Enterprise sales have shifted. Five years ago, a security questionnaire was a formality. In 2025, it will be a gatekeeper. If you cannot prove your data handling practices meet global standards, the deal stops.
For companies selling to enterprise clients, data sovereignty and cross-border movement are no longer theoretical legal concerns. They are operational hurdles. When a US-based SaaS platform processes data for a German automotive giant, or a UK health-tech firm uses sub-processors in India, the flow of information triggers intense scrutiny.
This article addresses the specific requirements of ISO 27001 International Transfers. It explains why enterprise buyers obsess over where their data goes, how to implement Annex A controls that satisfy auditors, and why a human-led approach to compliance creates a competitive advantage in the sales cycle.
Why International Data Transfers Matter When Selling to Enterprise Clients
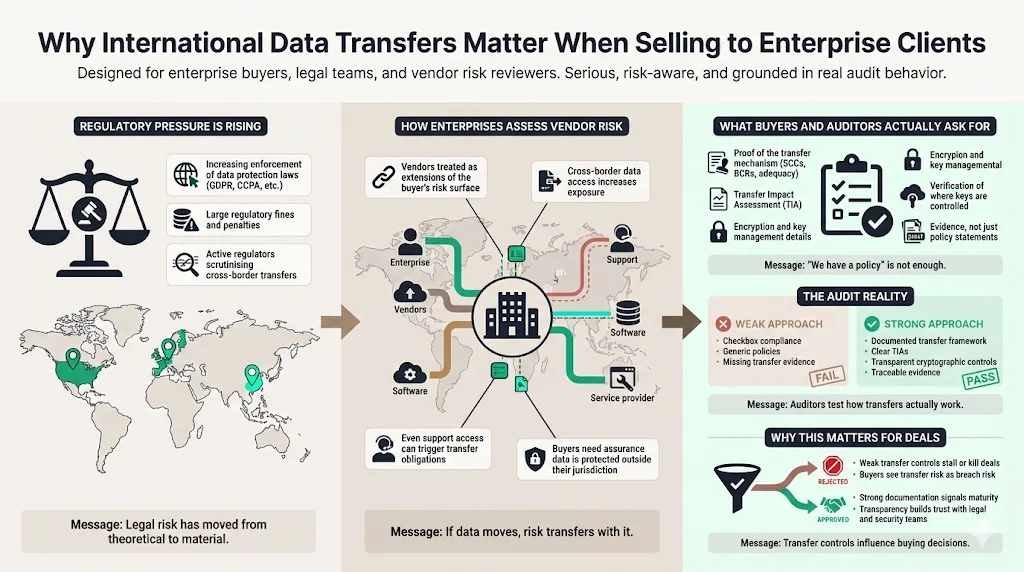
The regulatory environment for data privacy has tightened significantly. With GDPR fines totaling over €1.2 billion in 2024 alone, and stricter enforcement from bodies like the California Privacy Protection Agency (CPPA), enterprise legal teams are risk-averse.
They pass this pressure down the supply chain.
When a Fortune 500 company evaluates a vendor, they assess third-party risk. If your service involves moving their customer data across borders—even just for support access—you inherit their regulatory exposure. They need assurance that data leaving their jurisdiction remains protected to the same standard as if it stayed home.
The Audit Reality
In our experience supporting over 6,000 audits, we see a clear pattern. Auditors do not just ask if you have a policy. They ask for evidence of the transfer mechanism. They want to see the Transfer Impact Assessment (TIA). They verify if cryptographic keys are managed locally or accessible from the destination country.
If you handle ISO 27001 International Transfers as a checkbox activity, you will fail the due diligence phase of a major deal. Buyers view weak transfer controls as a potential breach waiting to happen. Conversely, a transparent, well-documented transfer framework signals maturity. It tells the buyer you understand their liability and have actively mitigated it.
Understanding ISO 27001 International Transfers
To implement controls effectively, we must first define what the standard requires.
What “International Transfers” Mean in Context
ISO/IEC 27001:2022 does not strictly define "international" in a political sense, but it focuses on "Information Transfer" (Control 5.14). However, in practice, this control becomes critical when organizational boundaries cross legal jurisdictions.
