The healthcare sector depends on trust. Patients entrust providers and insurers with deeply personal medical histories, genetic information, and insurance details. Under U.S. law this data is protected health information (PHI). HIPAA—the Health Insurance Portability and Accountability Act—created a legal framework to govern how PHI can be used and disclosed. However, rules and high‑stakes penalties alone do not keep data safe. Real security comes from operational discipline: mapping data flows, obtaining valid authorizations, enforcing data use restrictions, and logging every action. That is what HIPAA Consent Management is about.
Consent management in healthcare refers to the systems and processes by which organisations obtain, document, monitor, and act on patients’ authorisations for data use. It links patient authorisation, consent forms, electronic consent, data privacy, data security, and audit trails. In practice, it is the operational glue between the HIPAA Privacy Rule, the HIPAA Security Rule, state privacy laws, business associate agreements, and the technical systems that store and process ePHI.
For healthcare companies, getting consent management wrong is costly. The average cost of a healthcare data breach in 2025 reached US$7.42 million, with U.S. breaches averaging US$10.22 million due to fines and class‑action lawsuits. OCR’s 2024–2025 audit program targets cyber‑security vulnerabilities and plans to audit roughly 50 covered entities and business associates. OCR’s enforcement activity is increasing; since January 2024, only 0.001 % of regulated entities have resolved an enforcement action, but the penalties have been severe. In 2025, Warby Parker paid US$1.5 million after failing to conduct a HIPAA‑compliant risk analysis and manage system activity logs. Failure to manage consent properly drives many of these cases.
This article explains why HIPAA Consent Management matters, defines core terms, outlines regulatory obligations, proposes a five‑step process for healthcare teams, offers templates and examples, and concludes with best practices and FAQs. We will anchor the discussion in HIPAA but cross‑reference SOC 2, ISO 27001, GDPR, and NIST guidance where relevant. As a managed service provider that has supported 6,000+ audits over 25 years, Konfirmity brings practitioner insights on what works and what fails in the field.
HIPAA: Regulatory and Compliance Foundation
The HIPAA Privacy Rule
The HIPAA Privacy Rule dictates how covered entities and business associates may use and disclose PHI. It applies to any form of PHI—paper or electronic—and sets baseline conditions for uses and disclosures. Several provisions are particularly relevant to consent management:
- Permitted uses and disclosures: Covered entities may use PHI for treatment, payment, and health‑care operations (TPO) without patient authorisation. They may also share PHI for public interest activities (e.g., public health, law enforcement) and incidental uses when reasonable safeguards are in place. Uses outside these categories generally require explicit written authorization.
- Authorisation content: When authorisation is required, the Privacy Rule mandates that it be written in plain language and specify the data to be disclosed, the purpose, the recipient, an expiration date/event, and the right to revoke. Minimum necessary standards apply; organisations should disclose only the PHI needed for a given purpose.
- Individual rights: Patients have the right to access their data, request amendments, and receive an accounting of disclosures. They can revoke authorisation at any time except to the extent actions have already been taken.
The HIPAA Security Rule
The Security Rule covers electronic PHI (ePHI). It requires regulated entities to “ensure the confidentiality, integrity, and availability of all ePHI that [they] create, receive, maintain, or transmit” and to protect against reasonably anticipated threats and uses/disclosures not permitted by the Privacy Rule. Entities must also ensure workforce compliance. NIST SP 800‑66 Revision 2 (February 2024) explains that confidentiality means data is not made available to unauthorised persons; integrity means data has not been altered or destroyed; and availability means data is accessible upon demand. The Security Rule divides safeguards into administrative, physical, and technical controls. Examples include:
- Administrative: Conducting risk analyses, assigning security responsibility, workforce training, sanction policies, and contingency planning.
- Physical: Controlling facility access, device security, and workstation policies.
- Technical: Access controls, unique user IDs, audit controls, integrity mechanisms, encryption, and transmission security.
HHS has proposed significant updates to the Security Rule. The December 2024 draft (published Jan 6 2025) removes the distinction between required and addressable specifications and includes new requirements such as technology asset inventories, annual penetration tests, vulnerability scanning every six months, mandatory multi‑factor authentication, encryption of all ePHI at rest and in transit, network segmentation, and annual verification of business associates’ security measures. The public comment period closed in March 2025; a final rule is expected in late 2025.
State Privacy Laws and Other Frameworks
HIPAA does not cover all health‑related data. Apps, fitness devices, and mental‑health services often fall outside HIPAA’s scope, prompting states to pass their own laws. Washington’s My Health, My Data Act (2023) applies to “regulated entities” and covers sensitive categories like gender‑affirming care, reproductive health information, biometric and genetic data, and precise location. It requires explicit consent for collection and disclosure of health data beyond what HIPAA demands. Nevada’s Consumer Health Data Privacy Law (2023) and Virginia’s Consumer Data Protection Act have similar provisions. New York and Minnesota have passed fertility‑related privacy laws.
