In the current enterprise market, trust is not a sentiment; it is a contractual obligation. If you are selling to enterprise clients, you have likely faced the "security roadblock." The deal is moving forward, the product demo went perfectly, and then procurement hits the brakes. They demand a SOC 2 Type II report.
But they don't just want to see a badge on your footer. With the global average cost of a data breach reaching $4.88 million according to IBM’s 2025 Cost of a Data Breach Report, sophisticated buyers in 2026 are drilling down into the details of your report. They are looking for evidence of rigorous security practices, not just policy documents. This is where SOC 2 Penetration Testing becomes the deciding factor between a signed contract and a stalled deal.
SOC 2 Penetration Testing is an authorized, simulated cyberattack on your computer system, performed to evaluate the security of the system. Unlike a vulnerability scan, which identifies potential open doors, a penetration test attempts to walk through those doors to see how far an attacker can get.
For technical leaders and founders, understanding the distinction between "checking a box" and actual risk management is critical. Penetration testing is not merely an audit requirement; it is the primary mechanism to validate that your controls actually function when under pressure.
At Konfirmity, having supported over 6,000 audits across 25+ years of combined expertise, we see a clear pattern: companies that treat penetration testing as a core engineering discipline move through security reviews 3x faster than those who treat it as an annual annoyance.
What Is SOC 2 Penetration Testing?
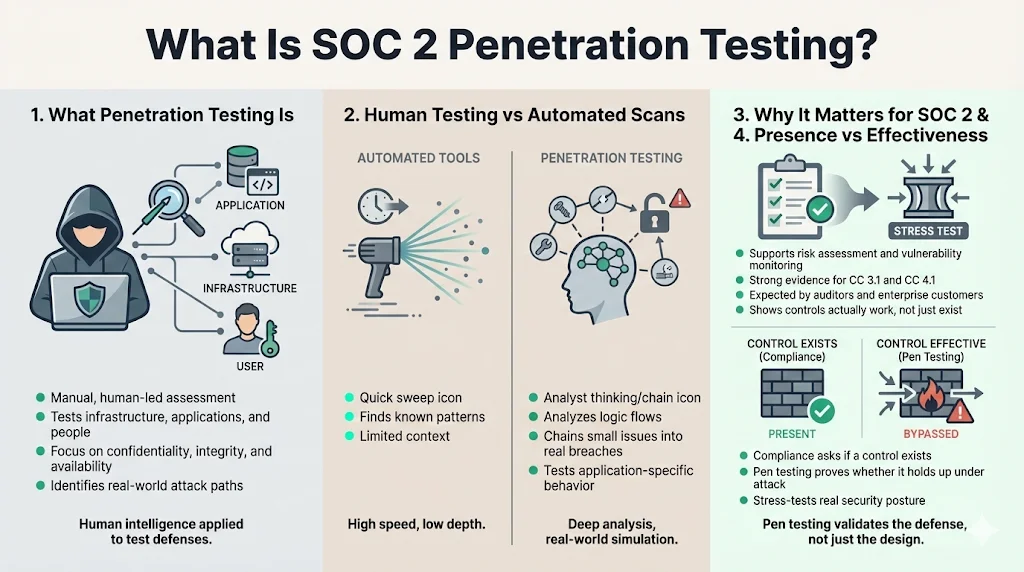
At its core, SOC 2 Penetration Testing is a manual, human-led assessment where ethical hackers attempt to exploit vulnerabilities in your infrastructure, applications, and people. The goal is to identify security weaknesses that an attacker could exploit to compromise the confidentiality, integrity, or availability of your data.
While automated tools are useful for quick sweeps, a penetration test involves critical thinking. A human tester analyzes logic flows, chains minor vulnerabilities together to create a major breach, and tests the resilience of your specific application logic.
Why Organizations Include It in SOC 2 Preparation
Technically, the AICPA (American Institute of Certified Public Accountants) does not explicitly write "You must perform a penetration test" in the Trust Services Criteria. However, they do require you to assess and manage risks (CC 3.1) and monitor your system for vulnerabilities (CC 4.1).
