Most companies selling into enterprise or regulated verticals know that procurement gates often ask for proof of data protection. Major buyers in Europe and beyond now require evidence that vendors can handle personal data lawfully and securely. In 2025, the EU General Data Protection Regulation (GDPR) remains one of the world’s toughest privacy laws, and its applicability extends well beyond the EU. If your product touches the data of an EU citizen—whether you operate a U.S. SaaS company or a global enterprise—you’re expected to meet GDPR’s requirements.
This article explains GDPR roles and responsibilities from the perspective of teams selling to enterprises. We’ll break down what it means to be a controller, processor or Data Protection Officer (DPO), show how the regulation’s seven principles drive operational demands and share practical steps drawn from Konfirmity’s experience supporting over 6,000 audits. Along the way we’ll reference guidance from regulators and frameworks like SOC 2, ISO 27001 and HIPAA to illustrate how data protection programs are built.
By the end of this guide you’ll know how to map data flows, assign clear responsibilities, implement controls and respond to customer and regulator questions. Whether you’re a CTO, CISO or compliance lead, you’ll leave with checklists, templates and examples to help your team stay audit‑ready.
Key Concepts & Who’s Who: Data Controller, Data Processor, Data Protection Officer and More
1) Data controller
The GDPR defines a controller as the entity that determines the purposes and means of processing personal data. In practice, that’s the organization deciding why data is collected and how it will be used. Controllers often include software vendors handling user registration, HR departments managing employee data, or marketing teams capturing leads. Responsibilities for controllers extend beyond simply choosing a legal basis; they must ensure processing is lawful, fair and transparent, set retention policies, handle data subject requests and oversee processors.
2) Data processor
A processor acts on behalf of a controller and processes data only under documented instructions. Common processors include cloud hosting providers, analytics services or outsourced payroll companies. Processors implement security measures, assist controllers with compliance (such as responding to access requests) and must not use the data for their own purposes.
3) Personal data
Under the GDPR, “personal data” means any information relating to an identified or identifiable natural person. This includes obvious identifiers like names and email addresses, as well as IP addresses, device IDs or any data that could indirectly identify a person. If you sell to enterprise clients, assume that most customer, employee and usage data falls under this definition.
4) Data Protection Officer (DPO)
A Data Protection Officer is a role required in specific circumstances. Organizations must appoint a DPO if they are a public authority or body, if they carry out large‑scale systematic monitoring of individuals, or if they process special categories of data (health, biometrics, etc.) on a large scale. The DPO’s tasks include informing the organization of its obligations, monitoring compliance, advising on impact assessments, receiving questions from data subjects and acting as the point of contact for supervisory authorities. Crucially, the DPO must have sufficient independence and direct access to senior management.
Other supporting functions
Data protection doesn’t sit in a vacuum. In most companies, a legal or privacy team interprets requirements, security engineers build controls, operations teams manage processes and product managers ensure privacy-by-design. For enterprise sellers, aligning these teams early helps avoid last‑minute surprises when a prospect asks for your data protection measures.
