Enterprise buyers routinely ask vendors to prove that their systems will protect data and maintain availability. A SOC 2 report is one of the most widely accepted forms of assurance because it shows how a service organization operates its controls over an observation period. Yet “SOC 2 compliance” isn’t a checkbox; it is built on clear accountability. As recent breach statistics show, the global average cost of a data breach reached US$4.44 million in 2025. In the United States the cost per breach is even higher—over US$10.22 million. With stakes like these, having well‑defined SOC 2 roles and responsibilities is more than an exercise in governance—it is a business requirement. This article explores how clear role assignment drives effective security controls, continuous compliance management and smoother audit preparation. It also explains why detailed role definitions matter for vendors selling to enterprise clients and healthcare organizations, where due‑diligence questionnaires, business associate agreements (BAAs) and data processing agreements (DPAs) examine not just control design but also who is accountable for operating those controls.
What SOC 2 Compliance Actually Is
SOC 2 framework and Trust Services Criteria. SOC 2 is an attestation standard developed by the American Institute of Certified Public Accountants (AICPA). Instead of prescribing specific controls, it defines a set of Trust Services Criteria (TSC)—security, availability, processing integrity, confidentiality and privacy—that describe the attributes a control environment must achieve. These criteria form “the basic elements of your cybersecurity posture” and represent organization controls, risk assessment, risk mitigation and change management. Security (the common criteria) is the only mandatory criterion for every SOC 2 audit; the remaining four are added based on customer requirements. The criteria can be summarized as follows:
Type I vs. Type II. A SOC 2 Type I report evaluates whether controls are suitably designed at a point in time. A Type II report goes further—it reviews the operating effectiveness of those controls across an observation period (often 3–12 months). Enterprise buyers almost always demand Type II because they need assurance that controls work day‑to‑day.
Role structure and documentation. SOC 2 compliance is not achieved by technology alone; it requires a governance structure, documented processes, evidence collection and continuous monitoring. The documentation includes security policies, procedures, risk assessments, asset inventories, change‑management logs and vendor contracts. These artifacts must show that controls are defined and operated by named individuals or teams, and auditors will trace evidence back to people. Relationship between SOC 2 compliance and organizational roles is thus two‑fold: clear role assignment ensures each control is owned and executed, and comprehensive documentation allows auditors to verify that ownership. Enterprise clients treat SOC 2 reports as a key risk evaluation tool because they demonstrate that the vendor’s people, processes and technologies operate in a controlled manner, reducing the likelihood of costly breaches.
Key SOC 2 Roles & Responsibilities
The success of a SOC 2 program hinges on assigning the right people to the right duties. Below are core roles, their responsibilities and how they tie back to SOC 2 requirements, ISO 27001 principles and other frameworks (HIPAA, GDPR, NIST). Smaller organizations may combine roles, but segregating duties to avoid conflicts of interest remains essential.
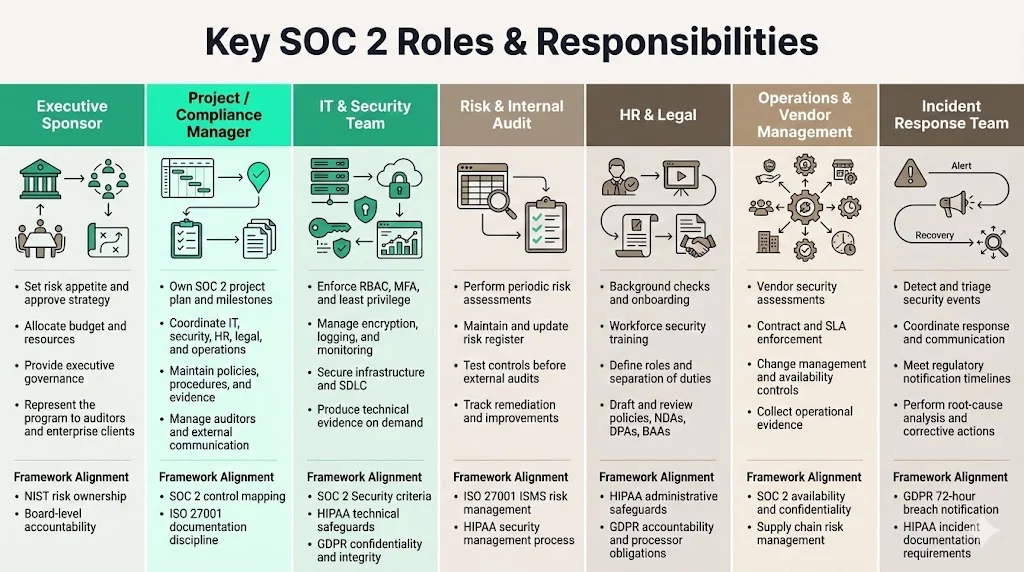
Executive Sponsor
The executive sponsor is typically a C‑level leader (CISO, CTO or CEO) who champions the SOC 2 initiative at the leadership level. Their responsibilities include:
- Set risk appetite and align strategy: The sponsor articulates the organization’s risk tolerance, approves budgets and ensures SOC 2 goals align with business objectives. NIST’s risk management framework assigns the Head of Agency the responsibility to “provide an organization‑wide forum to consider all sources of risk” and to “designate a Senior Accountable Official for Risk Management”.
