Most enterprise buyers now request proof of security and compliance before they sign a contract. A HIPAA Audit Timeline isn’t just paperwork – it is how regulators verify that electronic protected health information (ePHI) is handled properly. In late 2024 the Office for Civil Rights (OCR) resumed audits after a long pause because ransomware and destructive malware had hit hospitals and clinics hard. These audits will examine fifty covered entities and business associates, focusing on key parts of the Security Rule most relevant to hacking and ransomware. Understanding how an audit unfolds over time allows healthcare leaders to prepare evidence, strengthen controls and avoid costly penalties. In this article I explain the phases of the HIPAA Audit Timeline, share operational insights from more than 6,000 audits we have supported at Konfirmity, and offer concrete practices that keep your program ready all year.
What Is a HIPAA Audit?
A HIPAA audit assesses whether a covered entity or business associate is meeting the requirements of the Privacy Rule, Security Rule and Breach Notification Rule. The Privacy Rule governs how personal health information can be used or disclosed; the Security Rule sets administrative, technical and physical safeguards to protect ePHI; and the Breach Notification Rule defines when individuals and regulators must be notified after an incident. The OCR conducts external audits, but many organizations also run internal audits to check their controls before the regulator arrives. According to the American Health Information Management Association’s toolkit, when OCR selected entities for Phase 2 desk audits it contacted them by email and asked them to submit documentation through the OCR portal within ten days. Desk audits focus on specific controls and are performed remotely; on‑site audits are more comprehensive and include interviews and facility tours. The HIPAA Audit Timeline must therefore account for both remote document reviews and on‑site testing.
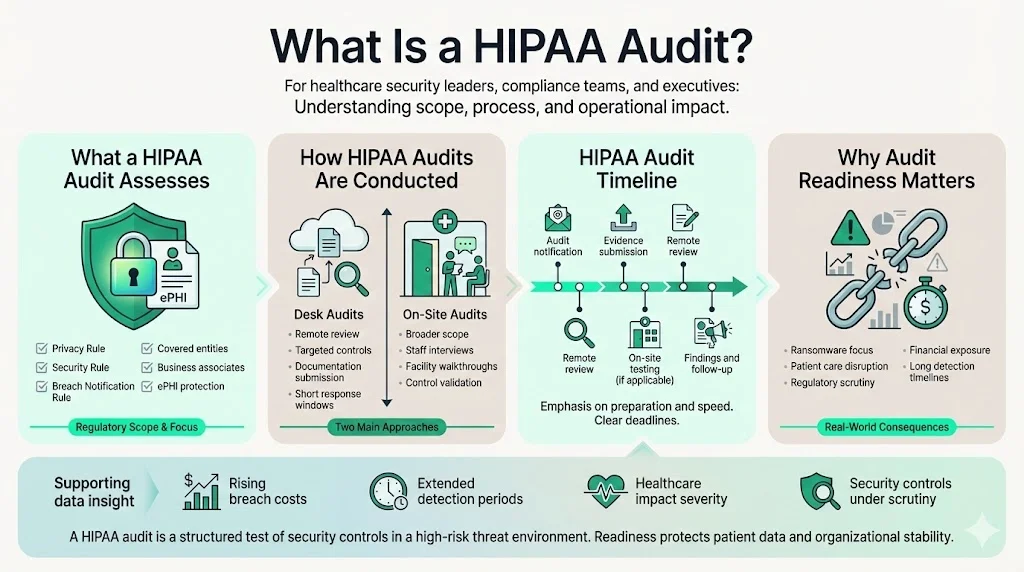
The return of the audit program reflects broader security pressures. NIST’s February 2024 update to Special Publication 800‑66 emphasises that ePHI created, received, maintained or transmitted by regulated entities must be protected against anticipated threats and impermissible uses. The OCR’s 2024–2025 audits concentrate on hacking and ransomware, underlining how a breach can disrupt patient care and have “massive financial ramifications”. In 2025 IBM reported that healthcare data breaches in the United States cost an average of $10.22 million, up from $9.36 million in 2024. Healthcare breaches also took longer to identify and contain than other industries, averaging 279 days. These figures underscore why security controls and audit readiness are not optional.