The 7 Main Principles of GDPR (which shape Roles & Responsibilities)
The GDPR outlines seven core principles that inform every obligation and decision:
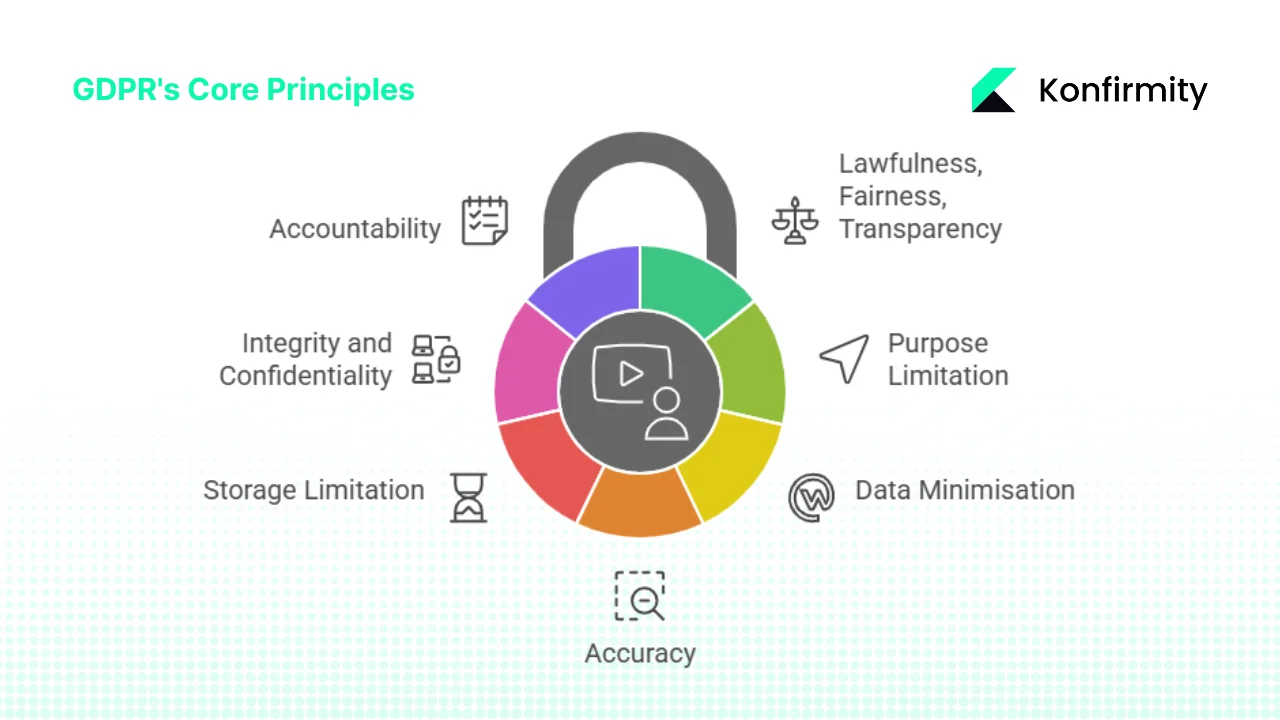
- Lawfulness, fairness and transparency – Processing must have a valid legal basis and be carried out in a way individuals understand. Controllers must tell data subjects how their data is used and on what grounds.
- Purpose limitation – Data collected for one purpose should not be repurposed unless it is compatible or individuals provide new consent.
- Data minimisation – Only the minimum amount of data necessary should be collected and processed.
- Accuracy – Personal data must be kept accurate and up to date; controllers must rectify or erase inaccurate data.
- Storage limitation – Data must not be kept longer than necessary for the purposes for which it was collected.
- Integrity and confidentiality – Appropriate security measures must protect personal data from unauthorized access, disclosure or destruction.
- Accountability – Controllers must document their compliance with these principles and be able to demonstrate it to regulators and clients.
These principles are more than abstract ideals; they guide concrete responsibilities. For example, lawfulness and transparency require controllers to choose a legal basis (consent, contract, legitimate interest, etc.), draft clear privacy notices and record processing activities. Data minimisation demands rigorous collection scoping, while storage limitation forces teams to define retention and deletion schedules. Integrity and confidentiality translate into encryption, access controls, vulnerability management and regular audits. Finally, accountability requires evidence—policies, logs, assessments and breach reports—to prove compliance.
Core Responsibilities by Role (with Practical Steps)
Data controllers
Controllers carry the weight of ensuring GDPR compliance. Below are key responsibilities with practical steps drawn from Konfirmity’s field work.
- Determine purposes and legal basis – Before collecting data, document why you need it and choose a lawful basis (consent, contract, legitimate interest, legal obligation, vital interest or public task). Maintain a register linking each processing activity to its basis.
- Maintain Records of Processing Activities (RoPA) – Article 30 requires controllers to keep records describing processing purposes, categories of data subjects and personal data, retention periods, categories of recipients and security measures. Use templates to record this information centrally and update it whenever processes change.
