Healthcare security leaders today face a compounding challenge. You are not only responsible for securing patient data against increasingly sophisticated ransomware attacks but also for proving that security to a growing list of stakeholders. Regulators, cyber insurance carriers, and enterprise partners all demand evidence of due diligence.
For many organizations, the Health Insurance Portability and Accountability Act (HIPAA) is the baseline. However, HIPAA is descriptive, not prescriptive. It tells you what to do (protect patient data) but not exactly how to build the architecture to do it. This is where the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) becomes critical.
The industry struggle is palpable. Security teams often manage HIPAA compliance in one silo and operational security in another. This leads to redundant work, "compliance manufacturing," and gaps in coverage that attackers exploit. By integrating these approaches, organizations can build a durable security posture that naturally satisfies regulatory requirements.
The most effective way to bridge this gap is by ensuring HIPAA Controls Mapped To NIST CSF are central to your strategy. This alignment translates the legal requirements of HIPAA into the operational language of NIST, allowing technical teams to execute security measures that satisfy compliance mandates simultaneously.
In this guide, we will break down the practicalities of this mapping, drawing from Konfirmity’s experience supporting over 6,000 audits. We will move beyond theory into the operational realities of protecting electronic Protected Health Information (ePHI) in a modern, threat-heavy environment.
Understanding HIPAA Security and Privacy Obligations
HIPAA remains the primary regulatory standard for US healthcare, designed to ensure that individuals’ health information is properly protected while allowing the flow of health information needed to provide high-quality health care.
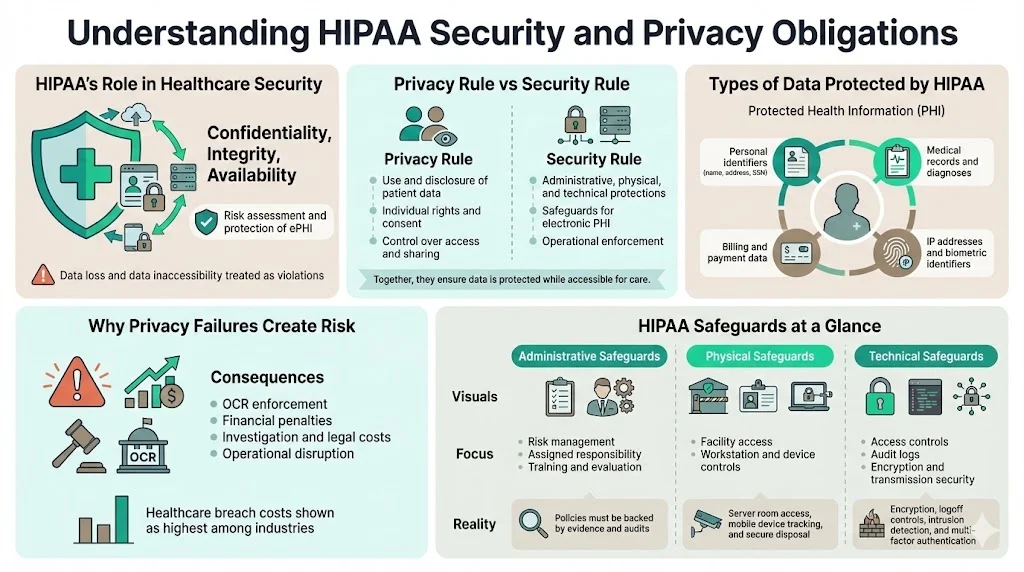
Brief Overview of HIPAA’s Role in Healthcare Security
HIPAA’s role extends beyond simple confidentiality. It mandates the integrity and availability of data. If a hospital cannot access patient records due to a ransomware attack, that is a HIPAA violation just as much as a data breach is. The regulation forces organizations to assess risks to ePHI and implement appropriate protections.
Difference Between the HIPAA Security Rule and Privacy Rule
It is vital to distinguish between these two pillars:
- The Privacy Rule addresses the saving, accessing, and sharing of medical and personal information. It focuses on an individual’s right to control the use of their personal health information.
- The Security Rule specifically operationalizes the protections for ePHI. It defines the standards for the administrative, physical, and technical safeguards required to ensure the confidentiality, integrity, and security of electronic protected health information.
Types of Patient Data Protected
HIPAA protects any information held by a covered entity regarding health status, provision of health care, or payment for health care that can be linked to an individual. This includes:
- Names, addresses, and SSNs.
