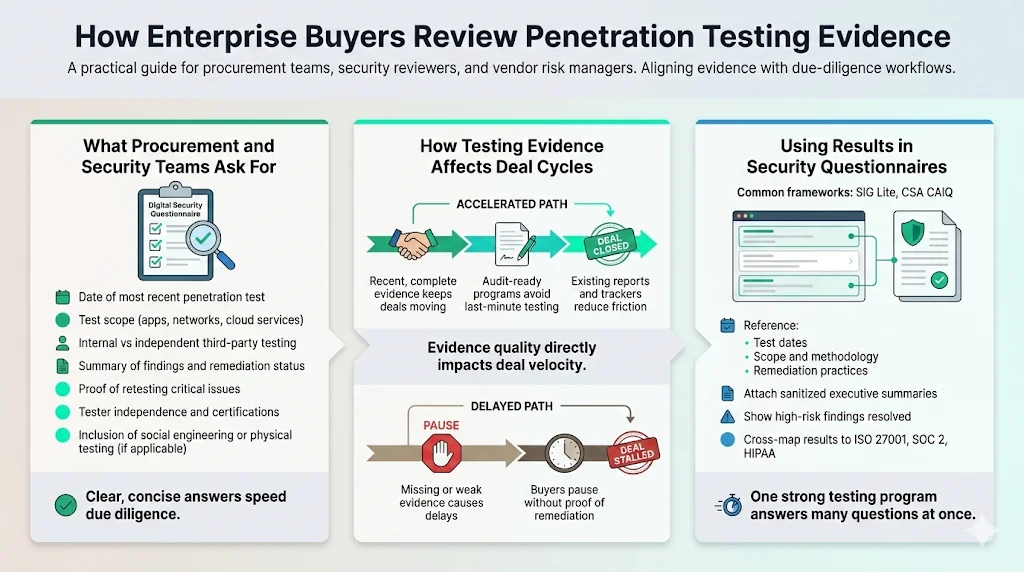
What Procurement and Security Teams Ask For
Buyers typically request: the date of the last ISO 27001 Penetration Testing exercise; the scope (applications, networks, cloud services); whether the test was internal or performed by a third party; high‑level findings and their remediation status; and proof that critical vulnerabilities were retested. Some buyers also request the tester’s certifications (e.g., OSCP, CREST) and independence. They may ask whether social engineering or physical testing was included. Providing concise yet informative responses speeds due diligence.
How Penetration Testing Affects Deal Cycles
Strong security evidence accelerates deals. Many enterprises will not proceed to contract without a recent penetration test and evidence of remediation. Weak or missing evidence can add weeks to the procurement cycle. Konfirmity clients often report shorter sales cycles because our managed service maintains audit‑ready evidence; they do not scramble to conduct a test when a deal lands. Instead, they provide the existing report, remediation tracker and risk register updates.
Using Testing Results During Security Questionnaires
Security questionnaires, such as SIG Lite or CSA CAIQ, often contain sections on vulnerability management and penetration testing. By referencing your testing program—dates, scope, methodologies, and remediation practices—you answer many questions directly. Attaching a sanitized executive summary of your penetration test and a list of remediated high‑risk findings gives reviewers confidence that security is part of daily operations. If your program covers multiple frameworks (ISO 27001, SOC 2, HIPAA), cross‑mapping results show that controls support diverse obligations.
Preparing for an ISO 27001 Audit With Penetration Testing
Pre‑Audit Checks
Before the audit, confirm that your penetration testing policy, scope documents, reports and remediation evidence are up to date. Verify that high‑risk findings have been remediated and retested. Ensure that the risk register and Statement of Applicability reflect the current state. Use a checklist to confirm that each control related to penetration testing (e.g., A.8.8, A.5.25) has evidence.
