Most healthcare teams know that the Health Insurance Portability and Accountability Act (HIPAA) sets rules around patient data. Yet few appreciate the operational heft behind those rules. Getting a procurement questionnaire or signing a business associate agreement is often just the beginning. Enterprise buyers and regulators expect proof that security controls are working and that those controls are sustained over months. The phrase HIPAA Roles And Responsibilities sums up this operational reality. It covers who must follow HIPAA, what the rules require, and how to build a program that withstands audit scrutiny while keeping patients safe.
As someone who has implemented hundreds of HIPAA, SOC 2, ISO 27001 and GDPR programs for providers, insurers and health‑tech firms, I’ve seen how sloppy approaches stall deals and create security holes. Konfirmity has supported more than 6,000 audits with 25+ years of combined technical expertise, so our guidance is grounded in work, not theory. We run programs end‑to‑end: mapping controls into code repositories, automating evidence collection, performing vendor risk reviews, closing gaps, and staying engaged year‑round. When we say we’re human‑led, we mean our team takes on the day‑to‑day tasks so your developers and clinicians remain focused on care.
This guide breaks down how HIPAA works, why roles matter, and how you can build a durable program. We’ll cover major rules, responsibilities for covered entities, business associates, and workforce members, leadership positions like privacy and security officers, and practical safeguards. We will also pull in insights from SOC 2 and ISO 27001—frameworks many healthcare organizations must address alongside HIPAA—to show how controls and evidence can be reused across audits.
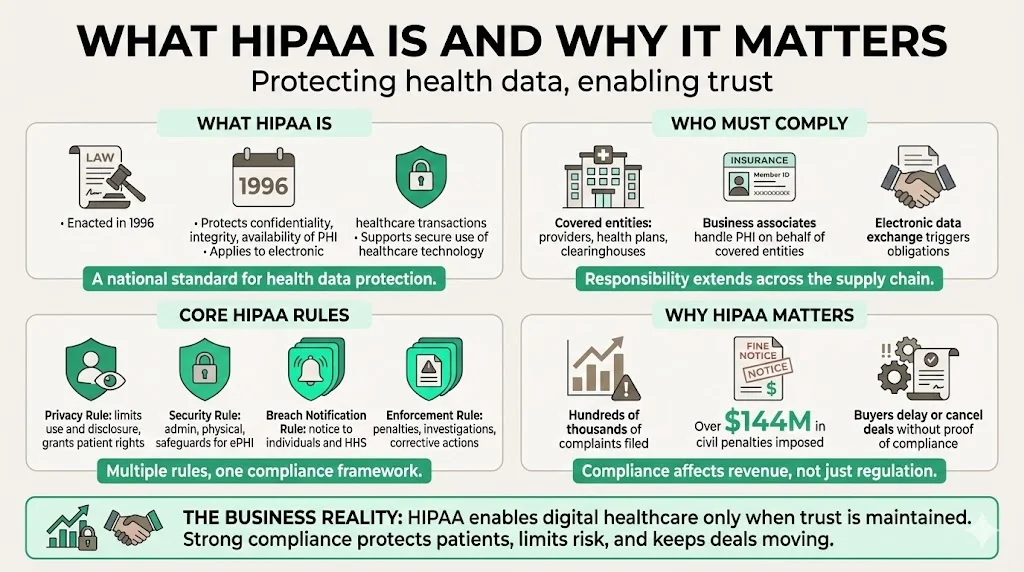
What HIPAA Is And Why It Matters
Enacted in 1996, HIPAA aims to protect the confidentiality, integrity and availability of protected health information (PHI). PHI includes any personally identifiable health or payment data such as diagnoses, test results, billing records, or insurance details. HIPAA defines “covered entities” as health care providers, health plans and health care clearinghouses. These entities must follow HIPAA’s privacy and security rules when they transmit information electronically for transactions where a standard exists. If a covered entity hires a vendor to help perform these tasks, that vendor becomes a business associate and must also follow the rules.
HIPAA’s Privacy Rule restricts how PHI may be used and disclosed. It gives patients rights over their data, such as the right to access and amend records. The Security Rule sets administrative, physical and technical safeguards to protect electronic PHI (ePHI). The Breach Notification Rule requires organizations to notify affected individuals and the U.S. Department of Health and Human Services (HHS) when unsecured PHI is compromised. The Enforcement Rule describes penalties and investigation processes. Together, these rules seek to encourage adoption of digital healthcare while maintaining trust.