- Provide governance and resources: They connect SOC 2 efforts to board governance, allocate funding and remove roadblocks. Without executive buy‑in, compliance initiatives stall.
- Act as point of contact for auditors and clients: During audits or enterprise customer due‑diligence, the executive sponsor provides assurance that management supports security and compliance.
Project or Compliance Manager
Sometimes called the SOC 2 program manager or compliance lead, this role oversees day‑to‑day execution:
- Plan and coordinate: They create a SOC 2 project plan, define milestones, track tasks and ensure cross‑functional alignment across IT, security, HR, legal and operations. They also manage readiness assessments, control mappings and remediation efforts.
- Maintain documentation: They oversee the documentation of policies, procedures, risk assessments and evidence. Auditors need proof that policies exist and are being followed. The compliance manager ensures that each document is up to date and mapped to the correct control owner.
- Manage external relationships: They coordinate with external auditors, monitor changes in SOC 2 requirements and communicate progress to leadership. They also handle vendor questionnaires and security addenda.
IT & Security Team
The IT and security team is responsible for implementing and operating technical controls:
- Access control and identity management: They enforce role‑based access control, multi‑factor authentication and least‑privilege principles. For example, the SOC 2 security criteria expect organizations to restrict access based on roles. HIPAA’s technical safeguards require access controls and audit mechanisms to protect electronic protected health information (ePHI), while GDPR calls for measures that ensure the confidentiality and integrity of personal data.
- Encryption and infrastructure security: They manage encryption at rest and in transit, network segmentation, endpoint security, logging and monitoring systems. They also oversee secure software development practices and vulnerability management.
- Evidence of control operation: When an auditor asks “show me that MFA was enforced in May,” the security team produces access logs, SIEM alerts and change‑management tickets. Evidence flows must be repeatable and traceable.
Risk & Internal Audit Personnel
Risk management and internal audit functions are critical for objectivity:
- Conduct risk assessments: They perform periodic risk assessments to identify threats and vulnerabilities. ISO 27001 places risk managers at the center of an Information Security Management System (ISMS), tasking them with identifying, assessing and addressing risks. In HIPAA, the security management process requires an “accurate and thorough assessment of potential risks and vulnerabilities to ePHI” and the management of those risks.
- Coordinate remediation: Once gaps are identified, risk teams work with control owners to prioritize and execute remediation. They maintain a risk register and track mitigation progress.
- Internal audit: They test control design and operating effectiveness before external audits. Internal auditors verify evidence, perform spot checks and recommend improvements. In ISO 27001, internal auditors evaluate the effectiveness of controls and provide recommendations.
HR & Legal Involvement
Human Resources and Legal functions support compliance through people processes:
- Background checks and onboarding: HR performs pre‑employment screenings, facilitates confidentiality agreements and ensures new hires receive security training. HIPAA’s administrative safeguards require workforce security policies that ensure only authorized members access ePHI.
- Define roles and access rights: HR works with security to define job descriptions that include SOC 2 duties. They coordinate role‑based access and separation of duties to reduce conflicts of interest.
- Policy compliance and legal support: Legal teams draft and review policies, NDAs, DPAs and BAAs. Under GDPR, data controllers must designate responsibilities, maintain documentation and ensure third‑party processors have proper data processing agreements.
Operations & Vendor Management Leads
Operational teams ensure that day‑to‑day business processes align with SOC 2 controls:
- Vendor risk management: Operations or procurement leads assess third‑party vendors’ security posture, ensure they comply with the organization’s controls and manage contracts. With supply‑chain attacks doubling from 15% to 30% of breaches between 2024 and 2025, vendor oversight is increasingly critical. Legal counsel ensures that contracts reflect SOC 2 obligations and that vendors sign BAAs or DPAs when handling sensitive data.
