Most enterprise buyers now ask for evidence of security and compliance before they will sign a contract. In healthcare, the stakes are higher because regulated entities hold sensitive patient information and are subject to the Health Insurance Portability and Accountability Act (HIPAA). OCR enforcement has accelerated: 22 investigations led to settlements or civil monetary penalties in 2024, and by mid‑2025 penalties were issued against organizations ranging from small clinics to large retailers, with fines from $5,000 to $1.5 million for failures such as inadequate risk analysis or late breach notifications. Auditors are not interested in a paper exercise; they want evidence that controls are designed and operating effectively over time. In my experience helping hundreds of healthcare and technology firms through over 6,000 audits, effective programs prioritize security, document every requirement, and monitor continuously. This article lays out a pragmatic HIPAA documentation approach that draws on NIST guidance, OCR rules and real‑world patterns from the field.
Why documentation matters under HIPAA
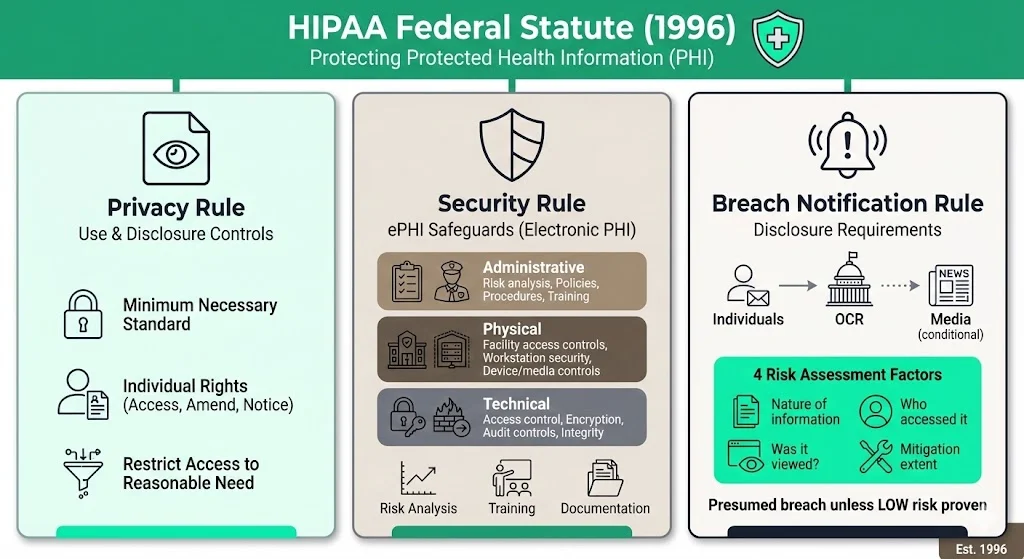
HIPAA is a federal statute created in 1996 to protect the confidentiality and availability of protected health information (PHI). Three rules are most relevant to documentation:
- Privacy Rule – defines how PHI may be used or disclosed and grants individuals rights to access, amend and receive notice of privacy practices. It embodies the “minimum necessary” standard requiring covered entities to restrict access and disclosure to what is reasonably needed for a given purpose.
- Security Rule – mandates administrative, physical and technical safeguards for electronic PHI (ePHI). Regulated entities must perform an accurate and thorough risk analysis, implement controls to reduce risks to an appropriate level and designate a security officer. They must also train workforce members on security policies and document incidents, sanctions and contingency plans.
- Breach Notification Rule – requires covered entities and business associates to notify affected individuals, OCR and sometimes the media after a breach of unsecured PHI. An impermissible use or disclosure is presumed to be a breach unless a risk assessment shows a low probability that the data were compromised. Four factors must be considered: the nature of the information involved, who accessed it, whether it was viewed and the extent of mitigation.
Regulated entities include health plans, healthcare providers and clearinghouses. Business associates such as billing firms, IT providers or transcription services also must comply when they handle PHI on behalf of a covered entity. Documentation is critical because:
- Proving compliance – the Security Rule’s documentation requirement (§ 164.316) states that entities must maintain written (or electronic) policies, procedures and records of actions, activities and assessments. The NIST SP 800‑66 guide emphasizes that risk analysis is the foundation of compliance and that entities must document decisions about administrative, technical and physical controls.
