Most enterprise buyers now request assurance artifacts before procurement. Without operational security and continuous evidence, deals stall—even when teams think they’re audit-ready on paper. IBM’s 2025 Cost of a Data Breach Report found that global breach costs averaged $4.44 million, while U.S. breaches cost $10.22 million, driven by regulatory penalties and slow detection. Attackers are also using artificial intelligence tools in 16 percent of breaches, with shadow usage of these technologies in another 20 percent; 97 percent of such incidents involve weak access controls. Such numbers show that token checklists no longer satisfy buyers. They want to see how you map ISO 27001 Controls Mapped To ISO 27002 and run vulnerability management as a living program.
I’m Amit Gupta, founder of Konfirmity. Over 6,000 audits and more than 25 years of combined field experience have taught our team hard truths: security that looks good on paper but fails under incident pressure is a liability. We see vendors lose deals because they can’t show ongoing vulnerability handling or evidence. Many have spent 550–600 internal hours prepping for a single SOC 2 audit, only to be asked for continuous monitoring later. Our managed service saves them roughly 75 hours per year and gets them audit-ready in 4–5 months instead of nine to twelve. In this article, I explain why ISO 27001 vulnerability management matters, how it ties to business risk and auditor expectations, and how to build a defensible program that maps ISO 27001 Controls Mapped To ISO 27002.
Why vulnerability management matters for enterprise vendors
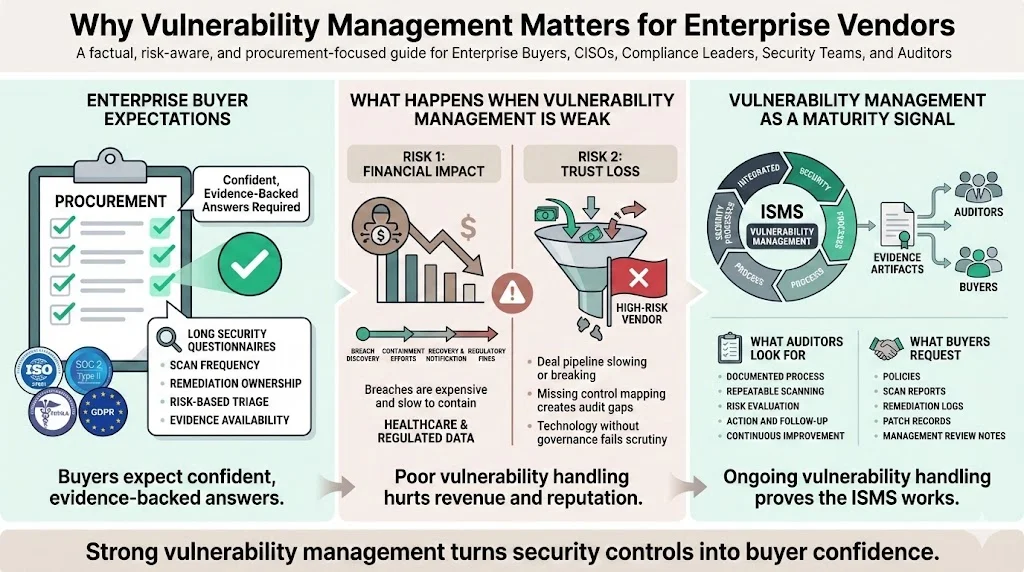
Enterprise buyers and healthcare entities vet vendors rigorously. Procurement questionnaires often exceed a hundred questions and cover frameworks like ISO 27001, SOC 2 Type II, HIPAA, and GDPR. They ask how your team identifies technical vulnerabilities, how often scans run, who owns remediation, and whether findings are triaged based on risk. When vendors can answer confidently—supported by real evidence—deal cycles accelerate.
