Most enterprise buyers now ask for concrete assurance that their suppliers meet security and privacy benchmarks before signing a purchase order. Having a report that proves your controls operate effectively across security, availability and privacy can be the difference between closing a seven‑figure deal and watching it stall for months. At Konfirmity, we’ve guided more than 6,000 audits with a dedicated team that has over 25 years of combined delivery experience. Through those engagements we’ve seen how one concept underpins every strong program: collect and keep only the information you need. This SOC 2 Data Minimization Guide explains why that principle matters, how it links to the SOC 2 Trust Services Criteria, and how to make it part of your day‑to‑day operations.
For context, a SOC 2 examination reports on controls at a service organisation that are relevant to security, availability, processing integrity, confidentiality and privacy. Enterprise customers and regulators depend on these reports to judge whether a provider’s safeguards are sufficient. Data minimization fits squarely within the privacy and confidentiality categories. It is also central to broader compliance obligations such as HIPAA’s minimum necessary rule and the data minimisation principle in the UK GDPR. In recent years, enforcement agencies from California’s CPPA to the EU’s regulators have emphasised that organisations must collect only the personal data they truly need and dispose of it when it is no longer required.
This guide is written for chief technology officers, security leaders and compliance officers at companies selling into large enterprises and healthcare organisations. It translates legal and auditing requirements into practical measures you can implement across your stack. We’ll explore the Trust Services Criteria, break down the steps to implement data minimization, describe supporting technical practices, warn about common mistakes, and show how these efforts shorten sales cycles. Throughout the piece you’ll see examples from Konfirmity’s managed service: typical SOC 2 readiness takes four to five months with our help versus nine to twelve months when managed in‑house, and clients save hundreds of hours each year because we handle evidence collection and control operations.
What is Data Minimization?
Data minimization is the practice of limiting the personal or sensitive information you collect, store and process to the smallest amount needed for a defined purpose. The UK’s Information Commissioner’s Office states that organisations must ensure personal data is adequate, relevant and limited to what is necessary. This means you should be able to articulate why each data element is needed and demonstrate that you routinely remove excess. The principle appears in several regulations: the HIPAA Privacy Rule requires covered entities to make reasonable efforts to use, disclose and request only the minimum necessary protected health information; the GDPR mandates that personal data be limited to what is necessary for the purpose of processing and retained for no longer than necessary; and California’s CPPA notes that data minimization is a foundational obligation under the state’s consumer privacy law.
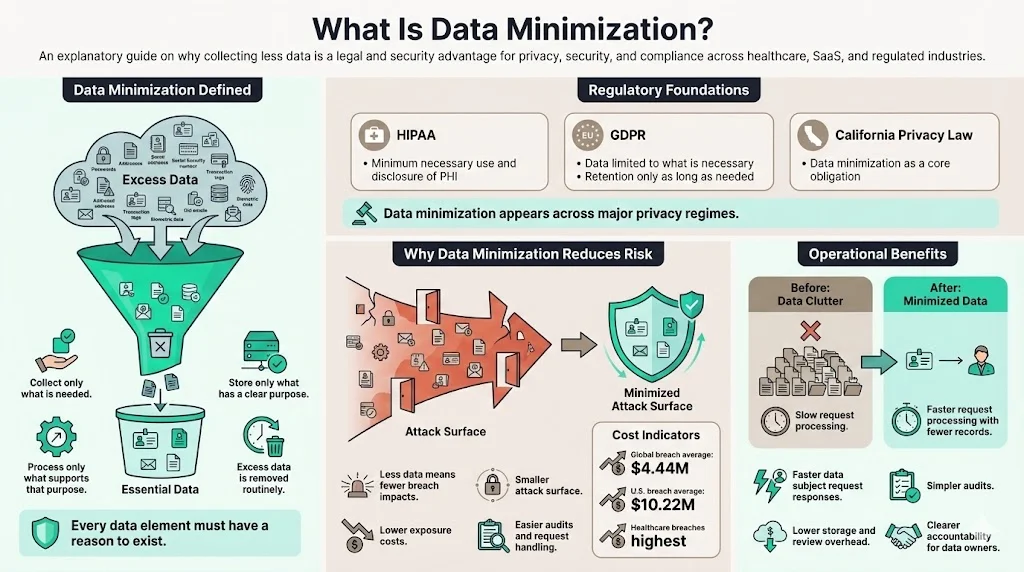
Data minimization isn’t just a checkbox for legal compliance. Holding less sensitive information lowers your attack surface and reduces the impact if a breach occurs. The 2025 data breach statistics from DeepStrike show that the global average cost of a breach was $4.44 million while U.S. breaches averaged $10.22 million. Healthcare incidents remained the costliest at $7.42 million. Every record you keep that isn’t required exposes you to these potential costs. Minimizing data also makes it easier to respond to data subject requests and audits because there is less information to review.