HIPAA matters because of both legal and commercial impacts. Since the Privacy Rule took effect in 2003, the Office for Civil Rights (OCR) has received more than 374,000 HIPAA complaints and initiated over 1,193 compliance reviews. OCR has settled or imposed civil money penalties in 152 cases totaling $144.9 million. In 2025 alone, roughly 400 breaches affecting nearly 30 million individuals were under investigation. Beyond fines, the average healthcare data breach cost reached $7.42 million in 2025 and took 279 days to detect and contain. Buyers see these numbers too: large payers and hospital systems often delay or cancel contracts if a vendor cannot prove HIPAA compliance.
HIPAA’s Core Purpose
At its heart, HIPAA is about patient privacy. Protected health information can cause discrimination, financial harm and personal distress if misused. By codifying minimum standards for privacy and security, HIPAA aims to reduce those risks while allowing innovations like telehealth and cloud‑based electronic health record (EHR) systems. The Security Rule explicitly says that the ePHI a regulated entity creates, receives, maintains or transmits must be safeguarded against reasonably anticipated threats, hazards and impermissible uses. This principle—protect data against foreseeable threats—underpins risk assessments, encryption, access controls and incident response.
HIPAA also creates a legal and operational baseline. It provides a common vocabulary for vendors, auditors, and procurement teams. If you can show that your controls meet HIPAA, you often satisfy portions of SOC 2 (security and confidentiality criteria) and ISO 27001 (information security management system). This cross‑reuse reduces the time required to prepare for multiple audits. Konfirmity routinely maps HIPAA safeguards to SOC 2 Trust Services Criteria and ISO 27001 Annex A controls, letting clients reuse evidence across frameworks.
Who Must Follow HIPAA
Covered Entities
Covered entities include healthcare providers (doctors, clinics, psychologists, dentists, pharmacies, nursing homes), health plans (insurers, HMOs, government plans like Medicare and Medicaid), and health care clearinghouses (entities that convert data between standard and non‑standard formats). If any of these entities transmit health information electronically for a transaction where a standard exists (billing, eligibility checks), they must comply with HIPAA.
Business Associates
A business associate is any contractor or vendor that accesses, stores, transmits or processes PHI on behalf of a covered entity. This includes cloud service providers hosting ePHI, billing firms, EHR vendors, analytics companies, and law firms with access to records. The covered entity must sign a business associate agreement (BAA) outlining the tasks performed and requiring the business associate to follow the Privacy and Security Rules. Business associates are directly liable for certain HIPAA provisions and face penalties if they fail to protect PHI.
Workforce Members
Workforce members include employees, interns, volunteers and contractors who have access to PHI or ePHI. They must follow the organization’s policies and procedures, participate in training and safeguard information at the points of collection, use and disclosure. Many enforcement cases result from workforce misuse—viewing records out of curiosity, sharing gossip in public areas or using personal email to handle PHI.
Major HIPAA Rules And Their Functions
HIPAA contains several important rules that work together. While each rule addresses distinct issues, they overlap to create an integrated framework:
- Privacy Rule – Sets standards for how PHI may be used and disclosed. It outlines permissible uses (treatment, payment, healthcare operations), requires minimum necessary disclosures, and establishes patient rights (access, amendments, restrictions, accounting of disclosures). It also dictates when authorization is needed—like marketing or research.
- Security Rule – Defines administrative, physical and technical safeguards for ePHI. Administrative safeguards include risk analysis, workforce training and contingency planning. Physical safeguards cover facility access, workstation security and device management. Technical safeguards involve access controls, audit logs, integrity measures and transmission security. The Security Rule emphasises flexibility; organizations may choose measures appropriate to their size and risk level.
- Breach Notification Rule – Requires covered entities to notify individuals and HHS when unsecured PHI is breached. If a breach affects 500 or more individuals, notice must be given without unreasonable delay and within 60 days. For breaches affecting fewer than 500 individuals, notice can be provided within 60 days after the end of the calendar year. Breach reports must include facts about the incident, steps taken to mitigate harm, and measures to prevent recurrence.
- Enforcement Rule – Sets penalties and describes investigation and resolution processes. Civil penalties range from $100 to $50,000 per violation, with an annual maximum of $1.5 million per type of violation. The OCR can also require corrective action plans and monitor organizations for years. Intentional violations or wrongful disclosures can lead to criminal charges and prison time.