Ignoring this reality means exposure on two fronts. First, the financial impact of breaches: IBM’s 2025 data shows that healthcare breaches average $7.42 million and take 279 days to contain. Second, the risk of losing buyer trust. Enterprises want to see mapping of controls across frameworks. Without ISO 27001 Controls Mapped To ISO 27002, a vendor may implement technology but fail to show how controls relate to risk treatment or how evidence supports continuous compliance. Auditors recognise this gap quickly.
How buyers and auditors use vulnerability handling as a maturity signal
Auditors evaluate vulnerability management to assess whether a service provider’s Information Security Management System (ISMS) is effective. Indusface’s compliance guide explains that ISO/IEC 27001 embeds vulnerability management as a risk treatment and continuous improvement process. Relevant controls—such as A.12.6.1 (obtain and evaluate information on technical vulnerabilities), A.18.2.3 (regular security reviews) and A.16.1.3 (incident response procedures)—require organisations to collect vulnerability information, assess exposure, and take action. Auditors ask for evidence showing this process is documented, repeatable, and auditable.
Enterprise buyers use similar checks during due diligence. They request policy documents, scan results, remediation logs, patch records, and management review notes to verify that vulnerability handling is ongoing and integrated into risk management. Without this evidence, they may classify a vendor as high-risk and either delay or terminate the procurement.
Understanding vulnerability management in ISO 27001
Vulnerability management is the process of systematically identifying, evaluating, prioritising, and mitigating weaknesses in IT systems, applications, networks, and cloud resources. Sprinto’s ISO 27001 guide notes that the objective is to safeguard confidentiality, integrity, and availability of sensitive data. It is not a one-time assessment; rather, it is an iterative lifecycle that includes asset inspection, discovery, evaluation, risk response, verification, and documentation.
One-time testing versus continuous vulnerability programs
Many companies view vulnerability management as a periodic test—often annual—focused on penetration testing. This approach fails for two reasons:
- Changing threat environment: The National Vulnerability Database recorded over 26,447 vulnerabilities in 2023, a significant jump from 8,051 in the first quarter of 2022. Bluefin’s analysis shows that shadow artificial intelligence usage contributed to 20 percent of breaches in 2025. Waiting a year to scan leaves exposures unaddressed.
- Audit expectations: NIST SP 800-61 r3 emphasises that incident response capabilities must include vulnerability management plans that identify and prioritise vulnerabilities, test responses, and update plans regularly. Auditors expect to see continuous scanning and evidence of prompt remediation. Linford & Company notes that a vulnerability management program is a continuous process defined to identify, evaluate, remediate or accept risks.
A continuous vulnerability program incorporates automated scanning, human validation, risk-based prioritisation, patch management, incident response integration, and ongoing monitoring. It ties back to risk assessment and supports the ISMS.
Where vulnerability management fits in ISO 27001
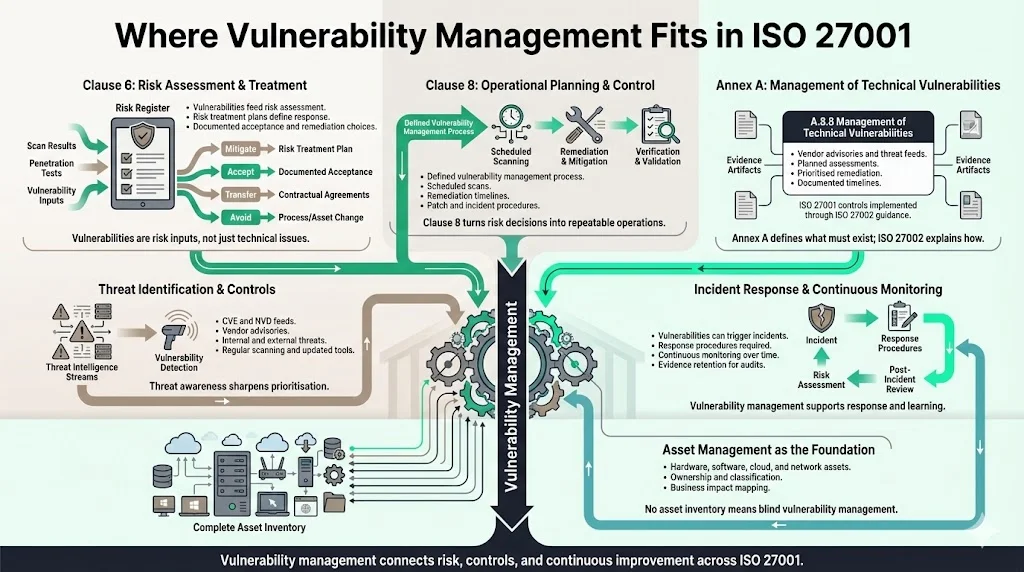
ISO 27001 structures its requirements around clauses that drive risk assessment, operational control, and continuous improvement. Vulnerability management touches multiple areas:
Clause 6: Risk assessment and treatment