International frameworks also influence HIPAA consent management. The GDPR requires data controllers to obtain explicit consent for processing special categories of personal data (e.g., health, biometric) and emphasises purpose limitation and data minimisation. ISO 27001:2022 mandates that organisations define an information security management system (ISMS), perform risk assessments, document controls, and conduct internal audits. SOC 2 is a voluntary attestation under the AICPA’s Trust Services Criteria, covering security, availability, processing integrity, confidentiality, and privacy; a Type 2 audit typically spans 3–12 months after a readiness period. These frameworks share common themes: risk‑based controls, access reviews, incident response, and continuous monitoring. Konfirmity leverages cross‑framework mappings to reuse controls across HIPAA, SOC 2, and ISO 27001, reducing time to audit readiness.
What “Consent” Means Under HIPAA
The term “consent” is often used loosely, but HIPAA draws a sharp line between authorisation and permitted uses/disclosures.
- Authorisation is a written permission from the patient to use or disclose PHI for purposes not otherwise allowed by HIPAA. For example, marketing communications or sharing data with third‑party analytics vendors generally require authorisation. Authorisations must specify recipient, purpose, data, expiration, and revocation rights.
- Permitted uses/disclosures include treatment, payment, and health‑care operations (TPO), public interest activities, and disclosures to the individual. These do not require authorisation but are still subject to minimum necessary and other safeguards.
The practical implication is that consent management is largely about managing authorisations for non‑TPO uses. Some organisations erroneously rely on generic consent forms to cover all processing. This is risky: regulators view consent as context‑specific. For instance, using PHI for clinical research may require a separate authorisation; the authorisation for research must state whether PHI will be de‑identified, whether data will be shared with sponsors, and whether the participant can revoke consent without affecting care.
Individual control is central to HIPAA. Patients can revoke authorisations at any time, and organisations must honour revocations promptly. They also have the right to restrict certain disclosures and request confidential communications. Effective HIPAA Consent Management ensures that these rights are operationalised across departments and systems.
Key Regulatory Obligations for Consent Management
Consent management intersects with multiple HIPAA provisions and enforcement trends. Key obligations include:
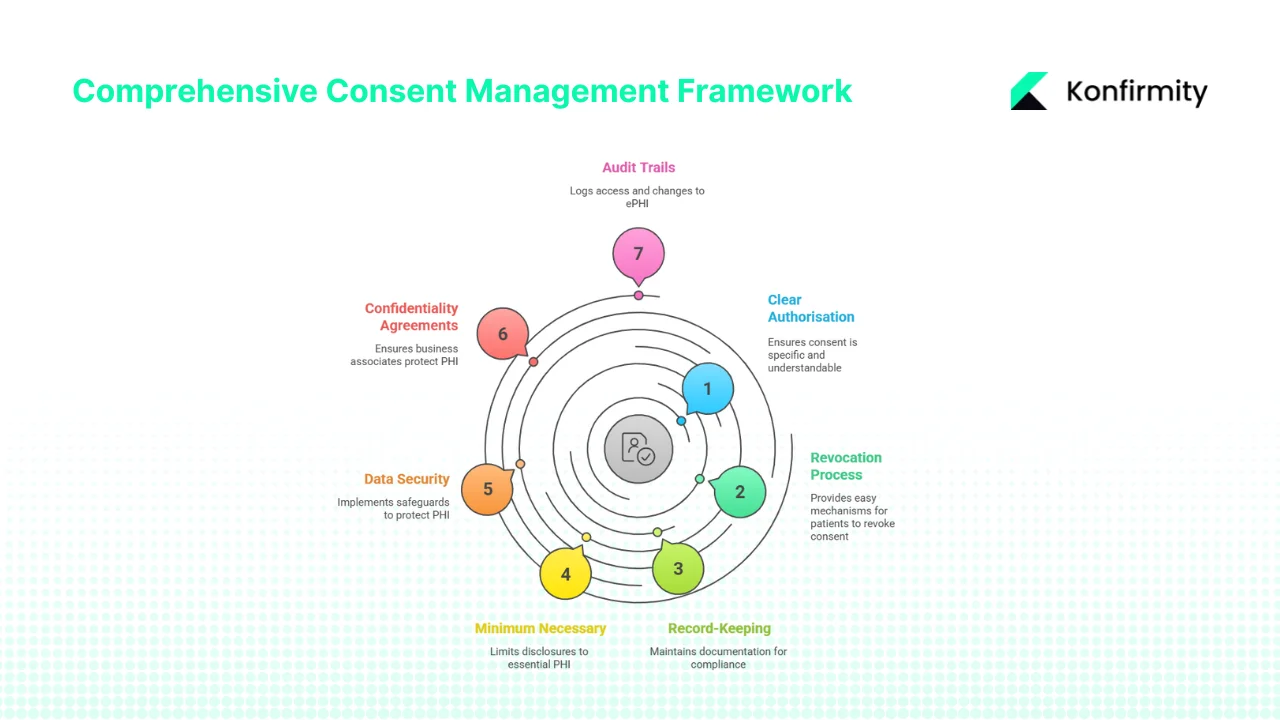
- Clear, specific authorisation: Authorisations must be written in plain language and contain the required elements: specific PHI, purpose, recipients, expiration, and revocation rights. Pre‑checked boxes or broad “blanket” consents are insufficient.
