For many CTOs and engineering leaders, the decision to move to a multi-region setup is driven by technical necessity—latency reduction or disaster recovery. However, for the enterprise buyer evaluating your risk profile, a multi-region footprint is a proxy for maturity. It signals that you have graduated from "startup that breaks things" to "enterprise partner that protects assets."
SOC 2 Multi-Region Architectures specifically refer to cloud infrastructure designs that distribute data and compute resources across geographically distinct locations to satisfy specific AICPA Trust Services Criteria—primarily Availability and Confidentiality.
Why does this matter right now? Because the cost of downtime is increasing. Recent industry data from 2024 and 2025 indicates that for enterprise SaaS platforms, a single hour of downtime can cost upwards of $500,000 to $1 million in SLA credits, remediation costs, and reputational damage. When procurement teams send over their security questionnaires, they look for structural assurance that you can withstand localized outages.
If your SOC 2 report shows a single point of failure in us-east-1, your deal is at risk.
What is SOC 2 and Why It Matters for Enterprise Buyers
SOC 2 is based on the SSAE 18 standard developed by the AICPA. For B2B companies, it acts as the primary currency of trust. Enterprise procurement teams rarely have the time to audit your stack personally. Instead, they rely on a SOC 2 report to verify that you have implemented the necessary governance, risk management, and technical controls.
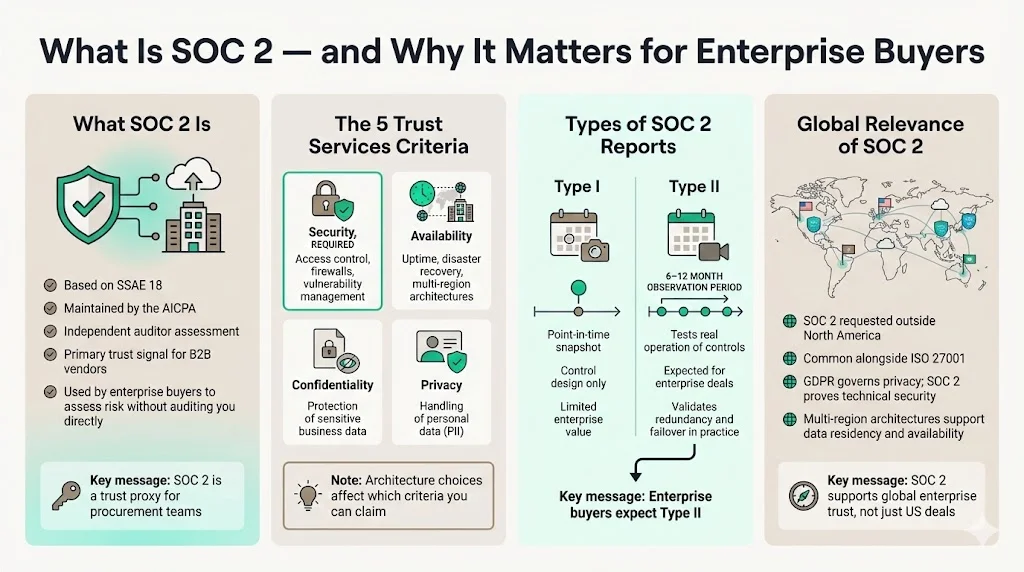
The 5 Trust Services Criteria
The AICPA defines five Trust Services Criteria (TSC). Your architecture directly impacts which of these you can claim:
- Security (Common Criteria): The baseline. Required for every SOC 2 audit. It covers access control, firewalls, and vulnerability management.
- Availability: This is where SOC 2 Multi-Region Architectures are critical. It addresses network performance, disaster recovery, and uptime commitments.
- Processing Integrity: Ensures system processing is complete, valid, accurate, timely, and authorized.
- Confidentiality: Protects information designated as confidential (e.g., proprietary business logic).
- Privacy: Addresses the collection, use, retention, disclosure, and disposal of personal information (PII).
Types of SOC 2 Reports
- Type I: A snapshot in time. It validates that your controls are designed correctly as of a specific date.
- Type II: The standard for enterprise deals. It verifies that controls operated effectively over an observation period (typically 6–12 months). This is where automated failover and multi-region redundancy are tested, not just described.
Is SOC 2 Relevant in Europe and Other Regions?
A common misconception is that SOC 2 is only for North America. In our experience supporting 6,000+ audits, we see European and Asian enterprises frequently demanding SOC 2 Type II reports alongside ISO 27001 certifications. While GDPR is the law of the land in Europe regarding privacy, SOC 2 provides the technical evidence that data is secure. For global SaaS companies, a multi-region strategy helps satisfy European data residency requirements while maintaining the security controls verified by SOC 2.