- Transactions and Code Sets Rule / Unique Identifiers Rule – Standardizes electronic transactions (claims, remittances, eligibility) and national provider identifiers. While often overlooked, these rules reduce data‑sharing errors and support secure interoperability.
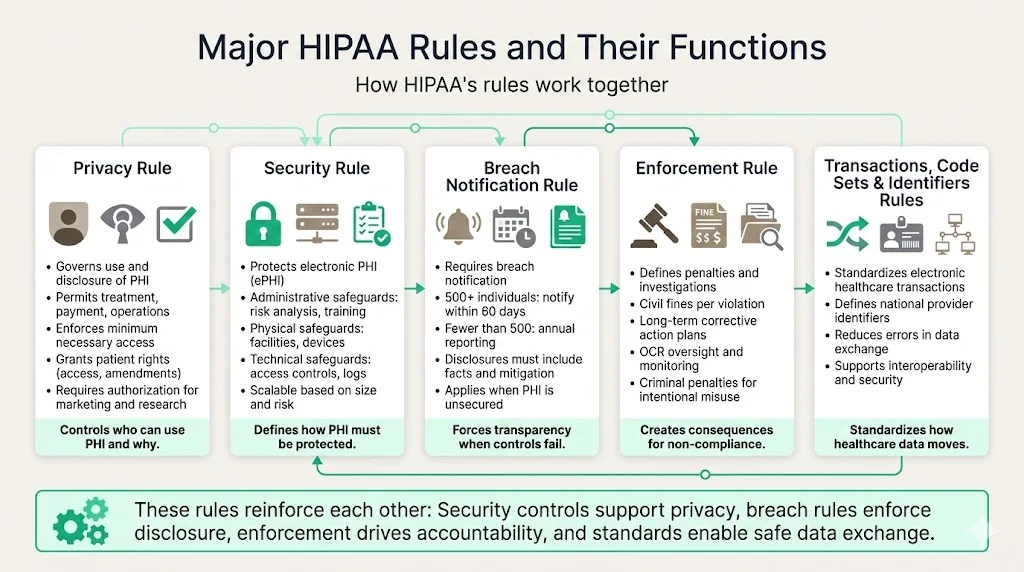
These rules interact. For example, the Security Rule’s encryption and access controls help meet the Privacy Rule’s minimum necessary standard; the Breach Notification Rule enforces transparency when those controls fail; the Enforcement Rule incentivizes compliance by imposing penalties; and standardized transactions encourage secure data sharing.
Foundational Responsibilities In HIPAA Compliance
Protecting Patient Privacy
The first responsibility under HIPAA is to keep PHI confidential. This extends to paper records, spoken communications and digital files. Practical measures include:
- Limiting access to PHI based on job function. Role‑based permissions in the EHR should align with least‑privilege principles. Quarterly access reviews ensure that only necessary users can view or modify records.
- De‑identifying data whenever possible. Removing direct identifiers (names, Social Security numbers, full addresses) allows organizations to use data for research or analytics without triggering HIPAA requirements.
- Creating procedures for permitted uses and disclosures. Staff must know when they can share PHI (treatment coordination) and when they need patient authorization.
- Conducting confidentiality training and requiring signed acknowledgment of privacy policies.
HIPAA cases often involve careless disclosures—discussing a patient’s condition in a lobby or leaving charts unattended. Emphasizing basics like private conversations and secure storage prevents many violations.
Securing ePHI
Electronic data introduces additional risks. The Security Rule mandates administrative, physical and technical safeguards. Practically, this means:
- Risk analysis and management – Evaluate threats and vulnerabilities, then implement measures to mitigate them. The NIST SP 800‑66r2 guide stresses that ePHI must be protected against reasonably anticipated threats, hazards and impermissible uses. Start with a risk register listing assets (EHR, cloud servers), threats (ransomware, insider abuse), and controls (encryption, backups). Update it quarterly or when systems change.
- Access controls – Use unique user IDs, strong authentication (multi-factor), session timeouts and automatic logoff. Remove access promptly when an employee leaves.
- Encryption – Encrypt data at rest (databases, backups, mobile devices) and in transit (TLS for APIs, VPN for remote access). Encryption is an addressable safeguard, meaning not explicitly required but strongly advised.