- Medical records and diagnoses.
- Billing and payment history.
- IP addresses and biometric identifiers used in hospital systems.
Why Data Privacy Failures Create Legal and Operational Risk
The Department of Health and Human Services (HHS) Office for Civil Rights (OCR) actively enforces these rules. Beyond fines, which can reach millions of dollars, the operational cost of a breach involves forensic investigations, legal fees, and reputational damage. In 2024, the average cost of a healthcare data breach reached nearly $11 million, the highest of any industry.
Subsection: HIPAA Safeguards at a Glance
HIPAA partitions its requirements into three distinct categories.
Administrative Safeguards
These are the policies and procedures designed to manage the selection, development, implementation, and maintenance of security measures.
- Focus: Security management processes, assigned security responsibility, workforce training, and evaluation.
- Operational Reality: This is where many fail. You might have a policy on paper, but if you lack evidence of monthly access reviews or annual risk assessments, you are non-compliant.
Physical Safeguards
These control physical access to protect against inappropriate access to protected data.
- Focus: Facility access controls, workstation use, and device and media controls.
- Operational Reality: This includes badge access systems for server rooms and increasingly, the tracking of mobile devices and laptops containing ePHI.
Technical Safeguards
These are the technology and the policy and procedures for its use that protect ePHI and control access to it.
- Focus: Access control, audit controls, integrity, person or entity authentication, and transmission security.
- Operational Reality: This involves encryption at rest and in transit, automatic logoff features, and intrusion detection systems.
What Is the NIST Cybersecurity Framework (CSF)?
While HIPAA provides the "what," NIST CSF provides the "how." Created by the National Institute of Standards and Technology, the CSF consists of standards, guidelines, and best practices to manage cybersecurity-related risk.
Purpose of NIST CSF in Modern Cybersecurity Standards
NIST CSF was designed to be a voluntary framework for critical infrastructure, but it has become the gold standard for private industry. It provides a common language for understanding, managing, and expressing cybersecurity risk to internal and external stakeholders.
Why NIST CSF Fits Healthcare Environments
Healthcare environments are complex, mixing legacy on-premise mainframes with cloud-native applications and IoT devices. NIST CSF allows organizations to apply risk management principles across this diverse stack. It moves security from a "checklist" mentality to a risk-based approach, which aligns perfectly with HIPAA’s requirement to conduct an accurate and thorough risk analysis.
The Five NIST CSF Functions
The framework organizes basic cybersecurity activities at their highest level.
1) Identify
Develop an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
- Healthcare Context: You cannot protect patient data if you do not know where it lives. This involves asset management and governance.
2) Protect
Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.
- Healthcare Context: This covers identity management, awareness training, and data security protection (encryption).
3) Detect
Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
- Healthcare Context: Continuous monitoring of networks for anomalies that could indicate a breach.
4) Respond
Develop and implement the appropriate activities to take action regarding a detected cybersecurity event.
- Healthcare Context: Having an Incident Response Plan (IRP) that includes notifying affected patients and the HHS if a breach occurs.
5) Recover
Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired.
- Healthcare Context: Restoring clinical data from backups to resume patient care.
Why Map HIPAA Controls to NIST CSF?
Managing HIPAA in isolation often leads to a "paper shield"—a compliance program that exists in binders but not in the server room.
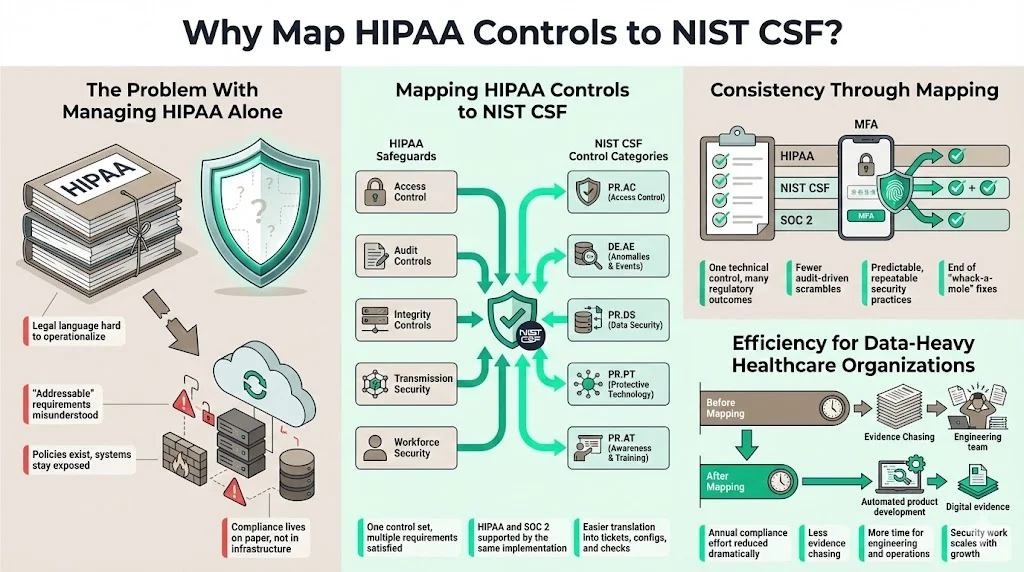
Challenges of Managing HIPAA in Isolation
HIPAA’s language can feel outdated. Terms like "addressable implementation specifications" often confuse IT teams. Does "addressable" mean optional? (Hint: No, it means you must implement it or an effective alternative). Without a modern framework, teams struggle to translate these legal terms into Jira tickets or configuration settings.