Audit Timeline Overview
The HIPAA Audit Timeline covers several stages from ongoing compliance through enforcement. Before an audit, organizations should operate in a state of continuous compliance: performing risk assessments, training staff and updating documentation. A formal audit typically begins when the OCR notifies an entity. Selection can be random, triggered by breach reports or complaints, or part of scheduled program cycles. In 2017 the OCR conducted a broad set of audits; it assessed only eight of the 180 HIPAA requirements and imposed no penalties, leading the Office of Inspector General to recommend a more extensive program. The resumed program responds to that recommendation and emphasises risk analysis and risk management.
Audits generally proceed through phases:
- Phase 0 – Continuous Compliance: Ongoing risk assessments, policies and monitoring.
- Day 1–30 – Immediate Response & Initial Documentation: Submission of requested documents within tight timeframes.
- Day 31–90 – Detailed Risk Assessment & Document Review: Auditors evaluate risk analysis, administrative, technical and physical safeguards.
- Day 91–120 – Interviews, Testing & Findings: On‑site visits, interviews and control testing.
- Day 121–150 – Audit Report & Corrective Actions: Findings are issued and corrective actions defined.
- Post‑Audit – Monitoring & Future Audit Readiness: Implementing remediation and maintaining readiness.
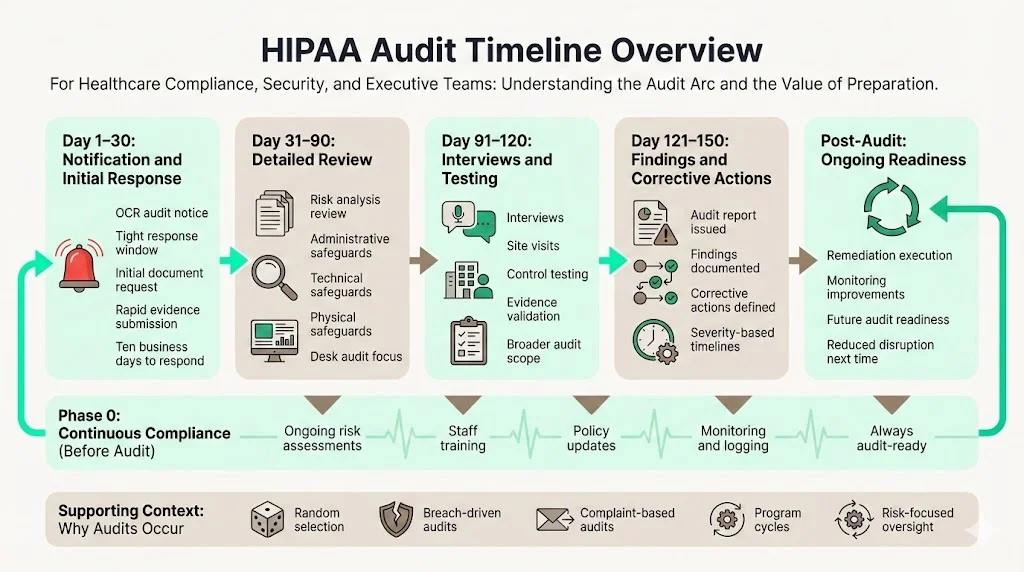
These ranges are approximate – actual durations vary depending on scope and the entity’s maturity. However, they provide a practical HIPAA Audit Timeline framework for planning. Covered entities selected for an audit typically have only ten business days to respond to initial documentation requests. After the initial submission, document review and risk assessment can take several weeks, followed by interviews and site visits that may span a month. Once findings are delivered, remediation deadlines vary based on the severity of issues.
Phase 0: Continuous Compliance (Pre‑Audit Preparation)
Waiting until an OCR notice arrives is a mistake. At Konfirmity we treat compliance as an ongoing process. Our experience across thousands of audits shows that organizations who conduct regular risk assessments, keep policies current and track training reduce the time and stress of an official review. The HIPAA Security Rule requires entities to protect ePHI against anticipated threats. Continuous compliance means aligning with that expectation every day.
Key tasks during this phase include:
- Assign privacy and security officers. Designate accountable leaders who oversee HIPAA programs and coordinate with legal and IT teams.
- Centralize documentation. Maintain a living repository of policies, procedures, risk assessments, incident reports, audit logs and training records. When OCR requests documents, having them organized cuts response time from weeks to days.
- Conduct periodic risk assessments. NIST advocates regular risk analysis and risk management. We recommend at least quarterly assessments, with additional reviews after significant changes such as system migrations or mergers.
- Train staff and track attendance. HIPAA requires workforce training. Use a learning management system to deliver training modules and record participation. Auditors often ask for evidence of attendance and exam results.