- Privacy by design and by default – Integrate privacy considerations into system architecture and product features. During design reviews, challenge features that collect data unnecessarily and ensure defaults favour minimal data collection.
- Retention and deletion policies – Define retention periods for each data category. Configure automatic deletion or anonymization once data is no longer needed to comply with storage limitations.
- Transparency and consent management – Draft user‑friendly privacy notices that explain what data you collect, why you collect it, how long you keep it and whom you share it with. Build consent flows that record when and how consent was obtained and provide mechanisms for individuals to withdraw consent.
- Facilitate data subject rights – Set up processes for responding to subject access requests, rectification, erasure (the “right to be forgotten”), restriction, portability and objection. Document each request and response time to demonstrate compliance.
- Data security – Implement technical controls: encryption at rest and in transit, strong access controls, secure coding practices, vulnerability management, intrusion detection, logging and monitoring. Adopt frameworks such as ISO 27001 or SOC 2 to structure these controls; for example, SOC 2’s Trust Services Criteria require security, availability, processing integrity, confidentiality and privacy controls.
- Data breach notification – Establish an incident response plan. Under GDPR, controllers must report breaches to the relevant supervisory authority within 72 hours of becoming aware and notify affected individuals without undue delay if the breach poses a high risk. Conduct periodic drills to test your plan and integrate findings from breach costs studies—IBM reported that the global average cost of a data breach was USD 4.44 million in 2025, with healthcare breaches averaging USD 7.42 million. Early detection and response significantly reduce costs.
- Data Protection Impact Assessments (DPIAs) – For high‑risk processing, conduct a DPIA to identify and mitigate risks to individuals. Document the rationale, results and mitigation measures.
Data processors
Processors have fewer obligations but must follow documented instructions from controllers. To maintain trust and comply with Article 28, processors should:
- Process only as instructed – Do not deviate from the controller’s documented purposes. Document instructions in Data Processing Agreements (DPAs) and confirm alignment before changing processes.
- Implement security measures – Apply technical and organisational measures, as required by Article 32. This includes encryption, access management, secure development practices, vulnerability scanning and regular audits.
- Assist controllers – Provide the controller with information needed to demonstrate compliance, such as data exports for access requests or logs for incident investigation. Cooperate during DPIAs and audits.
- Maintain records – Keep internal logs of processing activities if you process data for multiple controllers or process high-risk data.
- Sub‑processors – Obtain written authorization to engage sub‑processors. Ensure sub‑processors are bound by the same obligations and security standards.
- Support breach notification – Without delay, notify the controller about any personal data breach and provide information needed to fulfill the controller’s notification obligations.
Data Protection Officer (DPO)
Appointing a DPO is mandatory when you process sensitive data on a large scale, monitor individuals systematically or operate as a public authority. Even when not legally required, many enterprise sellers appoint a DPO voluntarily to reassure clients.
A DPO’s responsibilities include:
- Advising on obligations – Educate the company on GDPR requirements, other applicable laws (e.g., U.K. Data Protection Act, CCPA) and related frameworks like HIPAA and SOC 2.
- Monitoring compliance – Review policies, processes and technical controls regularly, track remediation and ensure evidence is collected for audits. Konfirmity’s managed service uses ongoing monitoring and remediation tracking to help clients stay audit‑ready.
- Conducting or reviewing DPIAs – Determine when a DPIA is necessary and assess whether proposed processing is compliant.
- Training and awareness – Develop training programs for employees who handle personal data. This includes security best practices, phishing awareness and privacy culture.
- Acting as point of contact – Serve as the liaison to supervisory authorities and respond to data subject questions. The DPO must report directly to the highest level of management and operate independently to avoid conflicts of interest.
Supporting roles
Other teams support GDPR compliance:
- Security team – Implements technical controls, manages vulnerability management, and coordinates incident response.
- Legal or privacy counsel – Interprets regulations, drafts contracts and ensures compliance with cross‑border data transfer requirements (e.g., Standard Contractual Clauses).
