Most enterprise buyers now demand concrete security evidence before procurement. Without operational security and continuous evidence, deals stall—even when engineering teams believe they are “ready” on paper. In 2025 the pressure has intensified: European regulators are increasing fines and enforcement, and recent data breach reports show that average breach costs remain painfully high. IBM’s 2024 Cost of a Data Breach report found the global average breach hit USD 4.88 million, while the 2025 edition noted that the average dropped to USD 4.44 million, mainly due to faster detection and containment. At the same time, the Dutch DPA imposed a €4.75 million fine on an online streaming service for unclear privacy notices and a €290 million penalty on a ride‑sharing app for improper data transfers. These figures underscore why a GDPR Readiness Guide matters: the cost of getting privacy wrong is rising, and enterprise clients will not do business with vendors who put them at regulatory risk.
This article outlines practical steps for companies selling to enterprise clients. It demystifies core GDPR concepts, shares templates that accelerate readiness, and explains how a human‑led managed service like Konfirmity builds durable programs rather than short‑term compliance paperwork. With over 6,000 audits delivered and 25+ years of combined expertise, our team has seen the pitfalls and knows how to build controls that stand up to buyers, auditors and attackers. We map controls across frameworks (GDPR, SOC 2, ISO 27001, HIPAA) and run programs year‑round so you can start with security and arrive at compliance.
What GDPR Readiness Means
Readiness differs from simple preparation or checklist exercises. It is the deep understanding of legal obligations and operational demands before implementation. Preparation involves gathering documents, while ongoing compliance means demonstrating that controls operate consistently over time. Readiness is the foundation for both—it ensures you know what to implement and why. The General Data Protection Regulation applies to organisations processing personal data of individuals located in the European Union, regardless of where the organisation is established. Even companies outside the EU that offer goods or services to EU residents must comply. Enterprise buyers therefore ask vendors around the world to prove readiness through data protection agreements and detailed questionnaires.
Understanding readiness also requires recognising GDPR’s broad territorial reach and its interconnection with other frameworks. The regulation mandates lawfulness, transparency, data minimisation, integrity and confidentiality. Article 6 enumerates lawful bases for processing, including consent, contract, legal obligation, vital interests, public interest and legitimate interests. Article 7 clarifies that consent must be clearly distinguishable, easily withdrawn and not tied to unrelated services. Article 33 imposes a 72‑hour breach notification requirement. Awareness of these provisions is the cornerstone of readiness.
Step‑by‑Step GDPR Readiness Checklist
A solid GDPR Readiness Guide breaks down requirements into actionable tasks. Below is a structured checklist based on regulatory sources, industry standards, and patterns observed across Konfirmity’s 6,000+ audits.

1. Data Inventory and Mapping
You cannot protect or justify data processing if you do not know what data you hold. Start by creating an inventory of personal data. Identify data subjects (customers, employees, vendors), categories of personal data (contact details, financial records, health information), storage locations (databases, SaaS platforms, backups) and data flows (between systems, third parties, and across borders). The EDPB’s 2024 coordinated enforcement action involved over 1,185 controllers and revealed that many lacked internal procedures and could not identify the data involved in subject access requests. Data mapping addresses this gap and underpins all subsequent controls.
A simple data inventory template might include fields such as:
Create this inventory across departments and update it regularly. Use it to drive data minimisation: only collect data that is necessary and purge data according to retention schedules. The EDPB’s report noted that lack of documented procedures and retention policies creates regulatory exposure.
2. Understanding and Documenting Legal Bases
GDPR requires every processing activity to have a lawful basis. Article 6 lists six possibilities: consent, contract, legal obligation, vital interests, public interest/official authority, and legitimate interests. Most enterprise workflows rely on a combination of contract (for delivering services), legal obligation (e.g., payroll records), and legitimate interests (analytics, fraud prevention). Consent is appropriate when individuals must voluntarily agree, but it is not always necessary or recommended.
