Most enterprise buyers now ask for assurance documents before procurement. Deals stall when teams rely on paperwork rather than real security operations. Boards of directors are also under new regulatory pressure: the U.S. Securities and Exchange Commission’s 2023 rules require public companies to report material cyber incidents within four business days and explain their risk management processes, impacts on strategy, and board oversight roles. The SolarWinds enforcement case shows that directors and executives can be held personally liable for misstatements about security practices. That means boardroom awareness of controls, risk exposure and mitigation plans has become mission‑critical.
This article, written for security, compliance, audit and executive leaders at firms selling to enterprise and healthcare clients, explains how to build actionable SOC 2 board reports in 2026. Drawing on AICPA guidance, ISO 27001, HIPAA, GDPR, current breach statistics, and patterns from Konfirmity’s experience across more than 6,000 audits and 25+ years of combined expertise, it shows how to translate technical evidence into business context and support strategic oversight. Konfirmity’s managed service reduces customer involvement to about 75 hours per year rather than the 550‑600 hours often spent on manual SOC 2 preparation, with readiness achieved in 4‑5 months instead of 9‑12 months on a self‑managed path.
What SOC 2 Means and Why Boards Care
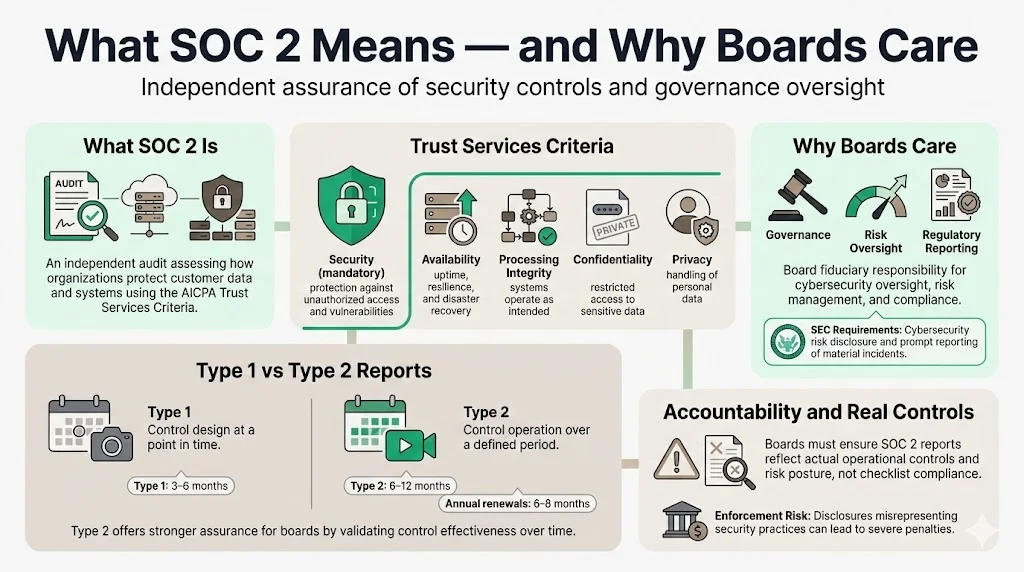
SOC 2 defined. SOC 2 is an independent audit of how an organization protects customer data and systems. It assesses internal controls against the AICPA’s Trust Services Criteria, which cover Security, Availability, Processing Integrity, Confidentiality and Privacy. Security (the only mandatory criterion) examines whether systems are protected from unauthorized access and vulnerabilities. Availability focuses on reliable uptime and disaster recovery plans; Processing Integrity checks that systems operate as intended; Confidentiality ensures only authorized persons can access sensitive data; and Privacy addresses how personal data is collected, used and stored.
Type 1 vs. Type 2 audits. A Type 1 report evaluates the design of controls at a point in time. A Type 2 report assesses whether controls operated effectively over an observation period (commonly six to twelve months). Boards should understand that Type 2 provides stronger assurance because it validates control operation over time. The first SOC 2 audit often takes 3‑6 months for a Type 1 and 6‑12 months for a Type 2. Subsequent annual reports are usually completed in 6‑8 months.
