A data warehouse in a healthcare context is more than a central repository for integrated data; it is the analytical engine that drives patient care improvements, operational efficiency, and financial forecasting. However, when this engine runs on electronic protected health information (ePHI), it becomes a high-stakes environment.
Security regarding ePHI is not merely a box-checking exercise. Breaches in the healthcare sector cost more than any other industry—averaging $9.77 million per incident in 2024. Beyond the financial sting, the erosion of patient trust is often irreversible.
This article addresses the specific requirements for HIPAA Data Warehouse Security For HIPAA compliance. We will move past high-level theory and examine the practical standards, technical safeguards, and administrative workflows required to protect patient data.
At Konfirmity, we have supported over 6,000 audits across 25+ years of combined experience. We have seen that compliance failures rarely stem from a lack of intention. They stem from a lack of execution. Organizations often purchase software tools expecting them to solve security problems, only to fail because they lack the human expertise to implement and maintain controls.
You will learn how to structure administrative, physical, and technical safeguards, how to manage risk dynamically, and how to utilize templates to standardize your security posture. This is about building a defense that stands up to HHS/OCR scrutiny and aggressive cyber threats.
What Counts as a HIPAA System of Record?
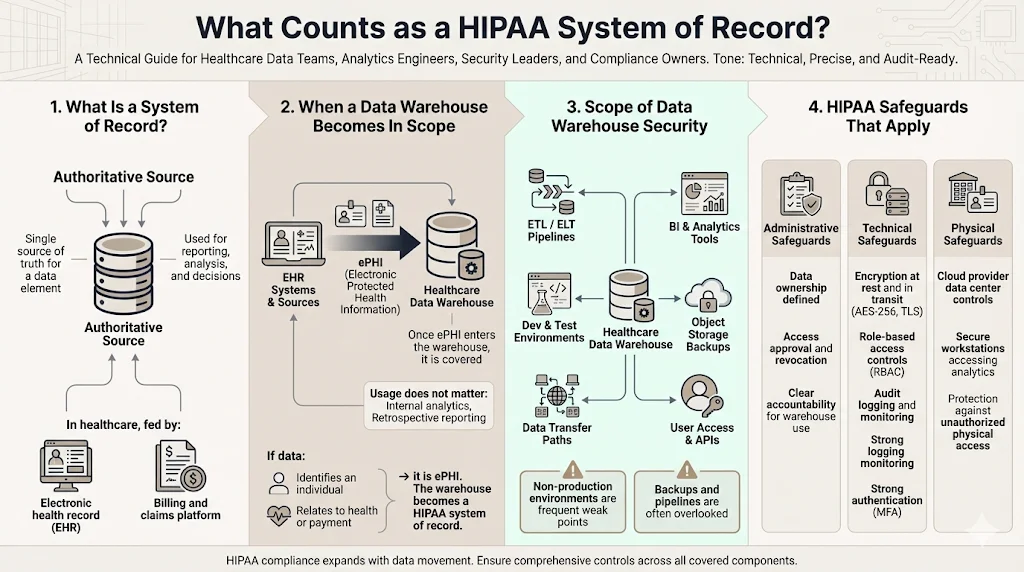
A system of record is the authoritative data source for a given data element. In modern healthcare architectures, data moves from Electronic Health Records (EHRs) and billing systems into data warehouses (like Snowflake, Redshift, or BigQuery) for analytics.
Once ePHI enters your data warehouse, that warehouse becomes a covered system under the HIPAA Security Rule. It does not matter if the warehouse is only used for internal reporting or retrospective analysis. If the data identifies an individual and relates to their past, present, or future health condition or payment, it is ePHI.
The Scope of HIPAA Data Warehouse Security For HIPAA
If your data warehouse stores ePHI, it falls directly under the HIPAA Security Rule (45 CFR Part 164, Subpart C). This rule mandates that covered entities and their business associates must ensure the confidentiality, integrity, and availability of all ePHI they create, receive, maintain, or transmit.
