Most enterprise purchasers insist on security evidence before signing a contract. Without ongoing proof of operational safeguards, deals stall even when teams think they are “ready” on paper. The same tension applies in healthcare: large providers, insurers, and their technology partners must show that they monitor their environments continuously. Rising breach costs and evolving regulations mean HIPAA Continuous Monitoring is central to safe patient care, business viability, and audit readiness. This article explains why and how organizations can implement durable monitoring that stands up under scrutiny.
Why Continuous Monitoring Is a Reality for Healthcare
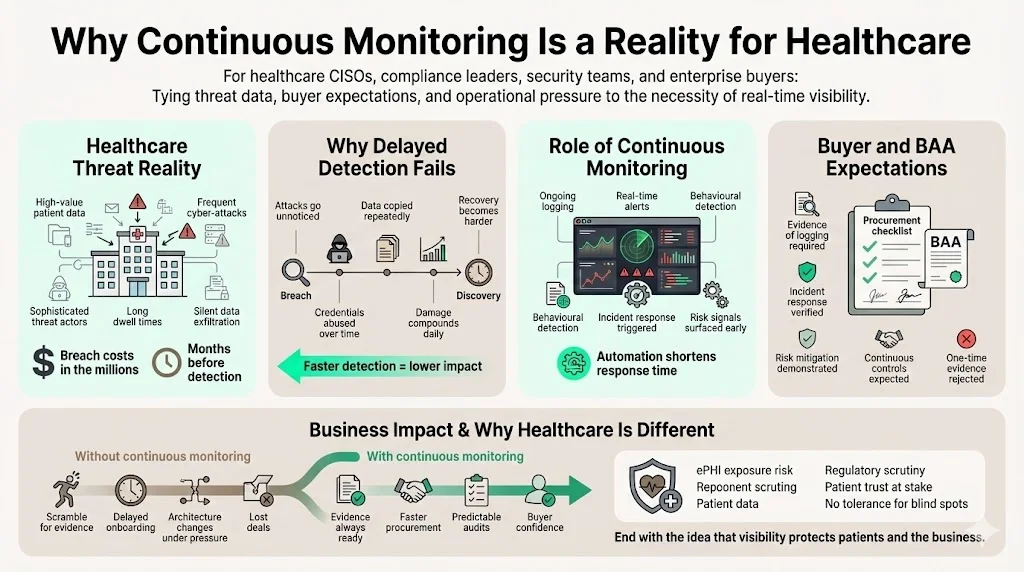
Cyber‑attacks on healthcare systems have grown in sophistication and frequency. IBM’s 2024 Cost of a Data Breach report found that the global average breach cost reached USD 4.45 million and the United States experienced an average breach cost of USD 9.48 million. Healthcare topped the list with average breach costs of USD 10.93 million. Breaches in this sector are often undetected for months—an average of 213 days elapsed before discovery, leaving attackers plenty of time to exfiltrate sensitive data. The same study highlighted that automation and AI security tooling reduced the average cost by USD 1.76 million and shortened the breach lifecycle by 108 days. These numbers underscore the operational need for near‑real‑time visibility into systems handling electronic protected health information (ePHI).
Procurement questionnaires and business associate agreements (BAAs) demand evidence of technical controls. Large health systems, insurers, and pharmaceuticals will not onboard a vendor who cannot demonstrate ongoing logging, incident response, and risk mitigation. Without HIPAA Continuous Monitoring, companies are left scrambling to assemble proof under tight deadlines, often delaying sales or forcing last‑minute changes to architectures. Organizations that treat monitoring as a one‑time project end up with stale evidence that fails both buyers and regulators.
Cross‑Framework Compliance and Audit Timelines
Healthcare organizations rarely operate under a single compliance regime. While each framework has its own nuances, there is substantial overlap around logging, access reviews, vulnerability management, and vendor oversight. Building one monitoring program that addresses these elements pays dividends across all frameworks. Guidance on proactive SOC 2 compliance stresses that continuous monitoring and risk assessment are key components of maintaining a strong security posture. The same article notes that compliance is not a single event; organizations must establish a monitoring program and schedule regular internal audits to ensure ongoing adherence. This philosophy aligns with the Security Rule’s expectation that entities regularly review records and update security measures, so a well‑designed program can satisfy multiple audits with a single evidence stream.
From our experience managing more than 6,000 audits across industries, companies that implement continuous monitoring early achieve audit readiness faster. A human‑led program with dedicated experts typically prepares a team for SOC 2 Type II or ISO 27001 in four to five months while requiring around 75 hours of client time. Teams that delay monitoring until auditors arrive often need nine to twelve months and consume 550–600 internal hours as they scramble to reconstruct logs, access reviews, and vulnerability reports. A managed service that collects evidence continuously—across HIPAA, SOC 2, and ISO 27001—keeps organizations audit‑ready year‑round without forcing them to hire a full security team.