- Operations – Handles day‑to‑day processes such as access reviews, training scheduling and evidence collection.
- Product and engineering – Build privacy‑by‑design features, implement retention logic and integrate security controls into the stack.
Supporting Pillars: Processes & Policies for GDPR Compliance
Beyond roles, GDPR compliance depends on strong processes and policies. Here are the pillars that enterprise sellers should establish.
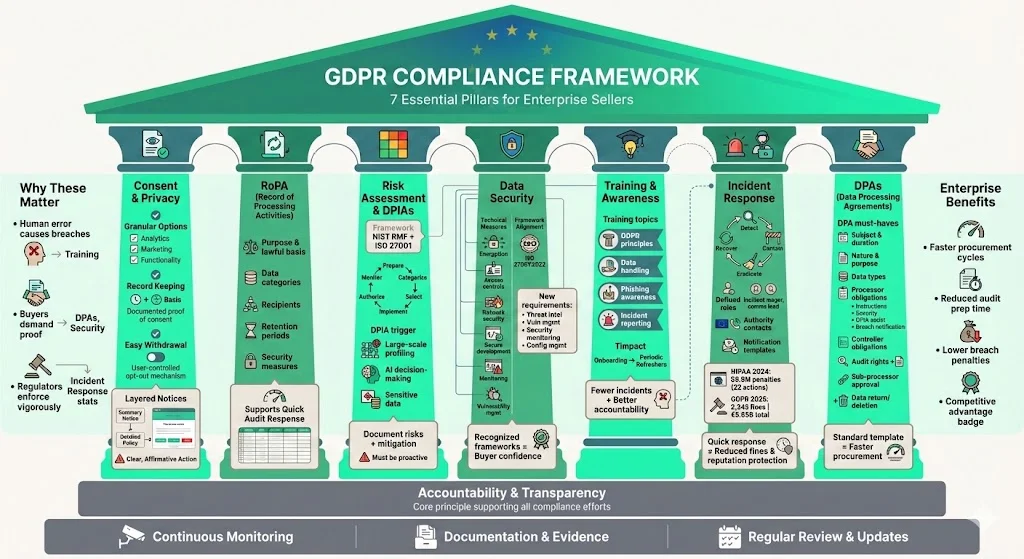
1) Consent management & privacy policies
Implement clear consent mechanisms. Provide granular options when processing data for different purposes (analytics, marketing, product functionality). Record the time, basis and scope of consent and build easy mechanisms for withdrawal. Use layered privacy notices—short summaries with links to detailed policies—to balance transparency and usability.
2) Records of Processing Activities (RoPA)
Maintain a living document of processing activities. Record the purpose, lawful basis, categories of data and data subjects, recipients, retention periods and security measures. This record supports accountability and helps respond to audits quickly.
3) Risk assessment & DPIAs
Develop a risk assessment framework. Use criteria from frameworks like NIST’s Risk Management Framework (Prepare, Categorize, Select, Implement, Assess, Authorize, Monitor) and ISO 27001. Perform DPIAs whenever processing could result in high risk to individuals, such as large‑scale profiling, use of AI for decision making or processing sensitive data. Document identified risks and mitigation actions.
4) Data security measures
Implement technical and organizational measures to protect data. Examples include:
- Encryption (at rest and in transit);
- Access controls (role‑based access, multi‑factor authentication);
- Network security (firewalls, intrusion detection, secure configuration);
- Secure development (static and dynamic code scanning, supply chain management);
- Continuous monitoring (log aggregation, anomaly detection);
- Vulnerability management (regular scanning, patching, penetration testing).
ISO 27001:2022 adds requirements for threat intelligence, vulnerability management, security monitoring and configuration management. Aligning your controls with recognized frameworks helps satisfy both GDPR and buyer expectations.
5) Training and awareness
A common cause of data breaches is human error. Provide regular training on GDPR principles, data handling, phishing and incident reporting. Make sure new hires complete training quickly and require periodic refreshers. In our experience, organizations with ongoing training see fewer incidents and can demonstrate accountability more readily.
