Most enterprise buyers now request assurance artifacts before procurement. Without operational security and continuous evidence, deals stall—even when teams think they’re “ready” on paper. Healthcare companies face the added pressure of protecting electronic protected health information (ePHI) under the Health Insurance Portability and Accountability Act (HIPAA) while ensuring that business systems remain audited and resilient. Merging HIPAA safeguards with a recognised governance framework helps teams maintain control.
This article explains how HIPAA Controls Mapped To COBIT can provide that structure. It draws on authoritative guidance from the U.S. Department of Health and Human Services (HHS), NIST’s 2024 resource guide for implementing the HIPAA Security Rule, and real‑world patterns gleaned from more than 6,000 audits and 25+ years of combined expertise at Konfirmity.
HIPAA & COBIT: Key Frameworks & Requirements
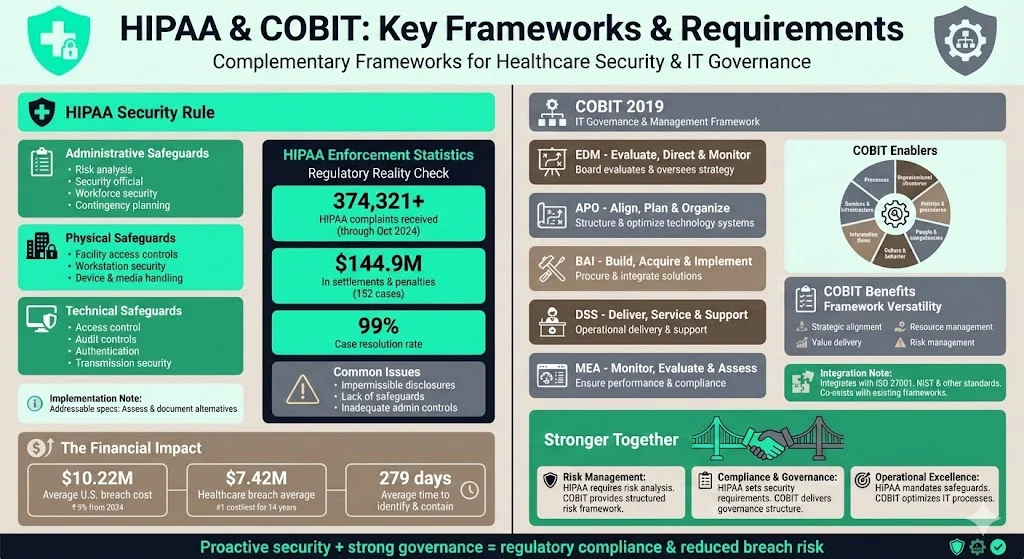
Overview of the HIPAA Security Rule:
The HIPAA Security Rule sets out administrative, physical and technical safeguards that covered entities and their business associates must implement to protect ePHI. Administrative requirements include a risk analysis, designation of a security official, workforce security measures, and contingency planning. Physical safeguards address facility access controls, workstation use and security, and device/media handling. Technical requirements mandate access control, audit controls, integrity protections, authentication and transmission security. Some implementation specifications are labelled “addressable,” meaning the organisation must determine whether they are reasonable and appropriate and, if not, document an alternative.
Regulatory oversight is significant. By October 31, 2024, the HHS Office for Civil Rights (OCR) had received more than 374,321 HIPAA complaints and initiated over 1,193 compliance reviews. It resolved 99% of these cases and obtained 152 settlements or penalties totaling roughly $144.9 million. OCR found that the most common issues were impermissible disclosures, lack of safeguards, and inadequate administrative safeguards. These figures show that regulators have moved from guidance to enforcement; healthcare organisations must proactively meet the Security Rule’s requirements.
Data‑breach costs underscore the stakes. IBM’s 2025 Cost of a Data Breach report found that U.S. breaches averaged $10.22 million—up 9% from 2024—because of higher fines and detection costs. Healthcare incidents remain the costliest across all industries; although the average cost of a healthcare breach fell to $7.42 million, the sector has recorded the highest breach costs for 14 consecutive years. Breaches take time to detect and contain—healthcare organisations needed 279 days on average to identify and contain an incident. These figures illustrate why proactive security and governance are essential.