The scope extends past the database tables. It includes:
- ETL/ELT Pipelines: The tools moving data in and out.
- BI Tools: Dashboards (Tableau, Looker, PowerBI) that visualize the data.
- Backups: Snapshots stored in object storage (e.g., S3 buckets).
- Dev/Test Environments: Often the most vulnerable point, where production data is copied for testing without sanitization.
Core HIPAA Regulations that Apply
HIPAA breaks safeguards into three specific categories. A compliant data warehouse must address all three.
Administrative Safeguards
These are the policies and procedures designed to clearly show how the entity will comply with the act. They comprise over half of the HIPAA Security requirements. For a data warehouse, this means defining who owns the data, who can access it, and how access is revoked.
Technical Safeguards
These controls protect the data at rest and in transit. They involve encryption, access control mechanisms, audit controls, and authentication integrity. This is where your engineering and DevOps teams will spend the bulk of their effort.
Physical Safeguards
Even in a cloud environment, physical safeguards apply. You must ensure that the physical servers (managed by your cloud provider) and the workstations accessing the warehouse (managed by you) are secure from unauthorized physical access.
Critical Security Requirements for HIPAA Data Warehouses
Achieving HIPAA Data Warehouse Security For HIPAA compliance requires a granular approach to these safeguards. Below are the specific requirements essential for passing an audit and, more importantly, securing patient data.
Administrative Safeguards
Risk Management and Risk Analysis
The foundation of HIPAA compliance is the Risk Analysis (45 CFR § 164.308(a)(1)(ii)(A)). You must conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI. In 2024, failure to conduct a thorough risk analysis was the most frequently cited violation in HHS enforcement actions.
This is not a one-time event. At Konfirmity, we often see organizations treat risk assessments as a "set and forget" document. This is a critical error. A valid risk management process requires:
- Asset Inventory: Cataloging every table, bucket, and pipeline containing ePHI.
- Threat Identification: Identifying what could go wrong (e.g., SQL injection, credential theft, insider threat).
- Mitigation Planning: Documenting the controls put in place to reduce those risks.
Security Policies and Procedures
You need documented policies that guide behavior. For a data warehouse, you need specific policies regarding:
- Data Classification: Defining what data constitutes ePHI.
- Sanitization: Procedures for scrubbing data before it enters lower environments.
- Account Management: How access is granted during onboarding and revoked during offboarding.
Technical Safeguards
Access Controls
The "Minimum Necessary" standard is vital here. A data analyst should not have SELECT * permissions on the entire warehouse.
- Role-Based Access Control (RBAC): Create specific roles (e.g., clinical_analyst, finance_auditor) with restricted views.
- Unique User Identification: Shared logins (e.g., admin/root) are strictly forbidden. Every user must have a unique ID to ensure accountability.
- Automatic Logoff: Sessions connected to the warehouse must terminate after a period of inactivity.
Encryption Methods
Encryption acts as the final line of defense.
- Encryption at Rest: Data stored on disks must be encrypted. Most cloud providers offer this by default (e.g., AWS KMS), but you must verify the configuration and manage the cryptographic keys properly. See NIST SP 800-111 for guidance on storage encryption.
- Encryption in Transit: All connections to the warehouse must use TLS 1.2 or higher. Data moving between the EHR and the warehouse must never traverse the network in cleartext.
Audit Controls & Monitoring
You must implement hardware, software, and procedural mechanisms that record and examine activity in information systems that contain or use ePHI.
- What to Log: Successful logins, failed logins, query execution history, and schema changes.
- Review Cadence: Logs are useless if no one watches them. You need automated alerts for anomalies, such as massive data exports or access from unusual IP addresses.
Physical Safeguards
Server Room Protections
For cloud-hosted warehouses, you rely on the provider's (AWS, Azure, GCP) SOC 2 Type II or ISO 27001 reports to attest to physical security. You must review these reports annually.