A transfer occurs not only when you physically move a database from a server in London to a server in New York. It also occurs when:
- A support engineer in Brazil views user logs hosted in Frankfurt.
- A sub-processor in the Philippines processes payroll data for US employees.
- Backup tapes are shipped to a secondary site in a different country.
Access equals transfer. If the data is viewable or processable from a different jurisdiction, the risks regarding confidentiality, integrity, and availability change.
Domestic vs. Cross-Border Data Flow
Domestic transfers usually operate under a single legal framework. Cross-border flows introduce conflicting legal obligations. For example, the US CLOUD Act may compel a US provider to disclose data, while GDPR may forbid that same disclosure. ISO 27001 International Transfers controls are designed to bridge these gaps, ensuring that security measures (like encryption and access control) travel with the data.
Why Enterprise Buyers Focus Here
Enterprise buyers fear "compliance drift." They worry that a vendor might be secure on day one, but six months later will outsource a critical function to a low-cost region without adequate safeguards.
- Supplier Risk: This is a primary concern. According to the 2025 Verizon DBIR, third-party breaches have doubled, now accounting for 30% of all security incidents.
- Financial Impact: The cost of failure is high. IBM's 2025 Cost of a Data Breach Report found that breaches involving third-party software vulnerabilities cost an average of $4.91 million, significantly higher than the global average.
- Reputation: A breach in a third-party vendor is often reported as a breach of the enterprise itself.
ISO 27001 Information Transfer Requirements Explained
ISO 27001 acts as the framework to manage these risks. The standard does not prescribe exactly how to encrypt data, but it demands you identify the risk and address it.
Core Intent of the Control
The primary objective of information transfer controls is to prevent loss, unauthorized access, or corruption of information while it is in transit or being accessed remotely. The protection level must remain consistent. You cannot have AES-256 encryption at rest in your primary data center and then send files via unencrypted FTP to a vendor.
Annex A Control 5.14 (Information Transfer)
This is the specific control auditors examine. It requires:
- Policies and Procedures: Formal rules for valid transfers.
- Agreements: Contracts (like Data Processing Agreements) with external parties.
- Technical Controls: Mechanisms to secure the transmission.
What Auditors Expect: When we run internal audits for our clients, we look for specific artifacts. If you claim to use SFTP for all client data, we check the logs. If you claim to strip PII before sending data to a dev environment abroad, we inspect the datasets. The standard demands that what you say in your policy matches what happens in your stack.
Information Transfer Policy as a Foundation
Your Information Transfer Policy is the governing document. It must define:
- Classification: Which data types can be transferred and which cannot (e.g., "Restricted" data stays in the EU).
- Authorization: Who can approve a new data flow.
- Mechanisms: Acceptable tools (e.g., "Only use the corporate VPN or approved encrypted file share").
This policy synchronizes your internal operations with enterprise security reviews. When a buyer asks, "How do you secure data in transit?", you attach this policy and the accompanying evidence.
International Compliance and Privacy Regulations
ISO 27001 provides the structure (the ISMS), but regulations provide the specific rules you must follow.
Mapping to Global Privacy Regulations
ISO 27001 is regulation-agnostic, which makes it powerful. By implementing Control 5.14 effectively, you create a foundation that satisfies multiple laws:
- GDPR (Europe) & UK GDPR: Requires adequate protection for data leaving the EEA/UK. ISO 27001 controls demonstrate technical and organizational measures (TOMs).
- CCPA/CPRA (California): Focuses on consumer rights and sale of data. Strong transfer controls help track where data lives, enabling accurate consumer requests.
- HIPAA (USA): Requires Business Associate Agreements (BAAs) and security for ePHI. Transfer controls ensure ePHI isn't exposed during vendor exchanges.
Addressing Data Sovereignty
Data sovereignty is the concept that electronic data is subject to the laws of the country in which it is located. Enterprise customers often have strict residency requirements.
For example, a German healthcare provider may stipulate that patient data never leaves Germany. If your architecture relies on a global content delivery network (CDN) or a "follow-the-sun" support team, you might inadvertently violate this contract.
Konfirmity Insight: We help clients map their data flows visually. We identify every sub-processor and data center location. If a client has a strict sovereignty requirement, we assist in architecting "pins" or dedicated instances to ensure compliance. This is where software fails and human expertise is required; a tool cannot redesign your AWS architecture to meet a German enterprise requirement.