6) Incident response and data breach notification
Have a documented incident response plan that outlines detection, containment, eradication and recovery steps. The plan should define roles (e.g., incident manager, communications lead), include contact information for supervisory authorities, and provide templates for notifying customers and regulators. As of 2024, HIPAA enforcement actions showed that regulators increasingly focus on hidden data flows in websites—one enforcement sweep collected over $9.9 million in penalties from 22 actions relating to browser‑based tracking. GDPR enforcement is similarly vigorous, with more than 2,245 fines issued by early 2025 and total penalties exceeding EUR 5.65 billion. A quick, transparent response helps mitigate fines and reputational damage.
7) Data processing agreements (DPAs)
Whenever you engage a processor, execute a DPA that covers:
- The subject and duration of processing;
- The nature and purpose of processing;
- The type of personal data and categories of data subjects;
- Processor obligations (only process per instructions, implement security measures, assist with DPIAs and breach notifications);
- Controller obligations (provide lawful instructions, maintain compliance);
- Audit rights and cooperation;
- Sub‑processor approval and requirements;
- Data return or deletion at termination.
Many buyers will require you to supply a DPA as part of the procurement process. Using a standard template speeds negotiations and shows preparedness.
Practical Step‑By‑Step Guide for Busy Teams
Drawing on our experience helping clients achieve SOC 2, ISO 27001 and GDPR readiness, here’s a pragmatic roadmap to implement roles, responsibilities and supporting measures.
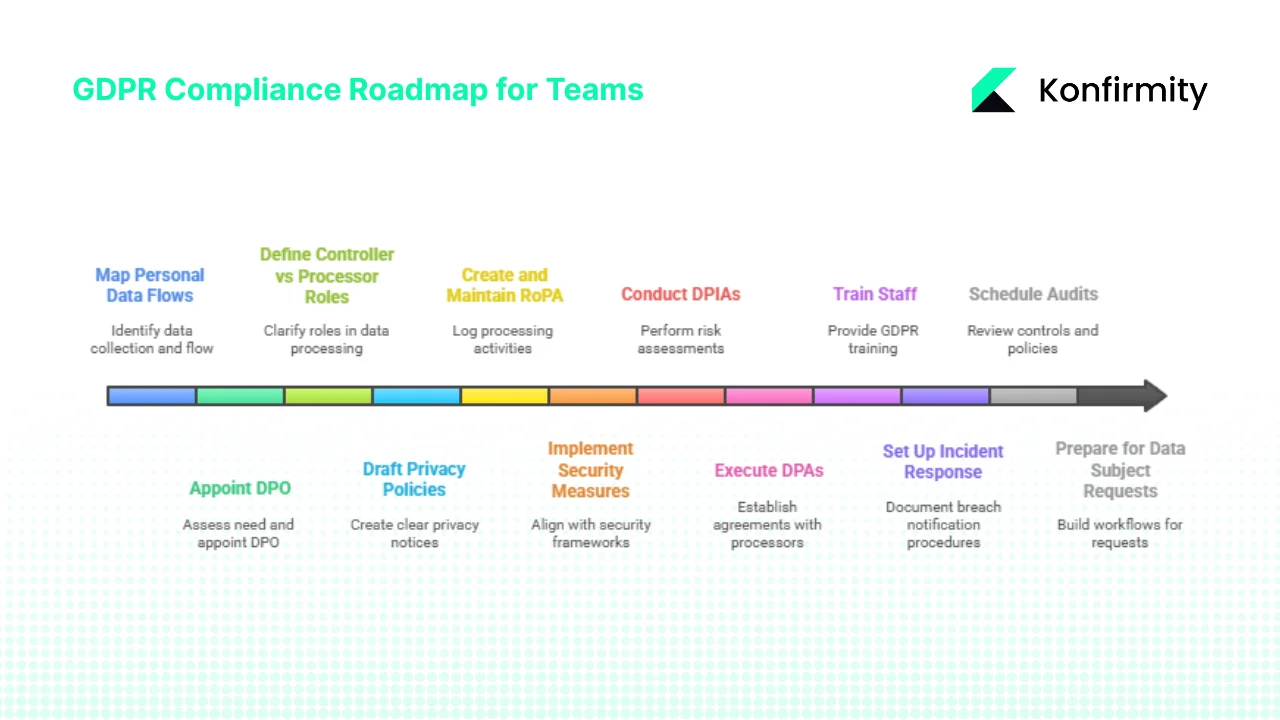
- Map personal data flows – Identify what data you collect, why, where it’s stored, who accesses it and where it flows (internal systems, processors, sub‑processors). Use a data inventory tool or spreadsheet.