What Is Multi-Region Architecture?
A multi-region architecture involves deploying your application stack and data stores across two or more geographically separated cloud regions (e.g., AWS us-west-2 and eu-central-1).
Companies adopt this complexity for three reasons:
- Disaster Recovery (DR): If a hurricane, power grid failure, or fiber cut takes a region offline, the business continues elsewhere. The July 2024 global IT outage, which cost Fortune 500 companies an estimated $5.4 billion, vividly demonstrated the fragility of interdependent systems.
- Data Sovereignty: Keeping German data in Frankfurt and Australian data in Sydney to meet regulatory demands.
- Latency: Placing computers closer to the user.
However, moving from a single region to multiple regions introduces massive complexity in data consistency and deployment pipelines. This is where "compliance manufacturing"—generating paper policies without technical implementation—fails. You cannot "document" your way into multi-region resilience; you must build it.
How Multi-Region Architecture Supports SOC 2 Requirements
Integrating SOC 2 Multi-Region Architectures into your roadmap isn't just good engineering; it simplifies your audit conversations significantly.
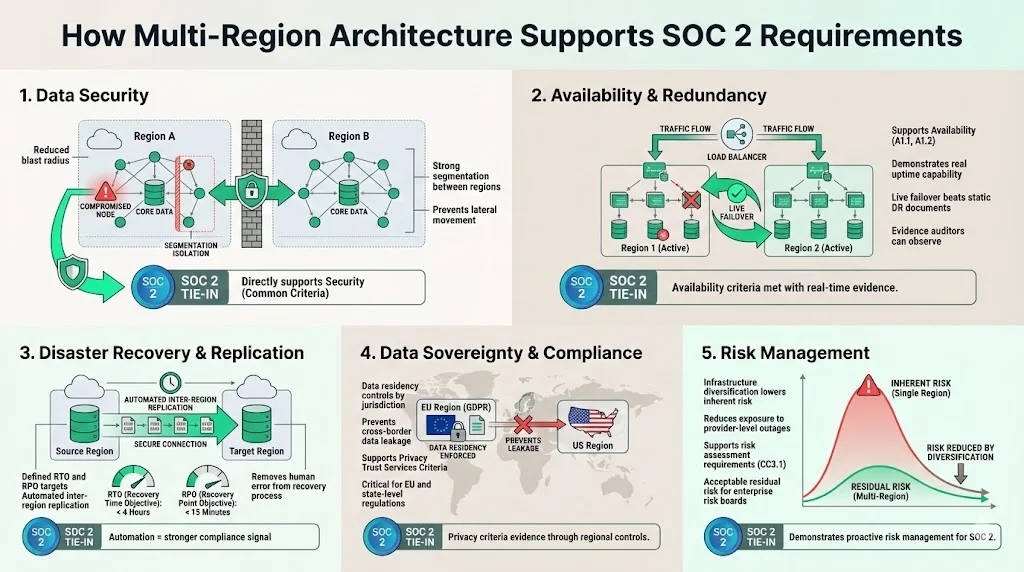
1) Data Security
Distributing services reduces the blast radius of a security incident. If an attacker compromises an edge node in one region, proper segmentation (a core Security criteria requirement) prevents lateral movement to your primary data store in another region.
2) Availability and Redundancy
The Availability criteria (A1.1, A1.2) asks for evidence that you have the capacity to meet your objectives. A multi-region setup allows you to demonstrate "active-active" or "active-passive" configurations. During an audit, showing a live failover capability is far more convincing than showing a theoretical DR plan document that hasn't been touched in two years.
3) Disaster Recovery and Inter-Region Replication
Auditors look for the ability to restore data within defined RTO (Recovery Time Objective) and RPO (Recovery Point Objective) limits. Cloud-native features like Cross-Region Replication (CRR) for S3 buckets or Global Tables in DynamoDB provide automated, verifiable evidence that data is preserved across boundaries. This automation is crucial. In our managed service model, we emphasize that human error is the enemy of compliance; automated replication removes the human variable.
4) Data Sovereignty and Compliance
When you sell to enterprise clients in regulated jurisdictions (like the EU or California), they will ask where their data resides. A well-designed multi-region architecture allows you to tag data by origin and enforce policies that prevent it from leaving a specific legal boundary, directly supporting the Privacy TSC.
5) Risk Management
Risk assessment is the foundation of SOC 2 (CC3.1). By diversifying your infrastructure footprint, you lower the inherent risk of provider-level outages. This allows you to present a "Residual Risk" rating that is acceptable to conservative enterprise risk boards.
