Enterprise buyers have become wary of promises without proof. Before they sign a contract, security teams send detailed questionnaires, procurement inserts security addenda, and legal teams push for data protection clauses. If your company stores or processes customer data, you will hear the demand for SOC 2 For Data Processors compliance. This attestation, defined by the American Institute of Certified Public Accountants (AICPA), provides independent assurance that your controls protect data and deliver reliable service. A clean report can shorten sales cycles and remove procurement objections.
However, SOC 2 is much more than a badge. It ties your internal security practice to external expectations. The framework evaluates five areas—security, availability, processing integrity, confidentiality, and privacy—through policies, procedures, and evidence. Passing an audit means you have designed and operated controls that address these criteria over time. This article explains what SOC 2 For Data Processors entails, how the trust service principles work in practice, and how to prepare for audit readiness. Throughout this discussion we refer to SOC 2 For Data Processors because the requirements apply specifically to organisations that process data on behalf of others. Drawing on authoritative sources such as AICPA guidance, ISO/IEC 27001, NIST risk frameworks, HIPAA requirements, and the latest breach cost data, as well as lessons learned from Konfirmity’s human‑led managed service, it shows how to build a program that withstands attackers, auditors, and clients alike.
What Is SOC 2 for Data Processors
SOC 2 is an attestation framework for service organizations that handle data on behalf of others. An independent auditor reviews your control environment against the trust service criteria and issues a report describing whether controls are suitably designed and operating effectively. The term data processor comes from privacy laws like GDPR: a processor handles personal data on behalf of a data controller and must follow the controller’s instructions. In the context of SOC 2 For Data Processors, it refers to companies that store, process, or transmit client data but do not decide why or how that data is used.
Enterprise clients request SOC 2 for three main reasons. First, it provides risk management assurance. A SOC 2 report shows that you have identified threats to client data and implemented controls to mitigate them, lowering the likelihood of breaches and operational disruptions. Second, it offers transparency. The report contains management’s assertion, a system description, and the auditor’s tests. This gives clients confidence that you actually enforce access reviews, monitor logs, and respond to incidents. Third, it matches other frameworks. Many procurement teams map their due‑diligence process to NIST SP 800‑53, ISO 27001, or HIPAA. A SOC 2 report uses a common language that often overlaps with these requirements, making it easier for clients to trust your program.
Trust Service Principles and Their Application
The SOC 2 trust service principles define the areas auditors examine. Security is mandatory; the other four are optional depending on your services and commitments. Selecting the right combination depends on your product, customer needs, and risk assessment.
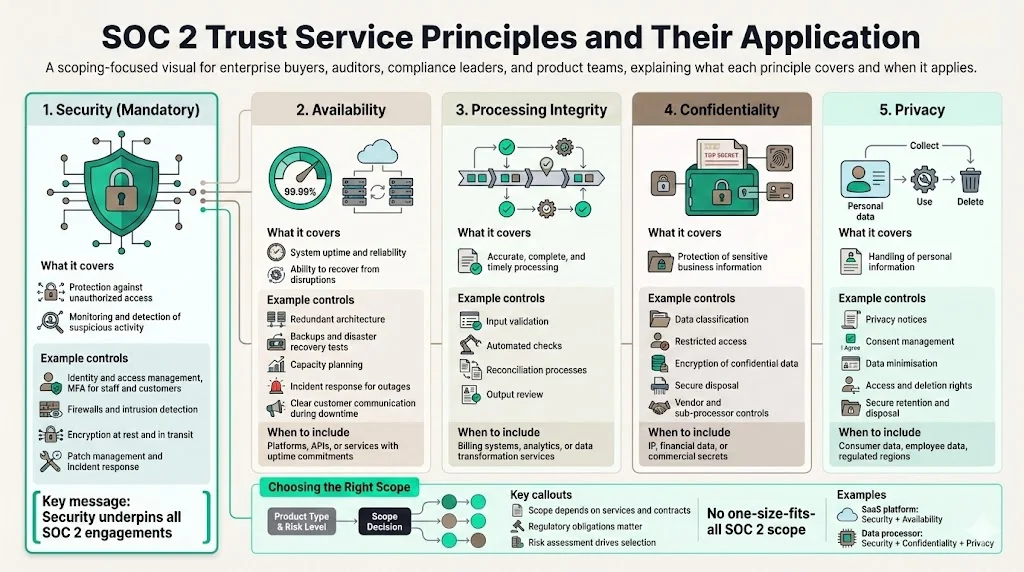
Security: Protecting Systems and Data
Security covers safeguards that prevent unauthorized access, misuse, or modification. Schellman explains that this category ensures only authorized individuals have appropriate access and that activities are monitored to detect suspicious behaviour. Controls include identity and access management, firewalls, intrusion detection, vulnerability scanning, log monitoring, security training, incident response, and change management. Because security underpins all other criteria, it is included in every SOC 2 For Data Processors engagement. For processors, practical measures involve least‑privilege access, multi‑factor authentication for staff and customers, encryption of data at rest and in transit, regular patching, and a tested incident response plan with notification commitments.
