Most enterprise buyers now ask for security assurance artefacts long before a contract is signed. Without operational security and continuous evidence, deals slow down or stall—even when a vendor believes its controls are in place. As we look toward 2026, SOC 2 What Changed In 2026 becomes a crucial question for providers selling to large organisations and healthcare customers. This article, written from the perspective of a practitioner with more than 6,000 audits under our belt and 25 years of combined expertise at Konfirmity, explains how the SOC 2 landscape is evolving, what the changes mean for busy teams, and how to prepare.
What SOC 2 Covers and Why It Matters
At its core, the SOC 2 framework is an attestation scheme created by the American Institute of Certified Public Accountants (AICPA). It produces a report on controls at a service organisation that are relevant to the security, availability and processing integrity of the systems that handle customer data and the confidentiality and privacy of that information. Enterprise buyers rely on SOC 2 reports as evidence that a vendor has designed and operates its controls effectively.
Types of SOC 2 reports. A Type I report describes the design of controls at a specific point in time, whereas a Type II report tests the operating effectiveness of those controls over an observation period—usually three to 12 months. Enterprise clients typically want Type II reports because they demonstrate how controls perform in real operations. Healthcare customers often insist on Type II because of the sensitive nature of protected health information.
The table below recaps the five Trust Services Criteria (TSC) and how they apply. Security is mandatory for every SOC 2 examination. The other categories are optional and are included when the vendor’s services expose additional risks or when buyers request them.
Controls—policies, procedures and technical safeguards—are the mechanisms that address these criteria. Examples include identity and access management, multi‑factor authentication, encryption at rest and in transit, change‑management workflows, logging, monitoring and incident response. In practice, a SOC 2 Type II examination can involve 60–150 control points. A 2024 benchmark study found that 23% of SOC 2 reports contained more than 150 security controls, reflecting a more rigorous approach to compliance.
Quick Recap: Core Concepts Underpinning SOC 2
Before discussing what’s new, it’s useful to recall the core structure of SOC 2, because changes in 2026 build upon this foundation.
- Trust Services Criteria and Points of Focus. The AICPA’s 2017 Trust Services Criteria—revised in 2022—define the criteria and points of focus for each of the five TSCs. Updated guidance clarifies disclosures about how controls meet framework requirements and emphasises that management must describe its risk assessment process and specific risks. Points of focus have been modernised to include emerging technologies and threats. These revisions are part of the SOC 2 Audit Guide published by the AICPA in October 2022.
- Risk assessment and control environment. Under the security TSC, organisations must implement a control environment and risk assessment process. Updated guidance urges management to disclose how it identifies and analyses risks. The 2024 SOC benchmark study indicates that confidentiality is now included in 64.4% of SOC 2 reports, up from 34% in 2023, signalling that risk assessment is influencing scoping decisions.
- Subservice providers and third‑party dependencies. Most service organisations rely on subservice providers—cloud hosts, payment processors, SaaS platforms or contractors—to deliver their services. The benchmark study found that 89.6% of SOC 2 reports included subservice providers, up from 82% in the prior year. As the study notes, you inherit the risk of those you work with and should scrutinise reports that omit subservice providers.
- Controls must operate over time. A Type II report requires evidence that controls operate effectively over a period. Short‑term or ad‑hoc measures do not satisfy the requirement. Continuous monitoring, access reviews and change‑management records are essential to demonstrate operating effectiveness.
This recap sets the stage for understanding the developments anticipated for 2026.
SOC 2 What Changed In 2026 — Key Updates and Emerging Trends
The AICPA hasn’t released a wholly new version of SOC 2 for 2026. Instead, evolution reflects shifts in risk, technology and enterprise expectations. The following trends outline what SOC 2 What Changed In 2026 means for practitioners.