- Audit readiness – auditors will ask for risk assessment reports, incident logs, training records and evidence of policy enforcement over an observation period. A documented program allows you to demonstrate control design and operating effectiveness, essential for SOC 2 Type II or ISO 27001 certifications. A SOC 2 Type II audit, for example, covers control operation over three to twelve months.
- Incident response – when a breach occurs, your ability to provide timely notifications depends on having a well‑documented process with clear roles, contact lists and decision criteria. OCR settlements show that late or incomplete breach notifications lead to significant penalties.
What is a HIPAA Documentation Toolkit?
A HIPAA documentation toolkit is a curated collection of policies, procedures, templates, logs and records that help a regulated entity meet HIPAA requirements. It should provide a ready‑to‑use framework that you can adapt to your specific risks, systems and workflows. Unlike generic “compliance software,” a human‑led program builds controls inside your tech stack and keeps you audit‑ready year round. At Konfirmity we often describe our approach as “start with security and arrive at compliance.” A toolkit operationalizes that philosophy by ensuring that every requirement is documented, implemented and monitored.
CTA: Book a demo
Core components of a HIPAA documentation toolkit
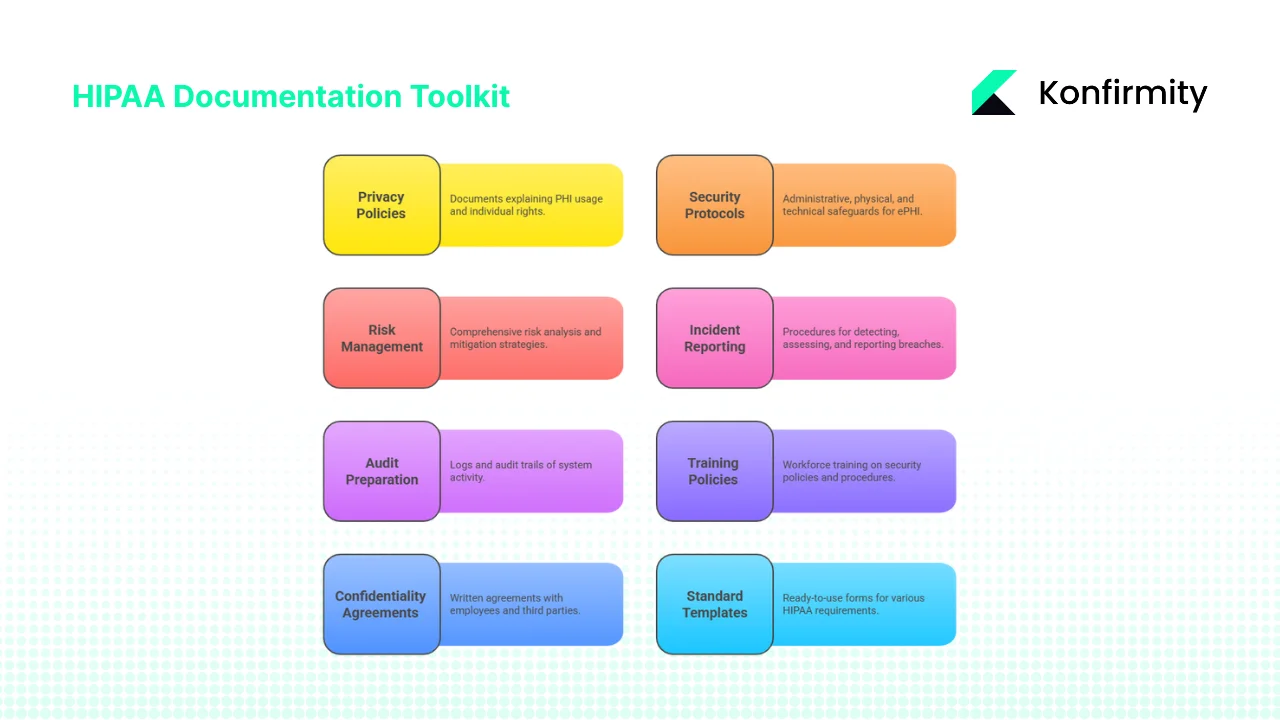
- Privacy policies – documents explaining what PHI is, how it may be used or disclosed and the rights of individuals to access, amend and restrict their information. The policies should incorporate the “minimum necessary” standard and outline procedures for responding to access requests and amendments. A notice of privacy practices must be provided and acknowledged by patients.