Availability: Uptime and Reliability
Availability measures whether systems are available for operation as promised. Auditors look at disaster recovery, business continuity, capacity planning, and incident handling. If your service must be highly available—such as a platform or API used by clients to process data—you may include availability. Controls can involve redundant architectures, tested backups, failover procedures, and monitoring of service commitments. Clear communication plans for outages also matter.
Processing Integrity: Accurate, Complete Processing
Processing integrity assesses whether systems perform their intended functions accurately, completely, and on time. For processors that transform or compute client data, this category ensures that processing is authorised and free from errors. Controls include input validation, reconciliation processes, automated checks, and review of output. It is distinct from data integrity: a system can process data correctly even if the input is flawed. If you bill clients, generate analytics, or manipulate data, processing integrity may be essential.
Confidentiality: Protecting Sensitive Business Information
Confidentiality covers safeguards to protect information designated as confidential from unauthorised access or disclosure. It requires you to define what qualifies as confidential, limit access, encrypt sensitive data, and dispose of it securely. For processors handling intellectual property, financial records, or commercial secrets, confidentiality is often included. Implement controls like data classification, restricted access, encrypted backups, secure disposal practices, and vendor management to ensure sub‑processors uphold the same commitments.
Privacy: Safeguarding Personal Information
Privacy focuses on personal information and compliance with your privacy notice and Generally Accepted Privacy Principles. It addresses how you collect, use, retain, and dispose of personally identifiable information. Controls involve privacy notices, consent mechanisms, data minimisation, access and deletion rights, and secure handling. Privacy is distinct from confidentiality because it deals specifically with information that can identify an individual. If you handle consumer or employee data, or operate in jurisdictions like the EU or US healthcare sector, privacy controls may be required.
Selecting which your services, customer contracts, regulatory obligations, and risk assessment results should drive principles to include. Cyber Sierra reports that scope is not one‑size‑fits‑all; a SaaS platform may focus on security and availability, while a data processing company may emphasise privacy and confidentiality. A structured risk assessment helps identify which areas need attention.
Core Compliance Standards and Internal Controls
Internal controls are the documented policies, procedures, and systems that enforce security and compliance. They provide the evidence auditors review to determine whether you meet the trust service criteria. ISO/IEC 27001, for example, defines requirements for an information security management system (ISMS) that helps organisations establish, implement, maintain, and continually improve security. The standard promotes a holistic approach by vetting people, policies, and technology. For SOC 2 For Data Processors, internal controls tie directly to risk management, reduce the likelihood of breaches, and prepare your organisation for an audit.
Example Control Categories
The following categories illustrate typical controls relevant to processors:
Internal controls should be matched to your organisation’s size, complexity, and risk profile. HIPAA’s Security Rule requires administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information. It also mandates risk analyses, assigned security responsibilities, training, and access management. Mapping controls across frameworks—ISO 27001, NIST SP 800‑53, HIPAA, and GDPR—allows you to reuse evidence and streamline compliance. Konfirmity routinely maps SOC 2 controls to these frameworks, matching least‑privilege policies with ISO 27001 control A.9, HIPAA information access requirements, and GDPR data minimisation principles.