- Perform internal audits. Simulate OCR requests by reviewing your program against the audit protocol. Identify gaps early and remediate them before regulators call.
Routine exercises make a huge difference. Entities that perform mock audits and maintain complete evidence sets often respond to OCR requests within three days, well under the ten‑day limit. Conversely, those who treat compliance as a one‑off event scramble to collect policies, sometimes missing required items like business associate agreements or breach notification procedures.
Day 1–30: Immediate Response & Initial Documentation
When the OCR selects an organization for an audit, the clock starts. The agency sends a notification and may request verification of contact details. Healthicity’s Stage 2 audit guidance warns that organizations have only ten days to upload the requested documents and respond to inquiries. The AHIMA toolkit confirms that selected covered entities were asked to submit documentation via the OCR portal within ten days. The initial request typically covers:
- Privacy policies and procedures. Current policies governing use and disclosure of PHI, notice of privacy practices and patient rights.
- Security measures. Documentation of administrative, technical and physical safeguards; network diagrams; encryption practices; and incident response plans.
- Breach reports and incident logs. Records of past breaches and investigations, including reports filed under the Breach Notification Rule.
- Risk assessments. The latest security risk analysis and any follow‑up management plans.
- Training logs. Evidence of workforce training completion, attendance and content.
- Audit trails. System logs showing user access, authentication, and changes to ePHI.
At Konfirmity we have optimized this phase. Our clients leverage our evidence repository to provide auditors with structured packages. We often respond within a week, supporting an efficient process. Entities without centralized documentation sometimes take the entire ten days or miss the deadline, increasing scrutiny.
Day 31–90: Detailed Risk Assessment & Document Review
After initial documents are submitted, auditors review evidence against regulatory requirements. They may request additional details or clarifications. This period often involves deep dives into risk assessment, controls and operational practices. NIST’s guidance emphasises that regulated entities must protect ePHI against anticipated threats, hazards and impermissible uses. Auditors therefore examine whether your risk analysis identifies threats like ransomware, misconfigured access controls and legacy systems.
Focus Areas During Document Review
- Administrative safeguards. Policies, procedures, workforce training records, sanction policies and contingency planning. Auditors compare training logs to staff rosters to confirm full participation.
- Technical safeguards. Access controls, authentication mechanisms, encryption at rest and in transit, audit logging, intrusion detection and vulnerability management. In our experience, incomplete logging and weak change‑management practices are common findings.
- Physical safeguards. Facility access controls, visitor management, device security and environmental protections. Auditors may ask for photographs or diagrams showing how servers and workstations are secured.
Auditors also scrutinize business associate agreements and vendor risk management. In the 2016‑2017 audit program the OCR found that many entities lacked formal contracts with their vendors and had not verified that business associates were themselves compliant. As of 2025 the resumed program focuses on risk analysis and risk management, so thorough documentation here is vital.
Day 91–120: Interviews, Testing & Findings
Once document review is complete, auditors often schedule on‑site or virtual interviews with key personnel. The AHIMA toolkit describes how Phase 2 audits included on‑site visits after desk audits and were designed to examine compliance mechanisms and discover risks not surfaced through complaint investigations. During this phase auditors may:
- Interview privacy and security officers, IT leaders and clinicians. They test understanding of policies and real‑world practices.
- Walk through facilities. Assess how physical access is controlled, whether visitors sign in, and how equipment is secured.
- Demonstrate system controls. Show how user provisioning occurs, how multifactor authentication is enforced, and how logs are reviewed.
- Verify training effectiveness. Spot‑check staff knowledge by asking how to report an incident or where policies are stored.
The objective is to see whether documented controls operate in practice. For example, a client may claim that access reviews are conducted quarterly, but auditors might ask for evidence of the last three reviews. At Konfirmity we prepare clients with mock interviews and ensure they can display screenshots, logs and change tickets on demand. The HIPAA Audit Timeline allows roughly one month for this phase, but schedules can vary depending on the complexity of the environment.
Day 121–150: Audit Report & Corrective Actions
After the fieldwork, auditors compile a draft report detailing observations, non‑conformities and recommendations. The entity usually has an opportunity to respond, clarify context and describe corrective actions taken. In the 2011‑2012 pilot program, OCR provided draft reports to auditees and allowed them to discuss concerns and corrective actions before the final report. Today the process is similar. The final report categorizes findings into observations (minor issues), required corrective actions or formal remediation plans with deadlines.