Pitfalls of “Compliance Manufacturing”
The appeal of quick‑fix compliance is strong. Some vendors advertise “two‑week compliance” packages that produce a binder of policies and checklists. These shortcuts ignore how auditors actually work. SOC 2 Type II requires evidence collected over an observation period of three to twelve months, while HIPAA regulators expect organizations to demonstrate regular log reviews, vulnerability scans, and incident responses. “Compliance manufacturing” yields documents that look polished but rarely reflect operational reality. In our fieldwork we see the same failures repeated: access controls that allow broad database queries, vulnerability scans run once and never repeated, and alerts that no one owns. These patterns not only lead to audit findings but also leave patient data exposed when incidents occur.
Combining Frameworks for Efficiency
Rather than managing separate programs for each framework, organizations should map controls once and reuse evidence across audits. A unified vulnerability management program with monthly scanning and remediation service‑level agreements simultaneously satisfies HIPAA’s proposed semi‑annual scanning requirement and SOC 2’s call to identify and address vulnerabilities. Similarly, regular access reviews and audit logs support both HIPAA and the SOC 2 Trust Services Criteria. Configuration baselines, incident response plans, and vendor risk management processes can all be shared.
A Shift From Periodic Checks to Ongoing Visibility
Historically, many healthcare organizations treated security as a checkbox exercise, relying on annual audits and deferred remediation. That model is breaking down. In 2024 OCR proposed making all Security Rule safeguards mandatory and requiring regulated entities to maintain asset inventories and network maps, updated at least once a year. The proposal also calls for semi‑annual vulnerability scanning and annual compliance audits. Even before these changes, the Security Rule expects organizations to review access logs and system activity regularly, evaluate and update security measures, and implement audit controls. NIST’s definition of continuous monitoring—maintaining ongoing awareness of security, vulnerabilities, and threats—reinforces that monitoring must become part of daily operations. Practitioners need to review logs and alerts routinely, tune thresholds to manage noise, and feed monitoring outputs directly into incident response. Automation through SIEM, vulnerability scanning, and configuration management tools makes this approach feasible and cost‑effective.
How Continuous Monitoring Supports Security, Privacy, and Compliance
Continuous monitoring delivers three core benefits. First, it improves security by providing near‑real‑time visibility into abnormal logins, data access spikes, or configuration changes. Annual audits miss transient compromises, whereas regular assessments keep pace with threats. Second, it protects patient privacy. Regular review of logs and strict access controls limit unauthorized disclosure and catch misconfigurations before data is exposed. Third, it supports compliance. Regulators expect evidence of risk analyses, audit controls, and regular review of system activity; continuous monitoring generates the artefacts needed to demonstrate that controls operate as intended.
Who Should Care About Continuous Monitoring?
Anyone handling ePHI, from hospitals and clinics to SaaS vendors and billing companies, needs an effective monitoring program. Covered entities must ensure that their business associates implement and document safeguards, so a vendor’s failure can cascade back to the healthcare provider. Implementing HIPAA Continuous Monitoring helps organizations satisfy due‑diligence requirements and accelerate procurement.
What HIPAA Continuous Monitoring Means in Practice
Definition. In practice, HIPAA Continuous Monitoring means maintaining ongoing awareness of security, vulnerabilities, and threats across all systems that handle ePHI. It involves continuous log collection, access reviews, vulnerability scanning, and configuration checks—activities that support the Administrative, Physical, and Technical Safeguards under 45 CFR § 164.308, § 164.310, and § 164.312.
One‑time assessments vs. ongoing monitoring. Initial risk assessments establish a baseline, but systems change frequently. Without ongoing monitoring, new risks go unnoticed. Continuous monitoring tracks deviations from the baseline, such as unauthorized privilege escalation or misconfigured cloud storage. HIPAA requires covered entities to evaluate and update security measures, and the proposed rule would mandate annual updates to asset inventories and network maps.
Integrating safeguards. Continuous monitoring spans administrative, physical, and technical controls. Policies define who reviews logs and how incidents are escalated. Facility access systems record entry and exit. Technical controls include access controls, audit logs, and configuration baselines. Training ensures that workforce members understand how to interpret alerts and respond promptly.