Overview of COBIT:
COBIT (Control Objectives for Information and related Technologies) is an IT governance and management framework developed by the Information Systems Audit and Control Association (ISACA). It offers best practices for aligning technology with business objectives and managing risks. The framework groups its processes into five core domains:
- EDM – Evaluate, Direct and Monitor: The board evaluates strategic options and oversees implementation.
- APO – Align, Plan and Organize: This domain structures and optimizes the use of technology systems.
- BAI – Build, Acquire and Implement: Focuses on procuring the right solutions and integrating them into business processes.
- DSS – Deliver, Service and Support: Addresses the operational delivery and support of technology services.
- MEA – Monitor, Evaluate and Assess: Ensures performance and compliance targets are met.
COBIT 2019 also defines seven enablers (components) of an effective governance program: processes, organisational structures, policies and procedures, people and competencies, culture and behaviour, information flows, and services/infrastructure. These components help integrate technology management with business strategy, risk management and regulatory compliance. The framework is designed to co‑exist with other standards; C‑Risk notes that COBIT integrates IT management practices and standards into a single framework covering strategic alignment, value delivery, resource management and risk management. Such versatility makes it a useful foundation for organisations that already rely on ISO 27001, NIST or other frameworks.
The Challenge for Healthcare Organisations
Healthcare entities often operate multiple systems—electronic health records, billing platforms, telemedicine services and cloud applications. Each system processes ePHI and must comply with HIPAA. At the same time, business partners expect assurance artifacts (SOC 2 reports, ISO 27001 certificates) during procurement. Fulfilling these obligations independently can multiply effort and lead to overlapping controls. Aligning HIPAA safeguards with COBIT’s governance structure helps reduce duplication and ensures that risk management, privacy safeguards and operational controls are collectively managed.
Why Mapping HIPAA to COBIT Makes Sense
Mapping HIPAA safeguards to COBIT processes provides several advantages:
- Streamlined compliance: By matching each HIPAA implementation specification to a COBIT process, teams can address regulatory requirements and governance obligations simultaneously. This prevents duplication across frameworks and simplifies audit preparation.
- Consistent audit and monitoring: COBIT’s MEA domain emphasises monitoring, evaluation and assessment, which dovetails with HIPAA’s requirements to track access to ePHI and evaluate security measures. A unified dashboard makes it easier to demonstrate compliance to auditors and buyers.
- Bridging regulatory and enterprise goals: The crosswalk published by OCR, NIST and ONC identifies mappings between the HIPAA Security Rule and the NIST Cybersecurity Framework (CSF). OCR notes that this crosswalk helps entities identify gaps and “bolster compliance” while acknowledging that using the CSF does not guarantee HIPAA compliance. A similar approach can bridge HIPAA and COBIT; mapping ensures that regulatory requirements are embedded in the broader governance model.
- Support for cybersecurity best practices: Healthcare organisations face increasing attacks: over 40% of data breaches in recent years involved healthcare and 91% of health organisations reported a breach. A governance framework encourages continuous risk assessment, incident response and improvement.
- Integration with other frameworks: Because COBIT integrates with standards like ISO 27001, NIST and FAIR, organisations can reuse controls across multiple certifications. This cross‑framework reuse reduces effort in due diligence and speeds procurement.
Understanding the Controls: HIPAA and COBIT
HIPAA Safeguards at a Glance
The Security Rule classifies controls into three broad categories:
- Administrative safeguards: Perform a risk analysis and implement risk management measures, assign security responsibility, control workforce access, conduct training, establish incident procedures and contingency plans, and evaluate safeguards regularly.
- Physical safeguards: Limit physical access to facilities, define workstation use and security, and control devices and media.
- Technical safeguards: Implement access controls, audit controls, integrity protections, authentication and transmission security.
Each safeguard contains standards and implementation specifications that may be required or addressable. For example, the Access Control standard requires unique user identification, emergency access procedures, automatic logoff and encryption of ePHI during transmission.