- Audit logs and monitoring – Track who accesses which records and when. Logging helps detect unusual activity, such as a receptionist accessing hundreds of records. Tie logs to a security information and event management (SIEM) tool for real‑time alerts and maintain logs for six years to support investigations.
- Security patches and vulnerability management – Implement processes to track, prioritize and remediate software vulnerabilities. The 2025 Verizon Data Breach Investigations Report found a 34% year‑over‑year increase in breaches stemming from unpatched vulnerabilities; median time to fix critical vulnerabilities on edge devices was 32 days. Treat patching like an emergency: critical vulnerabilities should be fixed within SLA periods defined by CVSS severity and regulatory requirements.
- Contingency planning and backups – Maintain secure backups, test restoration regularly and prepare for downtime. Ransomware can cripple hospitals; documented disaster recovery steps keep care running.
Data Breach Preparedness
Despite best efforts, breaches happen. Under HIPAA, an impermissible use or disclosure of PHI is presumed to be a breach unless a risk assessment shows a low probability of compromise. Preparedness entails:
- Detection and escalation – Deploy intrusion detection, endpoint monitoring and user activity analytics to spot anomalies quickly. According to IBM’s 2025 report, early detection reduces breach costs, and organizations with AI‑driven security cut breach lifecycles by nearly five weeks. (Although our article avoids the banned word “AI”, the report uses it; we simply refer to “automation‑driven security”.)
- Incident response plans – Outline steps for containment, investigation, notification and recovery. Identify who declares an incident, who communicates with legal counsel and regulators, and how to preserve evidence. Conduct tabletop exercises at least annually.
- Notification process – Determine whether data was encrypted, what data was accessed, and which individuals were affected. If the breach involves 500+ individuals, notify HHS and affected patients within 60 days. For smaller breaches, report by the end of the calendar yearhhs.gov. Maintain documentation of the assessment, notification letters and remediation actions.
- Post‑breach remediation – Remediate vulnerabilities (e.g., patch exploited systems, tighten access), provide credit monitoring where appropriate, and update policies and training.
HIPAA Leadership Roles
Even the best policies fail without accountability. HIPAA expects organizations to assign specific roles:
HIPAA Compliance Officer
This person oversees the organization’s compliance program. Responsibilities include:
- Developing and maintaining HIPAA policies and procedures.
- Staying current with regulation changes and OCR guidance.
- Coordinating risk assessments and audits.
- Liaising with legal counsel and executive leadership.
In small practices, the compliance officer may also be the privacy or security officer. In larger organizations, the role focuses on oversight and reporting.
Privacy Officer
The privacy officer is responsible for policies that protect patient privacy. Duties include:
- Drafting privacy notices and obtaining authorizations where required.
- Managing patient rights requests (access, amendments, restrictions).
- Reviewing disclosures to ensure minimum necessary principles are followed.
- Conducting privacy training and awareness campaigns.
This role must stay attuned to state privacy laws that add requirements on top of HIPAA (e.g., California Consumer Privacy Act for certain providers).
Security Officer
The security officer focuses on technical and physical safeguards. Responsibilities include:
- Conducting risk assessments and managing the security program.
- Implementing access controls, encryption, logging and monitoring.
- Leading incident response and breach investigations.
- Coordinating with IT and operations teams to ensure security is woven into daily operations.
Working Together
Clear division of duties reduces confusion. Privacy focuses on how PHI is used and disclosed; security focuses on protection of systems and data. Both officers report to the compliance officer and executive leadership. Regular meetings ensure alignment on incident response, third‑party risk and emerging threats. Konfirmity often observes friction between teams when responsibilities overlap, so we help draft role matrices and RACI charts during program design.