Document each processing activity and map it to a lawful basis. If the lawful basis is legitimate interests, conduct a balancing test to confirm that your interests are not overridden by the rights of individuals. A legal basis decision matrix can help:
This matrix should link to your data inventory. It ensures that you know why you hold each data element and helps defend your practices if challenged by regulators or clients.
3. Consent Management
Consent must be meaningful, informed and revocable. Article 7 requires controllers to be able to demonstrate that the data subject consented. Consent requests must be presented clearly and separately from other terms. Subjects must be told that they can withdraw consent as easily as they gave it.
Assess your existing consent mechanisms. Are you using pre‑ticked boxes or bundled consents? These practices violate GDPR. Instead, implement explicit opt‑in mechanisms with clear descriptions of purpose and retention. Keep records of when consent was obtained, for what purpose and by which method. Monitor expiry dates and renew consent if purposes change. A consent management checklist can include:
Enterprise workflows often involve multiple systems (marketing automation, CRM, support platforms). Use a central consent registry to synchronise records and honour withdrawal across all downstream systems. Remember that consent may not be a fallback; for example, if you rely on legitimate interests for analytics, do not also seek consent for the same purpose as a backup.
4. Privacy Policy and Notices
Transparency is a core principle. Organisations must inform individuals about what personal data they collect, why they collect it, how long they keep it and who they share it with. The Dutch DPA’s €4.75 million fine against a streaming service in November 2024 highlights the consequences of vague or incomplete privacy notices. The DPA found that the company did not clearly explain purposes, legal bases, sharing arrangements, retention periods or security measures.
Draft a concise, audience‑focused privacy policy covering:
- Data collection: Describe what personal data you collect for each service.
- Lawful basis: Explain the legal basis for each processing activity.
- Purposes: Explain why you collect and use personal data, avoiding ambiguous language.
- Data sharing: Specify the categories of third parties with whom data is shared (e.g., cloud providers, payment processors, analytics services) and the safeguards in place.
- Retention: Provide information about how long data is kept and the criteria for determining retention.
- Data subject rights: Provide clear instructions on how individuals can exercise their rights (access, correction, deletion, etc.).
- Contact information: Provide contact details for the Data Protection Officer or privacy team.
The policy should be easy to read (use plain language and short sentences), available in languages relevant to your users, and aligned with your brand voice. For enterprise clients, consider providing a more detailed privacy notice in the contract or Data Processing Agreement (DPA) to satisfy due diligence requirements.
5. Data Subject Rights Readiness
GDPR grants individuals rights to access, rectify, erase, restrict processing, object and request portability of their data. The EDPB’s 2024 coordinated enforcement action found that many organisations lacked internal procedures for handling access requests. In 2025 the focus has shifted to the right to erasure.
To be ready:
- Designate responsible staff: Assign a privacy team or data protection officer to oversee requests and coordinate with legal and IT functions.
- Define request channels: Provide a dedicated email address or web form for subject access requests (SARs). Ensure that the mechanism verifies the requester’s identity without collecting unnecessary data.
- Document workflows: Create a standard operating procedure describing steps for logging requests, verifying identity, collecting data from systems, redacting third‑party information and communicating with the requester. Use a tracking form to document date received, due date (one month by default), responsible owner and status.
- Automate retrieval: Integrate systems (CRM, HR, ticketing, data warehouses) to retrieve personal data quickly. Use the inventory to locate data across systems.
- Train teams: Educate customer support, HR and IT teams about the importance of responding to requests. Make sure they know how to recognise a SAR and where to route it.
A response workflow and tracking form can include fields for request type (access, correction, deletion), date received, deadline, responsible owner, systems involved, actions taken, and date of response. This ensures accountability and helps demonstrate compliance if audited.
6. Security Measures and Technical Controls
Data protection is inseparable from security. Article 32 requires controllers to implement appropriate technical and organisational measures, considering the state of the art, implementation costs and the nature, scope and context of processing. The 2024 IBM report shows that 40% of breaches involved data stored across multiple environments. Breaches in multi‑cloud environments cost more than USD 5 million on average and take longer to contain. Organisations with AI‑powered security and automation saw their identification and containment time reduced by nearly 100 days.
