In the high-stakes world of enterprise sales, a paper certificate is no longer enough. Ten years ago, you could flash an ISO 27001 badge and close the deal. Today, enterprise buyers, particularly in regulated sectors like healthcare and finance, demand more. They want operational proof. They want to know that your security controls function on a Tuesday afternoon in November, not just during the week of your external audit in May.
This shift has moved the conversation from "Do you have a certificate?" to "How do you maintain security daily?" This is where ISO 27001 continuous monitoring becomes the difference between a stalled procurement cycle and a signed contract.
At Konfirmity, we have supported over 6,000 audits. A clear pattern has surfaced: companies that approach ISO 27001 as a "one-and-done" project struggle during vendor reviews. Their answers to due diligence questionnaires are vague. Their evidence is stale. Their sales cycles drag on because they can not prove they are in control of their environment. Conversely, organizations that build a program based on ongoing oversight move through procurement faster.
Why do enterprise buyers care? Because point-in-time certification captures a single moment. It does not account for the new code you shipped last week, the three new vendors you onboarded yesterday, or the access rights of the employee who left this morning. Continuous monitoring supports trust because it proves resilience. It signals to your prospects that you manage risk actively.
In this guide, I will walk you through the operational reality of maintaining an ISO 27001 program. We will examine the specific clauses that drive monitoring, the controls that matter most to auditors, and how to build a system that keeps you audit-ready year-round without crushing your engineering team.
What ISO 27001 Continuous Monitoring Means in Practice
Many leaders confuse monitoring with simple logging. While logs are an input, ISO 27001 continuous monitoring is a broader discipline. It is the recurring process of assessing your Information Security Management System (ISMS) to verify that controls are effective, risks are managed, and compliance is maintained.
Think of the difference between a photograph and a CCTV feed. An annual audit is a photograph—a snapshot of your security posture at a specific instant. Monitoring is the CCTV feed. It provides visibility into trends, anomalies, and failures as they happen.
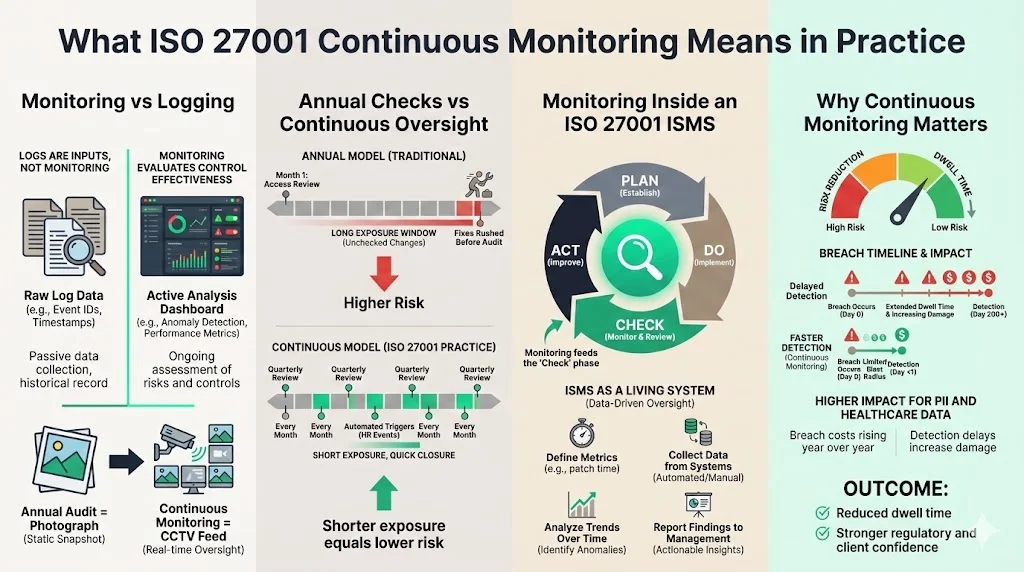
Difference Between Annual Checks and Ongoing Oversight
In a traditional, "check-the-box" approach, a company might perform a user access review once a year, right before the auditor arrives. They scramble to revoke access for terminated employees and fix permission errors.
In a continuous model, that review happens quarterly or monthly. Better yet, it is triggered automatically by personnel changes. The difference in risk exposure is massive. If an engineer leaves in January and retains access until a December audit, you have eleven months of critical exposure. With ongoing oversight, that gap closes to days or weeks.