Approved Transfer Mechanisms for Cross-Border Data Flow
You cannot simply email a database to a colleague in another country. You need approved mechanisms.
Common Mechanisms Under ISO 27001
- Secure Networks: VPNs, TLS 1.2 or 1.3 for all web traffic, and IPsec tunnels for site-to-site transfers.
- Encryption: Using industry-standard algorithms (AES-256) to encrypt data before it moves. If the data is intercepted, it remains unreadable.
- Authentication: Multi-Factor Authentication (MFA) for any access point that allows cross-border data retrieval.
Selecting the Right Mechanism
This is a risk-based decision.
- Low Risk: Public marketing data. Transfer via standard HTTPS is acceptable.
- High Risk: Financial records or PII. Requires end-to-end encryption and strict identity management.
For enterprise clients, ISO 27001 International Transfers documentation must show that you selected the mechanism based on the sensitivity of the data. If you use the same method for public blogs and patient records, an auditor will flag a non-conformity.
Security Measures for International Transfers
Security measures fall into two buckets: Technical and Organizational.
Technical Controls
- Encryption Standards: Do not roll your own crypto. Use validated libraries. Ensure cryptographic keys are rotated and managed securely.
- Secure File Transfer: Ban email attachments for sensitive data. Use secure portals (e.g., Box, ShareFile, or internal tools) that generate audit logs of who downloaded what and when.
- Data Masking/Anonymization: If the destination country (e.g., a dev team in a high-risk region) does not need live data, use synthetic data or mask PII fields before transfer.
Organizational Controls
- Role-Based Access (RBAC): Restrict access based on need. A developer in the US does not automatically need access to EU production databases.
- Training: Employees are the biggest risk. Train staff on why they cannot use personal Dropbox accounts or unauthorized USB drives to move company data.
- Clear Ownership: Assign an owner for every data flow. If the flow breaks or leaks, who is responsible?
Contractual and Legal Safeguards
Technical security is useless if the legal framework is flawed.
Confidentiality Agreements and Data Protection Clauses
Contracts transform trust into legal obligation. When we review client contracts, we look for specific clauses that enterprise buyers expect:
- Right to Audit: The buyer can inspect the vendor’s security.
- Breach Notification: Strict timelines (e.g., 24 or 72 hours) to report a transfer-related breach.
- Sub-processor Liability: The vendor accepts responsibility for their downstream partners.
Meeting Legal Requirements
- Standard Contractual Clauses (SCCs): For EU data transfers to non-adequate countries, SCCs are the standard. They are non-negotiable legal texts.
- Transfer Impact Assessments (TIAs): This is a critical document. It assesses whether the destination country’s laws (e.g., US surveillance laws) undermine the protections offered by the SCCs.
- Binding Corporate Rules (BCRs): For large multinationals, these allow intra-group transfers. They are complex and costly to implement but highly regarded.
For ISO 27001 International Transfers, the auditor will check if these agreements are signed and current. A missing DPA with a critical sub-processor is a major non-conformity.
Risk Management for Cross-Border Transfers
ISO 27001 is a risk management standard, not a prescriptive checklist. You must identify, analyze, and address risks.
Identifying Risks
- Regulatory Risk: The destination country changes its privacy laws.
- Security Risk: The transmission channel is intercepted.
- Availability Risk: The destination region suffers political instability or infrastructure failure.
Assessing and Mitigating Risks
We use a risk register to score these threats.
- Risk: Data interception during transfer to a backup site.
- Likelihood: Low.
- Impact: High.
- Treatment: Implement TLS 1.3 and encrypt backups at rest.
- Residual Risk: Acceptable.
This "math" is what auditors want to see. They want proof you thought about it.
Implementation Roadmap for Companies Selling to Enterprises
Implementing ISO 27001 International Transfers controls is not an overnight task. It requires a structured approach.
Step 1: Map International Data Flows
You cannot protect what you cannot see. Create a data flow diagram.
- Source: Where does data originate?
- Path: How does it travel? (Public internet, private line, VPN).
- Destination: Where does it rest?
- Access: Who looks at it?