Board accountability. Corporate directors have a fiduciary duty to oversee governance, risk management and compliance. The new SEC disclosure rule requires annual reports to describe the board’s oversight of cybersecurity risk and mandates prompt public reporting of material incidents. Failure to provide accurate disclosures can lead to enforcement actions, as seen when the SEC charged SolarWinds and its CISO for misleading statements about security practices. Boards must therefore ensure that SOC 2 reporting reflects actual operational controls and risk posture rather than superficial checklists.
SOC 2 Fundamentals for Leaders
Trust Services Criteria: Why They Matter to Directors
The AICPA’s Trust Services Criteria map directly to the risk types that matter to boards.
Boards should evaluate which criteria apply to their organization and customers. For example, a SaaS provider serving healthcare clients might include Privacy to address HIPAA and GDPR obligations, while a fintech company may emphasize Availability and Processing Integrity to support service‑level agreements.
Understanding SOC 2 Reports
- Type 1: Provides a snapshot of control design. Useful when a company needs to show that controls exist (e.g., during due diligence or early procurement). However, it does not prove ongoing effectiveness.
- Type 2: Demonstrates that controls operate effectively over time. It is the gold standard for enterprise buyers because it shows evidence across an observation period.
Boards should insist on Type 2 reports for mature programs and verify that the observation period aligns with contract requirements.
Observation Period and Evidence Collection
During a Type 2 audit, auditors observe control operation over 3–12 months. Evidence must be collected continuously, not retroactively. Controls such as access reviews, change‑management logs and incident response records must be maintained throughout the period. Without automation, teams can spend 500‑600 hours gathering evidence and chasing documentation. Automated platforms streamline this process by integrating with cloud services, identity providers and ticketing systems to collect evidence in real time.
Why SOC 2 Board Reporting Is Critical in 2026
Boards are facing unprecedented accountability for cyber risk. New SEC rules require disclosures about risk management processes, impacts on strategy and board oversight. The average cost of a U.S. data breach reached US $10.22 million in 2025—more than double the global average of $4.44 million. The same report noted that more than half of data breaches were caused by malicious activities, with human error and IT failures accounting for the rest. The rapid rise of AI also introduces new risks: AI was involved in 16% of breaches, and 97% of companies hit by AI‑related incidents lacked proper access controls.
In this context, SOC 2 board reporting must do more than state that a report exists. It should provide directors with a clear view of how controls work in practice, what risks remain, and whether remediation efforts are improving the organization’s security posture.
What Boards Need from SOC 2 Reporting
Aligning with Corporate Governance and Enterprise Requirements
Effective SOC 2 board reporting bridges audit evidence with corporate goals, regulatory obligations and contractual commitments. Boards should confirm that SOC 2 reporting:
- Meets contractual obligations. Many enterprise clients require SOC 2 Type 2 reports annually. Contracts may specify which Trust Services Criteria are in scope and how often updates must be provided.
- Supports regulatory compliance. For healthcare and financial firms, SOC 2 reporting supplements HIPAA or PCI requirements. The HIPAA security rule mandates periodic evaluation of security measures and audit controls to examine activity in systems containing ePHI. GDPR requires processing personal data lawfully, for specified purposes, collecting only necessary data, keeping it accurate, limiting storage duration, ensuring integrity and confidentiality, and demonstrating accountability. SOC 2 evidence often overlaps with these obligations (e.g., access logs, encryption, incident response).
- Advances risk management. Directors want to see whether controls address the organization’s top risks, including third‑party and AI‑related threats. Align SOC 2 metrics with the enterprise risk register so that board members can compare security risks against other business risks.
Key Elements of Effective SOC 2 Board Reports

- Executive summary metrics. Provide a concise overview of audit status, including which Trust Services Criteria are in scope, whether the organization passed with exceptions and when the next audit is due. Use plain language and avoid jargon.