- Security protocols – administrative safeguards such as assigning a security officer, workforce training and sanctions; physical safeguards such as facility access controls and device management; and technical safeguards like access control, audit controls, authentication and transmission security. Policies should address encryption, logging, least‑privilege access and secure disposal. For example, NIST SP 800‑66 states that entities must implement reasonable and appropriate policies and procedures and document changes.
- Risk management documentation – a comprehensive risk analysis is a required implementation specification under § 164.308. Reports should identify assets, external sources of ePHI, threats and vulnerabilities, evaluate likelihood and impact, and prioritize mitigation. Documentation should show how decisions about security controls were made and track risk levels over time.
- Incident reporting and breach notification procedures – documented processes for detecting incidents, assessing whether a breach occurred and notifying affected parties. The Breach Notification Rule outlines factors for determining breach probability and requires notification of individuals and OCR. Templates should include fields for date/time, description, affected records, containment actions and notification status.
- Audit preparation and record‑keeping – logs and audit trails of system activity are mandatory under the Security Rule. A toolkit should include access log templates, audit checklists and a register of external audits or assessments. Keep risk assessment reports, policy revisions, training records and incident reports for at least six years.
- Training policies and records – the Security Rule requires workforce members to be trained on security policies and procedures. Documentation should include training schedules, attendance records, acknowledgement forms and refresh protocols. OCR settlements in 2024 highlight penalties against entities that failed to train staff.
- Confidentiality and business associate agreements (BAAs) – written agreements with employees and third‑party partners who handle ePHI are required. BAAs must ensure that associates comply with the Security Rule and agree to notify the covered entity of breaches. Include confidentiality statements for staff, vendors and contractors.
- Standard templates and procedural documentation – ready‑to‑use forms for privacy policies, security protocols, risk assessments, incident reports, training acknowledgements and BAAs. These templates enable consistency and speed when responding to audits or incidents.
The case for a structured toolkit
In 2024 about 275 million healthcare records were breached in the United States, and the average cost of a healthcare breach reached $10.22 million. OCR enforcement is focusing on documented risk analysis and mitigation: most 2025 settlements involved failures to conduct a risk analysis or maintain adequate policies. A well‑designed toolkit not only fulfils regulatory requirements but reduces the time your team spends reinventing documents. In our practice, using a common set of templates and controls typically reduces internal effort from 550–600 hours a year to around 75 hours. This frees engineers and clinicians to focus on their primary duties while maintaining compliance.