- Appoint a DPO if required – Assess whether you process sensitive data or engage in large‑scale monitoring. If yes, appoint or outsource a DPO. Even if not required, consider naming a privacy officer to coordinate compliance.
- Define controller vs processor roles – For each relationship, clarify whether you’re the controller or processor. For joint operations, document responsibilities and accountability.
- Draft or update privacy policies and consent processes – Write clear, accessible privacy notices. Implement consent management solutions that record user consent and allow withdrawal.
- Create and maintain RoPA – Use a template to log each processing activity, including lawful basis and retention period. Update it regularly and review before audits.
- Implement security measures and access controls – Align with frameworks like ISO 27001 and SOC 2. Prioritize encryption, least‑privilege access, vulnerability management and continuous monitoring.
- Conduct DPIAs or risk assessments – For high‑risk processing, perform DPIAs. Leverage NIST’s RMF to categorize risks and choose controls.
- Execute DPAs with all processors and sub‑processors – Use standardized clauses covering instructions, security, assistance, sub‑processing and breach handling.
- Train staff and raise awareness – Provide mandatory GDPR training for relevant employees. Keep records of completion as evidence.
- Set up incident response and breach notification procedures – Document the plan, assign roles, rehearse scenarios and establish communication channels.
- Schedule periodic audits and reviews – At least annually, review your controls, policies and RoPA. Conduct internal or third‑party audits. Monitor regulatory updates (e.g., the transition deadline to ISO 27001:2022 by 31 October 2025) and adjust accordingly.
- Prepare to handle data subject requests – Build workflows and internal SLAs for responding to access, erasure, portability and objection requests. Document each response.
This roadmap is iterative. As your business evolves and new features launch, revisit each step to ensure continued compliance.
Real‑World Examples & Mini Case Studies (for Enterprise‑Selling Teams)
Example 1: SaaS company as a controller and processor
Consider the U.S. SaaS vendor offering project management software to European enterprises. The vendor collects user accounts, project details and metadata. For core product functions, the vendor decides why and how data is processed—making it the controller. However, it might also host third‑party integrations (file storage, chat), acting as a processor for data that customers upload.