Workstation Security
The endpoints accessing the warehouse are your responsibility. This includes:
- Full disk encryption (BitLocker/FileVault) on analyst laptops.
- Privacy screens for users working in public areas.
- Strict policies regarding the use of external drives.
Ongoing Compliance Support
Workforce Training
Human error causes the majority of breaches. Engineers and analysts working with the data warehouse must receive specific HIPAA training. They need to understand why they cannot copy production data to their local machine or a personal storage drive.
Business Associate Agreements (BAAs)
If you use a third-party cloud data warehouse (like Snowflake) or an ETL tool (like Fivetran), you must sign a BAA with them. The BAA establishes their liability for protecting the data. If a vendor refuses to sign a BAA, you cannot use them for ePHI.
Building Blocks of a Secure Data Warehouse
Constructing HIPAA Data Warehouse Security For HIPAA requires specific architectural decisions. It is not enough to layer security on top; it must be baked into the design.
1) Data Privacy & Confidentiality Safeguards
Limiting Data Exposure
The most effective way to secure ePHI is to store less of it. Use de-identification and pseudonymization techniques wherever possible. If the analytics use case does not require the Patient Name or Social Security Number, strip those fields before they enter the warehouse.
Separation of Duties
Ensure that the people building the warehouse (DevOps) are not the same people auditing the access logs (Security/Compliance). This prevents a single bad actor from manipulating data and covering their tracks.
2) Risk Management in Practice
Identifying and Ranking Threats
Risks are not equal. A misconfigured S3 bucket containing 10,000 patient records is a critical risk. A single missed patch on a non-production server is a low risk.
We utilize a risk-based approach at Konfirmity. We map threats to their potential business impact.
- Likelihood: How probable is the attack?
- Impact: What is the financial/reputational damage?
- Velocity: How fast would the breach spread?
Integrating Risk Assessments into Operations
Risk assessment should be triggered by change. If you add a new data source or integrate a new BI tool, update the risk assessment. Treat the risk register as a living document, not a static PDF.
3) Auditing and Monitoring
Required Logs
To satisfy the audit controls standard, you must log:
- Identity: Who ran the query?
- Action: What was the query? (e.g., SELECT * FROM patients WHERE condition = 'HIV')
- Target: Which data was accessed?
- Timestamp: When did it happen (UTC)?
- Origin: What IP address or service initiated the request?
Review Frequency
Automated tools (SIEMs) should ingest these logs in real-time. Security teams should review aggregated reports weekly and investigate high-severity alerts immediately.
4) Incident Response and Breach Prevention
Detection and Response
You need a plan for when defenses fail. NIST SP 800-61 provides a strong framework: Preparation, Detection & Analysis, Containment, Eradication, and Recovery.
- Containment: If a user account is compromised, how fast can you kill their active sessions and rotate their keys?
- Notification: Under the HIPAA Breach Notification Rule, you have 60 days to notify affected individuals and the HHS OCR if a breach affects more than 500 residents of a state or jurisdiction. The Change Healthcare ransomware attack in 2024, which affected an estimated 190 million individuals, serves as a stark reminder of the scale these incidents can reach.
Secure Data Storage Strategies
Storage strategy is the backbone of HIPAA Data Warehouse Security For HIPAA compliance.
1) Encryption at Rest & In Transit
Implementation Checkpoints
- Database Level: Ensure Transparent Data Encryption (TDE) is active.
- Column Level: For highly sensitive fields (SSN, credit card numbers), consider application-level encryption where the database only sees ciphertext.
- Key Management: Rotate cryptographic keys annually. Separate the keys from the data. If the database is compromised, the attacker should not also find the keys to decrypt it.
- TLS Configuration: Disable outdated protocols (TLS 1.0/1.1) and weak cipher suites. Force HTTPS for all web interfaces.