The SOC 2 Audit Process
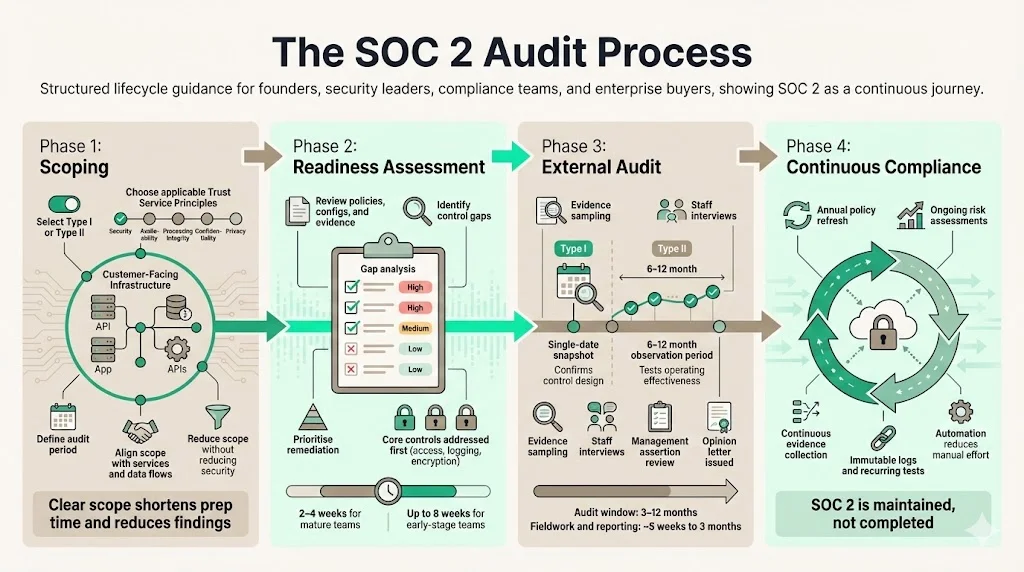
Scoping
Defining scope is the first step. Decide which systems, processes, and trust service principles to include. Konfirmity advises selecting report type (Type I or Type II), choosing criteria, and determining time frame during the pre‑audit phase. Scope should reflect your services and data flows while balancing audit complexity. Consider your business model (for example, whether downtime would affect customers), client requirements (some may require privacy or longer audit windows), industry regulations, and risk assessment results.
At Konfirmity we run scoping workshops with engineering and product leaders to map data flows and identify in‑scope systems. Focusing on customer‑facing infrastructure typically reduces the number of controls by twenty to thirty percent without sacrificing security. Clear scope helps avoid unnecessary findings and shortens preparation time.
Readiness Assessment
A readiness assessment measures your current state against the trust service criteria and identifies gaps. Our CISO team reviews policies, technical configurations, and evidence, then prepares a gap report with remediation steps and prioritisation. Mature organisations often complete readiness in two to four weeks; younger companies may need up to eight weeks. We suggest addressing core security controls—access, logging, encryption—before optional categories.
External Audit
After remediation you engage a CPA firm to perform the audit. There are two types of SOC 2 reports. Type I examines the design of controls at a specific point in time, verifying they exist but not how they operate. Type II assesses both design and operating effectiveness over a period, usually six to twelve months. Larger clients often request Type II because it demonstrates sustained performance. During the audit, the auditor reviews management’s assertion and system description, tests controls with sample evidence (such as access requests, change tickets, or incident logs), interviews staff, and issues an opinion letter. The audit window for a Type II report ranges from three to twelve months; fieldwork and reporting typically take five weeks to three months.
Continuous Compliance
SOC 2 is not a one‑time event. Policies should be refreshed annually, risk assessments repeated regularly, and evidence collected continuously. Onspring emphasizes the need for continuous monitoring, immutable logs, and recurring control tests to maintain compliance. Automation tools can collect evidence, monitor configurations, and alert you to control drift. Konfirmity’s managed service performs quarterly access reviews, monthly vulnerability scans, and continuous monitoring. Our evidence platform captures logs, screenshots, and policy updates linked to specific criteria, reducing the internal burden from hundreds of hours per year to about seventy‑five hours for the client.
How SOC 2 Supports Data Security and Risk Management
Adopting SOC 2 For Data Processors strengthens your security posture and reduces risk. The IBM 2025 Cost of a Data Breach report shows that while the global average cost fell to USD 4.44 million, the United States saw costs exceed USD 10 million. Many breaches were driven by weak access controls in machine‑learning enabled systems. Implementing SOC 2 controls can reduce the likelihood of such incidents. Strong access management prevents unauthorized actions, encryption mitigates the impact of data exposure, and continuous monitoring shortens detection and containment time. IBM found that extensive use of automation shortened breach response by eighty days and reduced costs by USD 1.9 million.
From a risk management perspective, SOC 2 introduces discipline. You carry out structured risk assessments, assign owners, and implement controls to address threats. Availability controls offer assurance that customers can rely on your services without unexpected downtime. Processing integrity demonstrates your systems perform correctly. Confidentiality and privacy show that sensitive information is protected. Together, these signals reduce contract objections and enhance reputation.
To illustrate the cost impact of breaches and the benefits of strong controls, the figure below compares average data breach costs (in USD millions) between organisations with and without automation and strong controls, based on IBM’s 2025 data. Organisations with automation and disciplined programs saw lower breach costs and faster recovery.