SOC 2 and the Trust Services Criteria
SOC 2 is based on the Trust Services Criteria developed by the American Institute of Certified Public Accountants. These criteria align with the COSO Internal Control Framework and cover five categories: security, availability, processing integrity, confidentiality and privacy. The security category (often called common criteria) underpins everything, while the other categories add specific requirements. Enterprise clients often insist on SOC 2 Type II reports because they include evidence of control operation over an observation period (usually three to twelve months) rather than just design at a point in time.
Data minimization maps to two categories: confidentiality and privacy. The Trust Services Criteria distinguish confidentiality from privacy by noting that confidentiality covers all sensitive information, while privacy applies only to personal information. Confidentiality requirements focus on protecting sensitive information from unauthorised access or disclosure. Privacy requirements go further, addressing the collection, use, retention, disclosure and disposal of personal information. These criteria require the entity to provide notice to data subjects, obtain consent when appropriate, limit use and retention, provide access for correction, and dispose of personal information to meet its objectives. Implementing data minimization helps satisfy both confidentiality and privacy criteria by ensuring your system holds only necessary personal data and has clear policies for retention and deletion.
How Data Minimization Fits into SOC 2
During a SOC 2 audit, service auditors evaluate whether your controls meet the relevant criteria. For data minimization this means examiners look at how you limit collection, use, retention and disposal of personal information. They review policies that define what data is needed, how you obtain consent, and what retention periods apply. They also test whether controls operate effectively over time—for example, whether your systems enforce field‑level data collection rules and whether deletion jobs actually purge records at the end of their retention period. The privacy criterion emphasises collection, choice/consent, use/retention/disposal, access, disclosure/notification, quality and monitoring. Each of these subcriteria has points of focus that auditors use as guidance. Examples include limiting collection to information needed for the entity’s objectives, ensuring personal information is only used or retained to meet those objectives, and providing data subjects with notice and choice.
Data minimization also intersects with internal control and information governance. Controls must be documented, assigned to control owners, and monitored. Auditors expect to see a structured data inventory, documented retention schedules, and evidence of deletion processes. When you embed data minimization into your systems, it reduces the volume of data to be tested, thereby simplifying the audit and reducing the chance of findings. Our managed service sets up automated tasks to enforce retention and deletion so that evidence is generated continuously rather than as an afterthought before the audit.
Key Steps to Implement Data Minimization
Implementing data minimization requires a structured plan. Below are key phases that we use when guiding clients through this work.