Step 2: Define and Document Policies
Draft the Information Transfer Policy. Ensure it is practical. Do not write policies you cannot enforce. If you say "no USB drives," but your engineering team relies on them, you have created a compliance gap.
Step 3: Apply Technical and Contractual Controls
Roll out the encryption tools. Configure the firewalls. Sign the DPAs with vendors. This is the execution phase.
- Konfirmity Insight: This is where many teams stall. They know what to do but lack the hands-on capacity to configure the SIEM or chase down vendor signatures. As a managed service, we handle this execution, often saving internal teams hundreds of hours.
Step 4: Monitor, Review, and Improve
Security is not static. New vendors are onboarded; new laws are passed.
- Internal Audits: Test the controls annually.
- Management Review: Senior leadership must review the risk of international operations.
Common Pitfalls to Avoid
In our years of delivery, we see the same mistakes repeated.
Treating Information Transfer as Only an IT Issue
It is a legal and business issue. IT can encrypt the pipe, but they cannot judge if the transfer violates a client’s data residency clause. Legal, Product, and Security must collaborate.
Missing Documentation
You might have perfect encryption, but if you lack the TIA or the risk assessment record, you will fail the audit. Auditors operate on evidence. "We do it" is not an answer. "Here is the log" is.
Overlooking Data Sovereignty Expectations
We have seen deals collapse because a vendor assumed "cloud" meant "anywhere." If a French enterprise client discovers their data is backed up in a US region without prior approval, it is a breach of contract.
Conclusion
ISO 27001 International Transfers are more than a compliance hurdle. They are a trust signal. In a market where enterprise buyers are paranoid about supply chain risk, the ability to demonstrate controlled, transparent, and secure cross-border data handling is a differentiator.
Structured controls reduce friction in sales cycles. Instead of weeks of back-and-forth over security questionnaires, you provide a solid packet: your ISO 27001 certificate, your Information Transfer Policy, and your external audit report. You move from "high-risk vendor" to "trusted partner."
However, maintaining this standard requires effort. It is not a one-time project. It requires continuous monitoring of data flows, vendor contracts, and regulatory changes.
This is where Konfirmity differs. We do not sell you software and wish you luck. We provide a human-led, managed service. We design the controls, implement them in your stack, and maintain them year-round. While a typical self-managed ISO 27001 program might consume 550-600 hours of your internal team's time annually, our clients typically spend around 75 hours. We handle the heavy lifting—the evidence collection, the policy updates, the risk reviews—so you can focus on building your product and closing deals.
Security that looks good on paper but fails in operations is a liability. Build controls that stand up to buyers, auditors, and attackers.
Frequently Asked Questions (FAQ)
1) What does ISO 27001 say about international data transfers?
ISO 27001 requires organizations to implement policies and procedures to protect information during transfer. While it does not explicitly ban transfers, it demands that the level of protection (confidentiality, integrity, availability) be maintained regardless of location. The standard requires you to identify risks associated with the transfer and mitigate them through technical and organizational controls.
2) Which Annex A control covers information transfer?
Annex A Control 5.14 (Information Transfer) is the primary control. It addresses the security of information transfer within an organization and with external parties. Control 5.10 (Acceptable use of information and other associated assets) and 5.12 (Classification of information) also play supporting roles by defining what can be transferred and how.
3) How do companies manage cross-border transfer risks?
Companies manage these risks through a combination of:
- Risk Assessment: Identifying legal and technical threats in the destination country.
- Encryption: protecting data in transit.
- Contracts: Using SCCs or equivalent agreements to legally bind the recipient.
- Transfer Impact Assessments (TIAs): Evaluating if local laws permit the recipient to honor the contract.
4) Are contractual safeguards required for international transfers?
Yes. ISO 27001 International Transfers require formal transfer agreements. These agreements must detail the responsibilities of both parties, the security standards to be maintained, and the liability in case of a breach. For EU data, these often take the form of Standard Contractual Clauses (SCCs).
5) How does ISO 27001 support data sovereignty requirements?
ISO 27001 supports sovereignty by enforcing strict asset management and transfer policies. By requiring organizations to map their data flows and define acceptable transfer mechanisms, the framework makes it easier to identify and restrict data movement to specific geographic regions, ensuring compliance with local residency laws.





.svg)





.svg)
.svg)