- Control environmental health. Summarize the percentage of controls operating effectively (e.g., 95% of controls tested were effective). Highlight any control failures and explain the impact. This ties into internal control reporting obligations and supports the board’s oversight duties.
- Risk assessment data. Present the top risks identified during recent SOC 2 audits and internal assessments. Include likelihood and potential financial impact. For example, a misconfigured cloud bucket might present a moderate likelihood but high impact due to potential breach costs. Use risk heat maps with clear red/yellow/green indicators.
- Changes in the threat environment. Report new vulnerabilities or threat trends (e.g., the rise of AI‑powered phishing or supply‑chain attacks). Provide context with external data: IBM’s 2025 report shows that U.S. breach costs are rising despite global declines and that AI involvement is accelerating.
- Compliance status relative to contracts and regulations. State whether the current SOC 2 report meets all contractual obligations and industry requirements (e.g., HITRUST or GDPR). Note any upcoming deadlines for recertification or updated reports.
- Evidence of control operation and audit trails. Provide documentation that controls operated as designed. For instance, show that access reviews were performed monthly; that incident response plans were executed during a simulation; that backups were tested; and that vendor risk assessments were completed.
- Risk management tracking. Detail how identified risks are being addressed. Include timelines for remediation, responsible owners and progress status.
Building a Practical SOC 2 Board Report Framework
Reporting Standards That Make Sense to Boards
Directors respond better to visuals than to dense paragraphs. Effective board reports often use:
- Traffic‑light summaries for top risks and control effectiveness (green = on track, yellow = attention needed, red = urgent).
- Risk heat maps aligning likelihood and impact across the Trust Services Criteria.
- Dashboards that show the percentage of controls operating effectively, number of audit exceptions, time to remediate findings and incident response times.
Sample Board Report Structure
- Cover page and status snapshot. Include the SOC 2 scope, audit period and overall outcome (e.g., unqualified opinion with no exceptions).
- Executive summary. Provide context on why the report matters (e.g., upcoming enterprise contract renewal), highlight key achievements and call out significant risks.
- Risk heat map tied to SOC 2 criteria. Show how each criterion maps to specific risks. For example, under Security, highlight any critical vulnerabilities; under Privacy, note any personal data exposure incidents.
- Control effectiveness dashboard. Present metrics such as the number of controls tested, percentage passing, number of exceptions and time to remediate. Compared to previous quarters to show trends.
- Red flags and action items. Summarize issues requiring immediate attention (e.g., a critical vendor lacking its own SOC 2 report). Assign owners and deadlines.
- Timeline for remediation. Provide a roadmap of open findings with expected completion dates, indicating any dependencies on third‑party vendors or technology changes.
Metrics and Key Performance Indicators
Use quantitative metrics to make the discussion concrete:
Example SOC 2 Board Reporting Scenarios
Quarterly Security Compliance Update
A technology company with enterprise clients produces a quarterly SOC 2 board report. The executive summary states that the SOC 2 Type 2 report covering the previous six months was issued with no exceptions. The report highlights a 95% control effectiveness rate, with two minor exceptions related to quarterly access reviews that were remediated within 20 days. A risk heat map shows that AI‑powered phishing is an emerging threat; the company has increased anti‑phishing training and implemented email filters. Under the Privacy criterion, a third‑party vendor misconfiguration caused limited exposure of anonymised data; the vendor has since updated controls and provided a SOC 2 report. The board notes that the incident has been fully contained and that there is no legal obligation to report under GDPR because no personal data was involved.
Annual Risk Review with Audit Outcomes
At the annual board meeting, the CISO presents the SOC 2 Type 2 report results along with ISO 27001 surveillance audit findings. The combined evidence shows that all critical controls operated effectively across both frameworks, but that two medium‑risk issues remain: (1) inconsistent vendor risk assessments and (2) missing change‑management documentation for a legacy application. The board is provided a 12‑month remediation timeline. A comparison of risk assessments year‑over‑year shows that overall risk decreased by 15% due to improved endpoint monitoring and vulnerability management. External data from the IBM cost of a data breach report is used to contextualize risks, showing that U.S. breach costs rose to $10.22 million and that malicious activity remained the primary cause.