- Operational controls: They enforce change‑management procedures, service availability (e.g., backup and disaster recovery), incident management and service level agreements (SLAs). They also gather operational evidence such as change tickets, backup logs and uptime reports.
Incident Response Team
Incidents are inevitable; how a company responds will determine whether a security event becomes a breach. The incident response team’s duties include:
- Detection and triage: Monitor logs, endpoints and network traffic to detect anomalies. They triage events, assess impact and decide whether to invoke the incident response plan.
- Coordinate response and communication: They coordinate internal teams and communicate with leadership, customers and regulators. GDPR requires organizations to notify data subjects and authorities within 72 hours of a breach, while HIPAA mandates documentation of security incidents and mitigation actions.
- Root‑cause analysis and post‑incident controls: After containment, they perform root‑cause analysis, implement corrective controls and document lessons learned.
Common SOC 2 Role Challenges and How to Solve Them
Role overlap and ambiguity. Many companies assign SOC 2 responsibilities informally. Without explicit role definitions, tasks fall through the cracks or multiple teams assume someone else is handling them. NIST’s risk management framework stresses the need to assign individuals to specific roles and to ensure there are no conflicts of interest. Best practice is to create a responsibility matrix that maps each control to an owner and back‑up. Review and update this matrix at least annually or when personnel change.
Insufficient documentation across teams. Auditors look for policies and procedures that are documented, approved and enforced. GDPR’s accountability principle requires organizations to document the data they collect, how it is used, where it is stored and who is responsible for it. Similarly, HIPAA requires covered entities to maintain documentation of their policies and procedures. In practice, this means your project manager must maintain a library of policies, SOPs, risk assessments and evidence artifacts with clear version control.
Difficulty mapping roles to controls. Controls often span multiple teams; for example, access reviews might involve IT, HR and managers. To solve this, break each control into tasks and assign each task to the appropriate role. Use cross‑functional workshops to map controls to owners and identify overlaps. ISO 27001 emphasises the role of control owners—experts who implement and maintain specific controls and monitor their effectiveness.
Limited training and awareness. People can only perform their duties when they understand them. HIPAA’s security awareness and training requirement obligates regulated entities to train all workforce members on security policies and to apply sanctions for violations. Similarly, GDPR calls for staff training and implementation of technical and organizational measures. Provide role‑specific training sessions that explain SOC 2 controls, evidence requirements and tools.
Best practices to address challenges: (1) develop a cross‑functional governance committee; (2) use a documented role‑responsibility matrix; (3) implement regular training and awareness programs; (4) establish clear escalation paths for incidents; and (5) schedule periodic internal audits to verify control ownership and evidence quality.
How Roles Tie to Core SOC 2 Requirements
Below we relate each major SOC 2 requirement to the roles that own it and provide pointers to applicable framework requirements.
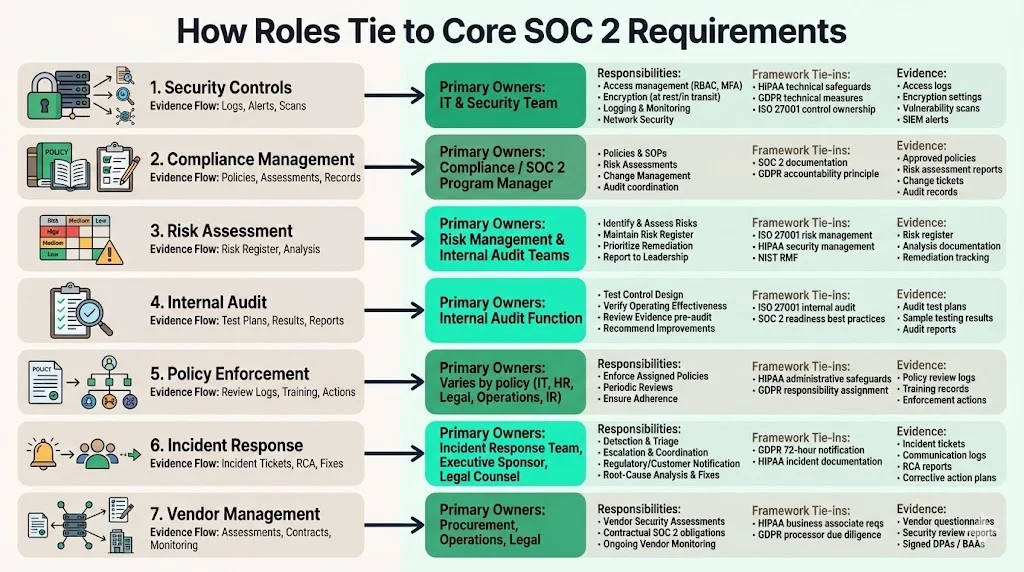
Security Controls
The IT and security team primarily owns security controls—access management, encryption, logging and network security—. They implement technical measures such as multi‑factor authentication, role‑based access control and logging. HIPAA’s technical safeguards call for access control, audit controls, integrity controls, authentication and transmission security. Under GDPR, data controllers must ensure appropriate technical and organizational security. ISO 27001 requires control owners to maintain specific controls and monitor effectiveness. Evidence for these controls includes access logs, encryption configurations, vulnerability scans and SIEM alerts.