Evidence Packaging
Prepare a package containing: the penetration testing policy; the most recent scope document with approvals; the penetration test report; the remediation tracker; and updated risk register entries. Redact sensitive information, such as proof‑of‑concept exploit code or credentials, while keeping enough detail to demonstrate exploitation. Include a cover sheet mapping each document to ISO clauses and Annex A controls. Label each file clearly so auditors can locate evidence quickly.
Answering Auditor Questions With Confidence
Auditors may ask why certain assets were in or out of scope, why the test used a particular methodology, or how severity ratings were determined. They may probe how you ensured tester independence. Prepare answers that reference your policy and risk assessment; explain that high‑risk systems were prioritized and that testing methods align with NIST SP 800‑115 guidelines. If the test was internal, explain segregation of duties. When asked about remediation, show the tracker with closure dates and evidence. Confidence comes from being able to trace every step from risk assessment to remediation.
Conclusion
ISO 27001 Penetration Testing is not just a compliance exercise—it builds trust with enterprise clients and reduces the risk of costly breaches. The ISO standard guides you to establish an ISMS and continually improve it; penetration testing validates that your controls work. NIST’s four‑stage methodology provides a structured approach, while the difference between vulnerability assessments and penetration tests reminds us that both are needed. In an era where data breaches still cost millions and regulators demand evidence of protection, a human‑led managed service offers lasting value. At Konfirmity, our experts build and operate the program for you, handle 6,000+ audits with a combined 25 years of expertise, and reduce internal effort from hundreds of hours to around 75 hours per year. Security that looks good on paper but fails under attack is a liability. Build controls that withstand buyers, auditors and attackers—and let compliance follow.
FAQ: ISO 27001 Penetration Testing
1. What Is ISO 27001 Penetration Testing?
ISO 27001 Penetration Testing refers to a risk‑based testing approach performed within an ISMS. It simulates real attacks against in‑scope assets to validate whether controls effectively protect confidentiality, integrity and availability. The test is designed based on risk assessments, follows a documented methodology (often aligned with NIST SP 800‑115) and feeds results into the ISMS for continual improvement.
2. Is Penetration Testing Required for ISO 27001 Certification?
The ISO 27001 standard does not explicitly mandate penetration testing. However, it requires organizations to manage risks and ensure that controls are effective. Penetration testing is a recognised way to provide evidence of control effectiveness and risk treatment. Most certification auditors expect to see penetration testing as part of a risk‑based vulnerability management program, especially for organisations handling sensitive data or selling to enterprise clients.
3. How Often Should Penetration Testing Be Done for ISO 27001?
Testing frequency should be determined by risk. Critical systems may require testing every six to twelve months, while lower‑risk systems may be tested annually or after major changes. NIST advises establishing an assessment policy that defines frequency. In practice, aligning penetration testing with risk assessment updates and change‑management processes ensures timely evidence.
4. Do Auditors Review Penetration Test Reports?
Yes. Auditors typically request the latest penetration test report, scope document, remediation tracker and evidence of retesting. They review whether the test was sufficiently comprehensive, whether findings were rated and remediated, and whether results were integrated into the risk management process. They may not need to see raw technical details but will expect to see proof of exploitation and closure of high‑risk findings.
5. Can Internal Teams Perform Penetration Testing?
Internal teams can perform penetration testing if they have the necessary skills and operate independently from development and operations. However, enterprise buyers often prefer third‑party tests for objectivity. Third‑party testers bring specialised tools and experience, and their reports carry more weight during audits and procurement. If you use internal teams, ensure segregation of duties and validate methodologies against NIST guidelines.
6. How Detailed Should Penetration Testing Documentation Be?
Documentation should be detailed enough to demonstrate methodology, findings and remediation without exposing sensitive exploit details. Reports should describe the scope, techniques and results clearly. Risk ratings should be explained, and remediation recommendations should be actionable. Supplementary evidence—screenshots, logs and proof‑of‑concept commands—should be stored securely and referenced in the report. Auditors need enough detail to verify that testing was performed thoroughly and that findings were addressed.




.svg)





.svg)
.svg)