- Revocation process: Organisations must provide patients with an easy mechanism to revoke authorisation. Revocations should be logged and propagated across systems to prevent further use or disclosure.
- Record‑keeping: HIPAA requires covered entities and business associates to maintain authorisation documentation for at least six years from its creation or the date it last was in effect. Tracking date, version, and patient ID is essential.
- Minimum necessary: Even when authorisation is obtained, disclosures should be limited to the minimum amount of PHI necessary to fulfill the stated purpose.
- Data security: The Security Rule mandates administrative, physical, and technical safeguards. Risk analysis, workforce training, unique user IDs, audit controls, and encryption are all relevant. Proposed updates will require annual penetration tests and multi‑factor authentication.
- Confidentiality agreements and business associate agreements (BAAs): Covered entities must ensure that business associates protect PHI through written agreements. BAAs should specify permitted uses/disclosures, safeguard requirements, and breach notification obligations.
- Audit trails: Entities must log access and changes to ePHI. NIST emphasises that audit trails support incident response and compliance verification. Proposed Security Rule updates will require annual reviews and testing of security measures.
What Is HIPAA Consent Management?
HIPAA Consent Management is the organised approach by which healthcare organisations obtain, document, track, enforce, and review patient authorisations for data use. It sits at the intersection of legal requirements and operational workflows. Key components:
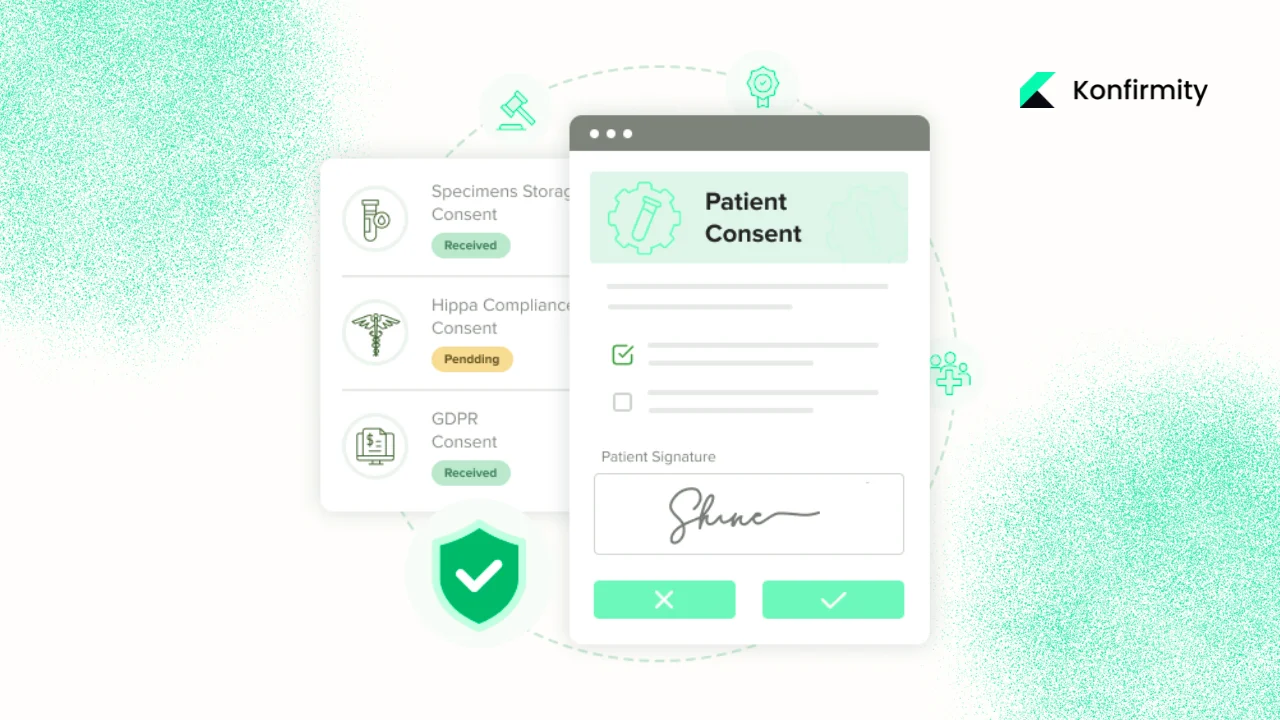
- Systems and processes: Tools for electronic consent (e‑signature platforms, patient portals), databases to store consent records, workflows to tie consent status to data access, and dashboards to monitor compliance.
- Linkage to authorisation: Each consent record must map to a specific authorisation form and version. When a patient gives authorisation through the portal, the system logs the form version, date, and details. This allows auditors to confirm that data use matches the authorisation.
- Monitoring and enforcement: Consent status must influence downstream data flows. For example, if a patient revokes authorisation for marketing communications, the CRM and email systems must reflect this change. Access management and data integration must be synced to the consent database.