Benefits of Security Controls Mapping
When you utilize a strategy with HIPAA Controls Mapped To NIST CSF, you create a unified control set. Instead of one set of protocols for your HIPAA audit and another for your SOC 2 Type II attestation, you implement a single high-standard control that satisfies both.
How Mapping Supports Consistent Healthcare Security Practices
Mapping ensures consistency. If NIST recommends multi-factor authentication (MFA) for remote access (PR.AC-7), implementing that control satisfies the NIST requirement and the HIPAA technical safeguard for access control and authentication. This reduces the "whack-a-mole" approach to security where teams scramble to fix individual issues based on which auditor is visiting.
Value for Organizations Handling Large Volumes of Patient Data
For enterprise healthcare companies, efficiency is capital. Konfirmity’s data shows that organizations using a mapped, managed approach reduce their internal compliance effort from 550–600 hours annually to approximately 75 hours. This releases key engineering talent to build product features rather than chase evidence artifacts.
HIPAA Controls Mapped To NIST CSF: Core Crosswalk
This section details the operational crosswalk. This is not just about matching text; it is about aligning intent and evidence. A proper HIPAA Controls Mapped To NIST CSF approach ensures that every regulatory requirement has a corresponding operational owner and technical implementation.
Administrative Safeguards Mapped to NIST CSF
Administrative safeguards comprise over half of the HIPAA Security Rule. They align heavily with the Identify and Protect functions of NIST.
Risk Analysis and Risk Management Alignment
- HIPAA: §164.308(a)(1) requires an accurate and thorough assessment of potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI.
- NIST Mapping: This maps directly to Identify (ID.RA).
- Operational Action: Conduct an annual risk assessment. However, do not stop at the PDF report. Use the assessment to drive your vulnerability management program. If the assessment identifies unpatched legacy servers, the remediation plan becomes a measurable operational task.
Workforce Training and Access Control Mapping
- HIPAA: §164.308(a)(5) requires security awareness training for all workforce members.
- NIST Mapping: This maps to Protect (PR.AT) - Awareness and Training.
- Operational Action: Implement automated training tools that track completion rates. Evidence for the auditor is not the policy saying you train people; it is the log showing 100% of employees completed the phishing simulation.
Policies and Procedures Tied to Identify and Protect Functions
- HIPAA: §164.316 requires written policies and procedures.
- NIST Mapping: Identify (ID.GV) - Governance.
- Operational Action: Policies must be living documents. We often see policies last updated three years ago. In a managed service model, these are reviewed annually and updated whenever significant infrastructure changes occur.
Physical Safeguards Mapped to NIST CSF
Physical safeguards are often overlooked in the cloud era, but AWS data centers and your remote employees' laptops fall under this jurisdiction.
Facility Access Controls and Asset Protection
- HIPAA: §164.310(a)(1) requires procedures to control access to physical facilities.
- NIST Mapping: Protect (PR.AC-2) - Physical Access.
- Operational Action: For cloud-native companies, this means reviewing the SOC 2 reports of your hosting providers (AWS, Azure, GCP) to verify their physical security controls. For hybrid companies, it means badge logs and visitor logs.
Device Security and Media Handling
- HIPAA: §164.310(d)(1) covers the receipt and removal of hardware and electronic media.