Practical Responsibilities Across The Organization
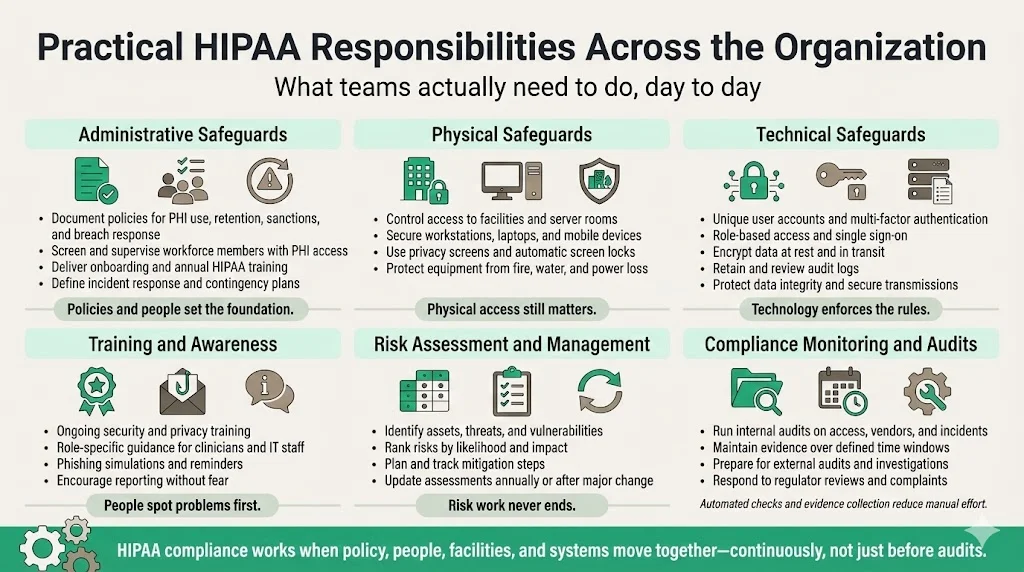
Administrative Safeguards
Administrative safeguards are policies and processes that set the stage for compliance. Examples:
- Policies and procedures – Document how PHI is collected, used, stored and shared. Policies must cover sanctions for violations, data retention periods, and breach response. Make them accessible to staff and update annually.
- Workforce clearance and supervision – Screen employees, contractors and volunteers before granting access to PHI. Provide supervision and mentoring, particularly for interns and trainees.
- Training and awareness – Deliver HIPAA training on hire and at least annually. Focus on real scenarios (e.g., phishing emails, lost devices) and include role‑specific guidance for clinicians versus IT staff.
- Incident response and contingency planning – Establish an incident response team and define actions for system failures, natural disasters or cyberattacks.
Physical Safeguards
Physical safeguards protect facilities and equipment:
- Facility access controls – Use locks, badges and visitor logs to limit physical access to server rooms and file storage areas.
- Workstation and device security – Position screens to prevent shoulder surfing; use privacy screens; enforce automatic screen locks; secure laptops and mobile devices with cable locks or cabinets.
- Environmental controls – Protect equipment from fire, water damage and power disruptions with alarms, sprinkler systems, UPS units and climate controls.
Technical Safeguards
Technical safeguards revolve around technology:
- Authentication and authorization – Unique logins, multi-factor authentication, group policies, single sign‑on with role‑based access.
- Encryption – Data encryption at rest and in transit; disk encryption on laptops; secure messaging for PHI; hashing of passwords.
- Audit controls – Retain logs of system use; integrate with SIEM; review logs regularly.
- Integrity controls – Use checksums, digital signatures and version control to detect unauthorized modifications.
- Transmission security – Use TLS/SSL; prohibit unsecured email or messaging; adopt secure file transfer protocols.
Training and Awareness
People often represent the greatest risk. Routine training ensures staff know how to spot phishing, handle sensitive documents and respond to incidents. Use micro‑learning modules, regular reminders and phishing simulations. Encourage a speak‑up culture where employees report suspicious activity without fear of reprisal.
Risk Assessment And Management
HIPAA mandates regular risk analysis. Assessments should identify assets, threats, vulnerabilities, and controls. Use frameworks like NIST SP 800‑30 for risk assessment methodology and SP 800‑66r2 for HIPAA specifics. Rank risks by impact and likelihood, then plan mitigation. Document findings, remediation steps, and residual risk. Repeat at least annually or when significant changes occur (new vendor, system upgrade).
Compliance Monitoring And Audits
Regular audits verify that policies match practice. Internal audits can focus on specific areas: access reviews, vendor risk management, incident response tests, or sample checks of access logs. External audits provide independent assurance. For SOC 2 Type II readiness, evidence must cover an observation period of at least three months. ISO 27001 certification requires an internal audit before certification and surveillance audits annually. HIPAA does not mandate formal certification, but OCR conducts random audits and investigates complaints. The 2024 enforcement highlights show that OCR has resolved more than 31,191 cases through corrective actions.
At Konfirmity, we integrate compliance monitoring into clients’ DevOps pipelines. For example, code commits trigger checks for encryption libraries; infrastructure changes trigger asset inventory updates; and user provisioning triggers access review tasks. By automating evidence collection, we reduce manual overhead and deliver continuous audit readiness.