Why Continuous Monitoring Matters for Patient Data Protection
Healthcare systems face ransomware, misconfigured cloud storage, and insider misuse. Remote work, connected medical devices, and third‑party services expand the attack surface, and stolen medical records fetch a high price on criminal markets. Real‑world failures show why vigilance matters: at Deer Oaks a coding error left discharge summaries publicly accessible for over a year, and a compromised account later exposed data for more than 170,000 individuals. Continuous monitoring catches anomalies—such as spikes in database queries, repeated failed logins, or unusual outbound traffic—so that teams can contain incidents quickly. IBM’s research indicates that automation shortens breach lifecycles by more than three months, reducing both harm to patients and the cost of notifications.
Is Continuous Monitoring Required Under HIPAA?
HIPAA’s Security Rule does not use the phrase “continuous monitoring,” but it requires organizations to regularly review records, implement audit controls, and update security measures. OCR enforcement actions often cite deficient risk analyses and failures to update them when implementing new technologies. Proposed amendments would make all safeguards mandatory and introduce specific timeframes for inventories, vulnerability scanning, and compliance audits, signalling regulators’ expectation of continuous oversight.
What Regulators Expect to See
Regulators consistently cite four common deficiencies: missing or outdated risk analyses, inadequate audit controls and log reviews, lack of oversight of business associates, and poorly defined incident response plans. Organizations that maintain clear, current evidence—such as risk analyses, audit logs, and documented responses—are better positioned during audits.
Core Components of HIPAA Continuous Monitoring
Effective monitoring involves several interlocking practices. This section outlines core components and describes how they contribute to security, privacy, and compliance.
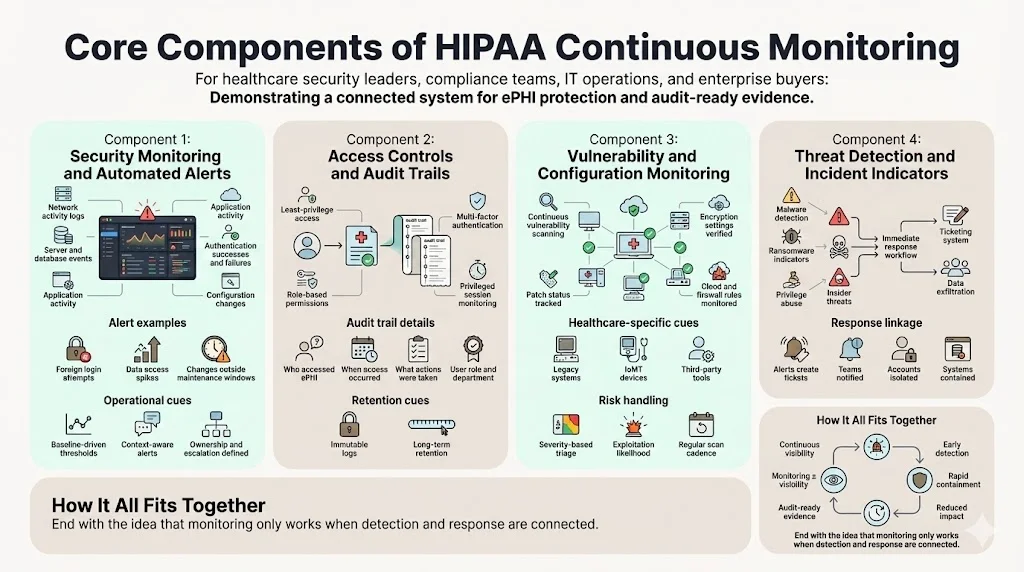
1. Security Monitoring and Automated Alerts
At the center is system activity monitoring across networks, servers, databases, and applications. Logs should capture successful and failed authentication attempts, file access events, configuration changes, and administrative actions. Modern SIEM platforms collect and correlate logs from disparate sources and can generate alerts for anomalous behavior. Examples include:
- Unusual login attempts, such as multiple failed logins from a foreign IP address.
- Sudden spikes in data access or large exports of records.
- System changes executed outside of maintenance windows.
Alert rules should be tuned to balance noise and sensitivity. Thresholds may be based on historical baselines, and context such as user role and location should inform prioritization. Alerts must feed into an incident response system with clear ownership and escalation paths.
2. Access Controls and Audit Trails
Access control is a Technical Safeguard. Organizations must enforce least privilege, require strong authentication (ideally multi‑factor), and regularly review user privileges. Audit trails record who accessed ePHI, when, and what actions they performed. These logs are essential during investigations and audits. For example, if a user downloads a large number of medical records at 3 a.m., the audit trail allows the security team to verify whether the action was authorized.
Audit logs should be immutable and retained according to policy (commonly six years, in line with HIPAA documentation requirements). Monitoring tools should flag access outside normal patterns and maintain context about the user’s role, department, and recent changes. Automated review of privileged sessions helps detect insider threats.