Our experience shows that many findings relate to incomplete risk analyses, missing documentation, outdated policies and insufficient audit logging. The penalties for non‑compliance can be significant. Emitrr’s 2025 guide states that penalties range from $137 to $2,067,813 depending on the severity of violations. However, the OCR’s aim is often remediation rather than punishment. Demonstrating recognized security practices and a proactive remediation plan can mitigate fines. Organizations should treat the corrective action plan as a project: assign owners, set deadlines, track progress and integrate improvements into daily operations. At Konfirmity we provide remediation tracking and ensure that corrective actions cross‑map to other frameworks such as SOC 2 and ISO 27001 so improvements have broad benefits.
Post‑Audit: Monitoring & Future Audit Readiness
Once the audit concludes, the work continues. Maintaining compliance and preparing for future audits requires ongoing monitoring, risk management and program updates. Entities that adopt continuous monitoring platforms, perform quarterly access reviews and update policies promptly stay ready for surprise requests. The HITECH Act’s safe‑harbor amendment encourages regulated entities to adopt recognized security practices for at least twelve months prior to a breach; doing so can reduce penalties and shorten investigations. Organizations should therefore invest in frameworks such as the NIST Cybersecurity Framework or SOC 2, which provide structured controls and evidence that can be reused across multiple audits.
At Konfirmity we operate year‑round as a managed service. Our dedicated team monitors vulnerabilities, manages incident response and conducts continuous evidence collection. Clients typically spend around 75 hours per year on compliance tasks with our service, compared to 550–600 hours with self‑managed programs. We also map controls across HIPAA, SOC 2 and ISO 27001 so evidence collected for one framework supports others. This cross‑framework approach saves time and ensures that improvements are not siloed.
Sample Audit Schedule