- Adaptable to volume and complexity: Large healthcare providers handle thousands of patients and many use cases (clinical care, research, insurance, analytics). Consent management must scale across departments and support multiple data collection channels (in‑person forms, mobile apps, EHR portals).
Common pitfalls include ambiguous or generic forms, missing revocation workflows, siloed systems where one department is unaware of revocations, and misalignment between the terms of the authorisation and actual data flows. Regulators have penalised organisations for not performing risk analyses or failing to manage access logs. An effective HIPAA Consent Management program addresses these weaknesses by integrating legal requirements into everyday operations.
A Five‑Step Practical Process for HIPAA Consent Management
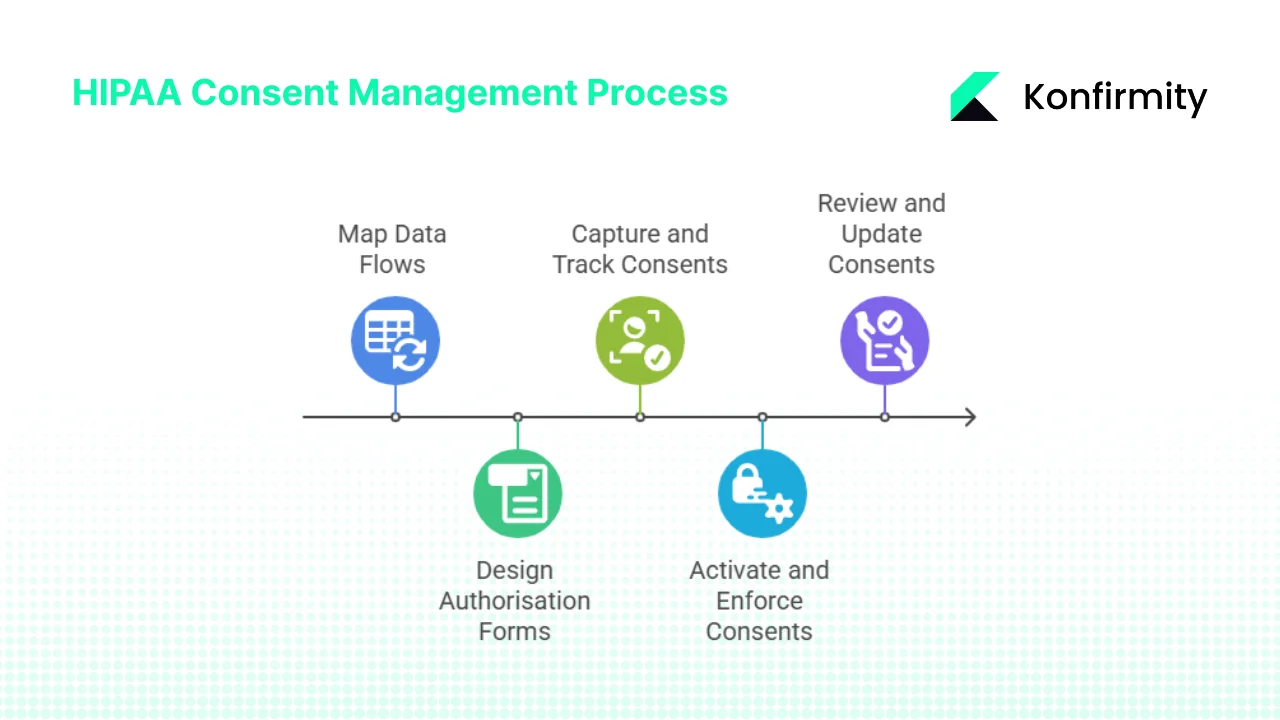
Step 1: Map Data Flows and Identify Consent Needs
You cannot manage consent until you understand where PHI travels. Start by cataloguing data sources (EHR, patient portals, telehealth apps, call centres), storage locations (databases, cloud services), processing activities (analytics, research, billing), and sharing relationships (internal teams, business associates, research partners). Identify which uses/disclosures fall under TPO or other permitted categories and which require authorisation. For each use case, determine whether the data contains special categories (e.g., genetic data, reproductive health information) that may invoke stricter consent under state laws like Washington’s My Health, My Data Act.
Create a data flow diagram and attach relevant regulatory obligations (Privacy Rule, Security Rule, state laws, BAAs, GDPR). This exercise also helps satisfy the proposed Security Rule requirement to maintain a technology asset inventory and network map illustrating the movement of ePHI.
Step 2: Design or Update Authorisation Forms and Workflows
Well‑designed forms are central to HIPAA Consent Management. For each non‑TPO use, develop an authorisation form that specifies:
- PHI to be used: Identify categories (medical history, lab results, genetic data, etc.).
- Purpose: Explain why the data is needed (research study, telehealth provider referral, marketing communications).
- Recipient: Name specific third parties or types of organisations.
- Expiration: Provide a date or event (e.g., “one year from signature” or “end of study”).
- Right to revoke: Explain how patients can withdraw consent and what happens to data already disclosed.