2) Data Retention and Archival
HIPAA Documentation Retention
HIPAA requires you to retain compliance documentation (policies, risk assessments, audit logs) for a minimum of six years from the date of its creation or the date it was last in effect, whichever is later.
Data Purging
Data warehouses have a tendency to grow indefinitely. Implement a data retention policy that dictates when patient data should be purged or archived. Storing data you no longer need is an unnecessary liability.
3) System Hardening and Patch Management
Configuring Systems
Default configurations are rarely secure. "Hardening" means removing unnecessary services, closing unused ports, and configuring tight parameters.
- CIS Benchmarks: Use the Center for Internet Security (CIS) benchmarks as a baseline for hardening your cloud infrastructure and operating systems.
Timely Patching
Vulnerabilities in database software must be patched immediately. Establish a Service Level Agreement (SLA) for patching.
- Critical vulnerabilities: 48 hours.
- High vulnerabilities: 14 days.
- Medium/Low: 30 days.
Policy Templates You Can Use
Templates are useful starting points, but they must be customized to your specific architecture. "Cookie-cutter" policies are easy for auditors to spot and reject.
At Konfirmity, we develop tailored policies, but you can look for structure in the following areas:
Data Warehouse Security Policy
This high-level document defines the purpose of the warehouse, the data classification, and the overall security mandate. It should state clearly that security takes precedence over convenience.
Access Control Matrix
A spreadsheet or document defining roles and their permissions.
- Columns: Tables/Views (e.g., Patient_Table, Billing_Table).
- Rows: Roles (e.g., Admin, Analyst, Auditor).
- Cells: Access level (Read, Write, None).
Encryption Policy
Defines the cryptographic standards (e.g., AES-256 for rest, TLS 1.2+ for transit) and the key management lifecycle.
Audit Logging Policy
Specifies which events generate logs, where logs are stored, how long they are kept (6 years minimum for compliance logs), and who reviews them.
Risk Assessment Checklist
A structured list used to evaluate the warehouse against the HIPAA Security Rule standards periodically.
Incident Response Plan
A playbook detailing roles, responsibilities, and communication trees during a security event.
Observation: While templates from providers like SecurityMetrics or SANS Institute offer good structures, they require significant customization to reflect your actual tech stack.
Best Practices Checklist
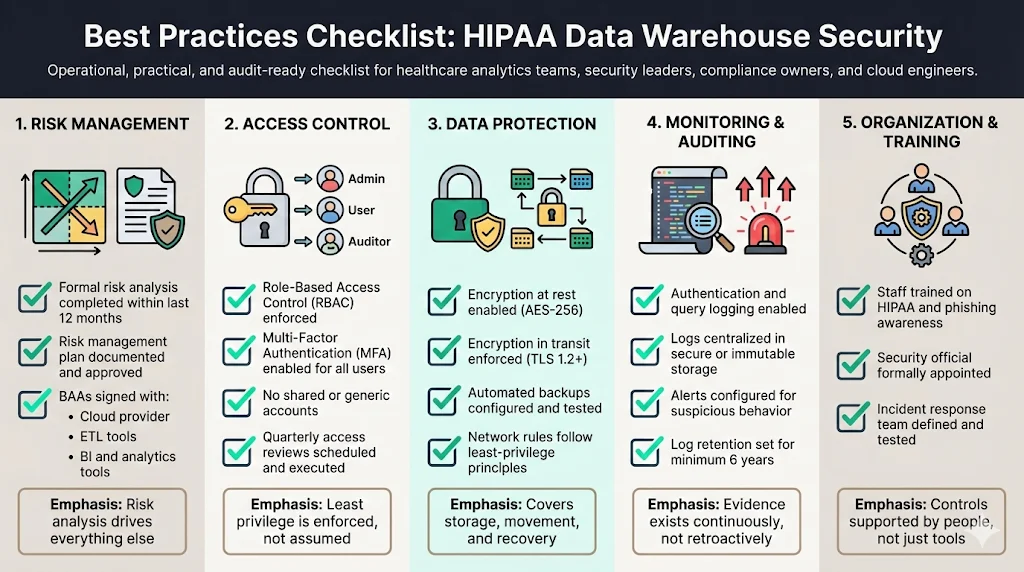
To operationalize HIPAA Data Warehouse Security For HIPAA, use this actionable checklist. This moves you from theory to execution.