- NIST Mapping: Protect (PR.DS) - Data Security.
- Operational Action: This is critical for hard drive disposal. You must have certificates of destruction for any server or laptop containing ePHI before it leaves your possession.
Technical Safeguards Mapped to NIST CSF
This is where the rubber meets the road for engineering teams.
Access Control and Authentication
- HIPAA: §164.312(a)(1) requires unique user identification and emergency access procedures.
- NIST Mapping: Protect (PR.AC) - Identity Management, Authentication, and Access Control.
- Operational Action: Implement Single Sign-On (SSO) and enforce MFA everywhere. The "unique user ID" requirement kills shared accounts. If you have a shared "admin" login, you are non-compliant.
Audit Controls and Activity Monitoring
- HIPAA: §164.312(b) requires hardware, software, and/or procedural mechanisms that record and examine activity in information systems.
- NIST Mapping: Detect (DE.CM) - Security Continuous Monitoring.
- Operational Action: Centralize logs. You need to know who accessed ePHI and when. In modern stacks, this means aggregating CloudTrail, application, and database logs into a SIEM or monitoring platform.
Transmission Security
- HIPAA: §164.312(e)(1) requires technical security measures to guard against unauthorized access to ePHI that is being transmitted over an electronic communications network.
- NIST Mapping: Protect (PR.DS-2) - Data-in-transit is protected.
- Operational Action: Enforce TLS 1.2 or higher for all web traffic. Ensure database connections are encrypted. Disable weak ciphers.
Common Gaps Found During HIPAA–NIST Mapping
Even with the best intentions, organizations often leave dangerous gaps. When executing HIPAA Controls Mapped To NIST CSF, we frequently encounter specific areas of failure.
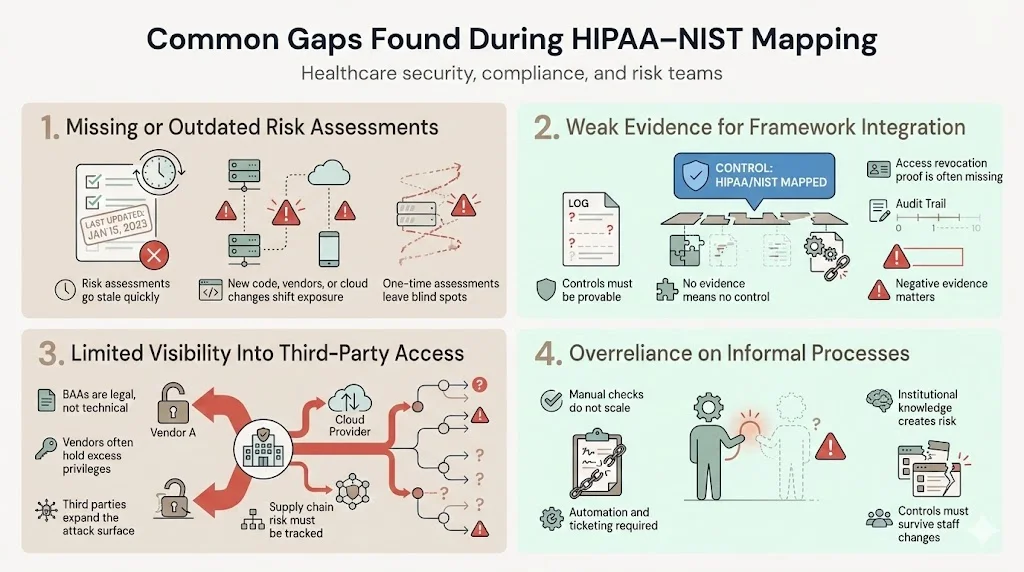
1) Missing or Outdated Risk Assessments
Many organizations treat the risk assessment as a "one-and-done" checkbox for the auditor. A risk assessment from 2023 is useless against 2025 threats. If you have deployed new code, added new vendors, or changed your cloud architecture, your risk profile has changed.
2) Weak Documentation Tied to Security Framework Integration
Auditors function on evidence. If you claim to perform quarterly access reviews but have no tickets, emails, or logs to prove it, the control does not exist. A common gap is the lack of "negative evidence"—proving that you revoked access for a terminated employee within the SLA window (usually 24 hours).
3) Limited Visibility into Third-Party Access
Business Associate Agreements (BAAs) are legally required, but they don't secure your data. We often find that vendors have excessive permissions to ePHI. Mapping to NIST’s Supply Chain Risk Management (ID.SC) helps identify this gap by forcing you to treat vendors as part of your attack surface.