COBIT Domains and Enablers
COBIT’s five domains (EDM, APO, BAI, DSS, MEA) cover the governance lifecycle from board oversight through operations and monitoring. Within these domains are processes such as DSS05 – Manage Security Services, APO12 – Manage Risk and BAI09 – Manage Assets. Each process has objectives and practices that describe how to manage and monitor controls. COBIT’s seven enablers—processes, organisational structures, policies/procedures, people, culture/behaviour, information and services/infrastructure—provide the levers for implementing these processes.
Mapping Logic – Turning HIPAA Safeguards Into COBIT Processes
Mapping is conceptually straightforward: for each HIPAA implementation specification, identify one or more COBIT processes and enablers that support it. This is similar to how OCR’s crosswalk maps HIPAA Security Rule standards to the NIST CSF and SP 800‑53 controls. The mapping does not replace HIPAA compliance; rather, it embeds HIPAA requirements within a structured governance program. Organisations that already use the NIST CSF or ISO 27001 can layer COBIT on top, creating a unified program for risk management, audit readiness and continuous improvement.
Conceptual Crosswalk
- HIPAA Access Control (Technical safeguard) → COBIT DSS05 Manage Security Services and APO12 Manage Risk (enablers: access‑control policies, identity management process).
- HIPAA Security Awareness and Training (Administrative safeguard) → COBIT APO07 Manage Human Resources and BAI08 Manage Knowledge (enablers: training policies, skill assessments).
- HIPAA Facility Access Controls (Physical safeguard) → COBIT DSS01 Manage Operations and DSS04 Manage Continuity (enablers: physical security procedures, facility management).
- HIPAA Risk Analysis (Administrative safeguard) → COBIT APO12 Manage Risk and MEA02 Monitor, Evaluate and Assess the System of Internal Control (enablers: risk management framework, internal audit).
These mappings illustrate that HIPAA requirements tie into multiple COBIT processes. In practice, a healthcare organisation can build a table that links each HIPAA specification to one or more COBIT processes and uses the enablers to implement policies, procedures and monitoring.
Step‑by‑Step Guide for Busy Teams

Step 1 – Establish Governance & Sponsorship
Set up a steering committee led by an executive sponsor (such as a chief technology officer or chief compliance officer) and an IT risk/compliance lead. Define the scope: which systems handle ePHI, which business units, and which business associates or third parties are in scope. Identify stakeholders from business, technology, security and legal teams. Governance is essential; the board and leadership must support the program so that policies and controls are adopted consistently.
Step 2 – Inventory & Baseline HIPAA Controls
Catalogue current safeguards using a simple grid: list each HIPAA standard, describe the existing implementation, assign an owner and classify the gap (none, partial, missing). Include administrative, physical and technical safeguards. This inventory forms the baseline for mapping and gap analysis. Tools such as NIST’s SP 800‑66r2 tables can help identify typical activities and sample questions.
Step 3 – Map HIPAA Controls to COBIT Processes/Enablers
Create a mapping table. For each HIPAA standard or implementation specification, list the corresponding COBIT processes and enablers. For example, mapping the Access Control standard to DSS05 Manage Security Services involves linking the organisation’s access‑control policy, identity management procedures, and authentication technologies. See the example table in the next section.
Step 4 – Assess Gaps & Prioritise Remediation
Assess the current maturity for each mapped control using a scoring matrix that considers risk impact, compliance gap and operational complexity. Prioritise remediation based on the severity of the risk and business impact. For instance, if audit logs (HIPAA audit controls) are incomplete, the gap might be classified as high risk because auditability is critical and is also a focus for SOC 2 and ISO 27001.
Step 5 – Define Control Implementation & Monitoring Plans
For each priority gap, define actions, responsible owners, timelines, metrics/KPIs and monitoring frequency. Align the monitoring with COBIT’s MEA domain: specify how often access reviews occur, what metrics are reported, and how audit logs are retained. Use templates to capture these plans, including start date, due date and status. Monitoring should include metrics such as number of unauthorized access attempts, percentage of systems encrypted, and number of training sessions completed.