Essential controls include:
- Access control: Implement least‑privilege access and role‑based permissions. Conduct periodic access reviews to remove unnecessary privileges.
- Encryption: Encrypt data in transit (TLS) and at rest. Use strong encryption for backups and portable media.
- Vulnerability management: Run regular vulnerability scans and penetration tests. Track remediation and enforce service‑level agreements for patching (e.g., 30 days for high‑risk vulnerabilities).
- Security monitoring: Deploy intrusion detection and logging. Collect logs from servers, applications and network devices, and store them centrally for analysis. Use automated alerting for anomalous behaviour.
- Incident response plan: Create documented procedures for detecting, containing and eradicating incidents. Align them with the breach notification requirements (see next section).
- Supply chain security: Evaluate third‑party vendors’ security. Ensure they have adequate controls and provide evidence (SOC 2, ISO 27001, or equivalent).
A security gap assessment template can include categories such as access control, network security, endpoint security, encryption, backup and recovery, incident response, and vendor management. For each category, record the current state, gaps, remediation tasks and responsible owner.
7. Data Breach Preparedness
Despite best efforts, breaches happen. GDPR Article 33 requires controllers to notify the supervisory authority within 72 hours of becoming aware of a personal data breach, unless the breach is unlikely to risk individuals’ rights. You must also notify affected individuals if the breach is likely to result in high risk.
Prepare a breach response plan that covers:
- Detection: Define how breaches are detected (security monitoring, user reports, vendor notifications). Include contact details for reporting suspected incidents.
- Triage and containment: Assign an incident response team. Assess the nature of the breach, contain the incident (e.g., isolate systems, revoke credentials) and prevent further exposure.
- Assessment: Determine the categories and approximate number of data subjects affected, the types of data involved, and likely consequences. Identify the legal basis and whether notification is required. Record facts and decisions.
- Notification: If required, notify the supervisory authority within 72 hours, describing the breach, its consequences and the measures taken to mitigate effects. If high risk to individuals, notify them promptly.
- Remediation: Address underlying weaknesses (patch vulnerabilities, update configurations, improve training). Document lessons learned and update procedures.
A data breach response template should include contact lists (internal stakeholders, legal counsel, regulators), decision criteria for notification, and communication scripts for authorities and data subjects.
8. Third‑Party Vendors and Data Processing Agreements
Enterprise companies often rely on third‑party service providers for hosting, analytics, payments and support. Under Article 28, controllers must ensure processors provide sufficient guarantees and process data according to written agreements. The Dutch DPA’s €290 million fine against a ride‑sharing app demonstrates the risk of inadequate transfer mechanisms: the company removed Standard Contractual Clauses (SCCs) from its data‑sharing agreements and was judged to lack appropriate safeguards.
Steps to manage third parties:
- Vendor inventory: Identify all vendors who process EU personal data on your behalf. Classify them by risk and data types processed.
- Due diligence: Assess each vendor’s security and privacy posture. Request their SOC 2, ISO 27001 or equivalent reports. Review their privacy policies and breach history.
- Data Processing Agreements (DPAs): Ensure you have signed DPAs with all processors. The DPA should specify processing instructions, security measures, breach notification obligations, subprocessor approval processes, assistance with data subject rights and audit rights.
- Transfer mechanisms: For transfers outside the EU, implement appropriate safeguards—SCCs, Binding Corporate Rules or adequacy decisions. Conduct transfer impact assessments to evaluate foreign law and government access risks.
- Monitoring and audits: Track vendor compliance. Require regular updates on certifications and breaches. Terminate or remediate when vendors do not meet obligations.
A DPA checklist might include sections for services provided, data categories, lawful basis, security requirements, breach notification timelines, rights and obligations, subprocessor approvals and audit rights.