3. Vulnerability Assessment and Configuration Monitoring
Vulnerabilities can be introduced by outdated software, misconfigurations, or insecure third‑party components. Continuous vulnerability assessment goes beyond annual scans. Automated scanners run weekly or monthly, depending on asset criticality, to detect missing patches, weak encryption, and misconfigured cloud permissions. Configuration monitoring tools track changes to baseline settings—such as firewall rules, storage permissions, and encryption configurations—and alert when deviations occur.
Healthcare environments often contain legacy systems, Internet of Medical Things (IoMT) devices, and unmanaged third‑party tools. These devices may lack modern security features. A robust monitoring program inventories all assets, including cloud services and business associates, and categorizes them by risk. Vulnerability findings are triaged based on severity (e.g., CVSS scores) and exploitation likelihood. The proposed HIPAA rule would require vulnerability scanning at least every six months, but many organizations choose monthly scans for high‑risk systems.
4. Threat Detection and Incident Indicators
Threat detection includes identifying malware, ransomware, privilege abuse, and insider threats. Behavioral analytics look for patterns that deviate from normal operations. Indicators might include:
- Unusual file encryption activity, which could signal ransomware.
- Privilege escalation attempts or execution of system commands by non‑administrative users.
- Data exfiltration, detected via abnormal outbound network flows or large file transfers to unknown destinations.
When detection tools identify such indicators, incident response should be immediate. Alerts should create tickets, notify the appropriate team members, and trigger containment steps such as isolating a workstation or disabling an account. An effective continuous monitoring program links detection and response so that teams can mitigate damage quickly.
Continuous Monitoring vs. HIPAA Risk Assessments
Risk assessments and continuous monitoring work together rather than replacing each other. A risk assessment establishes a baseline. It identifies assets handling ePHI, maps workflows, and evaluates threats and vulnerabilities. It yields a risk register that ranks potential issues by likelihood and impact. Continuous monitoring then tracks changes relative to this baseline.
Without a thorough risk assessment, monitoring lacks context. Teams might receive alerts but not understand which assets matter most or what constitutes a critical threshold. Conversely, if monitoring is absent, the risk assessment becomes static. As technologies and workflows change, the organization will face blind spots. Regulators expect both: a documented risk analysis and ongoing review of system activity.
Step‑by‑Step Guide to Implementing HIPAA Continuous Monitoring
A practical monitoring program aligns with HIPAA and other frameworks such as SOC 2 and ISO 27001. Focus on four essentials:
- Scope the environment. Inventory all systems, applications, and workflows that handle ePHI, including cloud services and third‑party partners. Mapping where data flows and who touches it sets the foundation for controls.
- Prioritize by risk. Use the risk assessment to identify high‑impact systems and vendors. Define monitoring objectives and metrics based on criticality so that scarce resources focus on the greatest risks.
- Implement and integrate tools. Deploy SIEM platforms, vulnerability scanners, configuration and cloud security tools, and set meaningful alert thresholds. Integrate monitoring outputs with incident response so that alerts trigger action instead of piling up.
- Document and review. Maintain policies, logs, scan reports, and incident records, and revisit them after system changes. HIPAA requires documentation retention for at least six years. Regular reviews keep monitoring aligned with evolving technology and risk.
Practical Examples
Example 1: Monitoring Access to Electronic Health Records
A mid‑size hospital deploys a SIEM that collects logs from its electronic health record (EHR) system. The hospital defines rules to detect access outside of normal working hours and to flag users who view more than 50 patient records within 10 minutes. One night, the SIEM generates an alert when a nurse’s account accesses 120 records at 2 a.m. The security team investigates, confirms that the account was compromised, and disables it. The audit trail shows exactly which records were accessed, supporting notification obligations and forensic analysis. The hospital then resets credentials, updates its MFA policy, and reports the incident to OCR as required.
Example 2: Monitoring Cloud Storage for ePHI Exposure
A health technology company uses Amazon S3 to store patient reports. Its cloud security posture management tool monitors bucket permissions and triggers alerts when a bucket becomes publicly accessible. During a routine check, the tool discovers that a developer accidentally configured a bucket to allow public read access. An alert is sent to the security engineer, who immediately restricts the permissions and initiates a review. Because the exposure lasted only a few minutes and there is no evidence of access, the company documents the incident and uses it in training. Without automated monitoring, the misconfiguration could have gone unnoticed, leading to unauthorized access and regulatory penalties.
Common Monitoring Gaps Leading to HIPAA Violations
Many HIPAA violations stem from monitoring that looks fine on paper but breaks down in daily use. These gaps often build up quietly until an incident forces attention.