In practice, auditors view penetration testing as the gold standard of evidence for these criteria. In addition, if you are a SaaS provider processing sensitive data, your enterprise customers will almost certainly refuse to accept a SOC 2 report that excludes penetration testing. It signals that your security posture has never been stress-tested.
The distinction matters because compliance checklists often rely on the presence of a control (e.g., "Do you have a firewall?"). Penetration testing verifies the effectiveness of that control (e.g., "Can we bypass your firewall rules to access the database?").
SOC 2 Basics You Need to Know
To understand where testing fits, you must understand the framework. SOC 2 is based on the AICPA's Trust Services Criteria (TSC). There are five categories:
- Security (Common Criteria): The only mandatory category. It requires systems to be protected against unauthorized access.
- Availability: The system is available for operation and use as committed or agreed.
- Processing Integrity: System processing is complete, valid, accurate, timely, and authorized.
- Confidentiality: Information designated as confidential is protected.
- Privacy: Personal information is collected, used, retained, disclosed, and disposed of in conformity with commitments.
The "Required" vs. "Expected" Dynamic
Many founders ask me, "Amit, is this strictly mandatory?"
Here is the reality from the field: While the standard offers flexibility, the market does not. If you present a SOC 2 report to a Fortune 500 buyer without a recent penetration test, their Third-Party Risk Management (TPRM) team will flag you as "High Risk."
Auditors expect penetration testing because it serves as independent validation. It proves that management is not just writing policies but is actively testing the defenses defined in those policies. It validates your Change Management, Access Control, and System Operations controls in one go.
Penetration Testing vs. Vulnerability Scanning
One of the most frequent errors we see involves companies confusing vulnerability scans with penetration tests. They are not interchangeable.
Use Cases in a SOC 2 Context
- Vulnerability Scans: Use these to satisfy continuous monitoring requirements (CC 4.1). You should run these weekly or monthly and integrate them into your CI/CD pipeline.
- Penetration Tests: Use these to validate the entire security model annually or after significant infrastructure changes. This provides the "point-in-time" assurance auditors need for your Type II observation period.
You cannot rely on scanning alone. A scanner will not find business logic errors, such as a flaw allowing a user to see another tenant's data by changing an ID in the URL. Only a human performing SOC 2 Penetration Testing will catch that.
How SOC 2 Penetration Testing Works
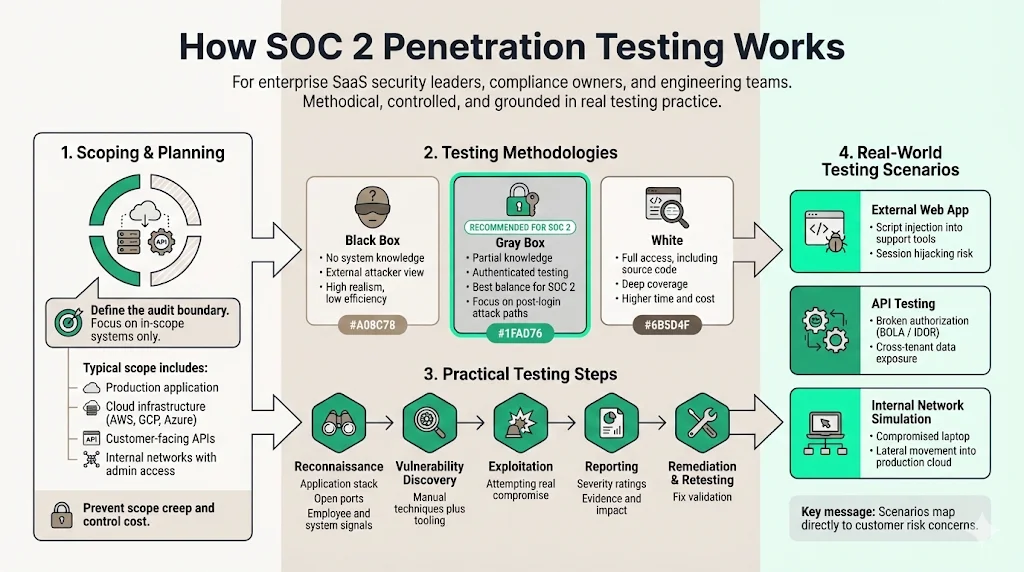
Effective testing requires structure. At Konfirmity, we manage this process so it delivers results without disrupting your engineering velocity.