Consider readability and accessibility: use sixth‑grade reading levels, multiple languages, and digital formats for mobile devices. Electronic consent workflows should support e‑signatures, audit trails, and versioning. Integrate consent capture into patient intake (in‑person or online), EHR portals, telehealth apps, and research enrollment. When third parties are involved (business associates, subcontractors), align forms with confidentiality agreements and BAAs.
Step 3: Capture, Track, and Manage Consents
Implement a centralised consent management system. Each consent record should include patient ID, form version, date/time, authorised data uses, recipients, expiration, and revocation status. Link consent records to downstream systems via APIs or integration connectors. For example, when a patient authorises sharing data with a telehealth provider, the system updates the EHR, scheduling platform, and telehealth service. Use unique identifiers and secure storage to meet audit and retention requirements. This step addresses OCR’s frequent enforcement finding that organisations lack adequate risk analysis and information system activity reviews.
Step 4: Activate and Enforce Consents in Data Usage
Consent management must move from a database to operational enforcement. For each consent record:
- Check permissions: Data retrieval or disclosure should validate that consent exists and is current. For TPO uses, enforce minimum necessary standards. For authorised uses, restrict data to what the patient agreed to share.
- Link to access control: Use identity and access management (IAM) systems to tie consent status to user permissions. Revocation events should trigger removal of access rights.
- Maintain audit logs: Document every access, disclosure, and use. Ensure logs capture user ID, timestamp, data accessed, purpose, and consent reference. Regularly review logs to detect deviations.
- Encrypt and protect data: Use encryption at rest and in transit, as required by the proposed Security Rule update. Apply multi‑factor authentication and network segmentation. Implement vulnerability scanning and penetration testing.
Step 5: Review, Audit, Revoke, and Update
Consent management is not a one‑time task. Conduct periodic audits to ensure consents collected align with actual data flows, that expired consents are removed, and that revocations are honoured. Provide easy mechanisms for patients to revoke or modify authorisations (portal options, phone line, paper form). Document all revocations and ensure downstream systems stop using the data. Version control forms and update them when regulations or use cases change. Proposed Security Rule updates require annual security audits, vulnerability scans every six months, and business associate security verifications. Align your consent management reviews with these cycles.
Real‑World Examples and Use Cases
Example A: Patient Portal E‑Consent for Telehealth
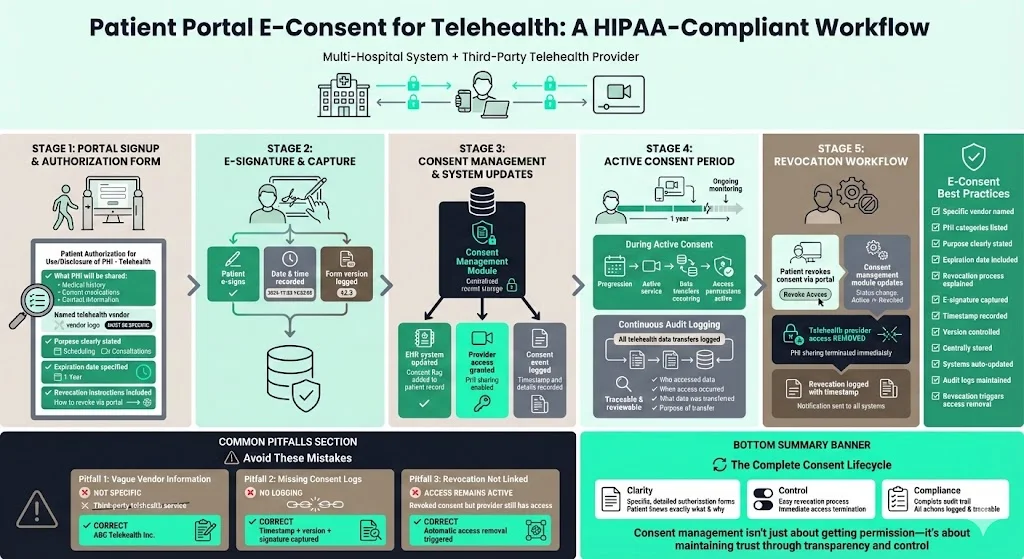
A multi‑hospital system introduces telehealth services via a third‑party provider. At the portal signup, patients receive an electronic authorisation form titled “Patient Authorisation for Use/Disclosure of PHI – Telehealth.” The form specifies that the patient’s medical history, current medications, and contact information will be shared with the telehealth provider for scheduling and consultations. It names the vendor, states that the authorisation expires one year from the date of signature, and explains that revocation can be done through the portal.
The workflow: the patient reads the form on the portal, signs with an e‑signature, and the system records the timestamp and version. The consent record is stored in the consent management module and triggers updates in the EHR and telehealth platforms. If the patient revokes consent, the telehealth provider’s access is removed. Audit logs record all telehealth data transfers. Common pitfalls: not specifying the telehealth vendor, failing to log consent details, and not linking the revocation to the telehealth platform.