1) Overreliance on Periodic Audits
Annual or quarterly audits help with compliance checklists, but they miss what happens between reviews.
- Risks change as systems, staff, and workflows change
- Misconfigurations can sit unnoticed for months
- Insider misuse and credential abuse rarely show up in scheduled audits
- Audit results are often treated as a finish line instead of a starting point
2) Alert Fatigue and Unclear Ownership
Security and compliance alerts only work if someone acts on them.
- High alert volume leads staff to ignore or silence warnings
- Alerts lack context, making it hard to judge urgency
- No clear owner is assigned to investigate or respond
- Escalation paths are undefined or inconsistently used
3) Inadequate Monitoring of Vendors and Third Parties
Business associates often handle large volumes of protected health data, yet visibility into their activity is limited.
- Vendor access is granted but not actively tracked
- Changes in vendor tools or workflows go unreported
- Security obligations are assumed rather than verified
- Logs and incident reports are not regularly reviewed
4) Weak Access Controls and Audit Trails
Poor access management makes it difficult to detect or investigate improper data use.
- User access is broader than necessary for job roles
- Terminated or transferred staff retain system access
- Audit logs are incomplete, inconsistent, or overwritten too quickly
- Log reviews are manual, infrequent, or skipped entirely
5) Failure to Act on Detected Issues
Finding a problem does not reduce risk unless it leads to action.
- Alerts are acknowledged but not investigated
- Root causes are not identified or documented
- Corrective actions are delayed or never completed
- Similar issues reappear because lessons are not applied
6) Limited Visibility Across Systems
Healthcare environments often rely on many disconnected platforms.
- Monitoring tools operate in silos
- Activity across EHRs, cloud services, and endpoints is not correlated
- Suspicious patterns go unnoticed when viewed in isolation
- Compliance teams lack a full picture of data access and movement
Best Practices for Long‑Term Monitoring Success
- Iterate and test. Tune alert thresholds and update rules as systems and threats change. Test incident response regularly through tabletop exercises to ensure alerts lead to action.
- Keep documentation current. Update policies, inventories, and procedures when you add or retire systems. The proposed rule would require annual updates to asset inventories and network maps, but more frequent reviews keep controls aligned with reality.
- Invest in expertise. Effective monitoring requires specialized skills. If you lack an internal security operations center, consider a human‑led managed service. Providers like Konfirmity deliver continuous monitoring, vulnerability management, and audit support with less overhead than building these capabilities in‑house.
Conclusion
Security measures that look good on paper but fail under real‑world pressure are liabilities. Attackers move quickly, and regulators are raising the bar. HIPAA Continuous Monitoring is not optional; it is the backbone of modern healthcare security. Ongoing visibility into systems handling ePHI helps detect threats early, reduce breach lifecycles, and provide evidence of compliance. It enables healthcare providers, SaaS vendors, and business associates to build trust with patients and buyers, close enterprise deals faster, and avoid surprise findings during audits. By designing and operating a durable monitoring program—backed by human expertise and integrated with incident response—organizations can protect patient data, maintain business continuity, and stay ahead of evolving regulations.
FAQs
1. What is continuous monitoring under HIPAA?
It is the ongoing collection, analysis, and reporting of security information across all systems that process or store ePHI. NIST defines continuous monitoring as maintaining ongoing awareness of security, vulnerabilities, and threats. Under HIPAA, this includes regular review of access logs, vulnerability scanning, and updating security measures.
2. Is continuous monitoring required for HIPAA?
While the term is not explicitly used in the Security Rule, covered entities must regularly review records, implement audit controls, and evaluate the effectiveness of security measures. The proposed rule would formalize time‑bound requirements such as annual inventory updates, vulnerability scanning, and compliance audits.
3. What tools support HIPAA monitoring?
Effective programs use SIEM platforms for log collection and correlation, vulnerability scanners for identifying software flaws, configuration management tools for detecting drift, and cloud security posture management tools for monitoring cloud resources. Managed services can integrate these tools and provide expertise.
4. How often should monitoring alerts be reviewed?
High‑risk alerts should be reviewed immediately, with acknowledgement within minutes and resolution within hours. Lower‑priority alerts can be reviewed daily or weekly. Regular tuning ensures that alert volumes remain manageable.
5. What monitoring gaps cause HIPAA violations?
Common gaps include skipping risk analyses, failing to review logs, not monitoring vendors, maintaining weak access controls, and ignoring alerts. Regulators have highlighted these deficiencies in enforcement actions.




.svg)






.svg)
.svg)