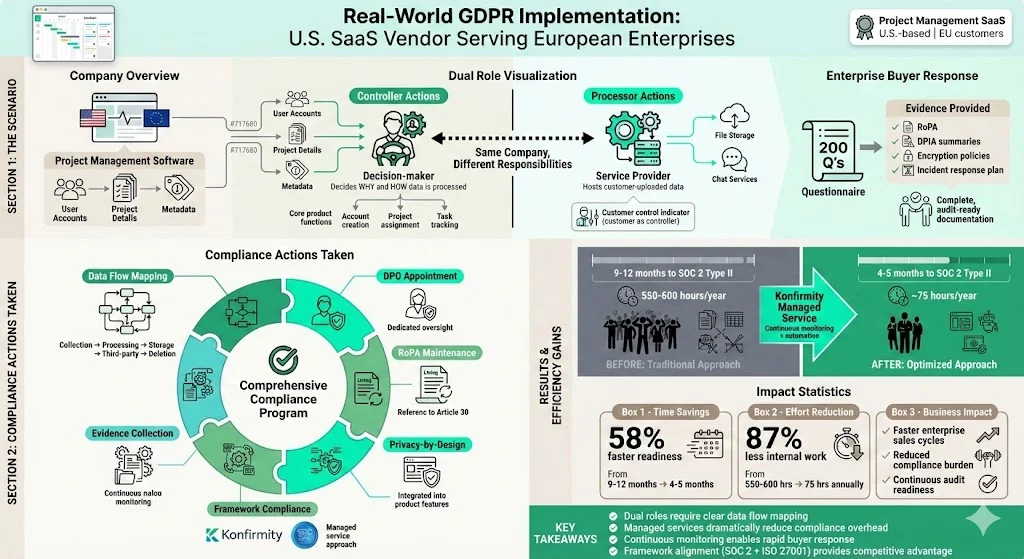
The company maps data flows, appoints a DPO, maintains RoPA, and implements privacy‑by‑design in product features. It uses Konfirmity’s managed service to build SOC 2 and ISO 27001 controls. When a European buyer issues a 200‑question security questionnaire, the vendor provides evidence: RoPA, DPIA summaries, encryption policies, and an incident response plan. By adopting continuous monitoring and evidence collection, the vendor reduces the time to SOC 2 Type II readiness from 9–12 months to 4–5 months and cuts internal workload to about 75 hours per year versus 550–600 hours for self‑managed programs.
CTA: Book a demo
Example 2: Service vendor processing sensitive data
A payment processing service handles credit card transactions for an ecommerce platform. The payment processor receives cardholder data and transaction details but only processes them under the merchant’s instructions, making it a processor. The processor executes a DPA with the merchant, detailing how data will be processed, stored, and deleted. It implements encryption, tokenization, and segmentation. To meet both GDPR and PCI DSS, the processor undergoes periodic audits and provides penetration test results to customers.
Example 3: Data breach response
Imagine a controller experiences unauthorized access to a marketing database. Within hours, the incident response team identifies that the attacker accessed names, emails and marketing preferences but not passwords. The company notifies its DPO, assembles stakeholders (security, legal, communications) and assesses whether the breach is likely to result in risk to individuals. Because the data can lead to phishing, the DPO advises reporting the breach. Within 72 hours, the controller notifies the supervisory authority and informs affected users with recommendations to watch for phishing. The breach is documented, including steps taken and lessons learned. The controller also notifies its processors and sub‑processors to check whether any data flows were affected. Preparation and rehearsal ensure the response meets the 72‑hour requirement and prevents compounding fines.
Template snippets
- DPA clause skeleton – “Processor shall process personal data only on documented instructions from Controller; implement appropriate technical and organisational measures per Article 32; assist Controller in ensuring compliance with Articles 32 to 36; ensure persons authorized to process data are bound by confidentiality; return or delete data upon termination; and allow for audits and inspections.”
- Privacy policy skeleton – Use simple language to explain what personal data you collect, why you collect it, how you use it, how long you keep it, how to contact you and how to exercise rights. Link to your DPO contact and specify the legal basis (consent, contract, etc.).
- DPIA checklist – Define the project scope; describe processing operations; assess necessity and proportionality; identify risks to rights and freedoms; specify measures to address risks; document residual risks; record decisions and monitoring.
- Breach notification email template – Briefly describe the incident (date, type of data, likely consequences); state what you’ve done to mitigate and prevent recurrence; provide guidance for recipients (e.g., change passwords, watch for phishing); include contact details for questions; and express commitment to data protection.
Common Pitfalls & How to Avoid Them
- Confusing controller vs processor roles – Misclassification leads to missed obligations. Conduct a role analysis for each data flow and document the result. When in doubt, err on the side of being a controller because controllers hold primary accountability.
- Not documenting processing activities – Regulators often penalize companies for lacking a processing record. Build a RoPA early and keep it up to date.
- Collecting more data than needed – Over‑collection violates the data minimisation principle. Review forms and logs to ensure you’re only collecting necessary fields.
- Vague privacy notices – Using legal jargon or hiding information undermines transparency and invites scrutiny. Draft notices in clear language and test them with non‑lawyers for comprehension.