Scoping and Planning
The first step is defining the "Audit Boundary." You do not need to test every server you own; you need to test the systems that are in scope for your SOC 2 audit. This usually includes:
- Your production application.
- The cloud infrastructure hosting it (AWS, GCP, Azure).
- APIs used by customers.
- Internal networks that have administrative access to production.
Proper scoping prevents scope creep and controls costs. It ensures the test focuses on the assets that matter most to your auditors and customers.
Testing Methodologies
There are three primary approaches to testing:
- Black Box: The tester has no prior knowledge of the system. They attack as an outsider. While realistic, this is inefficient for SOC 2 because the tester spends too much time on reconnaissance.
- Gray Box: The tester has partial knowledge (e.g., user credentials, architecture diagrams). This is the standard for SOC 2. It allows the tester to assess what happens after a user logs in (authenticated testing), which is where 80% of web application attacks occur according to the Verizon Data Breach Investigations Report (DBIR).
- White Box: The tester has full access, including source code. This is thorough but time-consuming.
For most enterprise SaaS companies, Gray Box is the most effective balance of depth and efficiency.
Practical Steps
- Reconnaissance: The tester gathers intelligence on your application stack, open ports, and employee data.
- Vulnerability Discovery: Using manual techniques and tools to find potential entry points.
- Exploitation: The distinct phase where the tester attempts to compromise the system using the found vulnerabilities.
- Reporting: Documentation of the findings, including severity levels (Critical, High, Medium, Low) and evidence.
- Remediation & Retesting: Your team fixes the issues, and the tester verifies the fixes.
Examples
- External Web App Test: A tester finds they can inject malicious scripts (XSS) into a support chat widget, allowing them to steal session cookies from your support agents.
- API Testing: A tester discovers an API endpoint that lacks proper authorization checks (BOLA/IDOR), a consistent leader in the OWASP API Security Top 10. This allows them to download user data belonging to other companies.
- Internal Network Simulation: A tester simulates a compromised developer laptop and attempts to pivot from the corporate network into the production AWS environment.
These scenarios map directly to the risks your customers worry about.
Penetration Testing and SOC 2 Controls
The output of a pen test maps directly to specific Trust Services Criteria.
- Security (CC 6.1 - External Threats): The test provides evidence that you are actively identifying and managing external threats.
- Confidentiality (C 1.1 - Identification of Confidential Information): If a tester can exfiltrate data, your controls for identifying and protecting confidential info are failing.
- Availability (A 1.2 - Environmental Threats): While pen tests don't usually run full DDoS attacks (to avoid downtime), they identify architectural weaknesses that could lead to outages under stress.
Auditors look for the "clean report" or the "remediation report." If your initial test has critical findings, that is acceptable provided you fix them and get a re-test showing they are closed. This demonstrates the control of "Remediation" is functioning.
Best Practices for Busy Teams
We know engineering resources are scarce. You cannot afford to halt product development for weeks to support a test.
- Schedule Smart: Do not schedule the test for the last week of your audit observation period. Recent industry data suggests the Mean Time to Remediate (MTTR) for critical vulnerabilities can exceed 60 days in unmanaged environments. If you find a critical issue, you need time to fix it before the audit window closes. Ideally, conduct the test 2–3 months before the end of your period.
- Use Automated Tools for Maintenance: Let scanners handle the low-hanging fruit (outdated libraries, SSL issues) so the expensive human testers can focus on complex logic.
- Prioritize High-Risk Systems: If you have a microservices architecture, focus the deep testing on the services that handle PII or ePHI.
- Documentation is Critical: The final report needs to be technical enough for engineers to fix issues but clear enough for auditors to understand the risk was managed.
At Konfirmity, we treat this as a managed service. We don't just throw a report over the fence; we help you integrate the fixes into your sprint cycles.
Choosing the Right Testing Partner
This is a decision that impacts your security and your budget.
What to look for:
- Certifications: Look for OSCP, CREST, or CISSP certified testers.