Clause 6 requires organisations to identify risks and determine treatment plans. Vulnerabilities identified through scanning and testing feed directly into the risk assessment. The risk treatment plan must address how these vulnerabilities will be mitigated, accepted, transferred, or avoided. Sprinto emphasises the need for a tactical plan that chooses between acceptance, transfer, mitigation, and remediation.
Clause 8: Operational planning and control
Clause 8 mandates that organisations plan, implement, and control processes needed to meet information security requirements. This includes defining the vulnerability management process, setting scan schedules, establishing remediation timelines, and documenting procedures for patch management and incident response. ControlCase notes that ISO 27001:2022 changed Clause 8.1 by adding content on operational planning and control, emphasising the importance of structured operational processes.
Annex A controls
Annex A of ISO 27001:2022 provides reference controls; vulnerability management is addressed explicitly in control A.8.8 Management of Technical Vulnerabilities. DeepAegis explains that organisations must obtain information about technical vulnerabilities, evaluate exposure, and take action promptly. Important activities include subscribing to vendor advisories and threat intelligence feeds, performing assessments at planned intervals, prioritising remediation based on asset criticality, and documenting timelines. Auditors often request evidence of scans, remediation records, and policies defining how vulnerabilities are tracked. Indusface further notes that ISO 27001 controls A.12.6.1, A.18.2.3, and A.16.1.3 require timely vulnerability information, regular reviews, and incident response procedures.
ISO 27001 and ISO 27002 must be considered together; ISO 27001 Controls Mapped To ISO 27002 means using ISO 27002 to implement and map the Annex A controls. ISO 27002 provides guidance on how to apply each control, emphasizing classification by control type, operational capability, security domain, cybersecurity concept, and information security property. Vendors must map their vulnerability management process to the relevant ISO 27002 guidance to ensure that controls are appropriately designed and implemented.
Asset management
Effective vulnerability management starts with a complete asset inventory. TrustCloud describes this as the foundation of vulnerability management; it should include all hardware, software, network components and cloud services. Assets must be linked to business impact so that vulnerabilities can be prioritised accordingly. Sprinto also advises categorising assets based on sensitivity and recording attributes like owner and location.
Threat identification and controls
Organisations need to identify both internal and external threats. Indusface explains that ISO 27001 control A.12.6.1 requires obtaining and evaluating information about technical vulnerabilities. This involves gathering threat intelligence, vendor advisories, and vulnerability databases such as CVE and NVD. NIST SP 800‐61 r3 highlights that vulnerability management plans help identify and assess all types of vulnerabilities and prioritise risk responses. Controls such as RA-5 under NIST SP 800‐53 call for regular scanning and updated tools.
Incident response and continuous monitoring
Vulnerability management does not stand alone; it feeds into incident response. Indusface emphasises that responsibilities and procedures must be in place for quick, effective response to incidents arising from unresolved vulnerabilities. NIST SP 800‐61 r3 states that business continuity and incident response plans should be synchronised with vulnerability management plans. Continuous monitoring, defined under NIST CA-7, requires organisations to collect and analyse scan data over time and to retain evidence of remediation.