- Inadequate training – Employees might inadvertently expose data through phishing or misconfiguration. Regular, role‑specific training reduces risk.
- Weak contract terms – DPAs missing security obligations or audit rights leave you vulnerable. Use a standard set of clauses and review third‑party terms carefully.
- No incident response plan – Delays in breach detection and reporting can turn minor incidents into major violations. Plan, practice and refine your response processes.
- Relying on “compliance manufacturing” – Vendors promising two‑week GDPR or SOC 2 certifications often ignore the observation periods and evidence depth required. Konfirmity’s experience shows that SOC 2 readiness typically takes 4–5 months with proper implementation and continuous monitoring. Quick fixes rarely stand up to audits or incidents.
CTA: Book a demo
Conclusion
Clear assignment of roles and responsibilities is foundational to GDPR compliance and enterprise trust. Buyers want assurance that vendors process data lawfully, minimize what they collect, secure it rigorously and respond quickly to incidents. Regulatory penalties, like the EUR 1.2 billion fine against Meta and the 2,245 fines recorded by March 2025, show that ignoring GDPR obligations is costly and reputationally damaging. Meanwhile, new enforcement trends—such as HIPAA’s focus on website tracking—illustrate that regulators are watching how companies use technology in marketing and analytics.
The good news is that building a sustainable program isn’t just about paperwork. When you start with security and arrive at compliance, controls become part of daily operations and evidence accumulates naturally. Konfirmity’s human‑led managed service helps companies implement controls, collect evidence and stay audit‑ready year‑round. By following the roadmap above—mapping data flows, appointing a DPO, documenting processing activities, implementing security measures, training staff, executing DPAs and preparing for incidents—you can meet GDPR obligations while maintaining buyer confidence and accelerating sales cycles.
FAQ Section
1) What are the 7 main principles of GDPR?
The seven principles are: lawfulness, fairness and transparency (have a valid legal basis and inform individuals), purpose limitation (use data only for specified purposes), data minimisation (collect only what’s necessary), accuracy (keep data correct), storage limitation (retain only as long as needed), integrity and confidentiality (secure data with technical and organisational measures) and accountability (be able to demonstrate compliance).
2) What are the 5 key responsibilities of a Data Protection Officer?
A DPO must: (1) inform the organization of its data protection obligations; (2) monitor compliance and perform audits; (3) advise on and review DPIAs; (4) train staff and promote awareness; and (5) act as the contact point for data subjects and supervisory authorities.
3) What are the 7 golden rules of GDPR?
Some practitioners refer to “golden rules” as practical restatements of the seven principles: (1) establish a lawful basis and be transparent; (2) collect only what you need; (3) use data only for stated purposes; (4) keep data accurate and up to date; (5) delete or anonymize data when no longer needed; (6) keep data secure; and (7) document everything to prove compliance. These correspond directly to the principles.
4) What are the roles and responsibilities of data processing (controller vs processor)?
A controller decides why and how personal data is processed and carries primary accountability. Responsibilities include defining legal bases, maintaining processing records, enabling data subject rights, implementing security measures, conducting DPIAs and reporting breaches. A processor processes data on behalf of a controller, follows documented instructions, implements security measures, assists the controller, maintains records when needed and must not engage sub‑processors without authorization.
5) When is a DPO mandatory?
A DPO is required when an organization is a public authority, engages in large‑scale regular monitoring of individuals, or processes special categories of data on a large scale. Even if not legally required, appointing a DPO or privacy officer can enhance trust with enterprise buyers.
6) What must a data processing agreement include?
A DPA must specify the subject and duration of processing, nature and purpose of processing, type of personal data and categories of data subjects, controller and processor obligations (including security measures and assistance with DPIAs and breach notifications), data subject request handling, audit rights, sub‑processor requirements, and data return or deletion upon termination. Using standardized clauses expedites contract negotiations and ensures regulatory alignment.





.svg)






.svg)
.svg)