Risk Management Benefits
- Reduced breach probability. Controls matching the trust service criteria lower the risk of unauthorized access, data loss, and operational failures.
- Fewer procurement objections. A current SOC 2 Type II report eases concerns from procurement teams, accelerating sales cycles.
- Enhanced vendor reputation. Demonstrated reliability and confidentiality commitments differentiate you from competitors.
- Regulatory harmony. SOC 2 controls overlap with HIPAA, GDPR, ISO 27001, and NIST requirements, enabling you to meet multiple obligations at once.
Common Challenges and How to Address Them
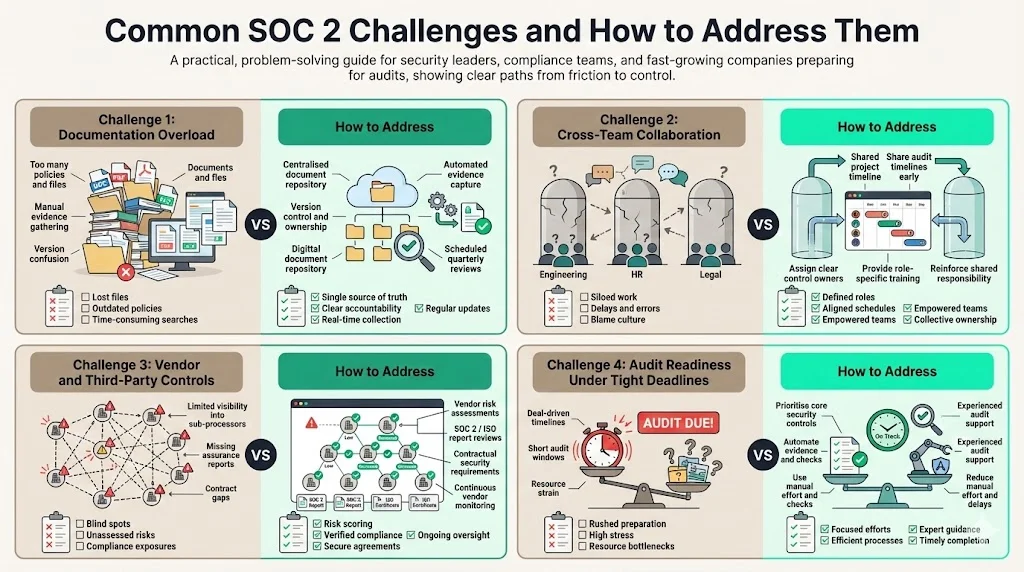
Documentation Overload
SOC 2 demands extensive documentation, including policies, procedures, system diagrams, logs, and evidence of control operation. Cyber Sierra reports that many teams feel overwhelmed by the volume of paperwork required. To manage this:
- Centralise your documentation. Store policies and procedures in a single repository with version control and clear ownership.
- Automate evidence collection. Use tools that capture logs, screenshots, and reports automatically, reducing manual effort. Konfirmity’s platform integrates with your stack to gather evidence continuously.
- Schedule regular updates. Review and update policies quarterly or when there are material changes to your environment.
Cross‑Team Collaboration
SOC 2 involves engineering, security, legal, operations, and sales. Without coordination, compliance efforts stall. Onspring points out that security is everyone’s responsibility. Improve collaboration by:
- Assigning control owners. Designate individuals responsible for access control, logging, incident response, vendor management, and other domains.
- Communicating timelines. Share the audit schedule and expectations with technical and business teams.
- Training stakeholders. Offer targeted training for developers, support staff, human resources, and executives. Use workshops and phishing simulations to reinforce learning.
Vendor and Third‑Party Controls
Processors often rely on sub‑processors like cloud providers. Evaluating and managing their controls is crucial. Best practices include:
- Conducting vendor risk assessments. Send security questionnaires, request SOC 2 or ISO 27001 reports from sub‑processors, and rate their risk.
- Embedding contractual obligations. Require vendors to maintain equivalent security standards, notify you of incidents, and participate in audits.
- Monitoring continuously. Track vendor compliance and renewal dates, set up alerts for security news, and perform periodic reviews.
Audit Readiness under Tight Deadlines
Many companies need a SOC 2 report quickly to close a deal. Pre‑audit preparation can range from two weeks to nine months, and the audit window can be as short as three months. To stay on schedule:
- Prioritise core controls. Focus first on mandatory security controls—access, encryption, logging—that address the majority of criteria.
- Automate tasks. Compliance automation tools gather evidence and surface configuration gaps, shortening prep time.