9. Risk Assessment and Data Protection Impact Assessments (DPIAs)
Risk assessments help identify threats and vulnerabilities affecting personal data. GDPR requires DPIAs when processing is likely to result in a high risk to individuals (e.g., large‑scale monitoring, profiling, processing special categories of data, or systematic automated decision making). Conduct risk assessments early—prior to launching new products or features—and repeat them regularly or whenever processing changes.
A risk assessment process involves:
- Identify processing activities: Describe the purpose, scope, context and data involved.
- Assess necessity and proportionality: Evaluate whether data processing is necessary for the intended purpose and whether less intrusive methods exist.
- Identify risks: Consider risks to rights and freedoms (unauthorised access, discrimination, financial loss) and organisational risks (reputation, fines).
- Evaluate likelihood and impact: Score each risk on a scale (e.g., low, medium, high) and consider existing controls.
- Define mitigation measures: Plan security and privacy controls to reduce risk (encryption, pseudonymisation, access restrictions, transparency measures).
- Document and monitor: Record findings and integrate them into project plans. Monitor controls and update assessments when processing changes.
A DPIA scoring sheet could use a table with columns for risk description, likelihood (1–5), impact (1–5), inherent risk (likelihood × impact), existing controls, residual risk and action plan. This structured approach demonstrates systematic risk management.
10. Audit and Monitoring Readiness
Compliance is not a one‑time event. Ongoing monitoring and internal audits verify that controls operate as intended. For organisations certified under ISO 27001:2013, the transition to ISO 27001:2022 is underway. SGS, a leading certification body, notes that all ISO/IEC 27001:2013 certificates will expire by October 31 2025 and no new audits to the old standard will be conducted after April 30 2024. Certificates issued during the transition will expire on October 31 2025. The updated standard reduces the number of information security controls from 114 to 93 and introduces attributes and purposes for each control.
To be audit‑ready:
- Define scope and objectives: Determine which business units, systems and third parties are in scope. For complex enterprises, consider separate scopes for sales, marketing and product teams.
- Schedule internal audits: Plan periodic reviews (e.g., quarterly) to test controls. Use audit checklists aligned with your frameworks (GDPR, ISO 27001, SOC 2). Document evidence such as policies, logs, access reviews and incident reports.
- Document deviations and remediation: Track findings, assign owners and document remediation. Prove that corrective actions were implemented and monitored.
- Prepare for external audits: Compile evidence packages. For SOC 2 Type II, prepare for an observation period of typically six to twelve months. For ISO 27001, coordinate transition audits. For GDPR, be ready to demonstrate accountability (records of processing, DPIAs, policies, contracts).
- Continuous monitoring: Implement tools and processes to track control effectiveness year‑round. Use dashboards and automated alerts for vulnerabilities, access anomalies and policy violations.
An audit readiness checklist should include items such as documentation review, risk assessments, training records, vendor DPAs, incident logs, access reviews and board oversight evidence.
Putting It Into Practice: A Readiness Roadmap
A phased approach helps organisations prioritise tasks and allocate resources effectively. Below is a roadmap based on Konfirmity’s experience supporting thousands of audits. The timeline is indicative and varies by data volume, system complexity and available resources.
Short‑Term (0–3 Months)
- Executive buy‑in: Obtain commitment from leadership. Appoint a Data Protection Officer or privacy lead and assign a budget.
- Data inventory: Map data and establish lawful bases. Start with high‑risk departments (sales, marketing, HR).
- Risk assessment & DPIA triggers: Identify high‑risk processing activities and initiate DPIAs.
- Interim controls: Implement essential security measures: encryption, access control, basic incident response procedures.
- Draft privacy notices: Create or update privacy policies and internal procedures.
Mid‑Term (3–6 Months)
- Consent and rights workflows: Deploy consent management solutions. Implement subject rights workflows and training.
- Vendor management: Inventory processors, conduct due diligence and sign DPAs.
- Policy finalisation: Finalise privacy notices, data retention schedules, and security policies.
- Continuous monitoring: Deploy logging, vulnerability scanning and access review processes. Address gaps identified in risk assessments.
- Pilot audits: Conduct internal audit or readiness assessments. Address remediation tasks.