How Monitoring Fits into an ISO 27001-Aligned ISMS
Your ISMS is a living organism. It breathes through data inputs. Continuous monitoring feeds the "Check" phase of the Plan-Do-Check-Act (PDCA) cycle. It involves:
- Defining Metrics: Knowing what to measure (e.g., time to patch critical vulnerabilities).
- Collecting Data: Gathering evidence from your tech stack (AWS, Azure, Jira, HR systems).
- Analyzing Trends: Identifying if your security posture is improving or degrading.
- Reporting: translating technical data into business decisions for management.
Why This Matters for Companies Handling Sensitive Data
If you process Personal Identifiable Information (PII) or operate in healthcare, the stakes are higher. A breach involving 10,000 records costs significantly more in 2025 than it did in 2020, with the global average cost of a data breach reaching $4.88 million. Regulators and clients expect you to detect intrusions quickly. The industry average for identifying a breach often exceeds 200 days, specifically in the healthcare sector. Effective monitoring drastically reduces this dwell time, limiting the blast radius of an attack.
ISO 27001 Clauses That Drive Continuous Monitoring
ISO 27001:2022 is explicit about the need for ongoing evaluation. It is not a suggestion; it is a requirement.
Clause 9.1: Monitoring, Measurement, Analysis, and Evaluation
Clause 9.1 is the engine room of ISO 27001 continuous monitoring. It mandates that the organization determines:
- What needs to be monitored and measured.
- The methods for monitoring, measurement, analysis, and evaluation to ensure valid results.
- When the monitoring and measuring shall be performed.
- When the results shall be analyzed and evaluated.
What Auditors Expect: Auditors do not want to see a blank dashboard. They expect to see historical data. If your policy states that you review server logs weekly, the auditor will ask for 52 weeks of evidence. If you say you track uptime, they want to see the availability reports for the entire certification period.
Linking Results to Management Review: Data for the sake of data is useless. Clause 9.3 requires that the output of this monitoring be presented to top management. This ensures that leadership is aware of security performance and can allocate resources to fix gaps.
Other Clauses That Support Continuous Monitoring
Clause 6 (Planning): You can not monitor what you do not understand. Clause 6 focuses on risk assessment. Your monitoring activities must target the high-risk areas identified here. If your primary risk is data leakage via third-party vendors, your monitoring plan must focus heavily on vendor risk management and data loss prevention (DLP) signals.
Clause 8 (Operation): This clause covers the execution of your security plans. Operational planning and control require you to keep documented information (evidence) to demonstrate that processes have been carried out as planned. Continuous monitoring automates the collection of this evidence.
Clause 10 (Improvement): How do you know what to improve? You look at the data. Clause 10 requires you to react to non-conformities and improve the ISMS. Monitoring identifies these non-conformities—such as a missed backup or an unpatched server—allowing you to apply corrective actions immediately.
Continuous Monitoring and Risk Management
Risk management is the heart of ISO 27001, and it is not static. A risk register created in Excel three years ago is a liability, not an asset. ISO 27001 continuous monitoring breathes life into risk management by providing real-time context.
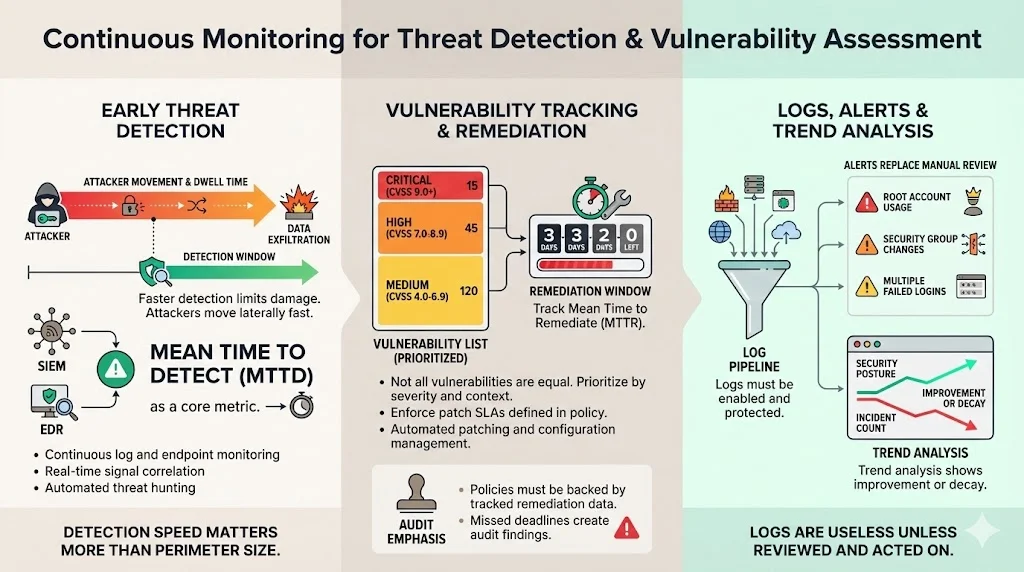
Identifying Changes in Risk Posture Over Time
Consider a SaaS company that pivots to using microservices driven by Artificial Intelligence. Their risk profile changes overnight. New libraries, new data flows, and new regulatory questions arise. Without monitoring, the risk register remains outdated until the next annual review. With a continuous approach, the introduction of new assets or vendors triggers a risk review.