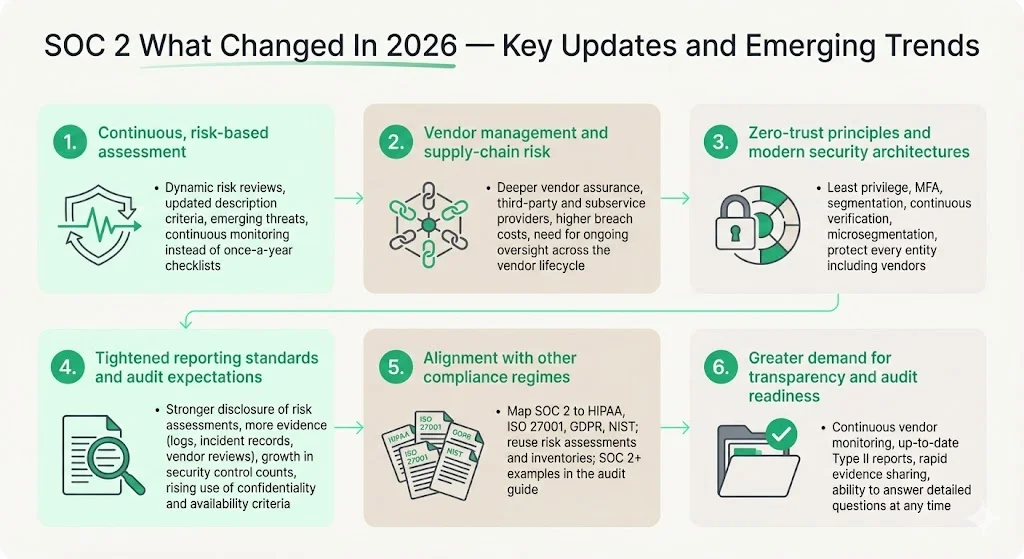
1. Greater emphasis on continuous, risk‑based assessment
Traditional SOC 2 programmes often relied on annual assessments and checklists. New guidance emphasises dynamic risk management. The updated SOC 2 description criteria require management to disclose how it identifies principal service commitments and system requirements, and how risk assessment informs control design. Revised points of focus address emerging technologies, threats and vulnerabilities, encouraging organisations to revisit their risks more frequently.
This shift aligns with the broader recognition that static questionnaires and periodic audits are insufficient. A Recorded Future analysis of supply‑chain breaches found that 30% of data breaches in 2024 involved a third‑party vendor, double the prior year. The report warns that static assessments provide outdated snapshots and argues that continuous, intelligence‑led monitoring is essential. For SOC 2, auditors and clients will look for evidence of ongoing risk evaluation, not just a once‑a‑year checklist.
2. Heightened scrutiny of vendor management and supply‑chain risk
With most providers relying on cloud platforms and SaaS partners, enterprise clients now demand deeper assurance around how vendors handle third‑party risk. The SOC 2 audit guide’s updated guidance clarifies system boundaries, including third‑party software applications, and references controls for assessing vendor risk. This is not just theory: the SOC benchmark study shows that nearly 90% of SOC 2 reports include subservice providers, while a Gartner‑cited survey reports that 78% of companies use 16 or more tools to manage their environments. More vendors mean more inherited risk.
Supply‑chain breaches are also costly. Recorded Future cites IBM’s data breach report, noting that the average cost of a third‑party breach exceeds $5.08 million. These incidents cost roughly 40% more to remediate than breaches originating within an organisation’s own systems. In addition, half of companies work with more than 100 vendors, up from 38% in 2023. This ecosystem introduces fourth‑ and fifth‑party dependencies that many organisations can neither see nor control.
Given these realities, SOC 2 What Changed In 2026 will involve auditors probing how service organisations evaluate, monitor and manage vendor security posture. Controls may need to cover vendor onboarding, periodic reassessment, contract management, off‑boarding and incident response coordination. The Prevalent third‑party risk management article highlights relevant trust services criteria—such as CC2.3 (communication with external parties), CC3.2 (risk identification) and CC9.2 (vendor risk management)—and notes that continuous monitoring across the vendor lifecycle helps organisations assess, manage and remediate vendor risks.
3. Adoption of zero‑trust principles and modern security architectures
Zero‑trust security has moved from theory to practice. The U.S. federal government’s strategy calls for agencies to use single sign-on with multi‑factor authentication, maintain inventories of all devices, encrypt all DNS and HTTP traffic, treat every application as internet‑accessible and categorise data for targeted protections. These goals reflect the core tenets of zero trust: continuous verification, least‑privilege access and breach assumption.