Essential ISO 27001 vulnerability management requirements
Documented process, scope and ownership
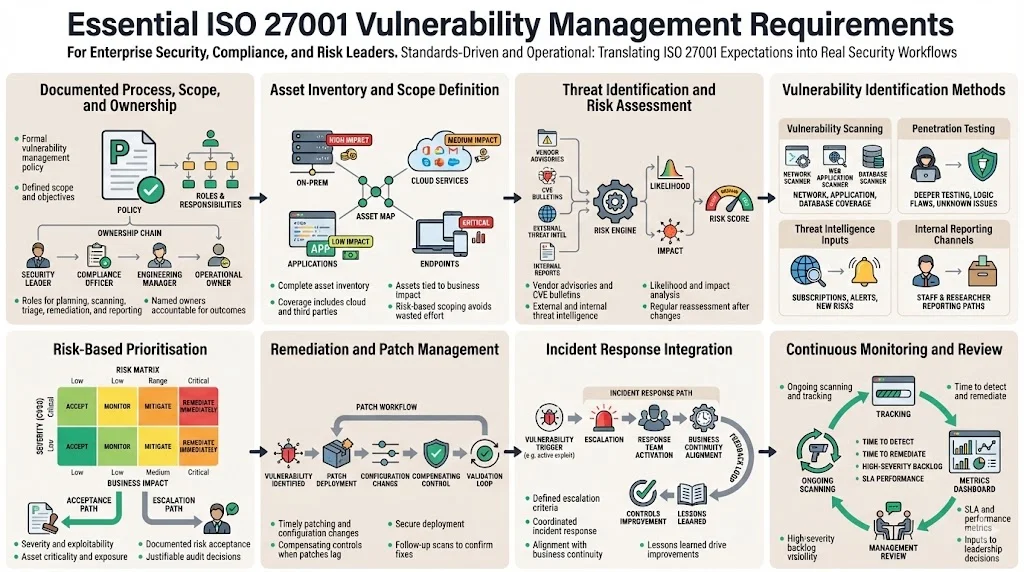
ISO 27001 requires that vulnerability management be documented. TrustCloud defines a vulnerability management policy as a formal document that outlines how organisations identify, evaluate, prioritise, and mitigate security weaknesses. The policy must specify scope (which systems are covered), objectives (reduce risk, ensure compliance, protect data), and roles and responsibilities for scanning, assessing, remediating and reporting. Clear ownership is essential; Sprinto notes that tasks vary: security managers handle planning and procedures, engineers validate and triage vulnerabilities, and large teams may include assessment analysts, incident responders, network admins and compliance officers.
Asset inventory and scope definition
As noted earlier, a detailed asset inventory is the cornerstone of vulnerability management. This includes on-premises infrastructure, cloud services, applications, endpoints and even intangible assets like intellectual property. Each asset should be linked to business impact so that vulnerabilities affecting critical systems receive priority. Linford warns that scanning all assets without understanding their purpose leads to excessive costs and false positives; assets must be selected based on risk.
Threat identification and risk assessment
Organisations must collect internal and external threat intelligence, including vendor advisories, CVE bulletins and threat feeds. Indusface lists control A.12.6.1, which mandates timely information on technical vulnerabilities. NIST RA-5 calls for scanning after significant changes and continuous monitoring Risk assessment involves evaluating the likelihood and impact of vulnerabilities and ranking them using metrics like CVSS scores, business impact and exposure. TrustCloud emphasises regular risk assessments to rank risks effectively.
Vulnerability identification methods
- Vulnerability scanning: Linford explains that scanners identify system flaws across networks, servers, applications and databases. Scans should be both internal and external; internal scans assess threats within the network while external scans look at the attack surface from outside.