Connecting Monitoring Data to Risk Mitigation Plans
When you identify a risk—say, "Unauthorized access to production databases"—you implement a mitigation, such as Multi-Factor Authentication (MFA) and bastion hosts. Monitoring verifies if that mitigation is working. Are you seeing failed MFA attempts? Is anyone bypassing the bastion host? If the metrics show the control is failing, the risk has re-emerged, and you must act.
Using Results to Prevent Control Drift
"Control drift" is the silent killer of compliance. You set up a perfect configuration for your cloud storage buckets in January. By June, three different developers had tweaked settings to troubleshoot deployment issues, leaving the buckets public. Continuous monitoring tools scan configurations daily, flagging drift the moment it happens. This allows you to revert changes before they become breaches.
Critical Security Controls to Monitor Under ISO 27001
You can not monitor everything. You must prioritize based on risk. In our experience managing security for hundreds of clients, these are the control categories that demand constant vigilance.
Administrative Controls
These are the human-centric rules.
- User Access Reviews: Are the right people holding the right permissions? We monitor this quarterly.
- Security Awareness Training: Who has completed their annual training? Who failed the phishing simulation?
- Vendor Management: Have critical vendors renewed their own certifications?
Technical Controls
These are the automated safeguards in your stack.
- Access Control: Logs of successful and failed logins, privilege escalation, and API access.
- Backup Integrity: It is not enough to run backups; you must monitor successful completion and periodically test restoration.
- Encryption: Verifying that data at rest and in transit remains encrypted using approved protocols (e.g., TLS 1.2+).
- Vulnerability Management: Tracking the time between detection of a CVE (Common Vulnerabilities and Exposures) and the deployment of a patch.
Physical Controls
Even for cloud-native companies, physical security matters.
- Office Access: If you have a physical office, monitor badge logs. Who entered the server room?
- Device Management: Are laptops encrypted? Is the MDM (Mobile Device Management) agent active on all endpoints?
Mapping Controls to Real-World Monitoring Activities
Monitoring Tools That Support ISO 27001
A major mistake companies make is buying a GRC (Governance, Risk, and Compliance) tool and thinking they are done. Software is a container; it is not the content. However, the right tooling is necessary to scale ISO 27001 continuous monitoring.
What to Look For
You need centralized visibility. You do not want to log into ten different portals (AWS Console, Google Workspace Admin, Jira, CrowdStrike, HR system) to gather evidence. You need a solution—or a managed service—that aggregates these signals.
Evidence Collection for Audits
The most tedious part of an audit is evidence collection. "Show me a sample of 25 new hires and prove they signed the NDA." "Show me the change logs for these 5 releases."
Effective monitoring tools automate this. They pull metadata from your HR system and your code repository automatically. At Konfirmity, we integrate directly with your stack. We don't just ask you to upload screenshots; our platform pulls the configuration data to prove compliance. This reduces the manual burden on your team by 80-90%.
Reducing Manual Effort While Keeping Teams Accountable
Tools should generate tickets, not just red lights on a dashboard. If a vulnerability is found, it should automatically create a Jira ticket for the engineering team with a defined Service Level Agreement (SLA). Monitoring tracks that ticket to closure. This bridges the gap between "security team sees a problem" and "engineering team fixes the problem."