- SOC 2 Experience: Do they understand the specific evidence auditors need? A generic pen test might miss the nuances required for a Type II report.
- Remediation Support: Will they help you understand how to fix the findings?
Internal vs. External: You generally cannot use your own employees for the official SOC 2 Penetration Testing. Auditors require independence. Even if your internal security team is brilliant, they grade their own homework. You need an objective third party to satisfy the independence requirement of the audit.
Engineering, Security, and Governance Workflows
The days of emailing a PDF report are over. Modern security demands integration.
- Integration: Findings from the pen test should flow directly into your issue tracker (Jira, Linear, Asana).
- SLA Tracking: Assign an SLA to each finding based on severity (e.g., Criticals fixed in 48 hours, Highs in 14 days). This is a metric auditors love to see.
- Collaboration: Security and Engineering must collaborate on the fixes. Often, a "fix" for a security flaw can break functionality. Ongoing dialogue is essential.
At Konfirmity, our platform acts as the connective tissue, tracking these remediation timelines so you have a verified audit trail ready for the auditor.
Common Mistakes to Avoid
In our experience helping companies through thousands of audits, we see the same stumbling blocks:
- The "Scan is Enough" Fallacy: Relying solely on automated vulnerability scans. Auditors will reject this as insufficient for high-risk environments.
- Testing Outside the Window: Performing the test the day after your audit period ends. This means the evidence doesn't count for the current audit year.
- Ignoring the "Low" Findings: While you must fix Criticals and Highs, a long list of ignored "Low" findings suggests a lack of rigorous security hygiene.
- No Retest: Fixing the bugs but failing to bring the tester back to verify the fix. You need that final "Clean" report.
Measuring Success
How do you know if your program is working? Track these metrics:
- Vulnerability Density: The number of valid findings per asset or line of code. This should decrease year over year.
- Mean Time to Remediate (MTTR): How fast are you closing the holes once found?
- Repeat Findings: Are the same issues popping up in every annual test? If so, your root cause analysis is failing.
- Pre-Audit Fix Rate: Percentage of critical findings resolved before the auditor arrives.
Conclusion
Security is not a state you achieve; it is a habit you practice. SOC 2 Penetration Testing is the rigorous exercise that keeps that habit sharp.
While the upfront cost and effort might seem high, the cost of a breach—or a lost enterprise contract—is exponentially higher. By integrating penetration testing into your annual compliance lifecycle, you do more than satisfy an auditor. You prove to your customers that you respect their data enough to attack your own defenses.
We established Konfirmity because we saw too many companies struggling to stitch together disparate tools and consultants. We believe in an outcome-based approach where security controls are implemented, managed, and verified by experts. We don't just advise—we execute.
Frequently Asked Questions
Q1: Is SOC 2 penetration testing a mandatory requirement?
Strictly speaking, the AICPA Trust Services Criteria do not mandate it by name. However, it is the standard method for satisfying the requirement to assess vulnerabilities and managing risks. Without it, most auditors will not sign off on a Type II report for a technology company, and enterprise buyers will likely reject your security packet.
Q2: How often should pen testing be done?
Typically, organizations perform SOC 2 Penetration Testing annually. Additionally, you should conduct a test after any significant change to your system architecture or major release. This ensures your control environment remains valid after changes.
Q3: How is a penetration test different from a vulnerability scan?
A vulnerability scan is an automated search for known issues, like checking if doors are unlocked. A penetration test is a manual, human-driven attempt to exploit those issues to gain access, like actually picking the lock and entering the room. Auditors value the test because it proves real-world risk exposure.
Q4: What should be included in a pen test report for SOC 2?
The report must include the scope of the test (what was tested), the methodology used, a summary of findings categorized by severity, detailed technical evidence of the exploits, and, crucially, a section on remediation (or a separate retest report) showing that the issues were resolved.
Q5: Can I use internal staff to perform SOC 2 penetration testing?
Generally, no. While internal testing is great for continuous improvement, SOC 2 requires independence. An external firm provides an unbiased view that internal staff cannot offer. Using internal staff for the official audit evidence is usually flagged as a conflict of interest by auditors.





.svg)




.svg)
.svg)