- Penetration testing: Penetration tests go deeper than automated scans. While ISO 27001 does not explicitly require penetration testing, auditors often expect it for high-risk systems. Linford notes that SOC 2 CC7.1 criteria require detection and monitoring procedures to identify changes and vulnerabilities. A structured vulnerability management program should include penetration tests to detect business logic flaws and zero-day issues.
- Threat intelligence inputs: Subscribing to vendor advisories, government feeds and commercial threat intelligence helps identify new vulnerabilities quickly.
- Internal reporting channels: Encourage employees and external researchers to report suspected vulnerabilities. TrustCloud highlights the need for ongoing reporting and metrics in vulnerability management.
Risk-based prioritisation
Not all vulnerabilities are equal. The prioritisation framework should consider severity (e.g., CVSS score), exploitability, asset criticality, exposure window and business impact. Sprinto emphasises evaluating vulnerability visibility, exploitability and impact when drafting an action plan. Linford recommends rating vulnerabilities as low, medium and high and prioritising remediation accordingly. Acceptance of risk must be documented, and the organisation should be ready to justify such decisions during audits.
Remediation and patch management
A timely patch management workflow is crucial. Indusface notes that vulnerability management requires obtaining information on vulnerabilities and taking appropriate action promptly. This means tracking vendor patches, deploying updates securely, and applying configuration changes or compensating controls when patches are not yet available. NIST SP 800‐61 r3 stresses that plans should identify resources needed for execution and be periodically reviewed. After remediation, organisations must validate that fixes are effective by performing follow-up scans.
Incident response integration
Some vulnerabilities may trigger immediate incident response. Indusface emphasises that responsibilities and procedures must exist for quick, effective response. NIST SP 800‐61 r3 advocates synchronising business continuity and incident response plans with vulnerability management to ensure coordinated actions. Escalation paths and timelines should be defined, and lessons learned from incidents must feed back into control improvements.
Continuous monitoring and review
Continuous monitoring means ongoing scanning, risk assessment and remediation tracking. TrustCloud lists ongoing monitoring and reporting as essential to ensure vulnerability management remains effective. NIST CA-7 requires continuous monitoring to maintain awareness of vulnerabilities. Metrics should be collected: time to detect, time to remediate, number of high-severity vulnerabilities outstanding, and compliance with service commitments (SLAs). These metrics inform management reviews and help leaders allocate resources.
Vulnerability scanning under ISO 27001
Vulnerability scanning tools identify known security flaws. Linford outlines several types:
- Network scans identify open ports, weak authentication, and misconfigurations from an external perspective.
- Host-based scans analyse individual systems or virtual machines to detect misconfigurations and missing patches.
- Wireless scans target wireless networks to detect misconfigurations that could allow unauthorised access.
- Application scans assess web applications and APIs for flaws like SQL injection and cross-site scripting.
- Database scans inspect databases for misconfigurations and weak authentication.
ISO 27001 does not mandate scan frequency; instead, it emphasises regular reviews. Sprinto advises that scan frequency should reflect asset risk, infrastructure complexity, compliance requirements, and changes. Linford suggests a hybrid model combining continuous monitoring for critical assets and scheduled scans for the wider environment. It is important to tune scans to avoid false positives by selecting appropriate assets and ensuring scanners are up to date.
Penetration testing and ISO 27001
ISO 27001 does not explicitly require penetration testing, but industry practice and auditor expectations often make it necessary, particularly for high-risk systems. Penetration testing does more than scanning by simulating attacks to exploit vulnerabilities. Linford explains that SOC 2 criteria CC7.1 require organisations to identify configuration changes and new vulnerabilities; penetration testing provides evidence that controls work under simulated attack. Sprinto notes that organisations should conduct periodic penetration tests as part of continuous improvement.
Penetration testing evidence can be used during ISO 27001 audits to show that vulnerabilities were exploited, triaged, and remediated. The test scope should cover web applications, APIs, network infrastructure, and cloud services. Results must be documented with risk ratings, remediation actions, and re-testing outcomes.