The table below summarizes the timeline by week and month. It is a practical guide rather than a fixed schedule. Real audits may overlap phases or adjust durations based on findings.
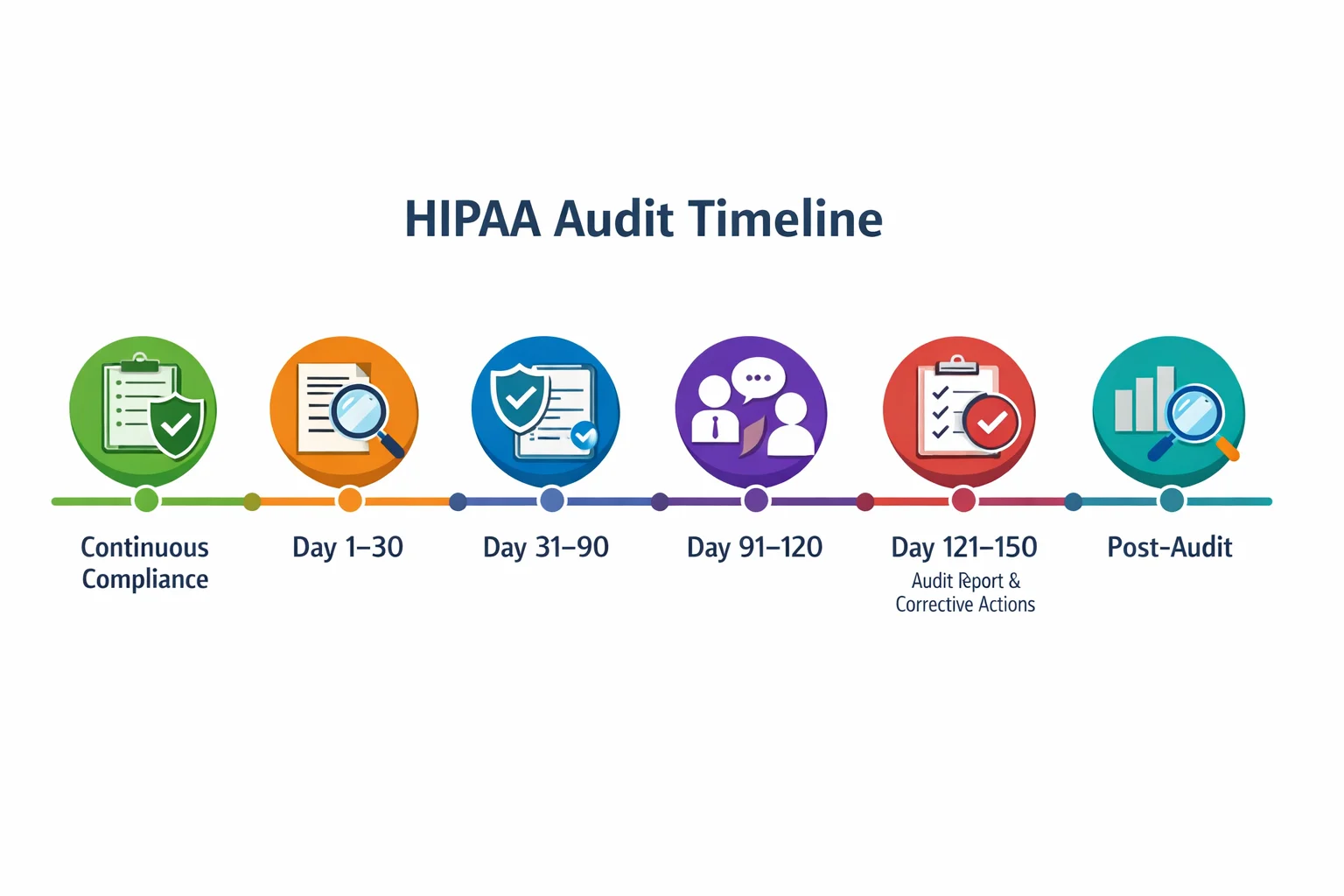
Visual Timeline
To complement the table, the following graphic offers a visual representation of the audit timeline. It shows the sequence of phases and underscores that continuous compliance anchors the process.
Common Challenges & How to Handle Them
Based on our delivery work, several recurring challenges slow down audits:
- Gaps in documentation. Many organizations cannot find signed business associate agreements, outdated privacy policies or completed risk assessments. Remedy: maintain a central repository and schedule quarterly document reviews.
- Missing training records. Auditors often ask for proof that every workforce member completed HIPAA training. Remedy: use a learning management system that records completion dates and test scores, and reconciles the roster regularly.
- Incomplete risk assessment evidence. Some entities perform assessments but fail to keep evidence showing how risks were identified and mitigated. Remedy: document the methodology, threat list, findings and action plan; store supporting artifacts such as vulnerability scan results and penetration test reports.
- Legacy systems lacking audit logging. Older electronic health record systems may not produce adequate audit logs. Remedy: implement compensating controls such as network‑level monitoring, upgrade systems where possible, and document the limitations with mitigation steps.
- Vendor sprawl. Covered entities often rely on dozens of third‑party vendors without proper due diligence. Remedy: maintain an inventory of vendors, execute business associate agreements and perform periodic assessments of their security posture.
- Weak change management. Auditors frequently find that access reviews and change‑management approvals are informal or undocumented. Remedy: institute change‑management workflows with approval checkpoints, logging and periodic audits.
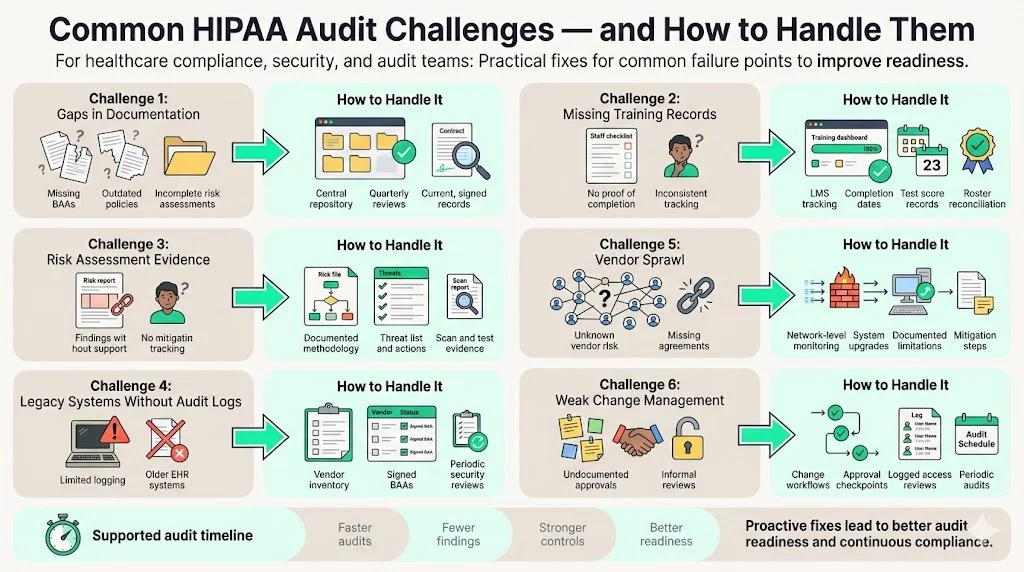
By addressing these challenges proactively, organizations shorten the audit process and improve security posture.