Step‑by‑step guide to building your toolkit
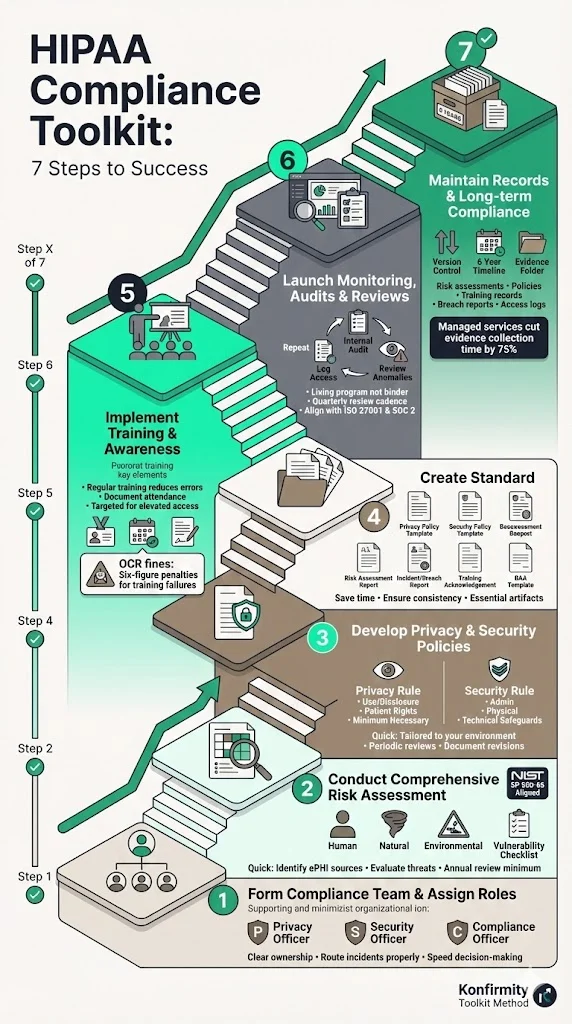
Step 1: Form a HIPAA compliance team and assign roles
Appoint a Privacy Officer and Security Officer responsible for documenting and enforcing policies. For larger organizations, a Compliance Officer may oversee the overall program. Make these roles explicit and communicate them to all staff so that incidents and policy questions are routed properly. Having clear ownership reduces ambiguity and speeds up decision‑making during incidents.
Step 2: Conduct a comprehensive risk assessment
Follow the NIST SP 800‑66 guidance: risk analysis is the first step toward compliance. Identify all sources of ePHI (internal systems, third‑party platforms, data flows). Evaluate threats—human, natural and environmental—and assess vulnerabilities such as weak access controls, unpatched systems or insufficient training. Document the likelihood and impact of each risk and decide which controls will reduce risk to an acceptable level. Keep reports and supporting evidence in your toolkit; auditors will want to see them. Perform the assessment at least annually and whenever you implement significant changes (new systems, acquisitions, external partners).
Step 3: Develop privacy and security policies and procedures
Use the findings from your risk analysis to design policies tailored to your environment. For privacy policies, explain how PHI may be used and disclosed, describe individuals’ rights to access and amend their information, and incorporate the minimum necessary standard. For security policies, address administrative, physical and technical safeguards: least‑privilege access, authentication, encryption, device management, secure disposal, and change management. Establish processes for responding to security incidents, sanctioning non‑compliance and backing up data. Review policies periodically; NIST recommends updating them as your organization changes and documenting any revisions.
Step 4: Create standard templates and documentation artifacts
Templates save time and ensure consistency. Essential templates include:
- Privacy policy template – sections: scope; definition of PHI; permitted uses/disclosures; patient rights (access, amendments, restrictions); minimum necessary principle; procedures for handling access requests; sanctions for violations.
- Security policy template – administrative safeguards (risk management, roles, training, sanction policy), physical safeguards (facility access, workstation security, device disposal), technical safeguards (authentication, encryption, audit controls, transmission security); sections on data classification, change management and vendor management.
- Risk assessment report template – inventory of systems and data, identified threats and vulnerabilities, likelihood and impact scores, mitigation actions, residual risk, and responsible owners.
- Incident/breach report template – date, time and description; systems involved; nature of PHI exposed; detection method; containment steps; risk assessment outcome; notifications (to individuals, OCR, media); corrective actions.
- Training acknowledgement form – training topic, date, employee name, signature, acknowledgement of understanding and commitment to comply.
- Business associate agreement template – permitted uses/disclosures, safeguarding requirements, breach notification obligations, obligations of subcontractors, termination clause.
Step 5: Implement training and awareness across staff
Employees are often the weakest link. Regular training reduces human error and demonstrates due diligence. At minimum, train new hires and conduct annual refreshers. Cover privacy policies, access controls, phishing awareness and incident reporting. Document attendance and have employees sign acknowledgement forms. Use targeted training for roles with elevated access. OCR fines show that failing to train workforce members can lead to six‑figure penalties.