Example B: Clinical Research Study
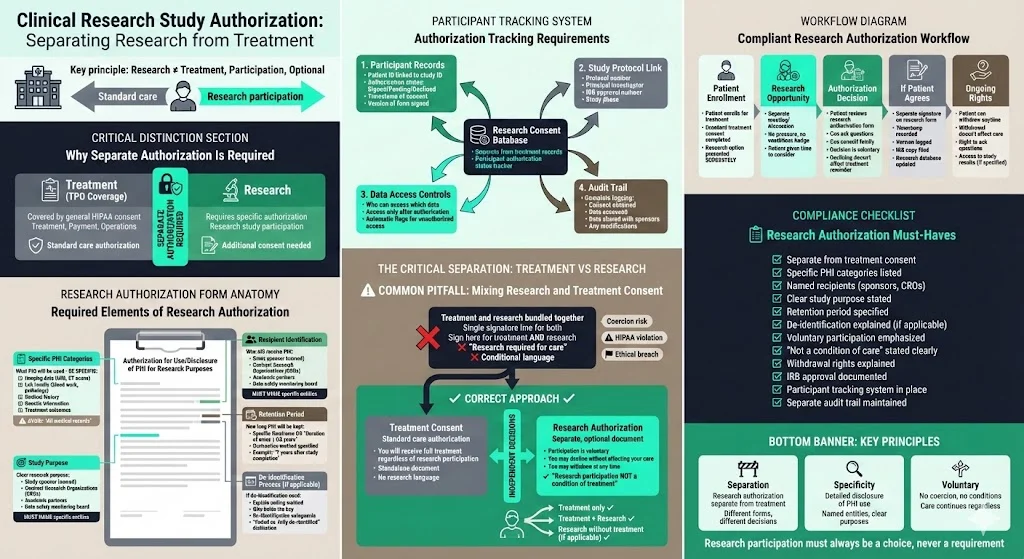
A hospital’s research department launches a clinical trial using patient data. They need a separate authorisation because research uses are not covered by TPO. The authorisation form must specify what PHI will be used (e.g., imaging data, lab results), who will receive it (sponsors, contract research organisations), the study purpose, and the retention period. If the study involves de‑identification, the form should explain how data will be coded. The system must track which participants have signed the research authorisation. A common pitfall is mixing research and treatment consent: research participation cannot be a condition of receiving standard care.
Example C: Marketing Communications
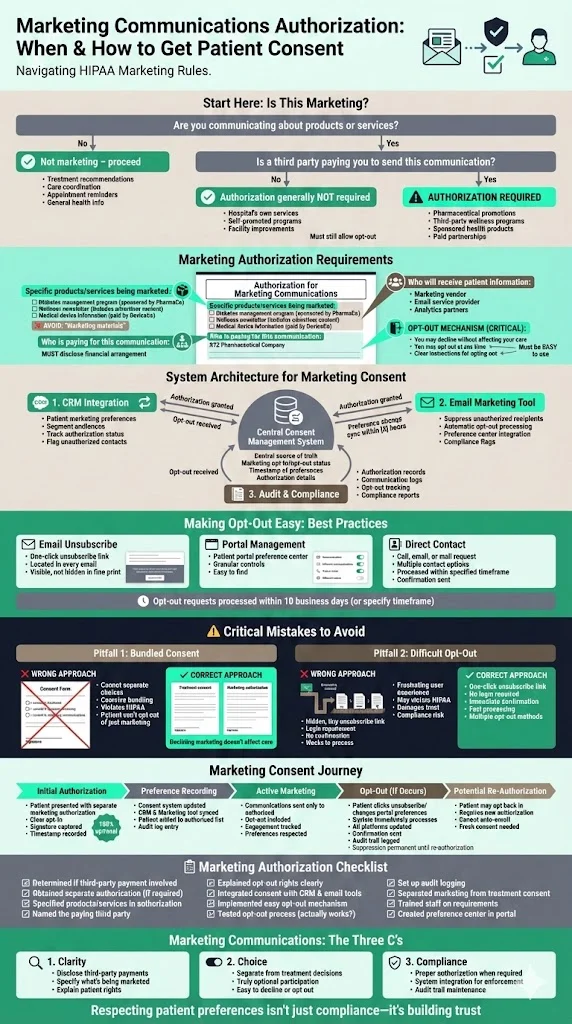
Healthcare organisations sometimes want to send newsletters or promotional materials. HIPAA generally requires authorisation for marketing that involves communication about products or services when the covered entity is paid by a third party. The authorisation must specify the marketed products/services, recipients, and that the patient may opt out. The consent management system should integrate with the CRM and email marketing tool. Pitfall: using a general consent form that lumps marketing with treatment and failing to provide an easy opt‑out.
Templates and Tools for Busy Teams
Template Headings for Authorisation Forms
- Patient Authorisation for Use/Disclosure of PHI – for third‑party data sharing (e.g., telehealth, analytics).
- Electronic Consent for Data Sharing – for e‑consent via patient portal or mobile app.
- Revocation of Authorisation – to allow patients to withdraw consent.
- Research Consent Form – with sections for sponsor, study purpose, data categories, and de‑identification.
