Healthcare organisations face a torrent of cyber‑attacks. In 2023 the U.S. Office for Civil Rights (OCR) recorded 725 reported breaches and more than 133 million records were compromised. Early 2024 brought the largest healthcare breach on record, when ransomware at Change Healthcare exposed over 276 million records. These figures emphasise how intertwined healthcare is with tech-based services and how appealing it is to attackers. In response, the OCR’s 2024‑2025 program will audit about 50 covered entities and business associates, focusing on hacking and ransomware, while proposed updates to the HIPAA Security Rule will make multi‑factor authentication, encryption, and regular testing mandatory.
Because the stakes are so high, selecting the right HIPAA auditor is more than a formality. An auditor may be internal, external, or a regulator, but their role is to review how you handle protected health information (PHI/ePHI) under HIPAA’s Privacy, Security, and Breach Notification Rules. This HIPAA Auditor Selection Guide explains what to look for in an auditor—knowledge of compliance rules, risk management skills, vendor assessment, strong reporting, workforce training evaluation, credentials, and ongoing monitoring—and provides a process to follow. It is written for healthcare providers, insurers, clearinghouses, and business associates seeking a practical path to compliance.
A broader view shows why this HIPAA Auditor Selection Guide matters. Hackers do not discriminate between large hospitals and small clinics; they target any entity handling PHI. Vendors and subcontractors often hold large volumes of sensitive data, which compounds risk when they lack strong security. Business partners increasingly ask for assurance before entering into contracts. Engaging a qualified auditor demonstrates your commitment to patient privacy and inspires trust.
What Is a HIPAA Compliance Audit?
A HIPAA compliance audit is a systematic review of your administrative, physical, and technical controls to verify that you protect PHI in line with HIPAA. It covers policies and procedures, training, risk analysis, incident response planning, facility security, encryption, access management, audit logging, and documentation. NIST Special Publication 800‑66 Revision 2 emphasises that risk analysis and risk management underpin the HIPAA Security Rule. In practice, an auditor examines whether you have identified threats and vulnerabilities, implemented appropriate safeguards, and maintained evidence.
Internal teams, independent third‑party firms, or the OCR may perform audits. Internal audits provide early insight but must be conducted by staff not involved in day‑to‑day operations to remain objective. External auditors bring specialised expertise and certifications (e.g., CISA, CISSP, ISO 27001, HITRUST). OCR audits are regulatory; non‑cooperation or failure to remediate can lead to penalties.
More than simply checking documents, a thorough HIPAA audit digs into how each safeguard operates. Administrative safeguards cover governance structures, appointment of a privacy and security officer, workforce training, and risk management processes. Physical safeguards include facility access controls, workstation security, disposal of media, and device management. Technical safeguards focus on user authentication, encryption of data at rest and in transit, audit logs, and intrusion detection. The auditor also reviews contracts with business associates, incident response and disaster recovery plans, asset inventories, and breach notification procedures. By examining both design and operating effectiveness, the audit provides a thorough view of compliance and security.
Why HIPAA Audits Matter for Compliance and Risk Management
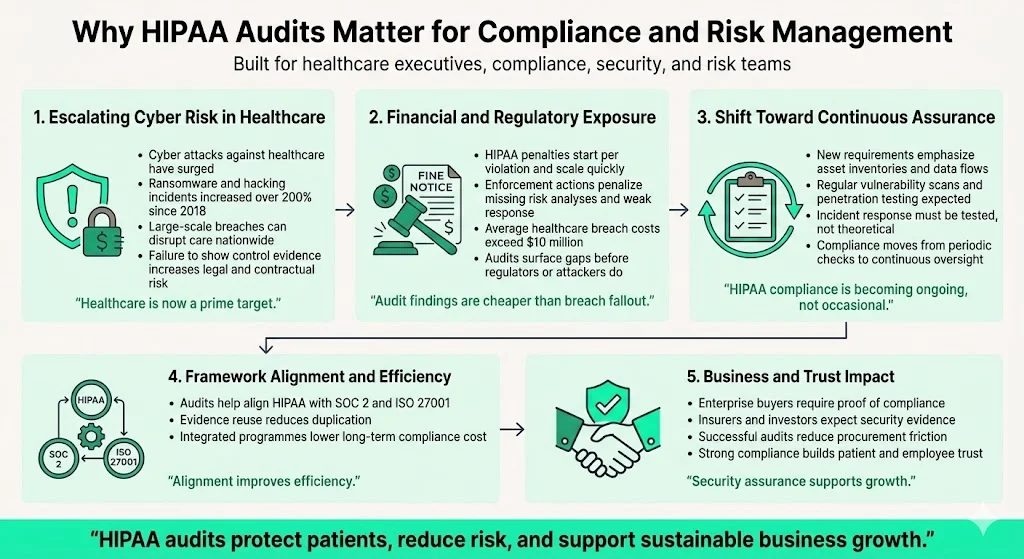
Cyber‑crime against healthcare has exploded. Hacking incidents and ransomware attacks increased by more than 200 percent between 2018 and September 2023. The Change Healthcare breach, which affected about 190 million individuals, showed how a single incident can disrupt care nationwide. Organisations that fail to demonstrate control implementation and evidence risk contractual penalties, lawsuits, and damaged trust.