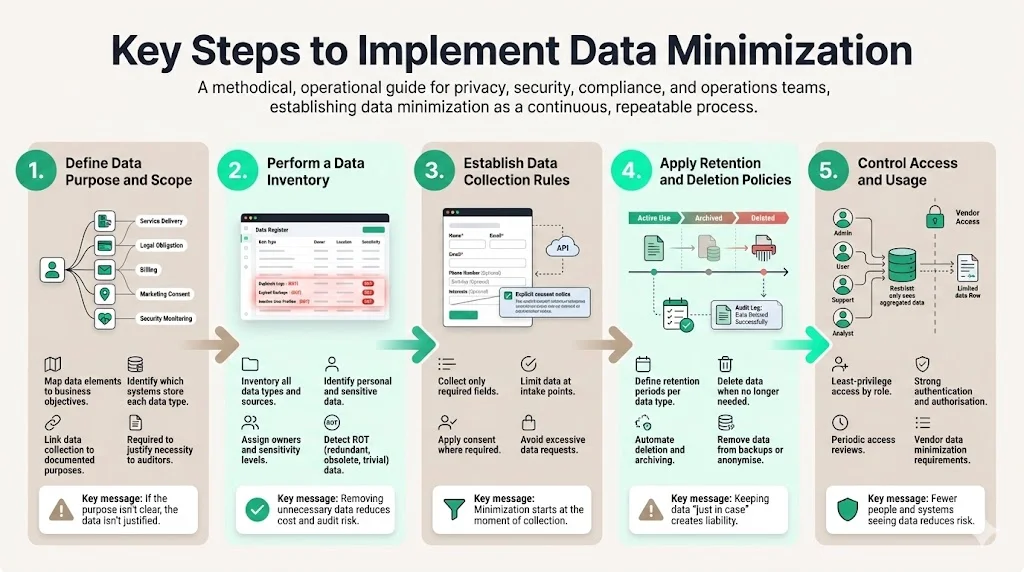
1) Define Data Purpose and Scope
Start by cataloguing why you collect each type of data. Map business objectives to specific data elements and identify which systems hold them. For example, you might collect email addresses for account access, transaction histories to fulfil billing obligations, and health information only if you provide healthcare services. Link each data element to a documented purpose in your privacy notice and internal policy. This mapping is essential for SOC 2 and regulatory compliance because you must justify your data collection to auditors and regulators. Without clear purposes it is impossible to decide what is necessary.
2) Perform a Data Inventory
Create a complete inventory of the data your organisation holds. Capture data types, sources, storage locations, owners and sensitivity levels. Identify whether the data is personal or sensitive, such as protected health information or payment card data. Evaluate each element against its purpose: does it directly support a business process or contract? Is it required by law or a customer agreement? If not, plan to stop collecting it or to purge existing records. Our experience shows that many organisations discover redundant, obsolete or trivial data during this exercise—also called ROT data. Eliminating this data reduces storage costs and improves audit readiness.
3) Establish Data Collection Rules
Once you understand what data you need, implement controls to ensure you only collect essential data at each interaction point. Define requirements for web forms, APIs and third‑party integrations. Only require mandatory fields when the data is needed to provide the service. Implement consent processes where required by law, ensuring that individuals know why you are collecting their data and how you will use it. California’s CPPA advisory notes that businesses should apply data minimization to every purpose for which they collect, use, retain or share personal information. It also warns that organisations should not request excessive information to process consumer requests. Your policies should mirror these expectations.
4) Apply Retention and Deletion Policies
Define how long each data type should be retained based on business needs, contracts and regulatory requirements. Set deletion schedules that purge data at the end of its useful life. The HIPAA Privacy Rule requires covered entities to make reasonable efforts to use and disclose only the minimum necessary information, implying that data should not be retained indefinitely. Reuters’ Practical Law journal emphasises that organisations are increasingly restricted to collecting only needed personal data, using it for explicit purposes and disposing of it once it is no longer required. Document your retention periods and deletion procedures so auditors can verify them. Implement automated tasks or cron jobs to delete or archive records on schedule and generate logs that serve as audit evidence. When deleting data from active systems, ensure it is also removed from backups or anonymised.
5) Control Access and Usage
Minimizing data also means controlling who can access it. Adopt least‑privilege policies so that employees and service accounts only see data necessary for their roles. Implement strong authentication and authorisation controls. Perform periodic access reviews and revoke accounts that are no longer needed. When working with vendors, verify that they maintain comparable controls and collect only the data needed to deliver their services. Supply chain breaches were involved in about 30% of incidents in 2025, so vendor management is a significant part of reducing risk. Include data minimization clauses in contracts with processors and subprocessors, and obtain evidence of their retention and deletion practices.
Technical and Operational Practices
Technology can streamline data minimization. Use automated discovery and classification tools to scan your databases, object stores and file systems for personal data. Label data based on sensitivity and retention requirements. Implement pseudonymization or tokenization to reduce the exposure of personal information in development and testing environments. When possible, collect aggregated or anonymous data instead of identifiable data to achieve your business purpose. For instance, storing hashed identifiers instead of raw email addresses can enable user management without exposing contact details.