Cross‑Framework Considerations & Market Impact
Healthcare organisations seldom operate under HIPAA alone. Enterprise buyers frequently ask for SOC 2 Type II or ISO 27001 certification alongside evidence of HIPAA compliance. Controls such as access reviews, encryption, vulnerability management and incident response support all these frameworks. According to Quantarra's 2025 analysis, compliance teams work in a many‑to‑many model where one control supports multiple frameworks, evidence must be reused but presented differently, and manual cross referencing causes duplicated work, inconsistent evidence and audit fatigue. To respond to due‑diligence requests quickly, healthcare companies should adopt a unified control mapping strategy.
Konfirmity implements this principle by mapping controls across HIPAA, SOC 2 and ISO 27001. For example, a single least‑privilege access control can satisfy HIPAA's technical safeguards, SOC 2's Security and Confidentiality criteria, and ISO 27001's Annex A controls. We define controls once, collect evidence continuously and organise it in a way that auditors for different standards can trace without rework. This approach reduces duplicated work and accelerates sales cycles. For complex procurements, we provide both the HIPAA report and the SOC 2 Type II attestation, demonstrating that controls are not just documented but operating over an observation period. Recognised security practices under the HITECH safe‑harbor amendment and cross‑framework readiness also mitigate penalties if a breach occurs. By investing in cross‑framework compliance, healthcare leaders can meet contractual requirements, satisfy regulators and secure their data without burning out their teams.
Conclusion
Healthcare organizations face relentless pressure to protect patient data while enabling efficient operations. The HIPAA Audit Timeline is not an arbitrary schedule; it reflects how regulators verify that administrative, technical and physical safeguards are working. Understanding each phase – from continuous compliance through post‑audit monitoring – helps executives allocate resources, assign responsibilities and avoid unpleasant surprises. The resumed OCR audit program underscores that audits are here to stay, while rising breach costs reveal the real price of inadequate security. A disciplined, year‑round program built on solid security controls and comprehensive evidence is the surest way to satisfy auditors and protect patients.
Konfirmity’s human‑led managed service demonstrates that good security and compliance can coexist with operational efficiency. By integrating controls into your stack, automating evidence collection and providing expert support, we reduce the burden on internal teams and improve audit outcomes. The choice is simple: invest in durable security and be ready when the OCR calls, or wait and hope – a gamble that grows riskier each year. Start with security and arrive at compliance.
FAQs
1. How long does a HIPAA audit usually take?
The full HIPAA Audit Timeline typically spans four to five months. After an organization receives notice, there is a ten‑day window to submit initial documentation. Document review and risk assessment take several weeks, followed by interviews and site visits. The final report and corrective actions phase may extend into the fifth month. The overall duration varies based on the scope of the audit and the entity’s preparedness.
2. What triggers a HIPAA audit?
Audits may be scheduled randomly, initiated after breach reports or complaints, or part of periodic program requirements. The 2024–2025 audits were launched in response to increasing ransomware incidents and an Office of Inspector General report that the previous program was too narrow. OCR director Melanie Fontes Rainer announced that new audits will focus on risk analysis and risk management.
3. Can a small healthcare provider be audited?
Yes. The HHS explicitly states that every covered entity and business associate is eligible, regardless of size. Small clinics, solo practices and regional labs have all been audited in past programs. The random selection process means any regulated entity could receive a notice. For small organizations, working with a partner like Konfirmity helps manage the evidence burden without overwhelming limited staff.
4. What happens if an audit finds non‑compliance?
Findings are categorized as observations, required corrective actions or remediation plans with deadlines. Organizations must prepare and implement a corrective action plan and may face civil monetary penalties if violations are serious. Penalties can range from a few hundred dollars to over two million dollars depending on severity. However, demonstrating proactive security practices and swift remediation often leads to reduced penalties. The safe‑harbor law also encourages entities to adopt recognized security practices for twelve months prior to a breach.





.svg)






.svg)
.svg)