IBM’s overview of zero trust explains that in such environments, network assets are inaccessible by default, and users, devices and workloads must pass continuous, contextual authentication and validation to access resources. Permissions are restricted to the minimum needed and revoked when the session ends. Zero‑trust enterprises assume attackers are already inside the network and employ microsegmentation, monitoring and rapid response to contain breaches. These principles extend to supply‑chain security: zero trust applies continuous, contextual authentication and least‑privilege access to every entity, including vendors, so that if a vendor account is compromised it cannot access sensitive resources.
For SOC 2 in 2026, auditors and clients will expect evidence that service organisations implement modern access controls, network segmentation, multi‑factor authentication and least‑privilege policies. Identity and access reviews, device inventories, API security and microsegmentation may become standard control expectations. While zero trust is not explicitly required by SOC 2, it aligns with the “logical and physical access controls” and “risk mitigation” points of focus under the security TSC.
4. Tightened reporting standards and audit expectations
As enterprise compliance demands rise—particularly in regulated sectors such as healthcare and finance—SOC 2 reports are expected to be more comprehensive. The AICPA’s revised SOC 2 description criteria emphasise disclosure of formal risk assessments. Points of focus now call for coverage of new threats, technologies and vulnerabilities. Service auditors may request more detailed evidence, such as logs showing continuous monitoring, incident response records, vendor risk assessments and automated control workflows.
The 2024 SOC benchmark study found that reports containing more than 150 security controls rose from 16% to 23%. Confidentiality is now included in 64.4% of SOC 2 reports, up from 34% in 2023, and availability appears in 75.3%. These trends suggest that service organisations are expanding scope to address client requirements. Meanwhile, reliance on internal audit to reduce testing dropped to 5.2% of SOC reports, likely because updated AICPA guidance reduces the weight given to internal audit.
5. Alignment with other regulatory and compliance regimes
Many enterprise buyers operate under multiple frameworks—HIPAA for healthcare data, ISO 27001 for information security management, the General Data Protection Regulation (GDPR) for privacy or the Digital Operational Resilience Act (DORA) in Europe. They expect their vendors to align SOC 2 controls with these regimes. The AICPA’s SOC 2 Audit Guide includes examples of SOC 2+ reports that integrate HIPAA privacy rules, ISO 27001, NIST and HITRUST. Updated guidance emphasises clarifying system boundaries and addressing third‑party software.
For 2026, expect a stronger push to map SOC 2 controls to other frameworks. Organisations that operate an Information Security Management System (ISMS) under ISO 27001 can reuse risk assessments, asset inventories and Statement of Applicability (SoA) to support SOC 2. Similarly, vendors handling health data may align SOC 2 privacy criteria with HIPAA’s administrative, physical and technical safeguards and Business Associate Agreements (BAAs). Cross‑framework mapping reduces duplication and helps meet buyer expectations.
6. Greater demand for transparency and audit readiness during due diligence
Enterprise procurement teams are adopting continuous vendor monitoring. According to Recorded Future, half of companies now work with more than 100 vendors, and static questionnaires leave them blind between review cycles. Buyers increasingly expect vendors to share up‑to‑date SOC 2 reports, control attestations and evidence of continuous monitoring. For many technology vendors, having a current Type II report is now a minimum requirement.
In this context, SOC 2 What Changed In 2026 means that vendors must be ready to produce documentation quickly, answer detailed security questionnaires and support their claims with verifiable evidence. The ability to present a well‑maintained SOC 2 report and show ongoing control effectiveness will differentiate vendors from competitors who treat compliance as a one‑time exercise.
Practical Guidance for Teams Preparing for 2026
Konfirmity has delivered security and compliance outcomes for hundreds of SaaS and cloud providers. We operate as a human‑led, managed service—implementing controls inside your stack and keeping you audit‑ready year‑round. Our experience shows that busy teams can be ready for a SOC 2 Type II examination in 4–5 months with about 75 internal hours when they work with us, compared with 9–12 months and 550–600 hours if they try to manage everything themselves. Here are the steps we advise.