Apply privacy‑by‑design principles in your development process. Ensure product managers and engineers understand the data minimization rules and implement them as acceptance criteria. Automate retention and deletion through scheduled jobs that are monitored for success. Use monitoring dashboards to surface metrics like percentage of records deleted on time and number of overdue records. During incidents, having less data makes for shorter investigation and notification cycles because there are fewer records to examine.
Operationally, assign clear ownership for each data set. Control owners should monitor compliance with retention schedules and respond to audit requests. Maintain a record of processing activities and data flow diagrams. During SOC 2 audits, auditors will sample evidence such as data inventory lists, deletion job logs and access review records. By embedding data minimization into your regular processes, you generate continuous evidence rather than scrambling to collect proof at the last minute.
Integrating Data Minimization with Other SOC 2 Controls
Data minimization does not stand alone. It integrates with the security, confidentiality and privacy controls across SOC 2. Risk management processes identify where personal data resides and assess threats to it. Access control and change management ensure that data is used appropriately. Incident response procedures define how to handle breaches involving personal data, including notification requirements. Vendor management processes evaluate whether third parties adhere to data minimization standards.
Minimizing data also reduces audit complexity. When there is less data and fewer storage locations, auditors have fewer samples to review and your team spends less time producing evidence. Konfirmity’s clients benefit from our control mapping across frameworks: we design controls that satisfy SOC 2 as well as ISO 27001, HIPAA and GDPR requirements. For example, a single data inventory and retention schedule can serve as evidence for SOC 2 confidentiality, ISO 27001 Annex A control 5.36 (retention), and GDPR Article 5(1)(c). Our end‑to‑end managed service means we don’t just advise—we implement controls inside your stack and run them continuously, producing evidence year‑round.
Common Pitfalls and How to Avoid Them
- Collecting data “just in case.” Many teams gather extra fields in sign‑up forms or logs because they think the information might prove useful later. This not only increases the risk of breach but also violates the minimization principle. The CPPA advisory warns that businesses should not collect beyond what is necessary to process consumer requests. To avoid this, require each data field to have a defined purpose approved by a data owner.
- Failing to document policies. Without written policies, your intentions are invisible to auditors and regulators. Define and publish data collection, retention, deletion and access policies. Ensure employees are trained on them and that evidence—such as signed policy acknowledgements and training records—is available.
- Ignoring ROT data. Over time, systems accumulate redundant, obsolete or trivial data. Reuters’ Practical Law notes that organisations are increasingly restricted to collecting only personal data they need and disposing of it appropriately. Plan regular clean-up initiatives to remove ROT data. Use scripts or tools to identify files or records that have not been accessed within a defined period and either archive or delete them.
- Automated processes without governance. Automation is essential for efficiency, but it must be backed by governance. Implement logging and monitoring for automated deletion jobs, and have control owners review the results. During our audits we often find deletion scripts failing silently. Set alerts to detect job failures and track them through a remediation process.
Benefits for Enterprise Clients
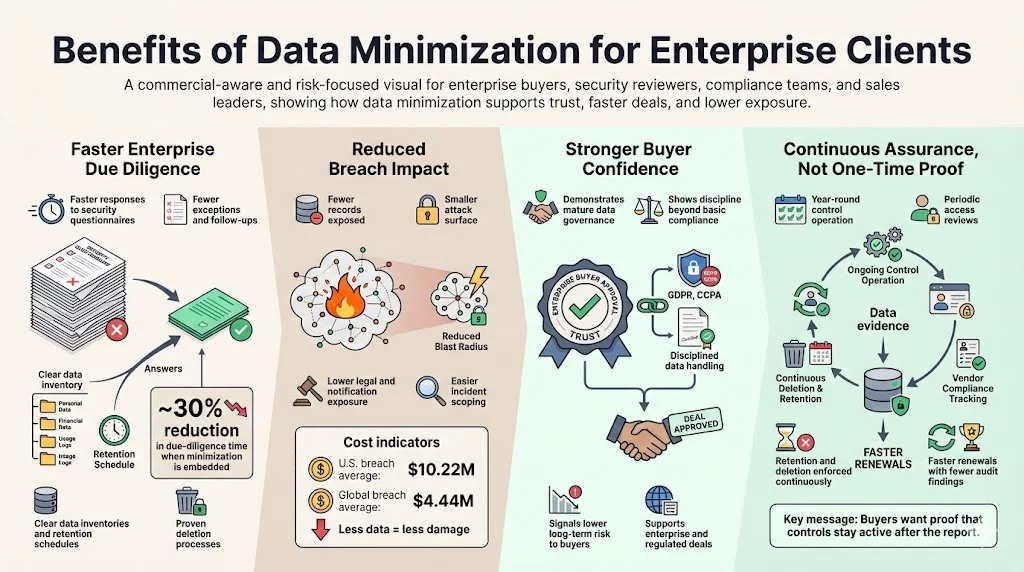