Continuous Monitoring for Threat Detection and Vulnerability Assessment
Security is not just about passing an audit; it is about stopping bad actors.
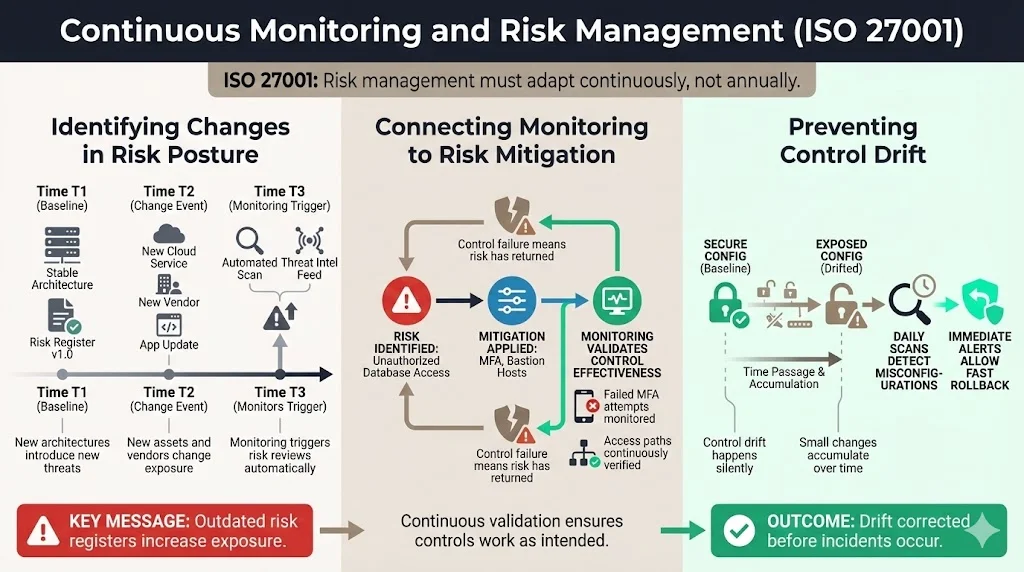
Using Monitoring to Spot Security Events Early
The concept of "Mean Time to Detect" (MTTD) is critical. 2024 data from CrowdStrike suggests that attackers are moving faster than ever, often pivoting from initial access to lateral movement in under an hour. Continuous monitoring of logs (SIEM) and endpoint activity (EDR) is your primary defense.
Tracking Vulnerabilities and Remediation Status
You can not patch every vulnerability immediately. You must prioritize based on severity (CVSS score) and context. Monitoring tracks your "Mean Time to Remediate" (MTTR). If your policy states critical patches must be applied within 7 days, your monitoring system must flag any ticket that exceeds this window. This is a common finding in ISO 27001 audits: companies have a policy but fail to track adherence to it.
Role of Logs, Alerts, and Trend Analysis
Auditors love logs. They want to see that logging is enabled, that logs are protected from tampering, and that someone is actually looking at them. Automated alerting rules are essential here. You can not manually review terabytes of logs. You need alerts for specific triggers: root login usage, modification of security groups, or multiple failed login attempts.
Incident Response and Continuous Monitoring
Clause 5.24 through 5.30 in ISO 27001:2022 deals heavily with incident management. ISO 27001 continuous monitoring is the trigger for your incident response (IR) plan.
Detecting Incidents Before They Escalate
Ideally, monitoring detects a "pre-incident"—a precursor event. For example, monitoring might detect a port scan or a phishing email report. By catching this early, the IR team can block the IP or purge the email before a compromise occurs.
Recording Response Actions for Audit Evidence
When an incident occurs, you must document it. What happened? When was it detected? What did you do? Post-incident, you must retain these records. Your monitoring system should act as the "black box" recorder for the event, preserving the timeline for auditors and regulators.
Using Post-Incident Data to Improve Controls
This closes the loop. After an incident, you perform a Root Cause Analysis (RCA). The RCA might reveal that a specific server was not being monitored or that an alert threshold was too high. You update your monitoring configuration based on these lessons. This demonstrates "Continual Improvement" (Clause 10) in the most practical way possible.
Internal Audits and Ongoing Compliance
The traditional internal audit is a painful, two-week exercise where an external consultant tears apart your processes once a year. It is disruptive and stressful.