HIPAA penalties can be severe. Civil monetary penalties start at $141 per violation and can exceed $71,000. Enforcement actions in 2025 resulted in fines of hundreds of thousands of dollars for entities that failed to conduct risk analyses or respond to incidents. At the same time, the average cost of a healthcare data breach surpassed $10 million. Audits therefore serve as a risk management tool to identify gaps before attackers or regulators do.
Proposed changes to the HIPAA Security Rule will require asset inventories, data flow mapping, twice‑yearly vulnerability scanning, annual penetration testing, and thorough incident response testing. Organisations must shift from occasional compliance activities to continuous assurance. A competent auditor can help you connect HIPAA with other frameworks like SOC 2 and ISO 27001, enabling evidence reuse and a more efficient security programme.
In addition to compliance obligations, audits support business growth. Enterprise clients, insurers, and investors regularly ask for security questionnaires, SOC 2 reports, and evidence of HIPAA compliance before signing contracts. Passing a well‑executed audit accelerates sales cycles and reduces friction during procurement. It also reassures patients and employees that the organisation values data protection. Without this foundation, deals may stall, insurance premiums may rise, and reputational harm may linger for years.
Main Criteria When Selecting a HIPAA Auditor
This HIPAA Auditor Selection Guide identifies seven criteria to evaluate. Using these criteria will help you distinguish between superficial assessments and audits that truly improve your security posture.
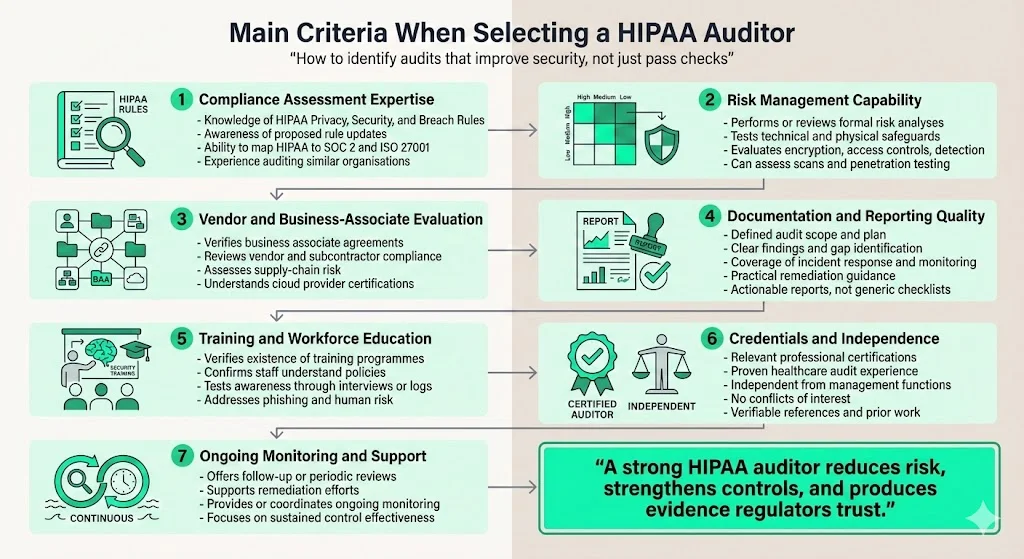
- Compliance assessment expertise: The auditor must know HIPAA’s Privacy, Security, and Breach Notification Rules and understand how proposed updates may affect safeguards. They should be able to map HIPAA controls to other frameworks and customize their approach to your organisation’s size and complexity. Ask whether they stay abreast of evolving guidance from the OCR and NIST and whether they have audited entities similar to yours.
- Risk management capability: Look for auditors who perform or review thorough risk analyses. They should test technical controls (encryption, access, intrusion detection) and physical safeguards and, if needed, conduct vulnerability scans and penetration tests.
- Vendor and business‑associate evaluation: Major breaches often originate with third parties. Auditors should verify that you have business associate agreements, evaluate vendor compliance, and assess supply‑chain risk. They should also understand cloud‑service provider certifications (e.g., SOC 2, ISO 27001) and how to assess subcontractors.