Data minimization isn’t only a compliance exercise—it directly supports enterprise sales. Buyers want assurance that their data will be protected and that you have the discipline to handle it responsibly. When your data minimization program is mature, you can answer security questionnaires quickly and with fewer exceptions. In our experience, companies that embed minimization into their controls cut the time spent on due‑diligence questionnaires by 30% because they can point to clear inventories, retention schedules and deletion evidence. Minimization also reduces breach risk: fewer records means a smaller target and a lower potential impact. The 2025 data breach report shows how expensive breaches remain—$10.22 million per incident in the U.S. and $4.44 million globally. Strong minimization practices can shrink the universe of affected data when an incident occurs, reducing notification obligations and legal exposure.
Enterprise clients also care about ongoing assurance. They want to see that you haven’t simply generated a SOC 2 report and moved on. Through our managed service we operate controls year‑round, perform periodic access reviews, track vendor compliance, and handle retention and deletion. This continuous approach leads to fewer findings and faster renewals; most of our clients pass their SOC 2 Type II audits with minimal issues.
Conclusion
Data minimization is a core discipline for any organisation that handles personal or sensitive information. It is central to the SOC 2 Trust Services Criteria, especially confidentiality and privacy, which require controls over collection, use, retention, disclosure and disposal. Regulators from HIPAA to GDPR and the CPPA require organisations to limit the data they collect and dispose of it when no longer needed. Minimizing data reduces your attack surface, lowers breach costs, and simplifies audits. By following the steps laid out in this SOC 2 Data Minimization Guide—defining data purpose, inventorying data, establishing collection rules, applying retention and deletion policies, and controlling access—you build a program that stands up to buyers, auditors and attackers alike.
Konfirmity’s human‑led, managed security and compliance service embodies this philosophy. We start with security and arrive at compliance, implementing controls inside your environment and running them every day. Our clients achieve SOC 2 readiness in four to five months instead of nine to twelve months, and they save hundreds of hours every year because we manage the evidence and remediation work. Security that looks good in documents but fails under incident pressure is a liability; build your program once, operate it daily, and let compliance follow.
Frequently Asked Questions
1. What does data minimization mean in the context of SOC 2?
It means limiting the collection, use and retention of personal or sensitive data to only what is truly needed for business purposes. This principle aligns with the SOC 2 confidentiality and privacy criteria and with external regulations such as HIPAA’s minimum necessary standard and the GDPR’s data minimisation principle.
2. Is data minimization required for every SOC 2 audit?
Not every SOC 2 engagement covers privacy, but data minimization practices still support both confidentiality and privacy criteria. Even when you report only on security and availability, minimising data helps reduce risk and simplifies audit evidence.
3. How does data minimization reduce risk?
By reducing the amount of data you hold, you shrink the potential attack surface and lower the impact if data is breached. The 2025 breach statistics show that U.S. incidents averaged $10.22 million while the global average was $4.44 million. Less data means fewer records at risk.
4. What’s the link between data retention policies and data minimization?
Retention policies define how long you keep data. Data minimization requires that you do not retain personal data longer than necessary. Documented retention schedules and automated deletion processes prove this to auditors.
5. How should companies document their minimization practices for SOC 2 audits?
Maintain a data inventory, write policies that describe the purpose of each data set, create process maps for data collection and deletion, and implement retention schedules. Provide evidence of execution—such as deletion logs and access review records—so auditors can confirm that your controls operate effectively.





.svg)






.svg)
.svg)