How Continuous Monitoring Simplifies Internal Audits
With continuous monitoring, the internal audit becomes a review of the dashboard. The auditor does not need to ask, "Did you do backups in March?" They can look at the backup success rate graph for March. The evidence is already there.
Preparing Audit Evidence Throughout the Year
At Konfirmity, we operate on a model of "continuous audit." We review controls monthly. If a control fails—say, an employee was not offboarded correctly—we catch it in the month it happened. We fix it immediately. This means that when the external auditor arrives for the certification audit, there are no surprises. The evidence is clean, organized, and historical.
Meeting Enterprise Customer Audit Requests
Your customers have the right to audit you (usually defined in the Master Services Agreement). They might send a massive spreadsheet or demand to see your latest penetration test and remediation report. With a managed service backing your monitoring, you can respond to these requests in hours, not weeks. You can confidently say, "Here is our real-time compliance posture."
ISO 27001 Continuous Monitoring Templates
While tools are great, you need structure. Here are the core artifacts we implement for clients to structure their monitoring.
1) Monitoring Plan Template
This document defines the "Who, What, When."
- Scope: Production Environment, Corporate IT.
- Metric: Uptime, Patch Latency, Access Reviews.
- Frequency: Daily (automated), Monthly (manual review).
- Owner: VP of Engineering / CISO.
2) Risk Monitoring Register
This is the evolution of the risk spreadsheet.
- Risk ID: R-012.
- Description: Data leak via S3 bucket.
- Primary Risk Indicator: Number of public buckets detected.
- Review Date: Quarterly.
- Current Status: Mitigated.
3) Control Performance Log
A simple log to track manual checks.
- Control: Physical Security Walkthrough.
- Date: 2025-10-15.
- Result: Pass.
- Notes: Front door lock repaired.
4) Incident and Corrective Action Tracker
- Incident ID: INC-2025-003.
- Source: Monitoring Alert (Datadog).
- Corrective Action: Firewall rule updated.
- Verification: Verified by Penetration Test on 2025-11-01.
Common Challenges Companies Face
Implementing ISO 27001 continuous monitoring is not without friction. Here are the hurdles we see most often.
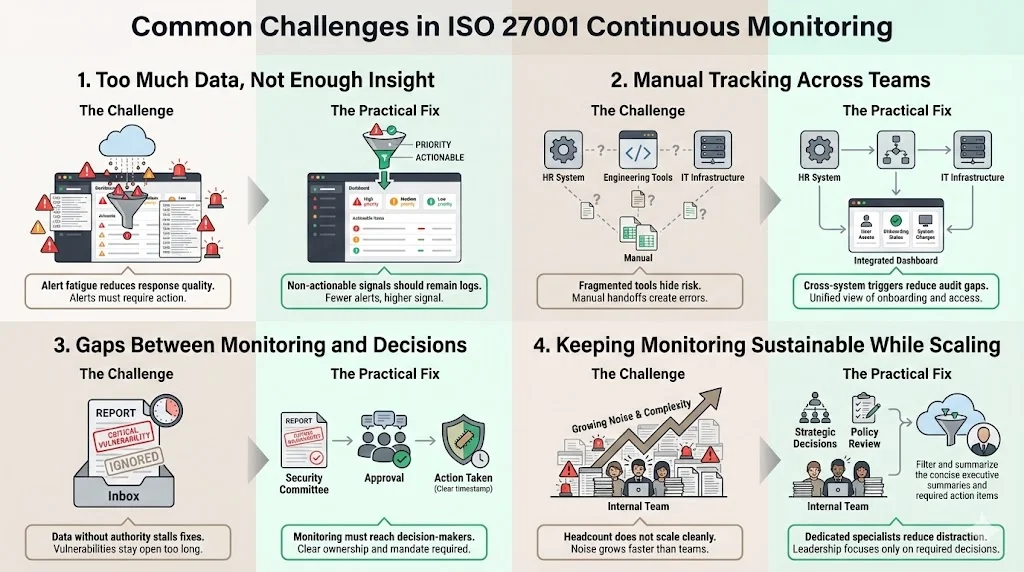
1) Too Much Data, Not Enough Insight
This is "alert fatigue." If your team gets 500 alerts a day, they will ignore 500 alerts a day. You must tune your monitoring to focus on actionable intelligence. If an alert does not require an action, it should be a log, not an alert.