Key Principles of a SOC 2 Multi-Region Architecture
Building SOC 2 Multi-Region Architectures requires adhering to specific design principles that satisfy auditors while keeping engineering overhead manageable.
1) Establish Trust Boundaries
You must define what is in scope. Not every microservice needs to be replicated globally. Identify the "Crown Jewels"—customer data, authentication services, and encryption keys. Create network segmentation that isolates these assets. In SOC 2 terms, this is about defining the "System Description" accurately.
2) Design for Fault Tolerance
Use Availability Zones (AZs) within a region for local high availability, and distinct regions for disaster recovery. Your architecture must handle the loss of a single component without human intervention. This maps to the SOC 2 requirement for "system resilience."
3) Automate Replication and Backups
One of the most frequent findings in Type II audits is failed backups. Manual backup processes eventually fail. Architect your storage layer to replicate automatically. Ideally, use immutable backups to protect against ransomware—a control that is increasingly requested by insurance providers and auditors alike.
4) Monitor and Alert Across Regions
You cannot protect what you cannot see. Centralized telemetry is non-negotiable. You need a unified view of security events (SIEM) across all regions. If an intrusion attempt happens in your Singapore region, your SOC (Security Operations Center) in Virginia needs to know instantly. This satisfies the "Security Monitoring" controls (CC7.1 - CC7.5).
5) Document Everything
This is where many technical teams stumble. You can have the best architecture in the world, but if there is no diagram, data flow map, or configuration standard, you will fail the audit. Architecture documentation is critical evidence. At Konfirmity, we maintain these artifacts continuously for our clients because we know that outdated docs are a red flag for auditors.
Step-by-Step Implementation Guide
Implementing SOC 2 Multi-Region Architectures is a systematic process. Based on our delivery of thousands of successful audit outcomes, here is the path we recommend.
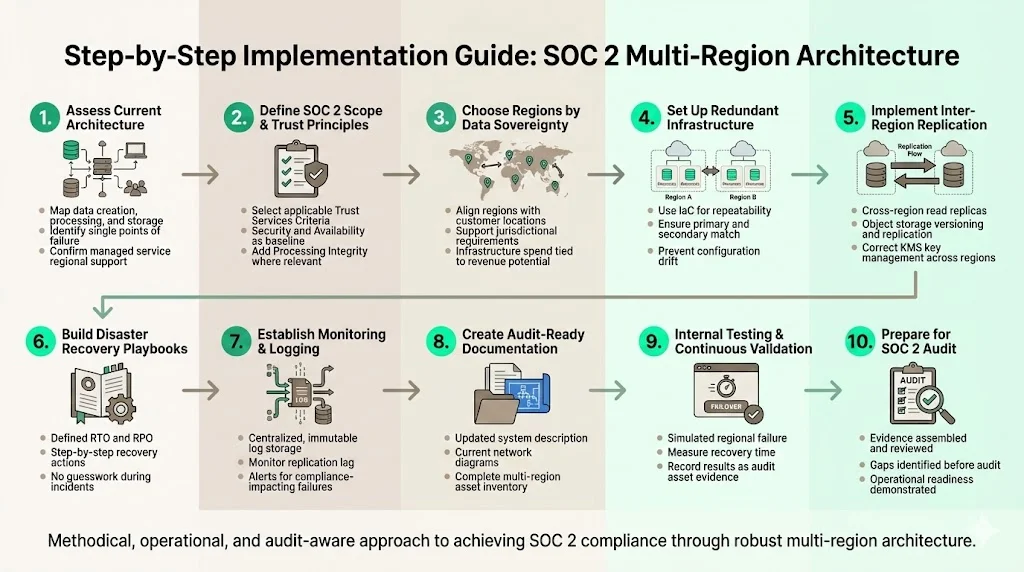
Step 1: Assess Your Current Architecture
Map your services. Identify where data is created, processed, and stored. Pinpoint single points of failure. If you use a managed service, does that provider support your target regions?
Step 2: Define SOC 2 Scope and Trust Principles
Decide which TSCs apply. If you are an e-commerce platform, Processing Integrity is vital. For most B2B SaaS, Security and Availability are the minimums.
Step 3: Choose Regions Based on Data Sovereignty
Don't just pick the cheapest region. Review your sales pipeline. If you have prospects in Germany, prioritize eu-central-1. Align your infrastructure spend with your revenue opportunities.
Step 4: Set Up Redundant Infrastructure
Use Infrastructure as Code (IaC) tools like Terraform or CloudFormation. You must ensure that your secondary region is a mirror of your primary. Configuration drift is a major compliance risk; IaC helps eliminate it.