- Documentation and reporting: An effective audit follows a defined plan and produces a clear report with findings, gaps, and practical suggestions. Reports should address incident response, breach notification, and continuous monitoring, ensuring that policies and evidence are current and complete. Request a sample report to evaluate whether the auditor provides actionable guidance rather than generic checklists.
- Training and workforce education: Insider negligence is a common cause of breaches. The auditor should verify that training programmes exist and that staff understand policies and can recognise phishing and other threats. Ask how the auditor will test staff awareness, such as through interviews or reviewing training logs.
- Credentials and independence: Choose auditors with relevant certifications and a track record of healthcare audits. They should be independent of your management functions and free from conflicts of interest. Check references and ask for samples of previous reports. Independence ensures that findings are objective and credible to regulators and partners.
- Ongoing monitoring and support: Because threats and regulations change, auditors should offer or suggest follow‑up reviews, periodic audits, and remediation assistance. Ask whether they provide continuous monitoring services or collaborate with managed security providers to ensure that controls stay effective.
Step‑by‑Step Guide to Selecting the Right HIPAA Auditor
Follow this abbreviated process to apply the HIPAA Auditor Selection Guide. This HIPAA Auditor Selection Guide sets out practical steps that any organisation can follow to engage the right auditor:

- Define scope. Decide whether the audit covers privacy, security, and breach notification, or focuses on specific areas. Include vendor and business‑associate assessments if needed. Clarity on scope prevents misunderstandings later and ensures the auditor assesses the areas most important to your organisation.
- Build criteria and shortlist. Use the seven criteria above to create an evaluation matrix. Identify firms with healthcare experience and request information about certifications, past audits, and references. Create a weighted scorecard to compare candidates fairly.
- Request proposals and verify credentials. Ask shortlisted firms to outline audit methodology, timeline, deliverables, testing techniques, reporting style, remediation support, and cost. Confirm certifications and independence. Evaluate how well proposals connect with your scope and whether auditors will provide interim updates.
- Pilot assessment (optional). Run a small‑scope engagement to test compatibility and gauge the auditor’s communication and insight. Use this session to see how thoroughly they analyse a sample control and how clear their suggestions are.
- Select and contract. Choose the auditor, define scope and deliverables, set timelines, and ensure confidentiality and data handling practices are documented.
- Prepare internally. Appoint a privacy and security officer, update policies and procedures, conduct a preliminary risk analysis, train staff, and gather documentation. Organise evidence into categories (policies, risk assessments, training logs, vendor agreements, technical configurations) to speed the audit. Preparation reduces the time and stress during the audit and demonstrates commitment to compliance.
- Execute and monitor. Cooperate during fieldwork, remediate findings promptly, and establish a plan for regular audits and continuous monitoring. Consider the audit as a learning experience rather than a pass‑fail exam.
Example Scenarios and Auditor Choices
Small clinics and mid‑sized facilities: A single‑site practice with basic electronic health records may start with a focused assessment that verifies policies, workforce training, access controls, and incident response plans. An outpatient centre using cloud‑hosted systems should select an auditor who can assess both internal safeguards and vendor compliance. These organisations should prioritise cost‑effective audits that include clear suggestions and post‑audit training.
Large health systems and tech-based start‑ups: Multi‑site hospital networks and health‑tech companies need auditors with deep technical expertise and the ability to review complex infrastructures. These auditors should conduct risk analyses across multiple sites, perform vulnerability scans and penetration tests, and examine disaster recovery and vendor oversight. Start‑ups, which often build telemedicine platforms or connected devices, require auditors who understand secure development, encryption, APIs, and cross‑framework compliance. Continuous monitoring is vital because both large systems and new companies change quickly.
Common Pitfalls and How to Avoid Them
- Focusing on price over quality: The lowest fee may not provide the depth of assessment required. Consider the value of expertise and thoroughness.
- Using internal staff without independence: Internal auditors may overlook problems because they are too close to operations. Independent reviews provide objectivity.
- Ignoring vendor risk: Many breaches stem from business associates. Ensure your auditor reviews contracts and third‑party controls.
- Viewing compliance as a one‑time event: Regulations and threats change. Incorporate periodic risk assessments, training, and monitoring.
- Neglecting documentation and training: Keep policies current, maintain asset inventories, test incident response plans, and educate staff.
- Failing to act on findings: Some organisations ignore audit results. View findings as a roadmap for improvement and allocate resources for remediation.