Step 6 – Execute, Monitor & Report
Implement remediation actions and integrate them into business processes. Monitor performance via predefined KPIs and report status to the governance body. COBIT’s EDM domain requires the board to evaluate strategic options and monitor implementation. Reporting should be concise: dashboards summarise open gaps, completed actions and incident metrics.
Step 7 – Review & Update
Conduct periodic reviews of the mapping, controls and threat environment. Update the mapping when technology or regulatory requirements change (e.g., adopting cloud services or remote access). Use findings from audits and incidents to refine controls. Continuous improvement is essential; frameworks only add value when embedded in day‑to‑day operations.
Concrete Examples & Templates
Below are example tables and templates that healthcare teams can adapt. These are simplified to illustrate the concept; modify them to fit your organisation’s environment.
Sample Mapping Table
Sample KPIs and Metrics Table
Control Implementation Plan Template
Governance Dashboard Layout
A governance dashboard should be simple and visual. Consider including:
- Overall compliance status: Gauge showing percentage of HIPAA safeguards implemented and mapped.
- Risk heat map: Visual matrix showing high/medium/low risk areas based on gap assessment.
- Trend charts: Lines showing incident counts, unauthorised access attempts and training completion over time.
- Remediation tracker: Table listing open actions, owners and due dates.
- Audit readiness: Indicator of controls ready for SOC 2/ISO 27001 evidence collection (e.g., number of controls with documented evidence vs. total controls).
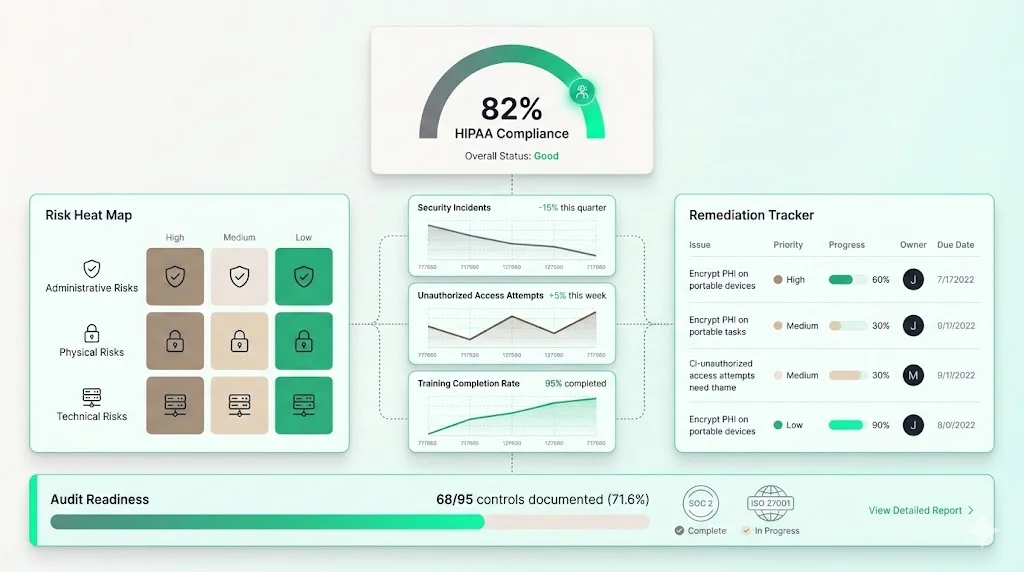
The above illustration depicts the concept of mapping HIPAA safeguards to COBIT processes. Icons representing administrative, physical and technical safeguards connect to COBIT domains, emphasising how controls flow into a unified governance framework.
Common Pitfalls & How to Avoid Them
- Treating mapping as a box‑ticking exercise: Mapping should not be a one‑time document. Embed controls into processes and measure them continuously.
- Unclear ownership: Assign control owners across business, technology and security teams to avoid gaps. Without clear accountability, remediations stall.
- Neglecting monitoring: Metrics and dashboards are critical. Without them, management cannot verify that controls are operating effectively.