Step 6: Launch monitoring, audits, reviews and updates
Continuous monitoring differentiates a living program from a binder collecting dust. Implement technical controls to log access to ePHI and system changes. Conduct periodic internal audits against your compliance checklist. Review logs for anomalies and test the effectiveness of controls. Update risk assessments and policies based on new threats or changes in the environment. In our experience, a quarterly review cadence is sustainable for most teams and aligns with ISO 27001 and SOC 2 observation periods.
Step 7: Maintain record‑keeping and ensure long‑term compliance
HIPAA requires records to be retained for at least six years. This includes risk assessment reports, policies, procedures, training records, breach reports and logs of access to PHI. Keep version control for policies and document who approved changes. When working with external auditors, provide evidence of continuous operation over the audit period, such as logs showing weekly access reviews or quarterly vulnerability scans. With a managed service like Konfirmity, teams typically cut the time spent on evidence collection by 75% compared with doing it themselves.
CTA: Book a demo
Sample templates and mini case example
Below are simplified outlines illustrating how toolkit artifacts might be structured. They are not full policies but show the key sections auditors expect.
Privacy policy template
- Scope: identifies which systems, departments and data types the policy covers.
- Definitions: explains PHI and ePHI.
- Permitted uses/disclosures: treatment, payment, healthcare operations; required disclosures; uses requiring an authorization.
- Patient rights: access, amendment, restriction, accounting of disclosures, right to complain.
- Minimum necessary: procedures to ensure only the minimum data are accessed or disclosed.
- Procedures for requests and complaints: how individuals can request access or file complaints; contact information.
Security policy template
- Administrative safeguards: risk analysis, risk management, assigned security officer, training and sanctions.
- Physical safeguards: facility access controls, workstation security, device/media controls.
- Technical safeguards: access control, audit controls, integrity controls, authentication, transmission security.
- Incident response: detection, containment, assessment, notification.
- Change management: procedures for introducing new systems or technology.
Incident/breach report template
- Date and time of discovery
- Description of the event: systems affected, type of PHI involved.
- Risk assessment: evaluation of the factors in the Breach Notification Rule.
- Containment and mitigation: actions taken to stop the breach and remediate.
- Notifications: individuals notified, OCR report date, media notification if required.
- Corrective actions: policy changes, training, technical controls.
Employee confidentiality and training acknowledgement
A one‑page form stating that the employee understands their responsibilities regarding PHI, agrees to comply with policies, has completed required training and will report suspected incidents promptly.
Business associate agreement template
- Permitted activities – specify how the associate may use or disclose PHI.
- Safeguards – require reasonable administrative, physical and technical safeguards.
- Reporting obligations – require notification of any breach or security incident.
- Subcontractor compliance – ensure subcontractors agree to the same conditions.
- Termination clause – allow termination if the associate fails to comply.
Mini case: implementing a toolkit in a small clinic
A five‑physician clinic in Mumbai wanted to streamline HIPAA documentation ahead of partnering with a U.S. telemedicine platform. With guidance from our team, they formed a compliance committee and used our templates to conduct a risk assessment. They discovered that lab reports were being sent via unencrypted email to an external billing vendor. The risk assessment rated this medium‑high and recommended adopting a secure file transfer platform with TLS 1.3 encryption and multi‑factor authentication. The clinic updated its security policy, executed a BAA with the vendor and trained staff on the new process. Within four weeks they completed the toolkit, documented all procedures and passed the telemedicine vendor’s due‑diligence review. The time invested was about 80 hours, compared with an estimated 250 hours without templates. More importantly, the clinic’s leaders gained confidence that they were meeting both HIPAA and international privacy obligations.
Using third‑party toolkits and compliance tools
Third‑party HIPAA toolkits can accelerate documentation by bundling policies, checklists, training modules and audit‑ready templates. These kits are helpful for smaller clinics with limited compliance staff or for larger organizations looking to standardize across departments. When evaluating a toolkit, consider:
- Alignment with current rules – verify that the toolkit reflects the latest HIPAA updates and proposed security rule modifications. In January 2025 OCR released a Notice of Proposed Rulemaking to strengthen the Security Rule, adding more detailed requirements for access management and encryption. Toolkits should incorporate guidance from this NPRM and NIST SP 800‑66r2.