The board approves increased budget for vendor risk management and instructs management to complete all change‑management documentation before the next audit.
Incident Follow‑Up Board Memo
A few months later, the company experienced a credential stuffing attack that compromised several low‑privilege accounts. The CISO immediately notifies the board (within four business days in accordance with SEC rules) and issues a brief memo. The memo includes: (1) timeline of events; (2) detection and containment actions (multi‑factor authentication prevented privilege escalation); (3) impact assessment (no sensitive data accessed, no customer impact); (4) root cause analysis; (5) changes to internal controls (enhanced monitoring, user training); and (6) lessons learned. The board reviews the memo, confirms that disclosure obligations are met and supports additional investment in passwordless authentication.
Common Challenges and Solutions
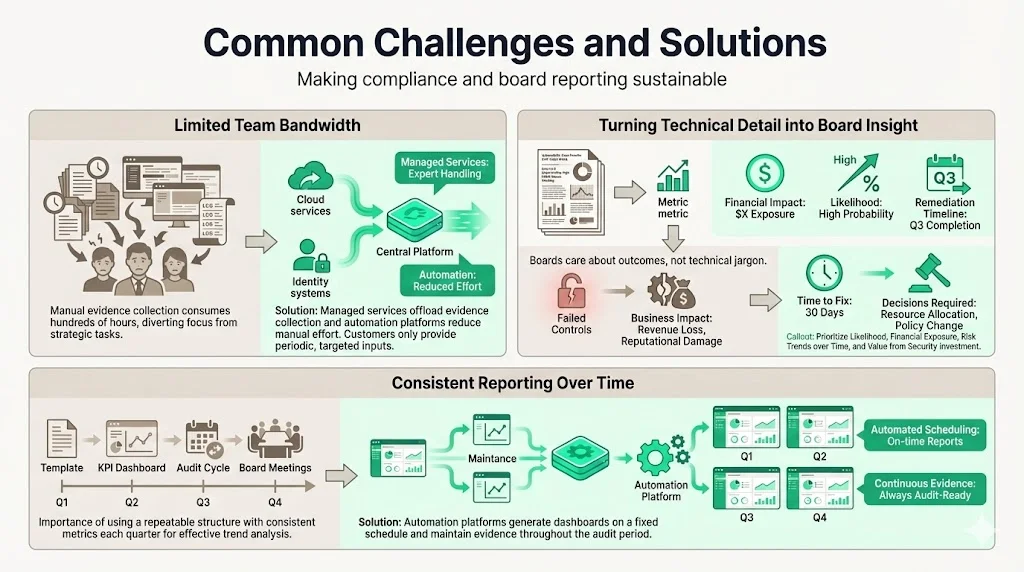
1) Busy Teams with Limited Bandwidth
Manual evidence collection and report preparation can consume hundreds of hours. Staff often juggle day jobs while gathering screenshots, logs and policies. With Konfirmity’s managed service, the heavy lifting is offloaded; automation integrates with cloud and identity services to collect evidence continuously. Customers only need to spend a few hours per month for check‑ins and internal inputs. For teams not using managed services, adopting a compliance platform can still cut manual work by up to 35%.
2) Translating Technical Details into Board Language
Security and compliance reports can be dense. Boards care about financial impact, likelihood of risks and progress over time. When presenting, avoid jargon and focus on outcomes: how many controls failed, what the consequences were, how long it took to remediate and what decisions are needed. Use metrics and visuals to connect technical details to business risks. The Kovrr guidelines suggest focusing on likelihood and financial exposure, risk posture over time and return on investment for cybersecurity spending.
3) Keeping Reporting Consistent Over Time
To build confidence, board reports should follow a consistent structure and set of metrics. Use a template that can be reused each quarter, with a fixed list of KPIs and risk categories. Schedule reporting cadences aligned with audit cycles and board meetings. Automation platforms can generate dashboards at set intervals and maintain evidence for the observation period.