Prioritisation framework
A strong prioritisation framework helps security teams focus on vulnerabilities that matter most. Consider:
- Severity: Use CVSS scores to gauge technical severity. CVSS 9.0–10.0 vulnerabilities are critical.
- Exploitability: Check whether active exploits exist. Bluefin notes that attackers use artificial intelligence for phishing and deepfakes in 16 percent of breaches.
- Business impact: Evaluate the asset’s importance; a vulnerability on a revenue-generating system merits urgent remediation.
- Exposure: Determine whether the vulnerability is externally accessible or shielded behind controls.
The treatment plan may involve mitigating, remediating, transferring, or accepting the risk. For accepted risks, document justification and revisit them during risk reviews. By mapping vulnerabilities to risk treatment, you show auditors that decisions are deliberate and risk-based.
Required documentation and evidence
Auditors and buyers expect thorough documentation. Evidence should include:
- Vulnerability management policy detailing scope, objectives, roles, identification methods, risk evaluation, remediation timelines, and exception handling.
- Risk assessment records linking identified vulnerabilities to business risks and treatment decisions.
- Scan reports from automated tools, with dates, scope, results, severity ratings, and false positive analysis.
- Remediation logs showing actions taken, responsible teams, dates, and status of each vulnerability.
- Patch management records documenting patch deployment timelines, approvals, and any compensating controls when patches are unavailable.
- Incident response tickets documenting when vulnerabilities triggered incidents, how they were handled, and lessons learned.
- Management review notes summarising metrics, trends, and decisions to improve the vulnerability management program.
Konfirmity provides templated registers and automation that link these pieces of evidence to controls, reducing manual effort.
Policy template for ISO 27001 vulnerability management
A structured policy guides the program and serves as evidence. Your policy should include:
Purpose and scope
Define why the policy exists and which systems it covers. Identify whether it applies to production infrastructure, development environments, endpoints, and cloud services. Establish objectives: protect sensitive data, reduce risk, meet ISO 27001 and other obligations.
Roles and responsibilities
List roles: security manager, engineers, application owners, network admins, compliance officers, incident response team. Describe each role’s responsibilities (e.g., scanning, risk assessment, remediation, reporting, approving exceptions). Ensure accountability.
Vulnerability identification methods
Document tools and techniques used: vulnerability scanners, penetration tests, code reviews, threat intelligence feeds, internal reporting channels. Specify scan schedules and scope.
Risk evaluation approach
Describe how vulnerabilities are prioritised. Include criteria such as severity, exploitability, asset importance, and business impact. Define how risk ratings map to remediation timelines (e.g., critical vulnerabilities fixed within seven days, high within 30 days, medium within 90 days).
Remediation timelines
Define service targets for fixing vulnerabilities based on their risk rating. Include escalation paths if deadlines are missed. Provide guidelines for testing patches to avoid introducing new issues.
Exception handling
Explain how teams can request exceptions to remediation timelines or risk treatment decisions. Require approval from security leadership and documentation of compensating controls. Ensure exceptions are reviewed regularly.
Customising the template
Adjust scope and language to reflect your environment. Connect to existing security policies (access control, change management, incident response) to avoid conflicting requirements. Write in clear, audit-friendly language. Konfirmity offers a ready-to-use policy mapped to ISO 27001 Controls Mapped To ISO 27002, so vendors can adapt quickly.
Operational templates and logs
In addition to the policy, maintain operational artefacts:
- Vulnerability register: A spreadsheet or database listing each vulnerability, asset, severity, CVSS score, discovery date, remediation status, owner, and comments. Map each entry to the relevant control and risk treatment plan.
- Remediation tracking sheet: A record of actions taken to resolve each vulnerability. Include ticket numbers, responsible individuals, dates of patch deployment, and evidence of validation.
- Patch management log: Track patches applied, pending updates, temporary workarounds, and approvals.