4) Overreliance on Informal Processes
"Jim checks the logs every Monday" is not a scalable control. If Jim goes on vacation or quits, compliance breaks. Informal processes are the enemy of durable security. You need automated alerts and ticketed workflows.
How Mapping Supports Audits and Assessments
The ultimate test of your security program is the audit. Whether it is an OCR investigation following a breach or a routine assessment, the preparation is identical.
Preparing for OCR Audits Using Mapped Controls
The Office for Civil Rights (OCR) has indicated that alignment with recognized security practices, like NIST CSF, can be a mitigating factor during enforcement actions. If you can demonstrate HIPAA Controls Mapped To NIST CSF and show a history of adherence, you demonstrate "good faith" effort.
Clear Evidence Trails for Auditors
Auditors appreciate structure. When you present your evidence organized by NIST functions—which inherently cover HIPAA safeguards—you tell a coherent story. You move from "Here is a pile of documents" to "Here is how we Identify risks, Protect data, and Detect threats."
Reduced Stress During Compliance Reviews
At Konfirmity, we operate on a model of continuous compliance. By maintaining evidence collection year-round, the "audit prep" phase shrinks from a panic-induced month to a simple export of existing data.
Practical Templates for HIPAA Controls Mapped To NIST CSF
Templates provide the structural foundation for your program. However, a template is only as good as the data you put into it.
HIPAA–NIST Crosswalk Template
Your primary tracking document should be a "Source of Truth" matrix.
- Column A: HIPAA Citation (e.g., §164.308(a)(1)(i)).
- Column B: HIPAA Control Description.
- Column C: NIST CSF Subcategory (e.g., ID.RA-1).
- Column D: Internal Control Owner (Job Title).
- Column E: Evidence Location (Link to Jira, S3 bucket, GRC tool).
- Column F: Frequency (Daily, Weekly, Quarterly, Annually).
Using a matrix centered on HIPAA Controls Mapped To NIST CSF ensures that if a NIST control is updated, you immediately see the impact on your HIPAA compliance posture.
Risk Assessment Mapping Template
This template links your HIPAA risk analysis to the NIST Identify function.
- Asset Inventory: List all systems touching ePHI.
- Threat: What could go wrong? (e.g., Ransomware, Insider Threat).
- Vulnerability: Weakness in the asset (e.g., Unpatched OS).
- Likelihood & Impact: Scored 1-5.
- Current Control: What NIST control is currently mitigating this?
- Remediation Plan: Who is fixing it and when?
Policy and Procedure Mapping Template
Align your written policies with cybersecurity standards. Instead of a generic "Security Policy," structure your documentation library to mirror the framework:
- Access Control Policy (Aligns with NIST PR.AC).
- Incident Response Policy (Aligns with NIST RS).
- Business Continuity Policy (Aligns with NIST RC).
This makes it incredibly easy for auditors to find what they need without digging through a 100-page monolithic document.
Implementation Tips for Healthcare Organizations
Moving from a fragmented state to a unified, mapped posture requires a deliberate approach.
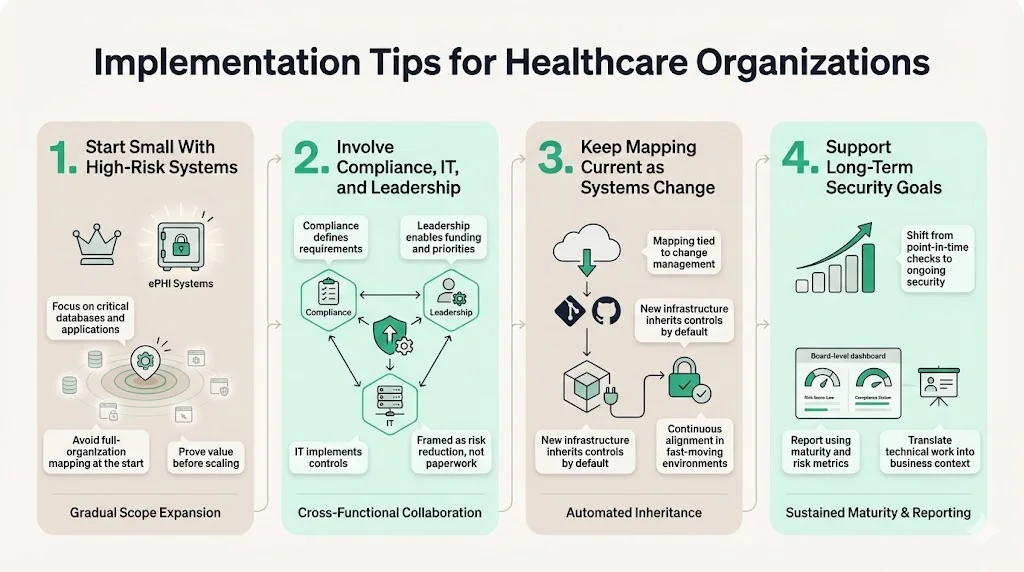
1) Starting Small with High-Risk Systems
Do not attempt to map the entire organization in week one. Start with the "Crown Jewels"—the databases and applications that store, process, or transmit ePHI. Apply the HIPAA Controls Mapped To NIST CSF methodology to this scope first.