Compliance Management
The compliance manager orchestrates policy creation, documentation, risk assessments and audit preparation. SOC 2 documentation requirements include policies, SOPs, risk assessments and change‑management logs. GDPR’s accountability principle mandates that data controllers maintain documentation and designate responsibilities. The compliance manager ensures that documentation is complete, up to date and mapped to controls and owners, and they coordinate responses to procurement questionnaires and auditor requests.
Risk Assessment
Risk and internal audit teams own the risk assessment process. ISO 27001 tasks risk managers with identifying, assessing and addressing information security risks. HIPAA’s security management process requires a thorough risk analysis and risk management. NIST’s RMF assigns the Head of Agency and Risk Executive the responsibility to develop a risk management strategy and assess ongoing organization‑wide risk. The risk team maintains a risk register, prioritizes remediation and reports to leadership.
Internal Audit
Internal auditors verify that controls are designed and operating effectively. They perform walkthroughs, test samples and review evidence before the external audit. ISO 27001 highlights the importance of internal audits to validate the effectiveness of the ISMS and provide recommendations Internal audit functions should be independent of the control owners to avoid conflicts of interest.
Policy Enforcement
Policy ownership varies across roles: security policies may be owned by the IT team; HR policies by HR; incident response policies by the incident response team; vendor management policies by operations and legal. Each policy must designate an owner responsible for enforcement and periodic review. HIPAA’s administrative safeguards require assigned security responsibility and workforce security policies. GDPR’s accountability principle requires organizations to maintain documentation and designate responsibilities. The compliance manager coordinates the policy catalogue, ensures regular reviews and monitors adherence.
Incident Response
Incident response responsibilities span detection, escalation, communication and recovery. The incident response team coordinates detection and triage. The executive sponsor and legal counsel approve public statements and regulatory notifications. GDPR’s breach notification rule requires affected data subjects and authorities to be informed within 72 hours. HIPAA requires regulated entities to document security incidents and their outcomes and to have contingency plans for emergencies. Evidence includes incident tickets, communications logs, root‑cause analysis reports and corrective actions.
Vendor Management
Vendor risk is managed by procurement, operations and legal teams. They assess vendors’ security posture, ensure contracts include SOC 2 obligations, and monitor ongoing compliance. Supply‑chain compromises accounted for 30% of breaches in 2025. HIPAA requires business associate agreements before vendors handle ePHI. GDPR requires data processing agreements and due diligence. Evidence includes vendor questionnaires, security review reports and signed contracts.
Templates & Tools to Define Roles
Practical tools can simplify role definition and evidence collection. Below are templates that Konfirmity recommends incorporating into your SOC 2 program.
Role‑Responsibility Matrix
Create a matrix that lists each role, its duties, the controls it owns and evidence required. Here is a simplified example:
Job Descriptions with SOC 2 Duties
Ensure that job descriptions include SOC 2 responsibilities. For example:
- Security Engineer: responsible for implementing and maintaining access control systems, encryption, logging and vulnerability management. Maintains evidence of control operation and supports audits.
- Compliance Manager: coordinates SOC 2 program, updates policies, leads risk assessments and manages audit readiness. Reports to the executive sponsor and ensures cross‑team alignment.
- Risk Manager: performs periodic risk assessments, maintains risk register, coordinates mitigation and reports to leadership. Collaborates with internal and external auditors.
Contact & Escalation Matrix
Develop a matrix that lists primary and secondary contacts for each control or function, including escalation paths for incidents. Include phone numbers, email addresses and on‑call schedules. This ensures that incidents or audit questions are routed to the right people and reduces response times.
Sample Policy Assignments
Assign each major policy to an owner and specify review frequency:
Evidence and Artifact Checklist
Create a checklist for each role specifying the artifacts they must collect for the audit. For example:
- IT & Security: access logs, network diagrams, penetration test reports, vulnerability scan results, change‑management tickets.