- Exception and risk acceptance document: Document reasons for accepting or deferring remediation, compensating controls, approvals, and review dates.
Common mistakes enterprise vendors make
Through 6,000+ audit engagements, Konfirmity has identified patterns of failure:
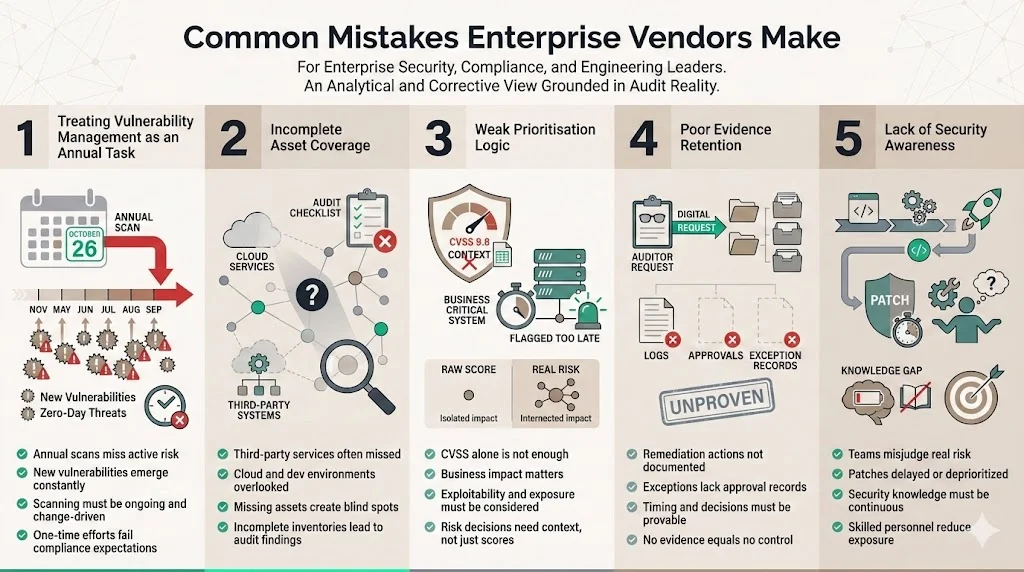
- Viewing vulnerability management as an annual task: Running scans once per year fails to address continuous risk. Threat actors exploit new vulnerabilities quickly. NIST RA-5 requires scanning regularly and after significant changes.
- Incomplete asset coverage: Teams often overlook third-party services, cloud workloads or development environments. TrustCloud emphasises that a detailed asset inventory is essential. Missing assets leads to blind spots and audit findings.
- Weak prioritisation logic: Many teams triage based only on CVSS scores. They don’t consider business impact, exploitability or exposure. Sprinto cautions that visibility and impact must guide the plan.
- Poor evidence retention: Vendors fail to keep remediation logs and approval records. When auditors request proof of timing and decisions, they come up short. Documentation of actions and exceptions is vital.
- Lack of security awareness: Without training, engineering teams may delay applying patches or misjudge risk. NIST SP 800‐61 r3 highlights that personnel must possess knowledge and skills to perform tasks with cybersecurity risks in mind.
Best practices for enterprise-ready vulnerability management
1) Connect vulnerability management with governance
Build the program under the umbrella of your ISMS. Map processes to ISO 27001 Controls Mapped To ISO 27002 to ensure that each control has an operational counterpart. Use your risk assessment to prioritise resources. Conduct management reviews regularly and adjust based on metrics.
2) Raise security awareness across engineering teams
Provide training on vulnerability identification, scanning tools, patch procedures, and documentation. Empower engineers to report vulnerabilities internally. Use role-based training as recommended by NIST SP 800‐61 r3.