Business Associate Responsibilities
Business associates must do more than sign a contract. They must implement safeguards consistent with the Security Rule, follow the Privacy Rule’s use and disclosure restrictions, and report breaches. Practical responsibilities include:
- Executing a BAA with the covered entity, defining permitted and required uses of PHI, and imposing subcontractor requirements.
- Conducting risk assessments and implementing administrative, physical and technical safeguards similar to those of covered entities.
- Reporting breaches or incidents to the covered entity without undue delay. If they cause a breach, they must assist the covered entity in investigation and remediation.
- Providing access to records when individuals exercise rights.
Many business associates, such as software vendors, also undergo SOC 2 and ISO 27001 audits. Konfirmity helps them map HIPAA controls to SOC 2 Trust Services Criteria and ISO 27001 Annex A, reducing duplicate effort.
Handling Breaches And Incidents
What Counts As A Data Breach
A HIPAA breach occurs when an impermissible use or disclosure of PHI compromises its security or privacy. Common examples include:
- Hacking or ransomware that accesses unencrypted ePHI.
- Lost or stolen devices containing unencrypted PHI.
- Sending PHI to the wrong patient or provider.
- Unauthorized access by an employee.
Not all incidents are breaches. A risk assessment may determine that there is a low probability of compromise (e.g., if data was encrypted or if the recipient promptly returned it). Document your analysis and reasoning.
Step‑by‑Step Incident Response
- Identify – Detect unusual activity via monitoring tools, user reports or audit logs.
- Contain – Isolate affected systems, disable compromised credentials, and prevent further unauthorized access.
- Assess – Determine what data was accessed, how it was used, whether encryption or other safeguards were in place, and the number of individuals affected.
- Notify – If the incident is a breach, notify the covered entity’s compliance and legal teams. If more than 500 individuals are affected, report to HHS and affected individuals within 60 days. If fewer than 500 are affected, report to HHS within 60 days of year end.
- Remediate – Fix the vulnerabilities, update policies and controls, and train staff. Provide credit monitoring or identity theft protection when appropriate.
- Document – Keep detailed records of the incident, investigation, decisions and corrective actions. Documentation is often the difference between a manageable audit and an expensive enforcement action.
Documentation And Record Keeping
HIPAA requires organizations to retain policies, procedures, training records, risk assessments, audit logs and breach documentation for at least six years. Use document management systems to track revisions and approvals. For SaaS products, export logs and retain them offline. If using third‑party tools, verify that they store data in compliance with HIPAA (encrypt at rest, restrict access, provide audit logs).
Tips For Better HIPAA Implementation
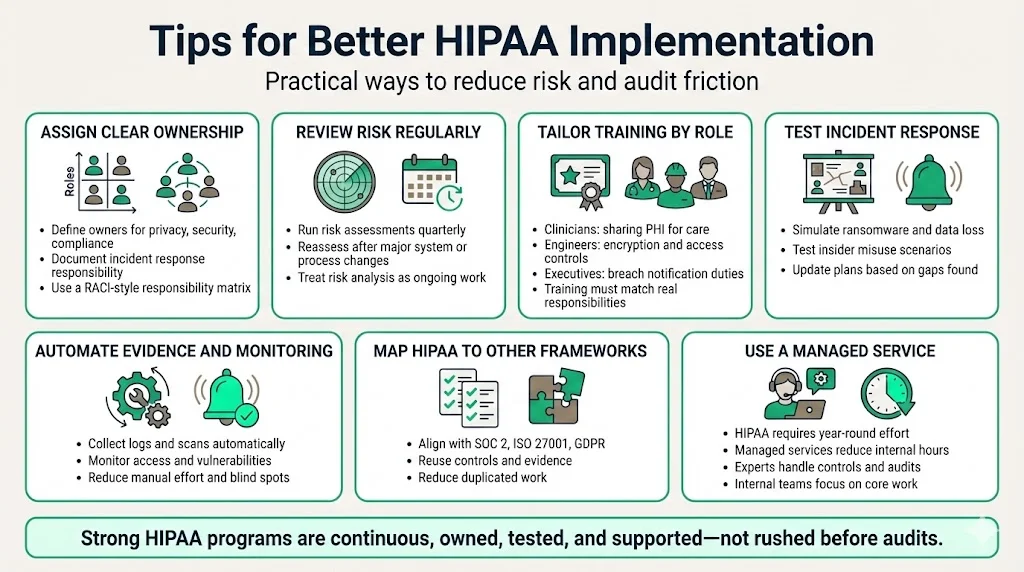
- Assign clear roles and responsibilities – Document who is responsible for privacy, security, compliance and incident response. Use a responsibility matrix to clarify who does what.