2) Involving Compliance, IT, and Leadership
Security is a team sport. Compliance understands the rules, IT understands the tools, and Leadership holds the budget. You need all three. Frame the initiative not as "more compliance work" but as "risk reduction and sales enablement." Enterprise buyers want to see this level of maturity.
3) Keeping Mapping Current as Systems Change
Cloud environments are dynamic. Code is shipped daily. Your mapping must be part of your Change Management process. If you spin up a new Kubernetes cluster, it must immediately inherit the NIST/HIPAA controls defined in your baseline.
4) Supporting Long-Term Healthcare Security Goals
This mapping supports the shift from "point-in-time" compliance to "continuous" security. It allows you to report to the Board of Directors using business-aligned metrics (e.g., "We are at 95% maturity on the NIST 'Protect' function") rather than obscure regulatory jargon.
Conclusion
The demand for rigorous data protection in healthcare will not recede. As threats evolve and patient data becomes more valuable on the black market, the regulatory and commercial pressure to prove security will only intensify.
Adopting a strategy of HIPAA Controls Mapped To NIST CSF is the most logical path forward. It creates clarity out of chaos. It allows your organization to build a security program that is defensible, durable, and operational. Instead of chasing separate requirements for HIPAA, SOC 2, and internal policies, you build a single, strong foundation that supports them all.
At Konfirmity, we believe that you should start with security and arrive at compliance. By focusing on the tangible controls that protect data—and verifying them with continuous evidence—compliance becomes a natural byproduct of good engineering. It is time to move beyond the binders and build a security posture that stands up to auditors, buyers, and attackers alike.
FAQs
1) What is the NIST CSF and why does it matter for HIPAA?
The NIST Cybersecurity Framework (CSF) is a set of guidelines and best practices for managing cybersecurity risk. It matters for HIPAA because while HIPAA demands that you protect data, it doesn't specify the technical details of how to do it. NIST CSF provides the structural "how" that fills the gap left by HIPAA's "what," offering a rigorous methodology for securing ePHI.
2) How do HIPAA safeguards map to NIST CSF functions?
HIPAA’s Administrative, Physical, and Technical safeguards align directly with the NIST functions of Identify, Protect, Detect, Respond, and Recover. For example, the HIPAA requirement for "Risk Analysis" maps to NIST's "Identify" function, while "Access Control" requirements map to the "Protect" function. This HIPAA Controls Mapped To NIST CSF alignment ensures that every regulatory requirement has a corresponding operational security action.
3) Is NIST CSF mandatory for HIPAA compliance?
Technically, no. HIPAA does not mandate the use of NIST CSF. However, the HHS Office for Civil Rights (OCR) and industry auditors widely recognize NIST CSF as the gold standard for demonstrating a complete security program. Using it provides a strong defense and evidence of due diligence during an audit.
4) What gaps are common when mapping HIPAA to NIST CSF?
Common gaps include outdated risk assessments that don't reflect current infrastructure, a lack of documentation or evidence for "Protect" functions (like terminated user access revocation), and insufficient monitoring of third-party vendors (Business Associates). Organizations often fail to link their written policies to actual technical controls.
5) How can mapping help during audits?
Mapping creates a clear "index" for auditors. Instead of searching for scattered evidence, an auditor can look at your HIPAA Controls Mapped To NIST CSF matrix and see exactly how you satisfy each requirement. It speeds up the audit process, reduces back-and-forth questions, and demonstrates a mature, organized control environment.




.svg)






.svg)
.svg)