3) Automate where possible
Automated scanning and tracking reduce manual error and increase coverage. Use scanners integrated with CI/CD pipelines to catch vulnerabilities early. Implement central dashboards that aggregate scan results, prioritisation, and remediation status. Konfirmity offers tools for continuous evidence collection, linking scans to controls.
4) Keep processes simple but defensible
Don’t overcomplicate. Clear policies, defined roles, risk-based timelines, and documented exceptions create a defensible program. Regularly test procedures through penetration tests and table-top exercises. Ensure that each control referenced in ISO 27001 Controls Mapped To ISO 27002 has a visible operational activity.
How strong vulnerability management supports sales
Enterprise sales cycles often hinge on security reviews. Vendors with strong vulnerability management can answer questionnaires faster and provide evidence proactively. This reduces friction during vendor risk reviews and builds trust. When you demonstrate a documented policy, continuous scan reports, timely remediation, and management oversight, buyers see maturity.
Konfirmity’s clients often report shorter sales cycles because they supply a full set of evidence at once. By operating a managed vulnerability program mapped to ISO 27001 Controls Mapped To ISO 27002, we help them move through procurement more quickly. Buyers appreciate transparency; they spend less time asking follow-up questions, and deals close sooner.
Conclusion
The 2025 threat environment demands more than annual testing. With average global breach costs at $4.44 million and rising U.S. penalties, enterprise vendors must regard vulnerability management as a core operational discipline. ISO 27001, supported by ISO 27002, provides the framework. Controls such as A.12.6.1, A.18.2.3, A.16.1.3 and Annex A.8.8 require organisations to obtain vulnerability information, assess risk, act quickly, and document evidence. NIST RA-5 and SP 800‐61 r3 mirror these expectations, stressing regular scanning, continuous monitoring, and integration with incident response.
A durable program involves a documented policy, complete asset inventory, risk-based prioritisation, timely patching, integration with incident response, continuous monitoring, and solid evidence. Vendors must map ISO 27001 Controls Mapped To ISO 27002 to real workflows. With human-led expertise and automation, Konfirmity builds and runs such programs, saving clients hundreds of hours and turning compliance into a by-product of sound security. As enterprise buyers tighten due diligence and regulations change through 2026, mature vulnerability management will remain a non-negotiable requirement.
Frequently asked questions
1. What does ISO 27001 require for vulnerability management?
ISO 27001 mandates ongoing identification, assessment, and treatment of vulnerabilities. Controls A.12.6.1, A.18.2.3 and A.16.1.3 require organisations to obtain information about technical vulnerabilities, review security regularly, and establish incident response procedures. Annex A.8.8 requires obtaining vulnerability advisories, assessing exposure, and taking action. Processes must be documented and linked to risk treatment plans.
2. How often should vulnerability scans run?
ISO 27001 does not specify a strict frequency. Sprinto suggests basing scan intervals on asset risk, infrastructure complexity, compliance obligations and change frequency. Linford recommends continuous monitoring for critical assets combined with scheduled scans. NIST RA-5 requires scanning regularly and after significant changes.
3. Is penetration testing mandatory under ISO 27001?
Penetration testing is not explicitly mandated, but auditors often expect it for high-risk systems. It complements vulnerability scanning by simulating attacks, uncovering business logic flaws and validating controls. SOC 2 criteria CC7.1 emphasise detection and monitoring of configuration changes and new vulnerabilities. A strong program includes periodic penetration tests.
4. What evidence do auditors ask for?
Auditors request the vulnerability management policy, risk assessment records, scan reports, remediation logs, patch management records, incident response tickets and management review notes. They look for proof that vulnerabilities are identified, prioritised based on risk, remediated within defined timelines, and that exceptions are documented.
5. How are vulnerabilities prioritised?
Prioritisation combines severity scores (e.g., CVSS), exploitability, business impact, and exposure. Vulnerabilities with high severity and impact on critical assets should be addressed immediately. Risk acceptance must be documented and revisited during risk reviews.





.svg)






.svg)
.svg)