- Conduct regular risk assessments – Don’t treat risk analysis as a one‑time project. Review risks quarterly and whenever significant changes happen.
- Provide timely and relevant training – Tailor training to specific roles. Clinicians need to know when they can share PHI for treatment; engineers need to understand encryption requirements; executives need to grasp breach notification obligations.
- Test incident response plans – Run tabletop exercises with scenarios like ransomware, lost devices or insider snooping. Identify gaps and update plans.
- Use automation and monitoring – Adopt tools that automatically collect evidence (access logs, vulnerability scans) and alert on anomalies. Automation reduces manual work and catches issues earlier.
- Integrate HIPAA with other frameworks – Many controls overlap with SOC 2, ISO 27001 and GDPR. Use cross‑mapping to avoid duplication. For example, SOC 2’s access reviews map to HIPAA administrative safeguards; ISO 27001’s Annex A includes controls for physical security, network security and supplier relationships.
- Partner with a managed service – HIPAA compliance is a continuous workload. Teams often underestimate the hours required to design controls, collect evidence and prepare for audits. Konfirmity’s end‑to‑end managed service can reduce internal effort to around 75 hours per year, compared with 550–600 hours when self‑managed, according to our delivery data. With our human experts handling control implementation, observation windows and auditor coordination, clients focus on caring for patients and shipping software.
Conclusion
HIPAA compliance is an ongoing program, not a checkbox. The rising cost of healthcare breaches—$7.42 million on average in 2025m—and the surge in investigations (over 374,000 complaints since 2003) show that the risks are growing. Meeting HIPAA Roles And Responsibilities means understanding who is regulated, what each rule demands, and how to build safeguards that stand up to auditors, regulators and attackers. It requires clear leadership roles, documented policies, strong technical controls and prepared incident response.
Organizations that treat compliance as a one‑time exercise often struggle when incidents occur or when large buyers request evidence. Instead, start with security and arrive at compliance. Design controls inside your stack, automate evidence collection, and involve dedicated experts who stay engaged throughout the year. Whether you’re a hospital, a biotech startup or a billing service, make HIPAA part of everyday operations. Security that looks good on paper but fails under pressure is a liability. Real compliance comes from durable programs, continuous monitoring, and committed teams.
FAQs
1) What are the responsibilities of HIPAA?
HIPAA requires protecting the privacy of PHI, securing ePHI through administrative, physical and technical safeguards, providing training to workforce members, limiting uses and disclosures to the minimum necessary, managing third‑party risk through BAAs, monitoring compliance through audits and logs, and reporting breaches. Covered entities and business associates must maintain documentation for at least six years.
2) What are the five HIPAA rules?
The five commonly cited HIPAA rules are the Privacy Rule, Security Rule, Breach Notification Rule, Enforcement Rule, and Transactions and Code Sets Rule (often combined with the Unique Identifiers Rule). The Privacy Rule governs how PHI is used and disclosed; the Security Rule mandates safeguards for ePHI; the Breach Notification Rule requires reporting of certain incidents; the Enforcement Rule sets penalties; and the Transactions and Code Sets Rule standardizes electronic transactions. Some resources also discuss the Omnibus Rule (HITECH Act amendments) and the HIPAA Final Rule that consolidated amendments in 2013.
3) What are the three HIPAA rules?
Sometimes, only the Privacy, Security and Breach Notification Rules are referenced because they contain the core operational requirements. The Privacy Rule addresses permissible uses and disclosures; the Security Rule requires risk assessments and safeguards for ePHI; the Breach Notification Rule sets reporting obligations.
4) What are the three functions of HIPAA?
HIPAA serves three main functions: (1) protecting patient privacy by restricting how PHI is used and shared; (2) securing ePHI through administrative, physical and technical safeguards; and (3) providing enforcement and breach reporting frameworks to ensure accountability. These functions promote trust in healthcare, encourage adoption of digital tools and create a level playing field for organizations handling sensitive data.





.svg)





.svg)
.svg)