Each template should include headings such as Description of PHI, Purpose of Use/Disclosure, Name or Class of Recipients, Expiration Date/Event, Revocation Right, Signature/Date, and Acknowledgment. Align the language with grade‑level reading standards and offer translations.
Checklist for Consent‑Management Workflow
- Mapping: Identify all PHI sources and flows. Determine whether each use/disclosure is permitted or requires authorisation.
- Design: Create or update authorisation forms with required elements. Verify readability and clarity. Include expiration and revocation.
- Capture: Implement systems to capture and store consent records. Ensure each record logs patient ID, form version, date, authorised uses, recipients, expiration, and revocation status.
- Enforcement: Connect consent status to data access controls. Log every use/disclosure, enforce minimum necessary standards, and monitor for unauthorized access.
- Review: Schedule periodic audits of consent records and data flows. Update forms when regulations change. Ensure revocation requests propagate across systems.
Tracking Dashboard Fields
A simple dashboard for HIPAA Consent Management might include: patient identifier, consent type (telehealth, research, marketing), form version, date signed, expiration date, authorised data categories, recipients, revocation status, and last audit date. Colour‑coded status indicators can highlight expired consents or missing revocation logs.
Decision Tree: When Is Written Authorisation Needed?
- Treatment, payment, or health‑care operations? → No written authorisation required, but follow minimum necessary and record‑keeping requirements.
- Public health (reporting diseases, vital statistics), law enforcement, or court orders? → Disclose without authorisation but document the legal basis.
- Marketing communication or sale of PHI? → Written authorisation required.
- Research study involving PHI beyond TPO? → Written authorisation required unless using a limited data set under a data‑use agreement.
- De‑identified data? → HIPAA authorisation not required if data meets the de‑identification standard.
- Sensitive categories under state laws (reproductive, mental health, genetic)? → Check state law; explicit consent likely required.
Tools and Platforms
Healthcare organisations should leverage patient portal modules with builtin consent features, consent management systems that integrate with EHRs, and audit log frameworks. Encryption and access control modules are essential to meet Security Rule requirements. Konfirmity offers a managed service that implements and monitors these controls across HIPAA, SOC 2, and ISO 27001 frameworks, freeing internal teams from heavy compliance workloads.
CTA: Book a demo
Best Practices and Pitfalls to Avoid
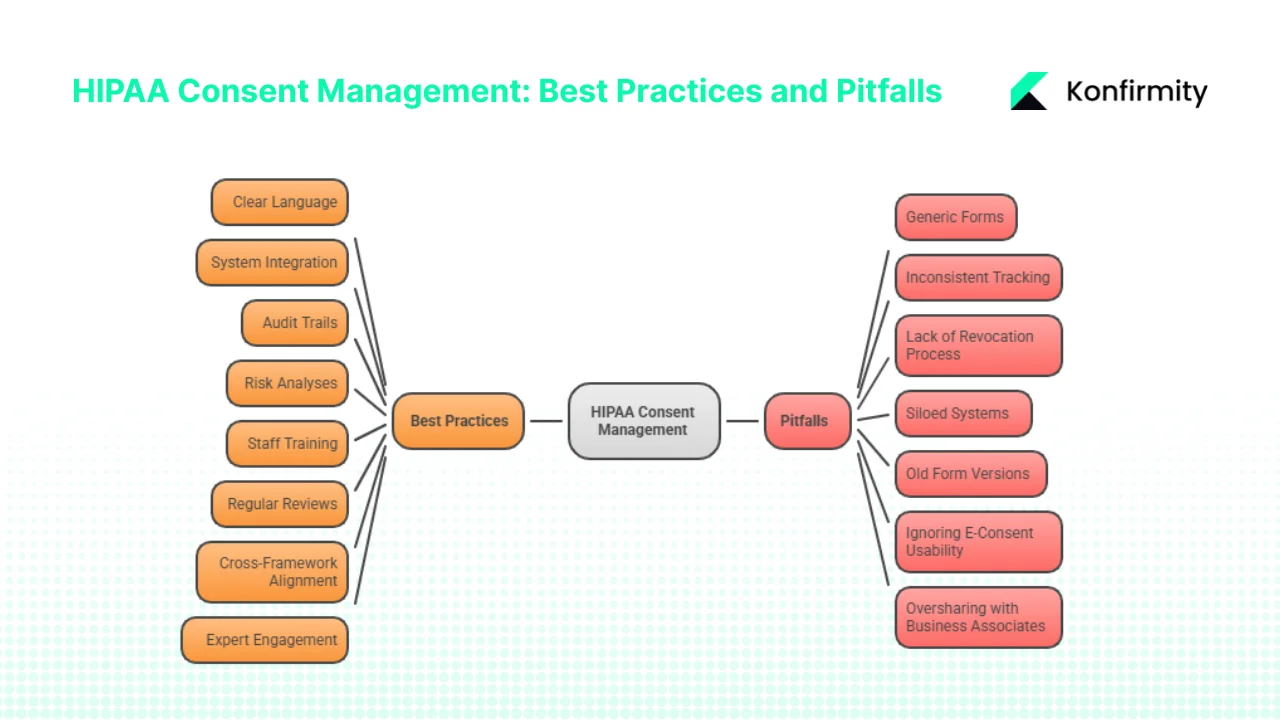
Best Practices
- Use clear language: Write authorisation forms in plain, accessible language. Avoid legal jargon.