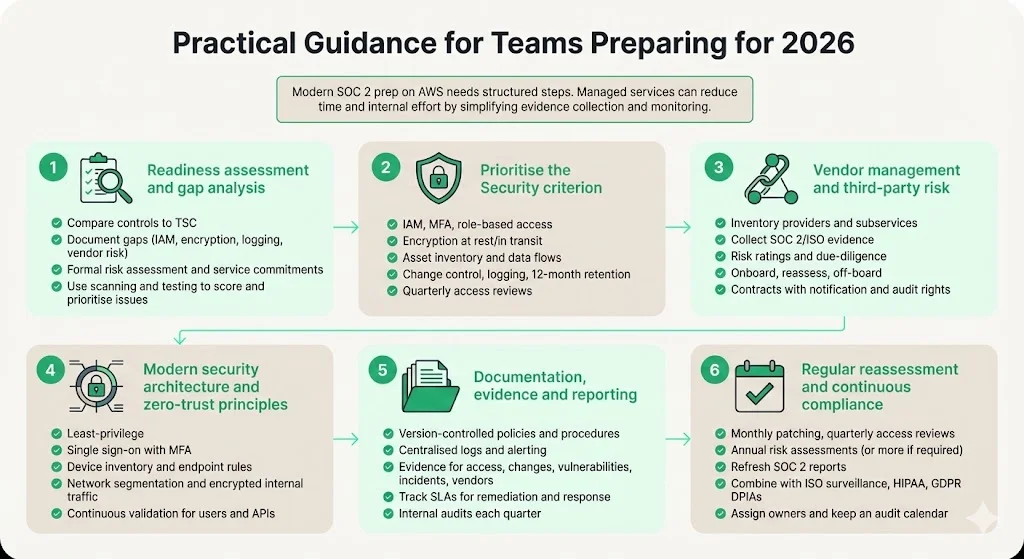
1) Conduct a readiness assessment and gap analysis
Start by comparing your current controls against the Trust Services Criteria. Document policies, procedures and technical safeguards; identify gaps in identity management, access control, encryption, change management, logging, incident response and vendor oversight. Make sure you have a formal risk assessment covering service commitments and system requirements. Tools such as Common Vulnerability Scoring System (CVSS) scanning, penetration testing and vulnerability management help quantify risk and prioritise remediation. A readiness assessment typically takes two to three weeks and yields a gap list with severity and remediation actions.
2) Prioritise the Security criterion as your baseline
Security is mandatory for every SOC 2 report. Establish strong identity and access management (IAM). Implement multi‑factor authentication, role‑based access control and segregation of duties. Encrypt data at rest and in transit. Maintain an asset inventory and document data flows. Establish change‑management procedures with peer review and automated pipelines. Enable centralised logging and monitoring; aggregated logs should be retained for at least 12 months for auditability and incident response. Perform quarterly access reviews and remove dormant accounts. Once security controls are solid, decide whether to add availability, processing integrity, confidentiality or privacy based on client needs and the nature of your service. Adding criteria increases cost and complexity, so ensure there is a clear business driver.
3) Adopt vendor management and third‑party risk practices early
Maintain a complete inventory of vendors and subservice providers. Collect and review their SOC 2 reports, ISO certifications and security questionnaires. Document risk ratings and due‑diligence results. Build policies for vendor onboarding, periodic reassessment and off‑boarding. Use contract clauses to require notification of security incidents, data breach reporting and right‑to‑audit. Automate vendor risk assessments and continuous monitoring where possible. The Prevalent framework lists criteria such as CC2.3 (communication), CC3.2 (risk identification) and CC9.2 (vendor risk management) to structure your programme.
4) Implement modern security architectures and zero‑trust principles
Move beyond perimeter‑based defences. Adopt least‑privilege access: grant users only the permissions they need, and revoke them when tasks are complete. Use single sign‑on with multi‑factor authentication and identity federation across internal and SaaS applications. Maintain an inventory of devices and enforce endpoint compliance. Segment networks into microzones and limit lateral movement; encrypt internal traffic. Monitor all requests and sessions; if behaviour deviates from baseline, trigger re‑authentication or block access. For workloads and APIs, use dynamic authorisation and enforce continuous validation. These measures map to the security TSC points of focus CC6 (logical and physical access), CC7 (system operations) and CC9 (risk mitigation).
5) Maintain documentation, evidence and reporting readiness
Use version‑controlled documentation for policies, procedures and system descriptions. Automate log collection from infrastructure, applications and third‑party services. Retain logs in a central repository with correlation and alerting capabilities. Document control performance with evidence such as access reviews, change records, vulnerability scans, incident tickets and vendor assessments. Keep track of Service Level Agreements (SLAs) for vulnerability remediation and incident response. Conduct internal audits at least quarterly to verify control operation. When working with Konfirmity, we handle evidence collection and organise it for auditors, reducing the burden on your team.