- Customizability – templates are starting points, not final documents. You must adapt policies to your unique workflows, systems and risks. NIST cautions that there is no one‑size‑fits‑all risk analysis methodology.
- Integration with other frameworks – if your organization also pursues SOC 2 or ISO 27001, look for toolkits that map HIPAA requirements to other control frameworks. For example, SOC 2 Type II audits evaluate the design and operating effectiveness of controls over three to twelve months. Many HIPAA safeguards overlap with the SOC 2 Trust Services Criteria (security, confidentiality, privacy), allowing you to reuse evidence across audits.
Even with a pre‑built toolkit, you remain responsible for implementing controls and maintaining documentation. Our observation across 6 000+ audits is that organizations that treat toolkits as a substitute for operational security fail audits, while those that use them as a starting point succeed.
Common pitfalls and how to avoid them
- Treating compliance as a one‑time project – HIPAA compliance is ongoing. Policies, risk assessments and training must be updated when new technologies are adopted or when threats change. In 2024 OCR penalized organizations for not reevaluating risks after system changes.
- Inadequate risk analysis – many 2025 settlements were due to missing or insufficient risk analyses. Conduct a thorough assessment that identifies all ePHI flows and documents decisions about controls.
- Lack of documentation – verbal policies or undocumented procedures do not satisfy OCR. Maintain written records of policies, training and incidents. Document decisions about why a particular control or alternative measure was selected.
- Poor access control and monitoring – failing to implement access controls and audit logs leads to unauthorized disclosures. Review access regularly and keep records of system activity. Many breaches result from credential misuse or unchecked vendor access.
- Missing or outdated BAAs – ensure that every vendor or partner that handles ePHI signs a current BAA. OCR penalties in 2025 included fines for missing agreements.
- Insufficient training and awareness – untrained staff can cause breaches through phishing, misdirected emails or social media posts. Document training sessions and refreshers.
CTA: Book a demo
Conclusion
A HIPAA documentation toolkit is not just about producing paperwork; it is a living system that demonstrates how your organization protects patient data and mitigates risk. By building a toolkit with privacy policies, security protocols, risk assessment reports, incident response procedures, training records and BAAs, you can show auditors and partners that your controls are designed and operating effectively. Implementing this toolkit reduces the chance of costly breaches—healthcare breaches cost an average $10.22 million in 2024—and shortens sales cycles by answering security questionnaires with documented evidence.
The most effective programs start with security: they design controls into the technology stack, monitor continuously and document everything. Compliance becomes a natural outcome rather than a separate project. Use the steps and templates in this guide to build your HIPAA documentation toolkit, and revisit it regularly as your organization and the regulatory landscape evolve.
Frequently asked questions
1) What is a HIPAA documentation toolkit?
It is a collection of policies, procedures, templates, logs and records designed to help an organization comply with HIPAA’s Privacy, Security and Breach Notification requirements. It includes privacy and security policies, risk assessment reports, incident response procedures, training records and business associate agreements.
2) Who needs to maintain HIPAA documentation?
Covered entities such as healthcare providers, health plans and clearinghouses, and business associates handling PHI or ePHI must maintain documentation of their policies, procedures, risk assessments, training and incident records.
3) How often should documentation be reviewed or updated?
Periodically and whenever there is a significant change—new technology, changes in staff or roles, updated regulations, an incident or after an audit. NIST guidance stresses updating policies and documentation as your organization changes and documenting revisions.
4) Are ready‑made HIPAA toolkits enough on their own?
They provide a solid baseline with templates and checklists, but you must adapt them to your organization’s specific workflows, risk profile and technology. There is no one‑size‑fits‑all risk analysis methodology.
5) What happens if we do not maintain proper documentation?
Without documentation, you may not be able to demonstrate compliance during an audit or after a breach. OCR settlements in 2024 and 2025 show that failures to conduct risk analyses, maintain policies or provide timely breach notifications result in significant fines and can damage trust with patients and partners.





.svg)






.svg)
.svg)