Checklist for Selecting a HIPAA Auditor (2026)
What to Expect During a HIPAA Audit
A typical audit proceeds through predictable stages:
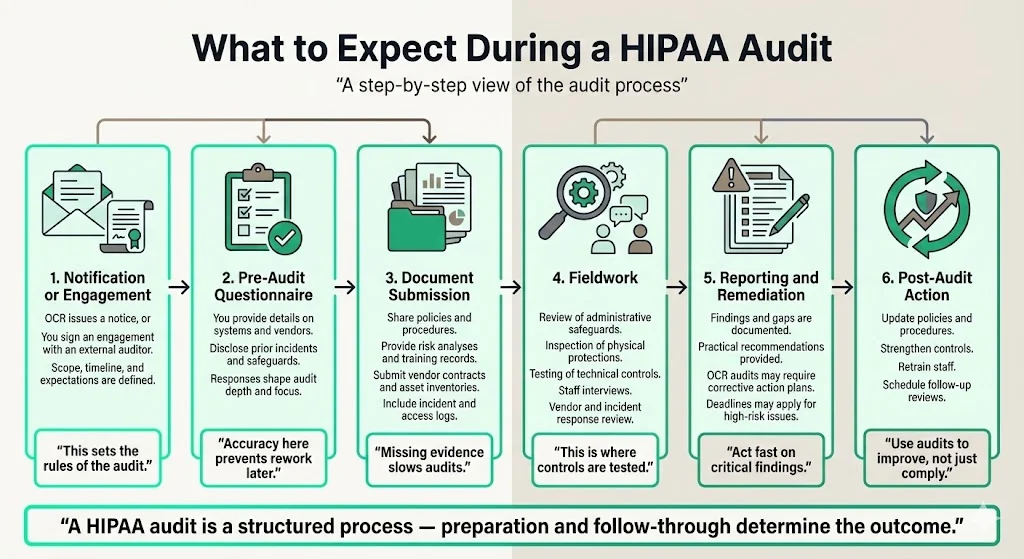
- Notification or engagement. You receive an OCR notice or sign a contract with an external auditor that sets scope and expectations.
- Pre‑audit questionnaire. You provide information about systems, vendors, and past incidents. Accuracy allows auditors to customize the review.
- Document submission. You share policies, procedures, risk analyses, training records, vendor contracts, incident logs, and asset inventories. Missing evidence can delay the process.
- Fieldwork. Auditors assess administrative, physical, and technical safeguards, interview staff, and test controls. They also examine vendor management and incident response readiness.
- Reporting and remediation. A report outlines findings, gaps, and suggestions. For OCR audits, corrective action plans may include deadlines. Address high‑risk issues promptly.
- Post‑audit action. Update policies, strengthen controls, re‑train staff, and schedule follow‑up assessments. Use the audit as an opportunity for continuous improvement.
Conclusion
Choosing the right auditor directly influences your ability to protect patient data, meet legal obligations, and maintain operational resilience. The HIPAA Auditor Selection Guide outlined here stresses the importance of assessing compliance knowledge, risk management skills, vendor oversight, reporting quality, training evaluation, credentials, and post‑audit support. Following the step‑by‑step process will help you narrow your options, verify credentials, and prepare effectively. Continuous monitoring and periodic reassessments ensure that compliance is more than a one‑time activity.
At Konfirmity, we have supported over 6,000 audits across 25 years. Our human‑led managed service accelerates readiness and reduces internal effort by embedding controls in your daily operations and collecting evidence continuously. By connecting HIPAA with SOC 2, ISO 27001, and GDPR, we enable evidence reuse and emphasize real security tasks such as least‑privilege access reviews, vulnerability triage, vendor risk workflows, and strong encryption. When controls are effective, compliance follows naturally. Use this HIPAA Auditor Selection Guide to select a partner who prioritises security outcomes over paperwork and helps your organisation build resilience. In the end, the HIPAA Auditor Selection Guide is an investment in trust and operational excellence.
FAQ
1. How should you prepare for a HIPAA audit?
Designate a privacy and security officer, map how PHI is stored and transmitted, conduct a risk analysis, update policies and procedures, train staff, and confirm that business associate agreements are in place. Conducting a pre‑audit gap analysis helps you address deficiencies before the formal assessment.
2. What are the four “C’s” of auditing?
Many internal audit frameworks refer to competence, confidentiality, communication, and collaboration. These principles ensure the auditor has the necessary skills, protects sensitive information, shares clear findings, and works constructively with the organisation.
3. Who conducts HIPAA audits?
The OCR performs audits of covered entities and business associates. Organisations also hire independent auditors or conduct internal audits to meet contractual obligations and manage risk.
4. What entities are subject to HIPAA audits?
Covered entities (healthcare providers, health plans, clearinghouses), business associates (vendors handling PHI for covered entities), and subcontractors of business associates must comply.
5. What are common HIPAA audit findings?
Many audits uncover missing or outdated risk analyses, inadequate access controls, lack of encryption, insufficient workforce training, incomplete business associate agreements, and gaps in incident response or logging. By learning from common findings, organisations can prioritise improvements and strengthen their programme.





.svg)






.svg)
.svg)