6) Plan for regular reassessment and continuous compliance
SOC 2 Type II demands sustained evidence across 64+ control points. Treat compliance as a continuous operation, not a project. Schedule recurring control activities—such as monthly patching, quarterly access reviews and annual risk assessments. Refresh your SOC 2 report at least annually; some enterprise clients require semi‑annual assessments. Integrate SOC 2 with ISO 27001 surveillance audits, HIPAA risk analyses and GDPR Data Protection Impact Assessments (DPIAs) to streamline effort. Maintain an audit calendar and assign owners for each control. A human‑led managed service ensures continuity when personnel change or budgets fluctuate.
SOC 2 and Enterprise Sales: Using Compliance as a Trust Signal
Security diligence now happens early in procurement. Enterprise buyers issue lengthy questionnaires, request SOC 2 reports, BAAs, DPAs and security addenda, and scrutinise control evidence. Deals can stall if vendors cannot answer questions or provide recent attestation. A current SOC 2 report tells buyers that your controls have been independently tested. For healthcare buyers, demonstrating HIPAA compliance and strong privacy controls builds confidence.
When you use a managed service like Konfirmity, you are always ready for due diligence. We integrate controls into your product and infrastructure, collect evidence automatically and maintain your SOC 2 report. This approach gives you a response advantage—deals close faster because you can provide auditors and procurement teams with clear, up‑to‑date documentation. It also differentiates you from competitors who rely on self-serve GRC tools or one‑off consultants. We design and operate the controls so that compliance follows naturally, not as an after‑thought.
Conclusion
The SOC 2 What Changed In 2026 conversation is less about a new framework and more about an evolving operating environment. Continuous risk assessment, robust vendor management, adoption of zero‑trust architectures, tighter reporting standards, cross‑framework integration and greater transparency are shaping expectations. For companies selling to enterprise and healthcare clients, SOC 2 is no longer optional; it is a de facto requirement that must be renewed regularly and supported by real security operations.
At Konfirmity, we believe security that looks good on paper but fails under incident pressure is a liability. Start with risk and controls, design a programme that operates every day, and let compliance follow. A human‑led, managed service—backed by thousands of audits and decades of experience—can give you the capacity and confidence to meet 2026 demands and win enterprise business.
Frequently Asked Questions
1. What technology trends will matter in 2026?
SOC 2 audits will increasingly evaluate adoption of zero‑trust security, advanced identity management, cloud‑native architectures and automation of compliance workflows. Auditors will expect continuous monitoring, dynamic authorisation, data classification and encryption across multi‑cloud environments. Tools that map controls to frameworks and automate evidence collection will become standard.
2. What is the future of SOC 2?
SOC 2 is moving toward continuous compliance, with greater integration into other regulatory regimes. Future SOC 2 examinations may require real‑time evidence feeds, richer vendor risk and supply‑chain assurance, and alignment with standards such as ISO 27001, HIPAA, GDPR and DORA. Dynamic risk management and proof of operational security will be central.
3. Is SOC 2 legally required?
SOC 2 is a voluntary standard. However, many enterprise and healthcare clients treat it as a contractual requirement. They may refuse to do business with vendors lacking a SOC 2 report or other acceptable assurance (such as ISO 27001 certification). Obtaining and maintaining SOC 2 compliance is therefore essential for market access.
4. What are the five criteria for SOC 2?
The Trust Services Criteria are Security, Availability, Processing Integrity, Confidentiality and Privacy. Security is mandatory; the others are included based on the nature of services and client expectations. Each criterion has points of focus and requires multiple controls to provide coverage.
5. What is the difference between SOC 2 Type I and Type II?
A Type I report evaluates the design of controls at a single point in time, while a Type II report tests both design and operating effectiveness over a period. Most enterprise buyers prefer Type II reports because they demonstrate that controls operate reliably day‑to‑day.
6. How often should you refresh your SOC 2 compliance?
Most organisations renew their SOC 2 Type II report annually. Highly regulated clients or fast‑growing vendors may refresh every six months. Continuous monitoring and internal audits help ensure control effectiveness between attestation cycles.





.svg)





.svg)
.svg)