Long‑Term (>6 Months)
- External attestations: Undergo SOC 2 Type II or ISO 27001 certification to demonstrate compliance to clients. With Konfirmity’s managed service, typical SOC 2 readiness windows are 4–5 months versus 9–12 months for self‑managed programs.
- Observation and evidence collection: Maintain consistent operation of controls. For SOC 2 Type II, controls must be observed over 6–12 months. Document evidence such as change management tickets, access reviews and incident reports.
- Integration and automation: Integrate privacy and security controls into engineering pipelines (CI/CD), ticketing and HR systems. Automate evidence collection to reduce internal effort. Konfirmity reduces internal effort to around 75 hours per year compared with 550–600 hours for typical self‑managed programs.
- Board oversight and reporting: Provide regular reports to executives and the board. Demonstrate how controls reduce business risk and support revenue.
- Continuous improvement: Use audit findings, incidents and stakeholder feedback to improve policies and controls. Track regulatory updates (e.g., NIST Privacy Framework 1.1 draft update aligning with Cybersecurity Framework 2.0, including AI privacy risk guidance) and adjust your program accordingly.
Common GDPR Pitfalls and How to Avoid Them
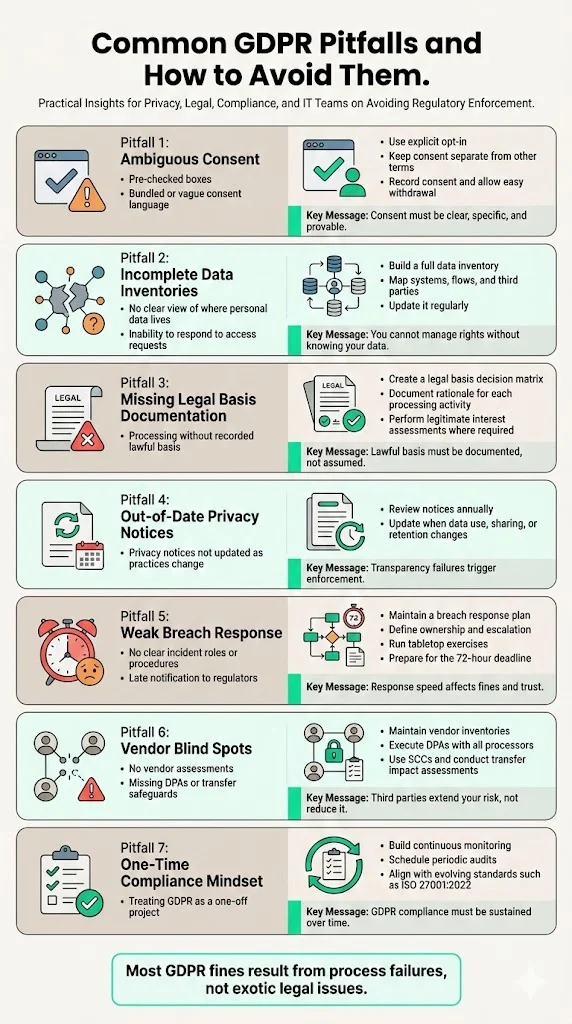
- Ambiguous consent: Collecting consent via pre‑checked boxes or broad statements fails GDPR. Use explicit opt‑in and keep records. Keep consent separate from other terms and provide easy withdrawal..
- Incomplete data inventories: Skipping data mapping leads to gaps. In the 2024 enforcement action, many controllers lacked documented procedures and could not locate data when handling access requests. Build and maintain the inventory.
- Missing legal basis documentation: Processing data without documenting the lawful basis exposes you to fines. Create a decision matrix and conduct legitimate interest assessments when needed.
- Out‑of‑date privacy notices: The streaming service fined €4.75 million failed to update its privacy statement for five years. Review privacy notices annually or whenever practices change.
- Weak breach response: Lacking a structured breach response plan can lead to late notifications and higher fines. Practise simulations, define roles and ensure you can meet the 72‑hour notification requirement.