- Integrate systems: Ensure that consent status flows to all relevant systems (EHR, CRM, telehealth, research databases). Use APIs and identity management to automate updates.
- Maintain audit trails: Log every access and disclosure. Document the consent reference for each data use.
- Perform risk analyses: Conduct thorough risk analyses, as OCR’s enforcement initiative focuses on this requirement. Update analyses when systems or partners change.
- Train staff: Provide periodic training on HIPAA consent management, privacy rules, and security practices. Include scenarios about revocation and minimum necessary.
- Review and update regularly: Align reviews with annual security audits, vulnerability scans, and BAA assessments. Update authorisation forms when new use cases emerge or laws change.
- Cross‑framework alignment: Map HIPAA requirements to SOC 2 and ISO 27001 controls. For example, SOC 2’s security and confidentiality criteria require access controls, change management, and incident response, which overlap with HIPAA’s administrative and technical safeguards.
- Engage experts: Managed service partners like Konfirmity can design, implement, and operate consent management programs. With 6,000+ audits supported and 25+ years of combined expertise, we reduce internal effort by up to 75 % compared to self‑managed compliance, accelerate SOC 2 readiness from 9–12 months to 4–5 months, and ensure continuous audit‑readiness for HIPAA.
Pitfalls
- Generic forms: Using one form to cover multiple purposes (treatment, research, marketing) leads to over‑collection and violates HIPAA’s specificity requirement.
- Inconsistent tracking: Storing consents in spreadsheets or unlinked systems results in outdated or missing records. This is a common root cause of OCR enforcement actions.
- Lack of revocation process: Without a defined process, revocation requests may be ignored or delayed, leading to continued unauthorised use.
- Siloed systems: Departments may operate separate consent tracking systems, causing misalignment. A unified consent database is essential.
- Old form versions: Failing to update forms when regulations change can lead to non‑compliance. Version control is critical.
- Ignoring e‑consent usability: Clunky interfaces discourage users from reading or understanding authorisations. Ensure mobile‑friendly design and support for assistive technologies.
- Oversharing with business associates: Disclose only the PHI necessary for the associate’s duties. Conduct annual BAA reviews and include updated security requirements like multi‑factor authentication and encryption.
Conclusion
Effective HIPAA Consent Management is not a paperwork exercise; it is a disciplined operational program that combines legal compliance, technical controls, and human processes. The HIPAA Privacy and Security Rules set the baseline, but state laws, SOC 2, ISO 27001, GDPR, and NIST guidance add layers of obligations. The risk of neglecting consent management is real: data breaches cost U.S. healthcare organisations over US$10 million on average, and OCR’s enforcement actions have resulted in multi‑million‑dollar penalties for risk analysis failures and unauthorised disclosures.
The five‑step process outlined—mapping data flows, designing authorisation forms, capturing and tracking consents, enforcing them, and regularly reviewing—is a practical roadmap. Healthcare leaders should integrate consent management into their security and compliance programs, leveraging cross‑framework mappings to maximise efficiency. Managed services like Konfirmity provide human‑led, year‑round support to implement and operate these controls, reducing internal burdens and accelerating audit readiness.
Now is the time to act. Review your current consent management process, update your authorisation forms, implement a central consent management system, and schedule your next risk analysis. Start with security and arrive at compliance.
FAQ
1) What is consent management in healthcare?
It is the system of obtaining, documenting, tracking, and enforcing patient authorisations for the use and disclosure of their protected health information. It aligns with HIPAA’s Privacy and Security Rules, state laws, and other frameworks, ensuring that PHI is used only as permitted and that patients’ rights to revoke consent are honoured.
2) What are the four requirements for informed consent?
Informed consent requires (1) disclosure—providing sufficient information about the procedure or data use; (2) comprehension—ensuring the individual understands the information; (3) competence—the individual has capacity to decide; and (4) voluntariness—the decision is free from coercion.
3) What are the five main rules of HIPAA?
They are the Privacy Rule, Security Rule, Transaction Rule, Identifiers Rule, and Enforcement Rule. The Transaction Rule standardises electronic transactions and code sets; the Identifiers Rule assigns unique identifiers for providers and health plans; the Enforcement Rule outlines investigation and penalty procedures and was amended in 2015 to increase penalties and add breach notification requirements.
4) What is consent management (general)?
Beyond healthcare, consent management refers to any system that obtains, records, monitors, and enforces data subjects’ consents or authorisations. It is used in advertising, analytics, and consumer services to comply with privacy laws like GDPR, CCPA, and other regulations. The core principles—specific purpose, clear disclosure, ability to revoke, and auditable records—remain the same.





.svg)






.svg)
.svg)