- Work with experts. A managed service like Konfirmity brings experience from more than six thousand audits and twenty‑five years of combined expertise. Our team often reduces readiness timelines from nine to twelve months to four to five months and cuts client involvement to about seventy‑five hours per year.
Actionable Examples
Sample Control Statement
When writing controls, be clear and specific. Here is sample language for a processing integrity control:
Control: “The system validates all input files for completeness and format compliance before processing. If records are missing or data types are invalid, the system triggers automated error handling, notifies the operations team, and prevents further processing until issues are resolved.”
Evidence: Input validation logs, error messages, incident tickets, and remediation records.
Simple Risk Register
A basic risk register can help prioritise mitigation:
Evidence Items
Auditors look for objective proof that controls operate as described. Typical evidence includes:
- Access review logs showing that user permissions were reviewed and approved.
- Screenshots of configuration settings (password policies, encryption settings) captured during the audit window.
- Monitoring logs demonstrating continuous collection and analysis of security events.
- Incident response reports documenting investigation, containment, and remediation of security incidents.
- Vendor certificates such as SOC 2 or ISO 27001 reports for sub‑processors.
Leveraging SOC 2 to Win Enterprise Business
SOC 2 reports are powerful sales tools. When responding to questionnaires or proposals, provide a current Type II report overview, including the scope, covered trust service criteria, and audit window. Call out any exceptions and remediation steps. Buyers often ask about your incident response procedures, breach notification timelines, and data governance practices. Answer clearly and factually; use the report to show that controls operate effectively over time.
When speaking with enterprise buyers, expect questions on:
- Security policies. Provide concise overviews of your access control, encryption, and patch management policies.
- Incident response. Explain your detection and response workflow, including time to notify clients.
- Data governance. Describe data classification, retention, and deletion practices, and how you honour confidentiality and privacy commitments.
- Third‑party management. Outline how you vet and monitor sub‑processors and the assurances you require from them.
Use your SOC 2 program to your advantage with your own vendors. Ask sub‑processors for their reports, include security obligations in contracts, and reserve audit rights. Maintain a vendor register with risk ratings and renewal dates. This demonstrates to your clients that you manage supply chain risk proactively.
Conclusion
Security that looks good on paper but fails in practice is a liability. SOC 2 For Data Processors is not about paperwork; it is about building a control environment that stands up to attackers, auditors, and buyers. By understanding the trust service principles and implementing internal controls that match ISO 27001, HIPAA, NIST, and GDPR, you strengthen your security posture and reduce risk. The IBM 2025 breach report shows that costs remain high and many machine‑learning related breaches involve weak access controls. A well‑designed SOC 2 program addresses these risks through strong identity management, continuous monitoring, and incident preparedness.
Konfirmity’s human‑led managed service delivers outcomes rather than a one‑off project. We implement controls inside your stack, operate them daily, and keep you audit ready year‑round. Clients typically achieve SOC 2 readiness in four to five months instead of nine to twelve and spend around seventy‑five hours per year on compliance. With more than six thousand audits supported and twenty‑five years of combined expertise, our team knows what works and what fails in the field. Investing in SOC 2 For Data Processors not only protects client data but also drives trust and growth. Begin with security, operate your program daily, and let compliance follow naturally.
FAQs
1: What does SOC 2 compliance mean for data processors?
It means your company has designed and operates internal controls around the trust service principles—security, availability, processing integrity, confidentiality, and privacy—to protect client data. An independent auditor verifies those controls and issues a report. For processors, SOC 2 demonstrates to clients that you handle their data securely and reliably.
2: Do all SOC 2 reports include all trust service principles?
No. Security is mandatory, but availability, processing integrity, confidentiality, and privacy are optional. You choose which criteria to include based on your services, customer requirements, and risk assessment.
3: What’s the difference between SOC 2 Type I and Type II?
Type I evaluates the design of your controls at a point in time; Type II assesses both design and operating effectiveness over a period, typically six to twelve months. Type II provides deeper assurance to enterprise clients.
4: Can SOC 2 help with compliance requirements like GDPR or HIPAA?
Yes. SOC 2 controls often overlap with other frameworks. HIPAA requires administrative, physical, and technical safeguards, while ISO 27001 promotes a risk‑aware management system. Implementing SOC 2 can support broader regulatory obligations.
5: How long does a SOC 2 audit take?
The pre‑audit phase can range from two weeks to nine months. A Type II audit window ranges from three to twelve months, with fieldwork usually taking five weeks to three months. Working with experienced professionals and automation tools can reduce these timelines.





.svg)





.svg)
.svg)