Step 5: Implement Inter-Region Replication
Configure your databases (RDS, Postgres, MongoDB) for cross-region read replicas. Enable versioning and replication on object storage. Ensure encryption keys (KMS) are managed correctly across regions, as keys are often region-specific by default.
Step 6: Build Disaster Recovery Playbooks
A playbook is a script for humans. When the pager goes off at 3 AM, engineers should not be guessing. Define clear RTO/RPO targets. Document the exact commands to promote a read-replica to master.
Step 7: Establish Monitoring and Logging
Ship logs from all regions to a centralized, immutable storage bucket or a logging platform (like Datadog or Splunk). Set up alerts for replication lag. If replication stops, you are no longer compliant with your own DR policy.
Step 8: Create Audit-Ready Documentation
Draft the System Description. Update network diagrams. Ensure your inventory list includes assets in all regions.
Step 9: Internal Testing and Continuous Validation
Run a game day. Simulate a regional failure. Measure how long it takes to recover. Record the results—this report is "Exhibit A" for your auditor.
Step 10: Prepare for SOC 2 Audit
Gather your evidence. This is where the difference between "software" and a "managed service" becomes clear. Software sends you alerts; a partner like Konfirmity reviews the evidence, spots gaps, and fixes them before the auditor arrives.
Common Challenges and How to Handle Them
Even with the best SOC 2 Multi-Region Architectures, friction occurs.
Cost Management: Duplicating infrastructure doubles your compute capability but can double your bill. Use auto-scaling aggressively in the failover region to keep costs low until traffic shifts.
Data Consistency: The CAP theorem is real. Achieving strong consistency across regions introduces latency. Be prepared to explain to auditors how your system handles "eventual consistency" without corrupting transaction data.
Regulatory Limits: Some data cannot be replicated. You may need to shard your architecture so that EU data stays in the EU, even during a disaster. This "cell-based" architecture is complex but highly defensible.
Synchronizing Evidence: Collecting evidence from distributed systems is tedious. Ensure your compliance collection tools have read-access to all relevant accounts and regions.
Real-World Examples
Note: Client names are anonymized to protect confidentiality.
The "Paper Tiger" Failure: A FinTech startup claimed to have multi-region DR in their policies. During a Type II observation period, AWS suffered a partial outage in us-east-1. The startup's application went down for 14 hours. The auditor noted a "deviation" (exception) in their report because the controls designed (multi-region failover) failed to operate. The result? A "Qualified Opinion" report that stalled three major enterprise deals.
The Scaled Success: A healthcare SaaS provider working with Konfirmity needed to close a deal with a major hospital network. We helped them implement SOC 2 Multi-Region Architectures utilizing automated failover for their HIPAA-scoped environment. During the audit, we provided evidence of a successful quarterly DR test and automated backup logs. The clean SOC 2 Type II report, combined with the proven RTO of under 15 minutes, accelerated their procurement cycle by four months.
Conclusion
The demand for SOC 2 Multi-Region Architectures is driven by a simple market reality: enterprise buyers are risk-averse. They need to know that your business can survive the unexpected.
Implementing this level of resilience is heavy lifting. It requires deep expertise in cloud engineering, regulatory frameworks, and audit defense. This is why "Do It Yourself" compliance often fails. A typical self-managed SOC 2 preparation takes 9–12 months and often burns over 1,000 hours of internal engineering time annually.
At Konfirmity, we take a different approach. We don't just give you a checklist; we act as your dedicated security team. We implement the controls, configure the clouds, and manage the audit. Our clients typically reach readiness in 4–5 months and spend only about 75 hours a year on compliance tasks.
Don't build security just to pass an audit. Build it to protect your business and win the trust of your biggest customers. If you are ready to stop guessing and start executing, assess your architecture against SOC 2 criteria today.
FAQ Section
1) What is multi-region architecture?
It is a cloud infrastructure strategy where services and data are deployed across geographically distinct locations (regions) to ensure high availability, disaster recovery, and compliance. For enterprise B2B firms, SOC 2 Multi-Region Architectures are critical for meeting availability guarantees.
2) What are the 5 criteria for SOC 2?
The Trust Services Criteria are Security (common to all), Availability, Processing Integrity, Confidentiality, and Privacy.
3) What are the different types of SOC 2?
A Type I report assesses the design of security controls at a specific point in time. A Type II report assesses the operating effectiveness of those controls over a period (usually 6–12 months).
4) Is SOC 2 used in Europe?
Yes. While GDPR governs privacy law, European enterprises widely accept SOC 2 as proof of security competence. Many global companies require both.





.svg)





.svg)
.svg)