Risk Management
- Conducted a formal Risk Analysis within the last 12 months.
- Documented a Risk Management Plan addressing identified risks.
- Signed Business Associate Agreements (BAAs) with all vendors (Cloud Provider, ETL tool, BI tool).
Access Control
- Implemented Role-Based Access Control (RBAC).
- Enforced Multi-Factor Authentication (MFA) for all users.
- Removed generic or shared accounts (e.g., "admin", "root").
- Scheduled quarterly access reviews to remove dormant accounts.
Data Protection
- Verified encryption at rest (AES-256) for all data stores.
- Verified encryption in transit (TLS 1.2+) for all connections.
- Implemented automated backups with testing for restoration.
- Configured "least privilege" network rules (firewalls/security groups).
Monitoring & Auditing
- Enabled logging for all authentication and query events.
- Centralized logs in a secure location (immutable storage preferred).
- Configured alerts for suspicious activities (e.g., bulk exports).
- Established a log retention period of at least 6 years for compliance records.
Organization & Training
- Trained all staff on HIPAA policies and phishing awareness.
- Appointed a specific Security Official responsible for compliance.
- Established an Incident Response Team and tested the plan.
Conclusion
Securing a data warehouse in a healthcare environment is a rigorous, ongoing obligation. It is not a project with a start and end date. The threat environment changes, your data volume grows, and your analytics needs shift.
The goal of HIPAA Data Warehouse Security For HIPAA compliance is not to produce a binder of policies that sit on a shelf. The goal is to create a resilient system that protects patient privacy while enabling the data insights that modern healthcare requires.
At Konfirmity, we believe that security must be human-led. Automated tools can scan for vulnerabilities, but they cannot interpret context, design durable controls, or negotiate with auditors. We don't just advise—we execute. We implement the controls inside your stack and manage the program year-round, ensuring that you remain audit-ready every day, not just the weeks before an assessment.
Effective security facilitates speed. When your data warehouse is secure by design, your analytics teams can innovate faster, knowing the guardrails are holding firm.
FAQs
1) Are data warehouses considered HIPAA systems of record?
Yes, when they store ePHI and influence patient care or billing decisions, they fall under HIPAA Security Rule obligations. Even if they are downstream copies of the EHR, the presence of ePHI mandates full compliance.
2) What access controls are required for analytics teams?
You must implement Role-Based Access Control (RBAC). Each analyst should have a unique ID, be protected by Multi-Factor Authentication (MFA), and operate with the minimum privileges necessary to perform their job. Shared passwords are never acceptable.
3) How should encryption be handled at rest and in transit?
Both stored data and data moving between systems must be encrypted using strong, current algorithms. Standard practice is AES-256 for data at rest and TLS 1.2 or higher for data in transit.
4) What logs must be kept for audits?
User access logs, change logs, administrative actions, and system events should be retained with timestamps. This ensures audit readiness and allows for forensic investigation in the event of a breach.
5) How do templates help with ongoing compliance?
Templates standardize policy creation, ensure consistency, and save time while documenting compliance. They provide a proven structure that helps ensure you do not overlook critical HIPAA requirements.
6) Why is HIPAA Data Warehouse Security For HIPAA so critical for business associates?
Business Associates are directly liable for compliance. If you provide analytics services to a hospital and suffer a breach, you are subject to OCR fines and reputational ruin. Strong security demonstrates to your enterprise buyers that you are a safe partner.





.svg)





.svg)
.svg)