Tools and Practices to Streamline SOC 2 Reporting
- Automated compliance platforms. Tools that integrate with cloud providers, identity platforms and ticketing systems can collect evidence continuously, reducing manual effort. They also provide dashboards for board reporting.
- Risk management workflows. Embedding risk assessments into daily operations ensures that issues are identified and tracked promptly. ISO 27001 requires risk assessments to identify assets, threats and vulnerabilities, estimate impact and select treatment options. A risk treatment plan should include an executive summary, scope, risk identification, treatment options, residual risk and monitoring plans.
- Cross‑framework mapping. Many controls overlap across SOC 2, ISO 27001, HIPAA and GDPR. For example, access control, logging and encryption support both SOC 2 Security and HIPAA technical safeguards, while GDPR’s integrity and confidentiality principle parallels SOC 2’s Security criterion. Mapping controls across frameworks reduces duplication and ensures comprehensive coverage.
- Dedicated managed service. Konfirmity offers an end‑to‑end managed service with dedicated CISO and security analysts. Unlike self‑service platforms or one‑off consultancies, we implement and operate controls, deliver continuous monitoring, coordinate audits and manage renewals. Customers invest around 75 hours per year, compared with 550‑600 hours when self‑managed.
Checklist for Your Next SOC 2 Board Report
Use this checklist before presenting your next SOC 2 board report:
- Clear summary of SOC 2 status. State the audit type (Type 1 or Type 2), period, scope and outcome.
- Link to risk register. Reference the enterprise risk register and show how SOC 2 findings map to top risks.
- Outstanding remediation items. List unresolved audit exceptions, with owners and expected closure dates.
- Trends over time. Compare control effectiveness, number of incidents and risk ratings with previous periods.
- Decisions needed from the board. Highlight any resource allocations or policy approvals required to address risks.
- Regulatory and contractual alignment. Confirm that evidence meets obligations under contracts, HIPAA, GDPR or other frameworks.
- Evidence and audit trails. Provide proof of control operation (e.g., logs, tickets, policy acknowledgments).
Conclusion
SOC 2 board reporting in 2026 must move beyond box‑ticking. Directors face growing scrutiny from regulators and shareholders, and the cost of failure continues to rise. Effective reporting links control evidence to business risk, communicates in plain language and uses metrics that drive action.
Konfirmity’s approach—“Start with security and arrive at compliance”—means building real controls inside your environment and maintaining them year‑round. With a managed service that combines automation and human expertise, you can achieve SOC 2 readiness in 4‑5 months, minimize your team’s time burden and deliver board reports that instill confidence in buyers, auditors and regulators.
FAQs
1. What is SOC 2 reporting?
A SOC 2 report is an independent audit of a company’s internal controls related to the Security, Availability, Processing Integrity, Confidentiality and Privacy of systems and data. It demonstrates that controls are designed (Type 1) and operating effectively over time (Type 2).
2. Who requires a SOC 2 report?
Enterprise clients, vendors and partners often require SOC 2 reports as proof of robust security and to meet their own risk‑management or regulatory obligations. Contracts may specify which Trust Services Criteria are in scope and may require annual Type 2 reports.
3. What are the five Trust Services Criteria?
They are Security (mandatory), Availability, Processing Integrity, Confidentiality and Privacy. Security protects against unauthorized access; Availability ensures uptime and resilience; Processing Integrity ensures systems operate as intended; Confidentiality restricts access to sensitive data; and Privacy governs personal data handling.
4. How often are SOC 2 reports required?
SOC 2 reports have no fixed legal frequency, but enterprise contracts typically require annual Type 2 reports. The initial Type 2 audit involves a pre‑audit phase and an observation period of 3–12 months. Subsequent audits usually occur annually to maintain assurance.
By adopting a disciplined approach to SOC 2 board reporting—grounded in real control evidence, risk alignment and clear communication—you can turn compliance from a bottleneck into a business enabler. Solid security is not just about passing audits; it’s about building trust that lasts.





.svg)





.svg)
.svg)