- Compliance: policies and procedures, risk assessments, control mapping, evidence of training, minutes of governance meetings.
- Risk & Audit: risk register, risk assessment reports, internal audit reports, remediation plans.
- HR: background check records, onboarding/offboarding checklists, signed NDAs and confidentiality agreements.
- Operations: backup logs, disaster recovery test results, vendor evaluations and performance reports.
- Incident Response: incident tickets, communications logs, root‑cause analyses, corrective actions.
Getting Ready for the SOC 2 Audit
Clear roles accelerate audit preparation and reduce unpleasant surprises. When each control has an owner and evidence flows are established, the external auditor’s job becomes verifying rather than discovering. Here’s how defined roles help:
- Evidence logs and accountability: With a role‑responsibility matrix in place, each owner knows what evidence to collect. For example, security teams regularly export access logs and encryption configurations; risk teams maintain a risk register and remediation tracker; compliance managers maintain policies and version histories. HIPAA’s requirement for documenting policies and procedures and GDPR’s accountability principle reinforce the need for documentation and evidence.
- Continuous monitoring vs. point‑in‑time preparation: Rather than scrambling at the end of the observation period, adopt continuous monitoring. NIST’s RMF emphasises developing a strategy for continuous monitoring of control effectiveness. Automate evidence collection where possible—e.g., scheduled access reviews, automated vulnerability scans and integration with ticketing systems—to reduce manual effort.
- Reduced audit timeline: Based on over 6,000 audits and 25 years of combined technical expertise, Konfirmity observes that clients who adopt a human‑led, managed approach typically achieve SOC 2 readiness in 4–5 months with about 75 hours of internal effort. In contrast, self‑managed programs often take 9–12 months and consume 550–600 hours of internal time. The following chart compares typical readiness timelines and effort hours:
- Improved sales cycles: When roles are clear and evidence is readily available, sales teams can quickly respond to procurement questionnaires and security addenda. Deals close faster because enterprise buyers gain confidence that controls are in place and accountable personnel are operating them.
Conclusion
SOC 2 compliance is not solely about obtaining a report; it is about building a control environment that stands up to auditors, buyers and attackers alike. SOC 2 Roles And Responsibilities must be explicit, assigned and documented. Leaders set the risk appetite and provide resources; program managers coordinate work and documentation; security teams implement controls; risk and internal audit teams verify effectiveness; HR and Legal enforce workforce and contractual obligations; operations manage day‑to‑day continuity and vendor risk; incident response teams handle the unexpected. Frameworks like ISO 27001, HIPAA and GDPR reinforce these responsibilities by requiring risk assessments, assigned security responsibility, documentation and training. By investing in a human‑led, managed SOC 2 program, vendors can satisfy enterprise clients, reduce breach risks and shorten sales cycles. Security that merely looks good on paper is insufficient; sustainable security comes from controls implemented inside your stack, operated every day by accountable people and continuously monitored. Start with security and arrive at compliance.
IX. Frequently Asked Questions
1. Why is role assignment critical for SOC 2?
Clear roles ensure that every control has an owner, responsibilities do not conflict and auditors can trace actions back to individuals. Frameworks like NIST require assigning individuals to specific roles to avoid conflicts of interest and to support continuous monitoring.
2. Can one person wear multiple SOC 2 roles?
Yes, especially in smaller organizations. However, segregation of duties must be maintained. For example, the same person should not both implement a control and audit it. A CISO may also act as the executive sponsor and compliance manager if there is a second individual to perform internal audits.
3. How often should roles and responsibilities be reviewed?
Review role assignments at least annually or whenever there is a major organizational change (e.g., acquisitions, leadership changes, introduction of new services). Periodic reviews ensure that responsibilities align with current operations and that no control is orphaned.
4. Do vendors need to be included in SOC 2 responsibility planning?
Yes. Third‑party vendors often handle sensitive data or critical services, and supply‑chain breaches accounted for 30% of incidents in 2025. Vendor management teams must evaluate vendor controls, ensure contracts include SOC 2 obligations and monitor vendors over time.
5. What’s the best way to document roles?
Use a responsibility matrix that lists roles, duties, control ownership and evidence expectations. Maintain updated job descriptions with SOC 2 duties, create a contact and escalation matrix and develop an evidence checklist for each role. Keep documentation in a version‑controlled repository accessible to auditors and team members.





.svg)





.svg)
.svg)