- Vendor blind spots: Failing to assess third‑party processors can be catastrophic. The ride‑sharing app’s €290 million fine came from inadequate safeguards and removal of SCCs. Maintain vendor inventories, DPAs and transfer impact assessments.
- One‑time compliance mindset: Treating GDPR as a project rather than a program leads to stale evidence. Build continuous monitoring and schedule periodic audits. Remember that ISO 27001:2013 certificates will expire by October 2025 and the updated standard has fewer controls.
Templates and Tools Summary
For quick reference, here is a list of templates mentioned in this GDPR Readiness Guide:
- Data inventory sheet: Fields for data type, source, purpose, retention, risk level and location.
- Legal basis decision matrix: Lists processing activities, lawful bases and rationale.
- Consent tracking form: Records consent mechanism, purpose, date, withdrawal option and record location.
- Privacy policy outline: Covers data collected, legal bases, purposes, sharing, retention, rights and contact information.
- Data subject rights (DSAR) workflow form: Tracks request type, received date, owner, systems, actions and response date.
- IT security gap assessment: Evaluates access control, encryption, vulnerability management, monitoring, incident response and vendor management.
- Data breach response plan: Steps for detection, containment, assessment, notification and remediation; includes contact lists and decision criteria.
- Vendor and DPA checklist: Tracks vendor names, services provided, data categories, contract status, safeguards and audit rights.
- Risk assessment and DPIA sheet: Includes risk description, likelihood, impact, inherent risk, existing controls, residual risk and action plan.
- Audit readiness checklist: Ensures documentation, risk assessments, training records, DPAs, incident logs, access reviews and board oversight are in place.
Conclusion
GDPR readiness is not about ticking boxes; it is about understanding obligations, designing controls into your operations and maintaining trust with enterprise customers. With data breaches costing millions and regulators imposing record fines, proactive readiness becomes a business imperative. By building a data inventory, establishing lawful bases, managing consent, drafting clear privacy notices, preparing for data subject rights, implementing strong security controls, planning for breaches, managing third‑party risk, performing DPIAs and maintaining continuous audit readiness, organisations can reduce risk and strengthen customer trust.
As Amit Gupta, founder of Konfirmity, I have helped hundreds of engineering teams transition from compliance manufacturing to true security. Our human‑led managed service executes controls inside your stack, runs continuous monitoring and keeps you audit‑ready year‑round. Security that looks good in documents but fails under incident pressure is a liability. Build the program once, operate it daily and let compliance follow. This GDPR Readiness Guide offers a path to doing just that.
FAQs
1. What is GDPR readiness?
Readiness refers to the state of understanding and planning for GDPR obligations before implementation. It involves mapping data, documenting lawful bases, preparing processes and policies, and establishing security measures. It differs from compliance (ongoing evidence that controls operate effectively).
2. Who needs to be GDPR ready?
Any organisation that processes personal data of EU residents must be ready, even if the organisation is based outside the EU. Companies selling to enterprise clients globally will face GDPR clauses in procurement contracts.
3. What’s the difference between GDPR readiness and compliance?
Readiness is the preparatory work—understanding obligations, creating inventories, drafting policies and designing controls. Compliance is the execution and demonstration of those controls over time, including continuous monitoring, evidence collection and external audits.
4. How long does GDPR readiness take?
It depends on data volume, system complexity and resources. With a human‑led managed service like Konfirmity, readiness typically takes 4–5 months for organisations with moderate complexity. Self‑managed programs may take 9–12 months due to the need to build expertise, map data and implement controls.
5. Do all third‑party vendors need DPAs?
Yes. Under Article 28, any processor handling EU personal data on your behalf must agree to written data processing terms. DPAs define processing instructions, security requirements, breach notification obligations and audit rights.
6. What personal data counts under GDPR?
Personal data includes any information relating to an identified or identifiable person. This covers obvious identifiers (name, email, ID numbers) and extends to online identifiers (IP addresses, device IDs), location data, financial data, health information and any combination of data that can indirectly identify a person.





.svg)






.svg)
.svg)