- Focusing only on technical safeguards: Administrative and physical safeguards are just as important; ignoring them is a common reason for OCR findings.
- Failing to update the map: Technology and threats change; update mappings when adopting cloud services, remote work or new regulations.
Benefits for Healthcare Organisations
- Better regulatory compliance and governance: Mapping HIPAA to COBIT consolidates requirements into one program, reducing duplication and ensuring that ePHI protections align with enterprise governance.
- Improved information governance and risk management: COBIT’s risk and governance processes help organisations understand, measure and address risks systematically.
- Audit readiness and continuous monitoring: A structured program simplifies evidence collection for SOC 2, ISO 27001 or GDPR audits and shortens procurement due‑diligence cycles. For example, SOC 2 compliance typically involves a pre‑audit preparation period of one to three months, an observation period of three to 12 months and an official audit lasting one to three weeks. By embedding controls into daily operations, teams reduce the time spent on audit preparation.
- Stronger security posture: Integrating HIPAA safeguards into a governance framework encourages risk assessments, incident response and continuous improvement. This is critical when the average healthcare breach costs $7.42 million and may take 279 days to contain.
- Reduced duplication across frameworks: If the organisation also seeks ISO 27001 or NIST compliance, mapping allows reuse of controls and reduces effort.
How to Roll Out in a Busy Team Environment
Rolling out a mapping program requires discipline but can start small:
- Pilot one system or business unit: Choose a high‑impact application handling ePHI and apply the mapping. Use the template tables above to organise controls and actions.
- Use lean project management: Break work into sprints; focus on quick wins such as implementing multi‑factor authentication and building a training program.
- Provide templates: Use the mapping table, KPI matrix and implementation plan templates to save time.
- Engage stakeholders: Involve clinicians, operations staff and legal teams early to ensure controls fit real workflows.
- Report visually: Use dashboards to communicate progress to executives and board members. Keep updates concise and regular.
- Iterate regularly: Schedule quarterly reviews; adapt the program as threats and systems change. Continuous improvement is the hallmark of a mature security program.
Conclusion
Healthcare organisations face steep breach costs and active enforcement of HIPAA. Building controls in isolation leads to duplicated effort and missed risks. Mapping HIPAA Controls Mapped To COBIT provides a structured, governance‑centric approach that ties regulatory requirements to enterprise processes. By following the step‑by‑step guide and adapting the templates provided, teams can build a program that stands up to auditors, buyers and attackers. The real value comes from embedding these controls into daily operations and continuously improving them.
FAQs
Q1. What are the three types of controls in the HIPAA Security Rule?
The Security Rule defines administrative, physical and technical safeguards. Administrative safeguards include risk analysis, designated security leadership, workforce training and contingency plans. Physical safeguards cover facility access, workstation security and device/media handling. Technical safeguards involve access control, audit controls, integrity protections, authentication and transmission security.
Q2. What is the crosswalk between the HIPAA Security Rule and the NIST Cybersecurity Framework?
In 2014, the Office for Civil Rights, NIST and ONC released a crosswalk mapping HIPAA Security Rule standards to the NIST Cybersecurity Framework and SP 800‑53 controls. The crosswalk helps healthcare organisations identify gaps and strengthen security, but using the CSF does not guarantee HIPAA compliance.
Q3. Is HIPAA a cybersecurity framework?
No. HIPAA is a U.S. law that includes a Privacy Rule, Security Rule and Breach Notification Rule. The Security Rule specifies safeguards for ePHI but does not provide a complete cybersecurity framework. Organisations often pair HIPAA requirements with frameworks like COBIT, ISO 27001 or the NIST CSF to build a mature security program.
Q4. What are the four security control types?
Security controls are often grouped into preventive (stop incidents from occurring), detective (identify incidents), corrective (remediate incidents) and deterrent (discourage malicious activity). HIPAA’s safeguards include all of these types—for example, access controls are preventive and deterrent; audit controls are detective; contingency plans are corrective.





.svg)






.svg)
.svg)