2) Manual Tracking Across Teams
The HR team uses one system, Engineering uses another, and IT uses a third. Getting a unified view of "onboarding" is difficult. Integration is the solution. Automation scripts that trigger across platforms prevent the "copy-paste" errors that lead to audit findings.
3) Gaps Between Monitoring and Decision-Making
You have a report showing critical vulnerabilities, but no one authorizes the downtime to patch them. This is a governance failure. Monitoring data must flow to a decision-making body (like a Security Committee) that has the authority to mandate fixes.
4) How Growing Companies Can Keep Monitoring Sustainable
You can not throw bodies at this problem. You need a force multiplier. This is why managed services are replacing DIY compliance. A dedicated team that understands the nuances of the standards can filter the noise and present you with only the decisions you need to make.
How Continuous Monitoring Supports Enterprise Sales
We started this article discussing enterprise sales. Let us bring it back to the bottom line.
Meeting Vendor Security Reviews Faster
When a Fortune 500 buyer sends you a SIG (Standardized Information Gathering) questionnaire, they ask 800+ questions. If you have to research every answer, you lose weeks. If you have continuous monitoring, you know the answers. You can export evidence instantly.
Answering Due Diligence Questions with Proof
When a buyer asks, "Do you encrypt data?" anyone can say "Yes." But if you can say, "Yes, and here is a report from our monitoring system showing 100% encryption coverage across all databases for the last 12 months," you win the trust argument immediately.
Building Long-Term Trust
Enterprise contracts are long. You want to be a partner, not a liability. By demonstrating that you have a mature, monitored security program, you position yourself as a safe pair of hands for their most sensitive data. This reduces the friction in legal reviews and accelerates the path to revenue.
Conclusion
ISO 27001 continuous monitoring is more than a requirement of the standard; it is a fundamental business practice for any company selling to the enterprise. It moves security from a theoretical exercise to an operational reality.
At Konfirmity, we believe that you should start with security and arrive at compliance. When you build controls that work—and monitor them to ensure they stay working—the audit becomes a non-event. You stop fearing the auditor and start using your security posture as a competitive advantage.
Companies that attempt to manage this with spreadsheets or "compliance automation" software often find themselves drowning in alerts or failing to provide the human context auditors require. Security is complex. It requires interpretation, judgment, and expertise.
By adopting a managed, human-led approach to continuous monitoring, you ensure that your organization remains resilient against threats and ready for scrutiny every single day of the year. Do not build security for a certificate. Build it for your business.
Frequently Asked Questions (FAQ)
1) What is ISO 27017 and ISO 27018?
These are extensions to the core ISO 27001 standard.
- ISO 27017 provides additional controls for cloud services. If you are a SaaS provider or a heavy cloud user, this standard clarifies how roles and responsibilities are split between you and your cloud provider (e.g., AWS or Azure).
- ISO 27018 focuses specifically on the protection of PII (Personally Identifiable Information) in public clouds. It is vital for companies dealing with GDPR or privacy concerns.
- Relation to ISO 27001: They act as add-ons. You typically get certified against ISO 27001 with the additional controls from 27017/27018 included in your Statement of Applicability.
2) What is continuous monitoring in cyber security?
In plain terms, continuous monitoring is the real-time or near real-time automated collection and analysis of security data. Unlike periodic testing (like an annual pen test), continuous monitoring constantly watches networks, systems, and data for anomalies, vulnerabilities, and threats. It allows organizations to react to attacks immediately rather than discovering them months later.
3) What are the 4 types of controls in ISO 27001?
ISO 27001:2022 organizes controls into four themes:
- Organizational (Administrative): Policies, procedures, roles, and responsibilities (e.g., Access Control Policy).
- People: Human resources, screening, training, and disciplinary processes.
- Physical: Securing offices, data centers, and equipment (e.g., Clear Desk Policy).
- Technological: IT security measures like encryption, firewalls, logging, and malware protection.
4) What is Clause 10 of ISO 27001?
Clause 10 focuses on Improvement. It dictates that an organization must not just sit on its hands after implementing security. It requires you to react to non-conformities (failures) and take corrective action. Crucially, it requires "Continual Improvement"—using the outputs of your monitoring and risk assessments to constantly upgrade the suitability, adequacy, and effectiveness of the ISMS. Monitoring results are the fuel that powers Clause 10 activities.





.svg)





.svg)
.svg)